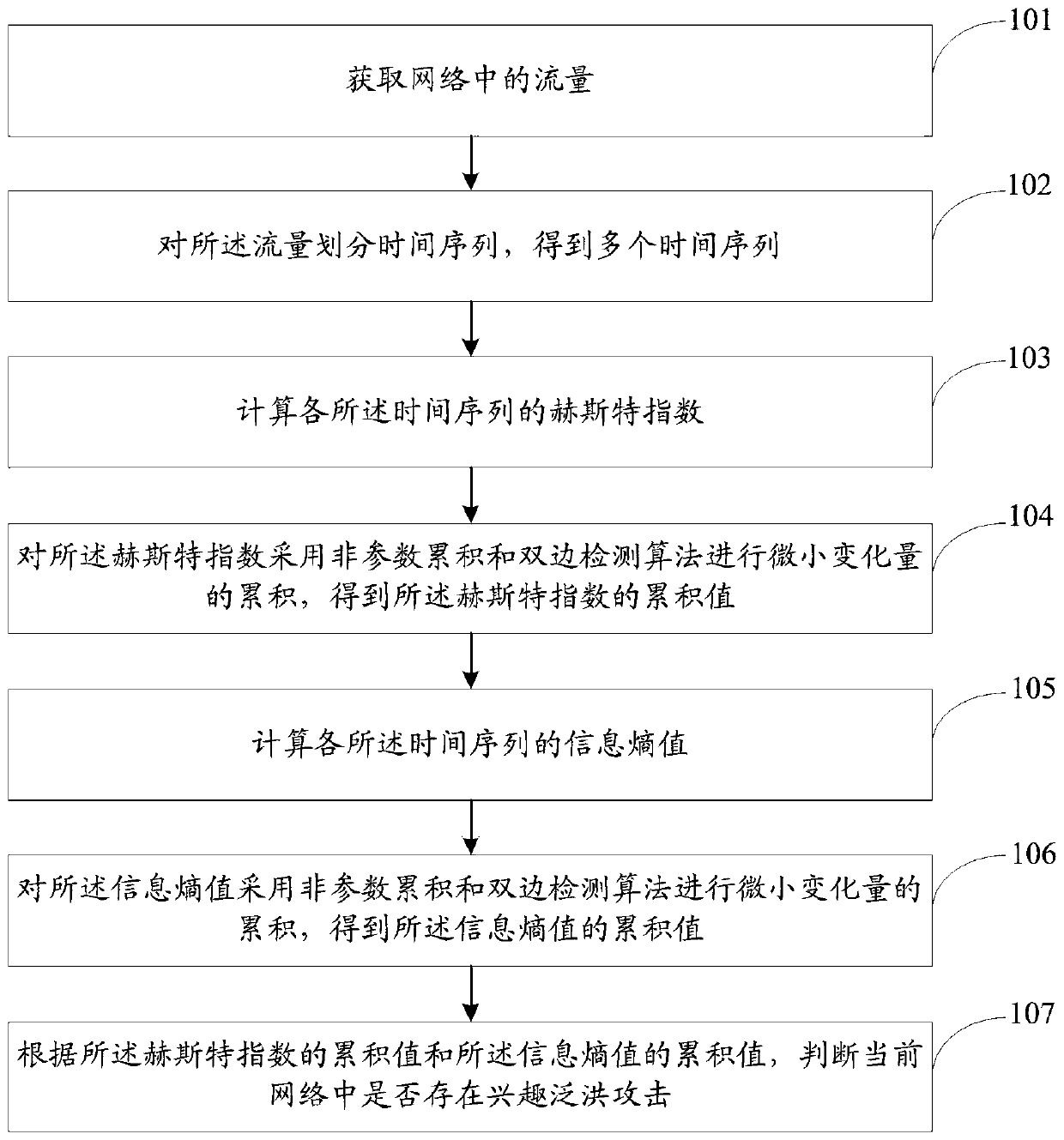
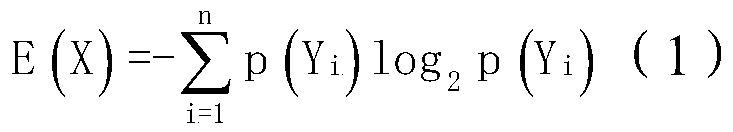Content center network interest flooding attack detection method and system
A content-centric network, flooding attack technology, applied in the field of content-centric network interest flooding attack detection, can solve problems such as interest flooding attacks, and achieve the effect of solving interest flooding attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
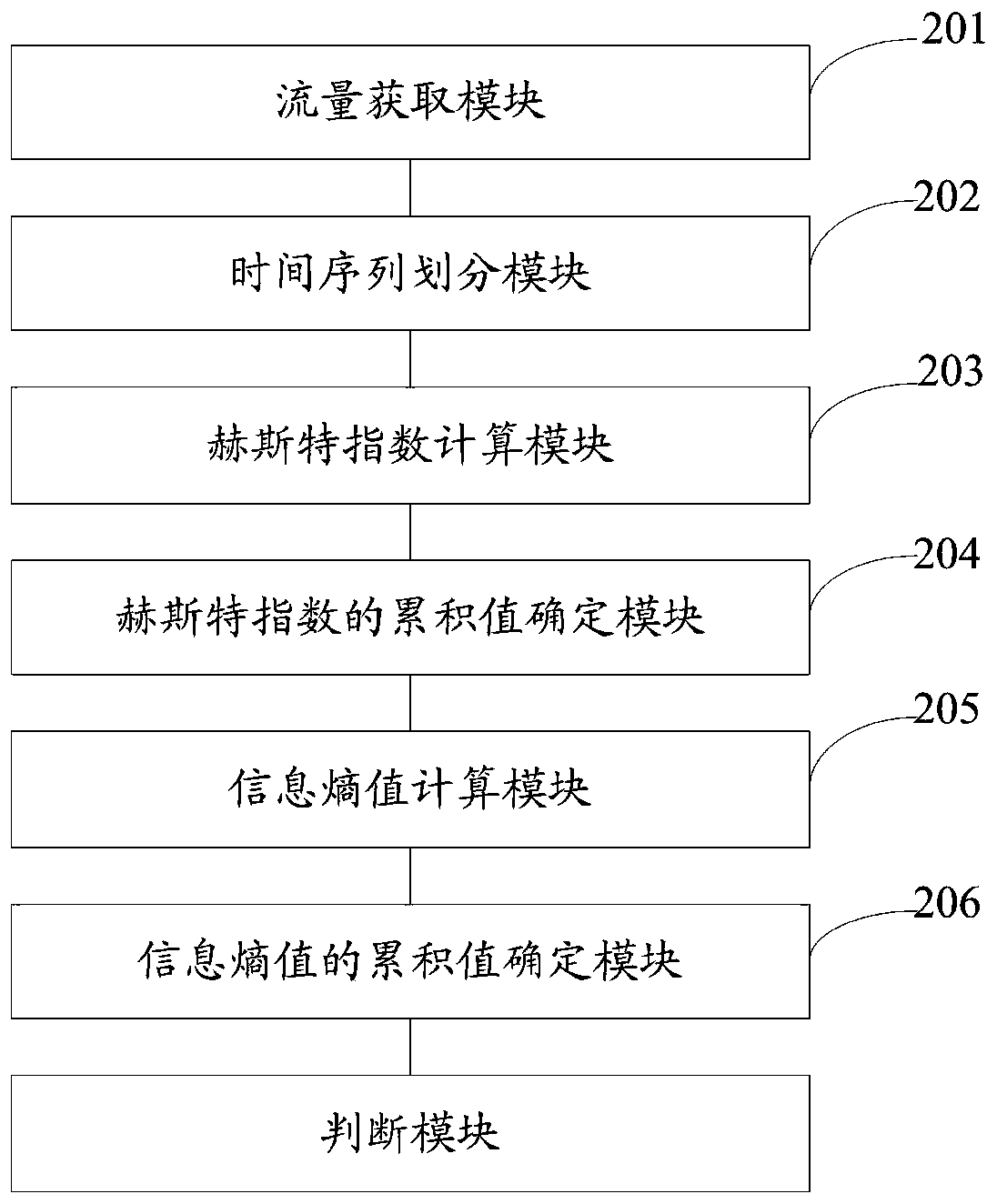
[0091] figure 2 It is a structural diagram of a detection system for interest flooding attacks in a content-centric network according to Embodiment 2 of the present invention. Such as figure 2 As shown, a detection system for interest flooding attacks in content-centric networks, including:
[0092] The traffic acquisition module 201 is configured to acquire traffic in the network.
[0093] The time series division module 202 is configured to divide the traffic into time series to obtain multiple time series.
[0094] The Hurst exponent calculation module 203 is configured to calculate the Hurst exponent of each time series.
[0095] The cumulative value determination module 204 of the Hurst exponent is used for accumulating the small variation of the Hurst exponent using a non-parametric accumulation and bilateral detection algorithm to obtain the cumulative value of the Hurst exponent.
[0096] An information entropy calculation module 205, configured to calculate the ...
Embodiment 3
[0102] S10, counting traffic in the network. Whenever an interest packet is received, information such as the content name of the interest packet, the number of requests, and the current time are collected.
[0103] Among them, the specific process of S10 is as follows:
[0104] S101, expanding the router PIT structure, adding a count field to record the number of times the Interest packet with the content name is requested in the current router;
[0105] S102. Whenever the network receives an Interest packet, record information such as the content name, count value, and current time of the current Interest packet.
[0106] For example, the data "10027999 nanoseconds since start of simulation: / root / good / %FE%03:14" indicates that at time 10027999ns, the interest packet with the content name " / root / good / %FE%03" was requested The number of times is 14.
[0107] S20, defining the size of the sliding window value, and dividing the collected network traffic into time series, so a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com