Securing communication of devices in the internet of things
A device and network technology, applied in the field of device communication in the protection of the Internet of Things, can solve problems such as low bandwidth
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] A detailed description of the illustrative embodiments will now be described with reference to the accompanying drawings. While this description provides detailed examples of possible implementations, it should be noted that the details are intended to be exemplary, and in no way limit the scope of the application.
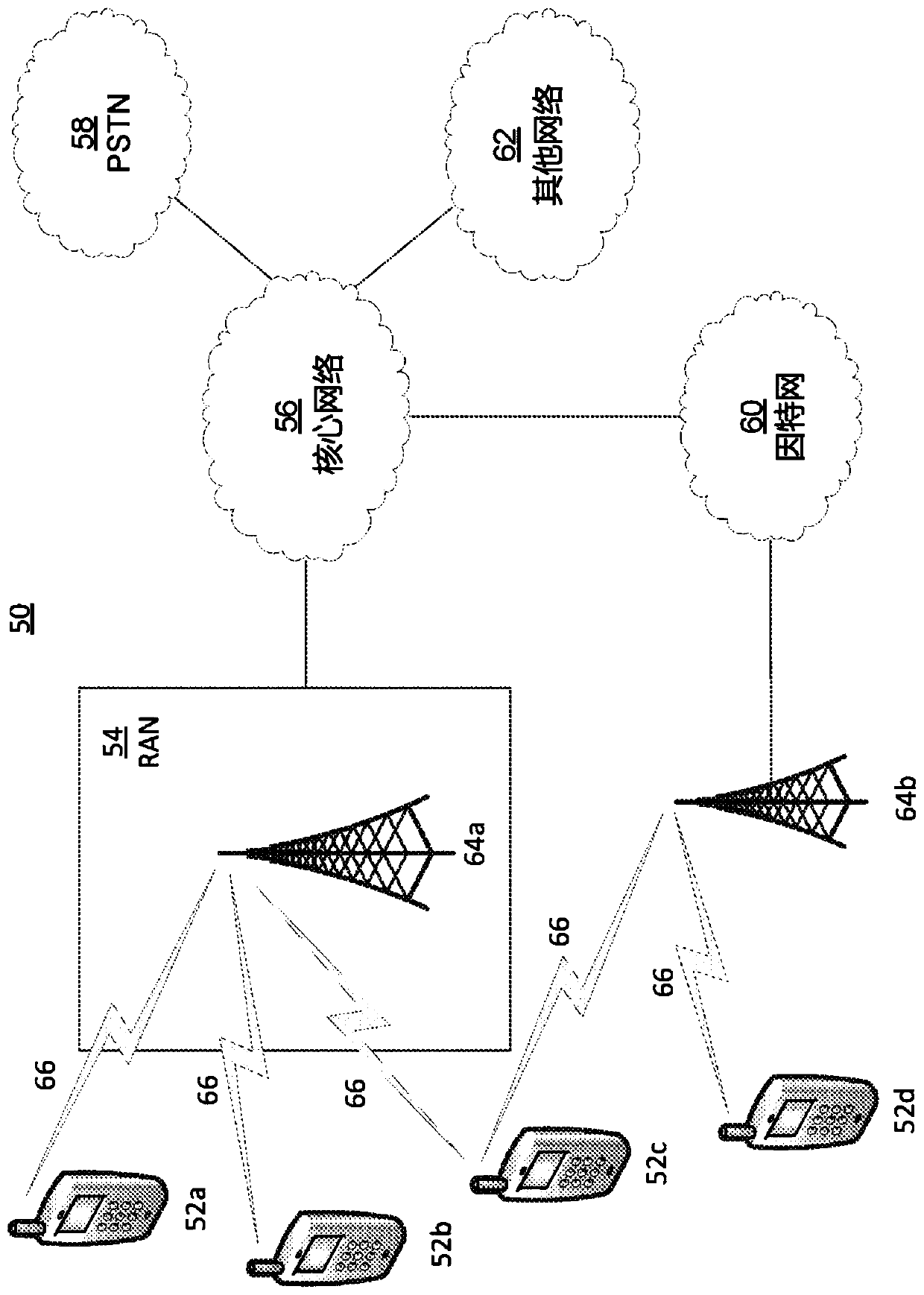
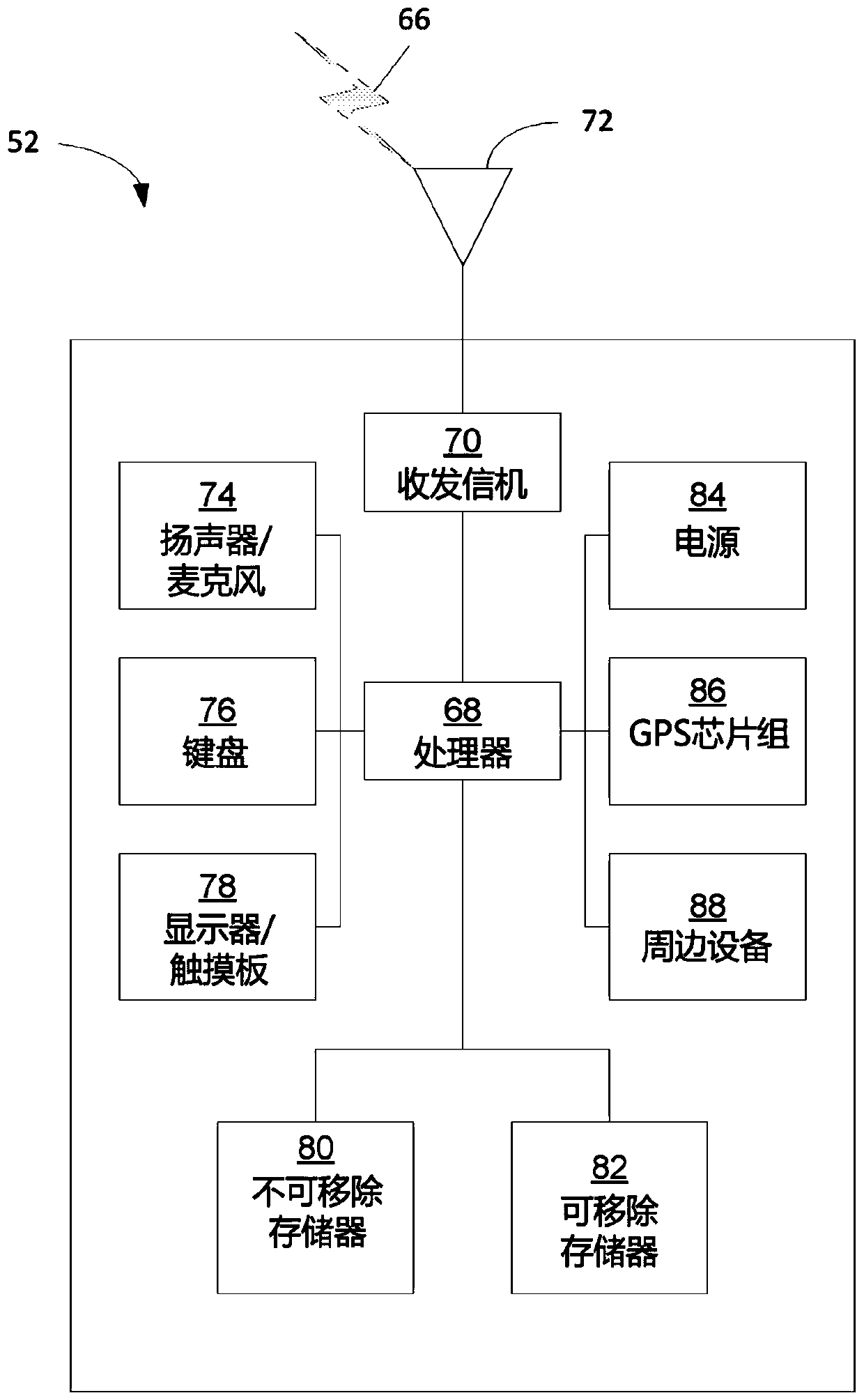
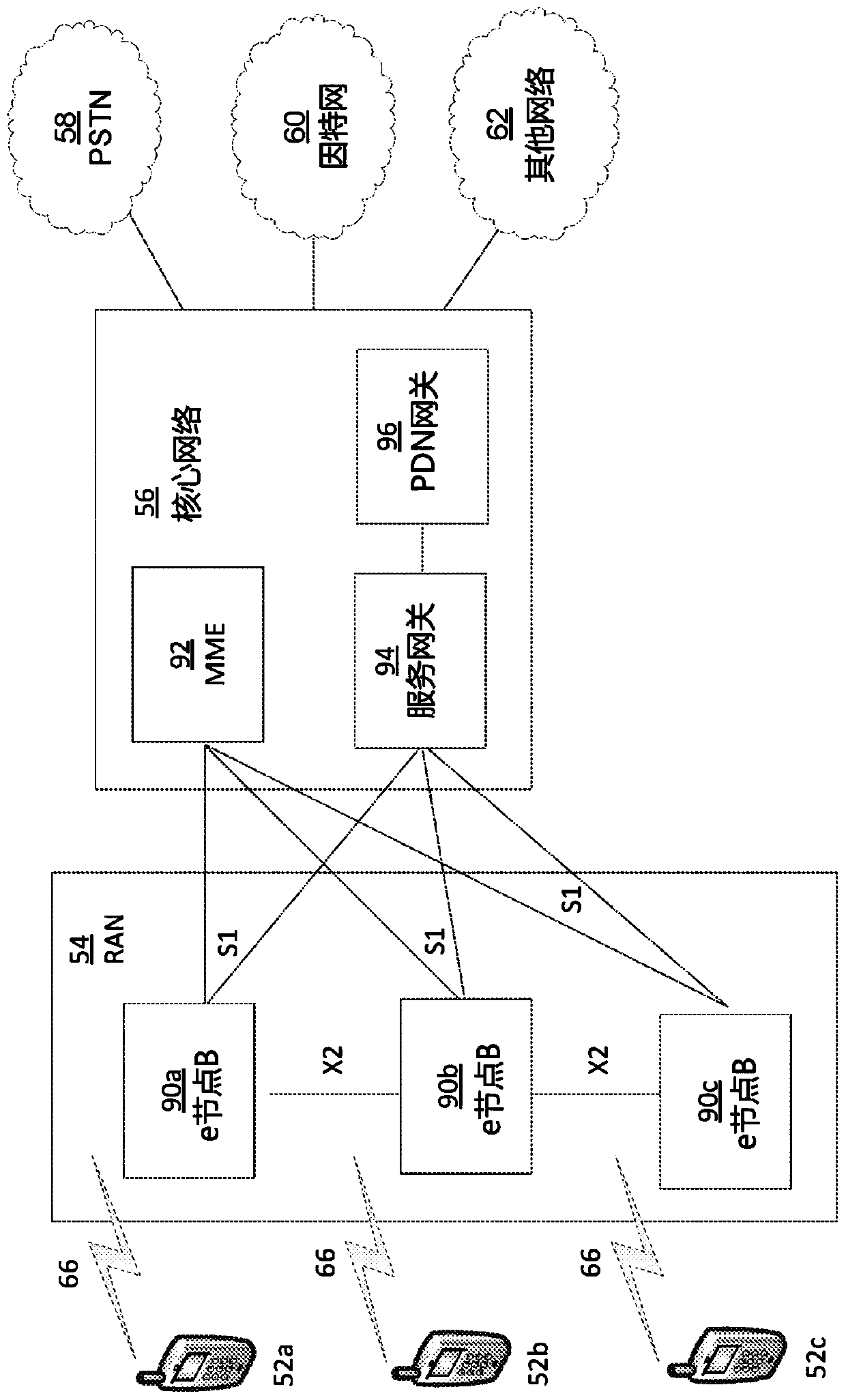
[0019] This paper recognizes that popular messaging protocols for IoT architectures are often weak for even basic security. It is further recognized here that some proposed solutions (e.g., using TLS and X.509 certificates for authentication and channel protection) are not suitable for resource-constrained devices and persistent IoT deployments. For example, encryption certificates with a limited lifetime are not suitable for long-term deployments. Therefore, it is recognized here that some features are missing in current IoT architectures based on publish / subscribe protocols. For example, in various example embodiments described below, there is a device-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com