Policy configuration method and system for cloud safety, electronic equipment and storage medium
A technology of security configuration and policy configuration, applied in the field of security on the cloud, can solve problems such as inconsistent security configuration policies, short life cycle, lack of security policy management, etc., to reduce complexity, improve operation and maintenance efficiency, and increase flexibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The specific implementations of a multi-standard security benchmark detection method, system, target host, server, electronic device, and storage medium provided by the embodiments of the present invention will be described below with reference to the accompanying drawings.
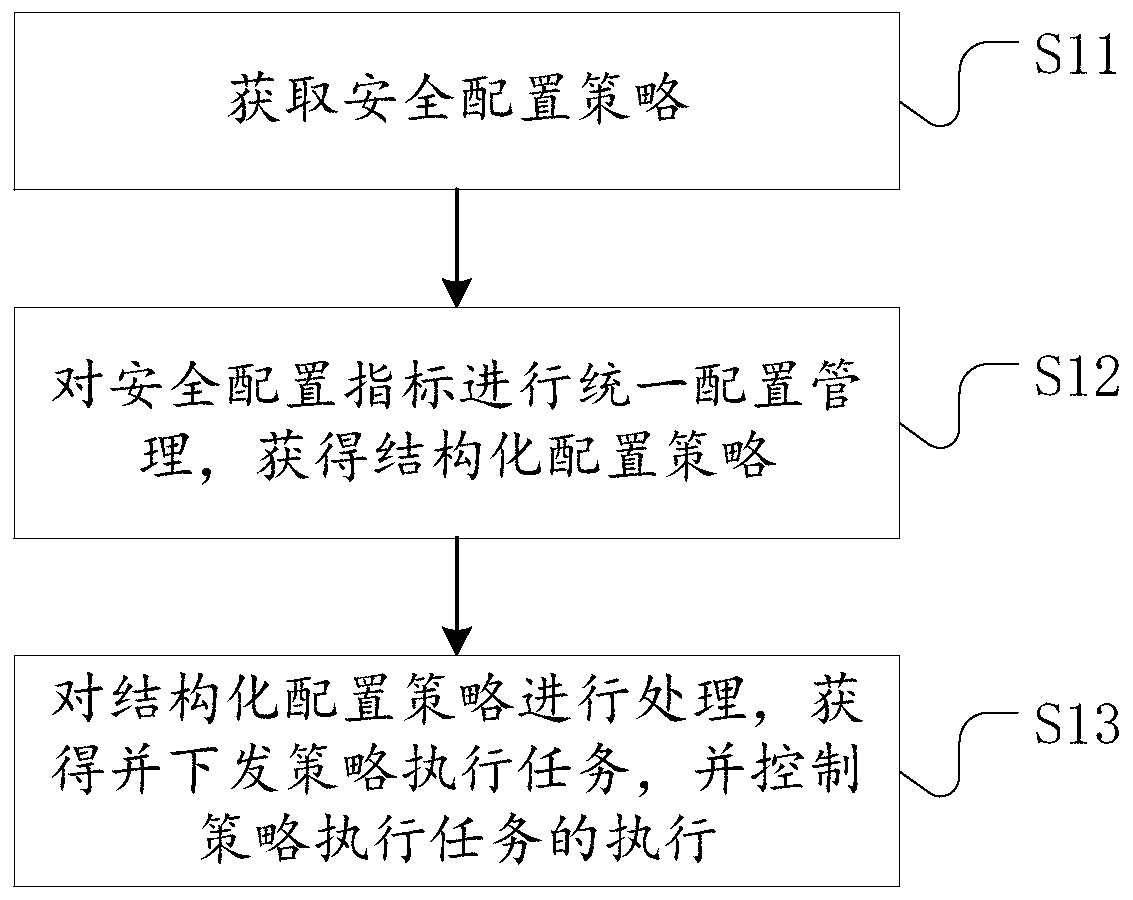
[0060] figure 1 A flowchart of a policy configuration method for cloud security provided by an embodiment of the present invention, as shown in figure 1As shown, the method includes the following steps:
[0061] Step S11: Obtain a security configuration policy, which includes security configuration indicators;
[0062] Step S12: Perform unified configuration management on security configuration indicators to obtain structured configuration strategies;
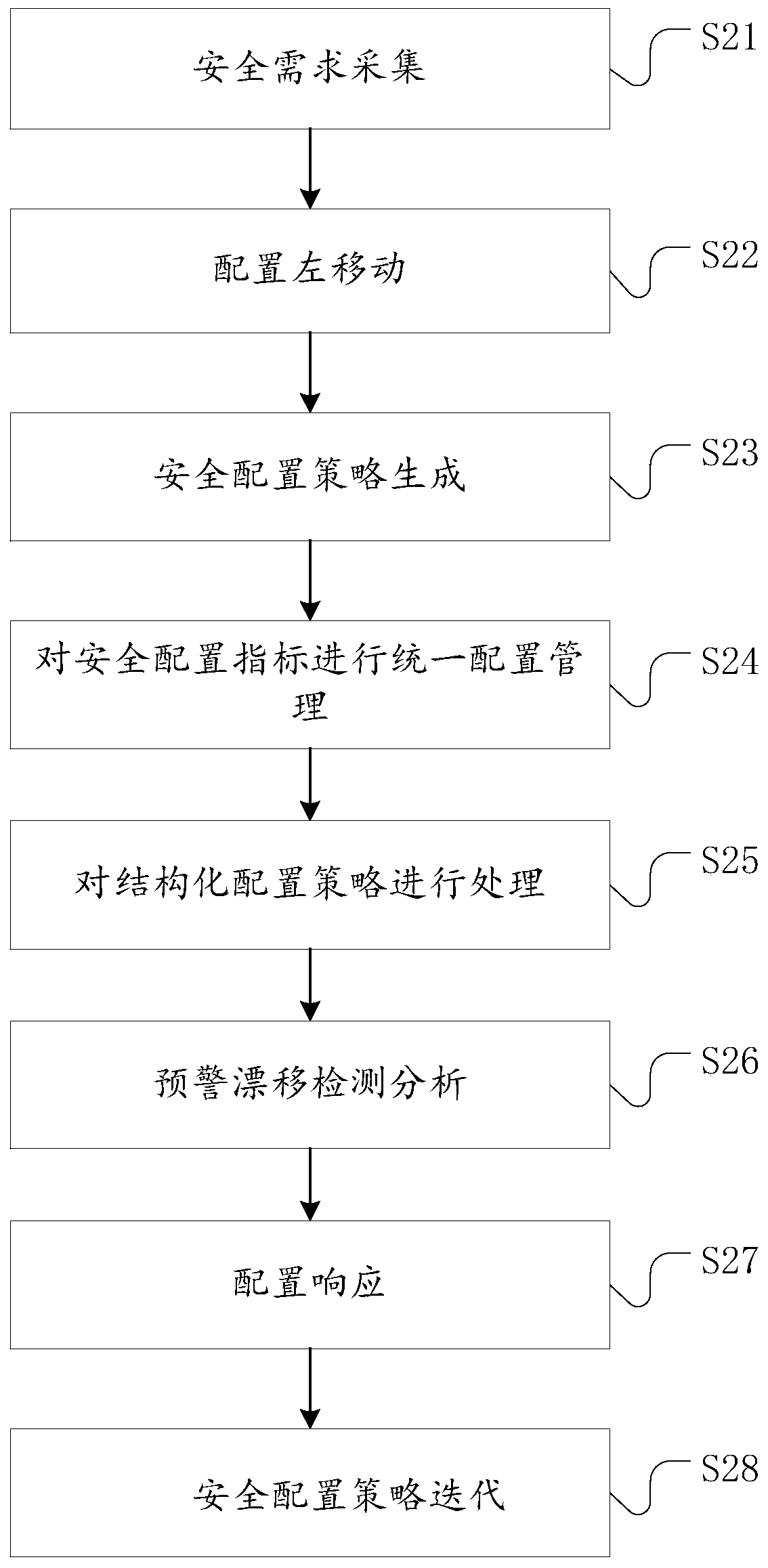
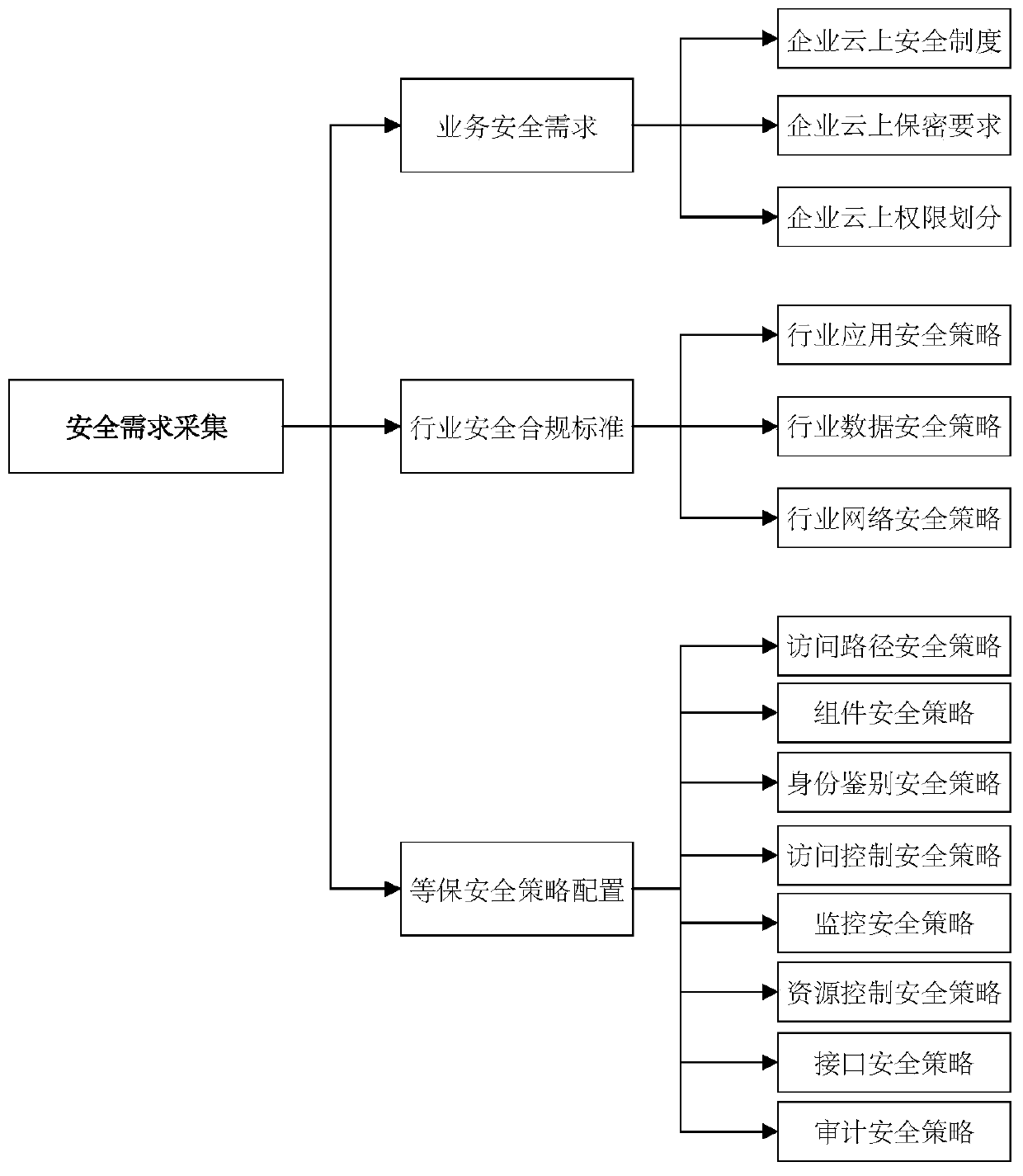
[0063] Unified management of the specified scenario-based, standardized, and index-based security configuration policies, and at the same time complete integration with CI / CD pipelines, that is, the right movement of security configuration policie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com