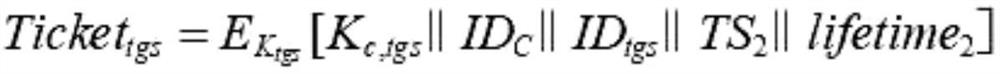A data security sharing system and method integrating kerberos authentication server and blockchain
An authentication server and data security technology, applied in data processing applications, digital data authentication, digital data protection, etc., can solve problems such as data leakage, difficulty in data fusion and association, damage to the interests of data owners, etc., to achieve high security, improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
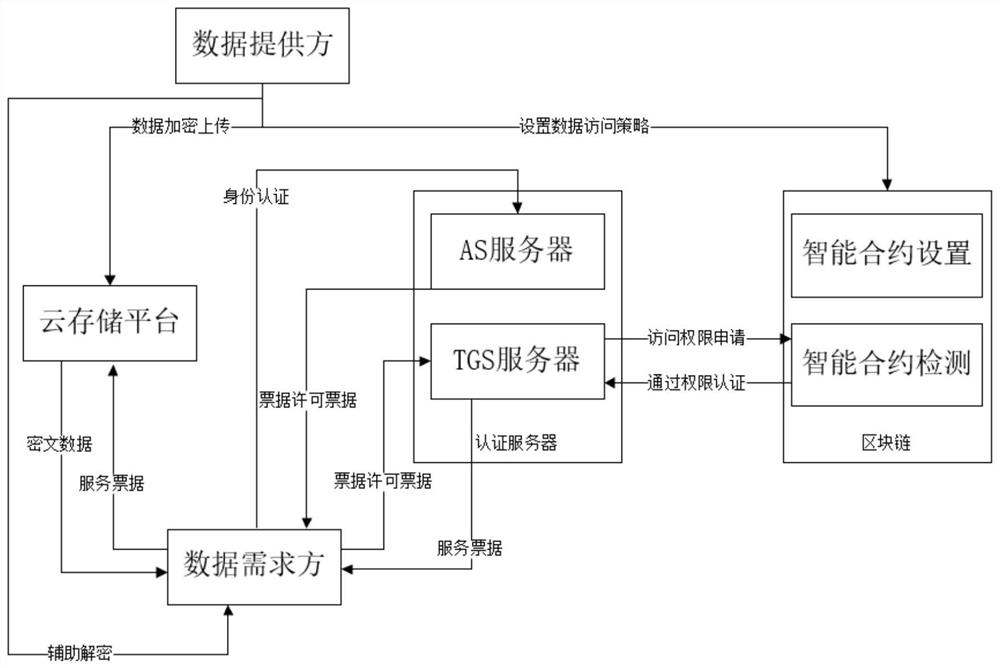
[0066] Such as figure 1 As shown, the present embodiment provides a data security sharing system that integrates a Kerberos authentication server and a block chain, including a data providing terminal, a data demand terminal, an AS server, a TGS server, a block chain, and a cloud storage platform;
[0067] The data supply terminal is respectively connected to the cloud storage platform and the blockchain, the data demand terminal is respectively connected to the cloud storage platform, the AS server, and the TGS server, and the TGS server is connected to the blockchain;
[0068] Among them, data transmission is performed between the data providing terminal and the cloud storage platform through the OpenSSL protocol, data transmission is performed between the data providing terminal and the blockchain through the OpenSSL protocol, and data is transmitted between the data demand terminal and the cloud storage platform through the OpenSSL protocol. Transmission, data transmission...
Embodiment 2
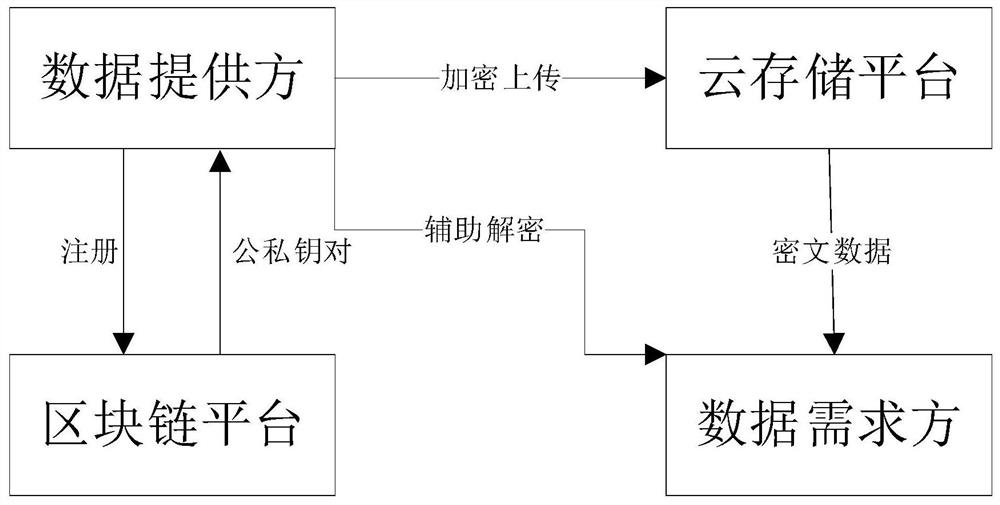
[0082] Such as figure 1 with figure 2 As shown, a data security sharing method of a data security sharing system that integrates a Kerberos authentication server and a block chain is based on the data security sharing system described in Embodiment 1, and its working method includes the following steps:
[0083] Step 1. Key generation and data encryption
[0084] After the data security sharing system described in Embodiment 1 is networked, the system first generates the shared key K of the AS server and the TGS server tgs , the shared key K between the TGS server and the cloud storage platform v ;
[0085] When the data provider terminal is registered in the system, the smart contract in the blockchain will generate a public-private key pair (PK, SK) according to the corresponding rules, and distribute it to the data provider terminal. The data provider terminal uses the P key pair distributed by the blockchain. K Encrypt the data to form ciphertext data and upload it to...
Embodiment 3
[0114] As described in Embodiment 2, a data security sharing method that integrates a Kerberos authentication server and a blockchain data security sharing system is different from Embodiment 2 in that:
[0115] Data provider terminals set or modify data access policies, and data demand terminals apply for data access permissions are automatically executed on the chain by smart contracts. After the data is uploaded to the chain, it cannot be tampered with, and any data access operation can be traced back.
[0116] In addition, during the endorsement process of each blockchain node, regulatory nodes such as government departments can be added to ensure the security and legality of data access authorization.
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap