Digital forensics method based on blockchain privacy protection and fine-grained access control
A privacy protection and access control technology, applied in the research field of cyberspace security, it can solve the problems of tampering with evidence, violating the digital chain of custody, harmful normative VDF procedures, etc., to achieve the effect of ensuring legality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
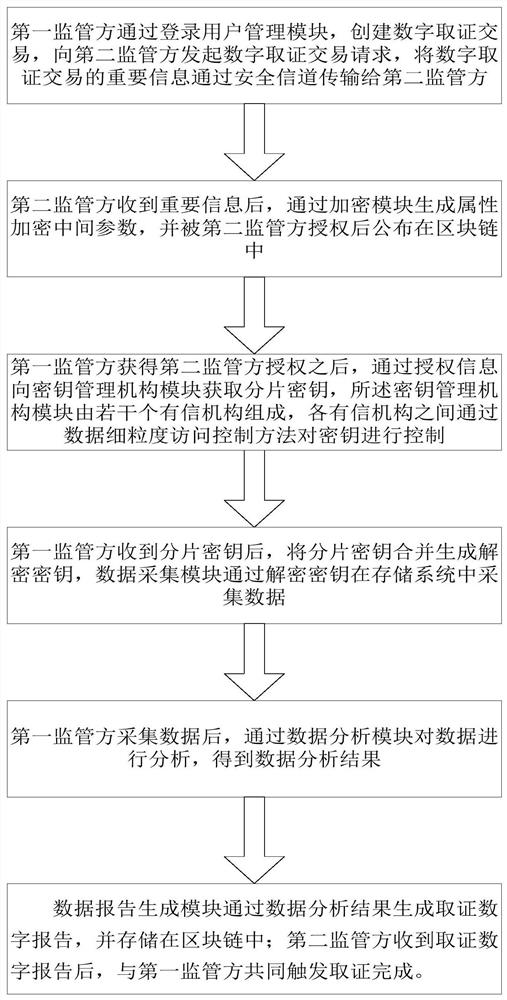
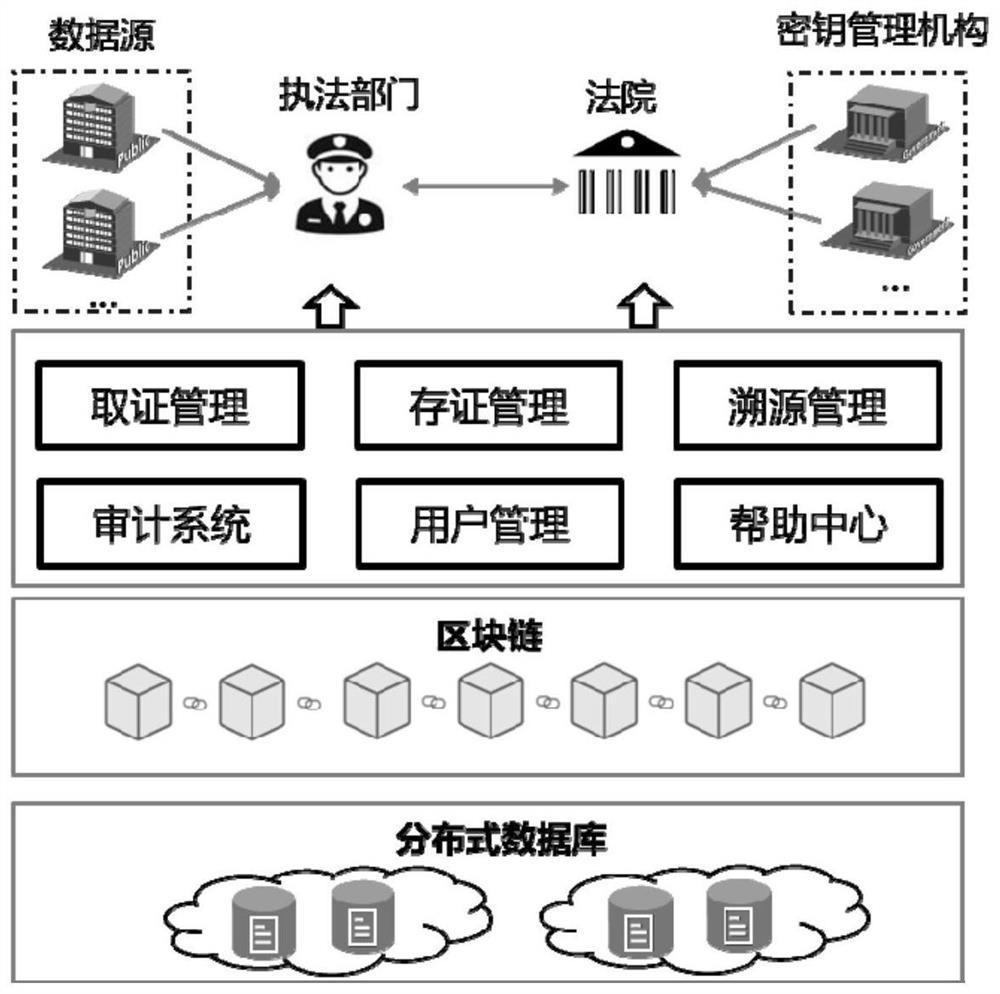
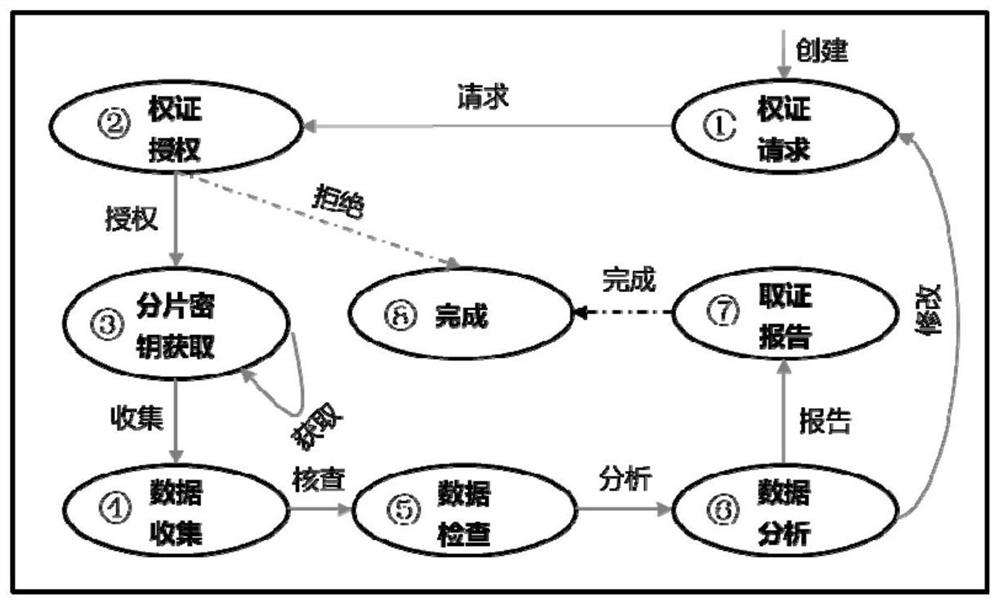
[0032] Digital forensics methods based on blockchain privacy protection and fine-grained access control, such as figure 1 As shown, through a digital forensics system based on blockchain privacy protection and fine-grained access control, the alliance blockchain composed of law enforcement agencies, courts, alliance key management agencies, data sources (enterprises or individuals), etc., The system as figure 2 As shown, it includes the business layer, application layer, blockchain layer and distributed data storage layer connected in sequence. The business layer is web-oriented digital forensics management, supports login operations of users with different roles, and realizes convenient user interaction functions; the application layer supports functional components such as evidence collection, evidence storage, and traceability. The data interface layer based on Web3j realizes the conversion logic between user input and smart contracts; the blockchain layer is an alliance ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com