A medical image sharing method based on chaotic encryption
A medical image and chaotic encryption technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of secret image damage, loss of hospitals and patients, and high fidelity requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
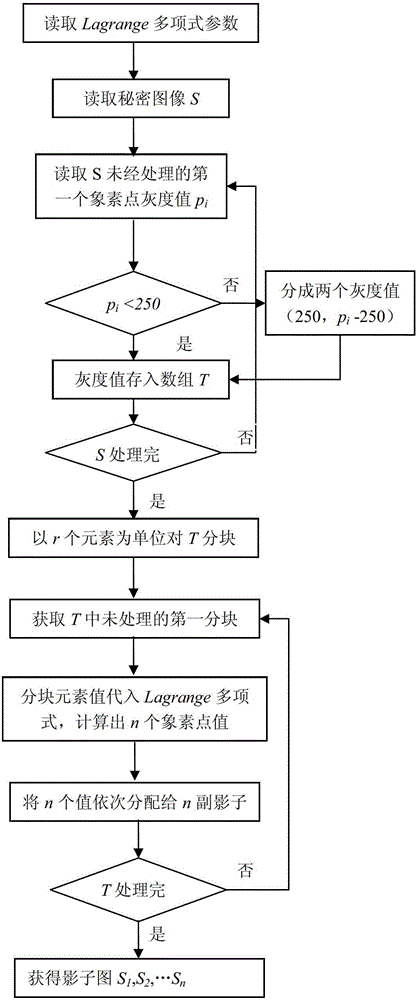
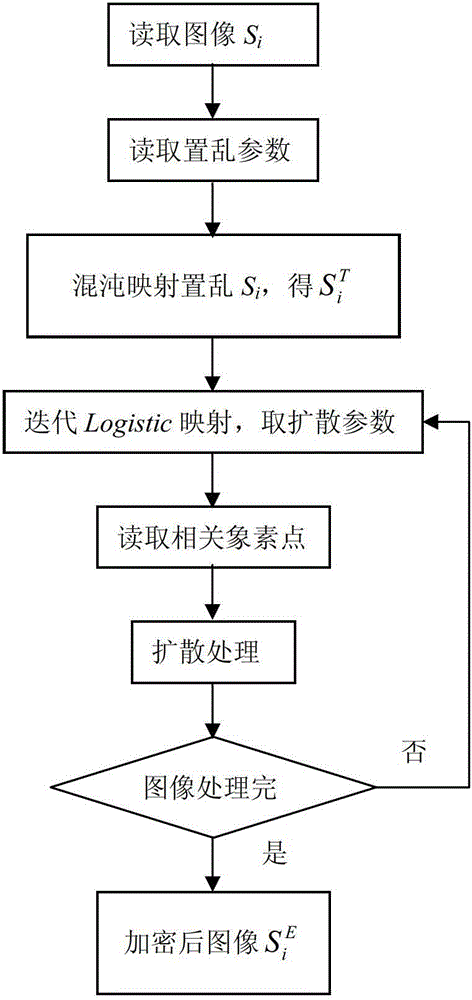
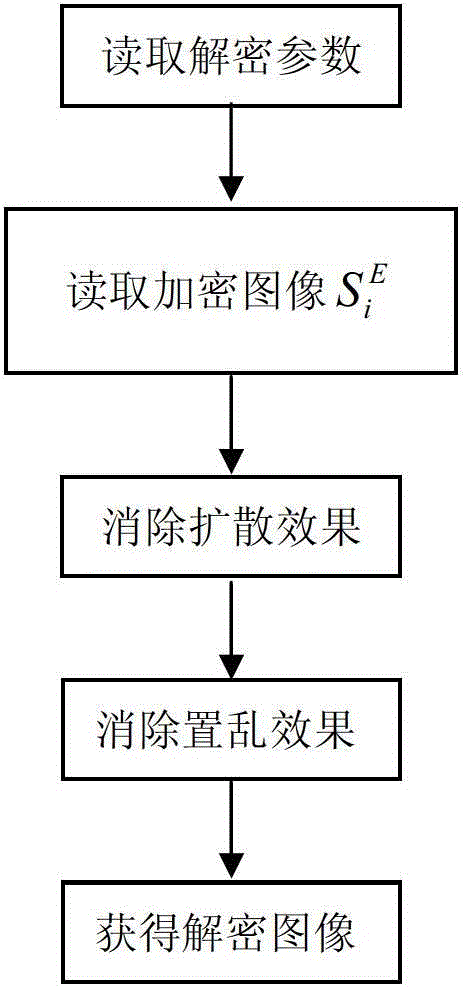
[0118] Such as Figure 1-5 Although the present invention is described in terms of specific embodiments, the principles of the present invention, as defined in the appended claims, can obviously be applied beyond the scope of the embodiments specifically described herein. Moreover, some details are omitted here in order not to obscure the inventive aspects of the present invention. Specific details not described in this application are within the knowledge of any person of ordinary skill in the art.
[0119] The drawings of the present application and the detailed description attached thereto are only used to illustrate exemplary embodiments of the present invention. To maintain conciseness, other embodiments of the present invention using the principles of the present invention are not specifically described in this application, and are not specifically illustrated by the accompanying drawings. "Example" only means "used as an example, instance, or illustration" herein.
[0120...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com