Adjustable encrypted duplicated data deleting method
A deduplication and adjustable technology, applied in the field of information security, to achieve the effect of reducing memory usage, balancing anti-frequency analysis capabilities, and balancing storage efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
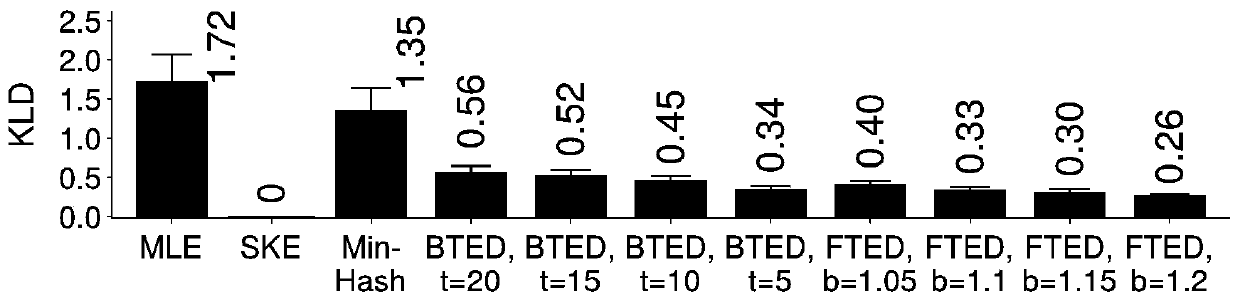
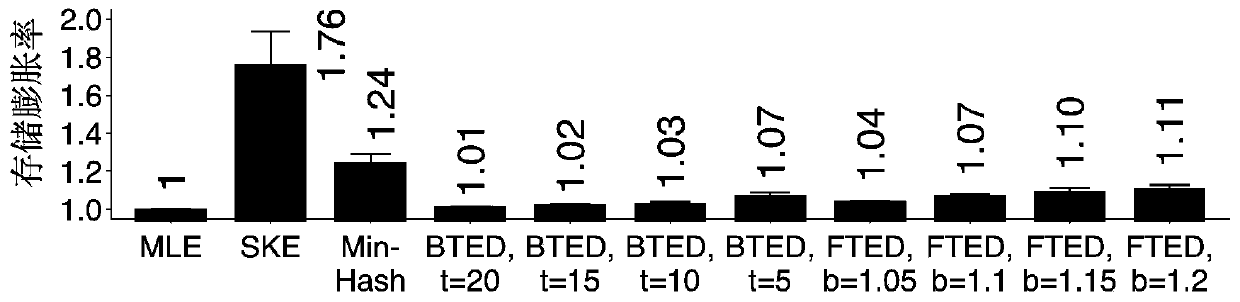
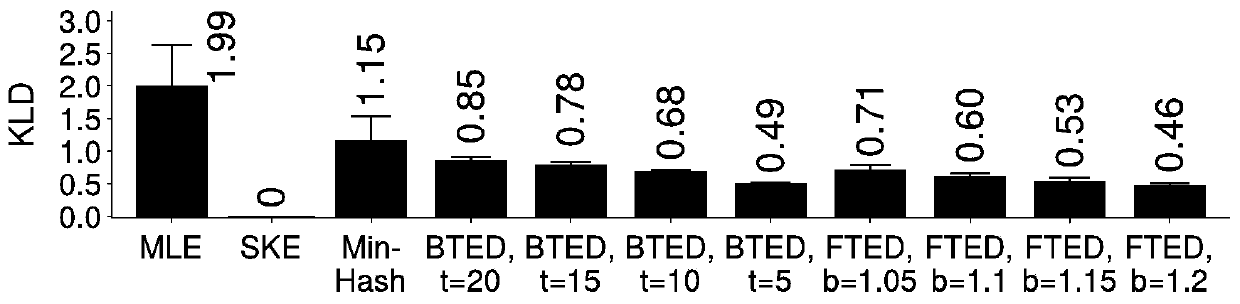
[0087] This embodiment compares and analyzes the tunable encrypted deduplication (TED for short) implemented based on the method of the present invention and the existing encryption method. Specifically, the following schemes are considered in the comparative analysis: ①MLE, using the hash value of each plaintext block as the key; ②SKE, selecting a random key for each plaintext block; ③MinHash Encryption (minimum hash encryption), the data segment The minimum hash value of all plaintext blocks is used as the key of all plaintext blocks in this data segment; ④ BTED (basic TED), does not apply automatic parameter setting adjustable encrypted deduplication; ⑤ FTED (full TED), complete application of three items Scalable encrypted deduplication of key technologies.
[0088] This embodiment will verify the effectiveness of the method TED of the present invention based on two real data sets FSL and MS.
[0089] The FSL dataset (http: / / tracer.filesystems.org / ) is a daily backup of 3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com