Anomaly detection using cognitive computing
An abnormal, computer technology used in the field of computer security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
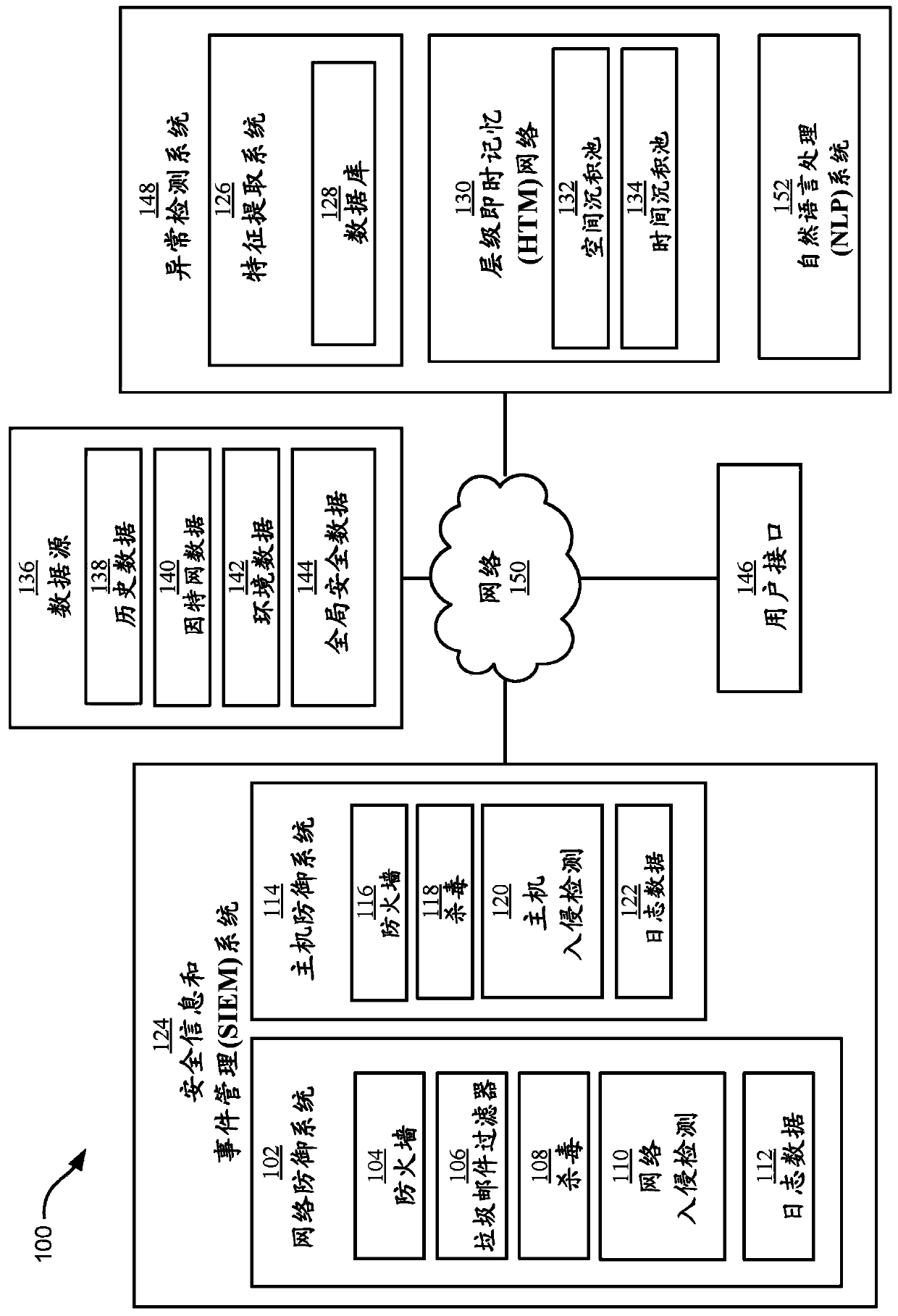
[0026] Aspects of this disclosure relate to computer security, and more particularly to anomaly detection systems. While the disclosure is not necessarily limited to such applications, various aspects of the disclosure can be appreciated by discussing various examples using this context.
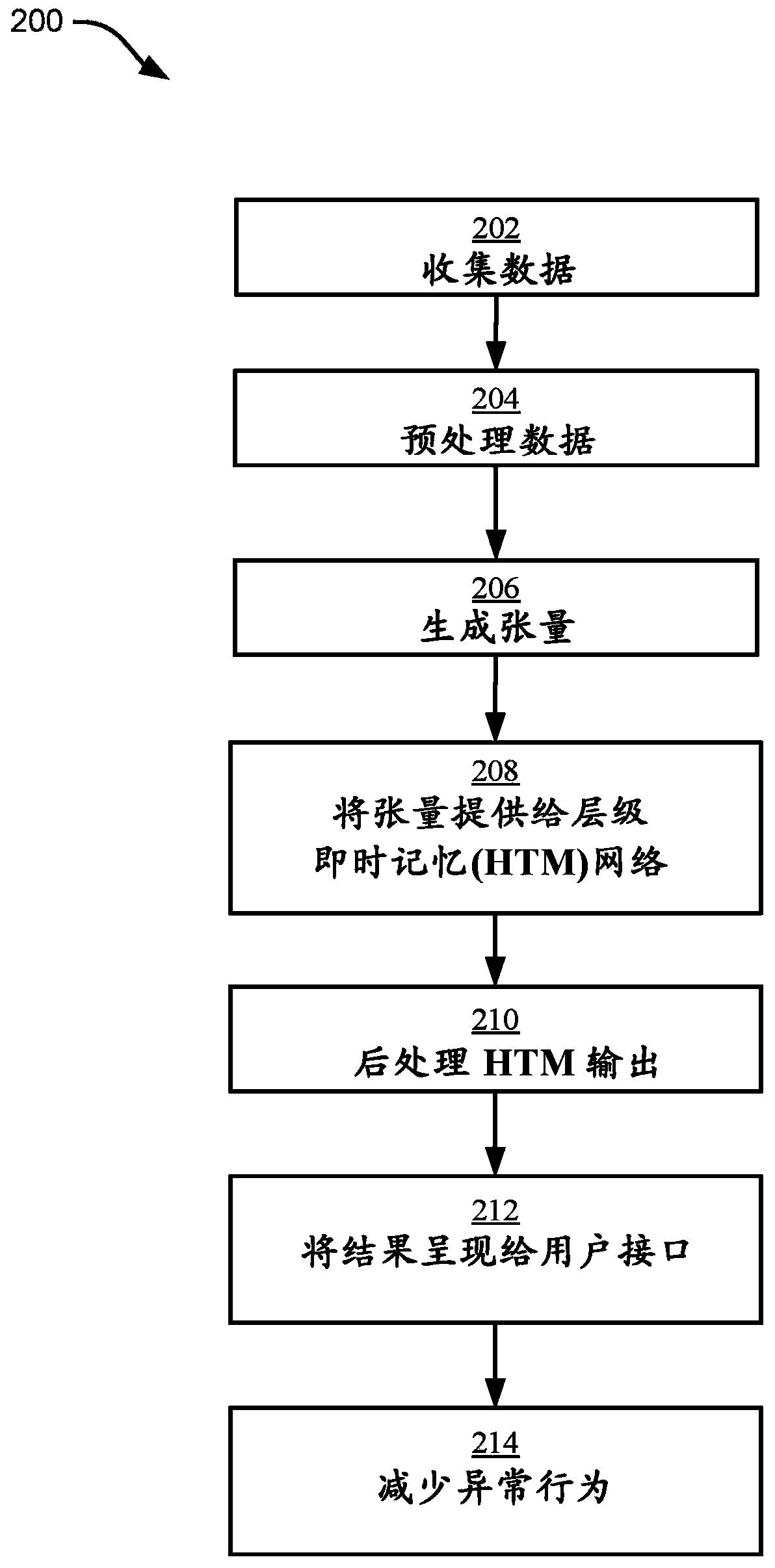
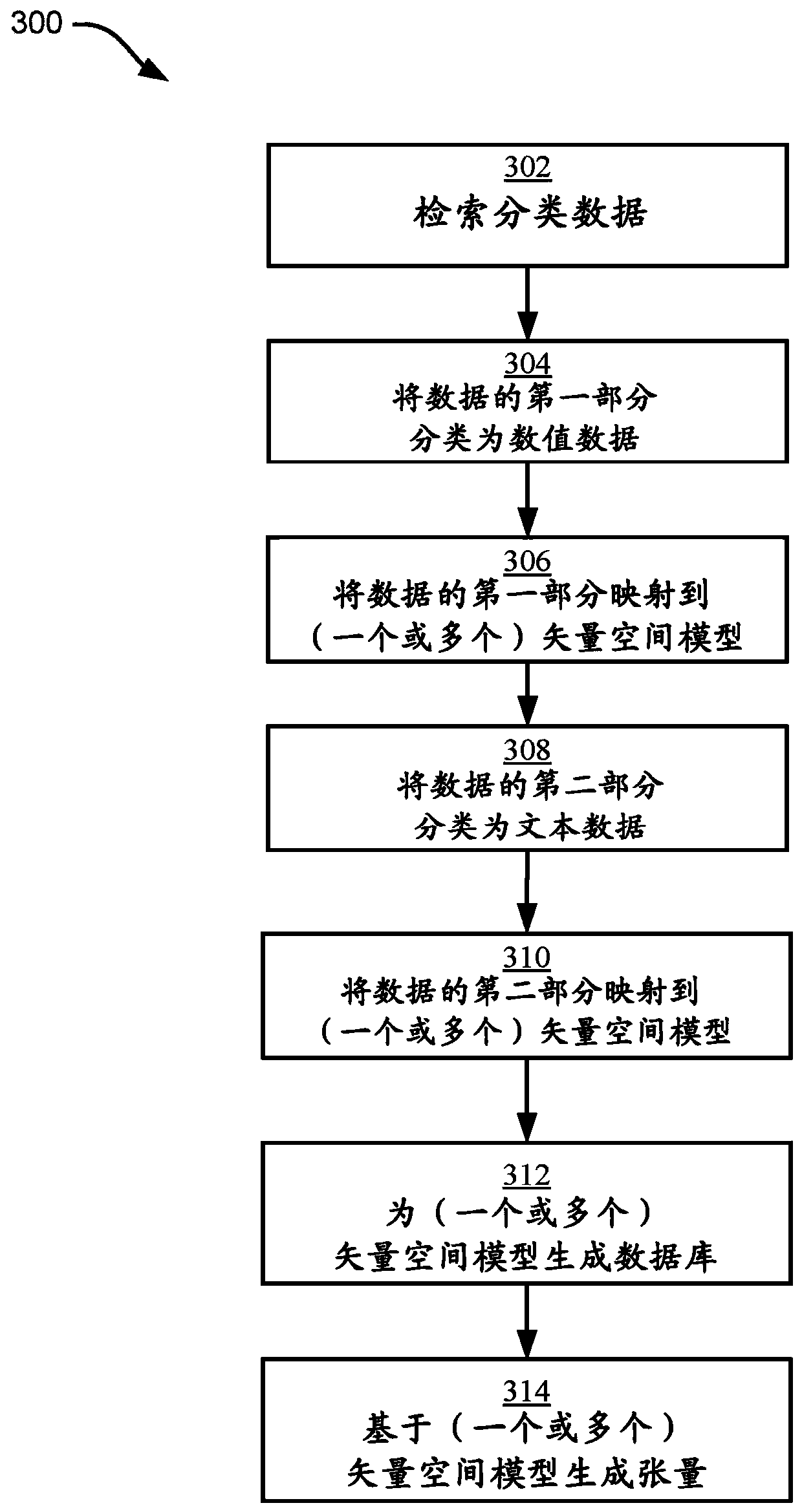
[0027] Aspects of the present disclosure relate to compiling heterogeneous network security data (e.g., log data, network data, computer data, application data, user behavior data, hardware data, etc.), converting heterogeneous network security data into isomorphic data, store structured data in arrays, input the arrays to a Hierarchical Just-in-Time Memory (HTM) network, analyze the output of the HTM network, and communicate relevant cybersecurity information to users (e.g., using question-and-answer (Q&A) systems, reports, infographics, charts , messages, alerts, anomaly scores, probabilities, etc.).
[0028] Aspects of the present disclosure exhibit many advantages. As a first example a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com