Domain name collection method and system, terminal and computer readable storage medium
A collection method and collection system technology, applied in the transmission system, digital transmission system, user identity/authority verification, etc., can solve the problem that the domain name cannot be detected
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
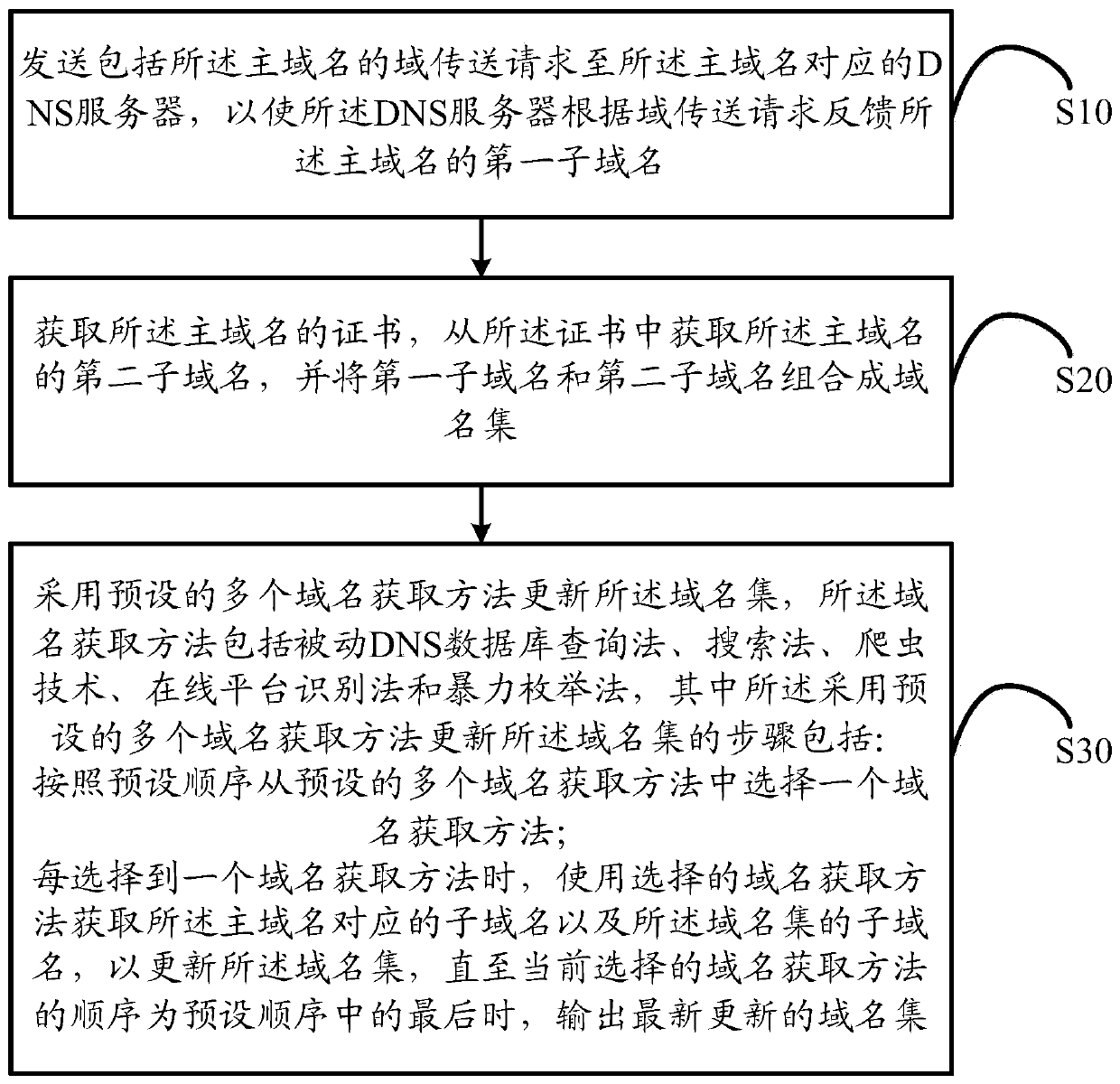
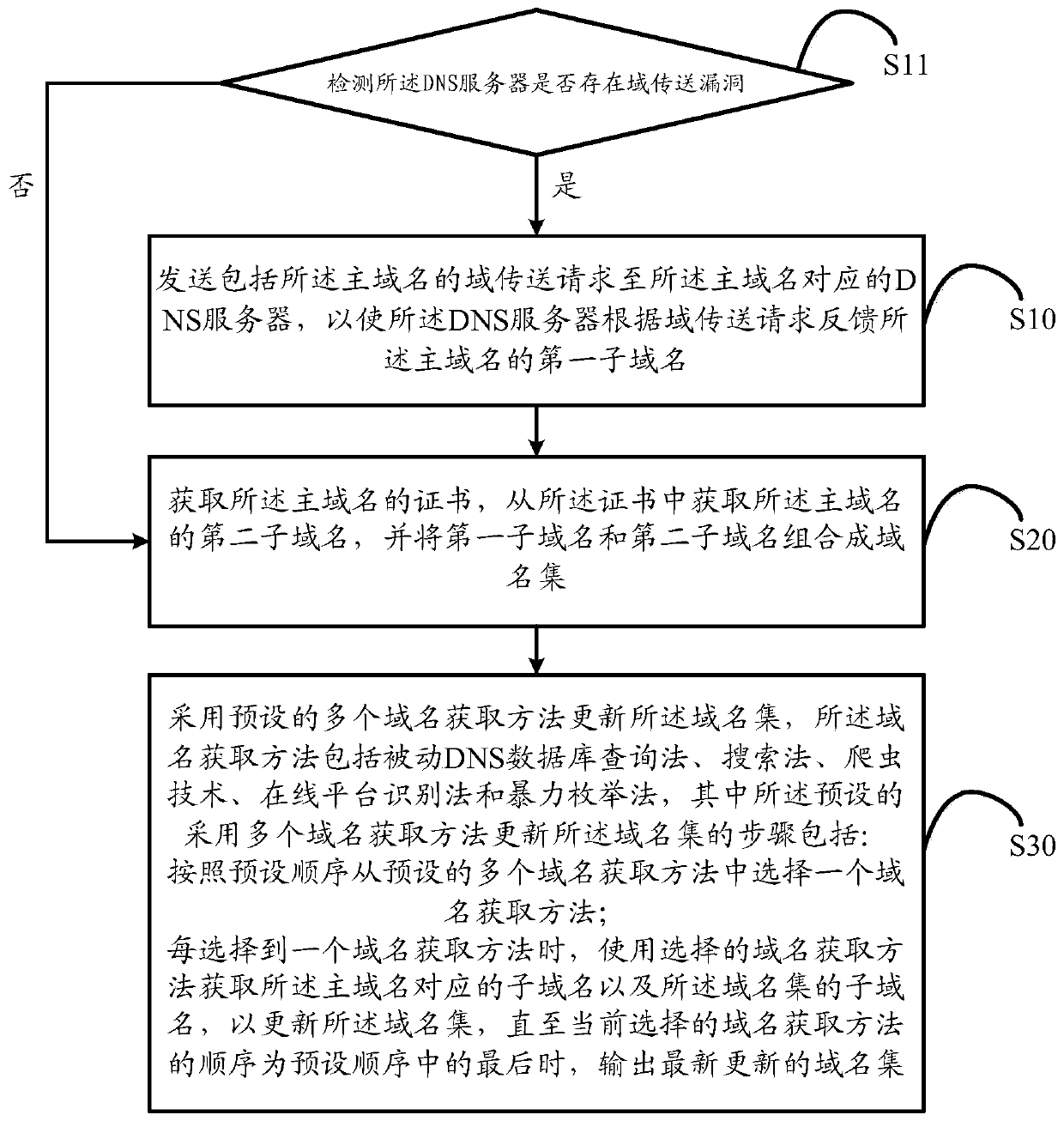
[0084] Further, please refer to image 3 , image 3 It is a schematic flowchart of the second embodiment of the domain name acquisition method of the present invention, based on the first embodiment, before step S10 includes:
[0085] Step S11 , detecting whether there is a domain transfer vulnerability in the DNS server; if yes, execute step S10; if not, execute step S20.
[0086] Before initiating a domain transfer request to the DNS server corresponding to the primary domain name, detect whether the DNS server has a domain transfer vulnerability. In this example, to detect whether the DNS server has a domain transfer vulnerability, you can use the existing Vulnerability mining and analysis methods for data, such as constructing some detection strings, generally called payloads, using these constructed data to package and send to the server, when the server returns the data and judges that it meets certain rules , a loophole is considered to exist. If there is a domain tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com