Gate passing authentication method and system and computer storage medium
An authentication method and gate technology, applied in wireless communication, sustainable communication technology, advanced technology, etc., can solve problems such as difficult to pass quickly, long time required, and no set of gate systems based on location information, etc., to reduce time , Improve efficiency, and optimize certification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
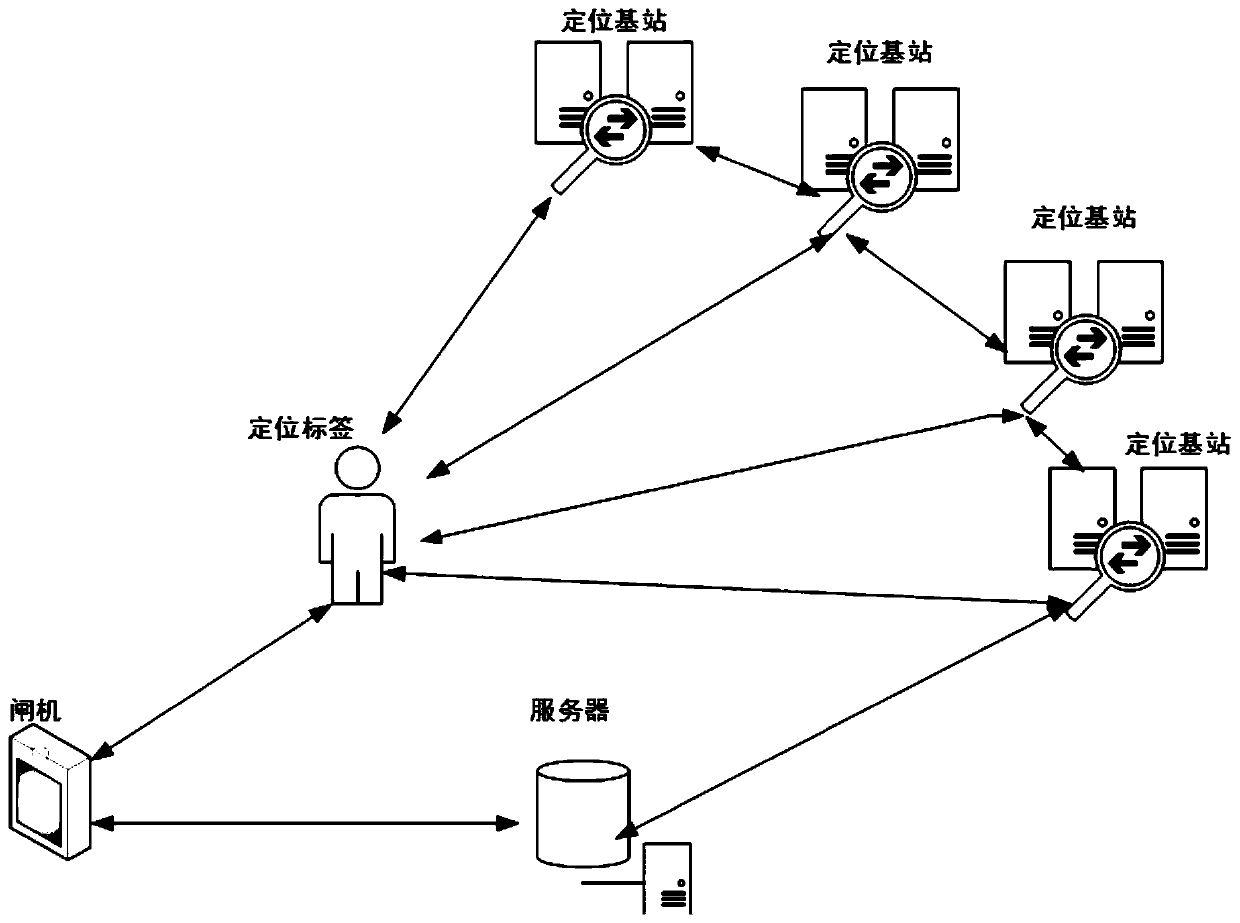
[0063] see figure 1 , figure 1 It is a structural schematic diagram of a gate pass authentication system disclosed in the embodiment of this application. Such as figure 1 As shown, the gate pass authentication system includes a positioning base station, a gate, a positioning label, and a server, wherein the positioning label communicates with the gate and the positioning base station, and the positioning base station is used to locate the positioning label and send the positioning information to the server. The positioning tag is used to verify the verification information sent by the gate. On the other hand, the server communicates with the positioning base station and the gate. The server is used to generate a security authentication start command based on the positioning information. The security certification start command carries positioning information and verification information.
[0064] Exemplarily, the gate pass authentication system includes 4 positioning base st...
Embodiment 2
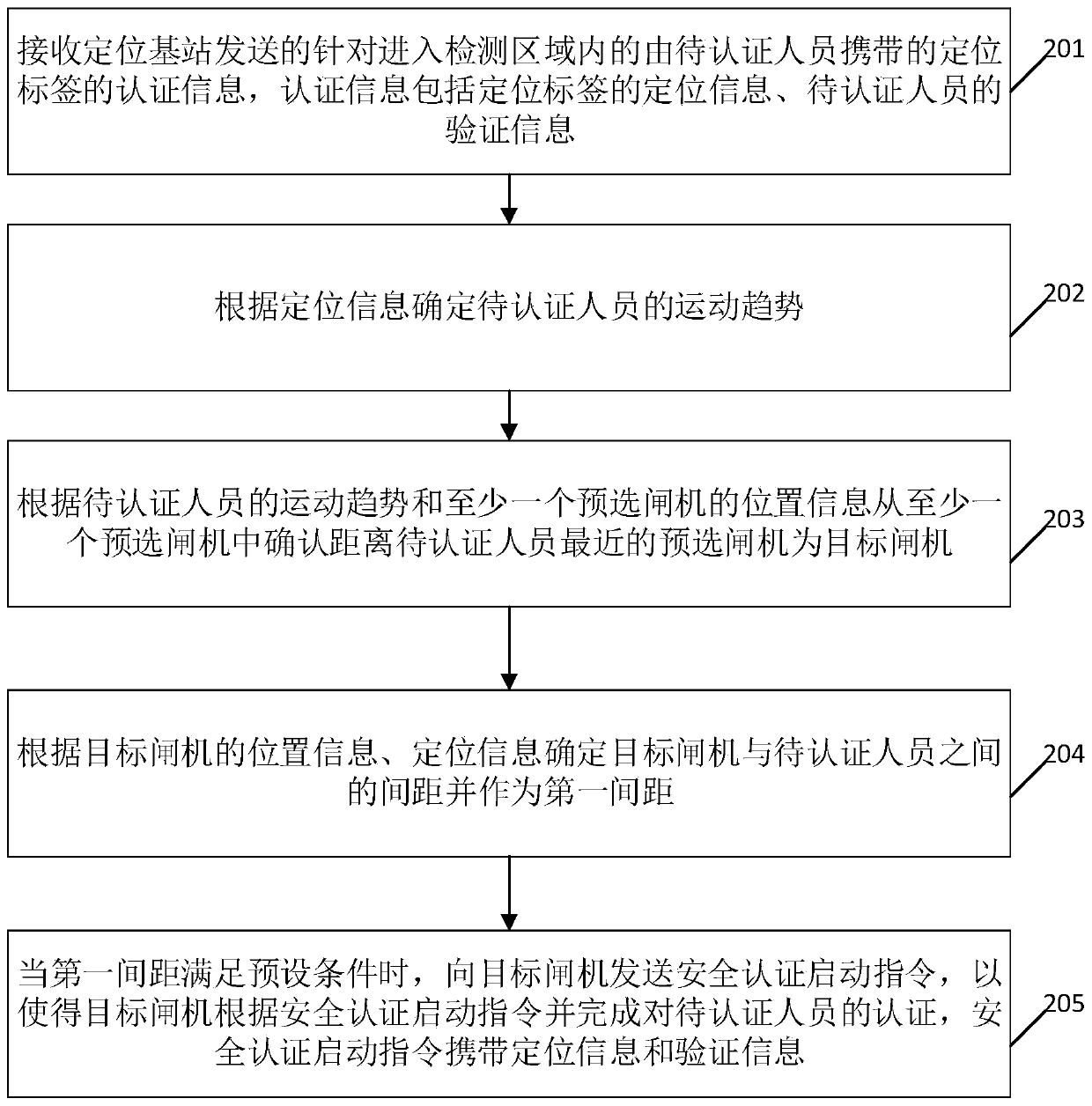
[0087] see figure 2 , figure 2 It is a schematic flowchart of a gate pass authentication method disclosed in the embodiment of the present application, and the gate pass authentication method is applied to a server. Such as figure 2 As shown, the gate pass authentication method includes steps:
[0088] 201. Receive the authentication information sent by the positioning base station for the positioning tag carried by the person to be authenticated entering the detection area. The authentication information includes the positioning information of the positioning tag and the verification information of the person to be authenticated;
[0089] 202. Determine the movement trend of the person to be authenticated according to the positioning information;
[0090] 203. Confirm that the preselected gate closest to the person to be authenticated is the target gate from at least one preselected gate according to the movement trend of the person to be authenticated and the position ...
Embodiment 3
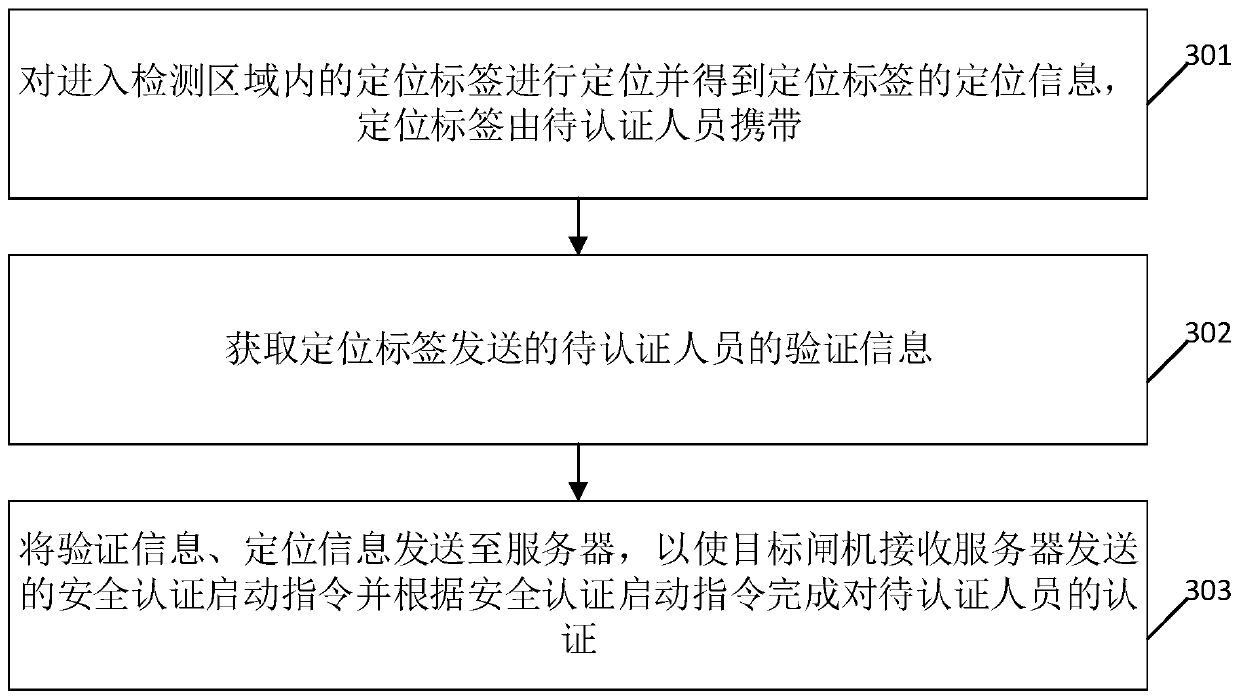
[0101] see image 3 , image 3 It is a schematic flowchart of a gate pass authentication method disclosed in an embodiment of the present application, and the gate pass authentication method is applied to a positioning base station. Such as image 3 As shown, the gate pass authentication method includes steps:
[0102] 301. Locate the positioning tag entering the detection area and obtain the positioning information of the positioning tag, and the positioning tag is carried by the person to be authenticated;
[0103] 302. Obtain the verification information of the person to be certified sent by the location tag;
[0104] 303. Send the verification information and location information to the server, so that the target gate receives the security authentication start instruction sent by the server and completes the authentication of the person to be authenticated according to the security authentication start instruction.
[0105] The positioning base station of the embodimen...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap