Java annotation-based dynamic configuration data desensitization method
A technology of data desensitization and dynamic configuration, applied in the field of data desensitization, it can solve the problems of sensitive data exposure, dynamic configuration data desensitization, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
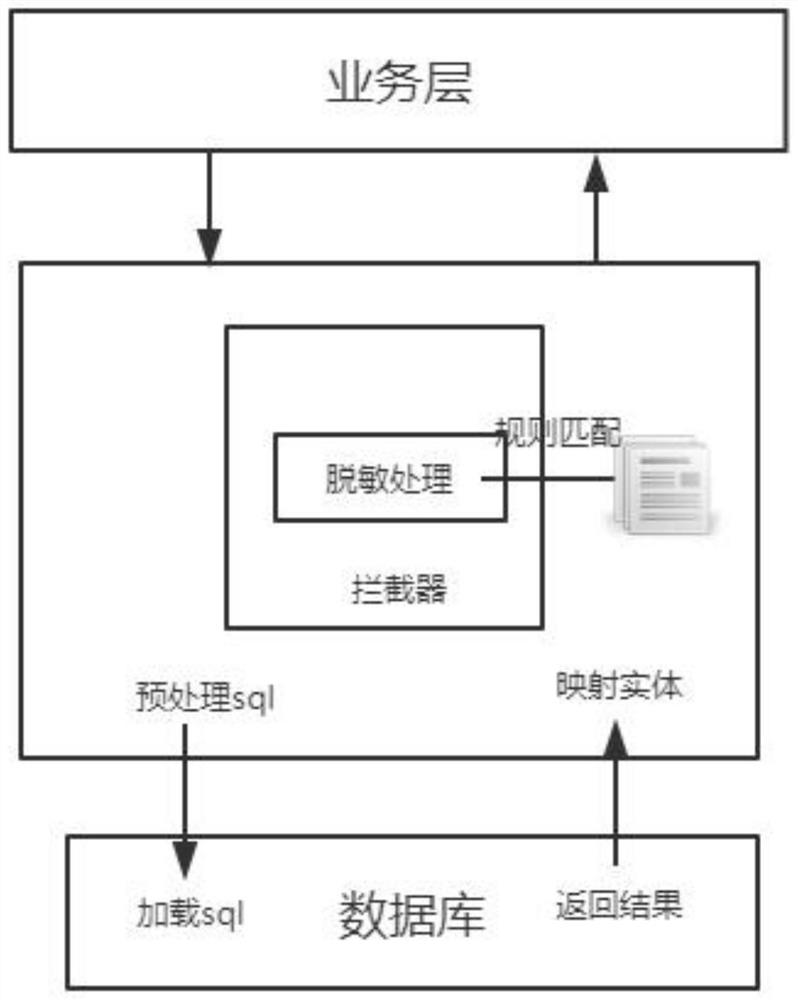
[0015] see figure 1 , a method for desensitizing dynamic configuration data based on java annotations, the steps are as follows:
[0016] Step 1: Configure the java basic environment and import the open source framework;
[0017] Specifically, install jdk to ensure the basic environment for java code to run. jdk is a software development kit for java language, which includes JVM standards and java core class libraries. In order to provide basic class libraries, import spring and other open source frameworks to provide faster For code development, configure environment variables to provide the underlying operating environment.
[0018] Step 2: Write a custom annotation to identify the desensitized data and the data that carries the data desensitization annotation in the information returned by the interceptor interception request;
[0019] Specifically, the interceptor implements interception through the HandlerInterceptorAdapter provided by spring. The process of business co...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap