Secret key generation method, signature method, signature verification method, signature verification device, equipment and medium
A technology of key generation and key parameters, which is applied to secure communication devices and key distribution, can solve problems such as reducing key security, and achieve the effect of improving security and privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Exemplary embodiments of the present application are described below in conjunction with the accompanying drawings, which include various details of the embodiments of the present application to facilitate understanding, and they should be regarded as exemplary only. Accordingly, those of ordinary skill in the art will recognize that various changes and modifications of the embodiments described herein can be made without departing from the scope and spirit of the application. Also, descriptions of well-known functions and constructions are omitted in the following description for clarity and conciseness.
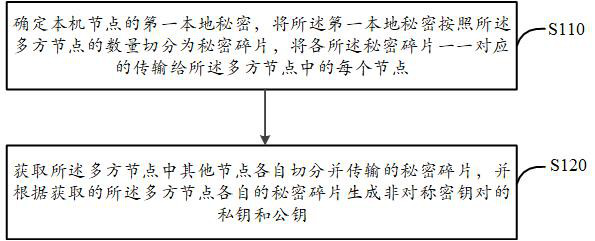
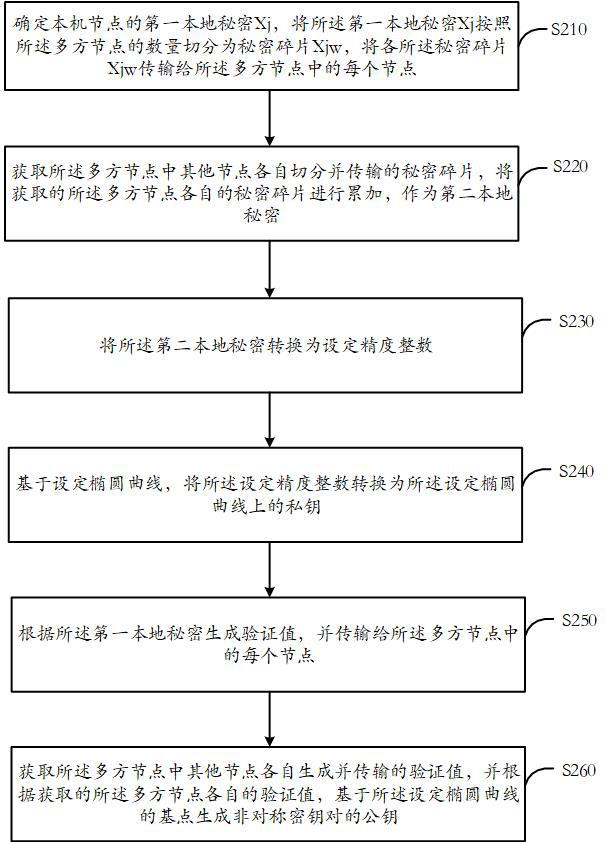
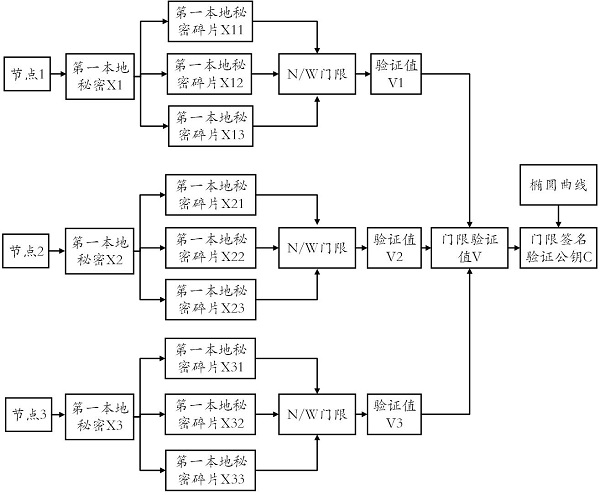
[0046] figure 1 is a schematic flowchart of a method for generating a key according to an embodiment of the present application. This embodiment is applicable to key generation in threshold signature, thereby improving the security and privacy of key generation. The key generation method disclosed in this embodiment can be executed by a key generation device, which...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap