Distributed authentication method and system in restricted environment
An authentication method and an authentication system technology, which are applied in the field of distributed authentication methods and systems in a restricted environment to achieve the effects of enhancing mutual trust, improving offline autonomy, and improving access security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059]
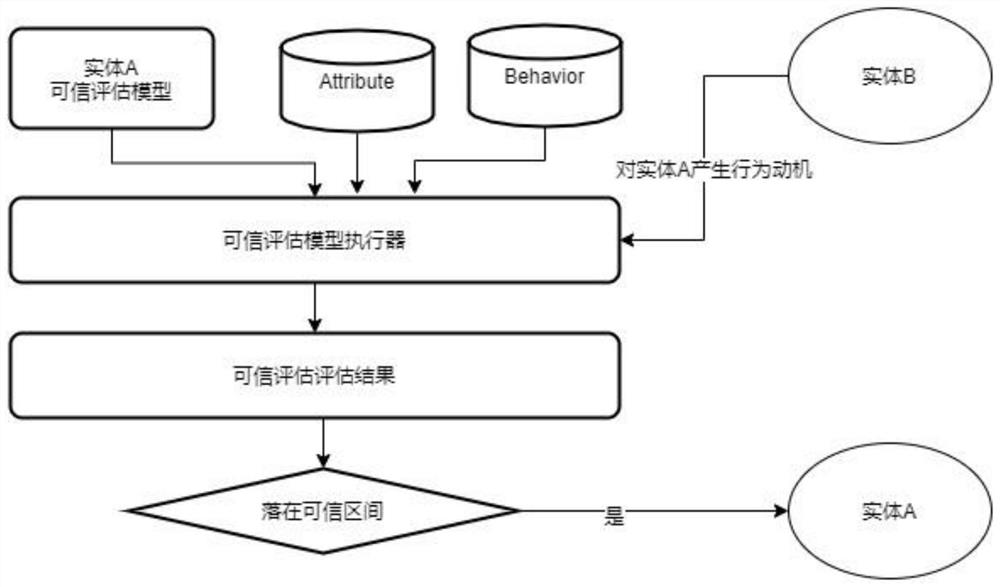
[0060] Wherein, α and β represent weights, α+β=1, according to the statistics and analysis of operation and maintenance data, α adopts 0.45, and β adopts 0.55;
[0061] f
[0062] f
[0063] Among them, i represents the weight of high-risk vulnerabilities, a represents the number of high-risk vulnerabilities, j represents the weight of medium-risk vulnerabilities, and b represents
[0064] f
[0065] f
[0066] Among them, m represents the number of attack behaviors, and n represents the number of attack behaviors.
Embodiment 2
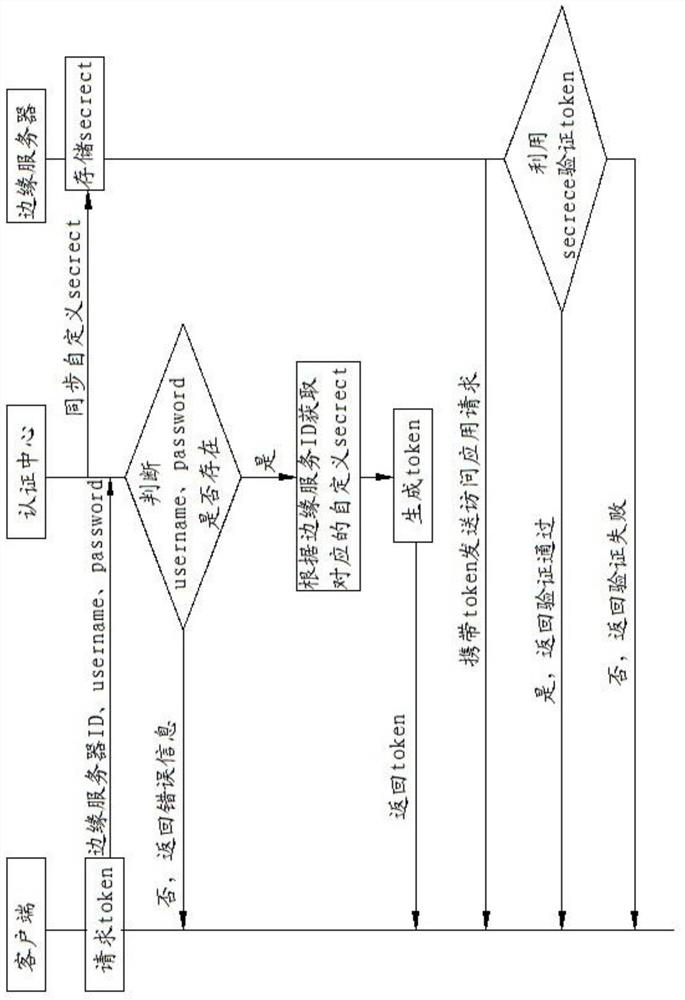
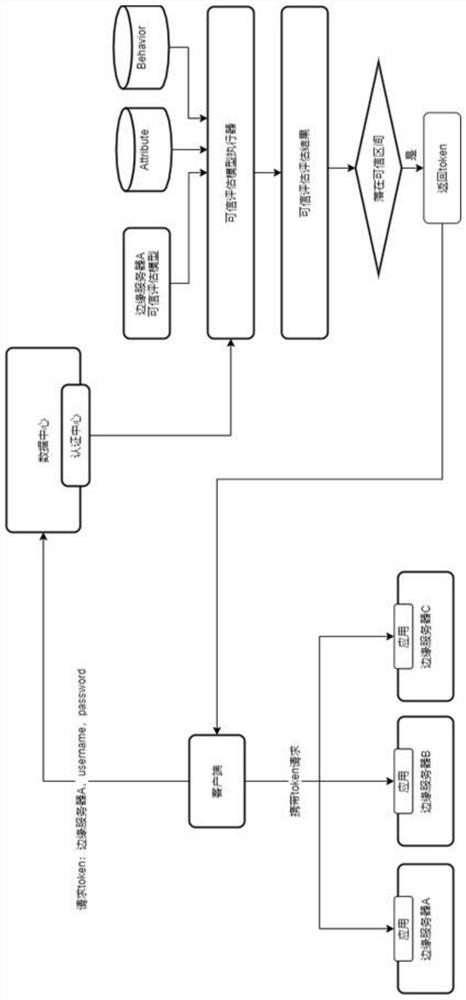
[0073] The client is used to initiate a token request, and the token request includes an edge server ID, a system user name and a password.
[0075] There are multiple edge servers, each edge server is connected to the client, and the edge server receives the application access.
[0078]
[0080] f
[0081] f
[0082] Among them, i represents the weight of high-risk vulnerabilities, a represents the number of high-risk vulnerabilities, j represents the weight of medium-risk vulnerabilities, and b represents
[0083] f
[0084] f
[0085] Among them, m represents the number of attack behaviors, and n represents the number of attack behaviors.
[0087] In this embodiment, the authentication server generates a JWT token through a custom secret.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com