Network Security Risk Assessment System
A risk assessment system and risk assessment technology, applied in transmission systems, data exchange networks, digital transmission systems, etc., can solve the problems of lack of self-learning, lack of self-learning of risk assessment models, and ignoring effects, so as to maintain accuracy and achieve The effect of adaptability and self-learning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
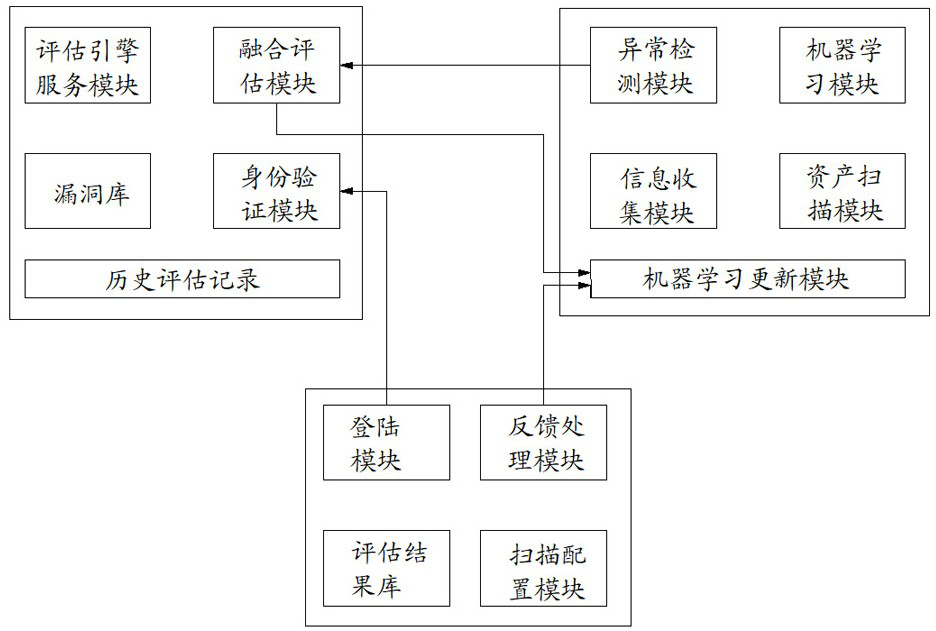
[0056] Such as figure 1 As shown, a network security risk assessment system includes a server and a client using a C / S architecture, and an agent installed on the assessment target system.
[0057] In this embodiment, the server side includes a vulnerability assessment engine service module, a vulnerability database, historical assessment records, an identity verification module, and a fusion assessment module.
[0058] 1. The server side includes the evaluation engine service module, which listens to accept the client’s request. According to the parameters contained in the request: the detected target system address, network configuration, and client permissions, etc., the agent sends a start scanning command to execute the scanning task, and according to Based on the results returned by the agent, start the assessment module to assess the risk of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com