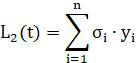Database security risk assessment system
A technology of risk assessment and security risk, which is applied in the field of database security risk assessment system, can solve the problems of one-sidedness of assessment results, lack of self-learning, self-adaptive ability, difficult database system unknown security risk assessment, etc., and achieve the effect of maintaining accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
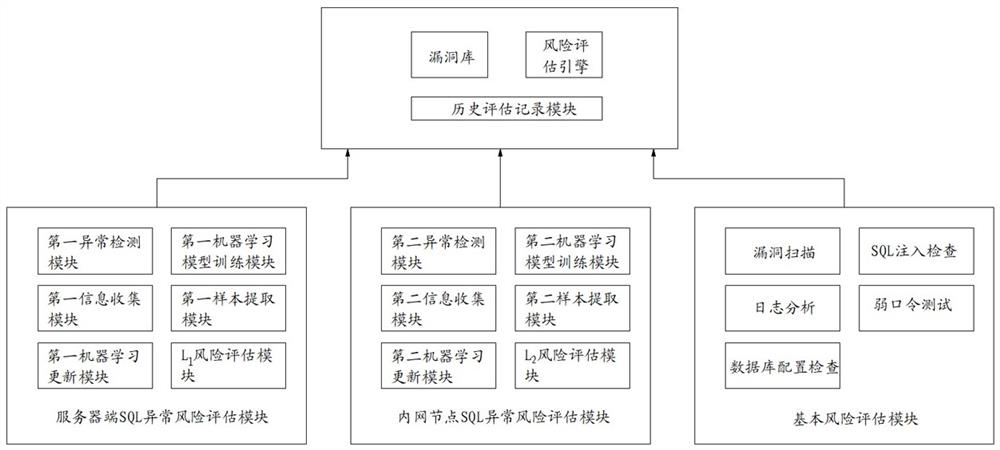
[0053] Such as figure 1 As shown, a database security risk assessment system includes:
[0054] The risk assessment engine dispatches the server-side SQL exception risk assessment module, the intranet node SQL exception risk assessment module, and the basic risk assessment module to perform the first round of "server-side SQL exception risk assessment ", the second round of "intranet node SQL exception risk assessment ", the last round of "basic risk assessment ";
[0055] The server-side SQL abnormality risk assessment module detects the abnormality of the SQL commands executed by the database server stored in the log records during the current round of detection cycle, and completes the server-side SQL abnormality risk assessment ;
[0056] Intranet node SQL abnormality risk assessment module, which detects abnormalities in the SQL operation behavior of the client database collected during the current round of detection cycle, and completes the intranet node SQL abno...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com