An active security defense system based on centralized management and control
A security defense, centralized control technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below is a further detailed description of the present invention according to the accompanying drawings and examples:
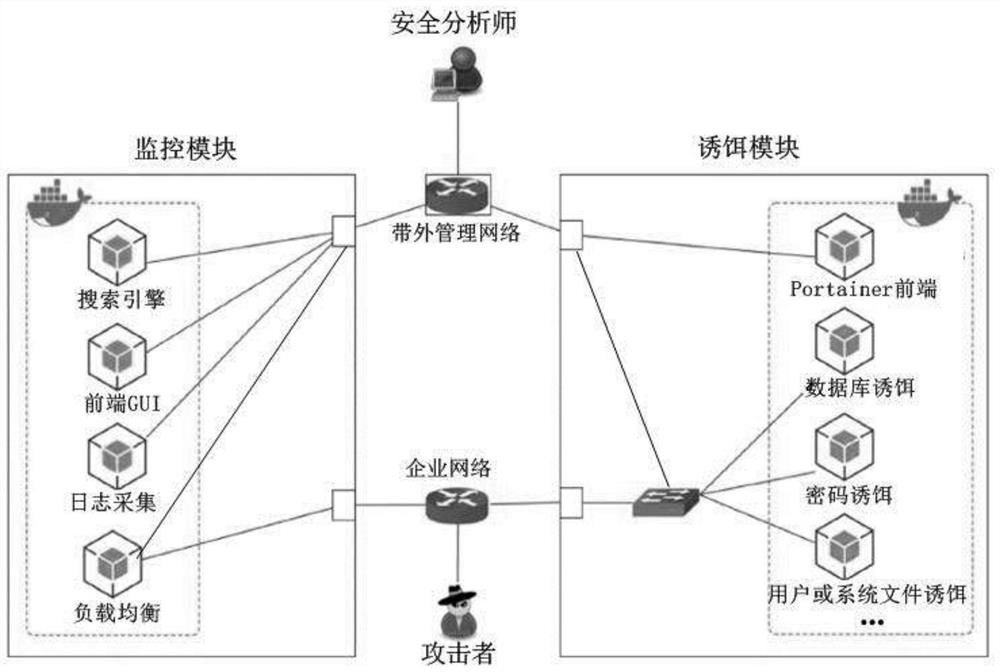
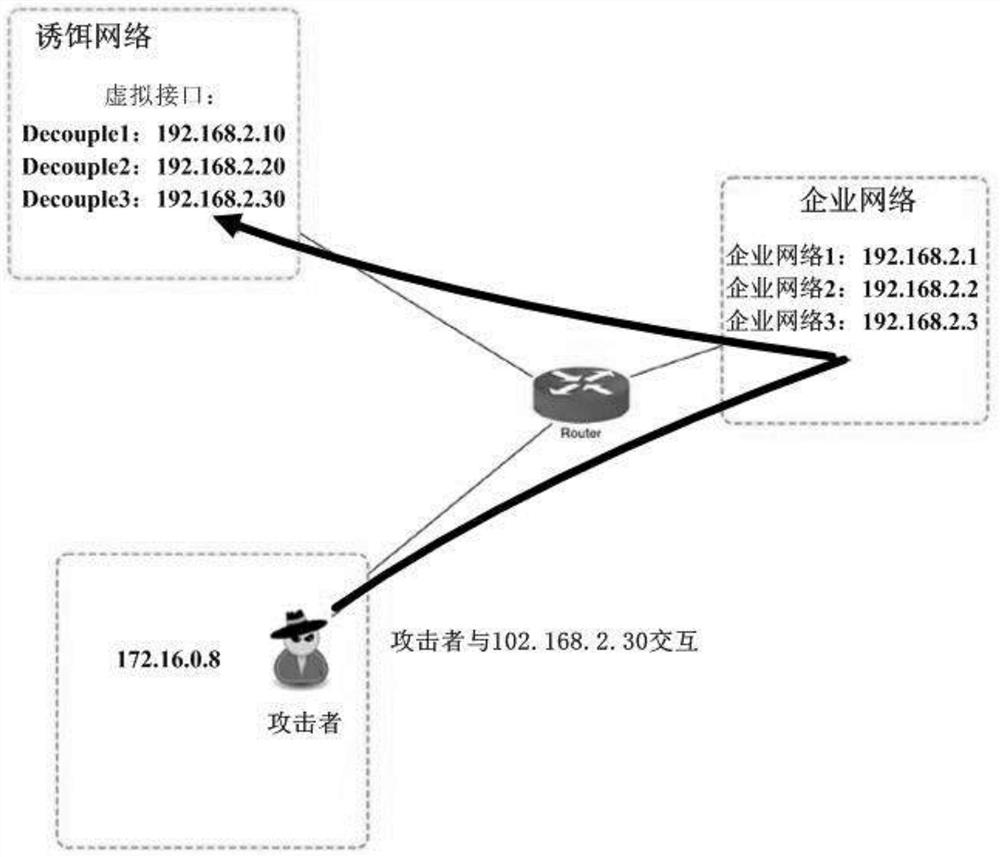
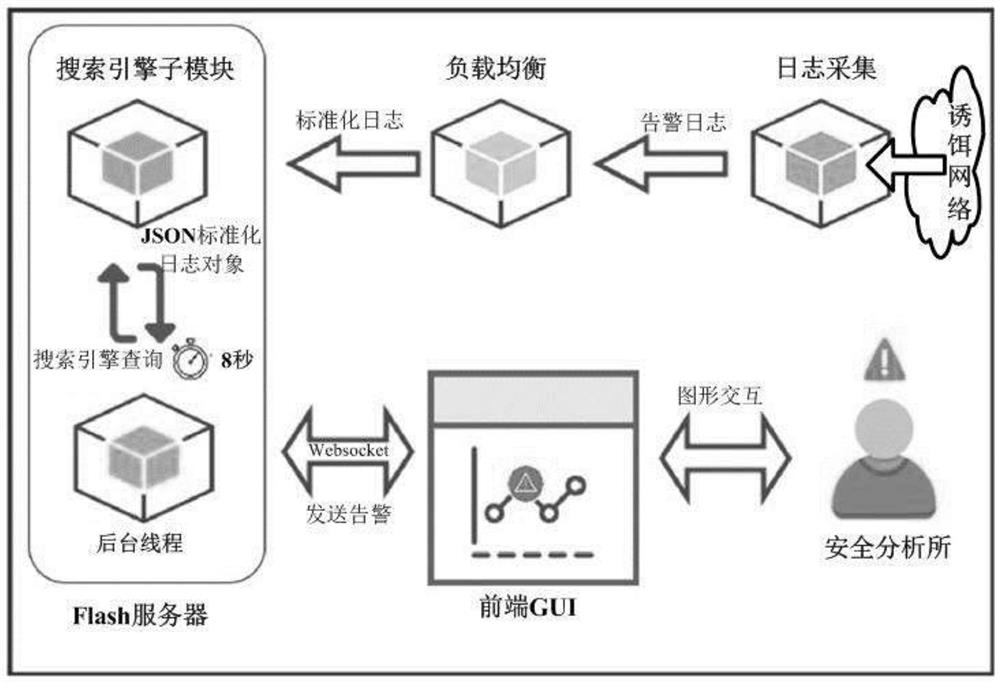
[0026] An active security defense system based on centralized control, customized and developed for centralized control. It shows a significant improvement in performance and usability over previous honeypots. Particularly:
[0027] 1, with extraordinary flexibility. They can be in the form of any digital entity and can be placed anywhere in the corporate network environment; while attackers are able to evade some forms of decoys, they may still be trapped by others;
[0028] 2. Flexible deployment and placement, creating uncertainty that will slow down attackers and possibly even drive them away (i.e. deterrent effect);
[0029] 3. Different decoys for each attack stage can be provided for different stages in the cyber kill chain model; for example, if fake documents are distributed on social networking platforms, attackers may be misled in the del...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com