File encryption method and system, electronic equipment and storage medium
A file encryption and storage medium technology, applied in electronic digital data processing, instruments, digital data authentication, etc., can solve the problems of personal privacy leakage and personal privacy leakage of the owner, and achieve the effect of protecting personal privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
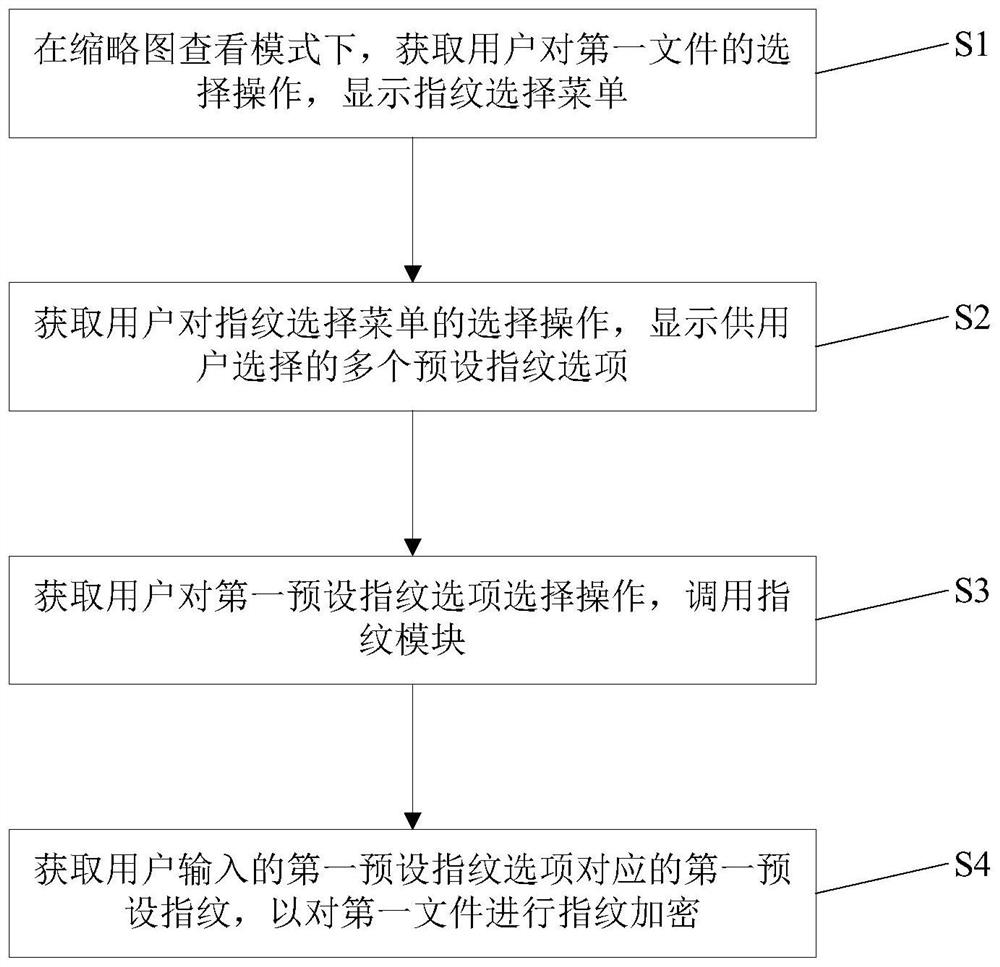
[0041] figure 1 Shows the flow chart of the file encryption method in Embodiment 1 of the present invention. This embodiment provides a file encryption method, such as figure 1 shown, including the following steps:
[0042] Step S1, in the thumbnail viewing mode, acquire the user's selection operation on the first file, and display the fingerprint selection menu.
[0043] Specifically, the first file may be a file stored in the terminal, and the terminal may be a mobile phone or a tablet computer provided with a fingerprint module, and the first file may be a picture or video stored in an album application of the terminal. The selection operation of the first file by the user may be one of a long press operation, a touch operation, and a click operation, but is not limited thereto, and the long press operation may be an operation in which the pressing time exceeds 1 second. For example, after the user starts the photo album application in the terminal, he can select the priv...
Embodiment 2
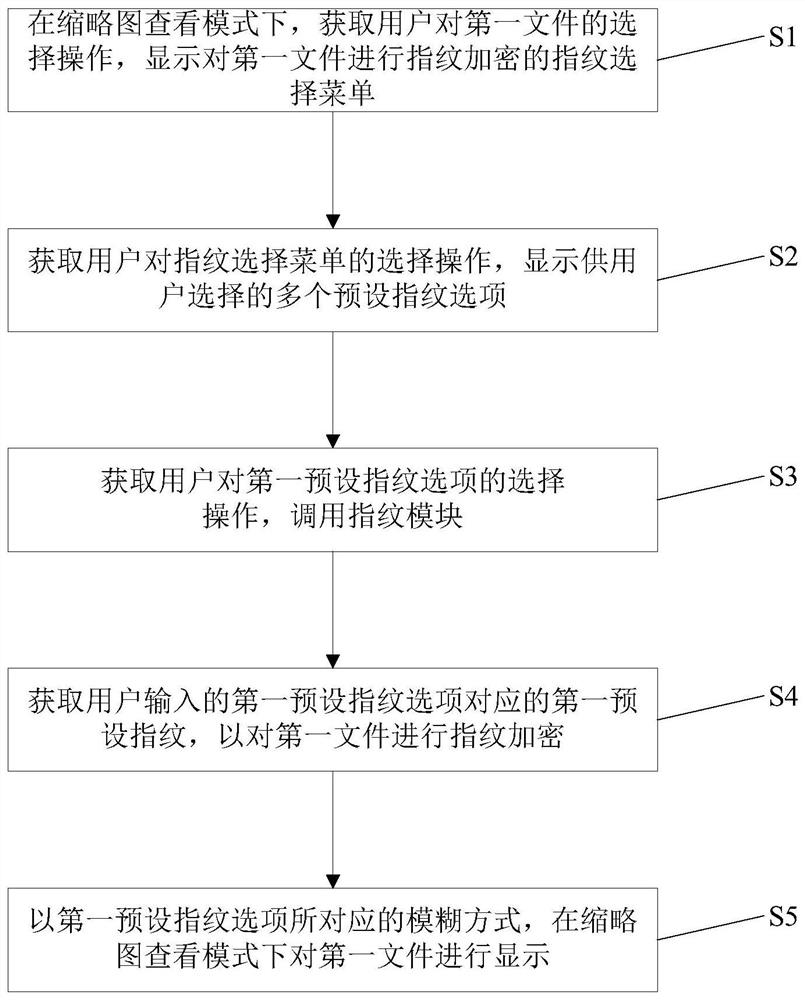
[0053] figure 2 Shows the flow chart of the file encryption method in Embodiment 2 of the present invention. This embodiment provides a file encryption method, such as figure 2 As shown, on the basis of Embodiment 1, after step S4, the method further includes:
[0054] Step S5: Display the first file in the thumbnail viewing mode in the blurred manner corresponding to the first preset fingerprint option.
[0055] Specifically, the obfuscation method corresponding to the first preset fingerprint option may be to cover the first file to hide the content of the first file. The occlusion processing of the first file may include but not limited to: color occlusion, mosaic occlusion, fog occlusion, and pattern occlusion. In this embodiment, occlusion processing is used to achieve a coding effect and hide the content of the private file to be protected.
[0056] When masking the first file in the way of color masking, the preset fingerprints include fingerprint 1, fingerprint 2, ...
Embodiment 3
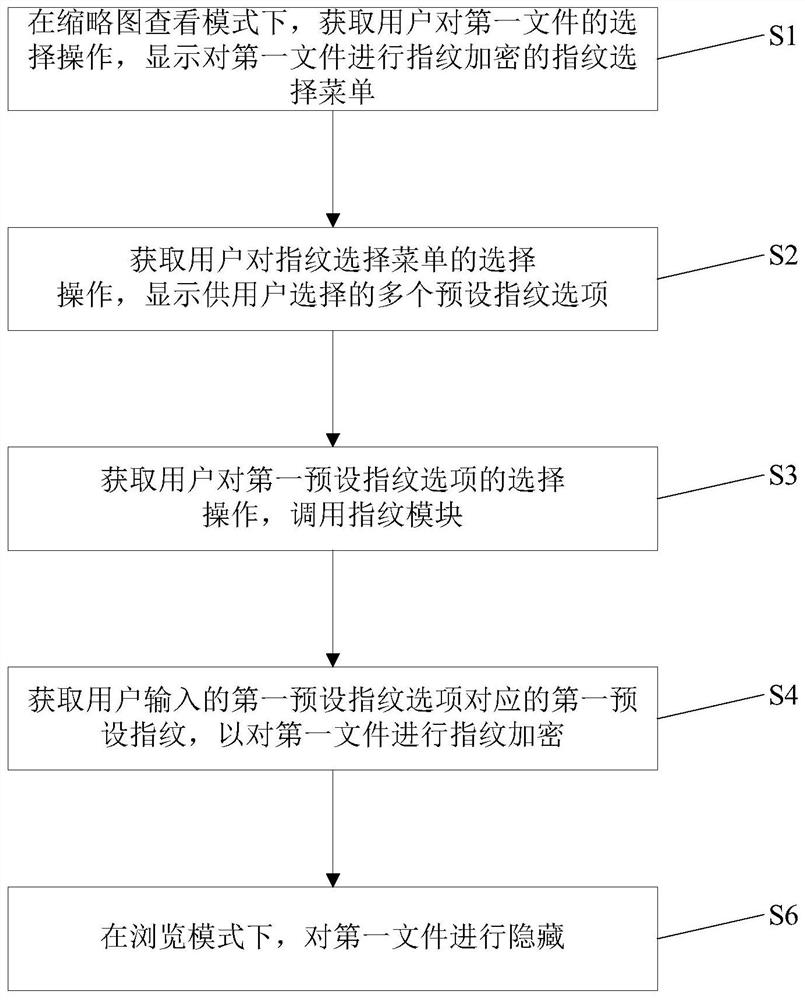
[0060] image 3 Shows the flow chart of the file encryption method in Embodiment 3 of the present invention. This embodiment provides a file encryption method, such as image 3 As shown, on the basis of Embodiment 1, after step S4, the method further includes:
[0061] Step S6, in the browse mode, hide the first file.
[0062] Specifically, taking the photo album application as an example, after starting the photo album application, when browsing the files in the photo album by sliding left and right on the terminal display screen, when browsing to the location of the encrypted first file, it will automatically jump to the first file Adjacent files of , to hide the first file.
[0063] In this embodiment, by hiding the first file when browsing files, the user's privacy can be effectively protected, and the personal privacy of the user can be prevented from being leaked during the process of swiping left and right to browse photos or videos when non-users view files.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com