Controlling provision of access to restricted local operator services by user equipment
A user equipment, operator technology, applied in the field of communication systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
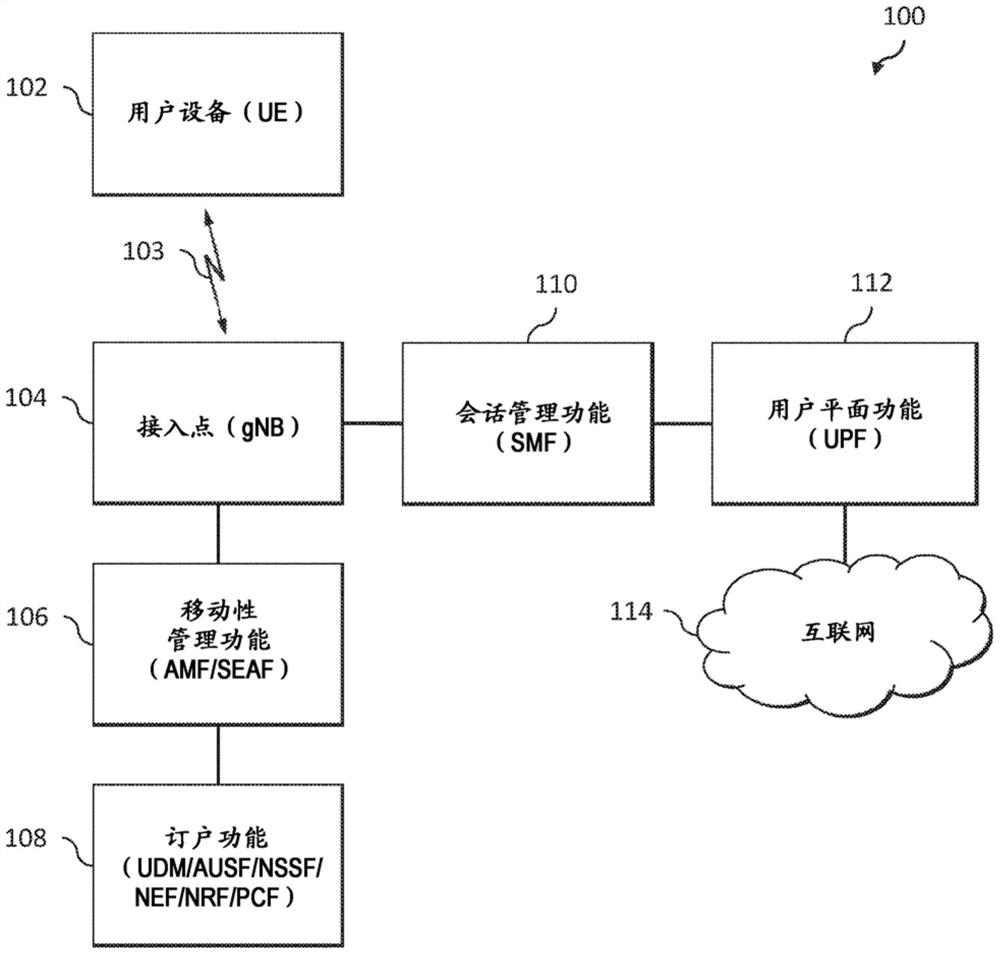
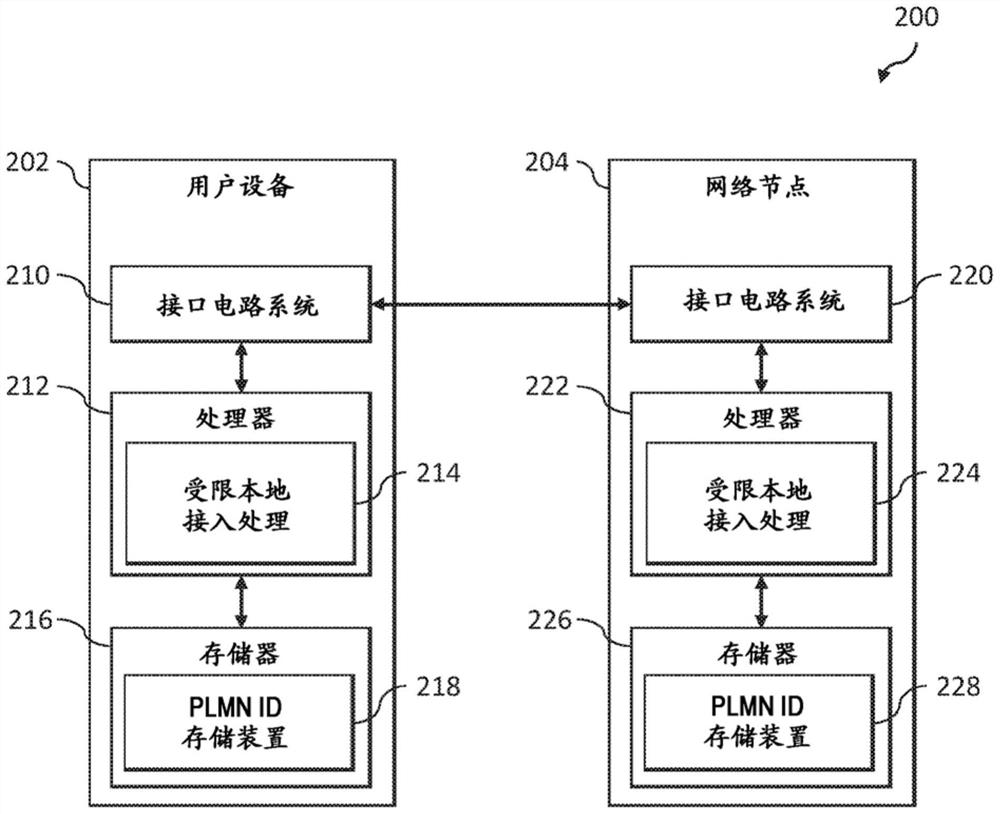
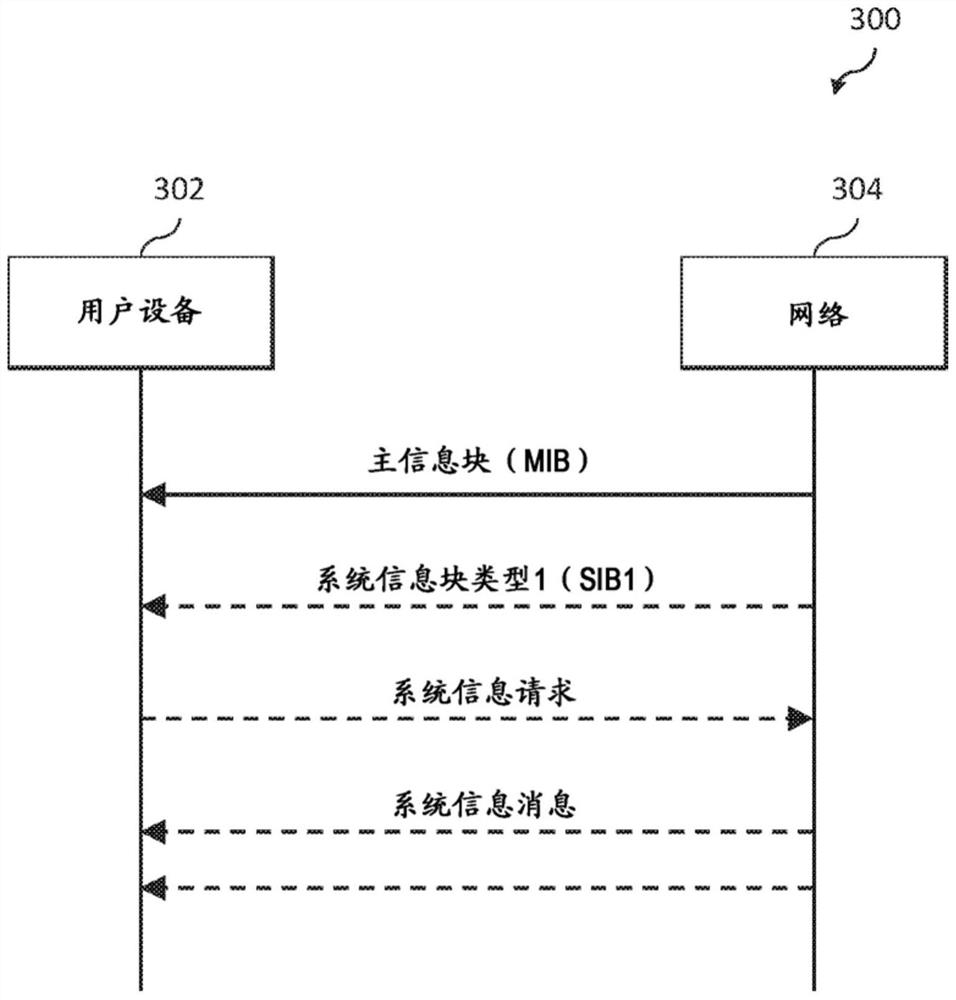
[0018] Embodiments will be described herein in connection with an example communication system and associated techniques for providing security in the communication system, eg, for user equipment seeking restricted local access to a mobile network. It should be understood, however, that the scope of the claims is not limited to the specific types of communication systems and / or processes disclosed. Embodiments may be implemented in various other types of communication systems using alternative procedures and operations. For example, although described in the context of a wireless cellular system utilizing 3GPP system elements, such as 3GPP Next Generation Systems (5G), the disclosed embodiments may be adapted in a straightforward manner to various other types of communication systems.
[0019] According to an illustrative embodiment implemented in the context of a 5G communication system, one or more 3GPP Technical Specifications (TS) and Technical Reports (TR) provide support...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap