Spoofing detection apparatus, spoofing detection method, and computer-readable storage medium
A deception detection, computer technology, applied in speech analysis, instruments, etc., can solve the problem of ASV being vulnerable to deception, and achieve the effect of suppressing misrecognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] Each exemplary embodiment of the present invention will be described below with reference to the accompanying drawings. The following detailed description is merely exemplary in nature and is not intended to limit the invention or the application and uses of the invention. Furthermore, there is no intention to be bound by any theory presented in the preceding background of the invention or the following detailed description.
(Content of invention)
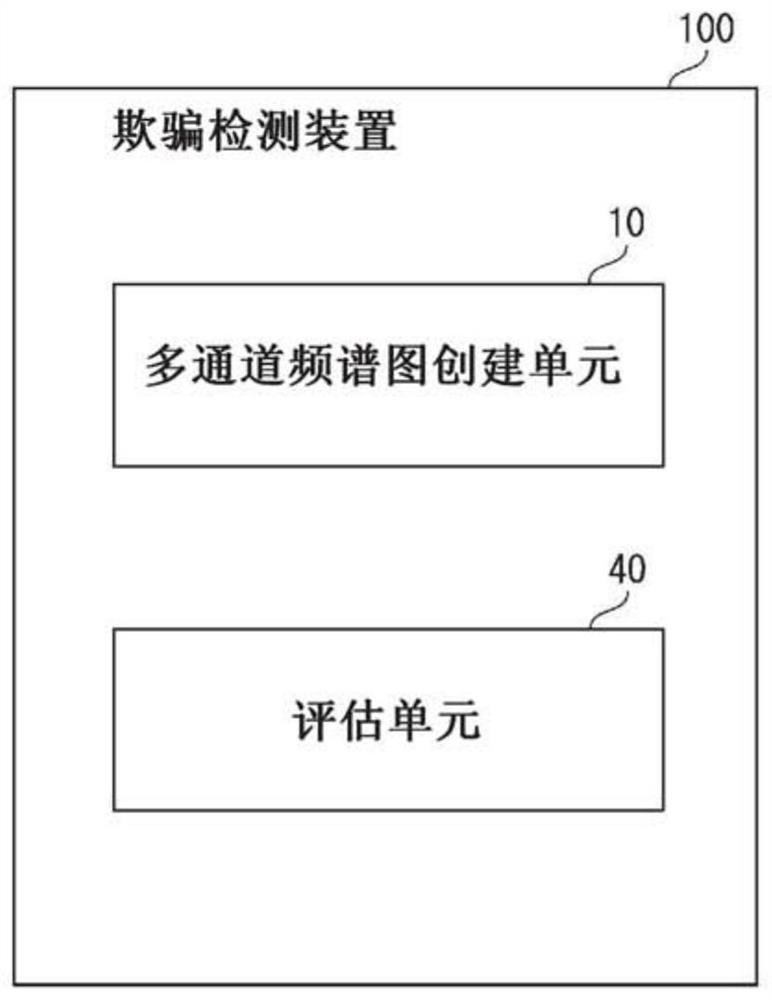
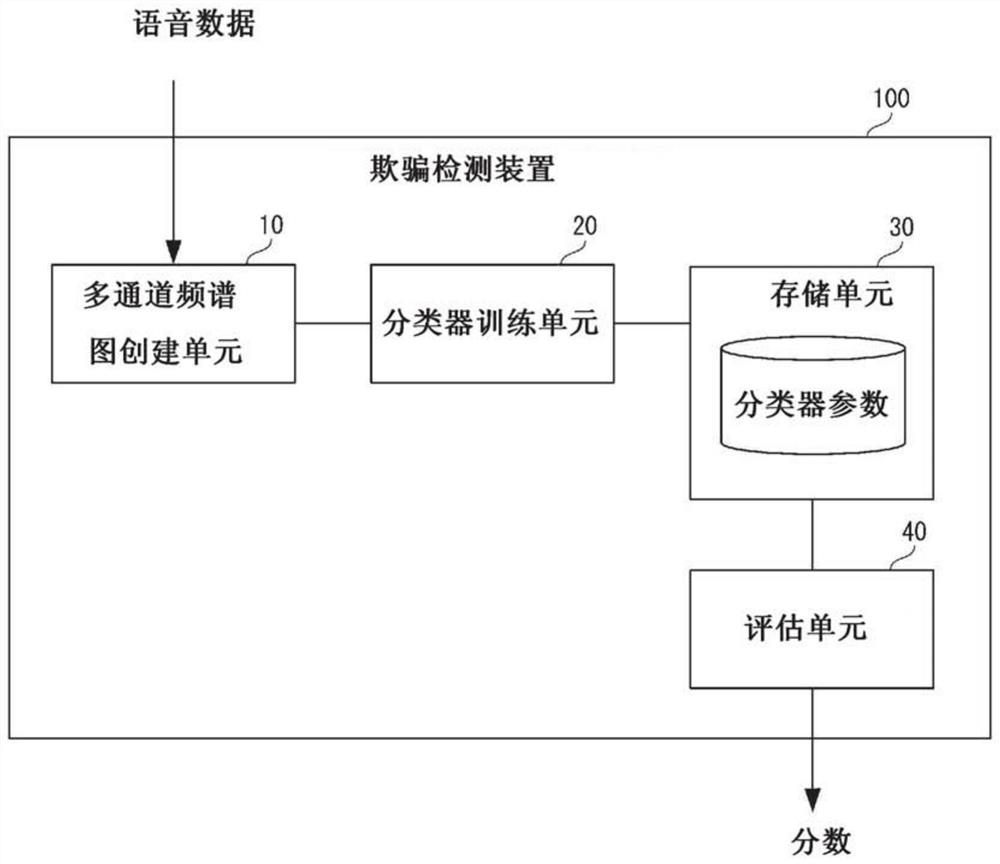
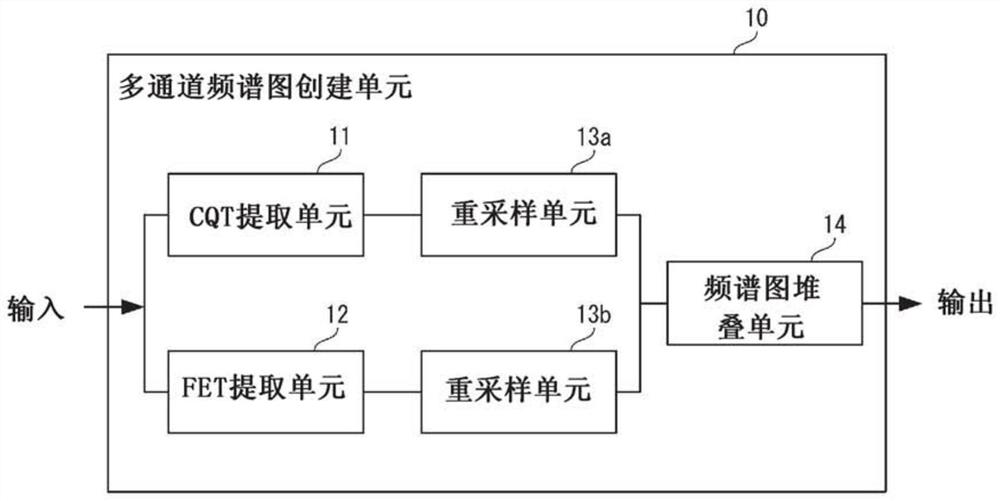
[0038] The invention fuses CQT and fast Fourier transform (FFT) spectrograms as multi-channel input in the neural network, so as to complement each other and ensure the robustness of the fraud detection system.
[0039] According to the present invention, the spoof detection apparatus, method and program of the present invention can provide a more accurate and robust representation of speech utterances for spoof detection. This is because the present invention provides a new fusion of multiple spectrograms as a multi-chan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com