Suspicious external connection detection method and device
A detection method and suspicious technology, applied in the direction of secure communication devices, digital transmission systems, electrical components, etc., can solve the problems of single data source of detection scheme, low accuracy rate of suspicious external connections, difficulty in finding unknown threats, etc., to achieve rich data sources , enhance suspiciousness, and get rid of dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
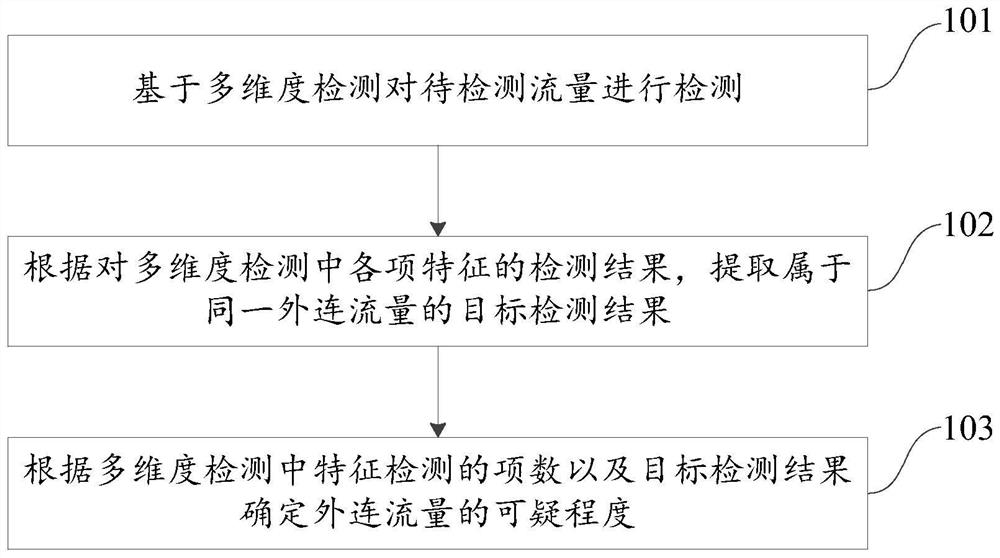
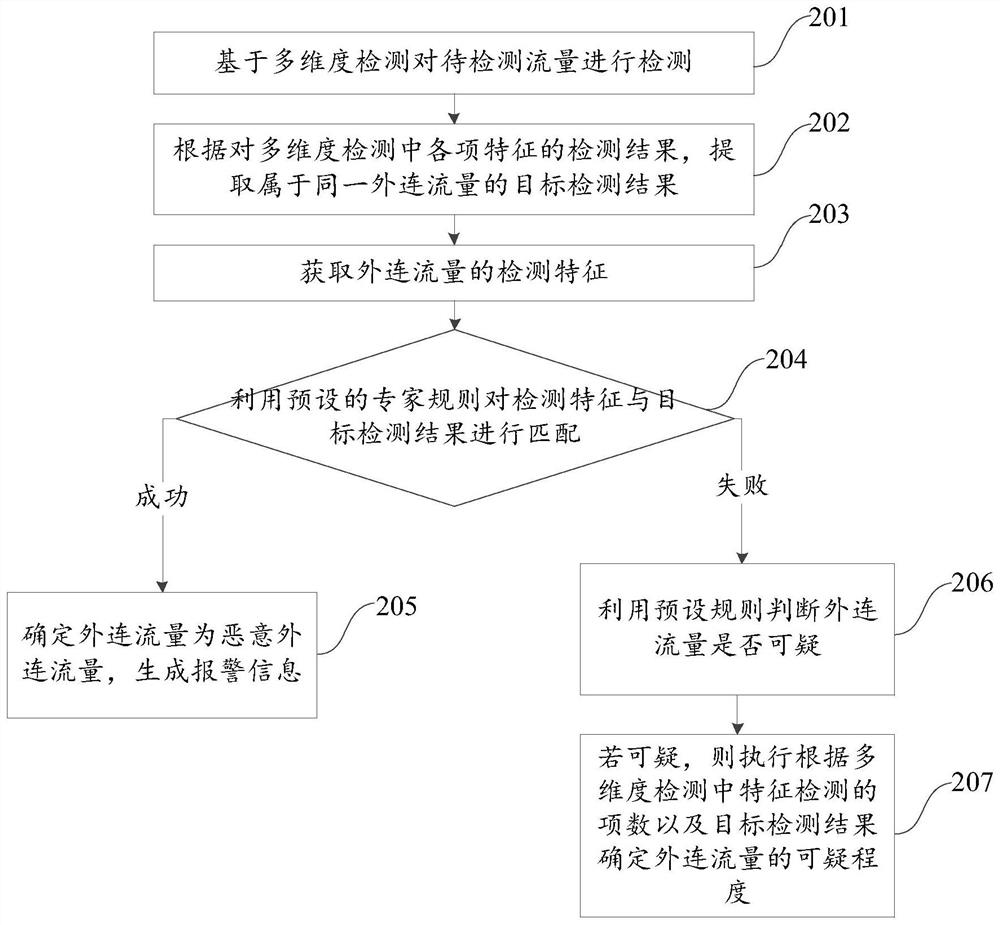
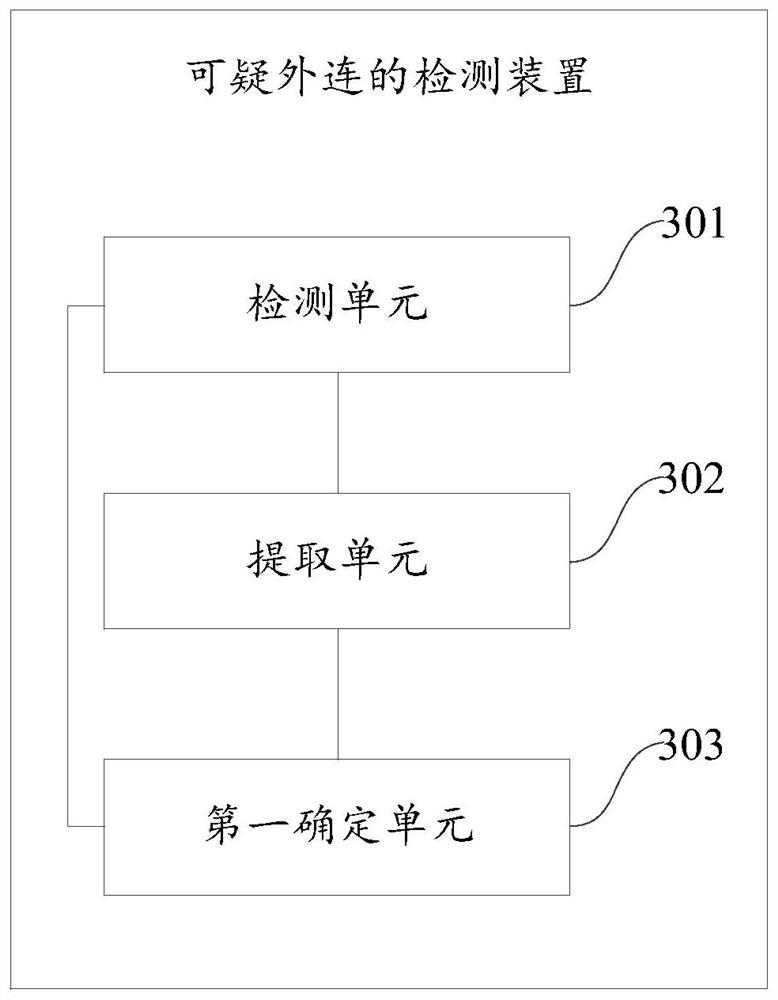
[0023] Exemplary embodiments of the present disclosure will be described in more detail below with reference to the accompanying drawings. Although exemplary embodiments of the present disclosure are shown in the drawings, it should be understood that the present disclosure may be embodied in various forms and should not be limited by the embodiments set forth herein. Rather, these embodiments are provided for more thorough understanding of the present disclosure and to fully convey the scope of the present disclosure to those skilled in the art.
[0024] With the development of network technology, more and more hackers use remote control Trojan horses and other means to remotely manipulate the accused host to steal valuable information in the enterprise. Among them, small and medium-sized enterprises are more likely to be attacked. , whether it comes from hacker attacks, internal business information leakage or damage from natural disasters, the losses caused are quite heavy....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com