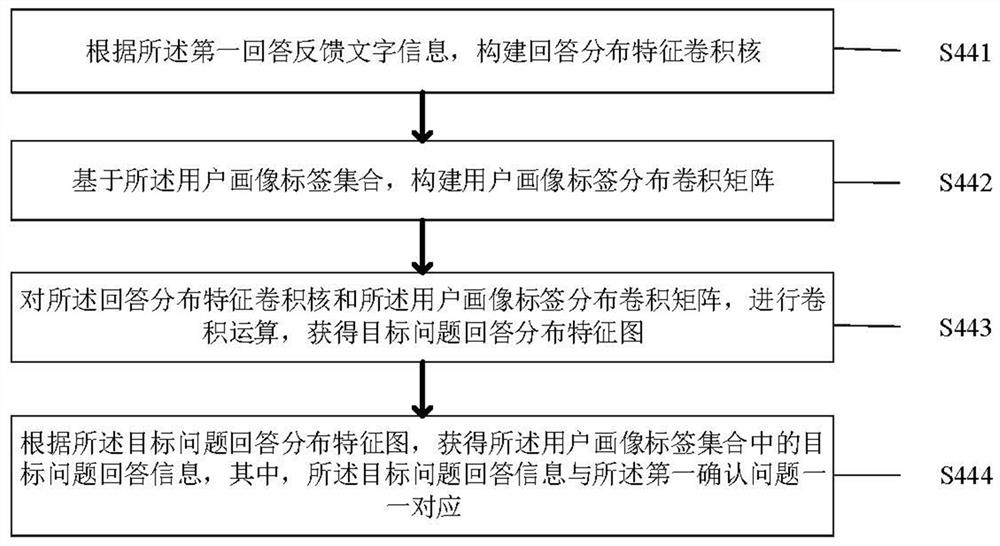
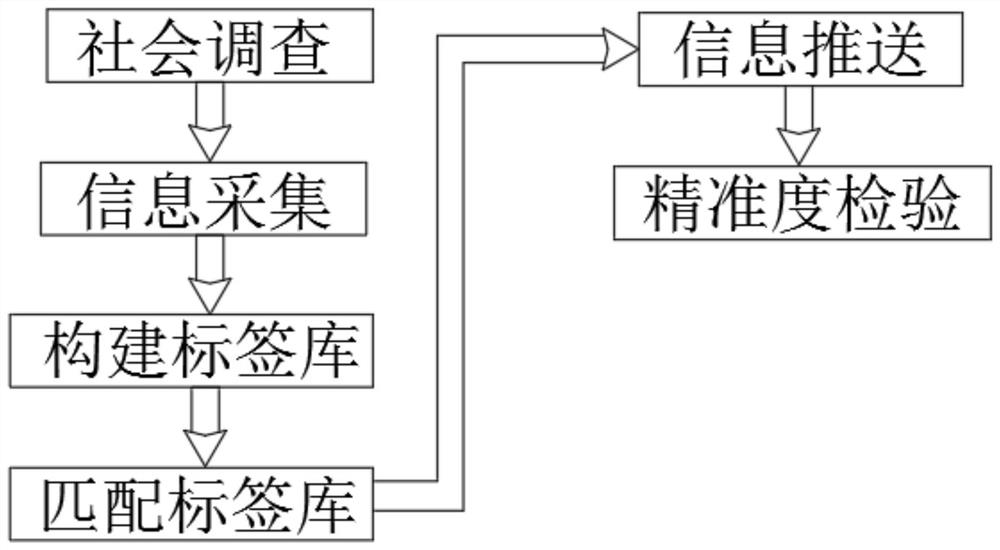
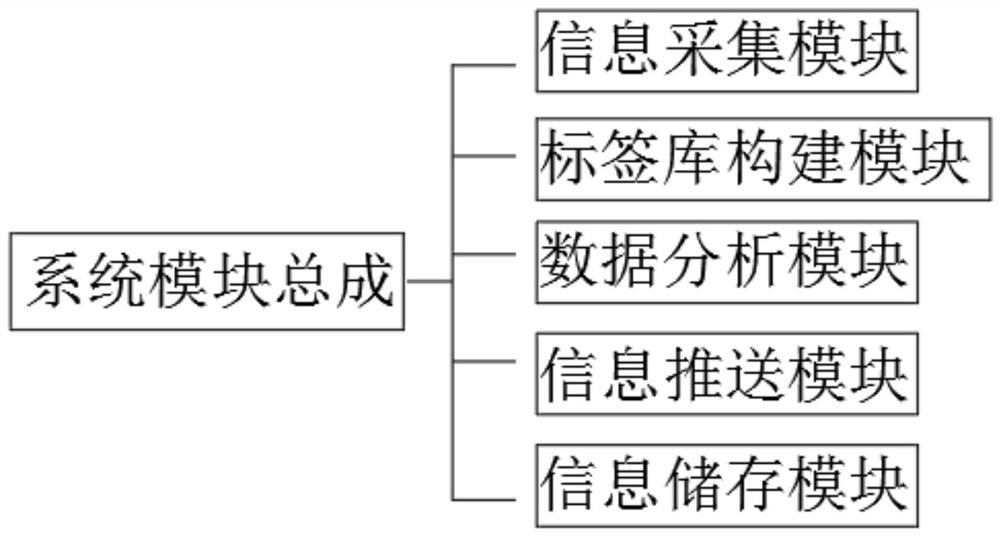
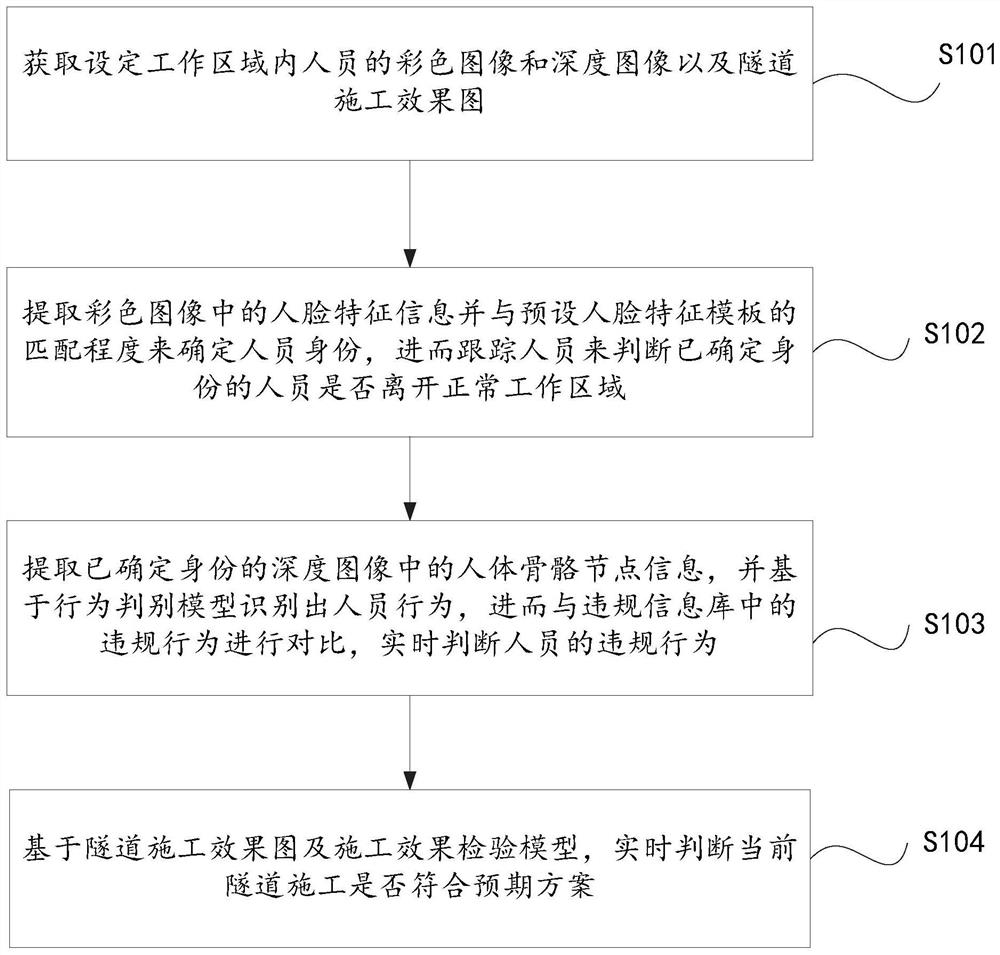
Patents
Literature
45 results about "Information behaviour" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information behaviour is traditionally associated with information seeking and narrower, system specific, information search techniques. Beyond information seeking, we can envisage a more general information behaviour (Wilson 2000), which itself can be sited within a still wider framework of information communication.
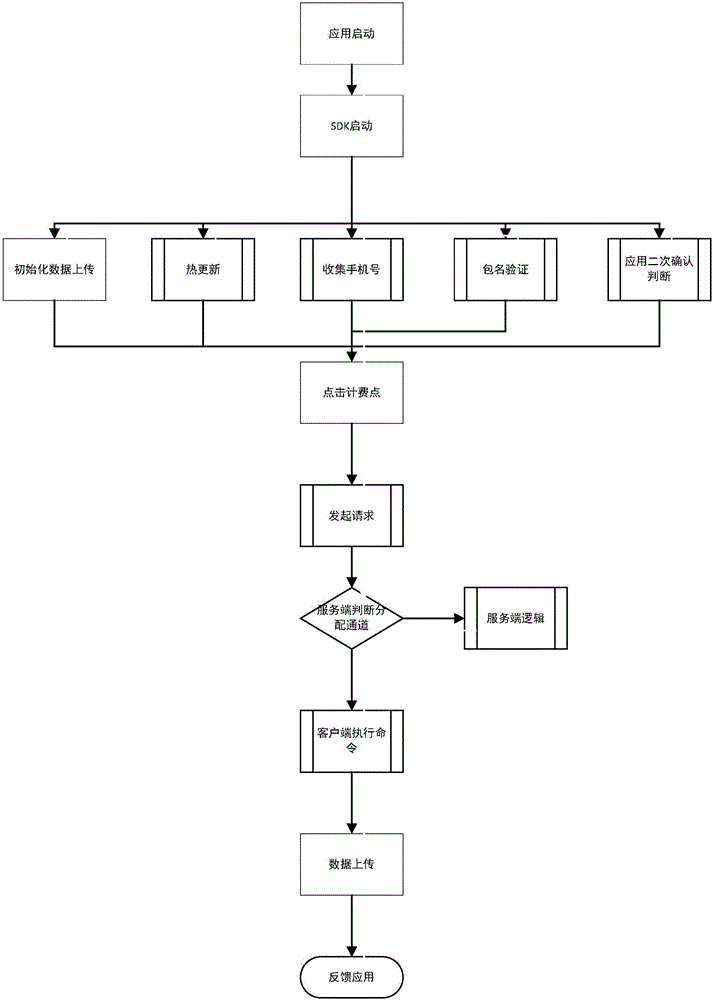
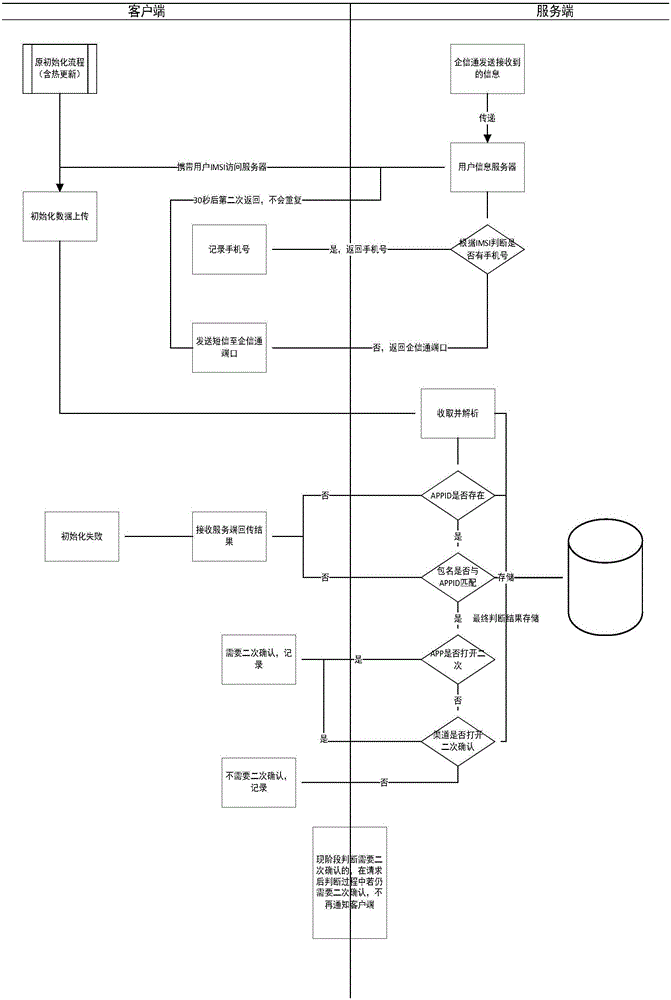
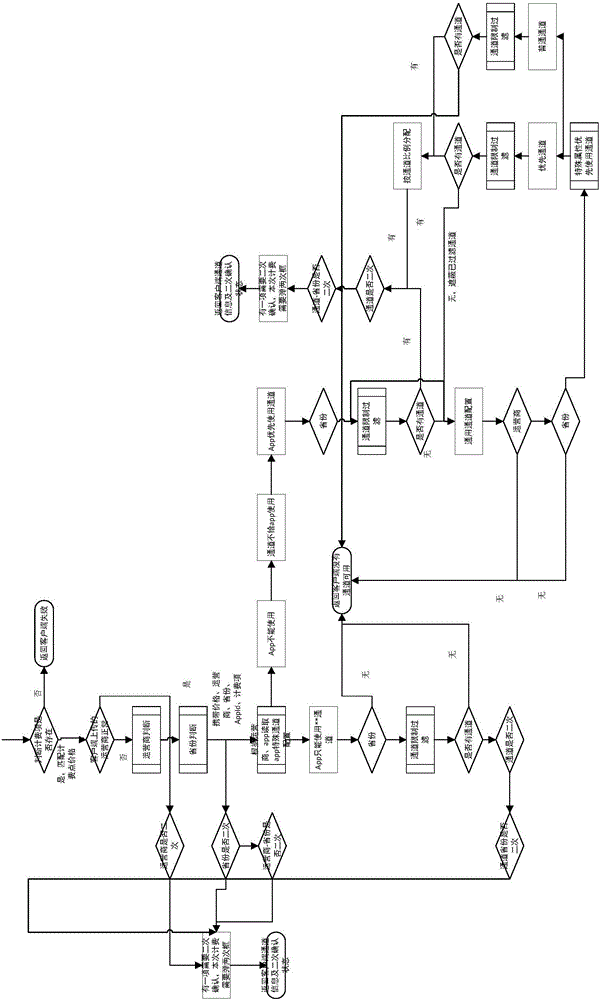
SDK processing method suitable for application client end payment
InactiveCN105913233AImprove convenienceSave time and costPayment architectureInformation behaviourSoftware engineering
The invention relates to an SDK processing method suitable for application client end payment. The SDK processing method is characterized by comprising the following steps: an SDK is started along with an application client end, and necessary initialization is realized in starting processes; when a user clicks on charging, the SDK communicates with a cloud server; the cloud server choose among charging channels; an application client end conducts charging operation, a charging result is fed back to the cloud server, a final charging result is displayed via the application client end, charging channels matching with three major mobile operators in china can be used, and great convenience can be realized; an SDK integration pack can be automatically updated. A mobile application provider does not need to check development documents provided by all platforms in a one-by-one manner; via use of cloud computing technologies, an optimal charging channel which conforms to conditions of the user can be automatically chosen, and a unified user platform can be built; the user only needs to check integrated and unified details at background, instead of checking user charging information, behavior information and the like of all the platforms in a one-by-one manner.
Owner:苏州云清伟业网络科技有限公司
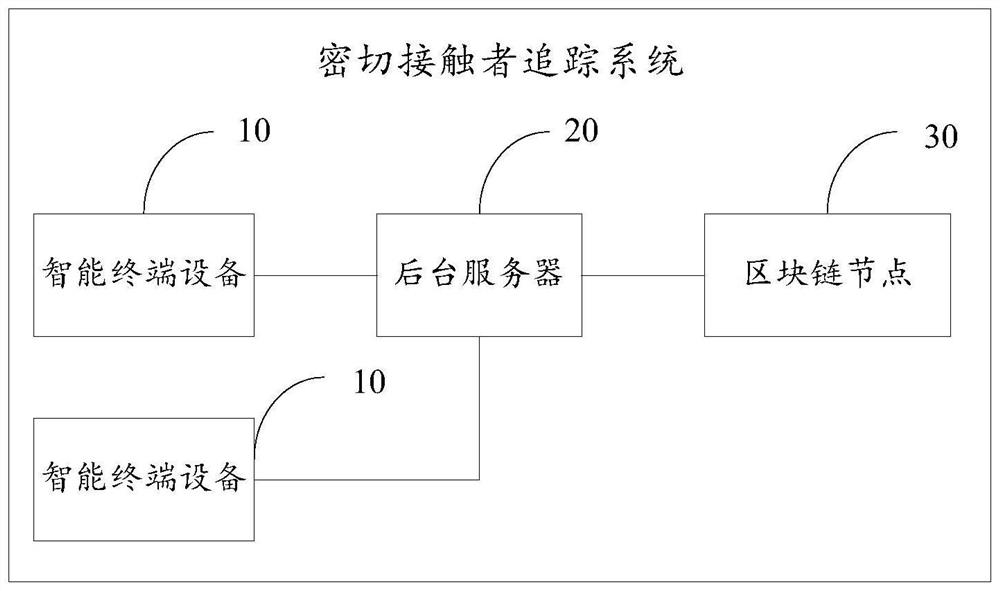
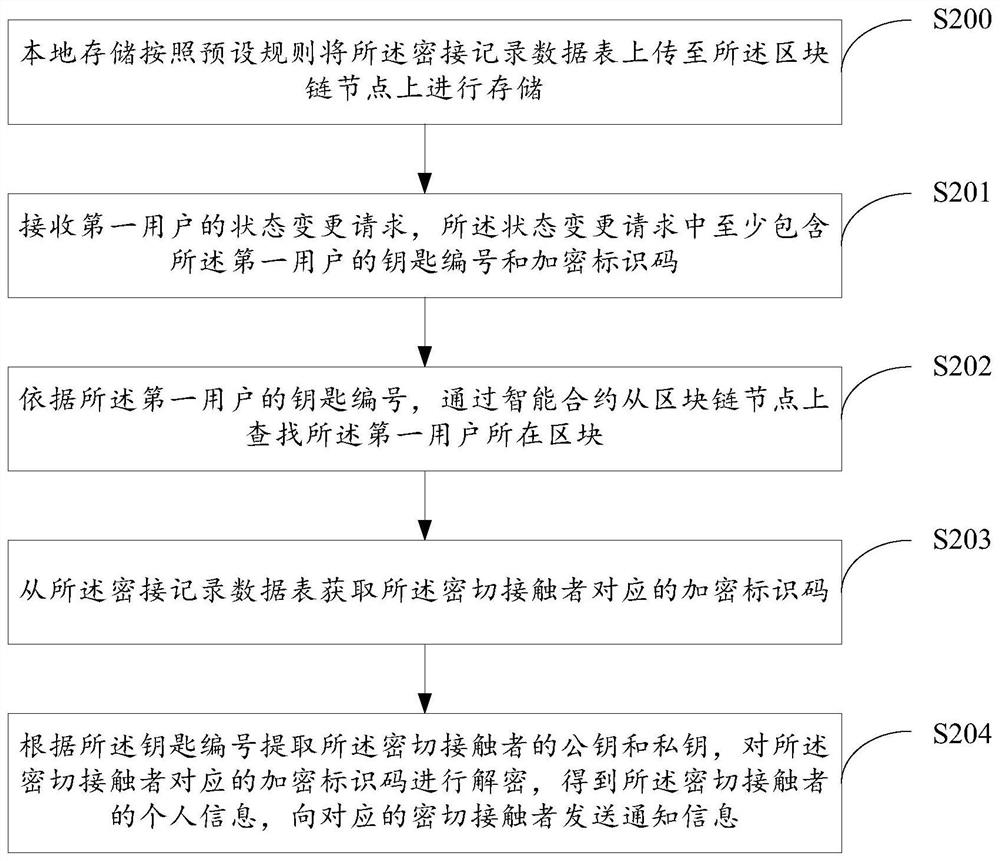
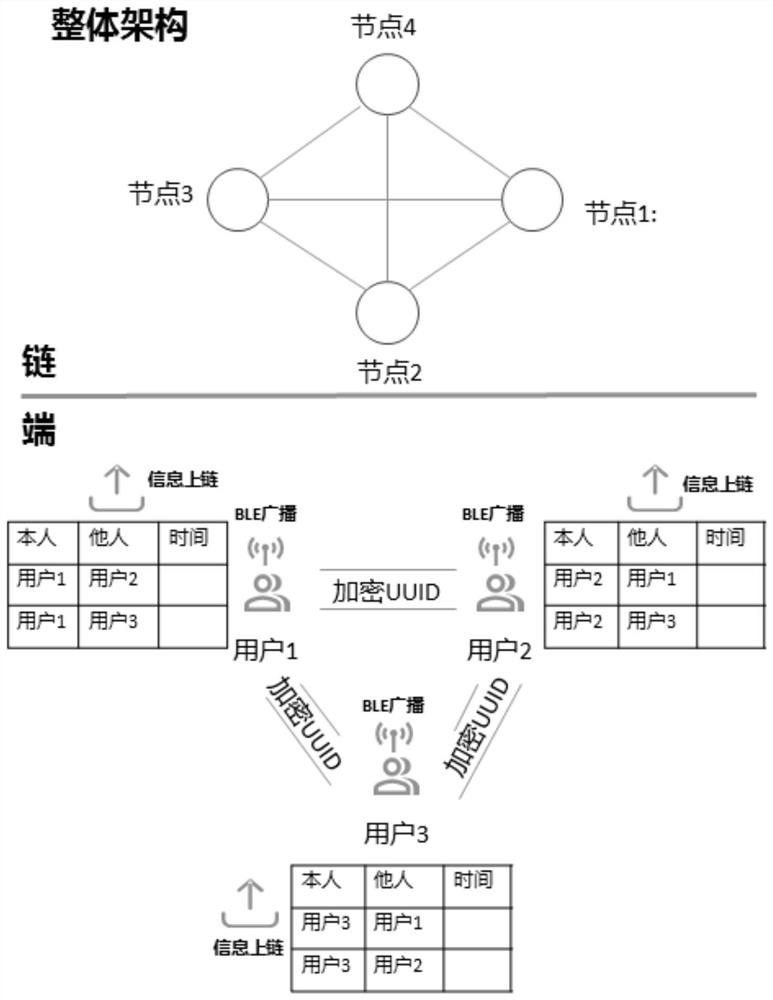
Close contact person tracking method, device, storage medium and electronic equipment
PendingCN112069542ARealize TrackingImplement the tracking functionDigital data protectionSpecial data processing applicationsDatasheetInformation behaviour
The invention provides a close contact person tracking method, a device, a storage medium and electronic equipment. The method comprises the steps: storing a close contact record data table comprisingan encryption identification code of a first user and an encryption identification code corresponding to a close contact person in a blockchain node in advance, and carrying out the intelligent contract technology when the state of a user changes; and executing decryption of the encryption identification code, obtaining the encryption identification code of the close contact person on the block chain, extracting the public key and the private key of the close contact person according to the key number of the close contact person, decrypting the encryption identification code corresponding tothe close contact person to obtain personal information of the close contact person, and sending notification information to the corresponding close contact person. The tracking of a close contact person is realized. In the tracking process of the close contact person, encryption protection is provided for personal information of the user, and the tracking function of the close contact person is achieved on the premise that personal privacy information (behavior data or position data and the like) of the user does not need to be provided.
Owner:BEIJING PRECISION MEDTECH CO LTD
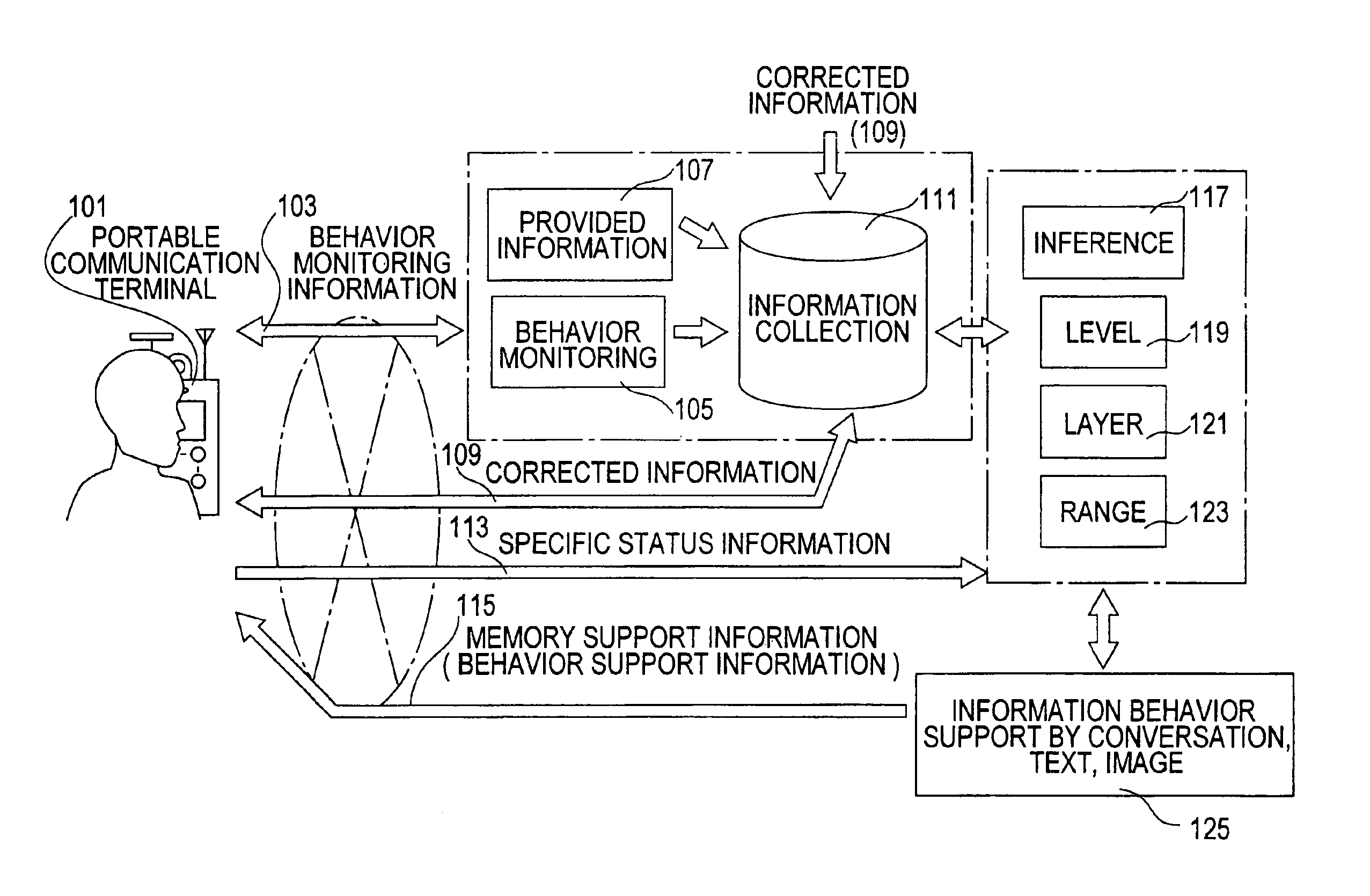
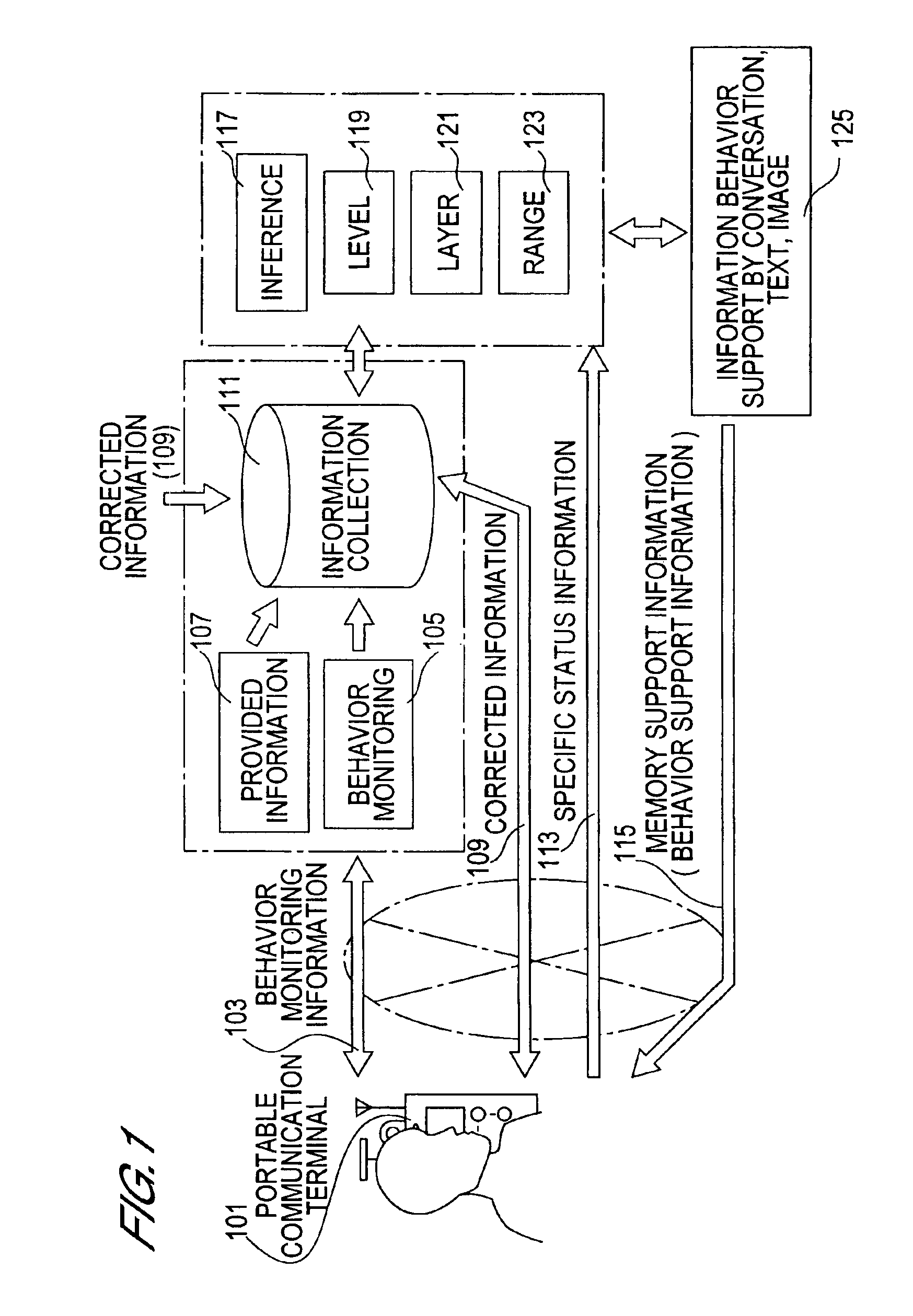
Method for complementing personal lost memory information with communication, and communication system, and information recording medium thereof
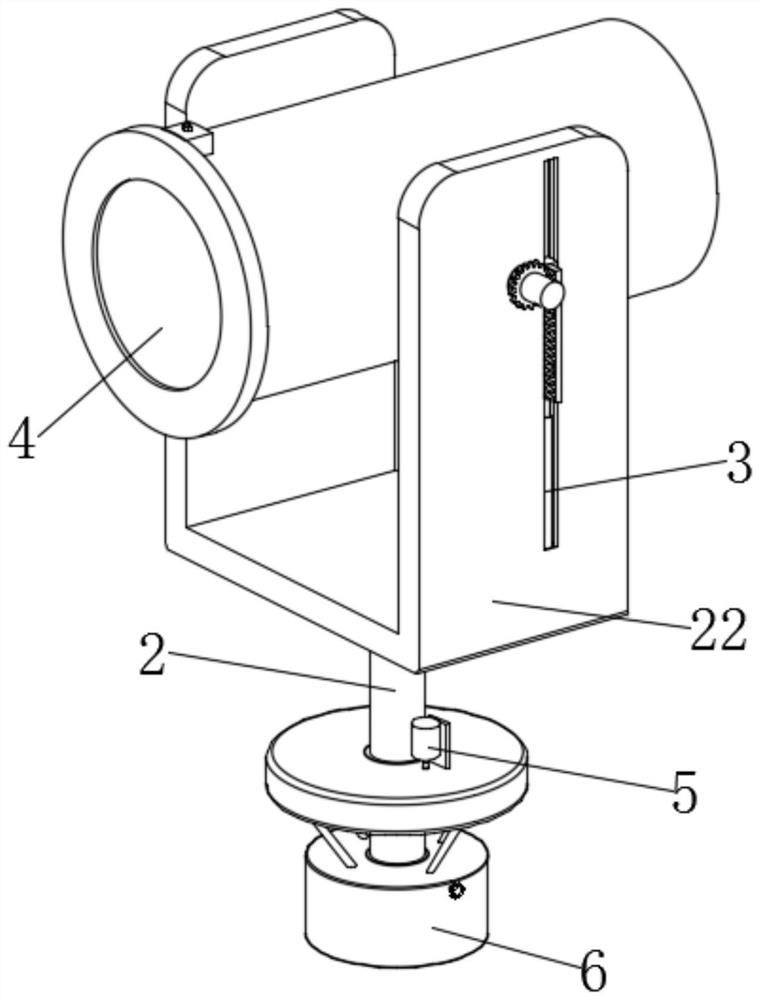
InactiveUS6950026B2Easy to implementIncrease flexibilityMaps/plans/chartsDiagnostic recording/measuringComputer hardwareCommunications system
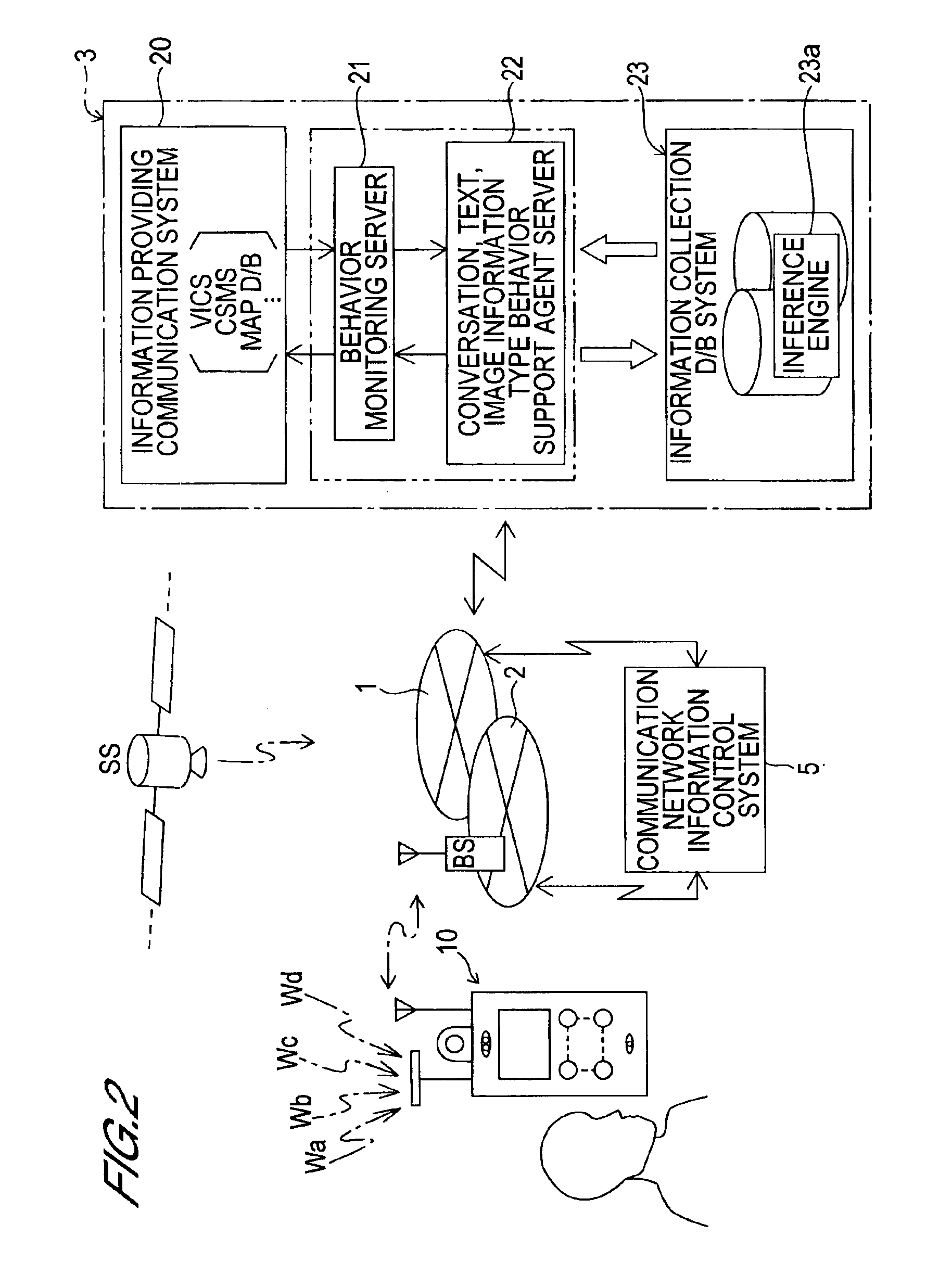
The present invention enables appropriate behavior of an individual who has problems with memory, and behavior support thereof with certainty. The individual who has problems with memory always carries the portable communication terminal and loads and collects various types of information along with an ID through the communication network as behavior monitoring information. Also various types of provided information (e.g. map information) are collected. When a specific status information (e.g. forgetting the road to take) of the individual who carries the portable communication terminal is loaded, memory support information (behavior support information) is generated by conversation, text and image, so that the specific status where the individual who lost memory cannot take an action to be performed next can be individually dispelled on the spot based on the information collected in the past and various types of provided information, and this memory support information is transferred to the individual carrying the portable communication terminal. In this way, information for dispelling a specific status where an individual who lost memory cannot take an action to be performed next on the spot can be implemented by inference, personally and instantaneously.
Owner:NAT INST OF INFORMATION & COMM TECH
Data privacy protection method and system based on block chain and authority contract
PendingCN113420319AEnsure safetyRapid positioningDigital data protectionInformation behaviourData privacy protection
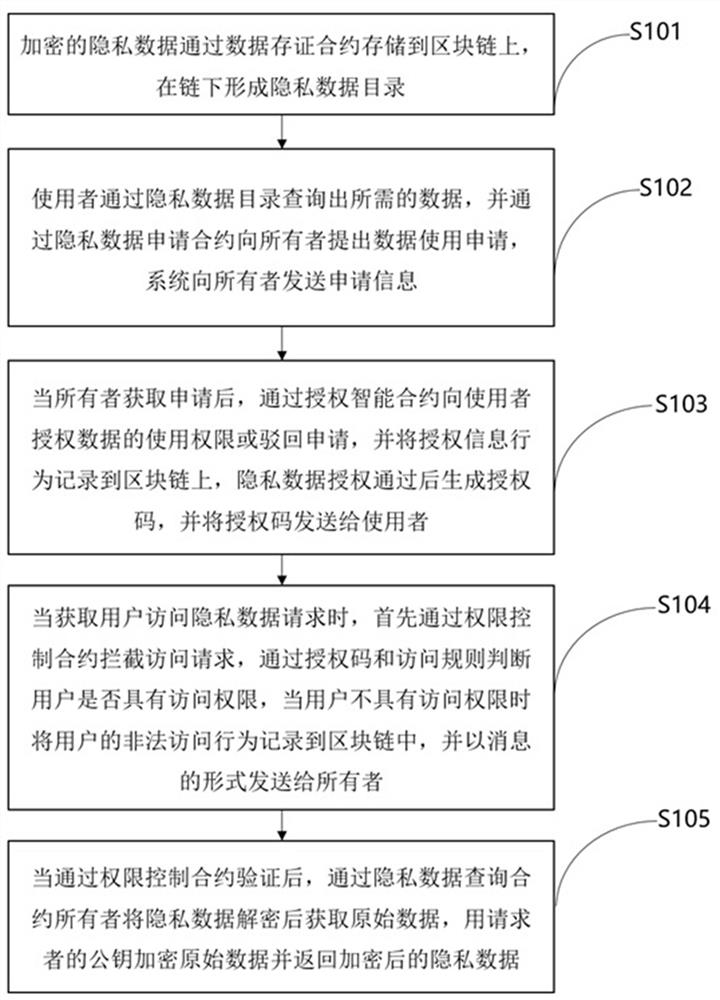
The invention discloses a data privacy protection method and system based on a block chain and an permission contract, and relates to the technical field of block chains. The method comprises the following steps of: 1) storing encrypted private data on a block chain to form a private data directory; 2) querying required data, and proposing a data use application to an owner through a private data application contract; 3) after obtaining the application, enabling the owner to authorize the use permission of the data to the user or reject the application through the authorization smart contract, and record the authorization information behavior on the block chain. 4) when a private data access request of the user is obtained, judging whether the user has the access authority or not through the authorization code and the access rule. and 5) after the privilege control contract verification is passed, decrypting the privacy data to obtain the original data, encrypting the original data by using the public key of the requester, and returning the encrypted privacy data. According to the method and system, the security of the privacy data can be remarkably improved, and the ownership of the privacy data can be ensured to facilitate sharing of the privacy data.
Owner:TSINGHUA TONGFANG CO LTD
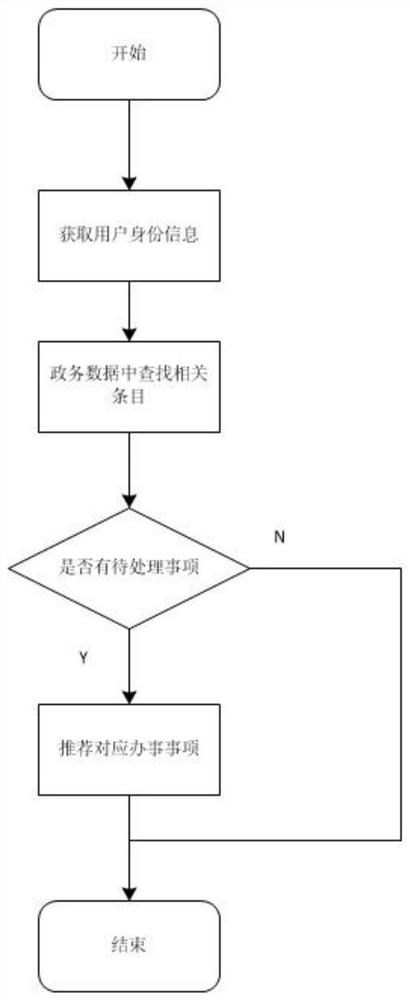
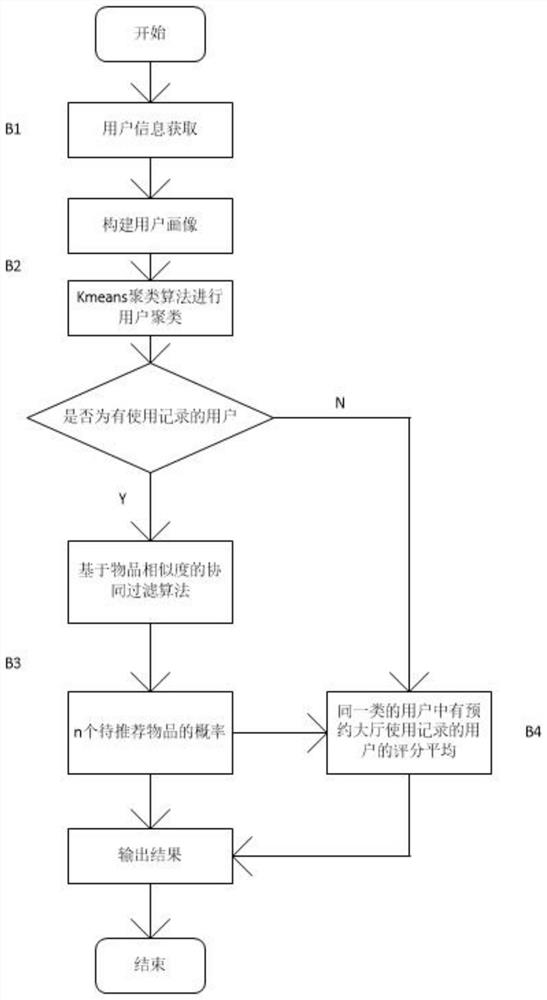
Government affair reservation service recommendation method based on machine learning
PendingCN114595850AEasy to useReduce time spent on search queriesReservationsMachine learningPersonalizationInformation behaviour
According to the government affair reservation service recommendation method based on machine learning disclosed by the invention, recommendation is carried out in various scenes, the scene I carries out data linkage, data sources are enriched, and items needing to be handled can be recommended according to personal records of all government affair departments, and the scene II constructs a user portrait and constructs user features in combination with basic information and behavior data of a user, so that the user experience is improved. According to information such as properties of services and appointment items, article features are constructed, article scores are calculated based on an article similarity model and user portraits, users are divided by adopting a clustering mode, and personalized customization and possible affair handling items can be recommended for both new and old users; in the third scene, the geographic position coordinates of the user and the geographic position coordinates of all the to-do sites are utilized, the coordinate positions are classified through a classification algorithm and then weighted calculation is carried out to give a suggested recent service site, item recommendation for different types of users in different scenes is achieved, the user can use the appointment service module more conveniently, and the user experience is improved. And the working efficiency is improved.
Owner:厦门市民数据服务股份有限公司
Method for registering life cycle information of file into OFD format file
ActiveCN112732654AAchieve Effective Track RecordEnable cross-application sharingDigital data protectionOffice automationInformation behaviourSoftware engineering
The invention discloses a method for registering life cycle information of a file to an OFD format file, which comprises the following steps of: in an OFD application environment, particularly an application environment adopting a workflow form system, distributing, circulating, checking, reading, editing, signing, storing, filing and backing up information generated in all operations as life cycle information to record and temporarily store; storing the life cycle information in an xml document of the file; and storing the xml document path into the extended content. No matter whether the file is in the application system or after leaving the application system, the main process information and behavior information of the life cycle of the file in the original application system can be seen clearly, and the service process system, such as a workflow form system, in the application environment can check the summarized file life cycle information, so that the user experience is improved. And the state of the file can be traced conveniently.
Owner:JIANGSU ZHONGWEI TECH SOFTWARE SYST
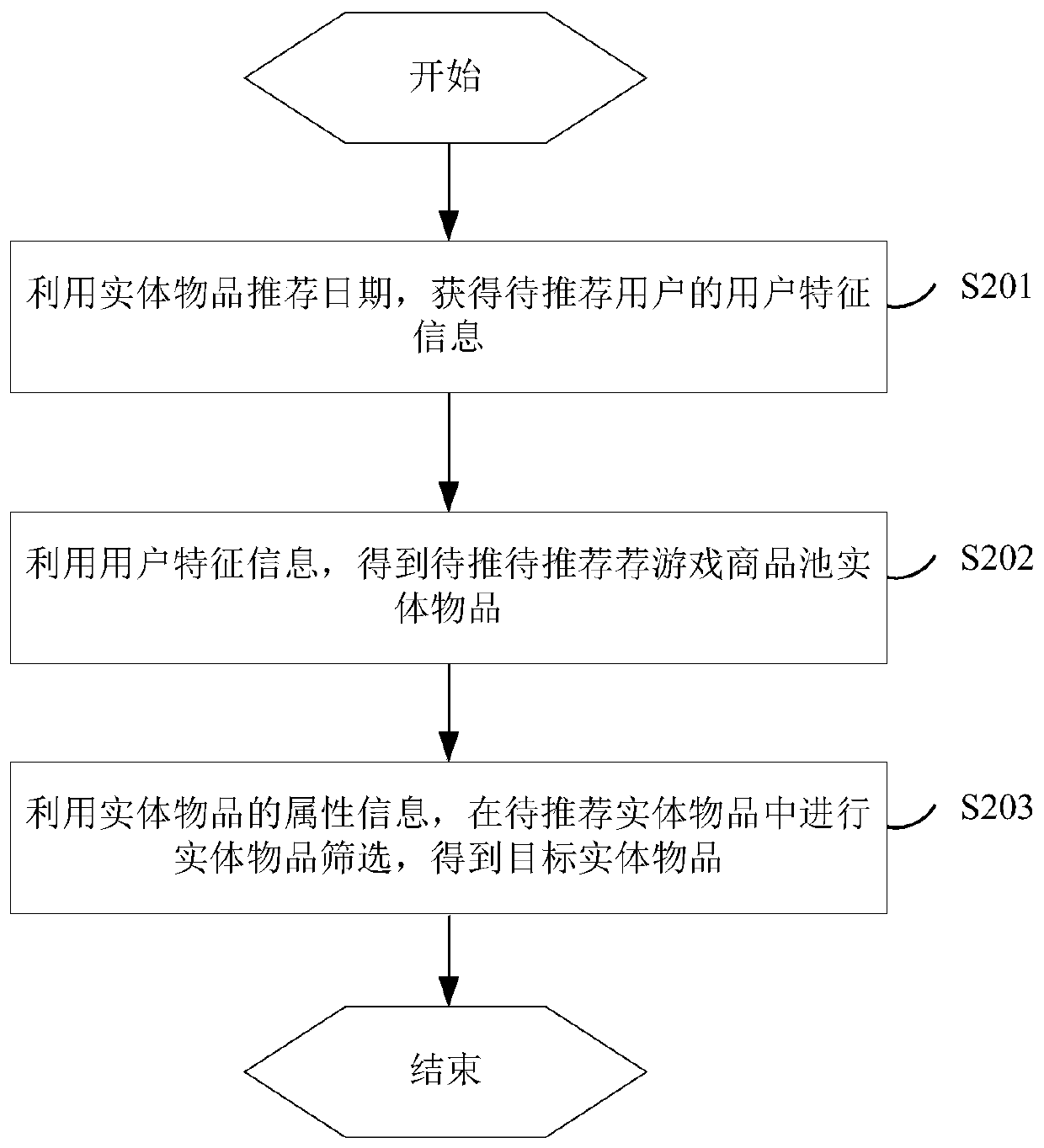
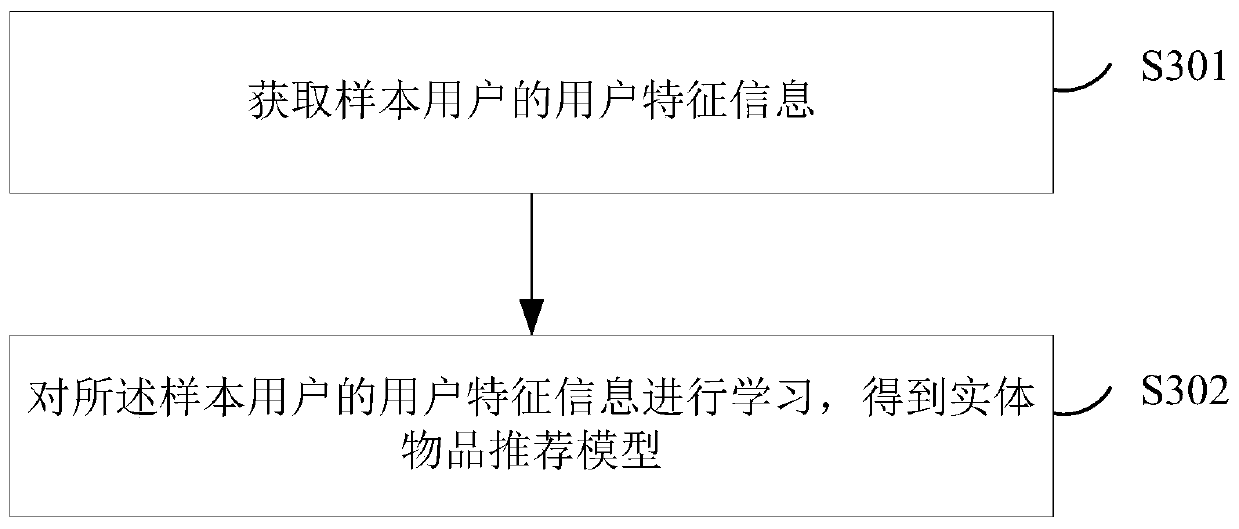
Entity article recommendation method and device, server and storage medium
InactiveCN110602532AAccurate analysisImprove accuracyVideo gamesSelective content distributionData miningInformation behaviour
The invention discloses an entity article recommendation method and device, a server and a storage medium, and belongs to the technical field of artificial intelligence. The entity article recommendation method includes: obtaining user characteristic information of the to-be-recommended user by utilizing the entity article recommendation date; obtaining a to-be-recommended entity article by utilizing the user feature information; and performing entity article screening in the to-be-recommended entity articles by utilizing the attribute information of the entity articles to obtain target entityarticles. The feature information of the user at least comprises the operation information behavior feature information of the user in the target application and the operation behavior feature information of the to-be-recommended user on the entity article; therefore, the analysis of the preference degree of the user to the physical object is more accurate; and screening is carried out in combination with the attribute information of the entity articles, so that the recommended entity articles better meet the requirements of the current recommended user, the occupation of server processing resources in the recommendation process is reduced, and the accuracy of entity article recommendation for different users is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for evaluating performance ability of person subject to enforcement of court
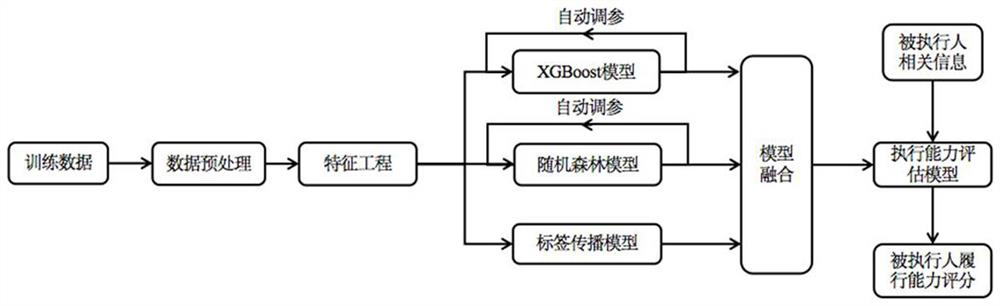
PendingCN111798303AAddressing capacity assessment issuesGuaranteed confidenceFinanceCharacter and pattern recognitionInformation behaviourFeature coding
The invention discloses a method for evaluating the performance ability of a person subject to enforcement of a court. Identity information, case information, behavior information, relation information, consumption information and property information of the person subject to enforcement are used as a feature training model, and a performance ability score is output. The method comprises the following steps: 1, performing data preprocessing including data association, data cleaning and continuous feature value processing; 2, performing feature engineering: carrying out feature coding and feature selection; 3, performing model training: carrying out model training through an XGBoost model, a random forest model and a label propagation model; 4, carrying out model parameter adjustment: automatically adjusting parameters of the XGBoost model and the random forest model by adopting improved grid search to search for optimal parameters; and 5, carrying out model fusion: multiplying the execution score output by each model by the weight of the model, and then summing the multiplied model scores to obtain a final performance ability score.
Owner:浙江公共安全技术研究院有限公司
Method and system for determining information similarity
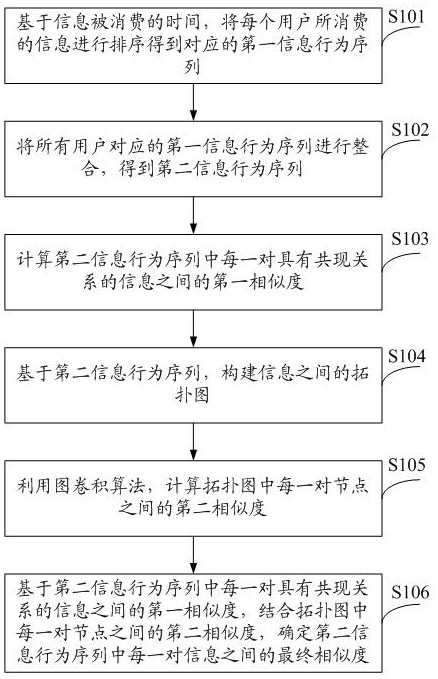
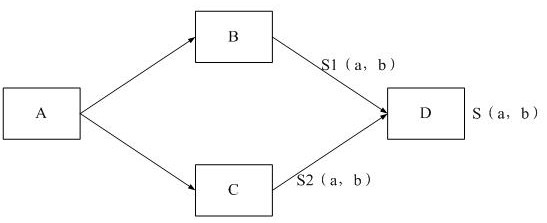
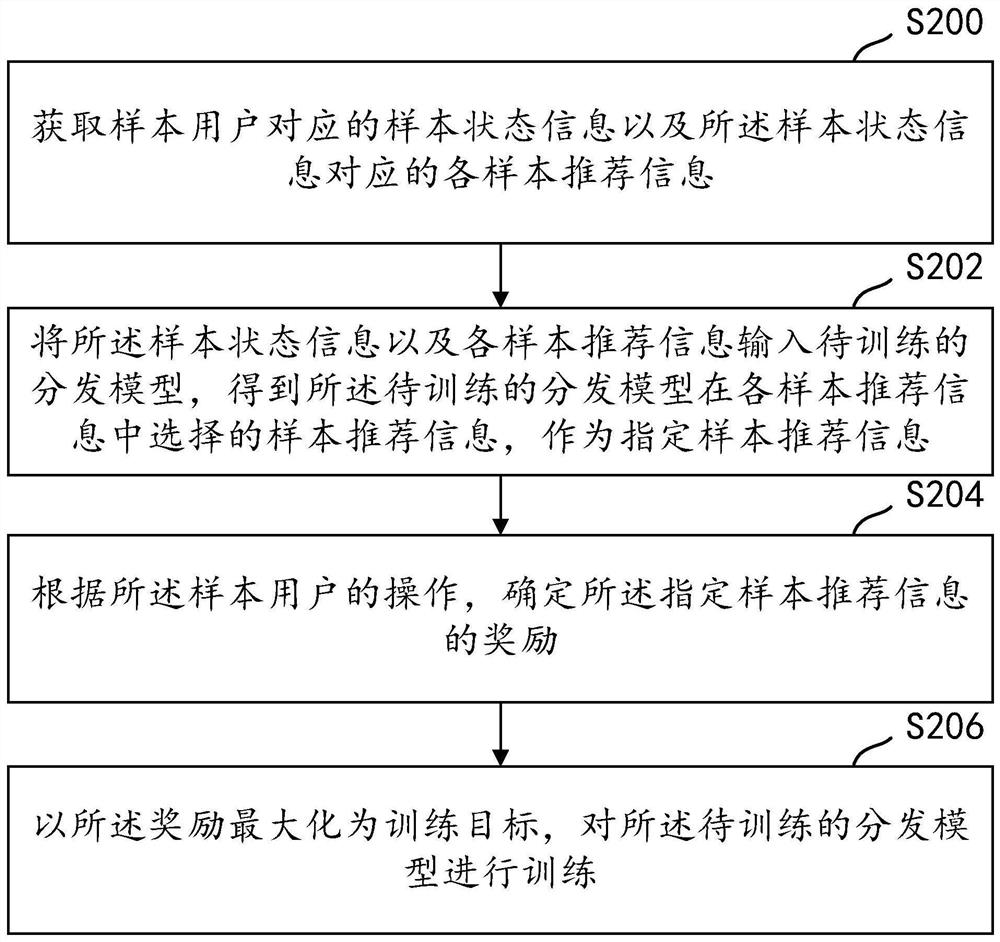
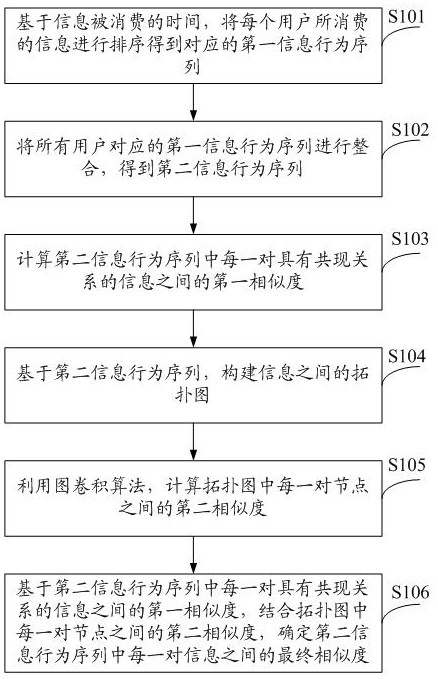
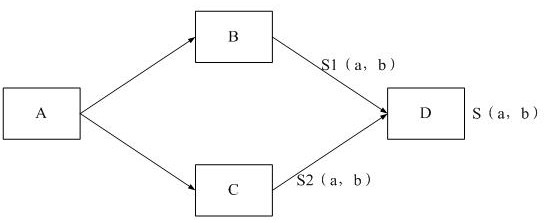
ActiveCN112989211AIncrease the number ofImprove accuracyDigital data information retrievalSpecial data processing applicationsInformation behaviourTopological graph
The invention provides a method and a system for determining information similarity, and the method comprises the steps: sorting the consumed information of each user based on the consumed time of the information, and obtaining a corresponding first information behavior sequence; integrating the first information behavior sequences corresponding to all the users to obtain a second information behavior sequence; calculating a first similarity between each pair of information with a co-occurrence relationship in the second information behavior sequence; constructing a topological graph among the information based on the second information behavior sequence; calculating a second similarity between each pair of nodes in the topological graph by using a graph convolution algorithm; and on the basis of the first similarity between each pair of information with the co-occurrence relationship and in combination with the second similarity between each pair of nodes in the topological graph, determining the final similarity between each pair of information in the second information behavior sequence. The final similarity between the information is calculated in combination with the two modes, the number of information covered by the mode of calculating the similarity is increased, and then the accuracy of information recommendation is improved.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
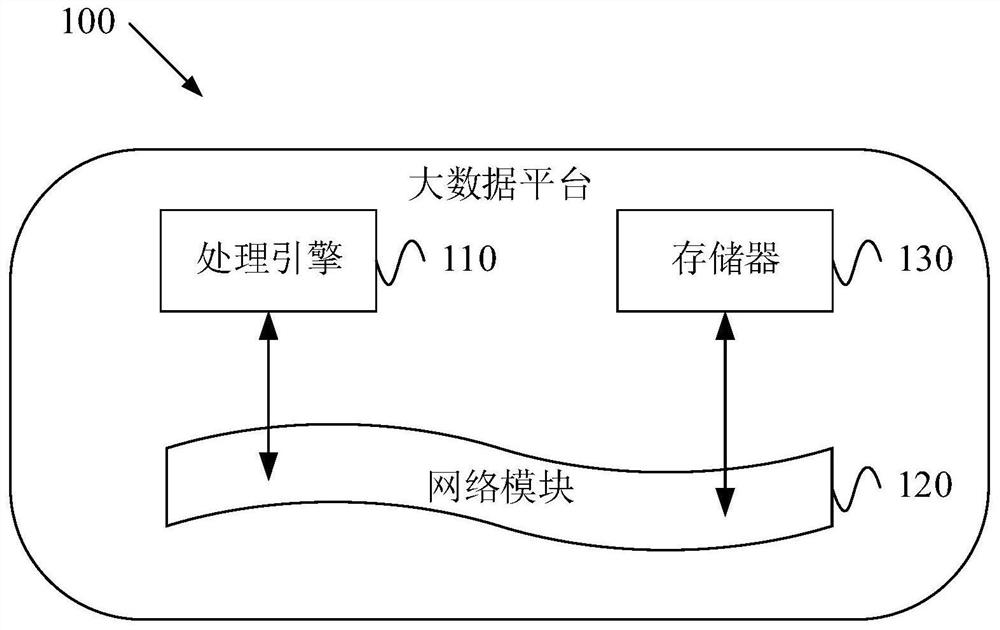
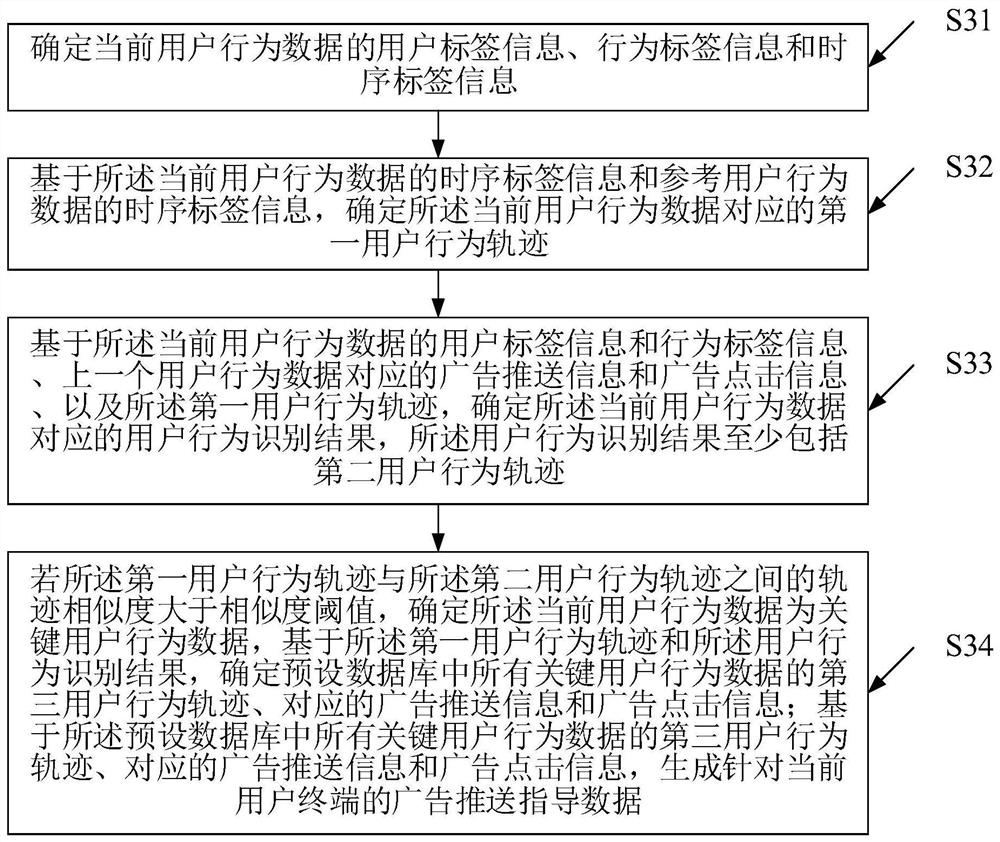
Data processing method based on big data and advertisement pushing and big data platform
ActiveCN112418935AAccurate advertising pushDigital data information retrievalSpecial data processing applicationsPersonalizationInformation behaviour
According to the data processing method based on big data and advertisement pushing and the big data platform, the user label information, the behavior label information and the time sequence label information of the current user behavior data can be analyzed, and the first user behavior track is determined in combination with the reference user data, so as to determine third user behavior tracks,corresponding advertisement pushing information and advertisement clicking information of all key user behavior data in a preset database according to different user behavior data, and finally generate advertisement pushing guidance data for guiding the big data platform to carry out personalized customization of an advertisement pushing target. The advertisement pushing guidance data covers advertisement pushing contents, advertisement pushing time periods, advertisement pushing forms and the like, and deep user behavior data analysis can be performed for each user, so that the advertisementpushing guidance data corresponding to different users in different time periods can be customized in a personalized manner, the pertinence and timeliness of advertisement pushing can be ensured, andaccurate advertisement pushing is realized.
Owner:上海东方财富金融数据服务有限公司
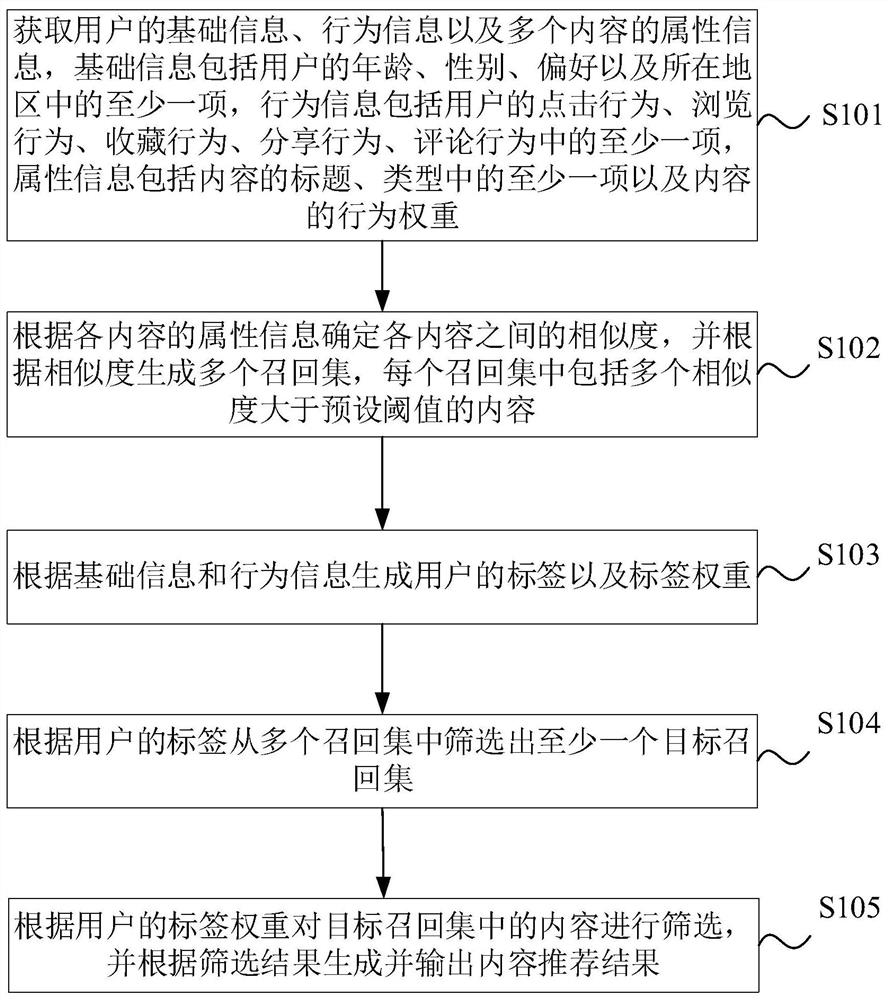
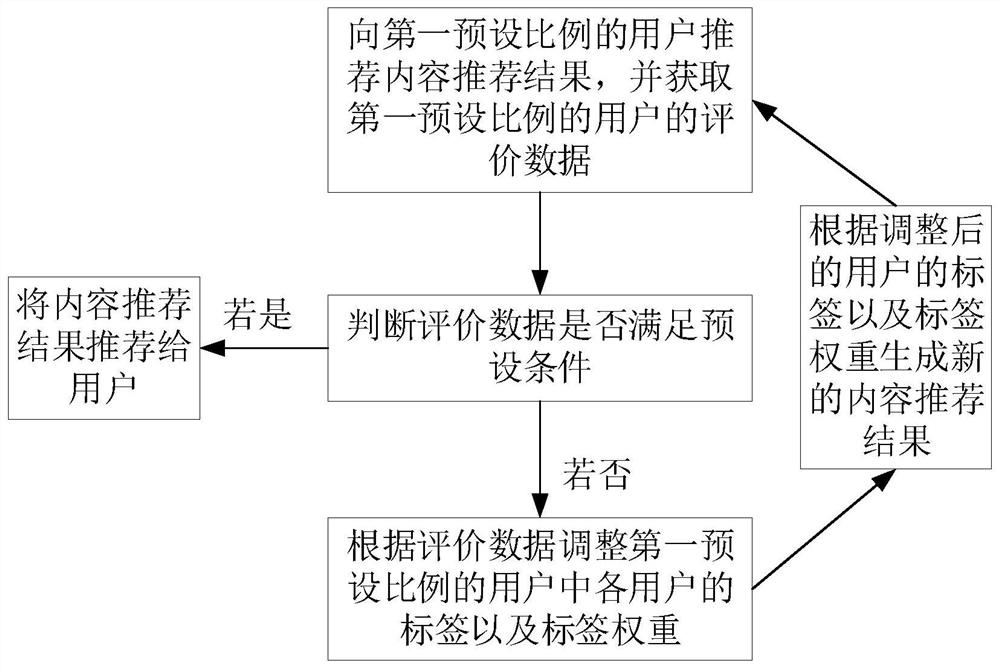
Content recommendation method and device, electronic equipment and storage medium
PendingCN113392329AExtended retention timeImprove accuracyDigital data information retrievalCharacter and pattern recognitionInformation behaviourEngineering
The embodiment of the invention provides a content recommendation method and device, electronic equipment and a storage medium, and relates to the field of data analysis. The method comprises the following steps: acquiring basic information and behavior information of a user and attribute information of a plurality of contents; determining the similarity among the contents according to the attribute information of the contents, and generating a plurality of recall sets according to the similarity, each recall set comprising a plurality of contents of which the similarity is greater than a preset threshold; generating a label and a label weight of the user according to the basic information and the behavior information; screening out at least one target recall set from the plurality of recall sets according to the labels of the users; and screening contents in the target recall set according to the label weight of the user, and generating and outputting a content recommendation result according to a screening result. According to the content recommendation method provided by the embodiment of the invention, the accuracy of recommending the content to the users without clear requirements can be improved, and the retention time of the part of users can be prolonged.
Owner:西安力传智能技术有限公司
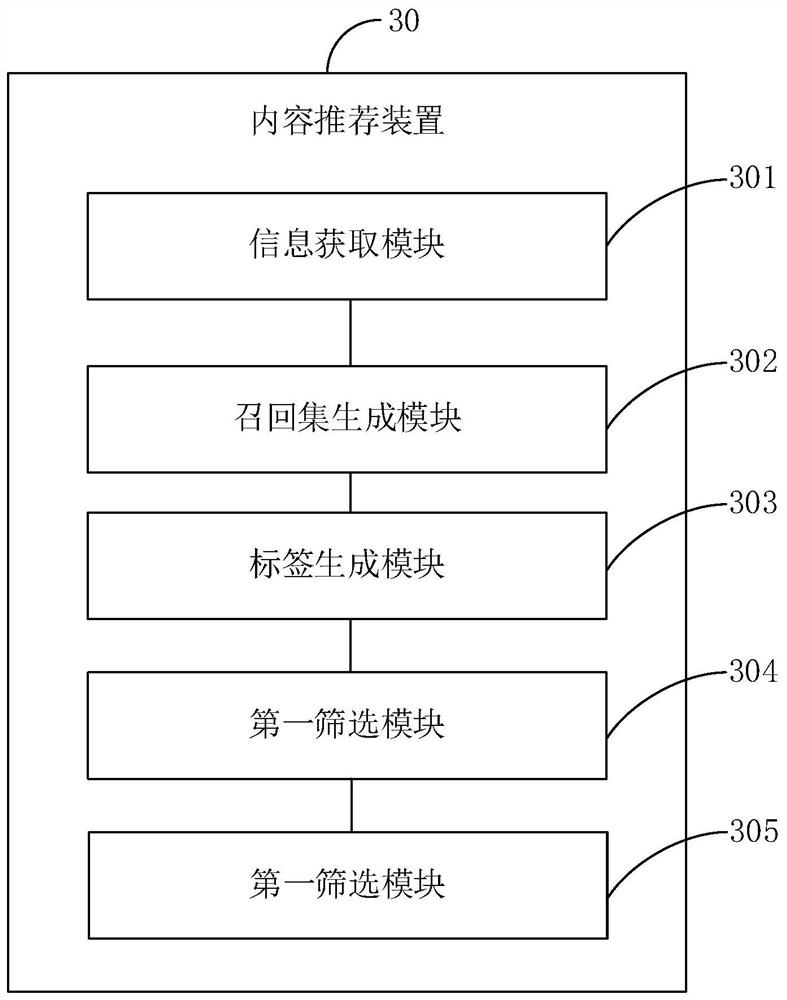
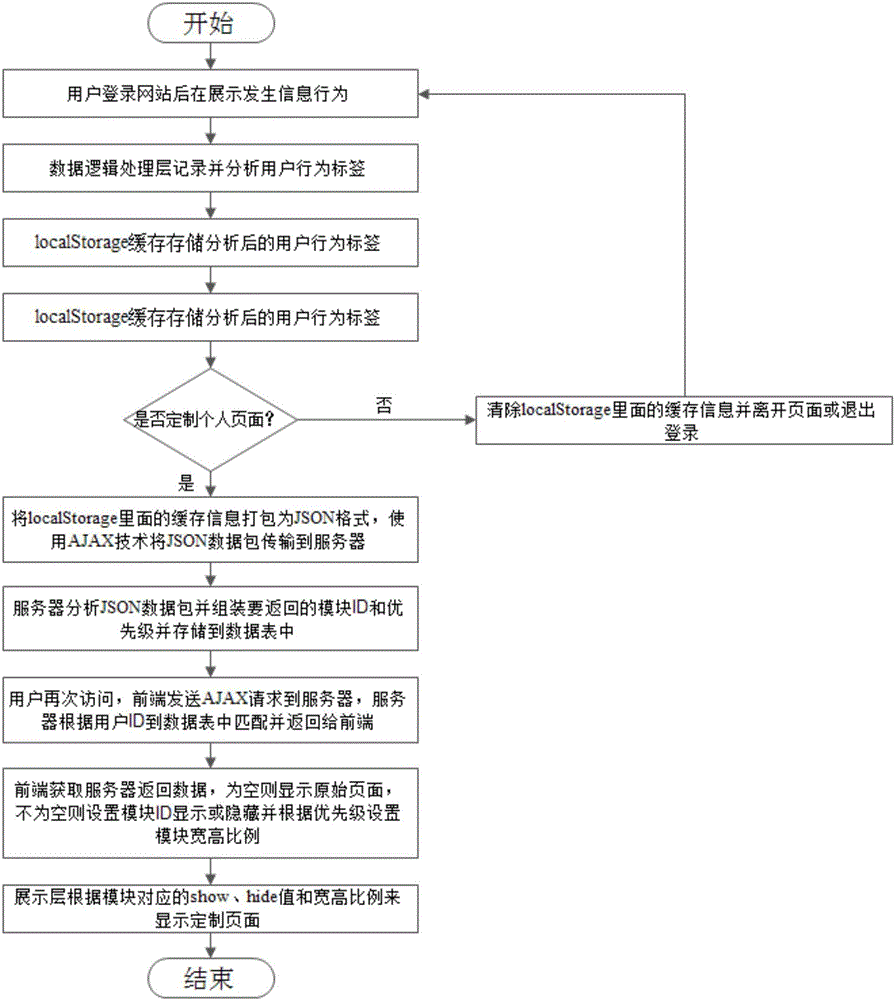
Method for dynamically displaying data at web front end based on user information behavior analysis
ActiveCN107436940AImprove experienceRelieve pressureWebsite content managementSpecial data processing applicationsInformation behaviourModularity
The invention discloses a method for dynamically displaying data at the web front end based on user information behavior analysis. The method comprises the steps that web pages are modularized, and different page module IDs are added to modules respectively; according to the page module ID which a user accesses to and the corresponding information behavior, a server generates the page module ID which needs to be returned after the user logins the page next time and sets the priority of the page module ID, and the page module ID and the priority of the page module ID and the user login ID are stored; under the condition that a user login ID generated when the user accesses to the page next time is matched with the stored user login ID, the page information corresponding to the data is displayed to the user. By means of the method, the information required by the user is displayed in the limited space as far as possible based on the premise that the response speed is not affected, and the user experience is improved.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
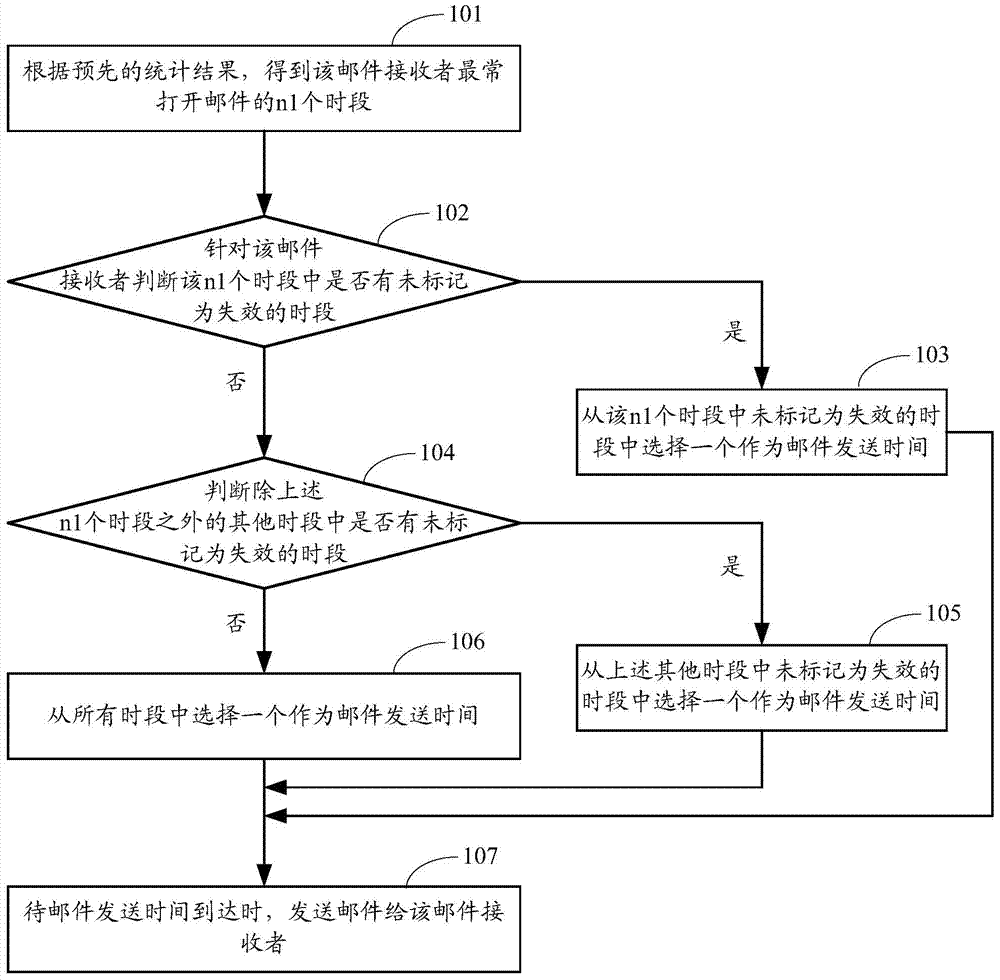
Method and device for determining time for sending information
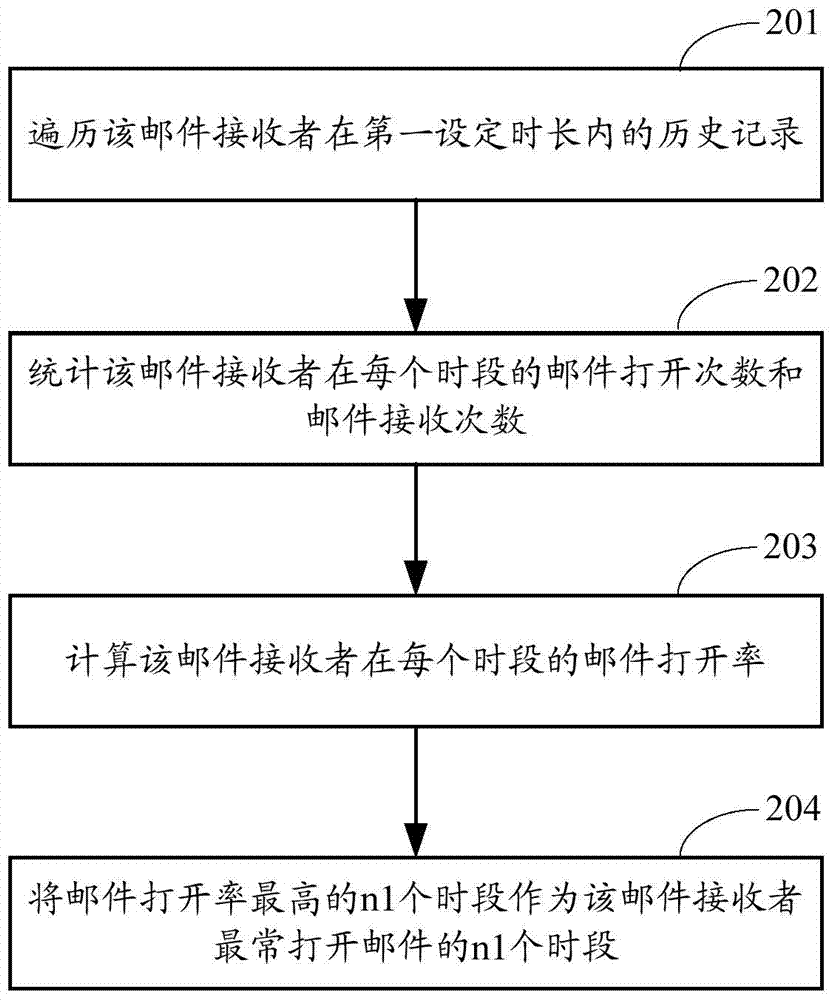
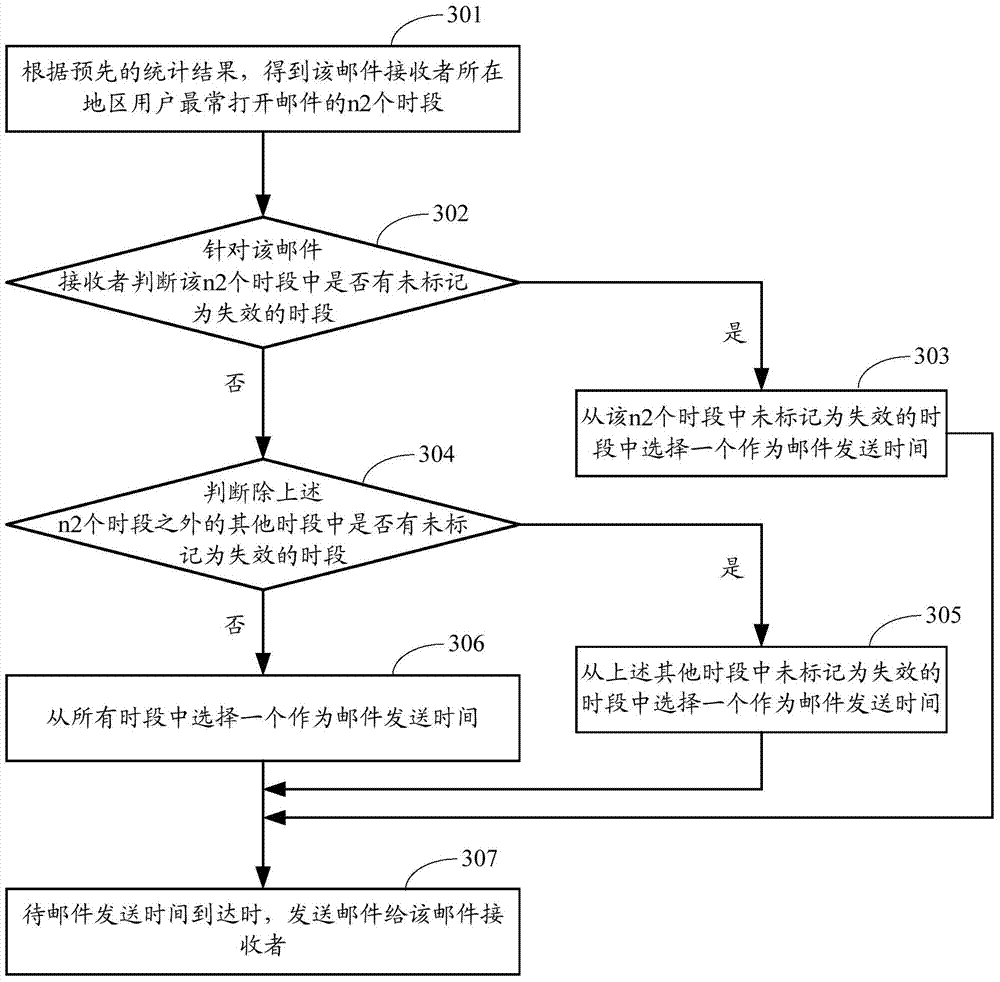
ActiveCN104717120AIncrease the probability of opening a messageData switching networksInstrumentsReal-time computingInformation behaviour
Owner:ALIBABA GRP HLDG LTD
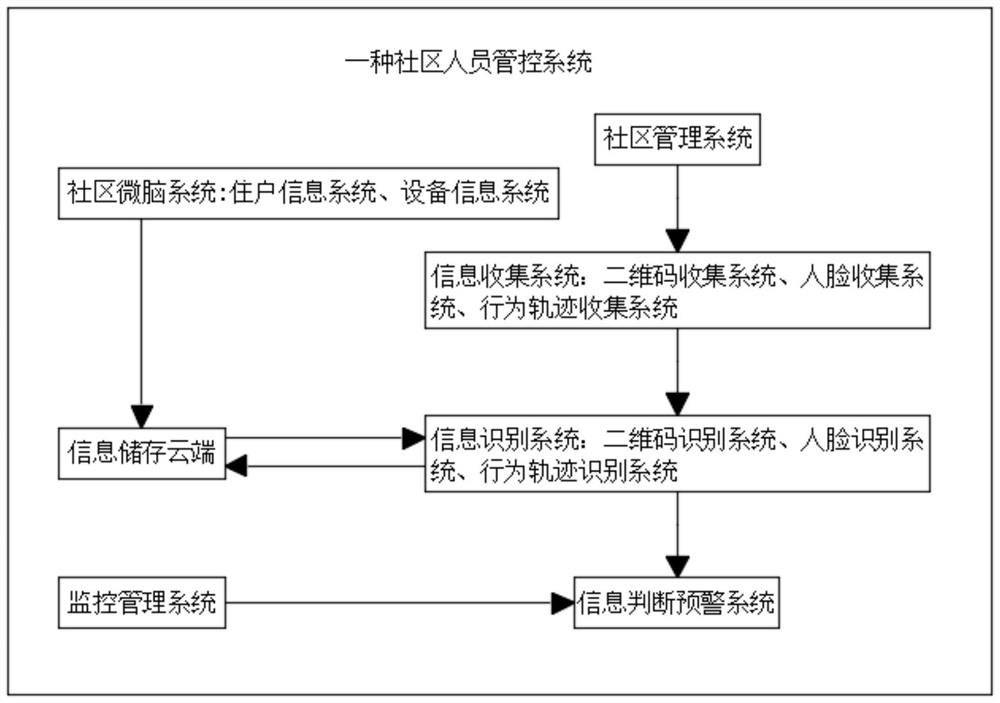
Community personnel management and control system
PendingCN113691637ARealize monitoringRealize managementTelevision system detailsColor television detailsInformation behaviourCollection system
The invention discloses a community personnel management and control system, and particularly relates to the field of community management, the community personnel management and control system comprises a community micro-brain system, a terminal of the community micro-brain system is connected with an information storage cloud, and a terminal of the information storage cloud is connected with a community management system; the community management system comprises an information collection system, an information recognition system and an information judgment early warning system, and a terminal of the information collection system is connected with a terminal of the information recognition system. Compared with the prior art, face information and behavior track information of residents are collected through an access control system and an applet client, the resident information is recognized through the information recognition system, when the recognized resident information is suspicious, the information judgment early warning system gives out early warning and transmits early warning information to a monitoring management platform, so that monitoring and management of a community are conveniently realized, therefore, the convenience of community management is effectively improved, and the community management effect is effectively improved.
Owner:HANGZHOU GUANGMAI TECH
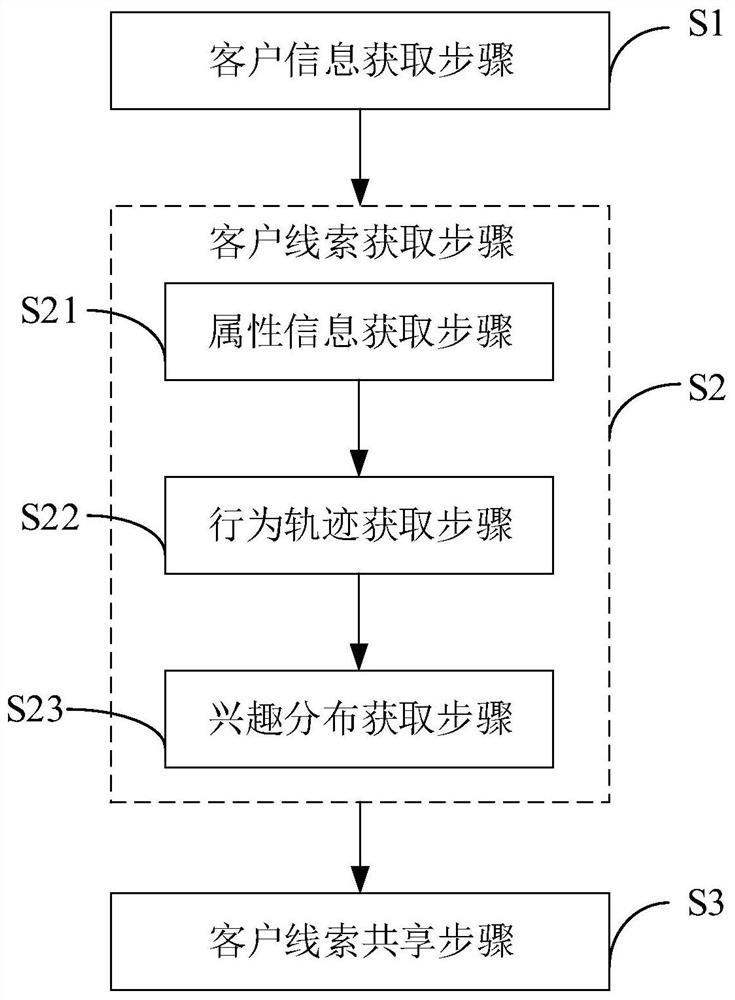
Client clue sharing method and system, computer and readable storage medium
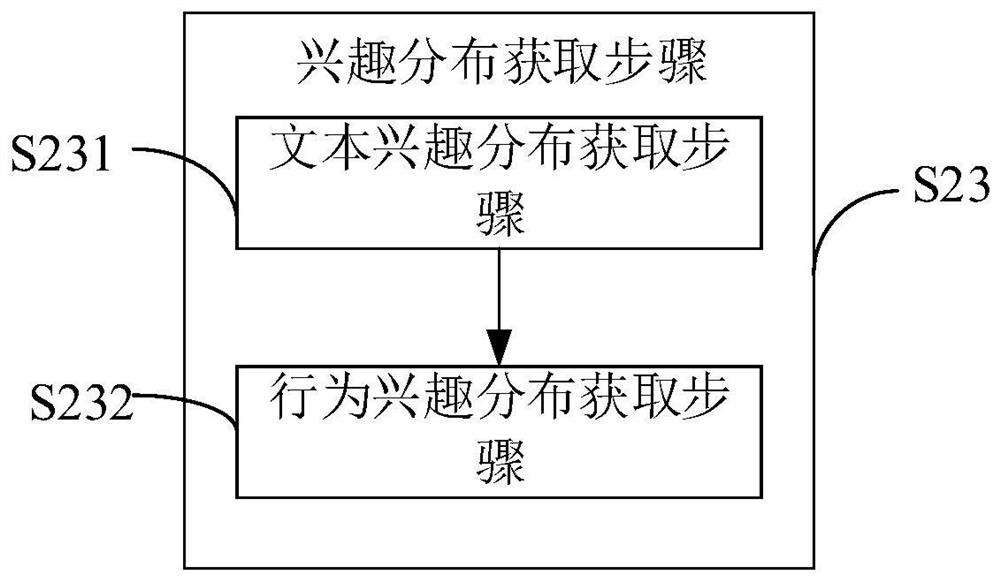
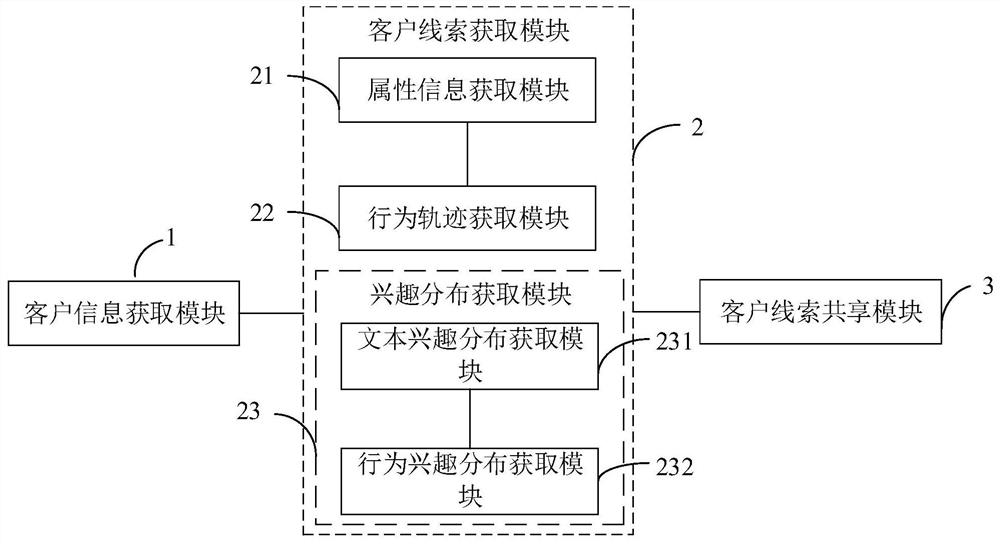
PendingCN112712394AResolve unfamiliar situationsImprove service qualityMarket predictionsData switching networksInformation behaviourComputer network
The invention relates to a client clue sharing method and system, computer equipment and a computer readable storage medium, and the client clue sharing method comprises: a client information obtaining step which is used for obtaining the message data generated by the message dialogue between a client and an exclusive service person, and the role data generated by the execution operation of a client role, and taking same as client information; a client clue obtaining step for extracting a client clue based on the client information, the client clue further comprising attribute information, a behavior track and interest distribution; and a client clue sharing step for pushing and displaying the client clue to the corresponding exclusive service personnel, so that the exclusive service personnel can know the client in real time. According to the invention, the client clues are extracted and shared, so that the problem that service personnel are unfamiliar with clients in the prior art is solved.
Owner:BEIJING MININGLAMP SOFTWARE SYST CO LTD
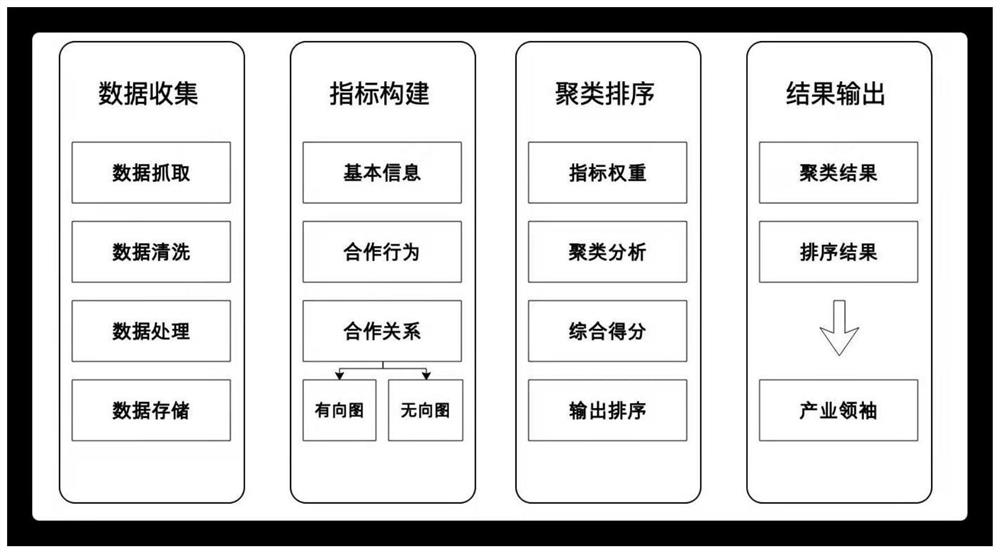
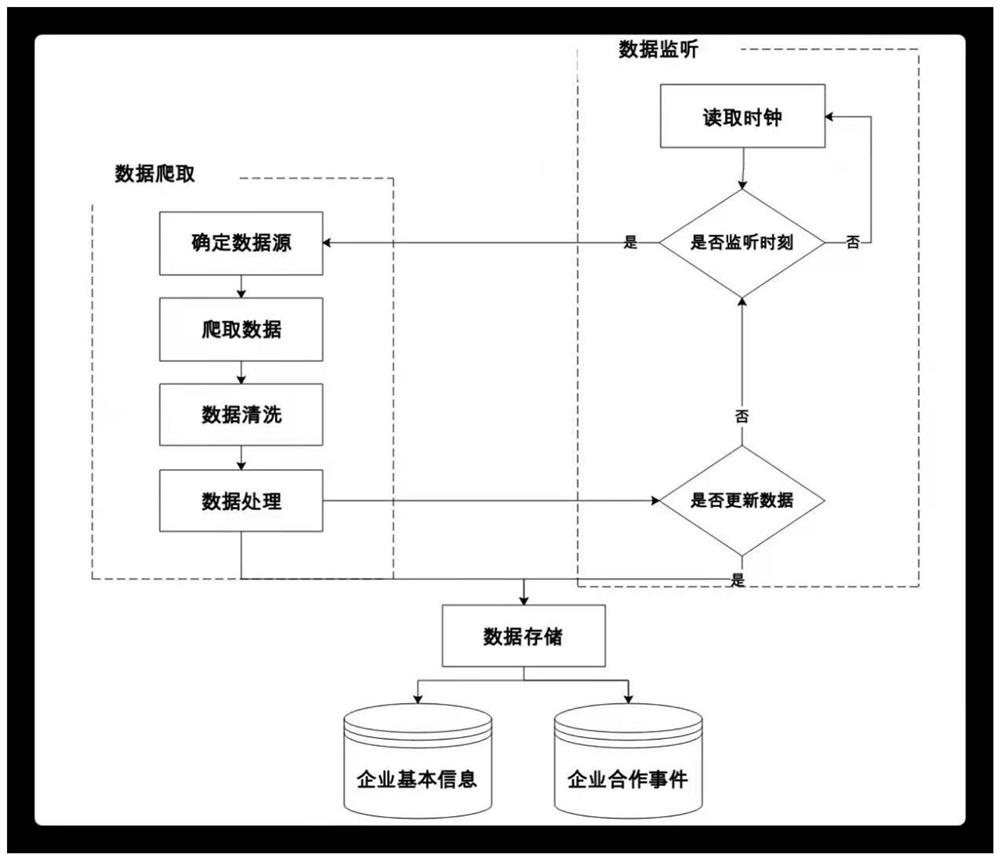
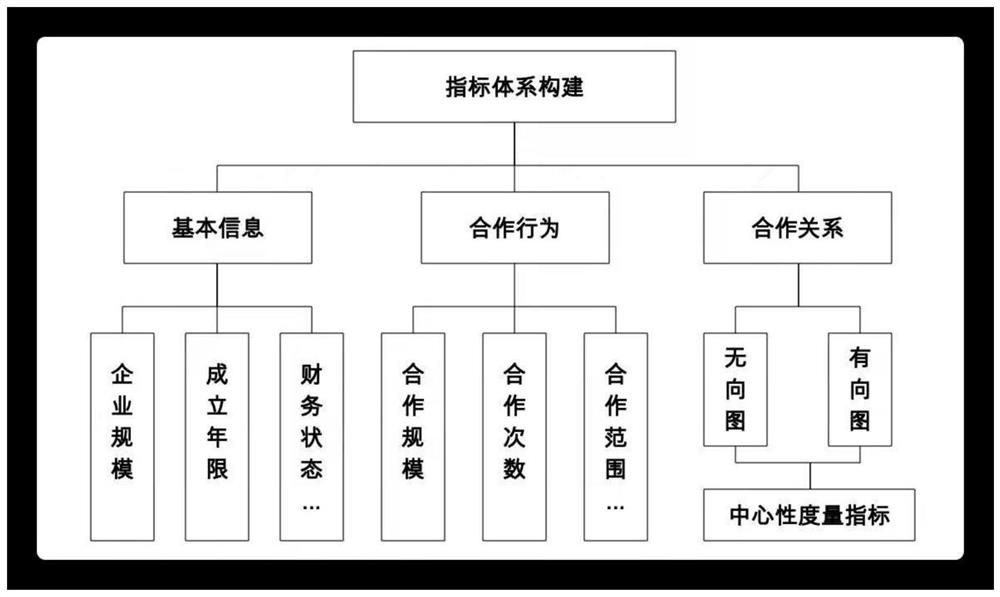
Industrial leader identification method based on clustering and comprehensive evaluation
PendingCN112785156AMeasurement reflects goodImplement sortingDatabase updatingWeb data indexingCluster algorithmInformation behaviour
The invention discloses an industrial leader identification method based on clustering and comprehensive evaluation. The industrial leader identification method comprises a data collection module, an index system construction module, a clustering and sorting module and a result output module. According to the method, indexes describing enterprise experience, scale and business relations are constructed, and an index system for evaluating enterprises is formed; a weighted k-means clustering algorithm and a TOPSIS comprehensive evaluation method are used in a mixed mode, the weight of each index can be automatically estimated in the clustering process, and then the weight is used for calculating the comprehensive score of the enterprise; and finally, descending sorting is performed on the enterprise comprehensive scores, and an industrial leader identification result is output. According to the invention, when the industrial leader is identified, the cooperation relationship among the enterprise basic information, the behavior information and the enterprise is considered, and the industrial leader can be identified more accurately and effectively.
Owner:罗家德 +1
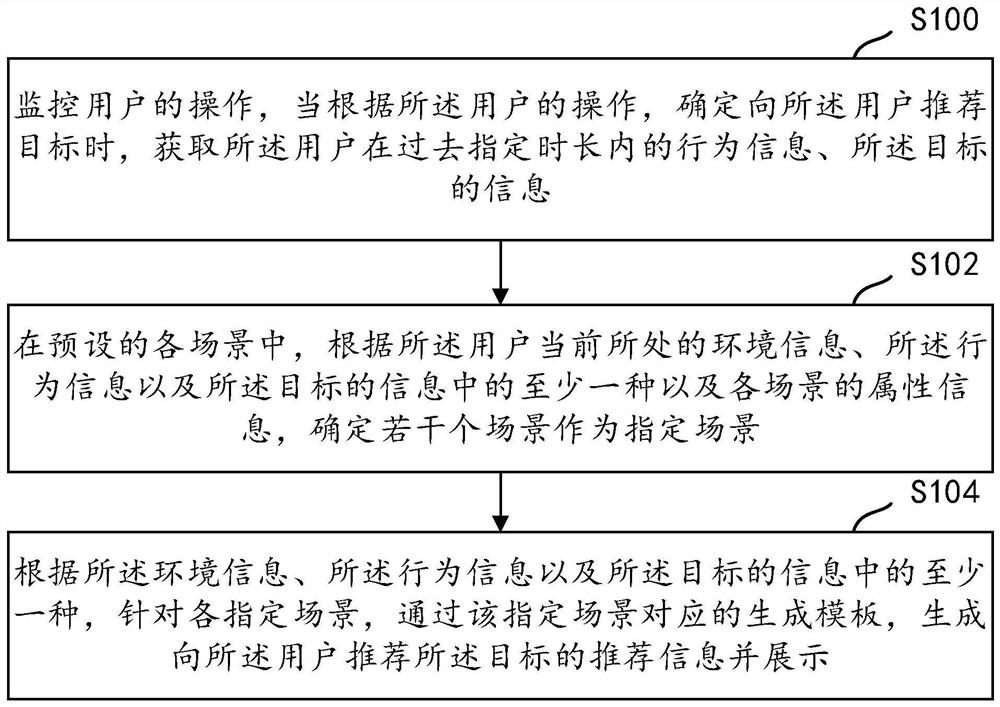
Information generation method and device
PendingCN112699307AMonitor operationDecision supportDigital data information retrievalBuying/selling/leasing transactionsInformation behaviourHuman–computer interaction
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
A method and system for determining information similarity
ActiveCN112989211BIncrease the number ofImprove accuracyDigital data information retrievalSpecial data processing applicationsInformation behaviourTopological graph
The present invention provides a method and system for determining information similarity. Based on the time when information is consumed, the information consumed by each user is sorted to obtain the corresponding first information behavior sequence; the first information behavior sequence corresponding to all users is The sequence is integrated to obtain the second information behavior sequence; calculate the first similarity between each pair of information with a co-occurrence relationship in the second information behavior sequence; based on the second information behavior sequence, construct a topological map between information; use The graph convolution algorithm calculates the second similarity between each pair of nodes in the topological graph; based on the first similarity between each pair of information with a co-occurrence relationship, combined with the second similarity between each pair of nodes in the topological graph The second similarity is to determine the final similarity between each pair of information in the second information behavior sequence. Combine the two methods to calculate the final similarity between information, increase the amount of information covered by the method of calculating similarity, and then improve the accuracy of information recommendation.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
Overdue risk identification method based on robust algorithm
ActiveCN111899091ASolve the problem that the independent and identical distribution condition is not satisfiedImprove accuracyFinanceForecastingInformation behaviourRobustification
The invention discloses an overdue risk identification method based on a robust algorithm. The method comprises the steps: obtaining basic information of a user and multi-dimensional behavior data, and generating basic information behavior data ; and modeling the basic information behavior data by using a loss function of a robust algorithm to generate model data. According to the method, the problem that in the prior art, independent identical distribution conditions are not met due to the fact that sample distribution is damaged can be solved, and the recognition accuracy and robustness canbe improved. Compared with the prior art, the method has the following advantages and positive technical effects: 1, the anti-interference performance and robustness of the algorithm are effectively improved by using the minimum and maximum game theory; 2, compared with a traditional method based on down-sampling or up-sampling, the model has higher precision; and 3, original sample distribution is well described, and the situation of sample imbalance or sample non-independent same distribution can be effectively handled;
Owner:HUA DATA TECH (SHANGHAI) CO LTD
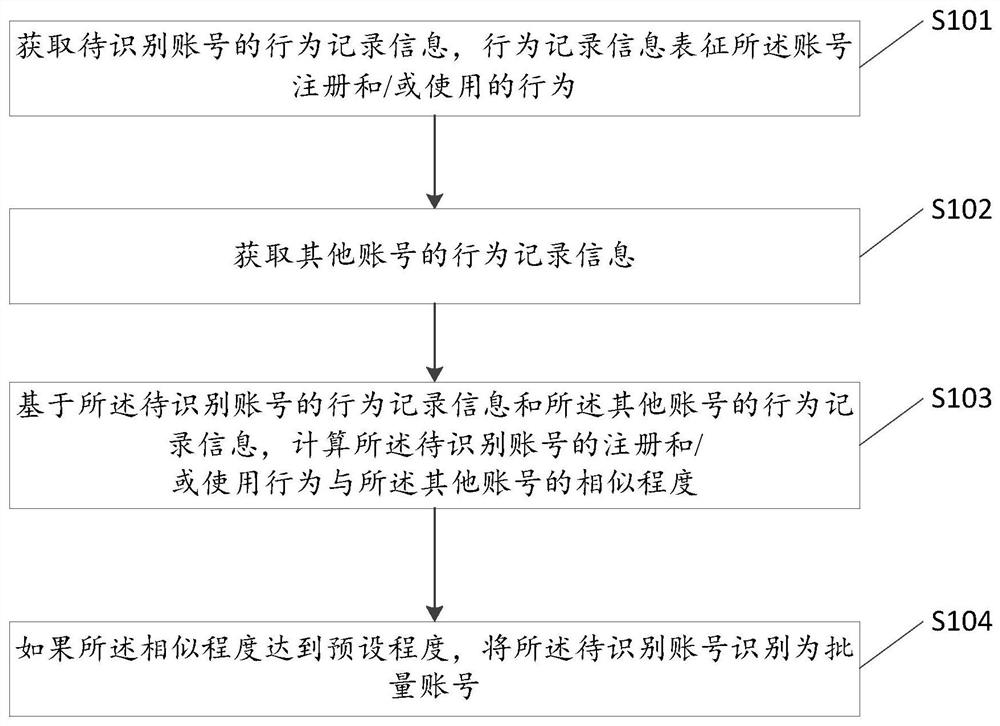
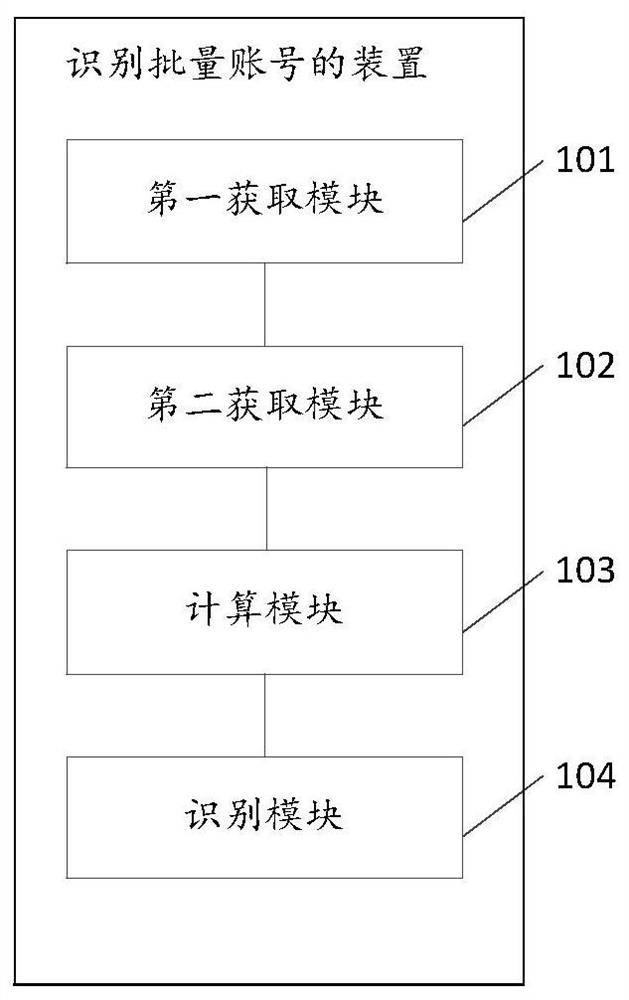
A method and device for identifying batch accounts
Embodiments of the present invention provide a method and device for identifying batch accounts, at least for solving the technical problem of identifying batch accounts. The method includes: obtaining behavior record information of the account to be identified, which represents the registration and / or use behavior of the account; obtaining behavior record information of other accounts; based on the behavior record information of the account to be identified and the Behavior record information of other accounts, calculating the degree of similarity between the registration and / or usage behavior of the account to be identified and the other accounts; if the degree of similarity reaches a preset level, identify the account to be identified as a batch account.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
A data flow type recognition model update method and related equipment
ActiveCN111404833BThe recognition effect is accurateImprove efficiencyKernel methodsTransmissionData packInformation behaviour
The embodiment of the present application provides a method for updating a data flow type identification model and related equipment, the method includes: determining the first data flow type corresponding to the current data flow according to the packet information and the behavior recognition model of the current data flow; The relationship and the general characteristics of the current data flow determine the second data flow type corresponding to the current data flow, wherein the target correspondence is the correspondence between multiple general characteristics and multiple data flow types; if the first data flow corresponding to the current data flow If the type is different from the type of the second data stream corresponding to the current data stream, the correction data corresponding to the current data stream is obtained, wherein the correction data corresponding to the current data stream includes the message information of the current data stream and the second data corresponding to the current data stream Stream type, the correction data is used as training samples to update the behavior recognition model. This way of obtaining training samples for updating the action recognition model is more efficient.
Owner:HUAWEI TECH CO LTD
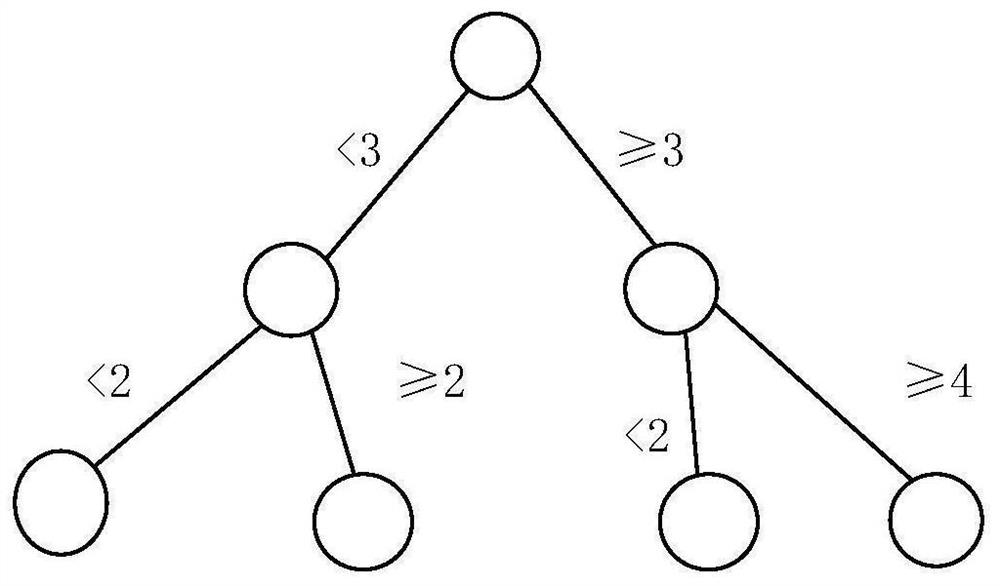
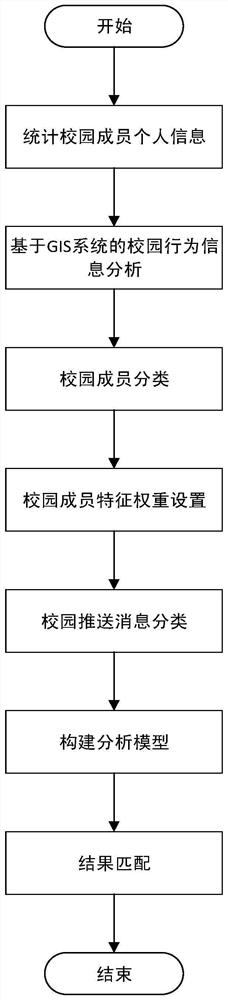
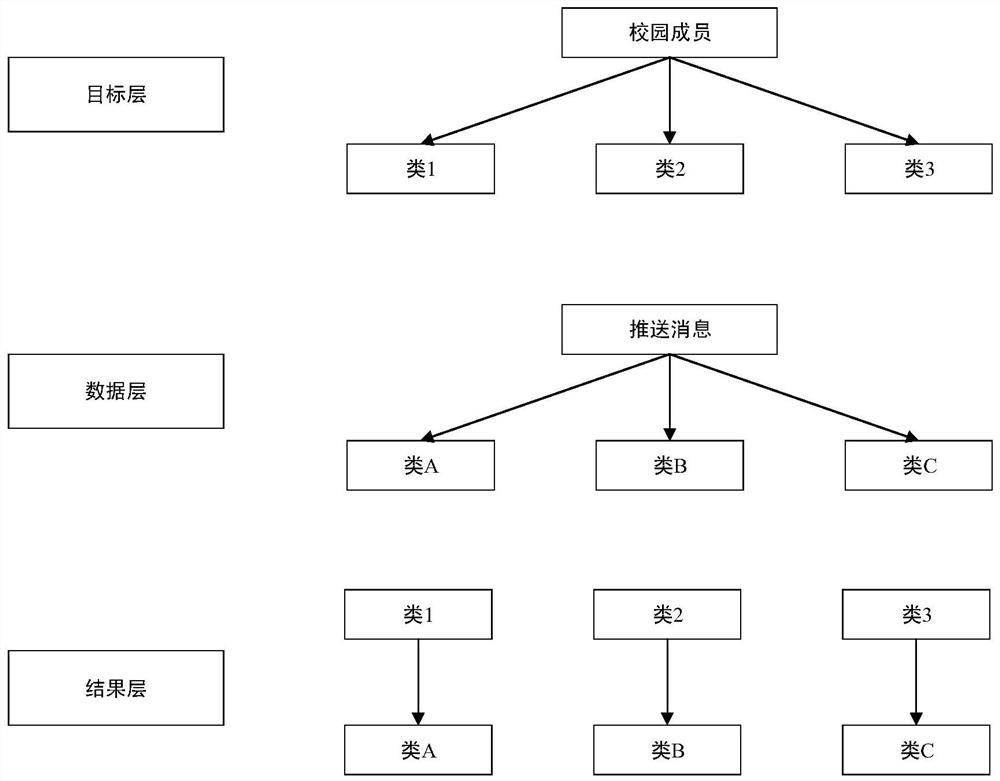
An optimization method for campus message push based on gis system
ActiveCN109347903BImprove acquisition efficiencyImprove push qualityDigital data information retrievalData switching networksInformation behaviourOperations research
A campus message push optimization method based on GIS system. First, according to the personal information of campus members, the decision tree classification algorithm is used to classify members into corresponding groups, and then based on the GIS system, the campus information behavior of campus members is counted, and the characteristics are classified and given. Each feature is given a certain weight, and then the redundant information in the campus push messages is removed through big data technology, and the classification results are classified according to the characteristics of campus members, and then an analysis model is constructed. Finally, different campus members are classified according to the weight and interest characteristics. Push different messages. The present invention can meet the push message requirements of different campus members.
Owner:ZHEJIANG UNIV OF TECH
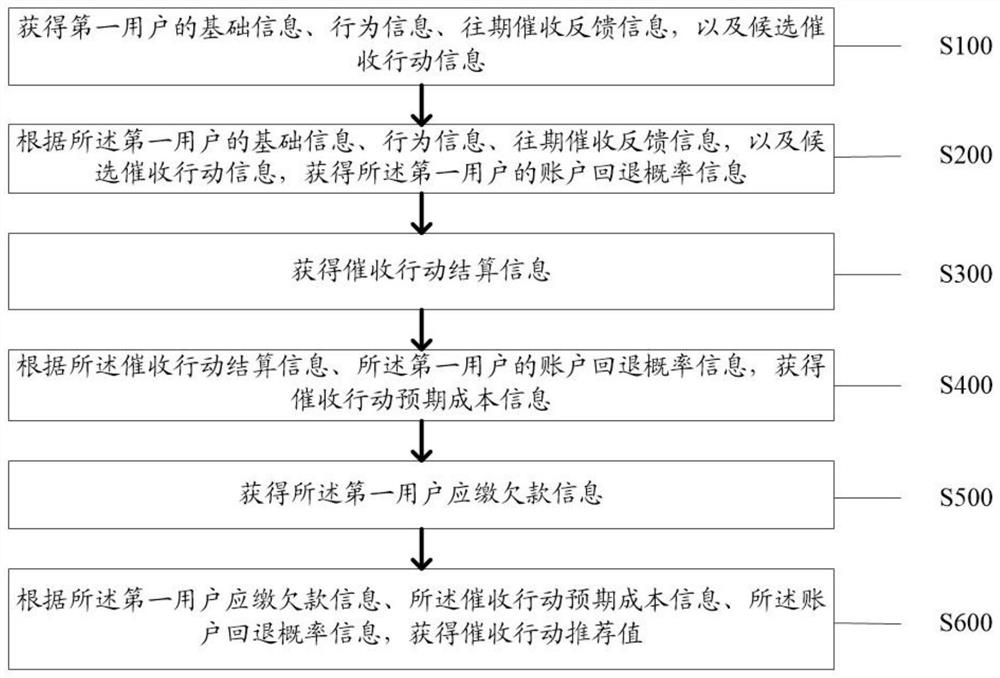
Collection action recommendation method and device
ActiveCN112785419AAccurately evaluate recommendationsFinanceCharacter and pattern recognitionInformation behaviourEngineering
The invention discloses a collection action recommendation method and device. The method comprises: obtaining basic information, behavior information, previous collection feedback information and candidate collection action information of a first user; acquiring account rollback probability information of the first user according to the basic information, the behavior information, the previous collection feedback information and the candidate collection action information of the first user; acquiring collection action settlement information; acquiring expected cost information of the collection action according to the settlement information of the collection action and the account rollback probability information of the first user; obtaining the debt information that the first user should pay; and obtaining a collection action recommendation value according to the first user payable debt information, the collection action expected cost information and the account rollback probability information. The technical problem that the feasibility of the collection action cannot be accurately evaluated in the prior art is solved, and the technical effect of accurately evaluating and recommending the collection action is achieved.
Owner:CHINA CITIC BANK
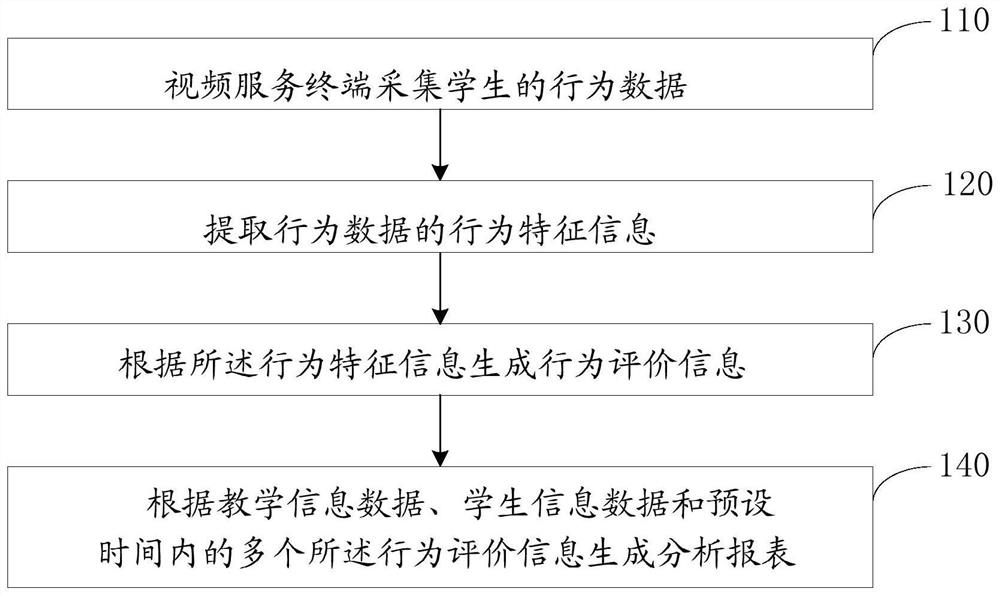
Classroom data processing method
PendingCN114358573ARealize real-time trackingCharacter and pattern recognitionResourcesInformation behaviourMood
The invention relates to a classroom data processing method. The method comprises the steps that a video service terminal collects behavior data of students; extracting behavior feature information of the behavior data; generating behavior evaluation information according to the behavior feature information; the behavior evaluation information comprises mental state evaluation information, emotional state evaluation information, learning state evaluation information and interpersonal relationship evaluation information; generating an analysis report according to the teaching information data, the student information data and the multiple pieces of behavior evaluation information within the preset time; the student information data comprises student IDs; the analysis report comprises a comprehensive literacy evaluation report, a campus safety early warning report and a teaching quality evaluation report. According to the classroom data processing method, the behavior data of the students at the school are continuously collected for a long time, so that comprehensive literacy, academic conditions and emotions of the students are comprehensively tracked in real time, and the teaching quality of teachers is tracked in real time.
Owner:北京碧云数创科技有限公司
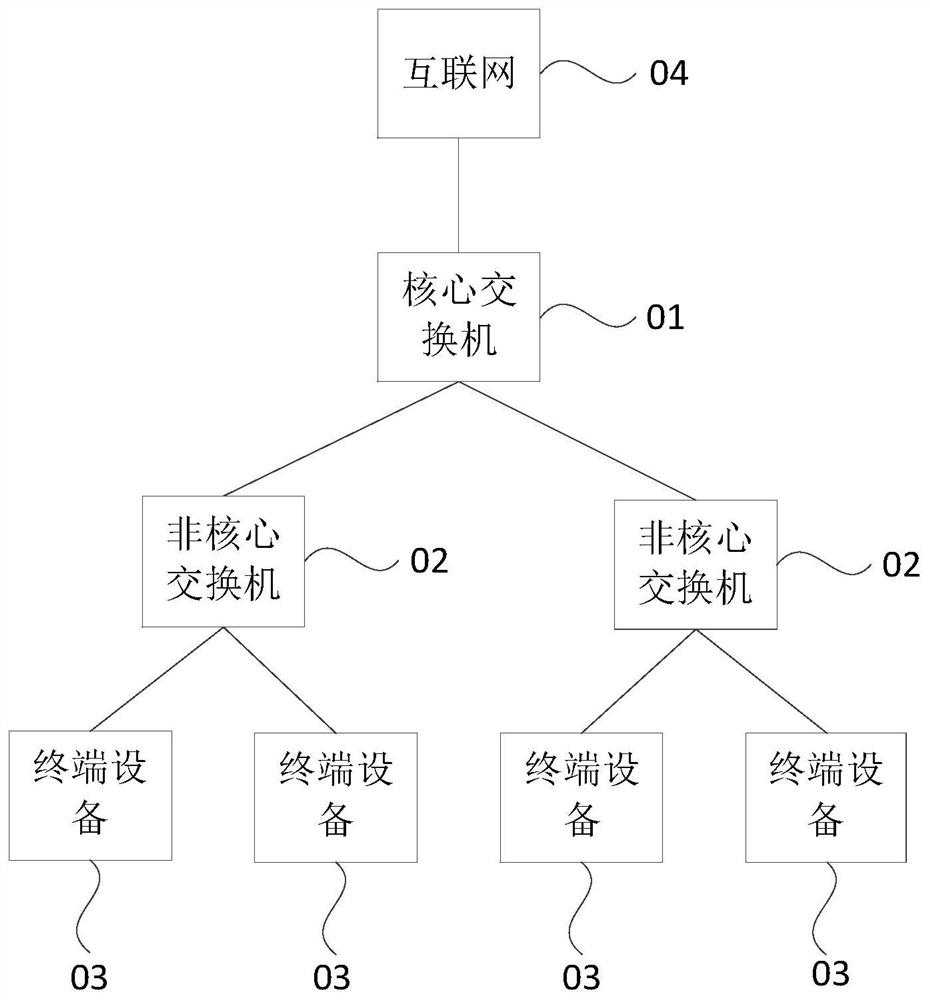
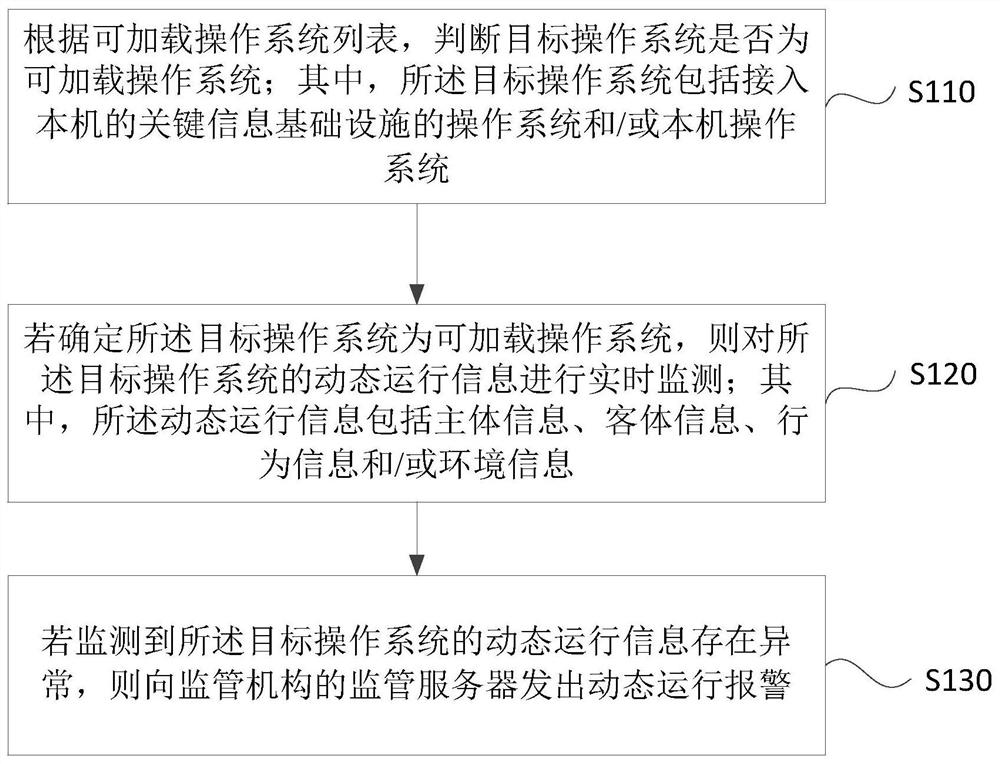
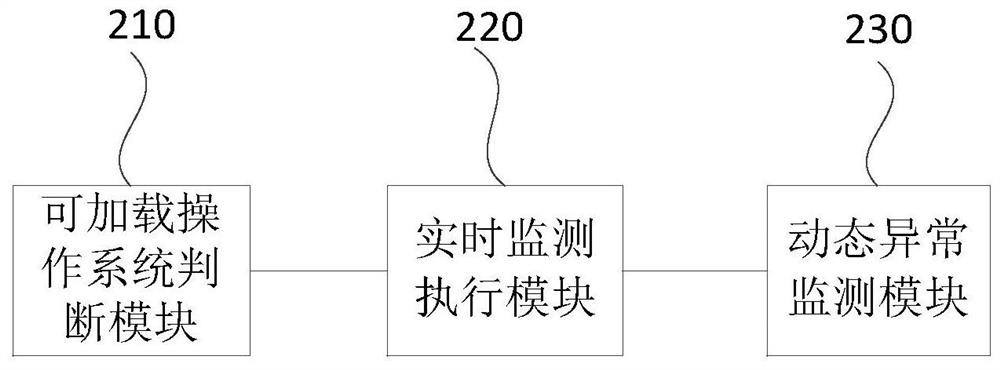
Key information infrastructure abnormity monitoring method and device
The embodiment of the invention discloses a key information infrastructure abnormity monitoring method and device, electronic equipment and a storage medium, and the method comprises the steps: judging whether a target operating system is a loadable operating system or not according to a loadable operating system list, wherein the target operating system comprises an operating system accessing a key information infrastructure of a local machine and / or a local operating system; if yes, monitoring the dynamic operation information of the target operation system in real time, wherein the dynamic operation information comprises subject information, object information, behavior information and / or environment information; and if it is monitored that the dynamic operation information of the target operating system is abnormal, sending a dynamic operation alarm to a supervision server of a supervision mechanism. According to the technical scheme provided by the embodiment of the invention, the dynamic operation information in the key information infrastructure is effectively monitored, and meanwhile, the communication connection with the supervision server of the supervision mechanism is established, so that the supervision mechanism can obtain the abnormal state of each key information infrastructure in time.
Owner:EVERSEC BEIJING TECH
Campus Management System and Method
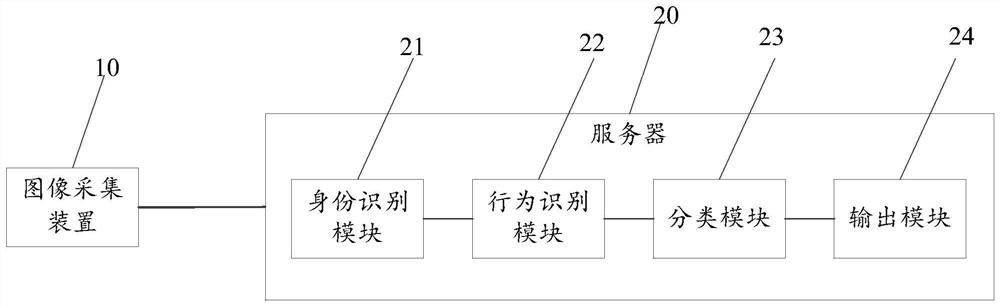
ActiveCN110502999BEfficient acquisitionCharacter and pattern recognitionResourcesInformation behaviourIdentity recognition
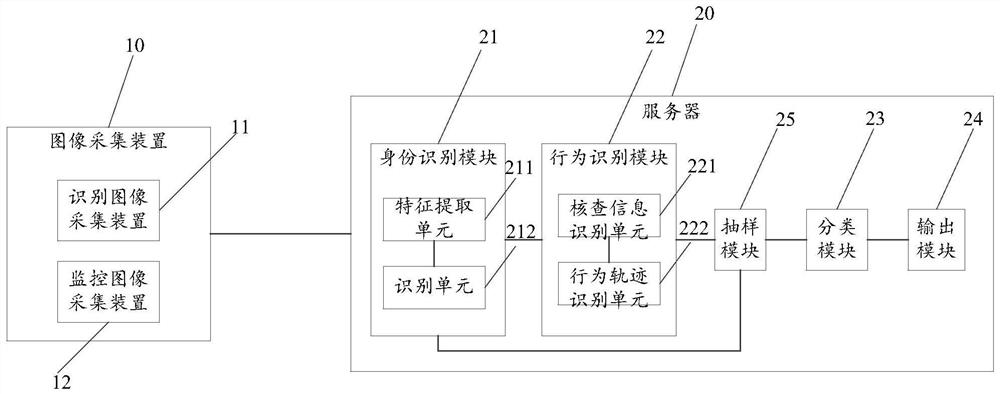
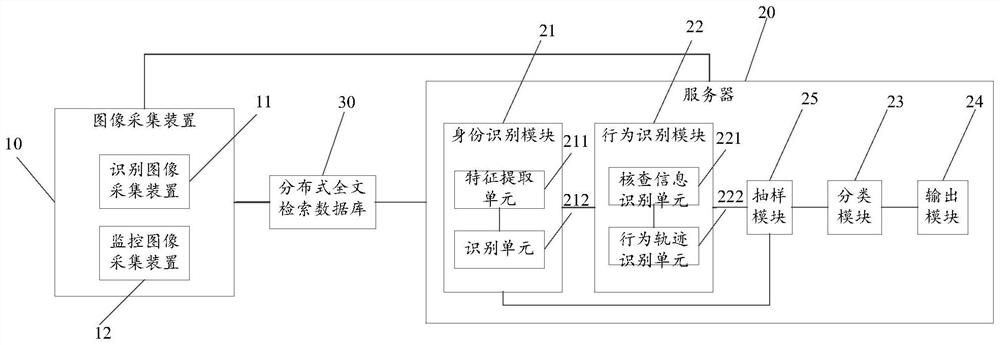
The invention discloses a campus management system and method, comprising: an image acquisition device for acquiring image information of school personnel; a server comprising: an identity identification module storing a trained first artificial intelligence model for identifying the image information, Obtain the identity information of the school personnel; the behavior recognition module identifies the behavior data of the school personnel according to the image information and the identity information of the school personnel; the classification module stores the trained second artificial intelligence model, and uses the school personnel identity information and the school personnel The personnel behavior data classifies the school personnel; the output module outputs the corresponding management strategy according to the classification results. Through the combination of artificial intelligence technology, the real, reliable, real-time and efficient acquisition of the behavior data of school personnel is carried out; the situation of students in school is classified through artificial intelligence technology, and data support is provided for the improvement of teaching quality and campus security, so that the campus management strategy is aimed at School staff to formulate and implement reasonably and accurately.
Owner:北京华三通信技术有限公司
Identity authentication anti-fraud method and system based on intelligent voice
InactiveCN113781059AImprove accuracyProtection securityFinanceProtocol authorisationInformation behaviourEngineering
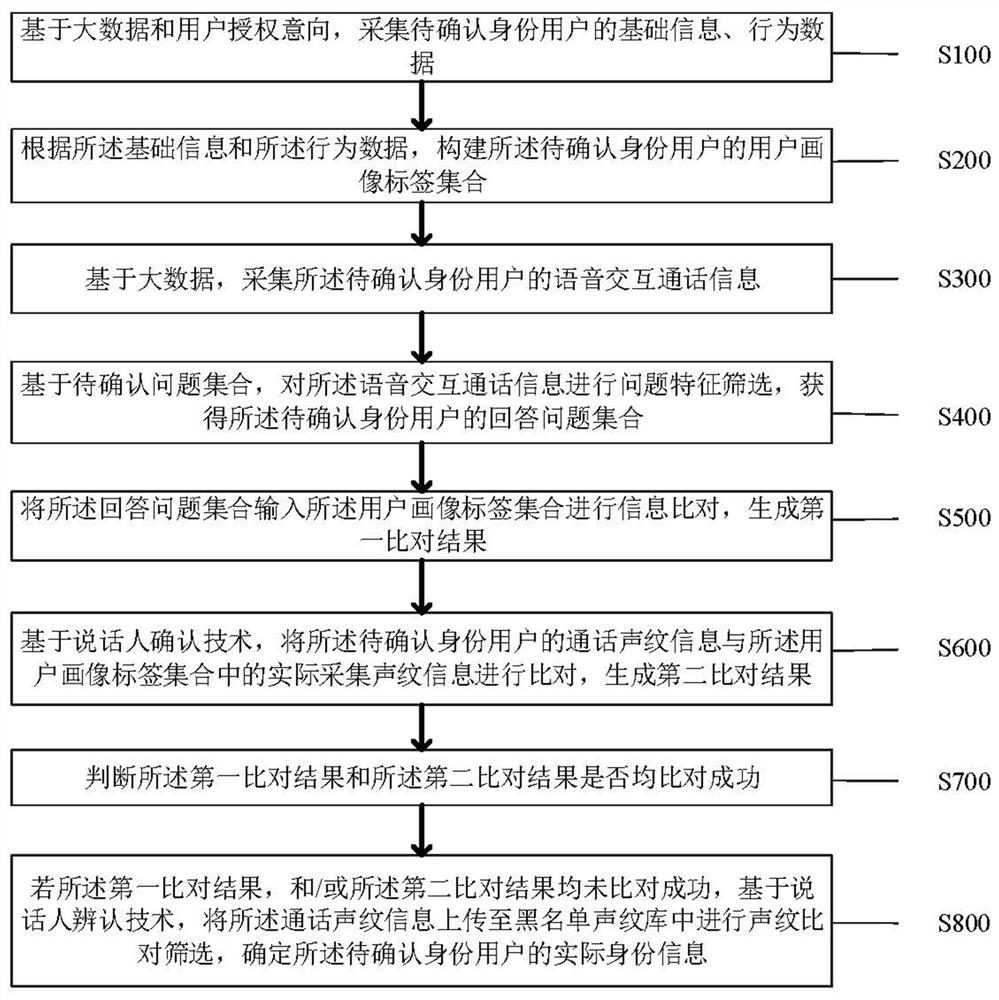
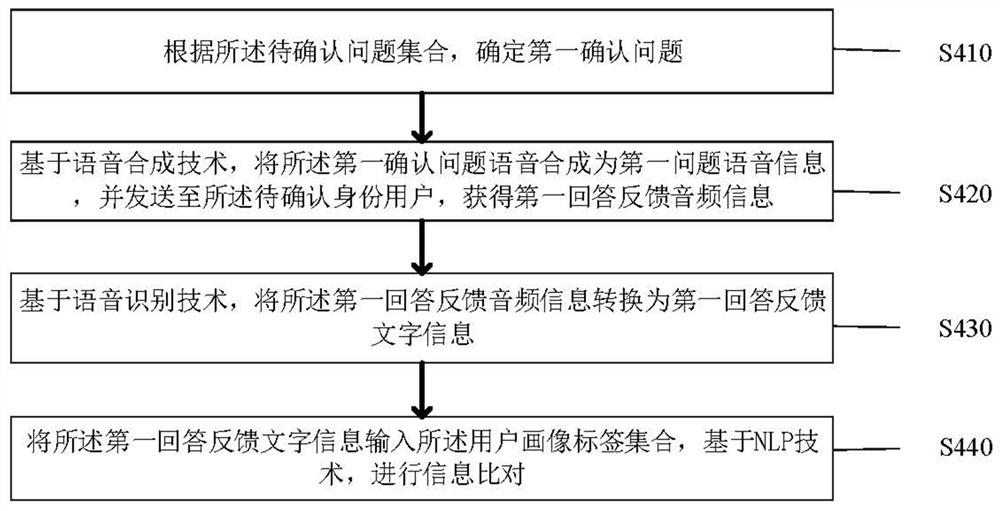
The invention provides an identity authentication anti-fraud method and system based on intelligent voice. The method comprises the steps of: collecting basic information and behavior data of a user with a to-be-confirmed identity; constructing a user portrait label set; collecting voice interaction call information; performing question feature screening to obtain an answer question set of the user with the to-be-confirmed identity; generating a first comparison result; generating a second comparison result; judging whether the first comparison result and the second comparison result are successfully compared or not; and if the first comparison result and / or the second comparison result are / is not successfully compared, uploading call voiceprint information to a blacklist voiceprint library for voiceprint comparison and screening, and determining the actual identity information of the user with the to-be-confirmed identity. The identity authentication anti-fraud method and system solve the technical problems that in the prior art, identity authentication depends on manpower and a single AI technology, the subjectivity of manual judgment is too high, the fraud confirmation accuracy of the single AI technology is not high, and scientificity is poor.
Owner:百融至信(北京)征信有限公司
User behavior data analysis system capable of distinguishing clients by labels
PendingCN113609270AIncrease diversityHigh precisionAdvertisementsData miningInformation behaviourEngineering
The invention relates to the technical field of network information, and discloses a user behavior data analysis system capable of distinguishing clients by labels, which comprises the following steps: S1, performing social investigation: determining a target APP, then carrying out random user investigation, and collecting basic information and preference characteristics of users in a questionnaire form; S2, performing information collection: collecting user information of the target APP, the user information including population attributes, credit information and behavior characteristics; and S3, constructing a label library. According to different labels, favorite information contents are pushed to different users, the operation intentions of the users are deeply analyzed, the requirements of the users on the market are quickly known in advance, the users are distinguished by using the labels, the information is accurately pushed, and the information pushing effect can be known through precision inspection, so that problems are found and solved. And a user behavior analysis system is perfected.
Owner:南京西桥科技有限公司
A device and technology for reading life cycle information of OFD format files
ActiveCN112862425BImprove reading efficiencyEfficient accessOffice automationExecution paradigmsInformation behaviourSoftware engineering
The invention discloses a device and technology for reading life cycle information of OFD format files. The invention directly reads the binary flow content in the OFD format file through the decompression technology, and obtains the life cycle file in the OFD format file through step-by-step searching. The method of the present invention enables people not only to read the content of the OFD file itself, but also to effectively consult the life cycle information of the OFD format file through the device and technology; to directly read the binary stream content in the OFD format file through the decompression technology, and to Effectively omit the process and time of decompressing to a temporary directory, and improve the reading efficiency of OFD format files. Regardless of whether the file is in the application environment or after it leaves the application environment, you can quickly and efficiently see the main process information and behavior information of its life cycle in the original application system.
Owner:JIANGSU ZHONGWEI TECH SOFTWARE SYST
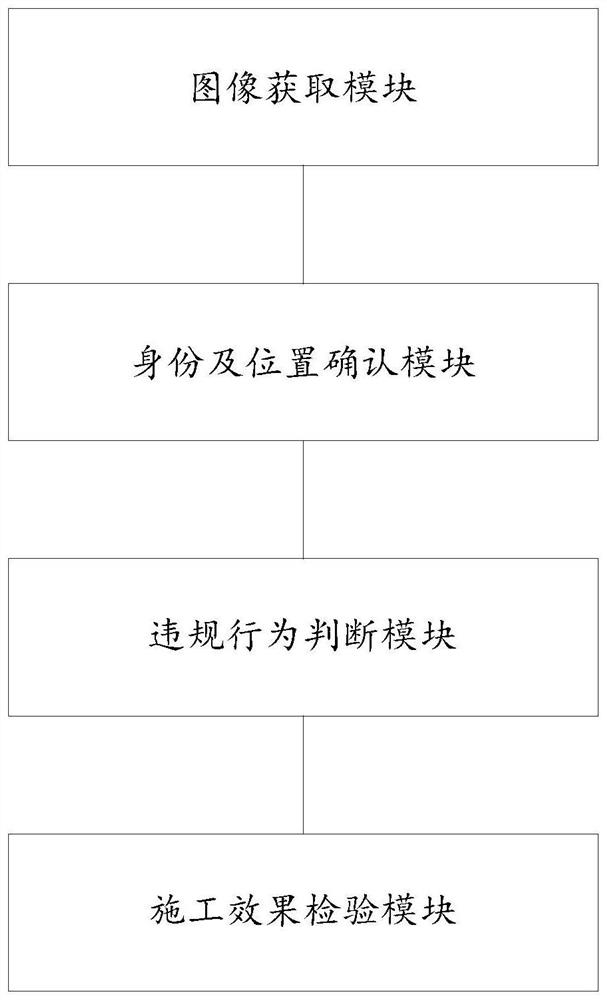
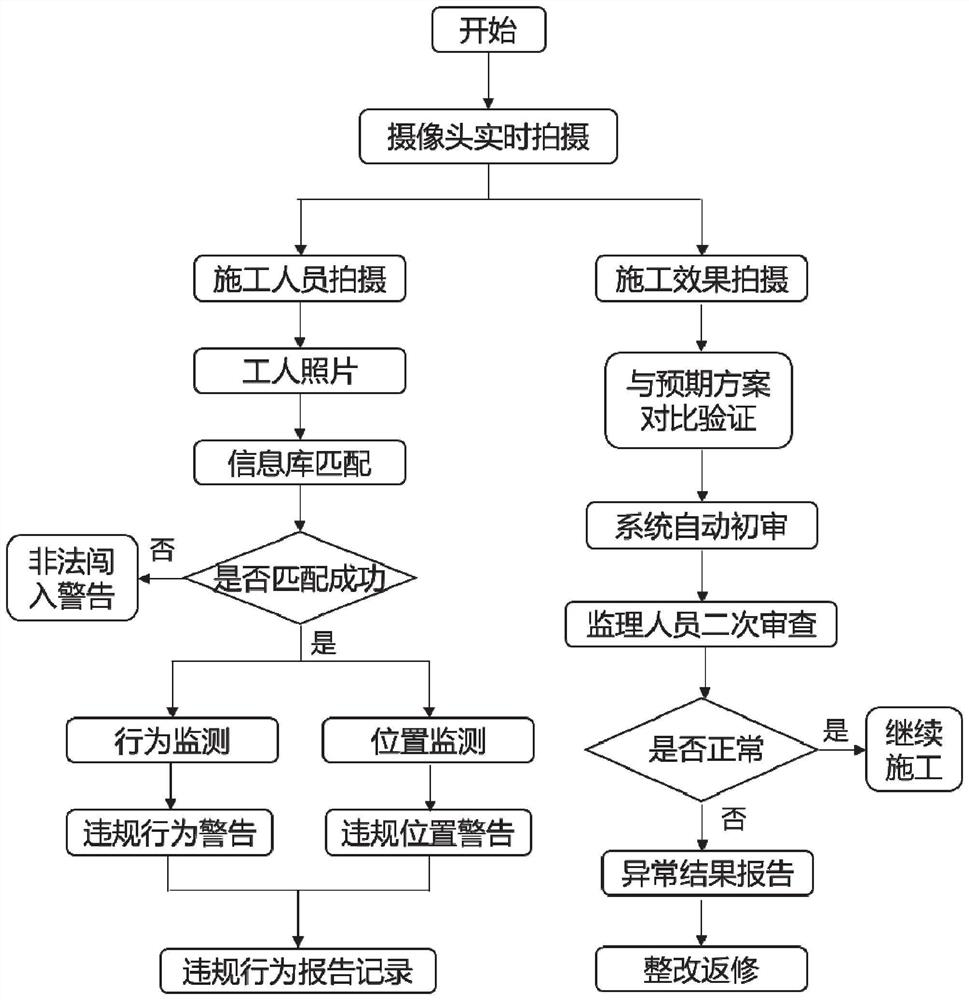
Construction safety discrimination method and system based on video information behavior pattern recognition
PendingCN114419475AGuarantee safe production and constructionCharacter and pattern recognitionArtificial lifePattern recognitionColor image
The invention belongs to the field of tunnel safety construction, and provides a construction safety judgment method and system based on video information behavior pattern recognition. The method comprises the following steps: acquiring a color image and a depth image of personnel in a set working area and a tunnel construction effect picture; extracting face feature information in the color image and determining the identity of a person according to the matching degree of the face feature information and a preset face feature template, and then tracking the person to judge whether the person with the determined identity leaves a normal working area; extracting human skeleton node information in the depth image of which the identity is determined, identifying personnel behaviors based on a behavior discrimination model, comparing the personnel behaviors with violation behaviors in a violation information base, and judging the violation behaviors of the personnel in real time; and based on the tunnel construction effect drawing and the construction effect inspection model, judging whether the current tunnel construction accords with an expected scheme or not in real time.
Owner:SHANDONG UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com