Key information infrastructure abnormity monitoring method and device
A technology of infrastructure and key information, applied in the field of network security, can solve problems such as lack of supervision methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
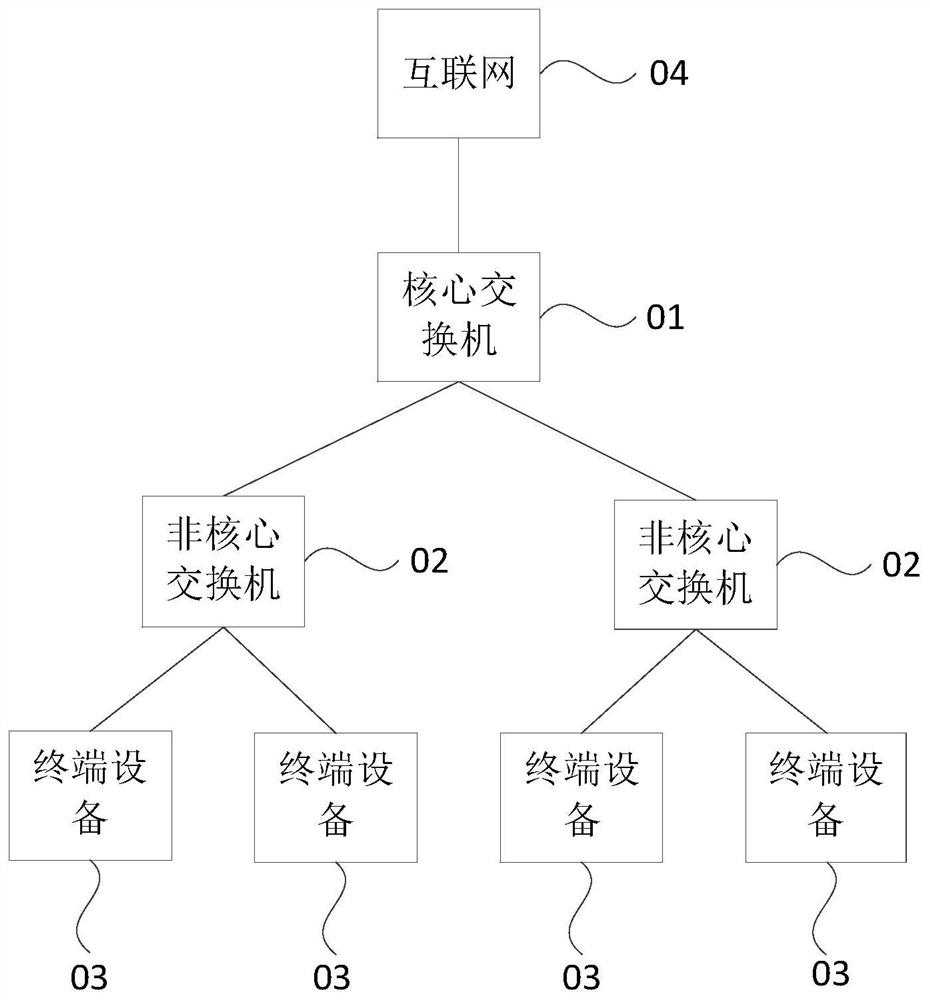
[0027] Figure 1B It is a flow chart of the abnormality monitoring method for critical information infrastructure provided by Embodiment 1 of the present invention. This embodiment is applicable to monitoring the operating system connected to the key information infrastructure of the machine, and / or whether there is a dynamic operation abnormality in the operating system of the machine. To perform, the device can be implemented by hardware and / or software, and integrated in electronic equipment, typically, can be integrated in the core switch of the internal local area network, the method specifically includes the following steps:
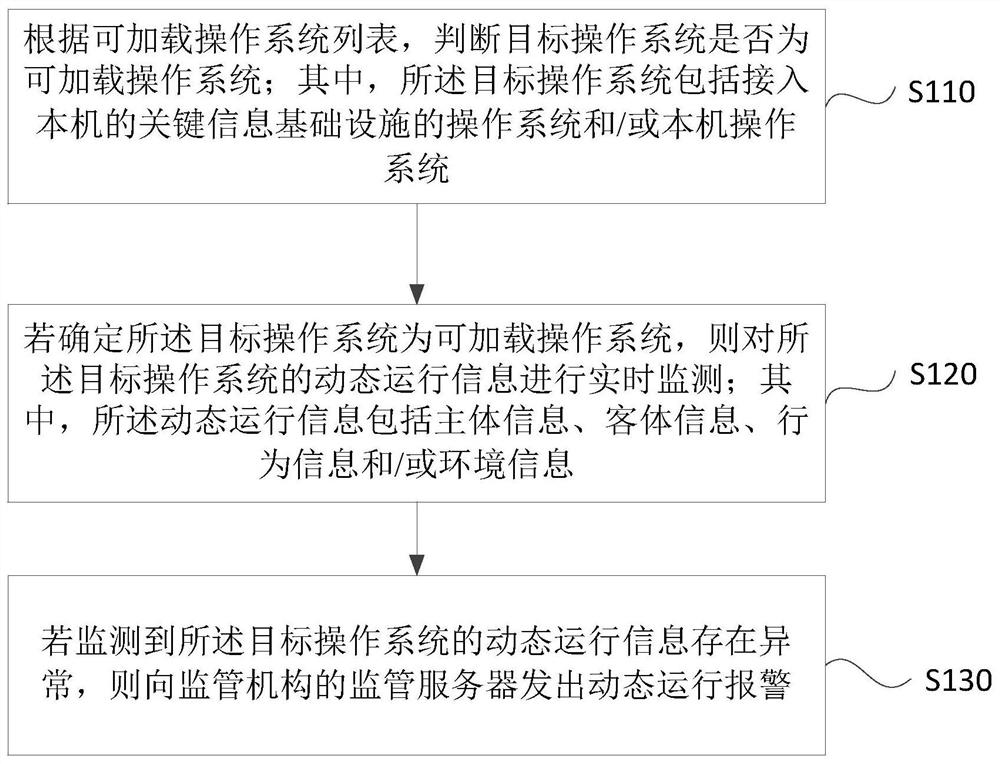
[0028] S110. Determine whether the target operating system is a loadable operating system according to the list of loadable operating systems; wherein, the target operating system includes an operating system that accesses the key information infrastructure of the machine and / or a local operating system.
[0029] The loadable operating system is p...
Embodiment 2
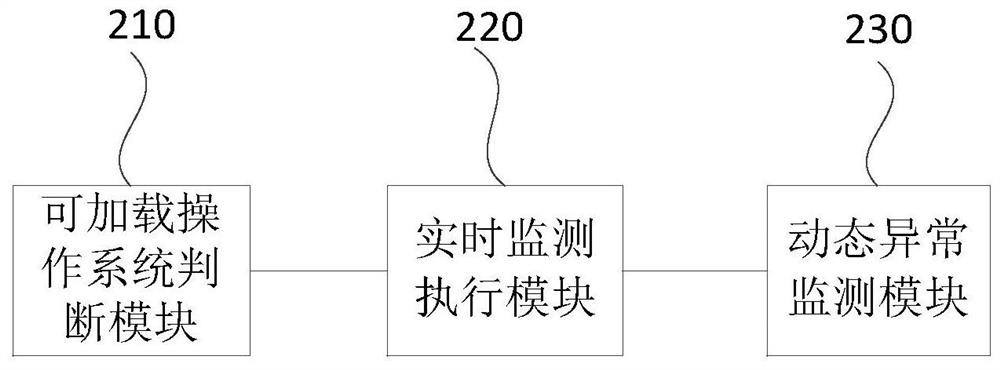
[0043] figure 2 The structural block diagram of the abnormality monitoring device for key information infrastructure provided by Embodiment 2 of the present invention, which can be realized by hardware and / or software, specifically includes: a loadable operating system judging module 210, and a real-time monitoring execution module 220 and a dynamic anomaly monitoring module 230.
[0044] The loadable operating system judging module 210 is used to judge whether the target operating system is a loadable operating system according to the list of loadable operating systems; wherein, the target operating system includes an operating system and / or access to the key information infrastructure of the machine or the native operating system;
[0045] The real-time monitoring execution module 220 is configured to monitor the dynamic running information of the target operating system in real time if it is determined that the target operating system is a loadable operating system; where...
Embodiment 3
[0062] image 3 It is a schematic structural diagram of an electronic device provided by Embodiment 3 of the present invention. image 3 A block diagram of an exemplary electronic device 12 suitable for use in implementing embodiments of the invention is shown. image 3 The electronic device 12 shown is only an example, and should not limit the functions and scope of use of the embodiments of the present invention.
[0063] Such as image 3 As shown, electronic device 12 takes the form of a general-purpose computing device. Components of electronic device 12 may include, but are not limited to, one or more processors or processing units 16, system memory 28, bus 18 connecting various system components including system memory 28 and processing unit 16.
[0064]Bus 18 represents one or more of several types of bus structures, including a memory bus or memory controller, a peripheral bus, an accelerated graphics port, a processor, or a local bus using any of a variety of bus s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com