Equipment configuration method, system and device, electronic equipment and storage medium
A device configuration and device technology, applied in the security field, can solve problems such as low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The following will clearly and completely describe the technical solutions in the embodiments of the present application with reference to the drawings in the embodiments of the present application.
[0058] It should be noted that the terms "system" and "network" in the embodiments of the present invention may be used interchangeably. "Multiple" means two or more, in view of this, "multiple" can also be understood as "at least two" in the embodiments of the present invention. "And / or" describes the association relationship of associated objects, indicating that there may be three types of relationships, for example, A and / or B may indicate: A exists alone, A and B exist simultaneously, and B exists independently. In addition, the character " / ", unless otherwise specified, generally indicates that the associated objects before and after are in an "or" relationship.
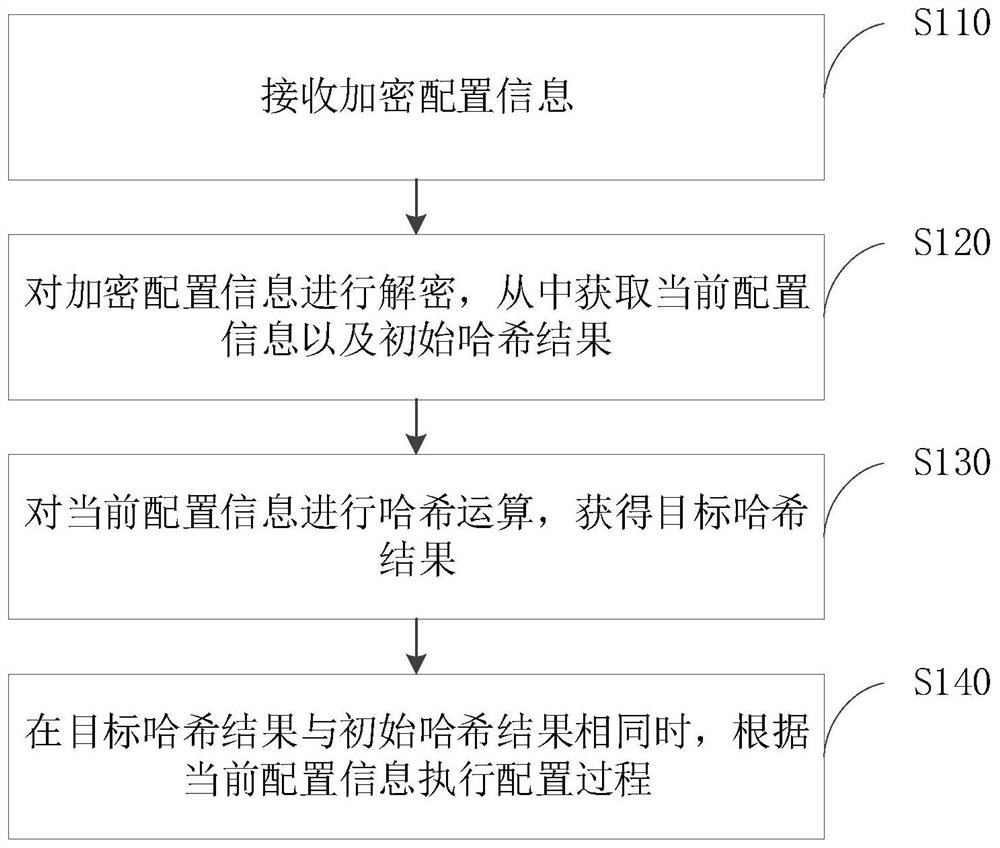
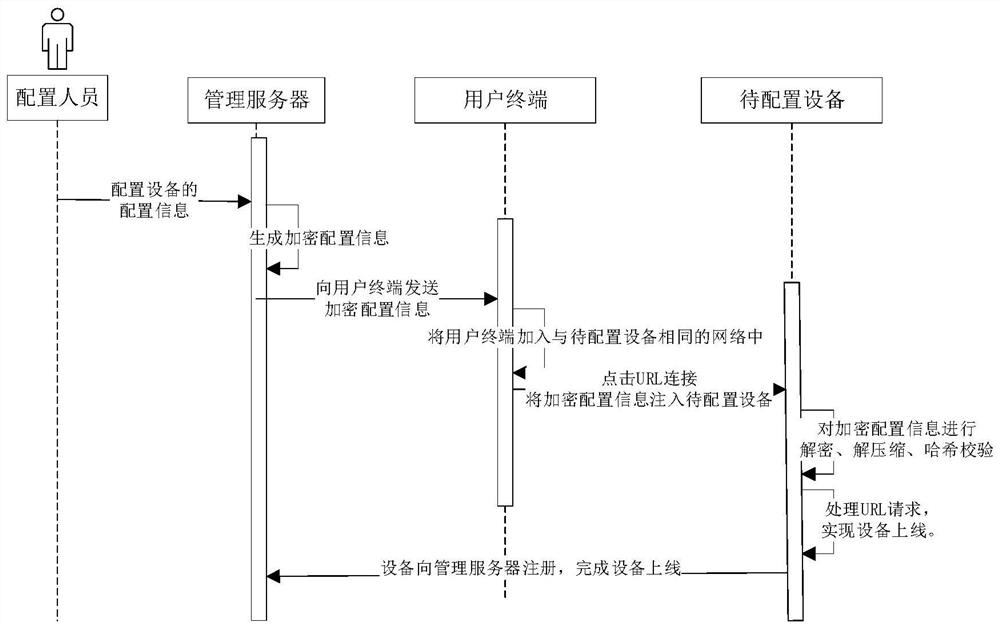
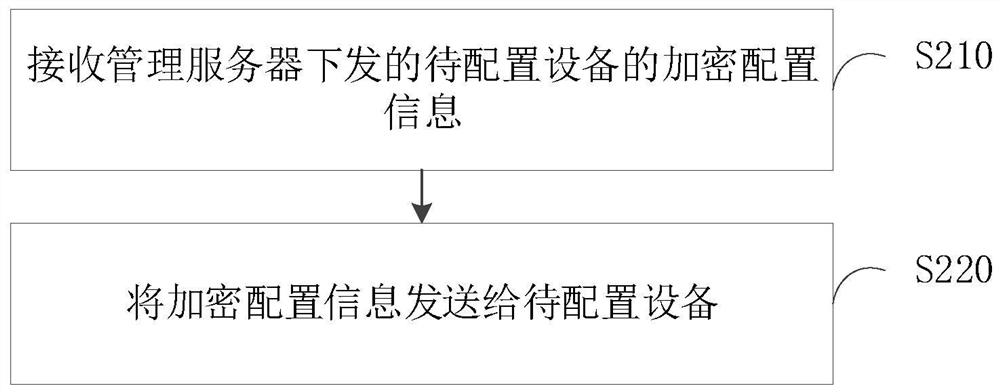
[0059] The embodiment of the present application provides a device configuration method, which is appli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com