Patents
Literature
36results about How to "Avoid misconfiguration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
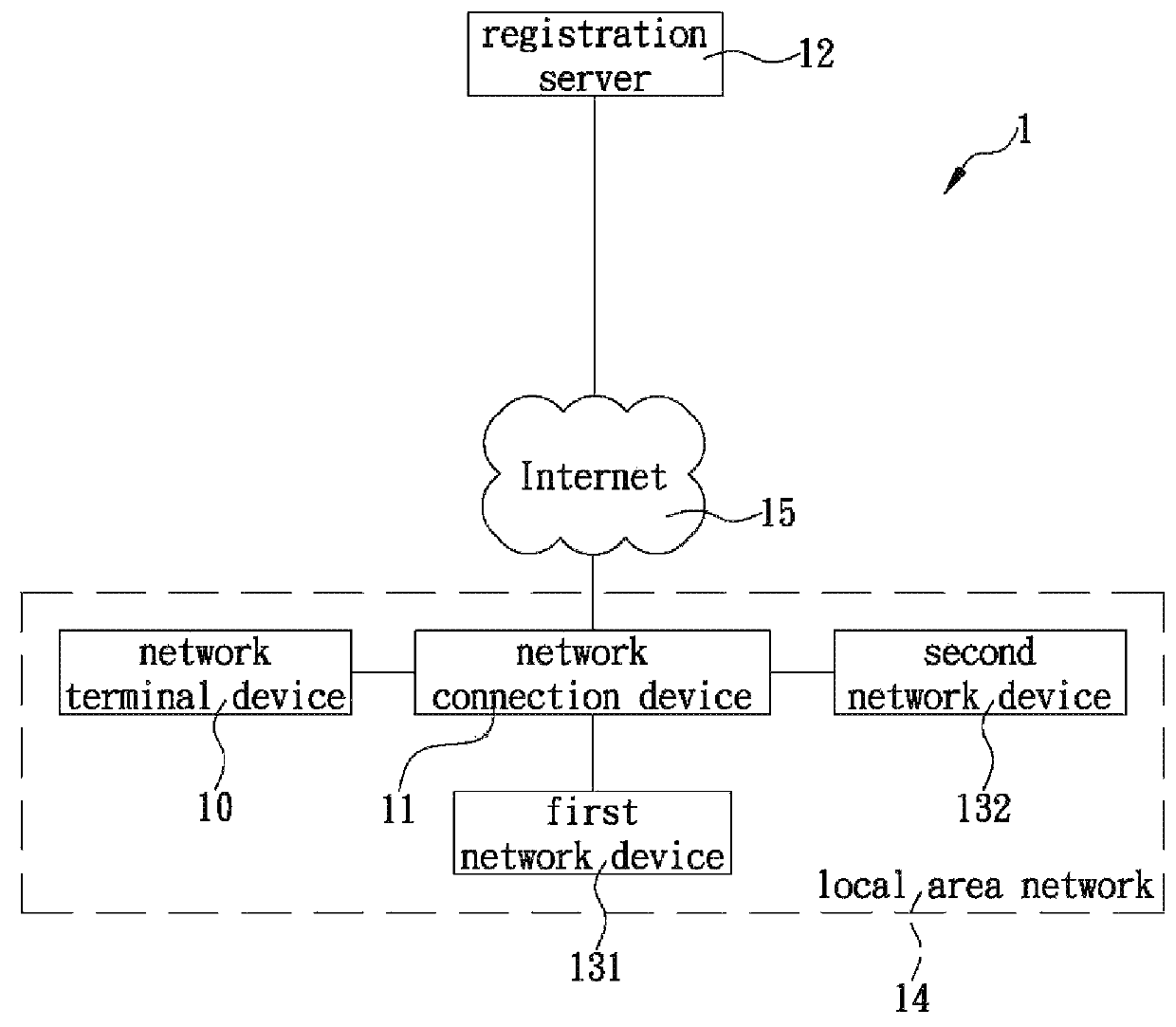
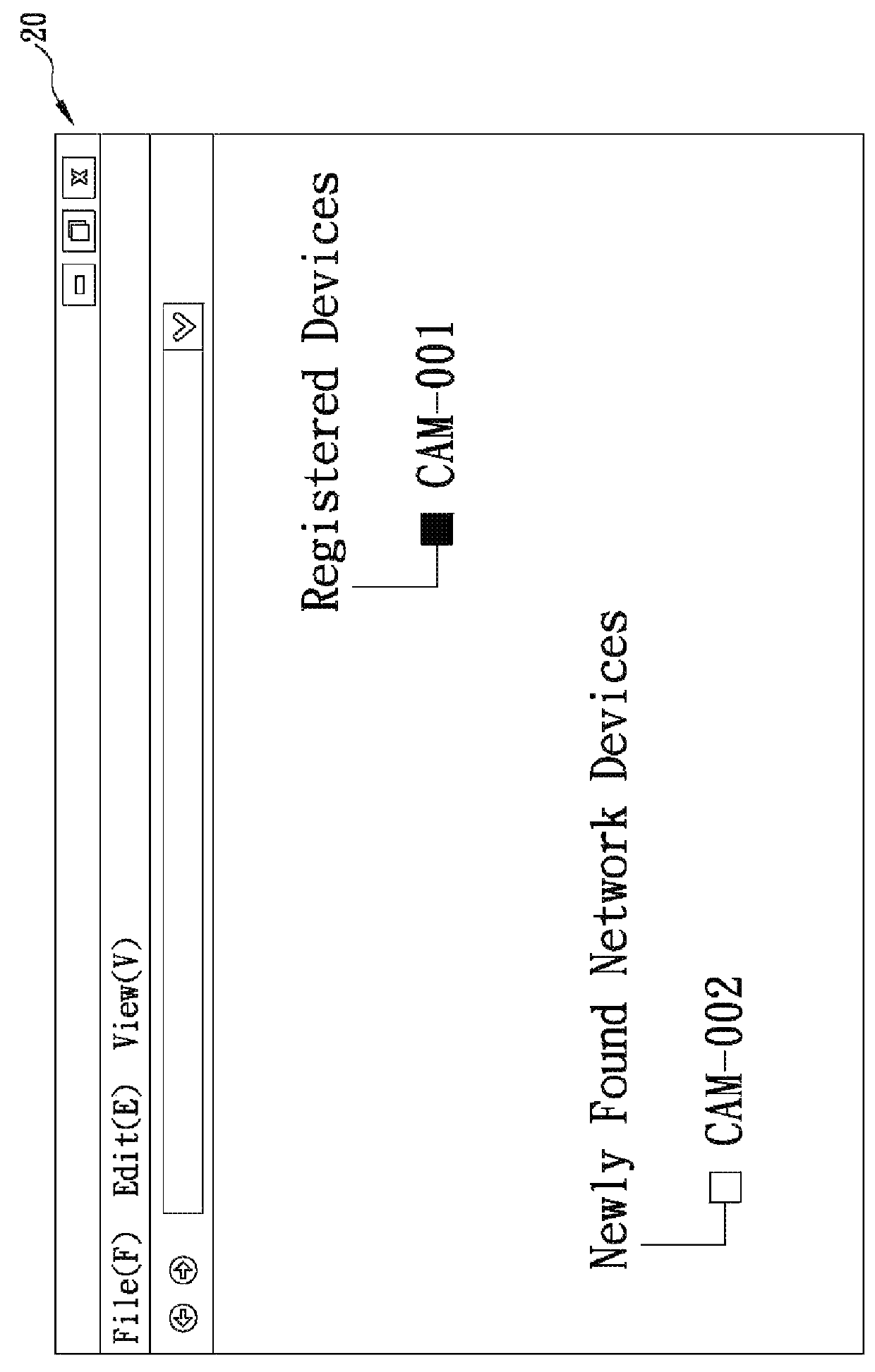
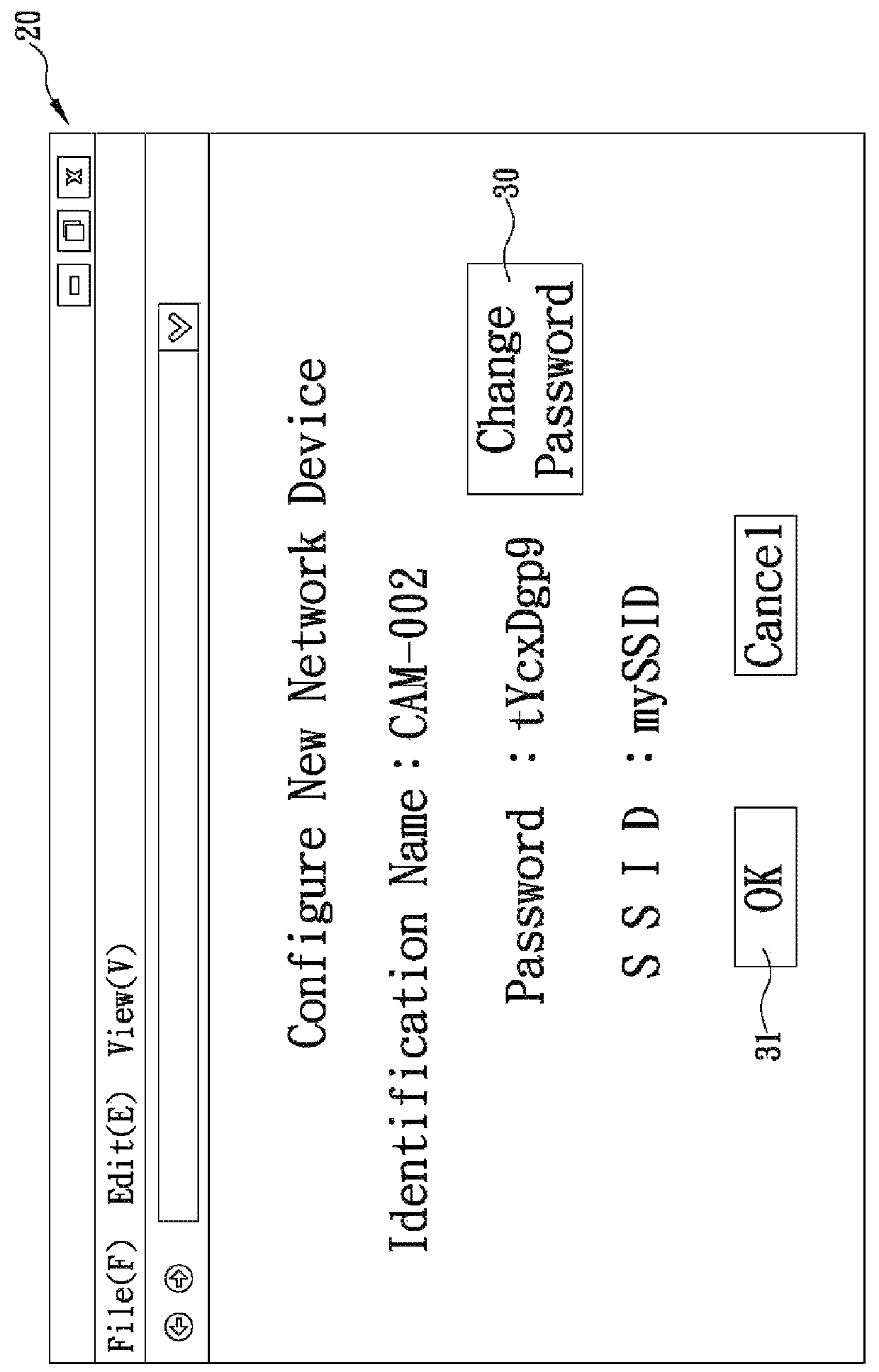
Zero-configuration system and method for network devices
ActiveUS20140040443A1Shorten the timeQuick configurationNetwork topologiesDigital computer detailsNetwork terminationNetwork connection
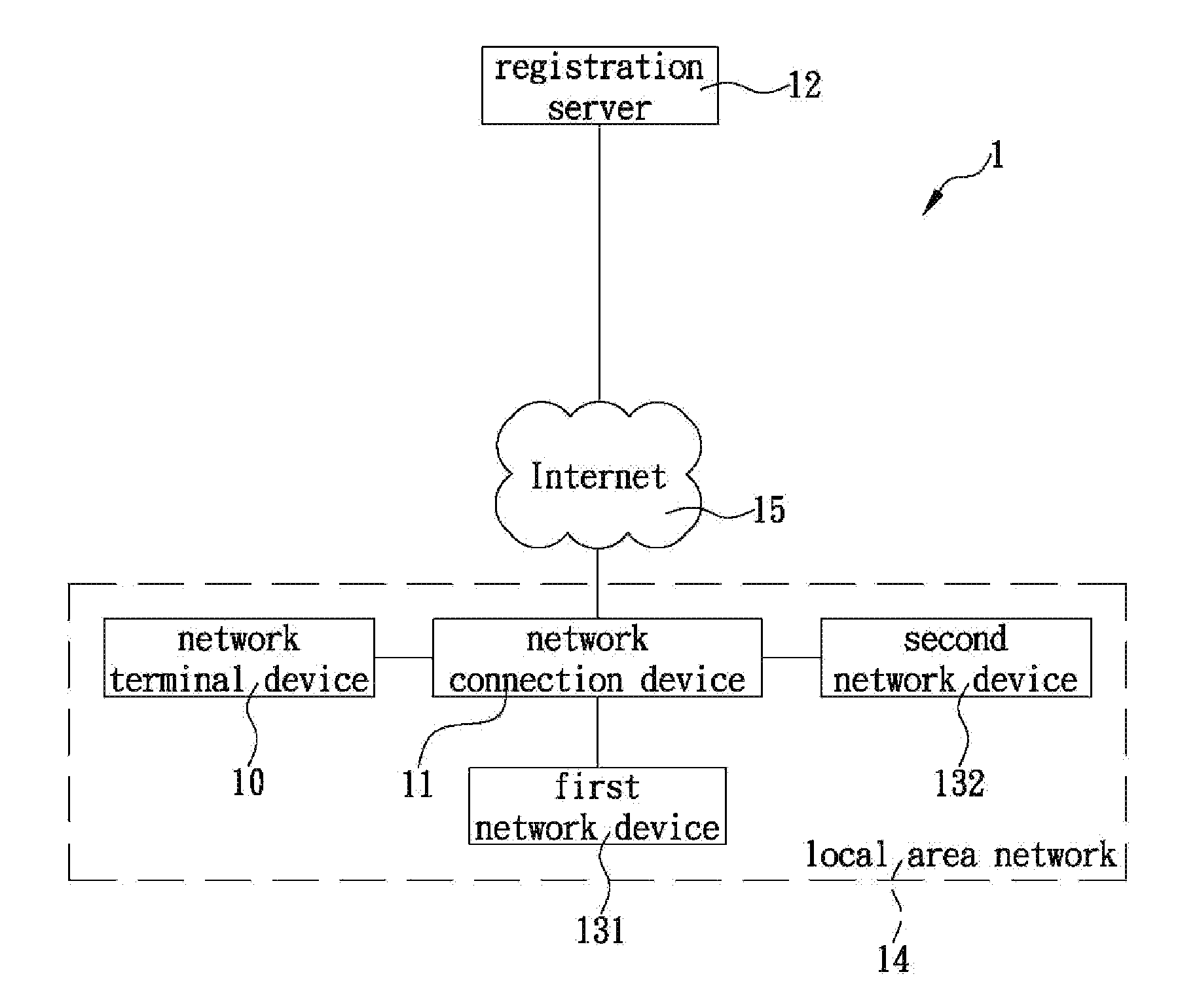
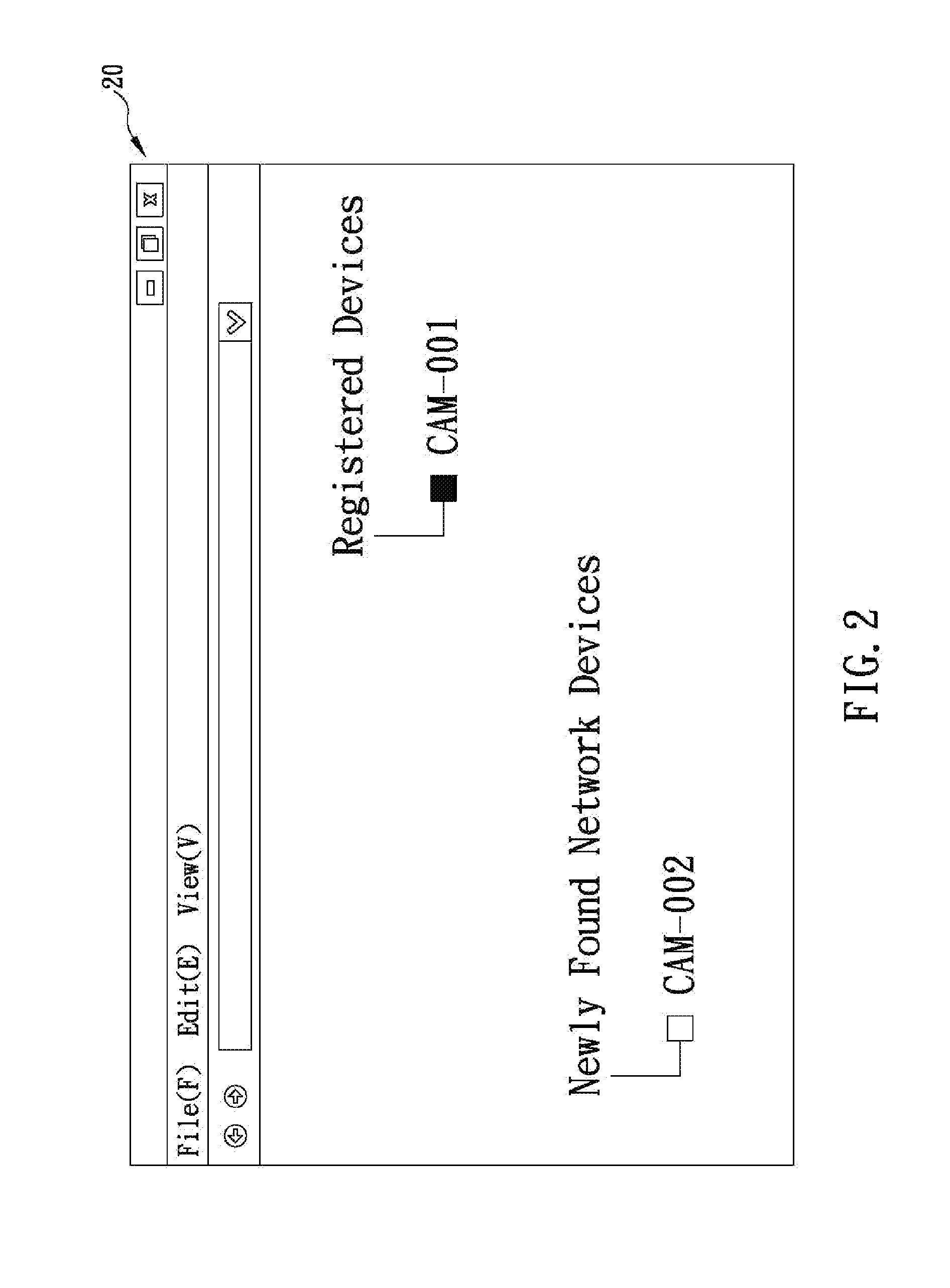
The present invention is a zero-configuration system including a registration server connecting (via the Internet) to a network terminal device through a network connection device, and a first network device located in a local area network same as the two devices and having a first identification name and a set of configuration values, wherein the registration server stores the first identification name corresponding to a user information. The network terminal device can login to the registration server by using the user information, and then scan the local area network and, when detecting a second network device having a second identification name not yet stored in the registration server, automatically receive the first identification name from the registration server, obtain the configuration values from the first network device, and configure the second network device according to the configuration values, so as to automatically connect to and access the second network device.
Owner:D-LINK
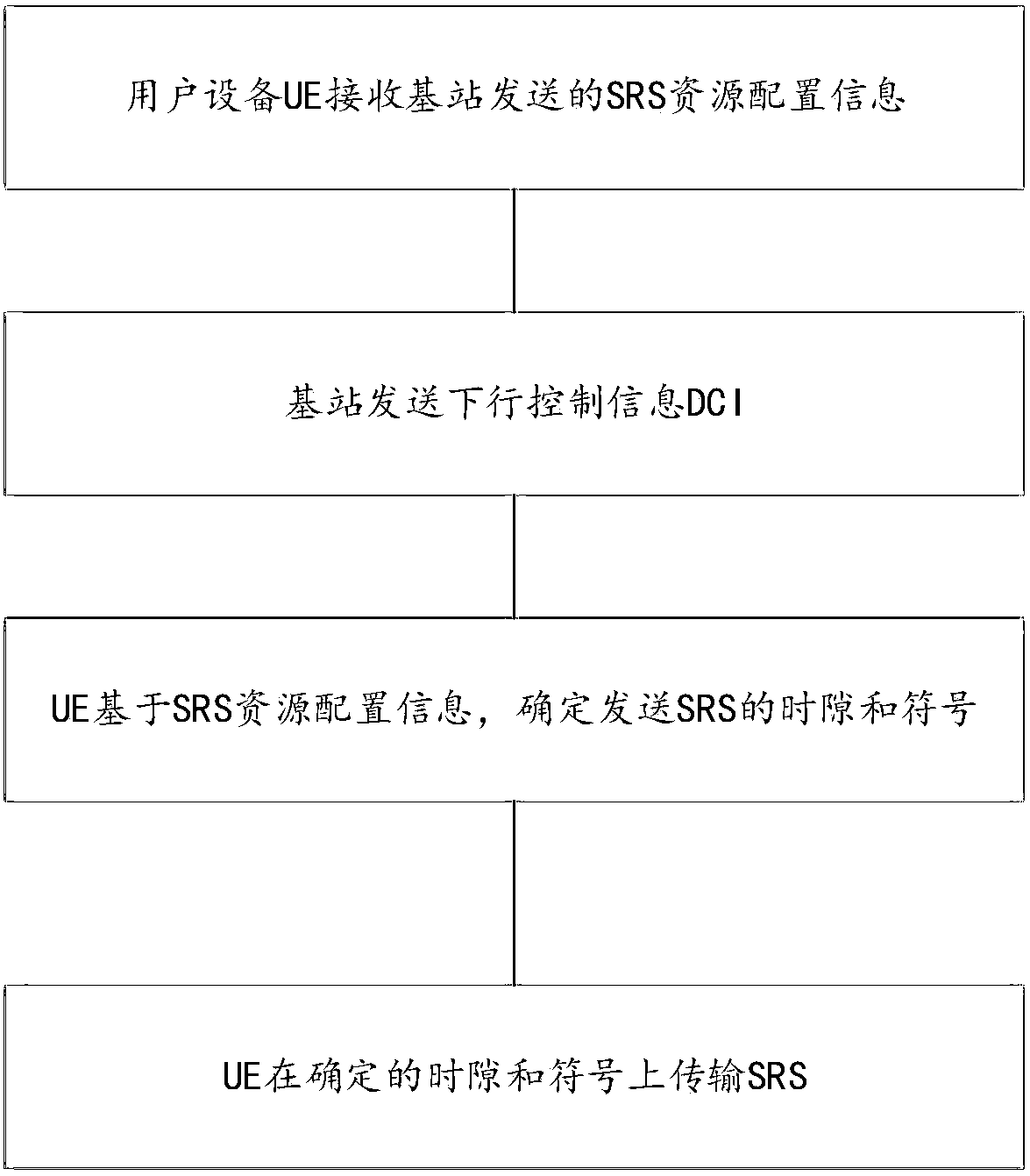
Sounding reference signal configuration method and device
ActiveCN110034889AFlexible trigger timeReduce overheadSignal allocationAllocation timingSounding reference signalVIT signals
The invention relates to the technical field of wireless communication, in particular to a sounding reference signal configuration method, which can solve the problem of when the SRS is transmitted. In the method, user equipment (UE) receives SRS resource configuration information sent by a base station; the UE receives downlink control information (DCI) sent by a base station; and the UE sends anSRS on the determined time slot and symbol, wherein the determined symbol is determined by the UE based on the SRS resource configuration information.
Owner:HUAWEI TECH CO LTD
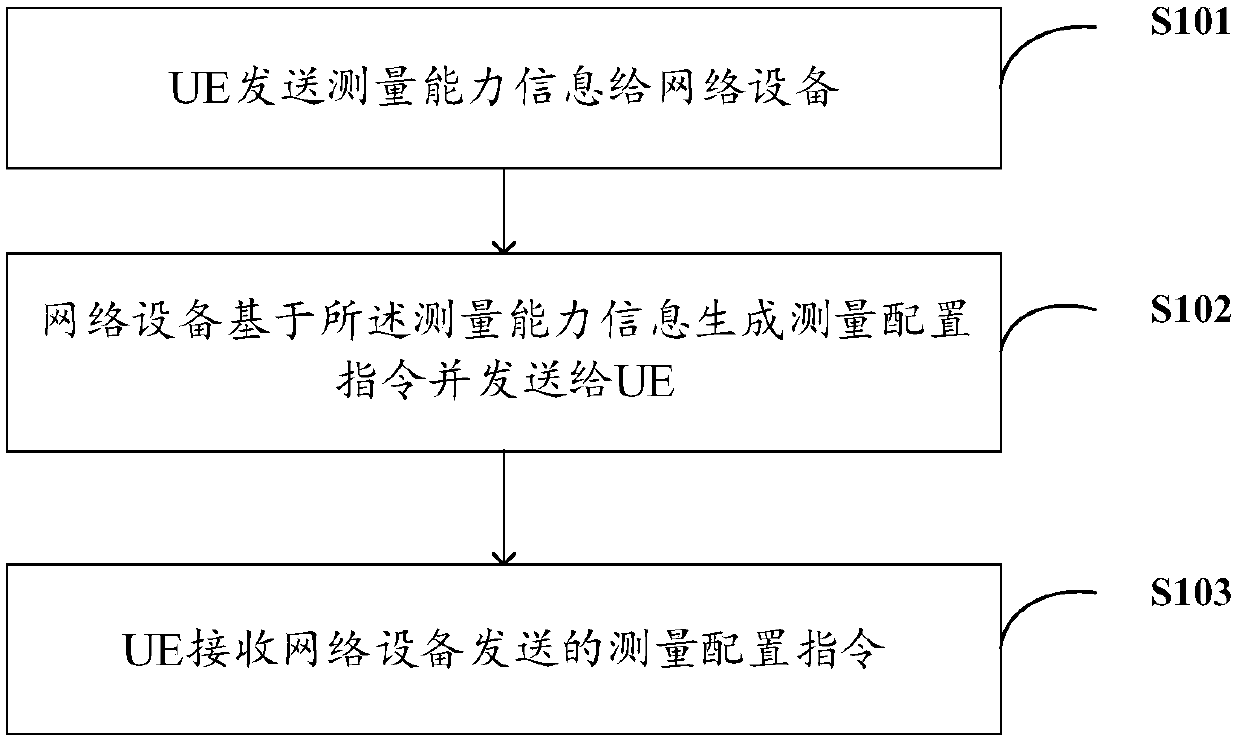
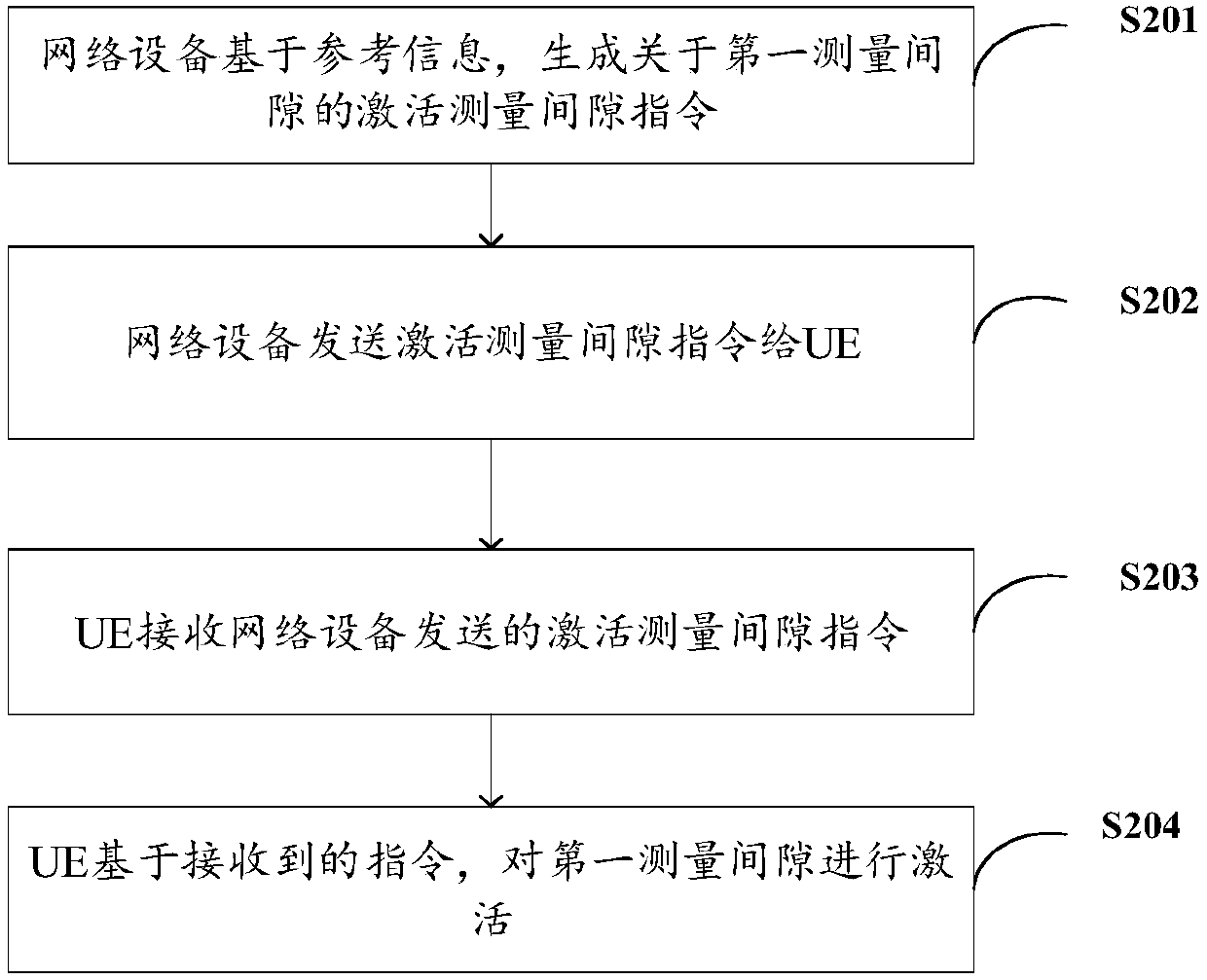
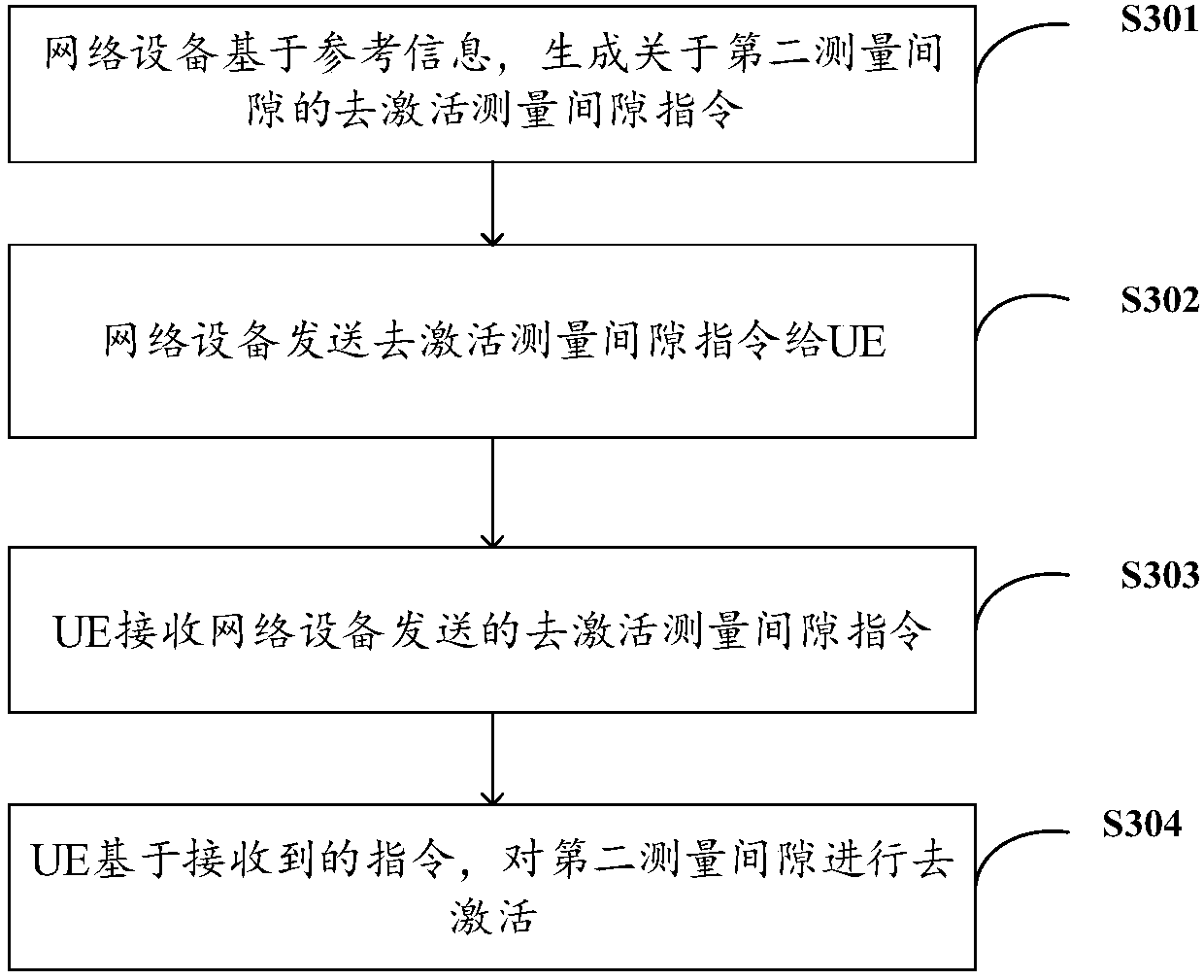
Measurement configuration method, user equipment, network equipment and storage medium
ActiveCN110740050AAvoid misconfigurationReduce changesSignal allocationData switching networksComputer networkEngineering
Owner:VIVO MOBILE COMM CO LTD
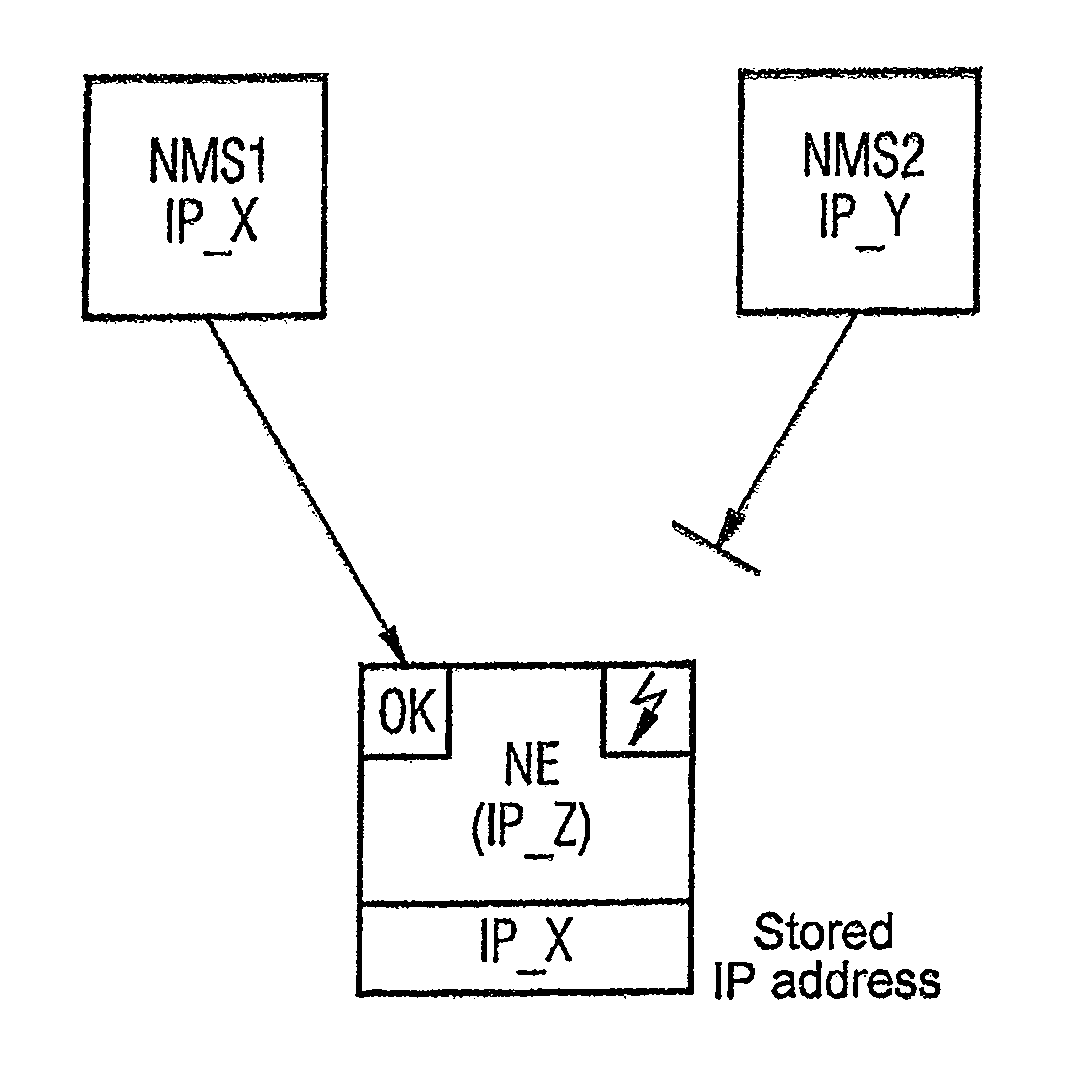
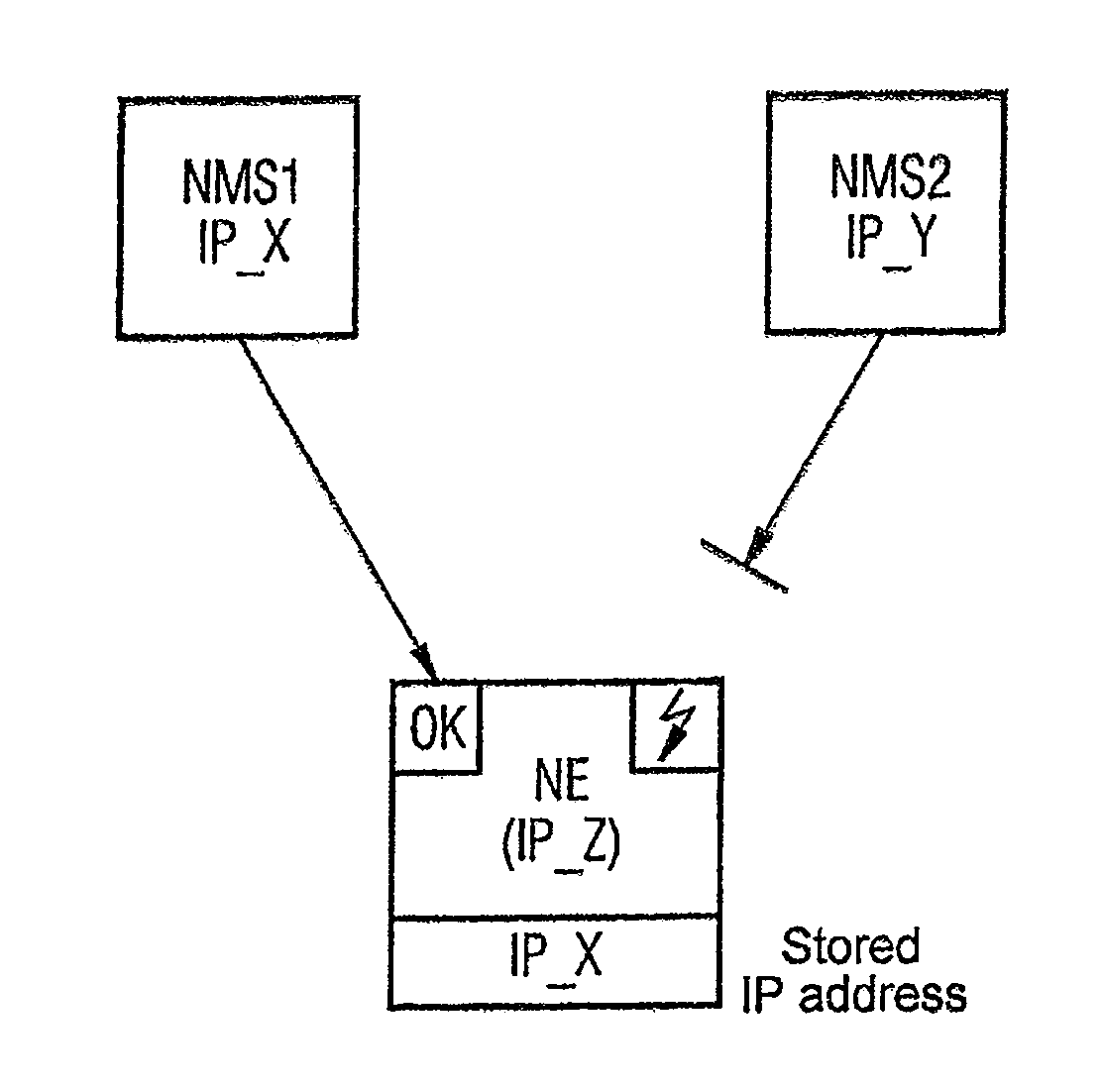
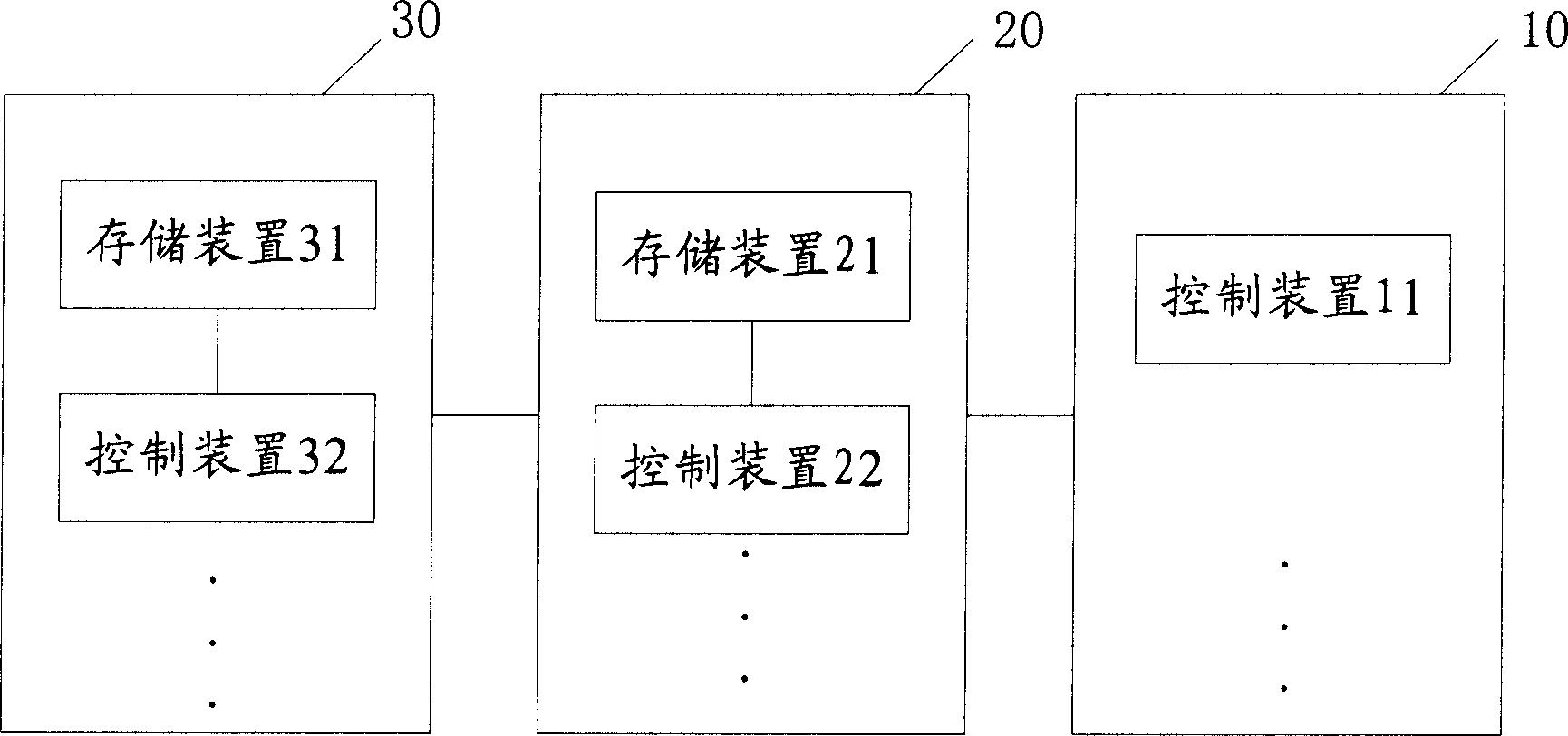
Method, Communications Assembly and Communications Device for Controlling the Access to at Least One Communications Device
InactiveUS20080162695A1Avoid misconfigurationProgram synchronisationDigital computer detailsInformation controlCommunications system
The invention relates to a method for controlling the access to at least one communications device (NE) by means of at least one additional communications device (NMS1, NMS2) in a communications network. According to said method, when the aforementioned communications device or devices (NE) is or are accessed, information representing the additional communications device or devices (NMS1, NMS2), such as e.g. the IP address, is recorded. Additional access is then controlled using said information. The invention is characterised in that only certain, predefinable communications devices (NMS1, NMS2) with access can access part of the information stored in the communications device(s) (NE) during a specific time period.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
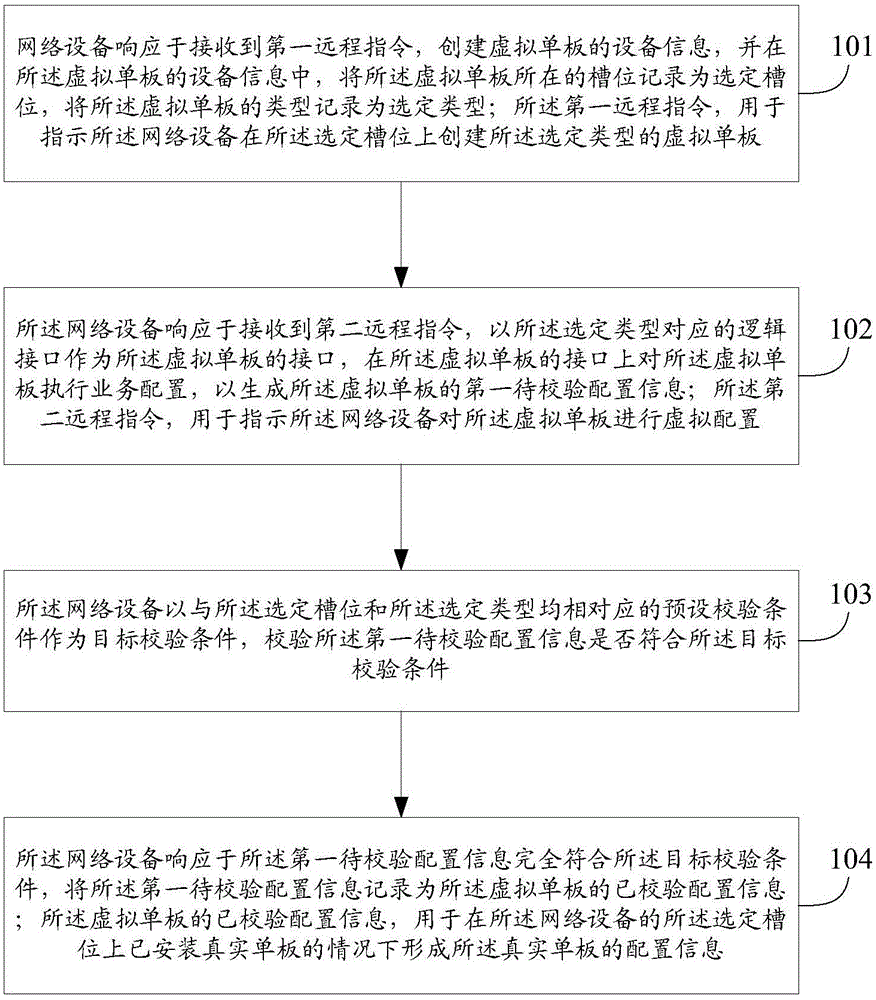
Method and apparatus of service configuration in network cutover
ActiveCN105099786AShort timeImprove efficiencyData switching networksService configurationOperating system
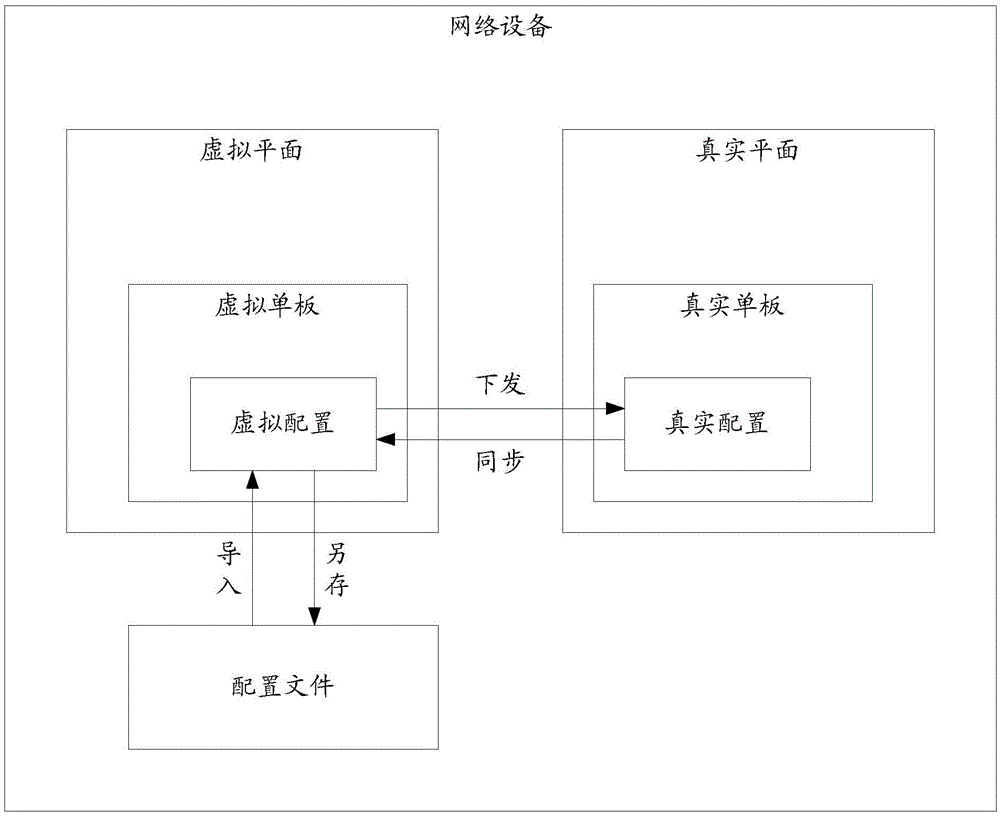
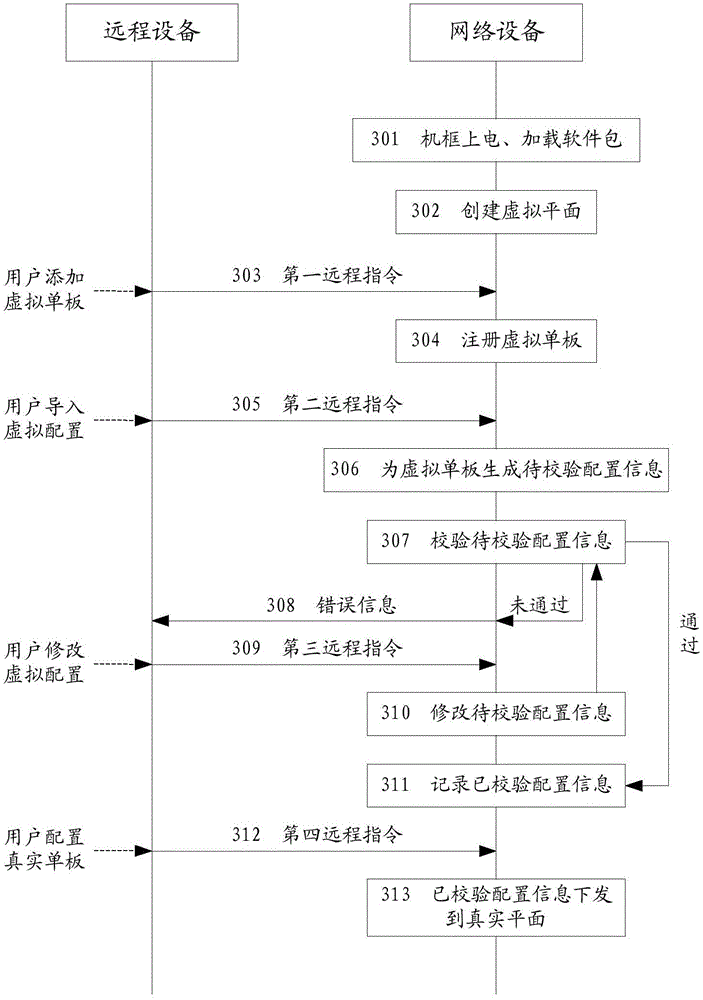
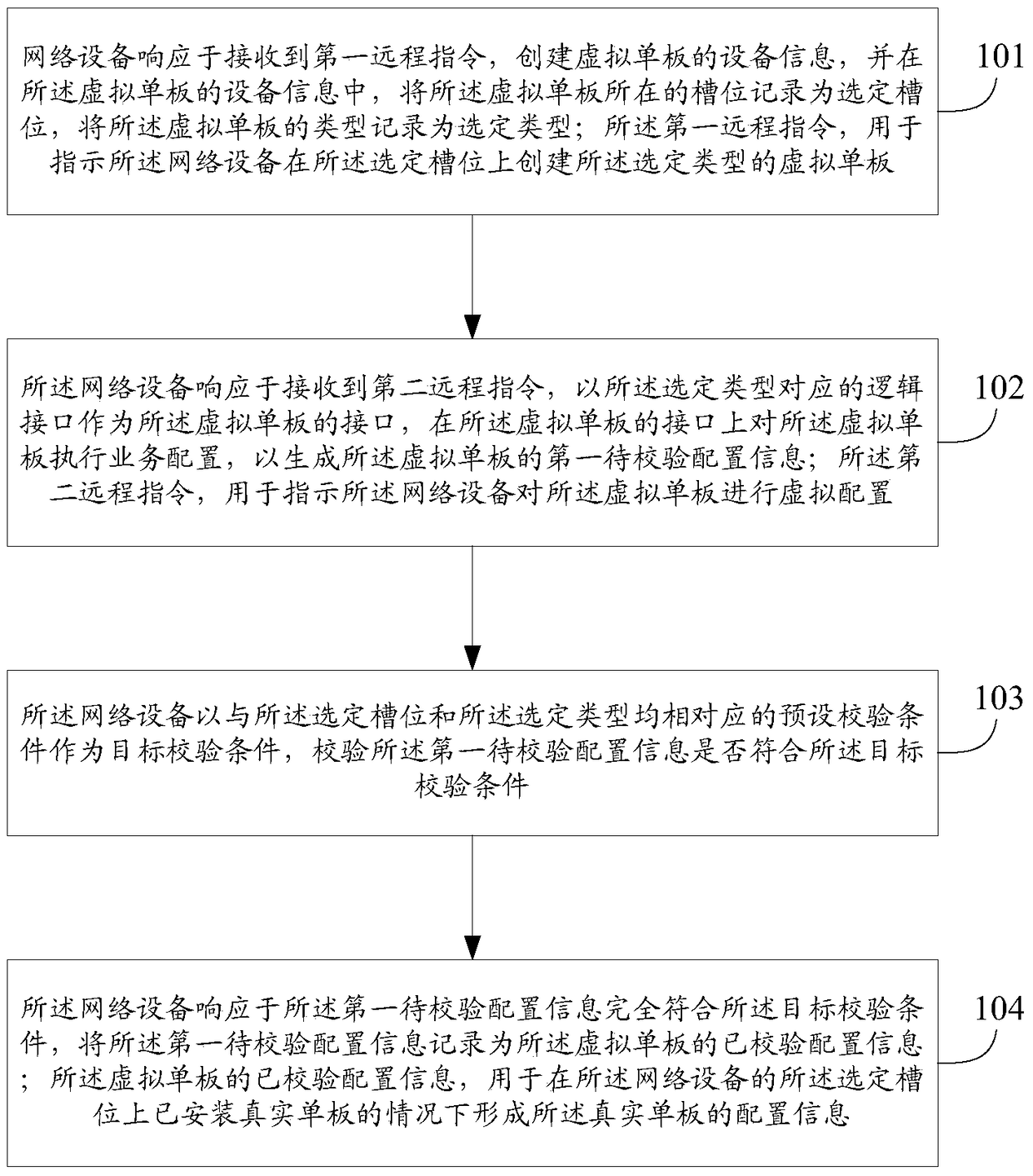
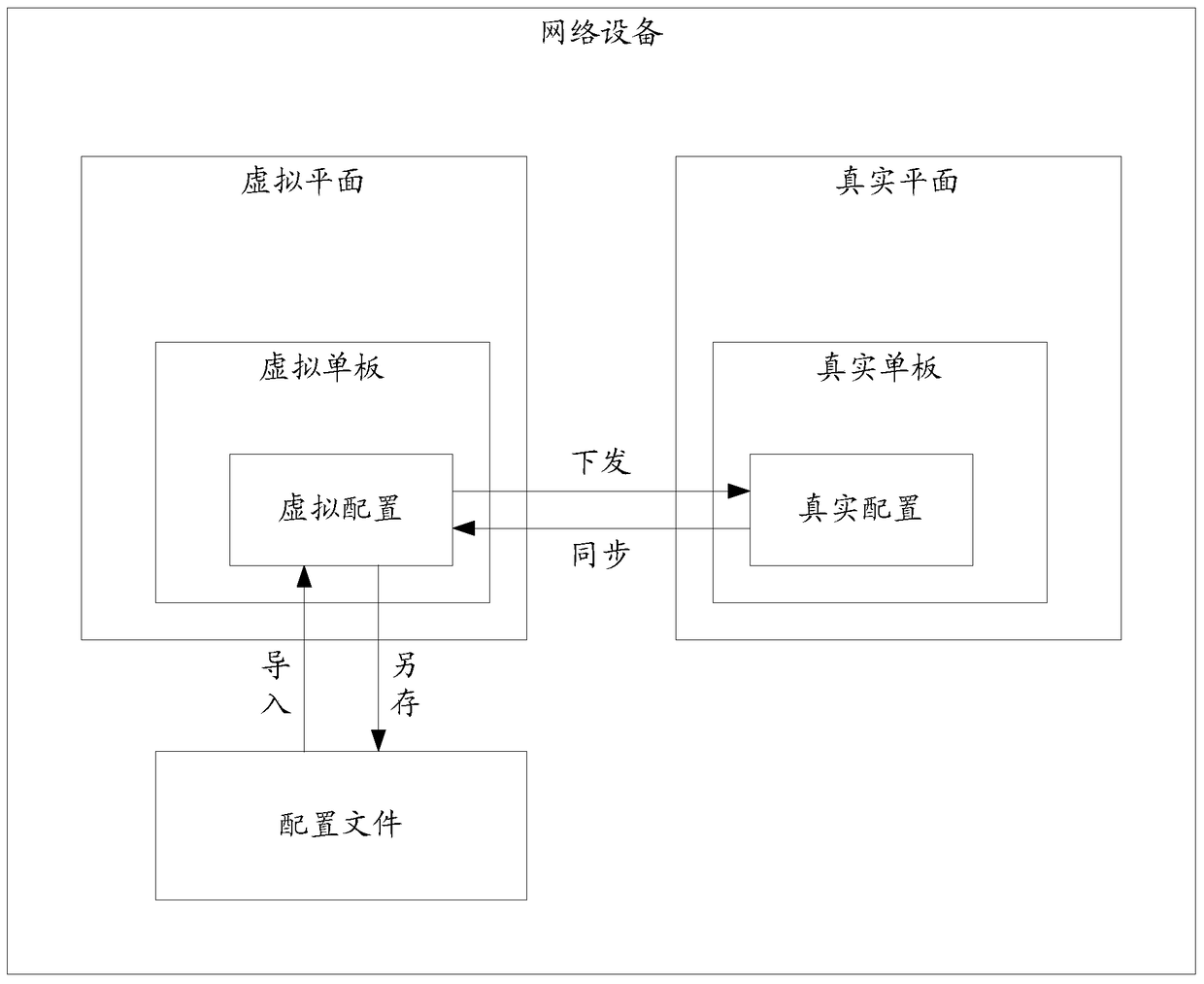
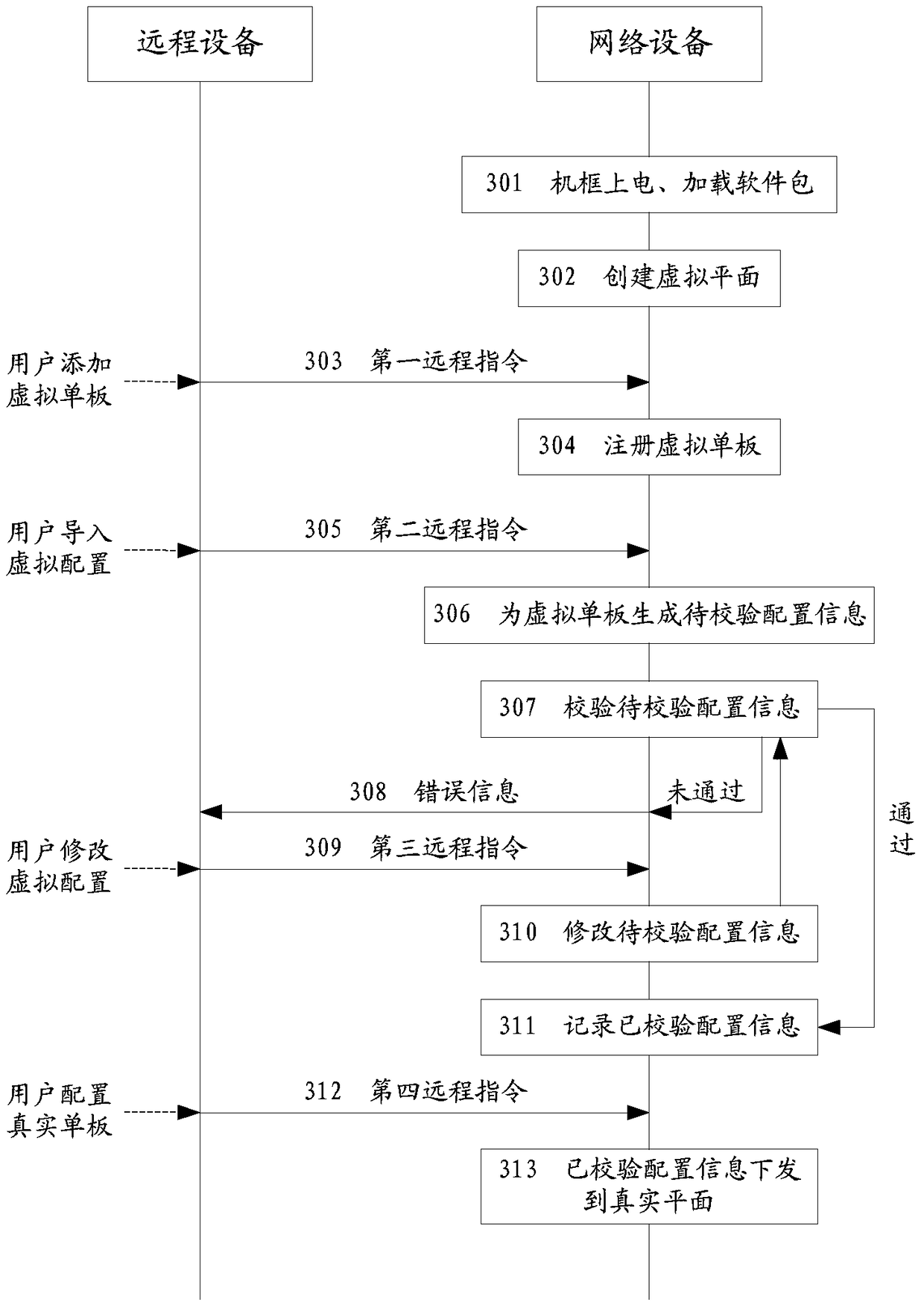
The invention discloses a configuration method of network service cutover in an embodiment. The method comprises: a network apparatus creates apparatus information of a virtual one board and records the selected slot position and the selected type of the virtual one board as responding to a first remote instruction received; the network apparatus performs service configuration on the virtual one board on a logic interface collecting to the selected type as responding to a second remote instruction received, in order to generate first to-be-verified configuration information; the network apparatus verifies whether the first to-be-verified configuration information satisfies a target verification condition by taking a preset verification condition corresponding to both the selected slot position and the selected type as the target verification condition; and the network apparatus, responding to that the first to-be-verified configuration information completely satisfies the target verification condition, records the first to-be-verified configuration information as the verified configuration information of the virtual one board so as to form the configuration information of service configuration on a real one board corresponding to the virtual single board. Besides, the embodiment of the invention further discloses a configuration apparatus of network service cutover.
Owner:HUAWEI TECH CO LTD
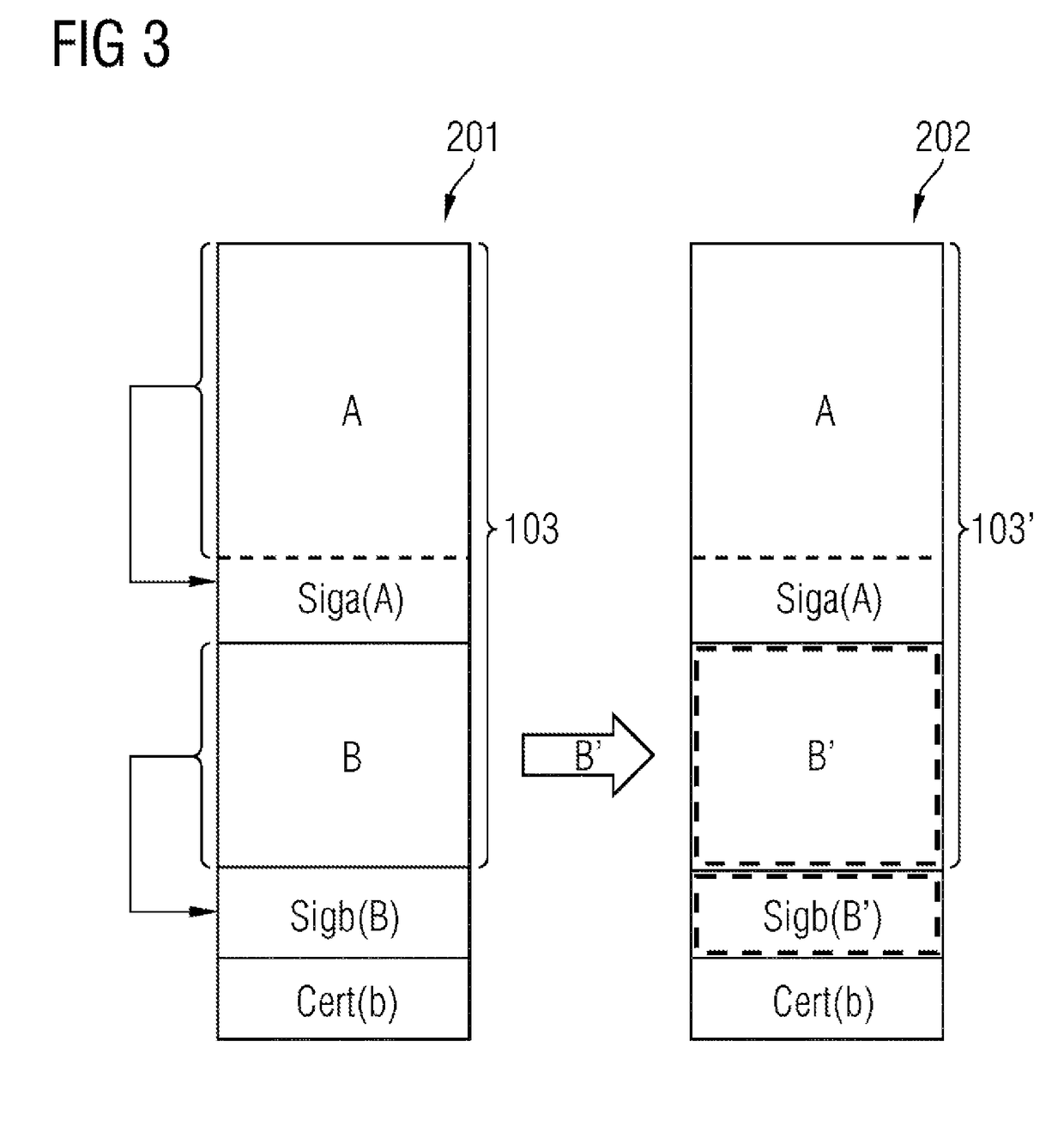
Method and arrangement for securely interchanging configuration data for an apparatus
InactiveUS20180131520A1Easy to operateEasy to disassembleUser identity/authority verificationDigital data protectionExternal storageDigital signature
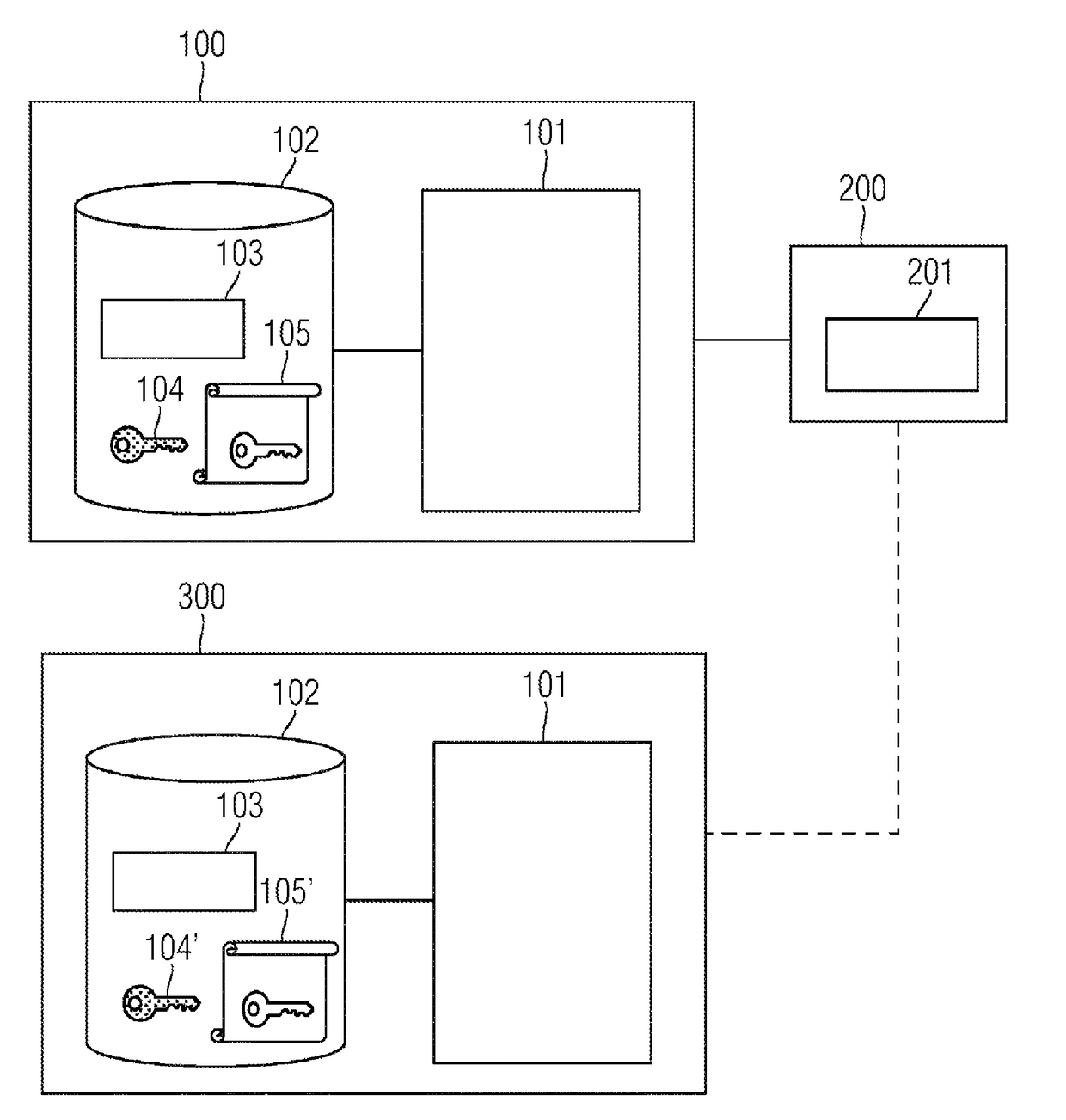
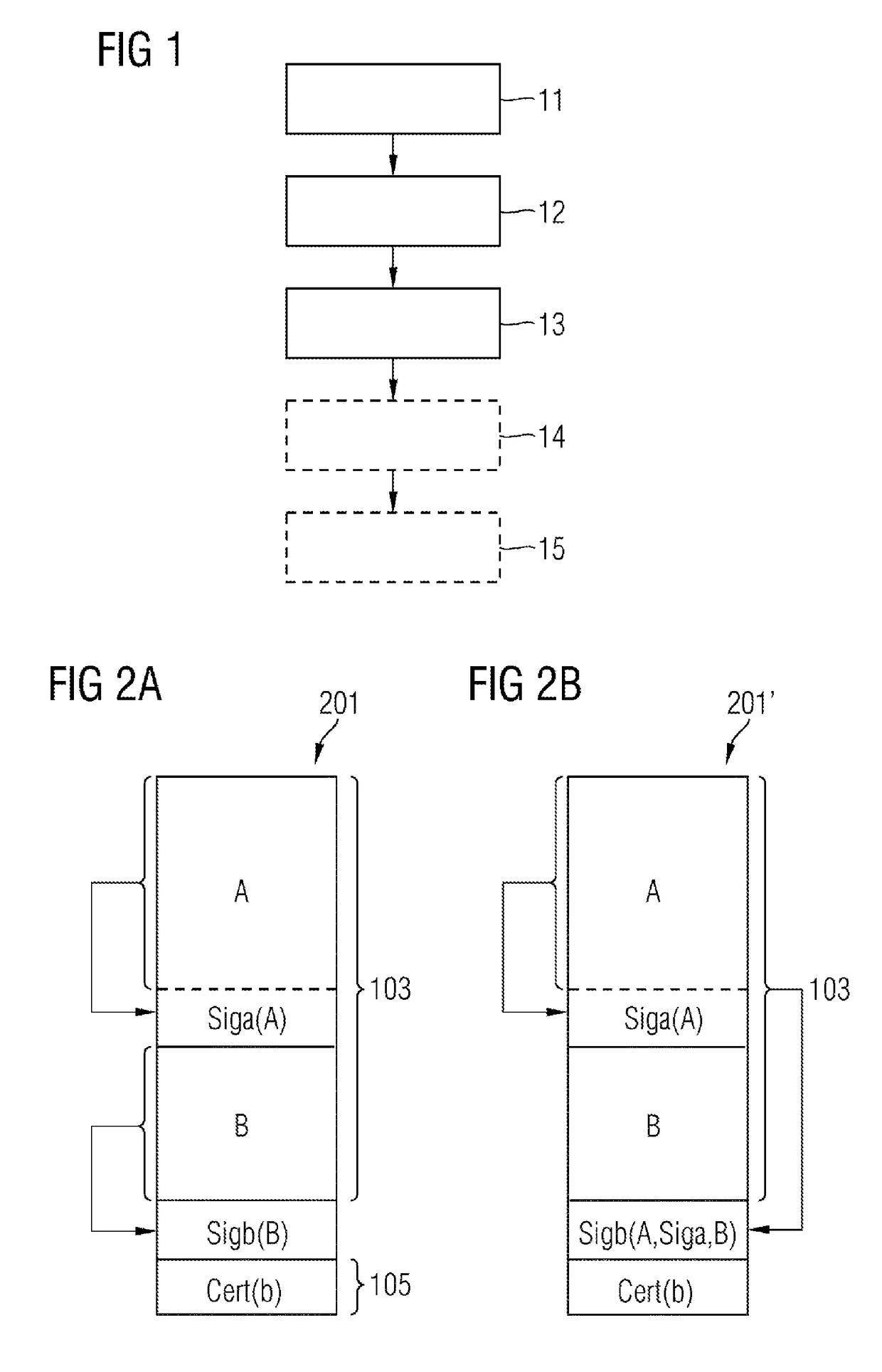
A method for securely interchanging configuration data between a first apparatus and a second apparatus, including the steps of producing a digital signature for the configuration data for the first apparatus using a piece of security information from the first apparatus, storing the configuration data, the digital signature and a security token in an external memory apparatus, and loading of the configuration data, the digital signature and the security token from the external memory apparatus into the second apparatus is provided. Furthermore, an arrangement for securely interchanging configuration data including an apparatus, and a first memory apparatus detachably connected to the apparatus is also provided.
Owner:SIEMENS AG
Cloud Security Posture Management systems and methods with a cloud-based system
ActiveUS20220046059A1Reduce riskPrevent cloud misconfigurationsTransmissionEngineeringCloud provider
Cloud Security Posture Management (CSPM) systems and methods include, in a node in a cloud-based system, obtaining a plurality of security policies and one or more compliance frameworks for a tenant of a cloud provider where the tenant has a cloud application deployed with the cloud provider, wherein each security policy defines a configuration and an expected value, and wherein each compliance framework includes one or more of the security policies; obtaining configurations of the cloud application; identifying misconfigurations of the cloud application based on a comparison of the obtained configurations with the plurality of security policies; analyzing the misconfigurations to determine risks including prioritization of the risks based on their likelihood of exposure to security breaches; and causing remediation of the identified misconfigurations and the determined risks, wherein the cloud-based system performs the CSPM service in addition to one or more additional cloud services.
Owner:ZSCALER INC
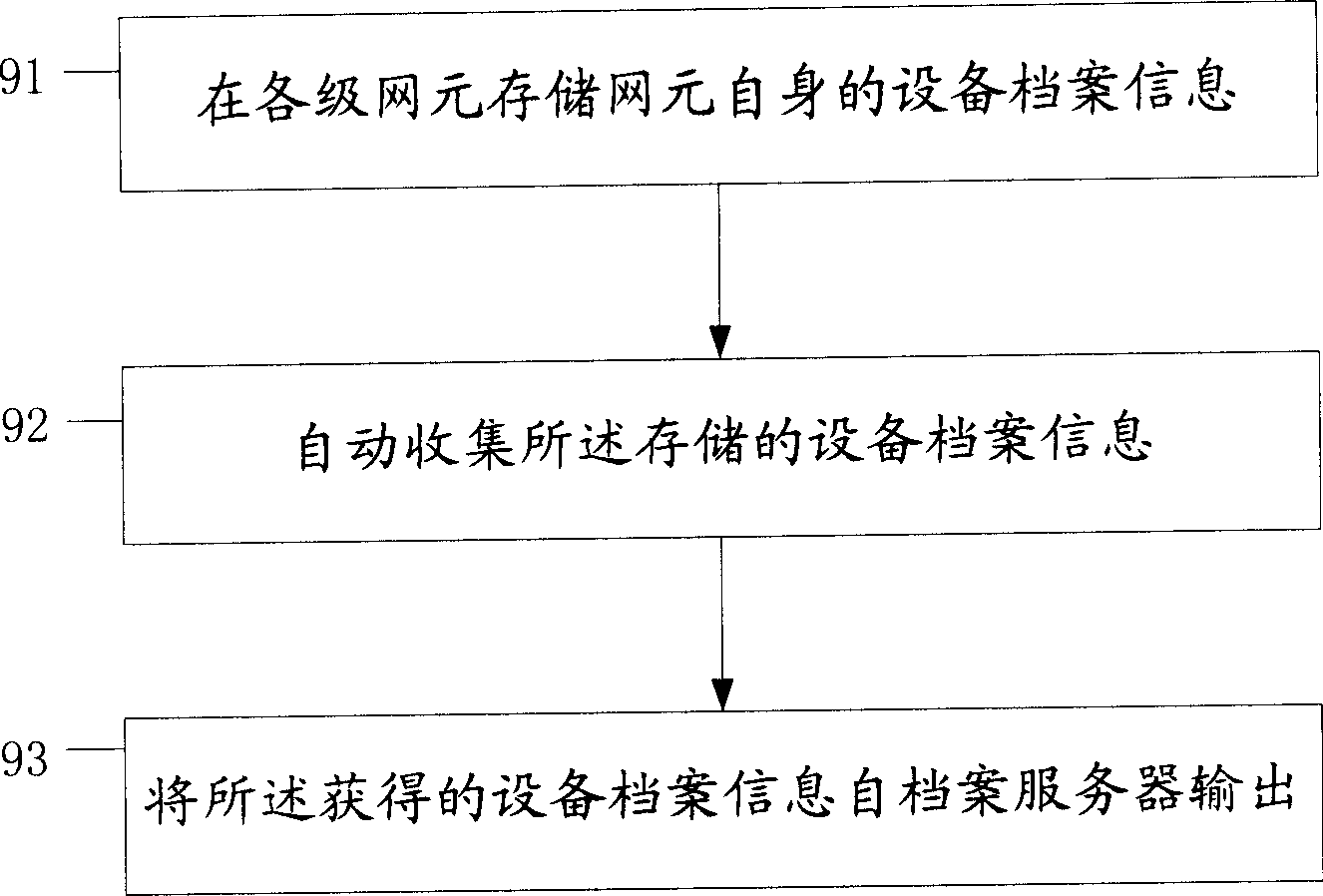
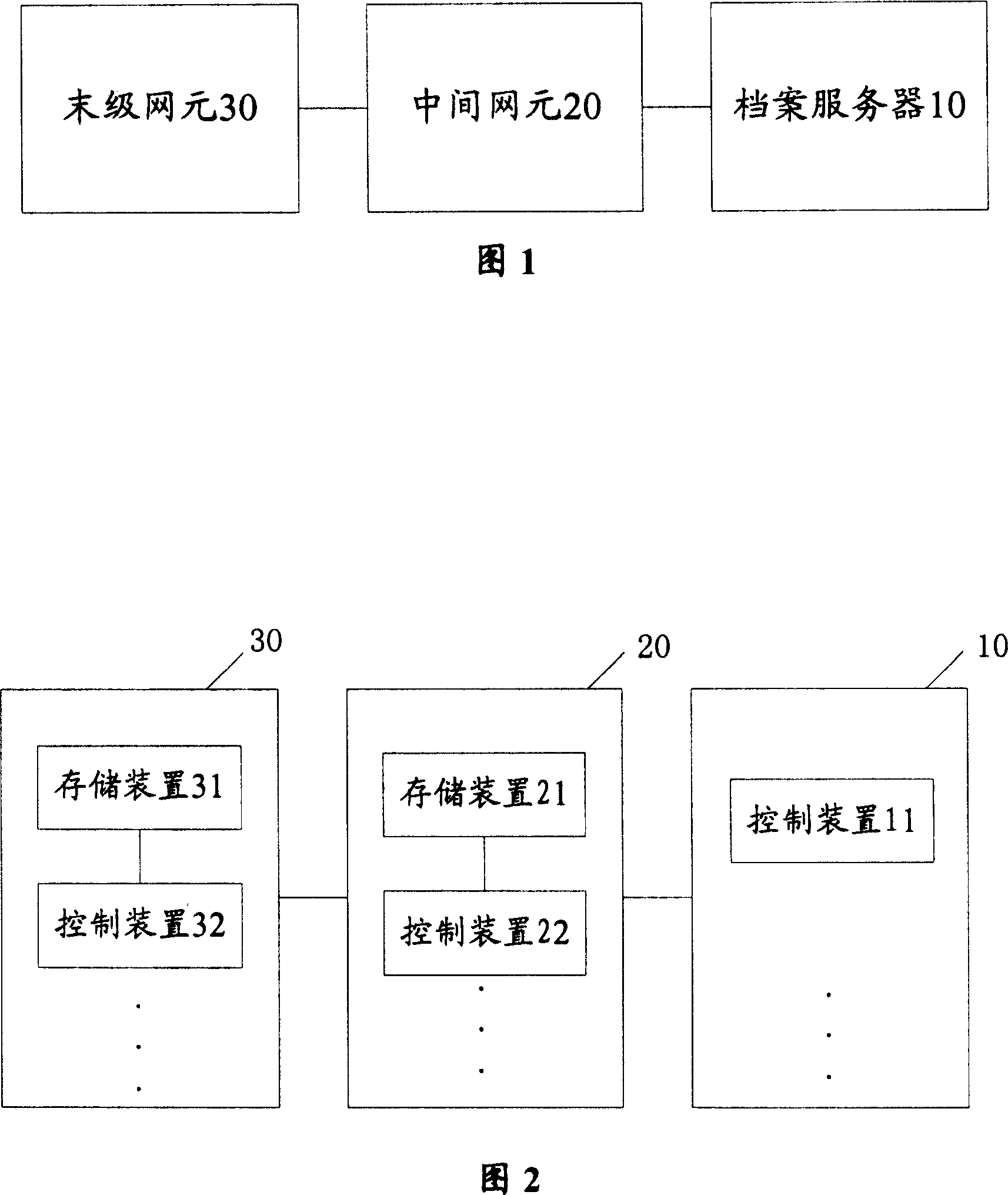
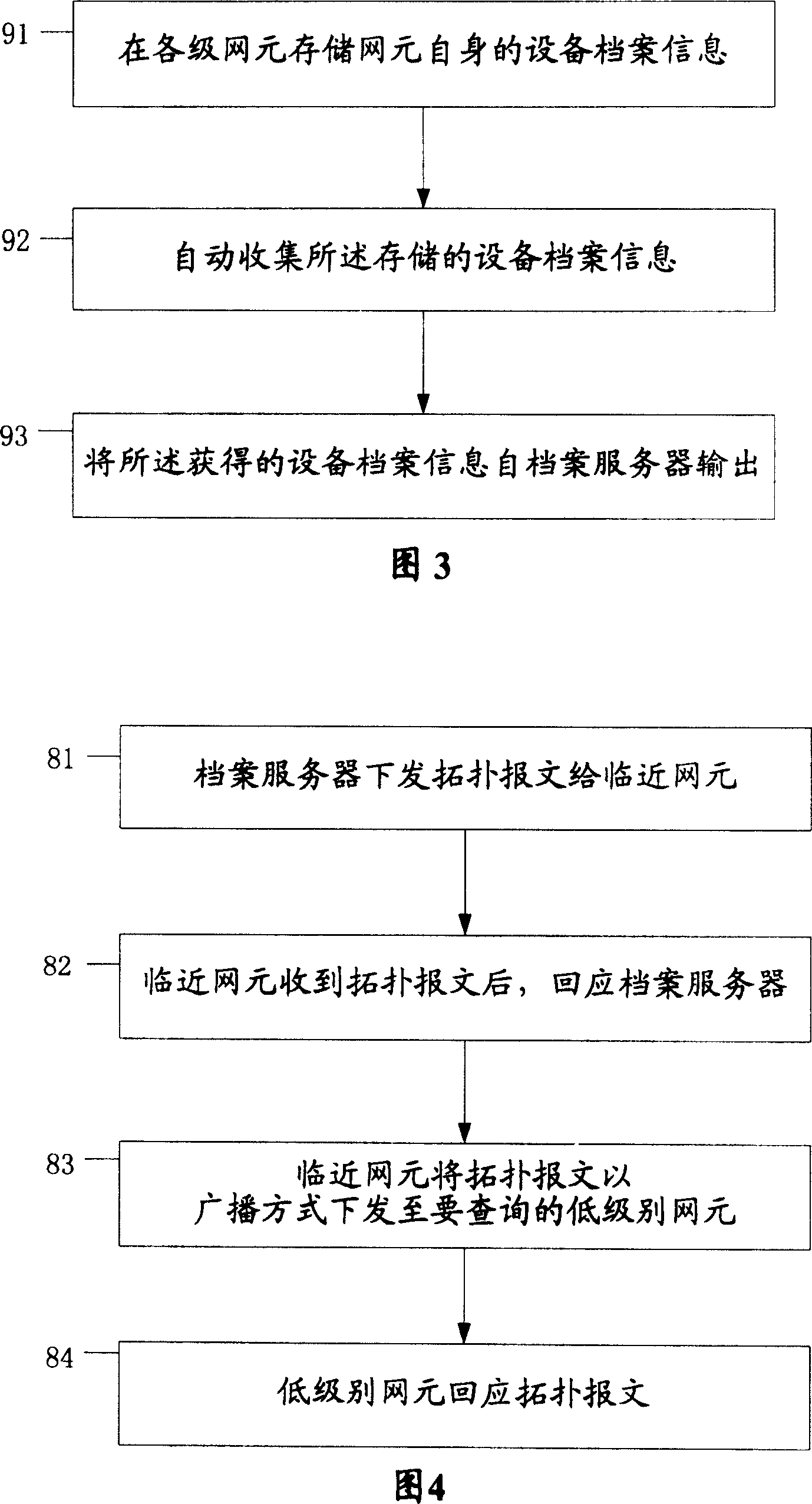
Management system and method for archives of equipment
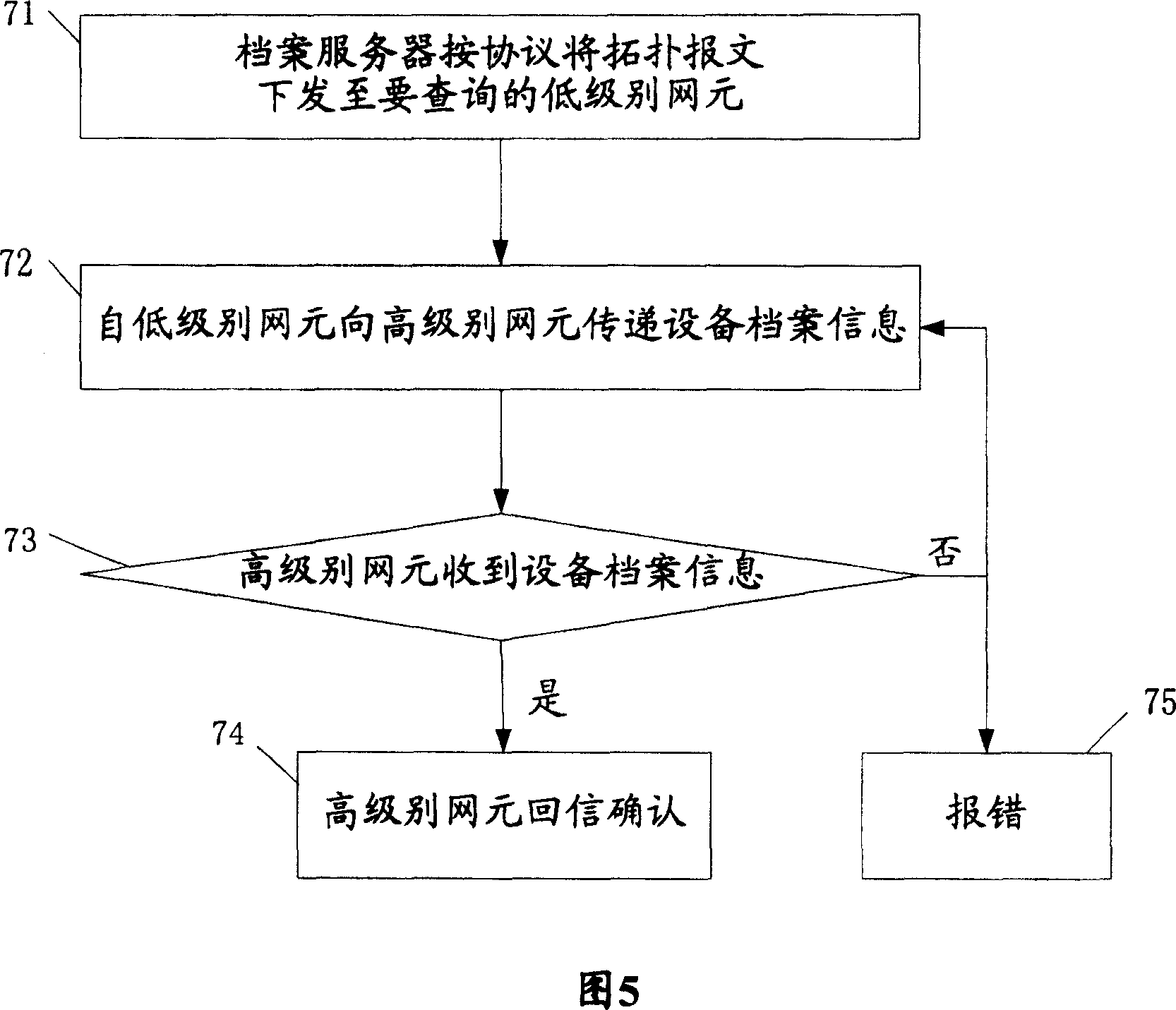
InactiveCN1661596ASimplify workGet running status in real timeSpecial data processing applicationsManagement systemNetwork element
The present invention provides an on-line equipment archive management system and its method. Said system includes network element capable of down-loading and storing equipment archive information by means of file mode and archive server connected with the described network element by adopting communication mode. Said equipment archive management method includes the following steps: storing equipment archive information in network element; the archive server gives out request message for obtaining equipment information; according to the request message the network element can send equipment archive information; then said archive server can output its obtained equipment archive information.
Owner:HUAWEI TECH CO LTD
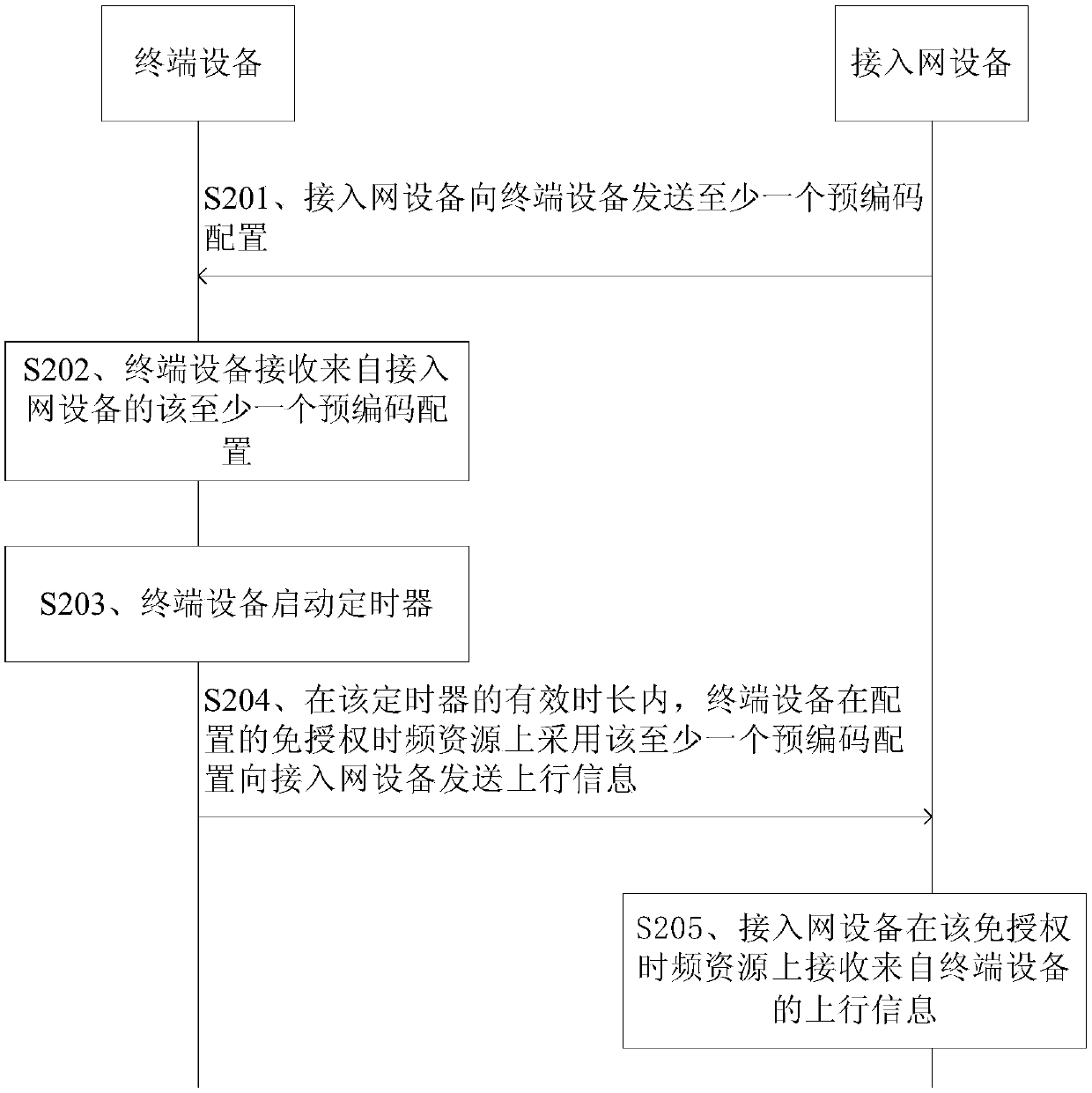
Information transmission method and device
ActiveCN110445521AValid duration is flexibleFlexible use timeRadio transmissionWireless communicationAccess networkInformation transmission
The embodiment of the invention provides an information transmission method and equipment. The method comprises the steps: receiving at least one precoding configuration from access network equipment,starting a timer, and transmitting uplink information to the access network equipment through employing the at least one precoding configuration on an unlicensed time-frequency resource in the effective duration of the timer. The embodiments of the present application can effectively avoid the inadaptation of precoding configuration caused by channel changes, thereby improving system performance.
Owner:HUAWEI TECH CO LTD
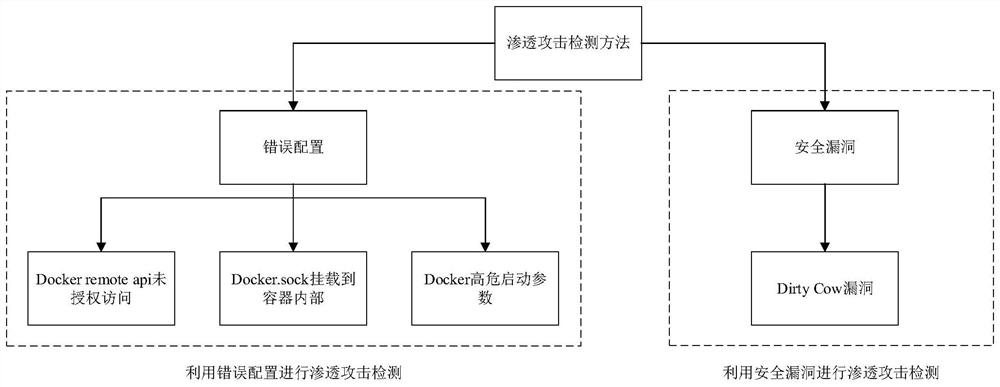
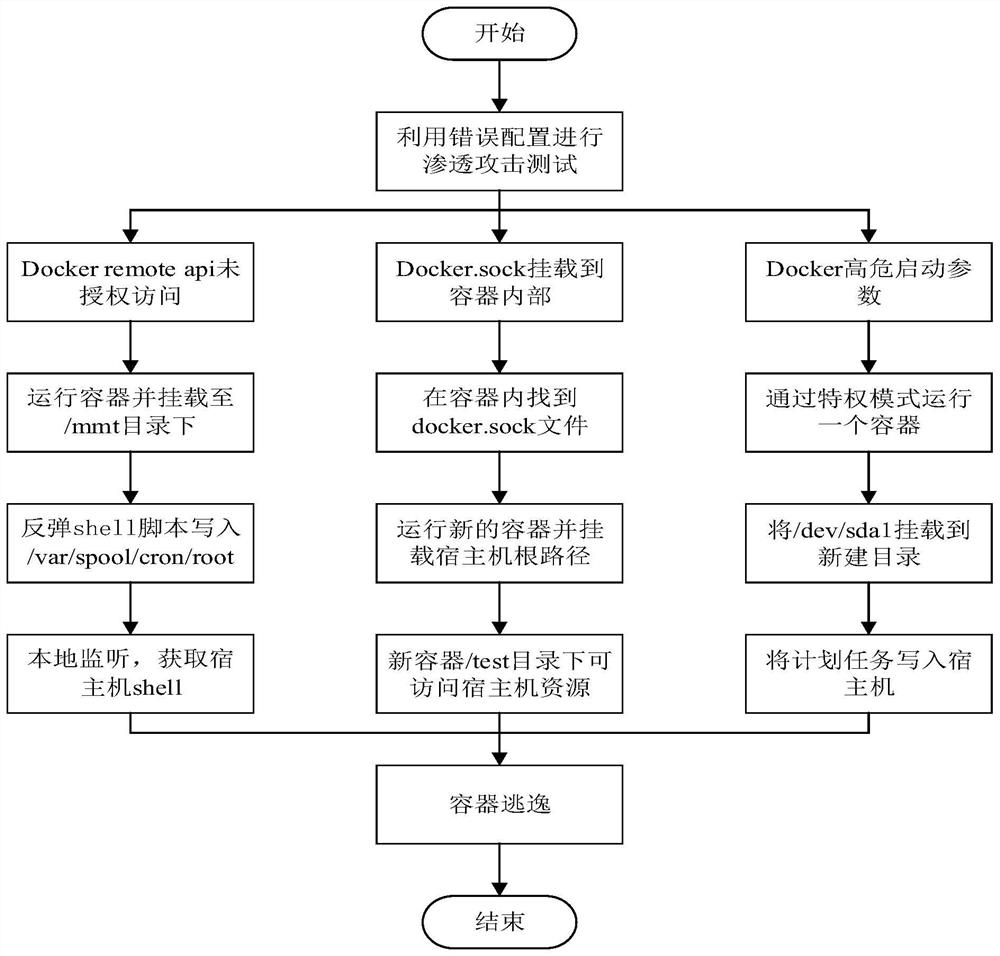
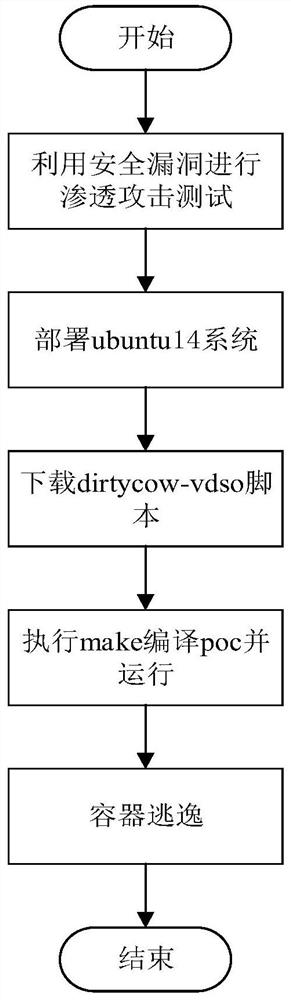
Penetration attack detection method for intelligent Internet of Things terminal container
PendingCN114547594AEasy to spot and fixPrevent escapePlatform integrity maintainanceSoftware simulation/interpretation/emulationComputer securitySecurity bug
The invention discloses a penetration attack detection method for an intelligent Internet of Things terminal container, which comprises the following steps of: 1) performing penetration attack on the container through security vulnerabilities, and detecting whether the container escapes or not; and 2) triggering escape of the container through wrong configuration, and performing penetration attack detection on the container. Through the penetration attack detection of the intelligent Internet of Things terminal container, the security problem of the container can be found in time, and the loss of a company caused by container escape due to wrong configuration and security vulnerabilities in the future is avoided; meanwhile, a safe use container manual can be made, wrong configuration of container escape caused by penetration attack is written, and the situation that the container escape is caused by wrong configuration in the container use process of a user is avoided; permeation attack detection is carried out on the container for many times, security problems caused by vulnerabilities are found in time, security threats faced by the container are analyzed, the container is prevented from external attacks, and safe and stable operation of a server is guaranteed.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +3
Zero-configuration system and method for network devices
ActiveUS9232410B2Shorten the timeQuick configurationNetwork topologiesDigital computer detailsNetwork terminationNetwork connection
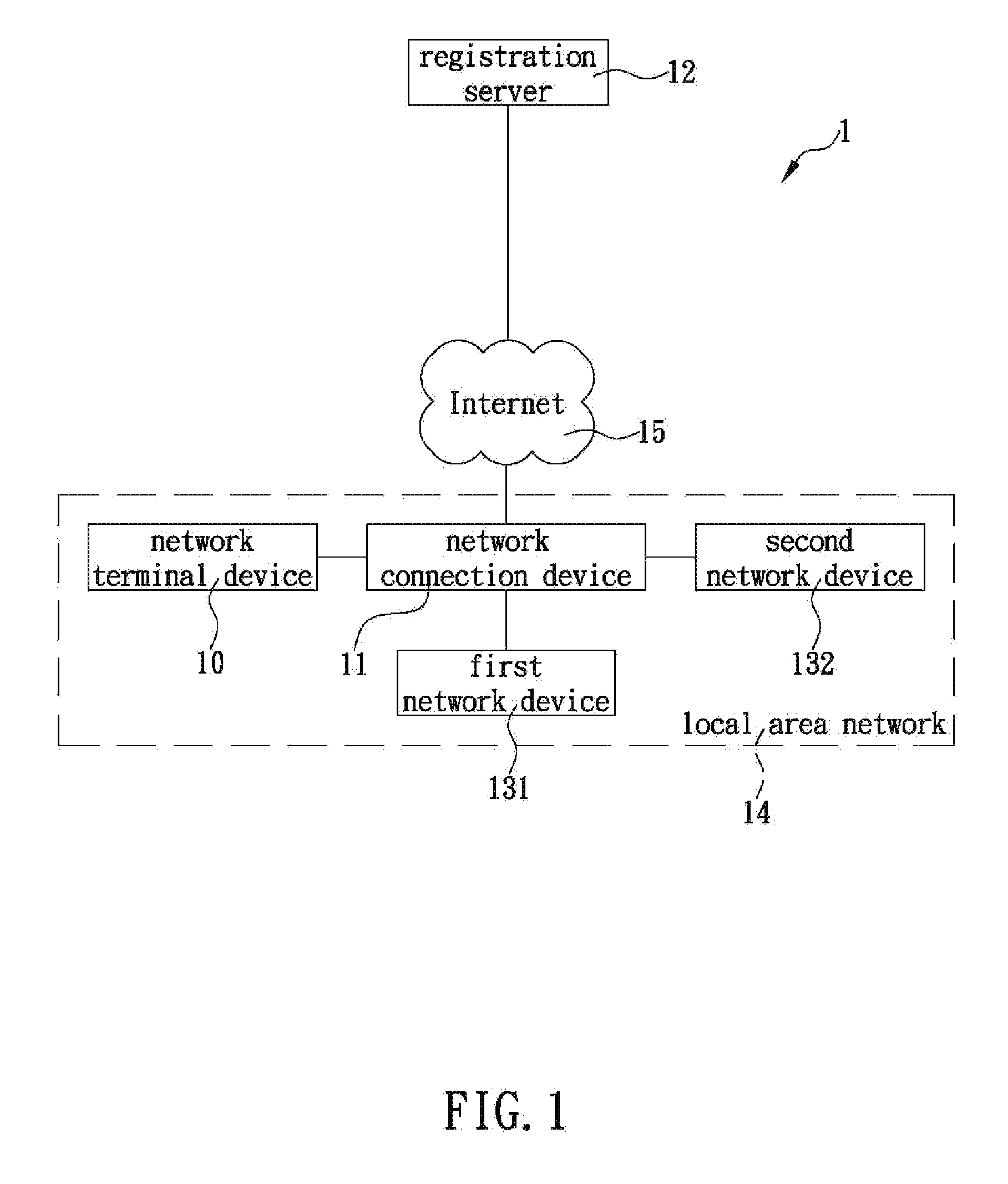
The present invention is a zero-configuration system including a registration server connecting (via the Internet) to a network terminal device through a network connection device, and a first network device located in a local area network same as the two devices and having a first identification name and a set of configuration values, wherein the registration server stores the first identification name corresponding to a user information. The network terminal device can login to the registration server by using the user information, and then scan the local area network and, when detecting a second network device having a second identification name not yet stored in the registration server, automatically receive the first identification name from the registration server, obtain the configuration values from the first network device, and configure the second network device according to the configuration values, so as to automatically connect to and access the second network device.
Owner:D-LINK
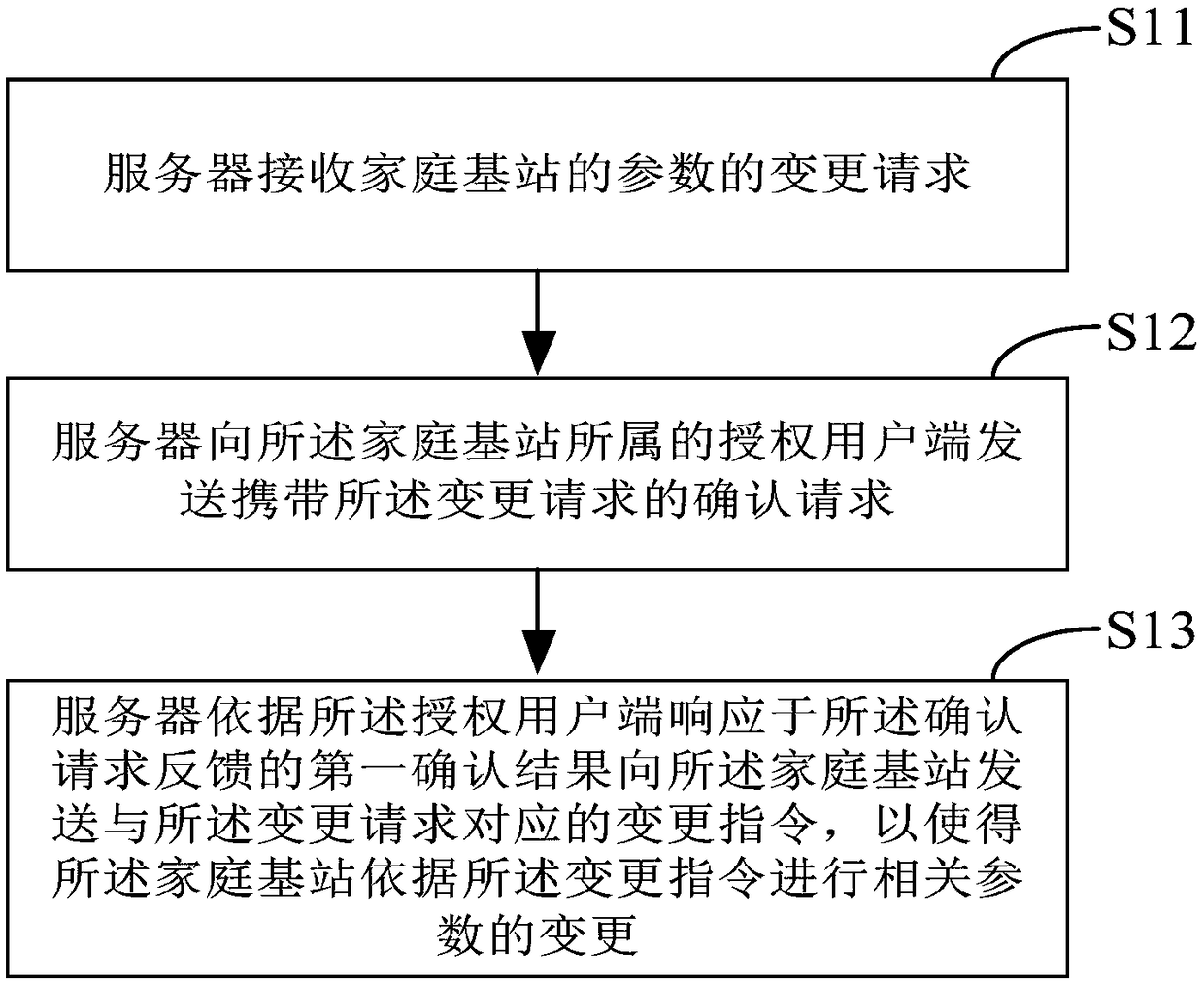
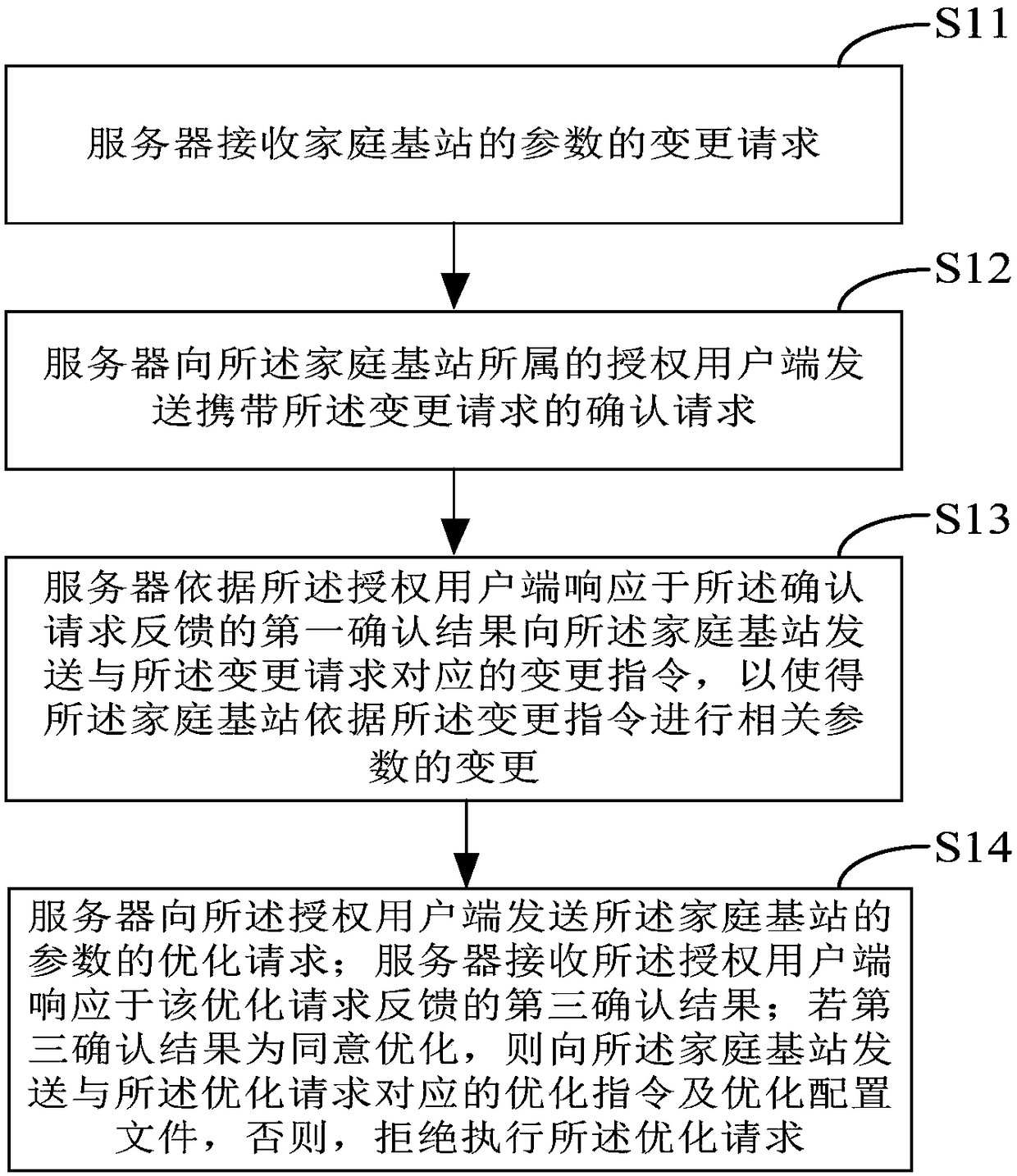
Method for preventing parameter of family base station from being tampered and family base station server
ActiveCN108235349AEnhanced anti-tamper securityConvenient open station configurationData switching networksWireless communicationMobile WebFemtocell
The invention provides a method for preventing a parameter of a family base station from being tampered. The method comprises the following steps that a server receives a change request of the parameter of the family base station; the server sends a confirmation request carrying the change request to an authorized user terminal to which the family base station belongs; and the server sends a change instruction corresponding to the change request to the family base station according to a first confirmation result fed back by the authorized user terminal in response to the confirmation request,so that the family base station changes the relevant parameter according to the change instruction. According to the method, an authorized user to which the family base station belongs participates inconfirming whether the relevant parameter of the family base station is changed and recovered, a function of carrying out optimization configuration on the family base station remotely is supported,and the anti-tamper safety of the parameter of the family base station is enhanced. The method and the family base station bring obvious technical advantages to the anti-tamper and recovery capabilityof the family base station and also bring the convenience to the maintenance of a mobile network.
Owner:COMBA TELECOM SYST CHINA LTD
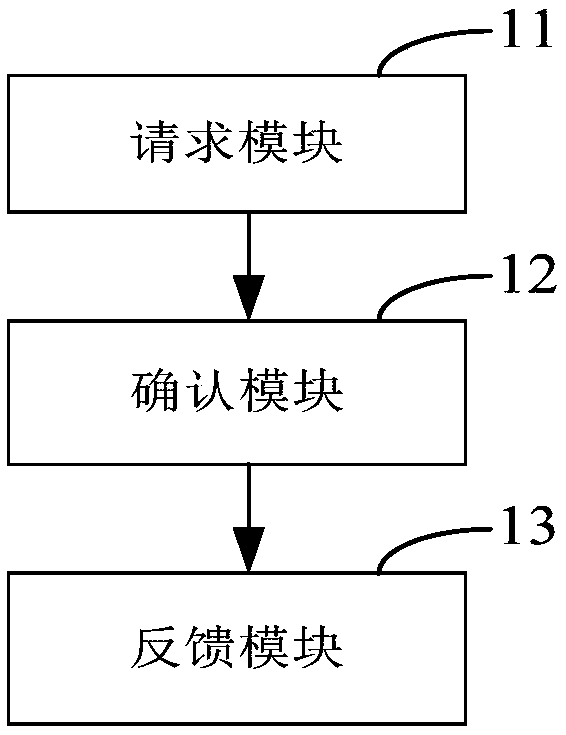
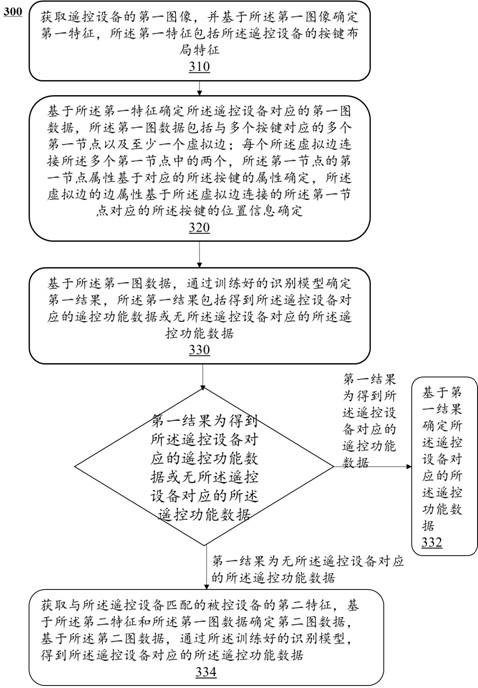
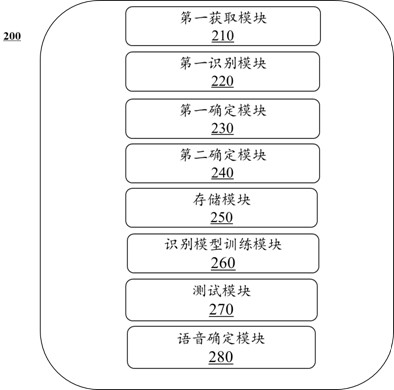
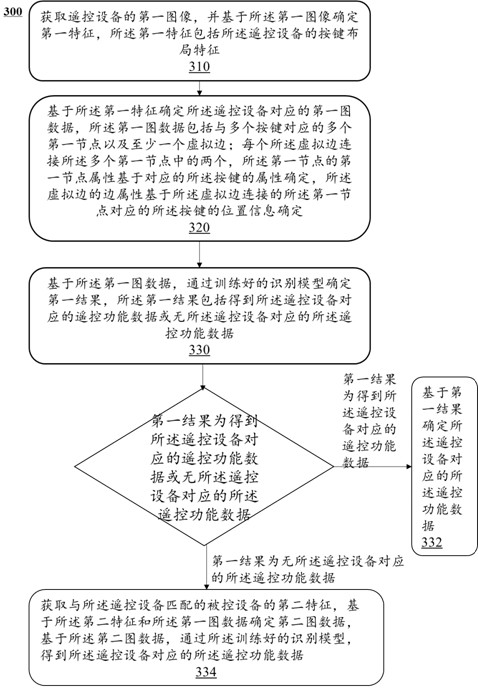
Method and system for configuring remote control function data according to image of remote control equipment
ActiveCN112085942AConvenient and accurate determinationImprove experienceNon-electrical signal transmission systemsTotal factory controlRemote controlEngineering
The embodiment of the invention provides a method and system for configuring remote control function data according to an image of remote control equipment. The method comprises the steps of obtaininga first image of the remote control equipment, and determining a first feature based on the first image, wherein the first feature comprises a key layout feature of the remote control equipment; anddetermining remote control function data corresponding to the remote control equipment based on the first feature. By identifying the image of the remote control equipment and determining the corresponding remote control function data according to the key feature layout, the remote control function data can be configured more conveniently and accurately, and the user experience is improved.
Owner:HANSONG NANJING TECH LTD
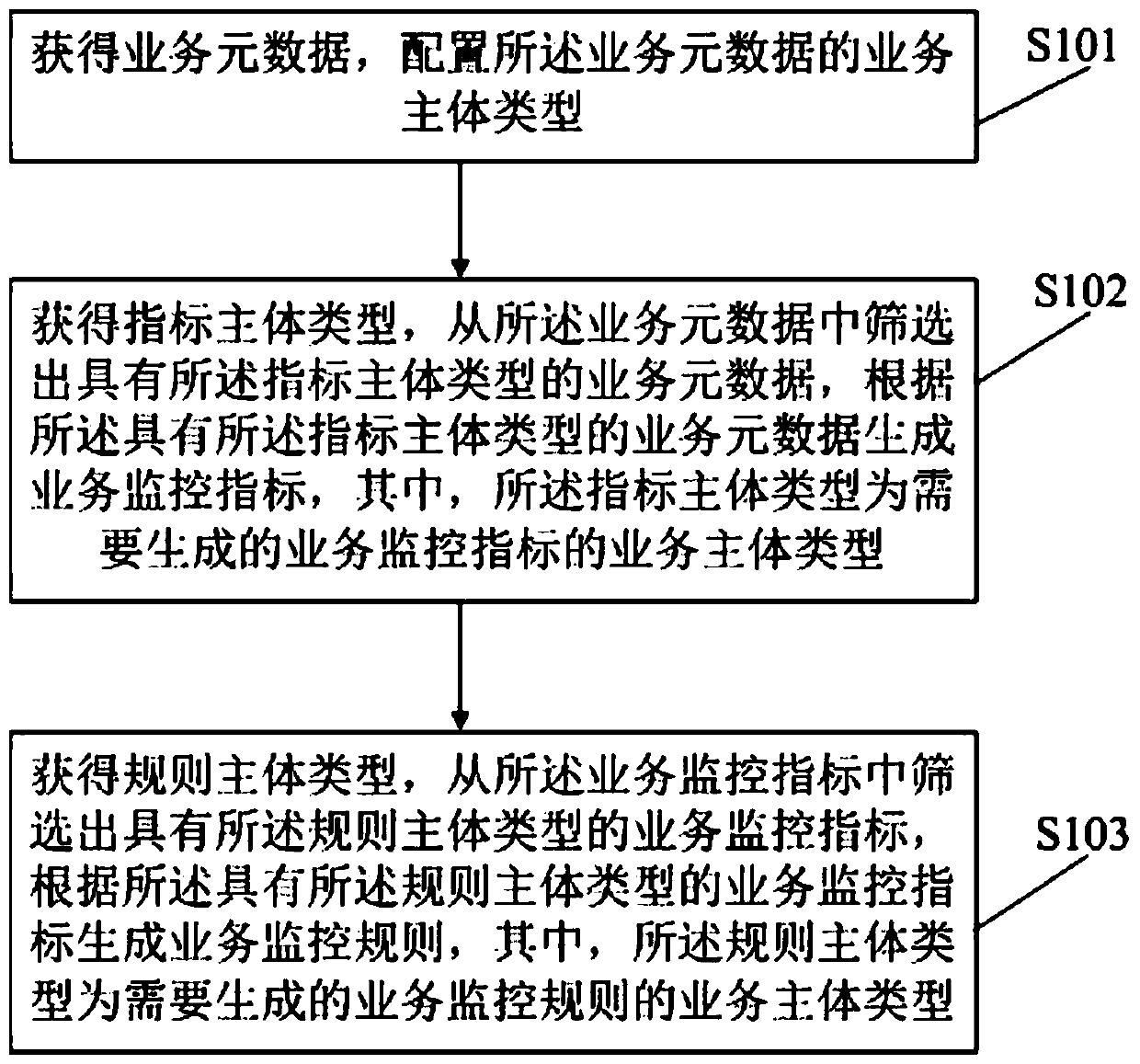
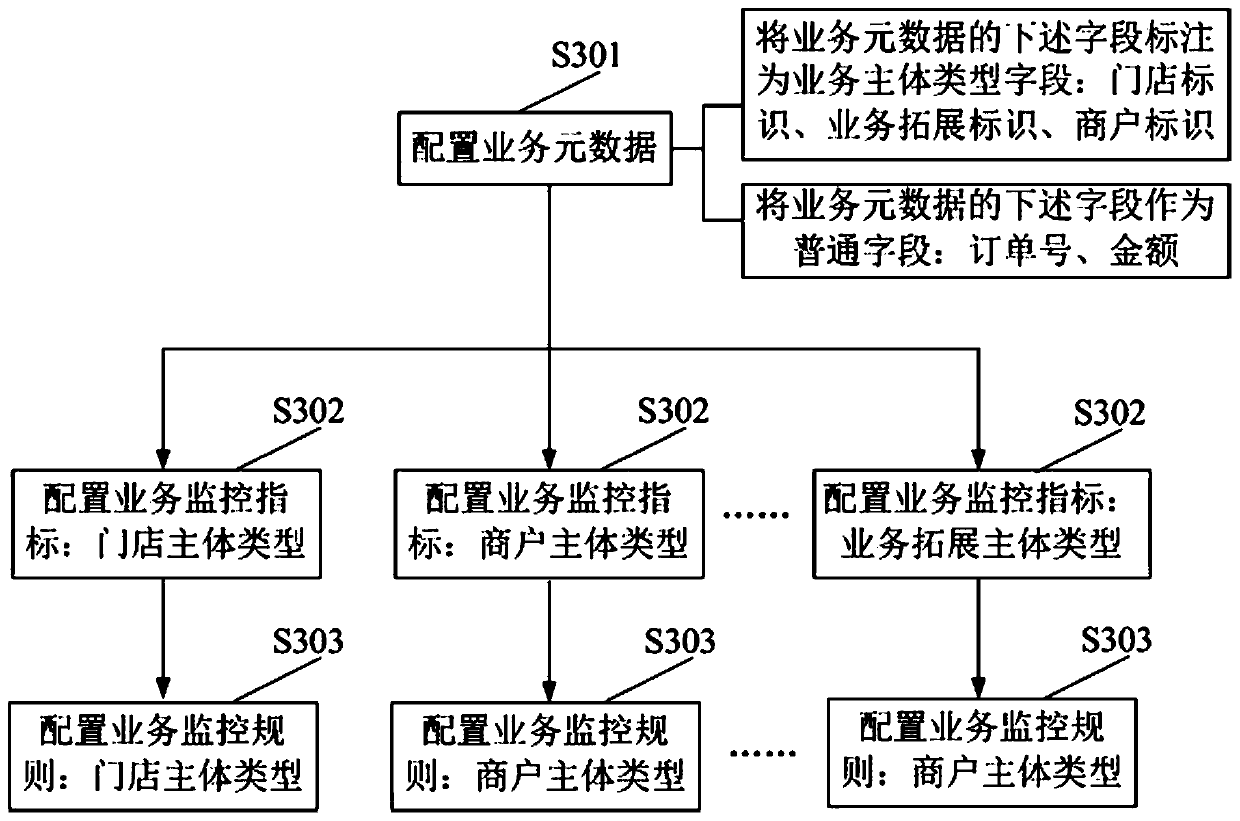
Business monitoring rule and business monitoring index generation method and device
InactiveCN110347713AAvoid misconfigurationResolve correctnessResourcesSpecial data processing applicationsMetadataBody type
The invention discloses a service monitoring rule generation method, which comprises the steps of obtaining service metadata, and configuring a service main body type of the service metadata; obtaining an index main body type, screening out service metadata with the index main body type from the service metadata, and generating a service monitoring index according to the service metadata with theindex main body type, the index main body type being a service main body type of a service monitoring index required to be generated; wherein the index body type is the type of a business body of a business monitoring index to be generated; obtaining a rule main body type, screening out business monitoring indexes with the rule main body type from the business monitoring indexes, and generating abusiness monitoring rule according to the business monitoring indexes with the rule main body type, the rule main body type being the business main body type of the business monitoring rule needing tobe generated. By adopting the method to correctly configure the service monitoring rules, the introduction of wrong configuration is avoided.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
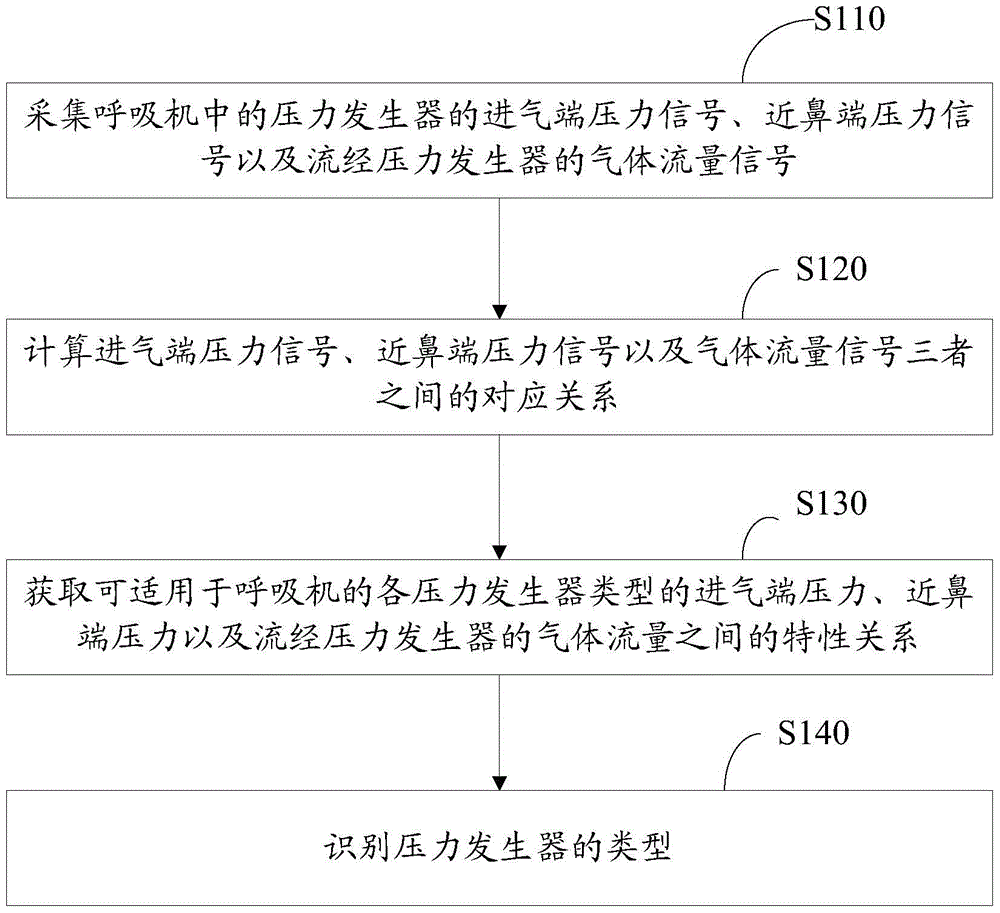
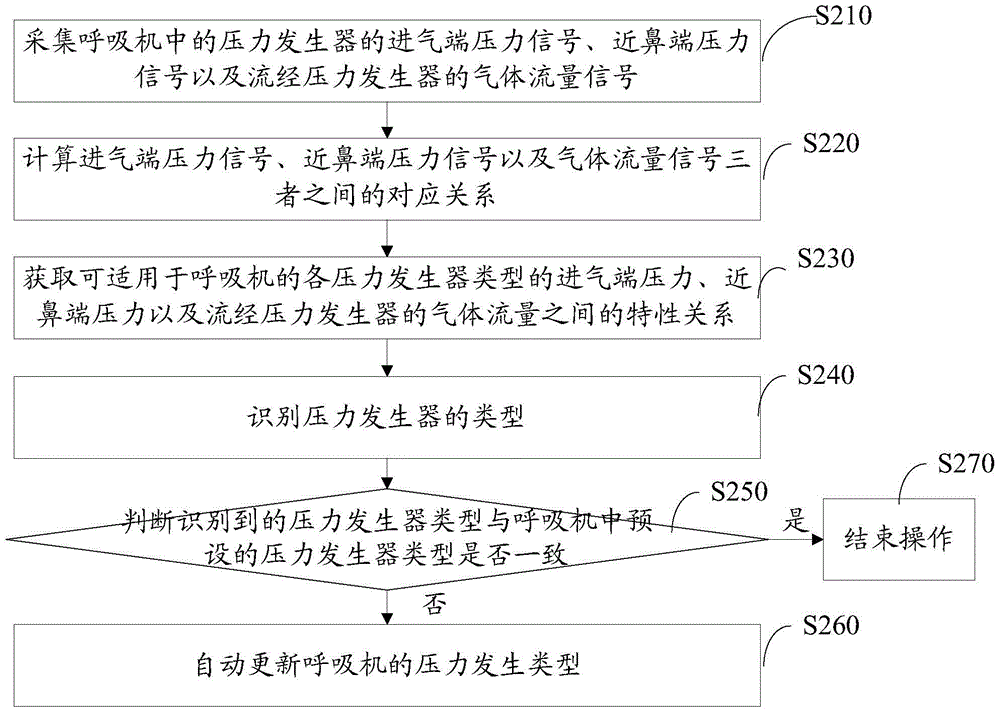
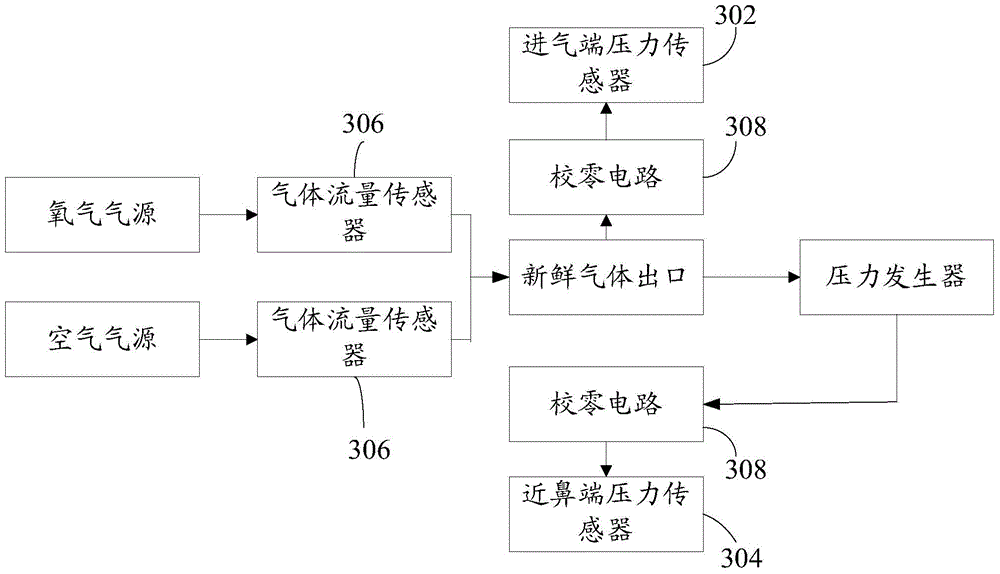
Pressure generator type identification method and device
ActiveCN104623777BRealize automatic and accurate identificationAccurate settingRespiratorsRespiratorIdentification device
The invention discloses a pressure generator type recognition method. The method includes the steps of acquiring a pressure signal of an intake end of a pressure generator in a respirator, a pressure signal of an adnasal end of the pressure generator and a flow signal of gas flowing by the pressure generator; calculating a correspondence of the signals; acquiring feature relations among the intake end pressures and adnasal end pressures of various pressure generators, suitable for the respirator, and the flows of gas flowing by the pressure generators; comparing the correspondence with the feature relations of the pressure generators so as to determine the types of the pressure generators. The pressure generator type recognition method and device has the advantages that medical staff can directly use recognition results to accurately set the types of the pressure generators in the respirator, mistaken setting caused by the fact that the medical staff is not familiar with the types of the pressure generators in the respirator and safety is high. The invention further discloses the pressure generator type recognition device.
Owner:SHENZHEN COMEN MEDICAL INSTR +1
Management system and method for archives of equipment
InactiveCN100365623CGuaranteed correctnessAvoid misconfigurationSpecial data processing applicationsManagement systemNetwork element
The present invention provides an on-line equipment archive management system and its method. Said system includes network element capable of down-loading and storing equipment archive information by means of file mode and archive server connected with the described network element by adopting communication mode. Said equipment archive management method includes the following steps: storing equipment archive information in network element; the archive server gives out request message for obtaining equipment information; according to the request message the network element can send equipment archive information; then said archive server can output its obtained equipment archive information.
Owner:HUAWEI TECH CO LTD
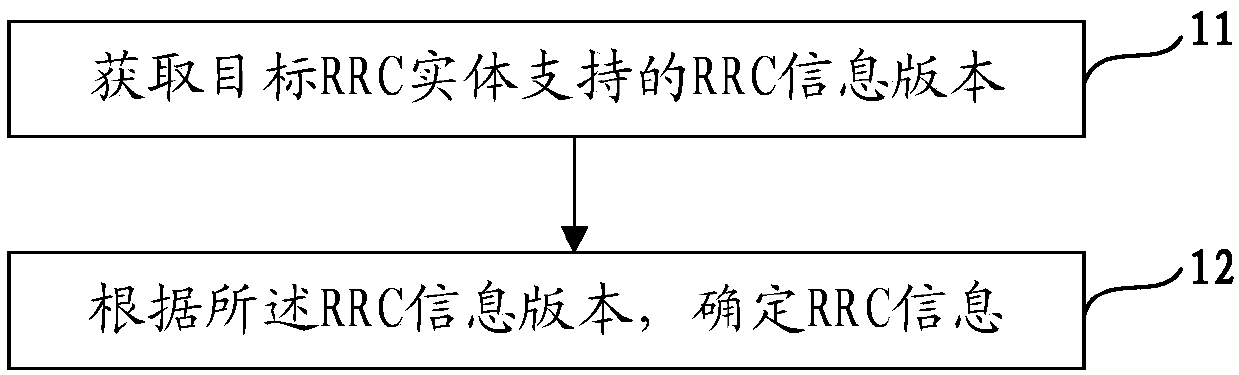
Coordination method of radio resource control (RRC) information version and network equipment
The invention provides a coordination method for a radio resource control (RRC) information version and network equipment, and the method comprises the steps: obtaining the RRC information version supported by a target RRC entity, wherein the target RRC entity is an entity for carrying out the radio resource control of a radio link control (RLC) entity in a second node; and determining RRC information according to the RRC information version. According to the invention, different nodes can understand the RRC information version supported by the RRC entity of the opposite side, and wrong configuration is avoided.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Functional contactor
ActiveCN109075483AMake sure the whole columnPrevent inflowElectrostatic discharge protectionScreening gaskets/sealsElectrical conductorEngineering
A functional contactor is provided. The functional contactor according to an exemplary embodiment of the present invention comprises: a conductive elastic portion having elasticity and electrically contacting a conductor of an electronic device; and a functional element including a first electrode electrically connected to a circuit board or a conductor of the electronic device, and a second electrode on which the conductive elastic portion is laminated through a solder. The second electrode includes a stopper in which an electrode is not formed to prevent a solder from being introduced into the periphery of a lamination area on which the conductive elastic portion is laminated.
Owner:AMOTECH
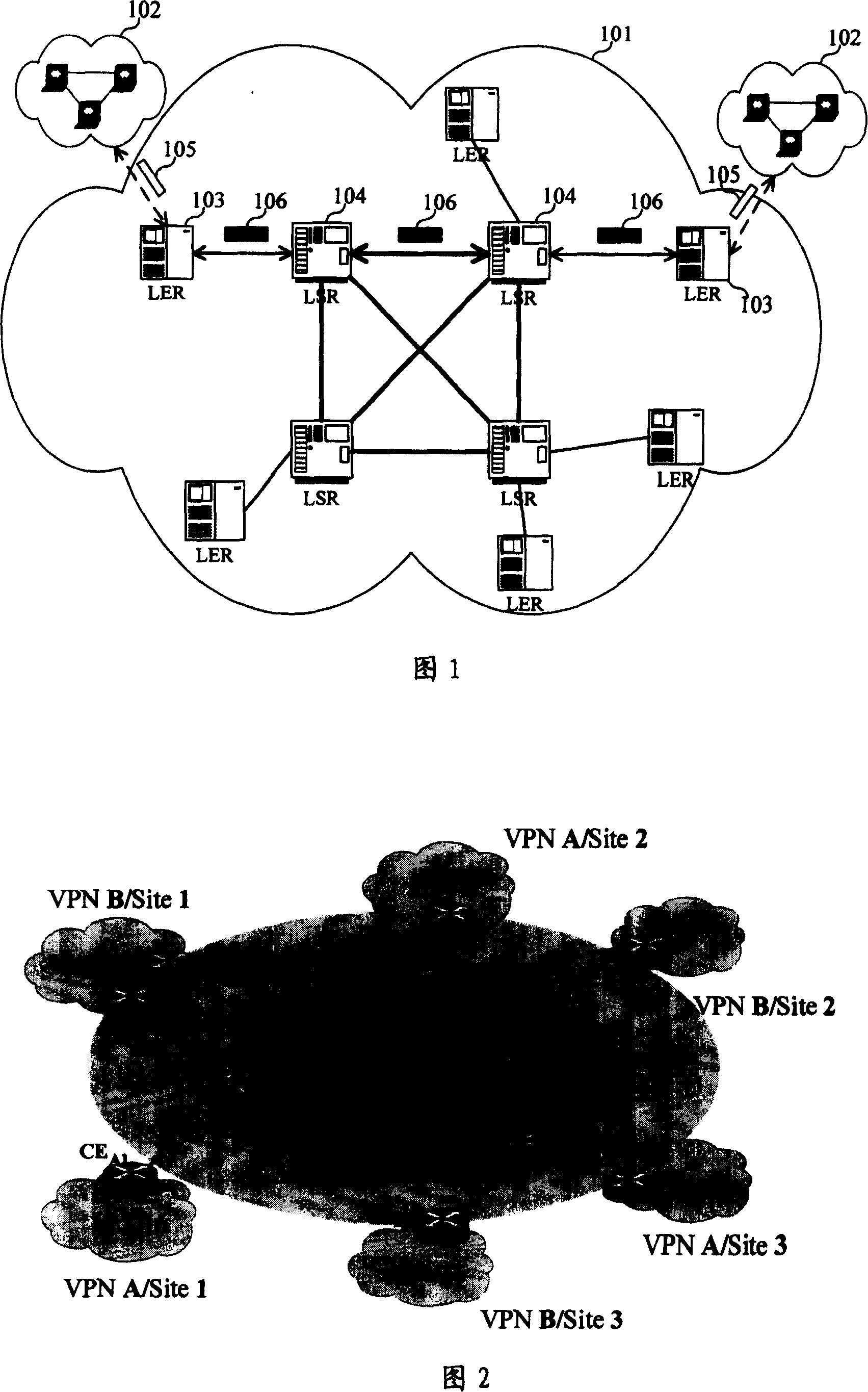
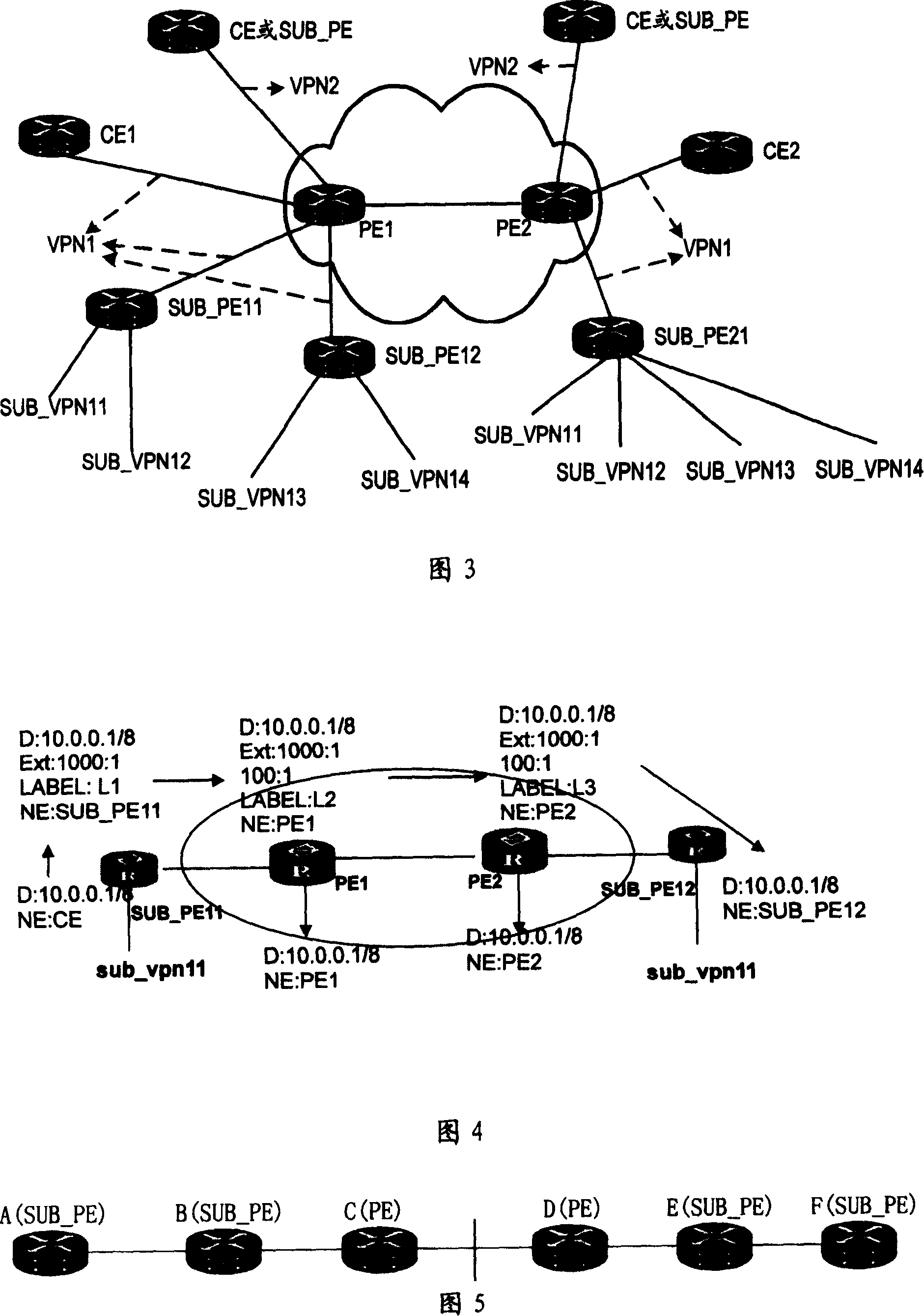
MPLS VPN and its control and forwarding method
ActiveCN100372336CAvoid misconfigurationAvoid security issuesNetworks interconnectionPrivate networkMPLS VPN
The present invention discloses a Virtual Private Network (VPN), which includes: a Sub-Provider Edge (SUB_PE), configured in a customer's network and connected with a PE in a provider's network; at least one SUB_VPN belonging to a same customer is configured under the SUB_PE and accesses the provider's network through the SUB_PE. The present invention also discloses a method for controlling and forwarding route of the VPN, including: an SUB_PE or a PE adds an export target attribute of the VPN where it is located to the route before transmitting; after receiving the route, the SUB_PE or the PE compares the export target attribute in the route with the import target attribute saved by itself, if they match, accept the route and forward it to a lower layer VPN; otherwise, reject the route.
Owner:HUAWEI TECH CO LTD
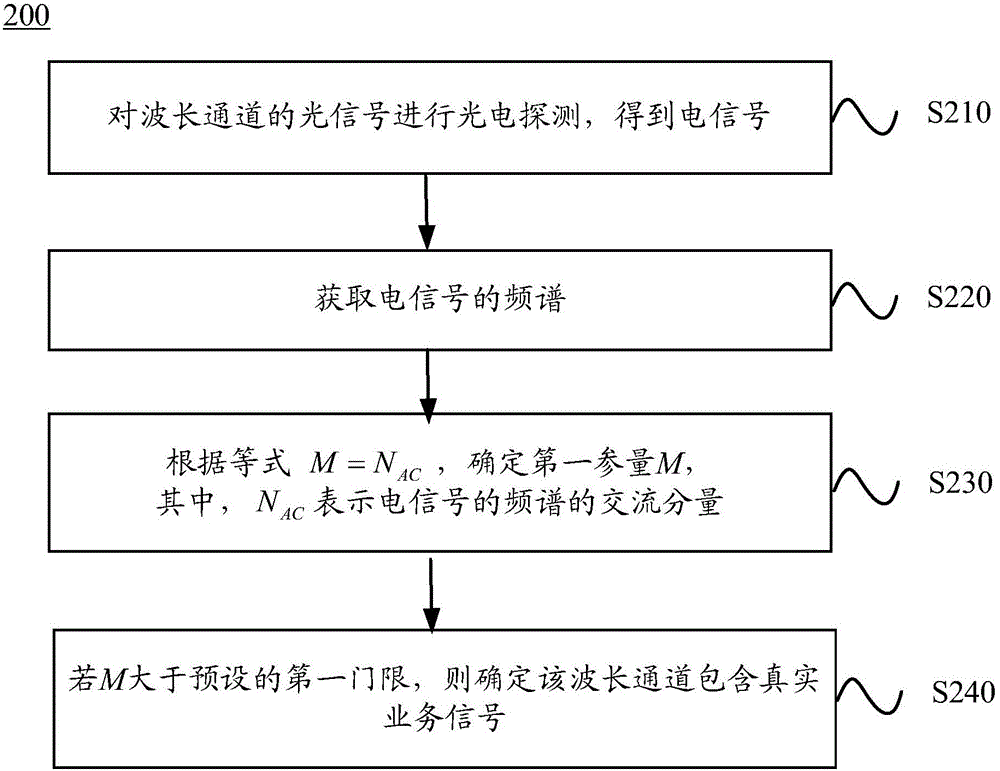
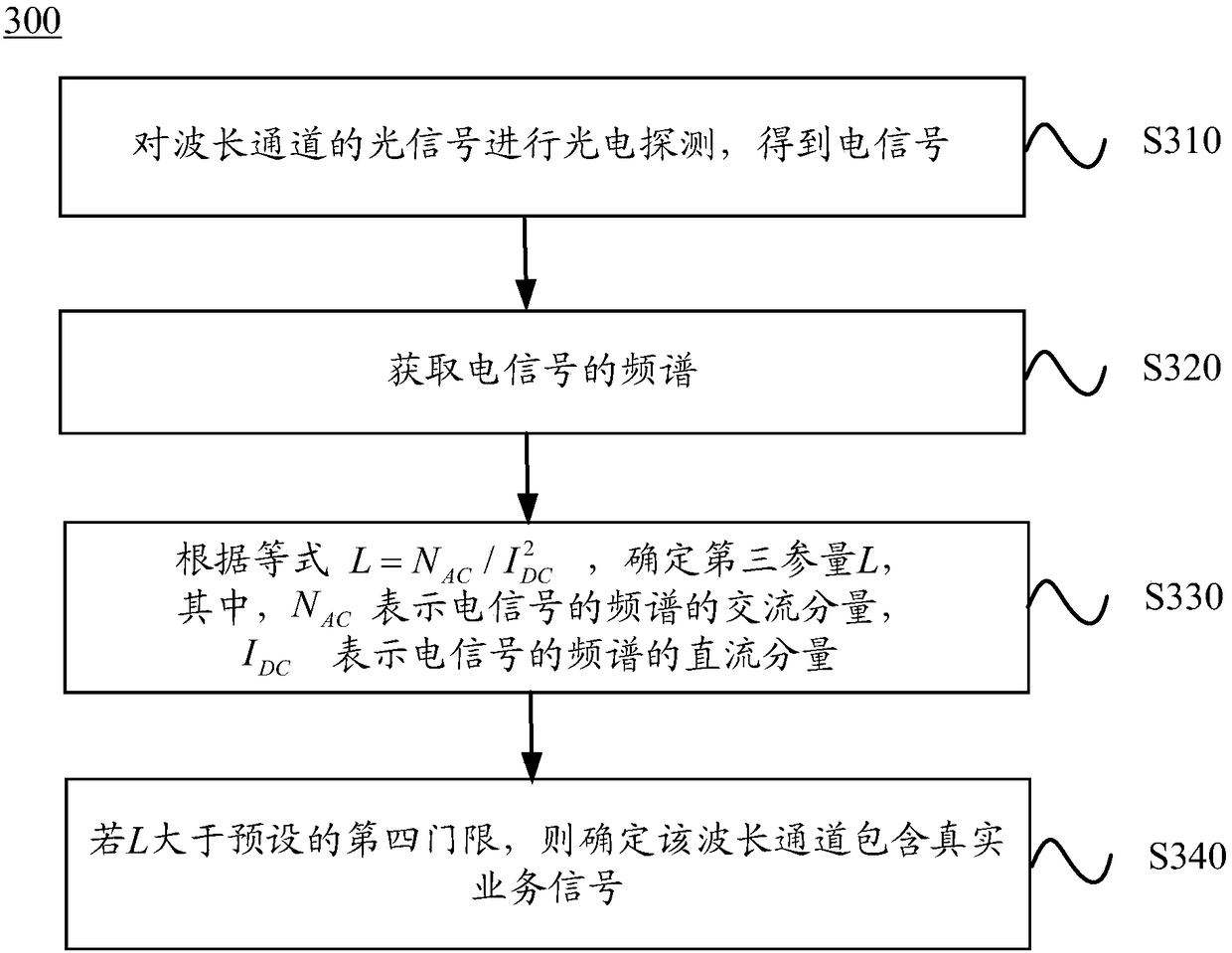
Method and device detecting wavelength channel
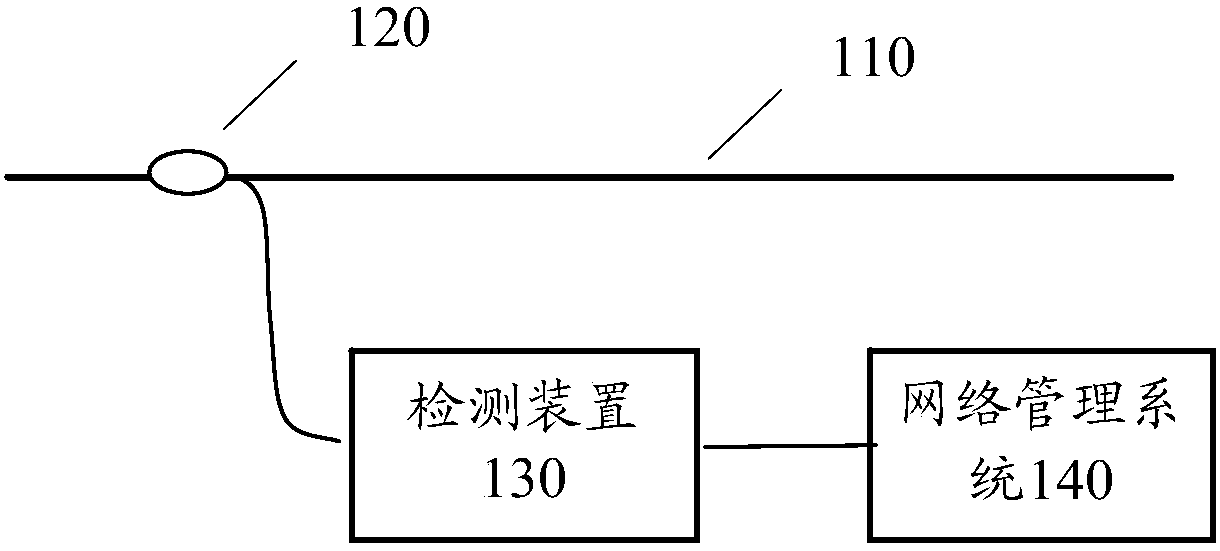
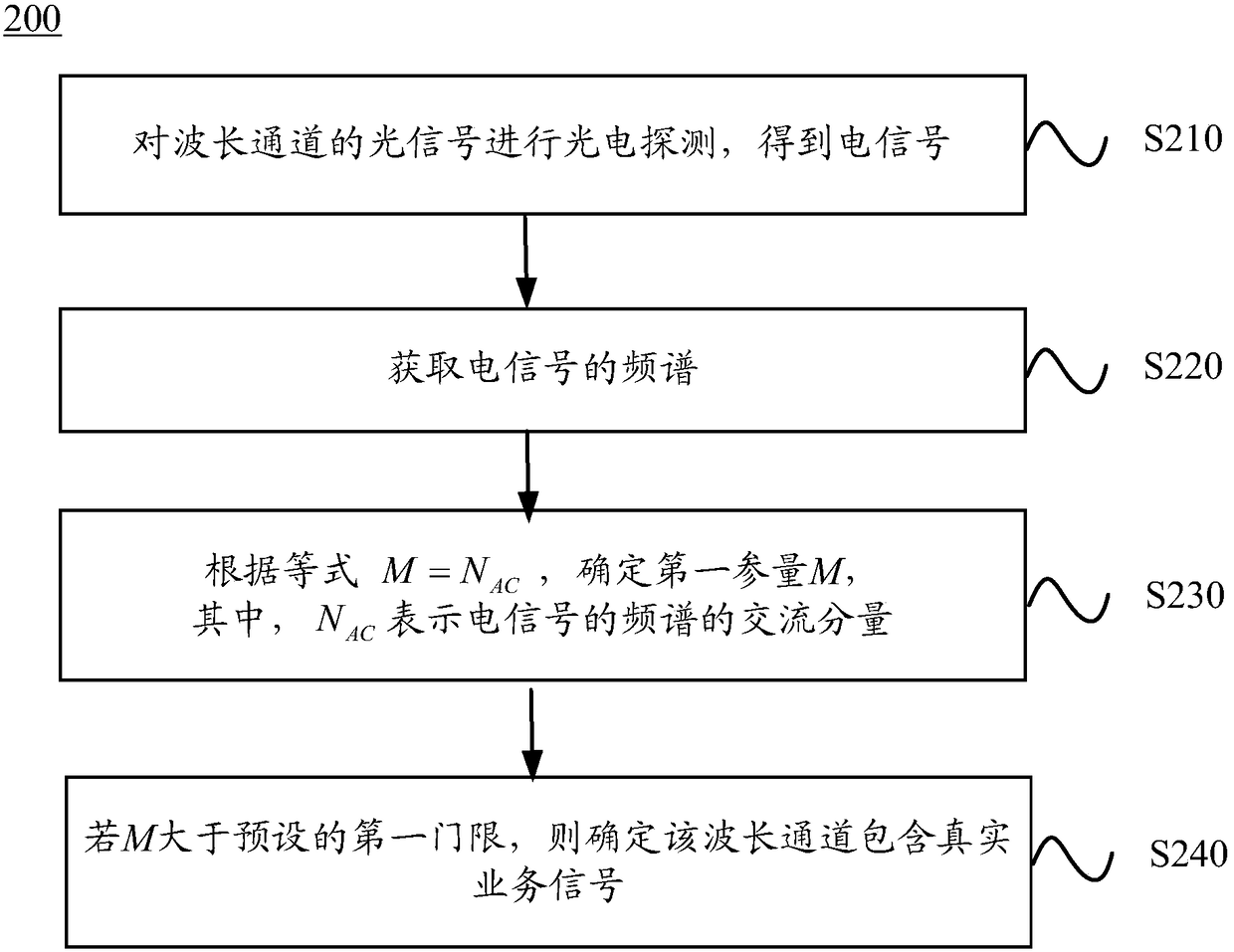
ActiveCN105899267AAvoid misconfigurationEntertainmentWavelength-division multiplex systemsFrequency spectrumNetwork management
The invention discloses a method and device detecting a wavelength channel; the method comprises the following steps: carrying out photoelectric detection for light signals of the wavelength channel, thus obtaining an electric signal; obtaining frequency spectrum of the electric signal; determining a first parameter M according to the equation M-NAC, wherein the NAC represents AC component of the frequency spectrum of the electric signal; determining the wavelength channel to contain a real business signal if the M is bigger than a preset first threshold. The method and device can prevent wrong configuration or operation of a network management system.
Owner:HUAWEI TECH CO LTD
Method and device for service configuration in network cutover
ActiveCN105099786BShort timeImprove efficiencyData switching networksInformation networksEngineering
Owner:HUAWEI TECH CO LTD
A blockchain interface configuration method based on communication security authentication
ActiveCN111327457BGuaranteed stabilityImprove securityUser identity/authority verificationCommunications securitySecurity authentication
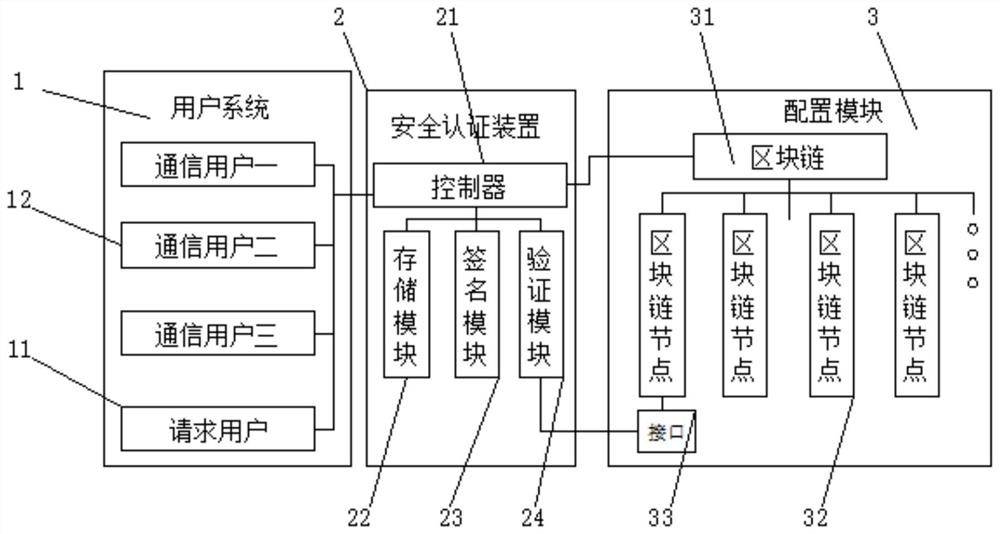
The invention discloses a block chain interface configuration method based on communication security authentication. Communication user, the security authentication device includes a controller, a storage module, a signature module and a verification module, the controller, storage module, signature module and verification module are connected in parallel with the controller, and the configuration module includes a block chain and a block chain The blockchain node is connected to the blockchain in parallel. By connecting the user system to the security authentication device, the communication request can be signed and authenticated. At the same time, the blockchain node is generated through the blockchain to connect the two users separately. , thereby avoiding configuration disorder, ensuring the stability of communication, and effectively improving communication security, effectively improving communication efficiency and information security, and facilitating use and promotion.
Owner:山东公链信息科技有限公司
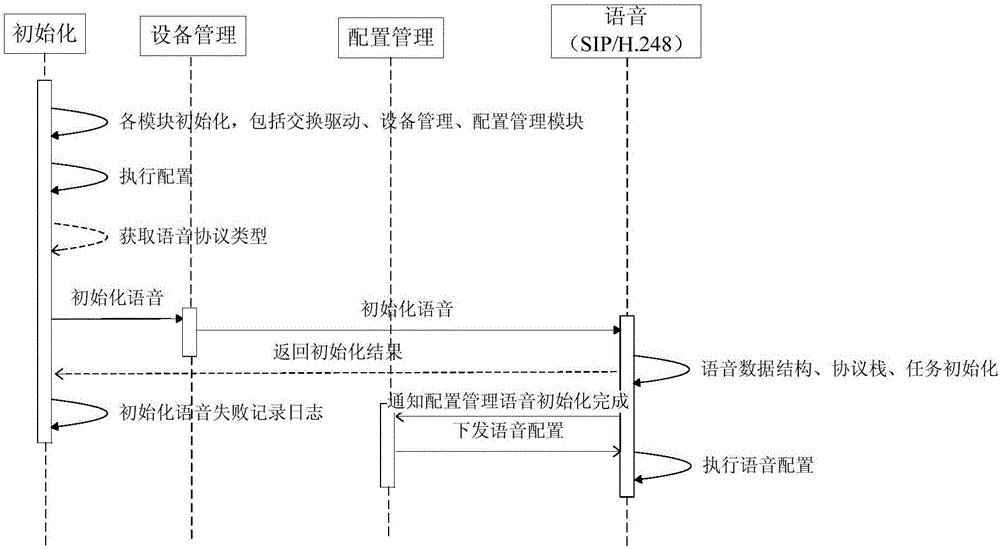
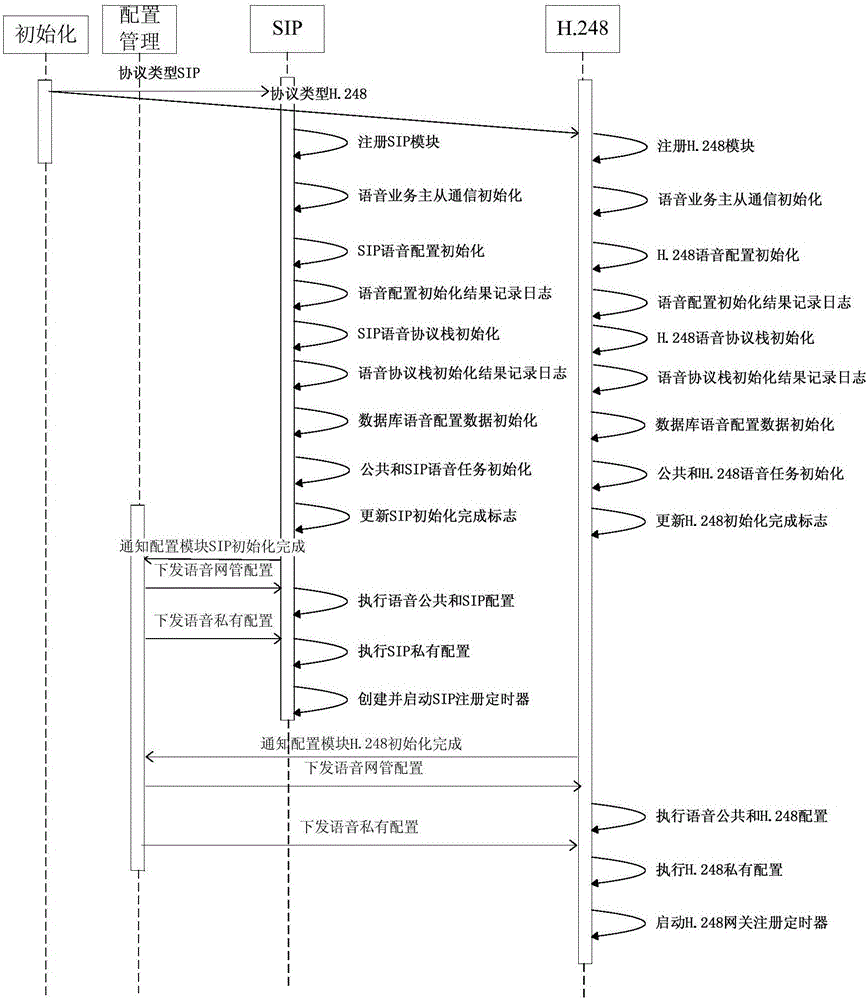
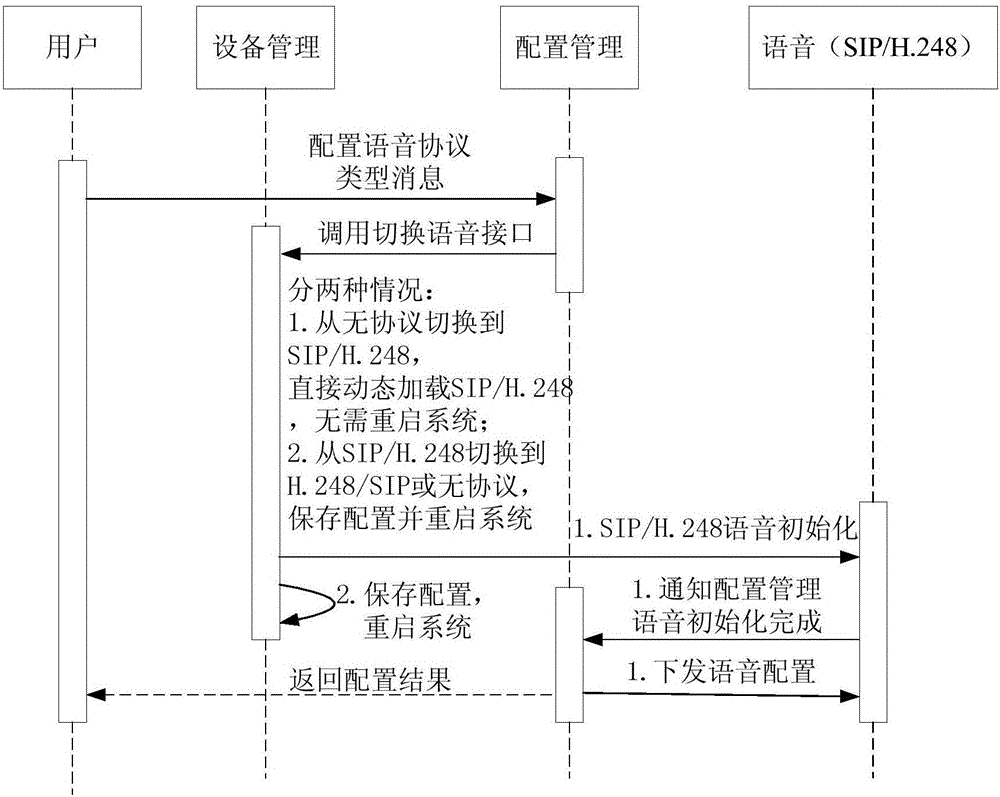
Achievement method of dynamic loading of PON supported voice bi-protocols
InactiveCN106790229AReduce activationReduce maintenance costsMultiplex system selection arrangementsData switching networksComputer hardwareComputer science
The invention discloses an achievement method of dynamic loading of PON supported voice bi-protocols. The method comprises the following steps that a device management module and a configuration management module of an ONU are initialized, and configuration files of the modules are executed after initialization is completed; according to a voice protocol type obtained from the configuration management module, a corresponding voice initialization interface encapsulated by the device management module is called, and a corresponding voice module is loaded and initialized; the configuration management module is informed of initialization completion, and voice configuration issued by the configuration management module is received and executed. Dynamic voice protocol loading is performed in a configuration voice protocol type, selection of the voice protocol type is clearly designated by a user, wrong configuration is avoided, the operation of updating ONU software version to switch voice protocols is omitted, the operating efficiency is improved, and project starting and maintaining costs are reduced.
Owner:FENGHUO COMM SCI & TECH CO LTD
A method and system for configuring remote control function data according to images of remote control devices
ActiveCN112085942BConvenient and accurate determinationImprove experienceNon-electrical signal transmission systemsTotal factory controlKey pressingRemote control
The embodiment of this specification provides a method and system for configuring remote control function data according to an image of a remote control device, including: acquiring a first image of a remote control device, and determining a first feature based on the first image, and the first feature includes the The button layout feature of the remote control device; determine the remote control function data corresponding to the remote control device based on the first feature. By identifying the image of the remote control device and determining the corresponding remote control function data according to the characteristic layout of the keys, it is possible to more conveniently and accurately configure the remote control function data and improve user experience.
Owner:HANSONG NANJING TECH LTD
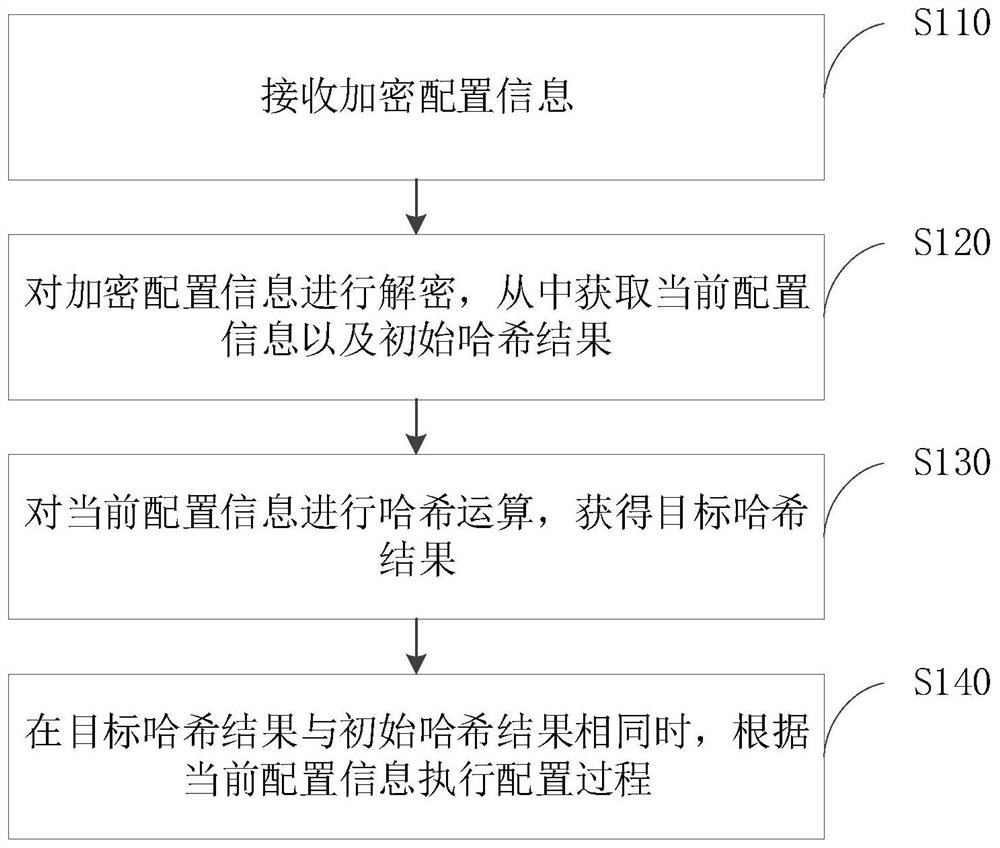
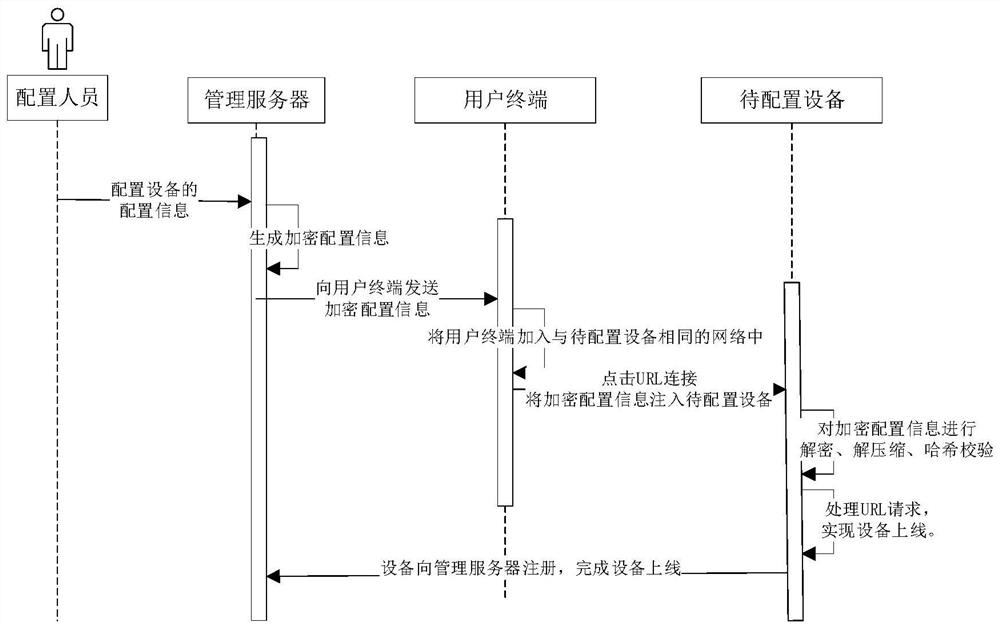
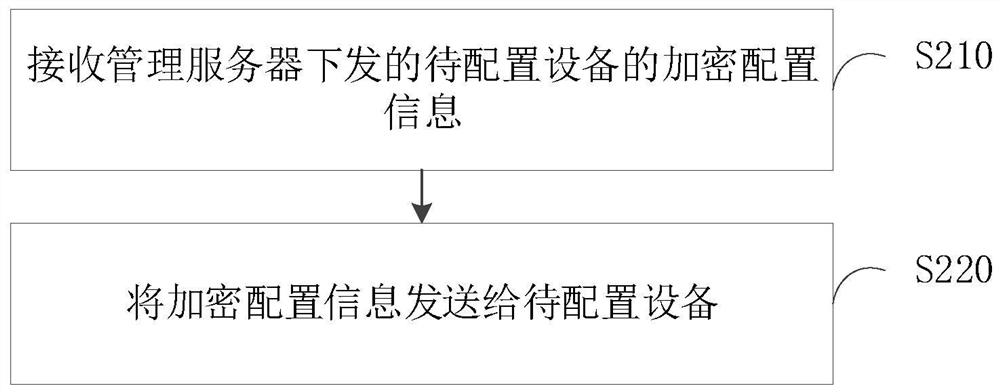
Equipment configuration method, system and device, electronic equipment and storage medium
PendingCN114301774AAvoid misconfigurationDigital data protectionSecuring communicationComputer hardwareOperating system
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Data acquisition method, device and equipment, and storage medium
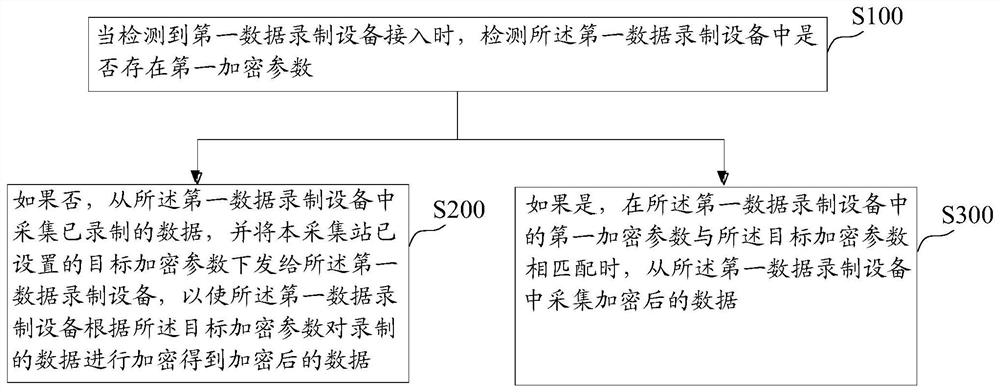
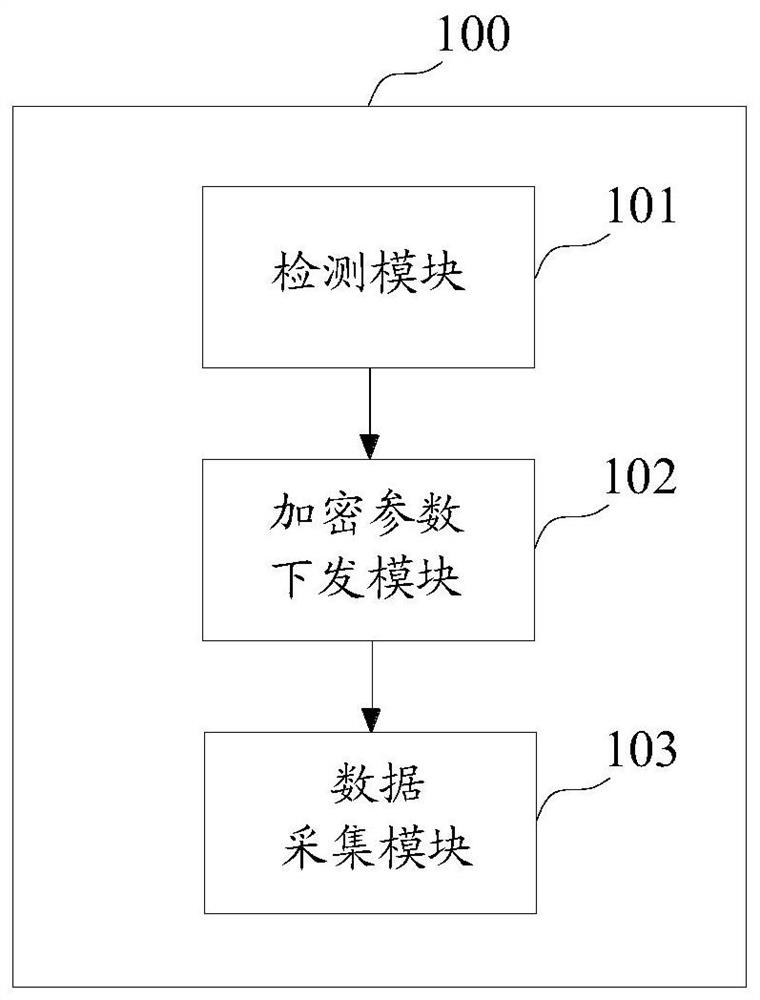
ActiveCN112911342AGuaranteed compatibilityAvoid misconfigurationTelevision system detailsColor television detailsData acquisitionEngineering
The invention provides a data collection method, device and equipment and a storage medium, and improves data security. The method is applied to an acquisition station, and comprises the following steps: when it is detected that first data recording equipment is accessed, detecting whether a first encryption parameter exists in the first data recording equipment or not; if not, acquiring data from the first data recording equipment, and issuing a target encryption parameter set by the acquisition station to the first data recording equipment, so that the first data recording equipment encrypts the recorded data according to the target encryption parameter to obtain encrypted data; if yes, when a first encryption parameter in the first data recording equipment is matched with the target encryption parameter, acquiring encrypted data from the first data recording equipment.
Owner:HANGZHOU HIKVISION DIGITAL TECH
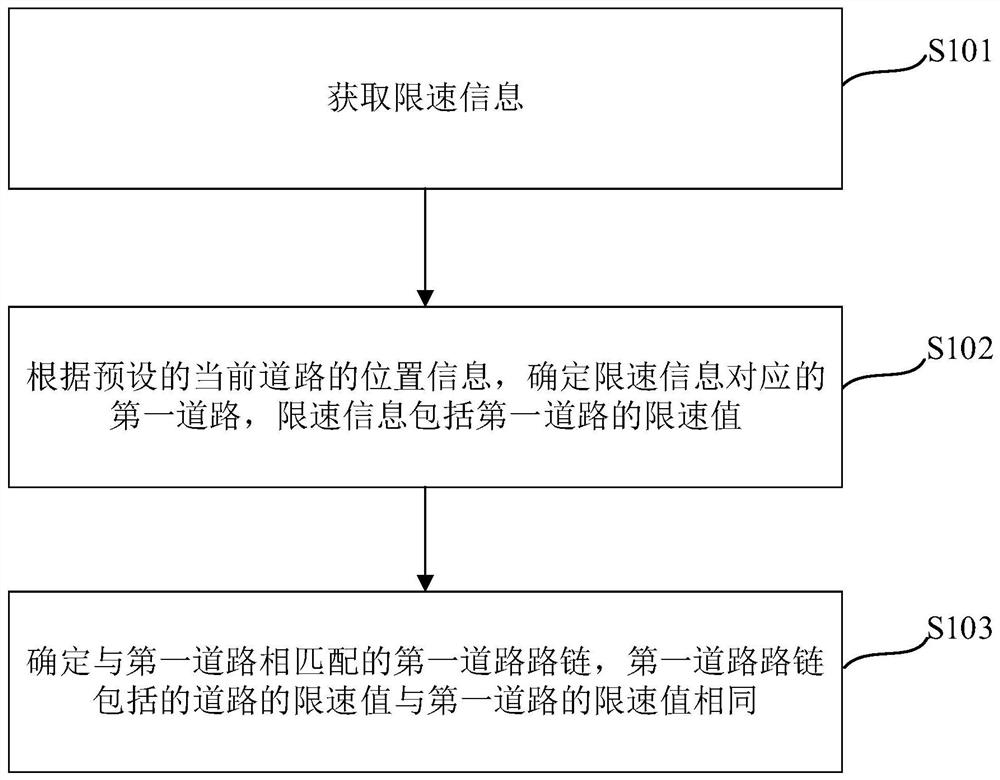
Method, device, device and computer-readable storage medium for determining road speed limit
ActiveCN112885129BAvoid misconfigurationImprove accuracyRoad vehicles traffic controlSimulationEngineering
Embodiments of the present application provide a method, device, device, and computer-readable storage medium for determining a road speed limit, including: obtaining speed limit information; For the road, the speed limit information includes the speed limit value of the first road; determine the first road link matching the first road, and the speed limit value of the road included in the first road link is the same as the speed limit value of the first road. This method determines the first road actually corresponding to the speed limit information through the position information of the current road in the electronic map, which can avoid setting the speed limit value of the first road as the speed limit value of the current road by mistake, thereby improving the speed of determining the speed limit of the road. At the same time, by determining the first road link that matches the first road, other roads with the same speed limit value as the first road are automatically calculated, which improves the efficiency of determining the road speed limit.
Owner:TENCENT TECH (SHENZHEN) CO LTD
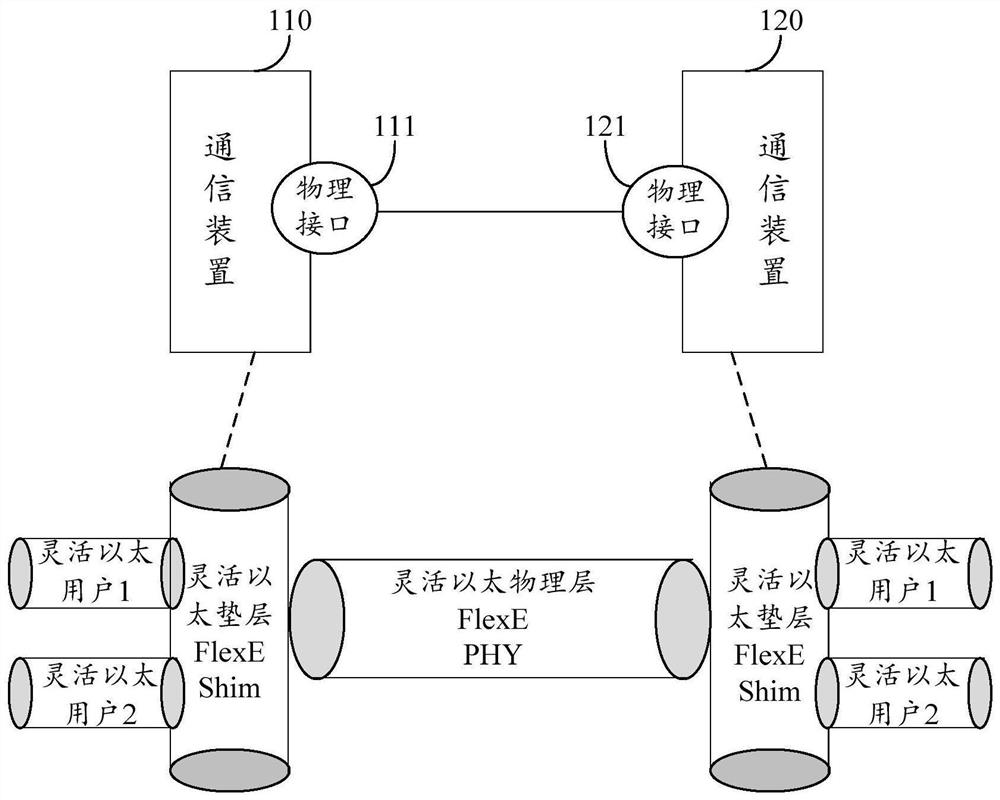
Resource management method and device for flexible Ethernet FlexE
PendingCN113973381AGuaranteed Bandwidth RequirementsGuaranteed normal forwardingTransmission path multiple useWireless communicationResource assignmentResource management
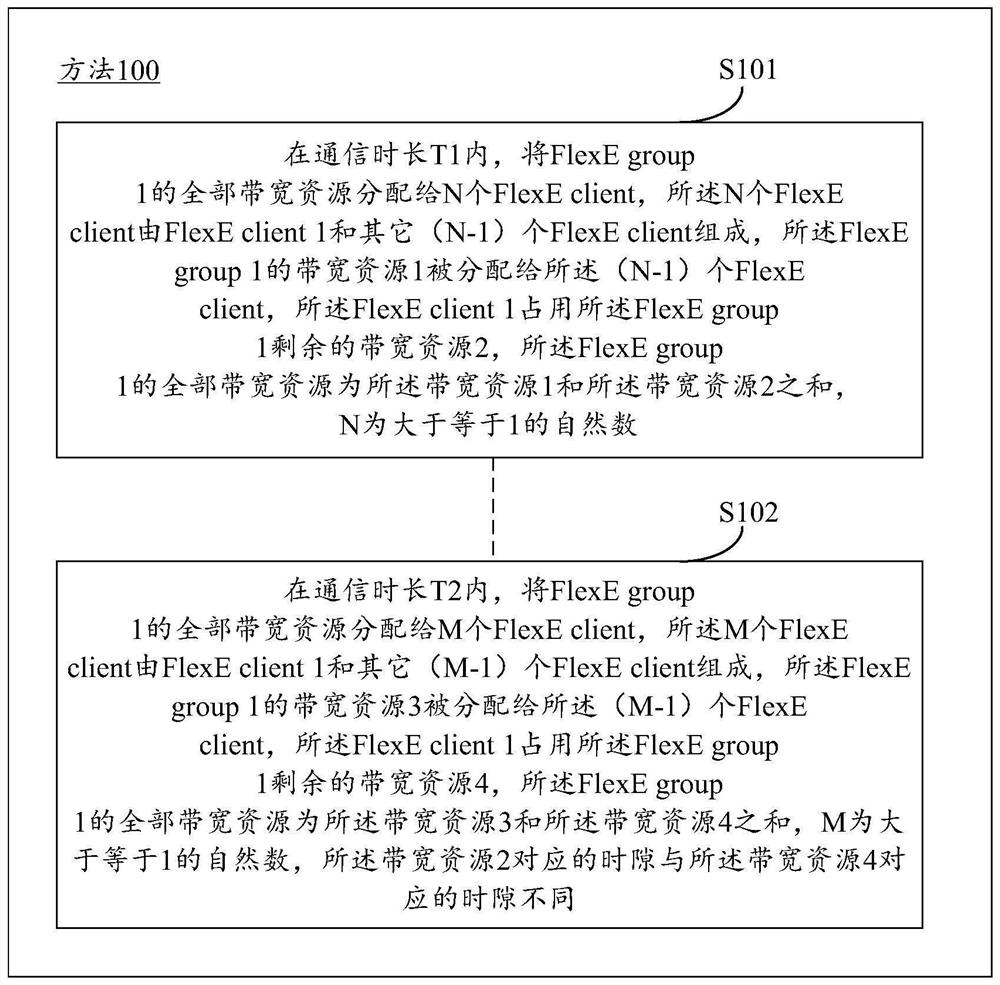
The embodiment of the invention provides a FlexE resource management method. A first communication device allocates all bandwidth resources of a first FlexE group to N FlexE clients within a first communication duration, wherein N is an integer greater than or equal to 1. The N FlexE clients are composed of a first FlexE client and other (N-1) FlexE clients, the first bandwidth resource of the first FlexE group is allocated to the (N-1) FlexE clients, the first FlexE client occupies the remaining second bandwidth resource of the first FlexE group, and all the bandwidth resources of the first FlexE group are the sum of the first bandwidth resource and the second bandwidth resource. The first communication device allocates all bandwidth resources of the first FlexE group to M FlexE clients within a second communication duration, M is an integer greater than or equal to 1, the M FlexE clients are composed of the first FlexE client and other (M-1) FlexE clients, third bandwidth resources of the first FlexE group are allocated to the (M-1) FlexE clients, the first FlexE client occupies the remaining fourth bandwidth resources in the first FlexE group, and all bandwidth resources of the first FlexE group are the sum of the third bandwidth resources and the fourth bandwidth resources.
Owner:HUAWEI TECH CO LTD
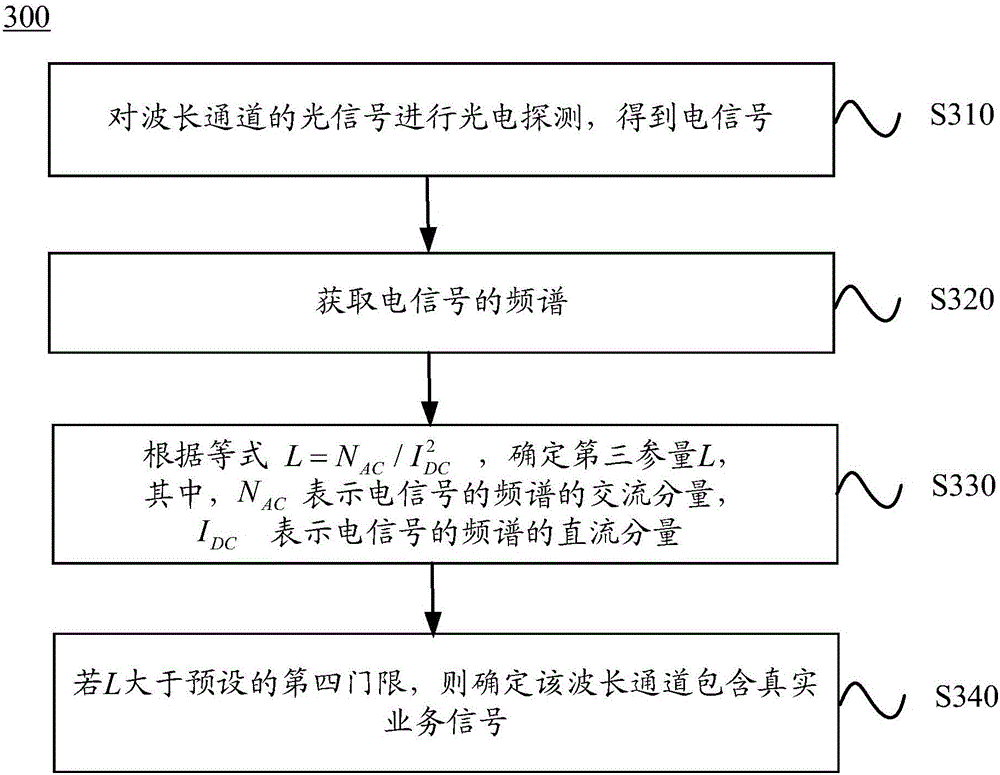
Method and device for detecting wavelength channels
ActiveCN105899267BAvoid misconfigurationWavelength-division multiplex systemsElectromagnetic transmissionFrequency spectrumSignal on
Owner:HUAWEI TECH CO LTD
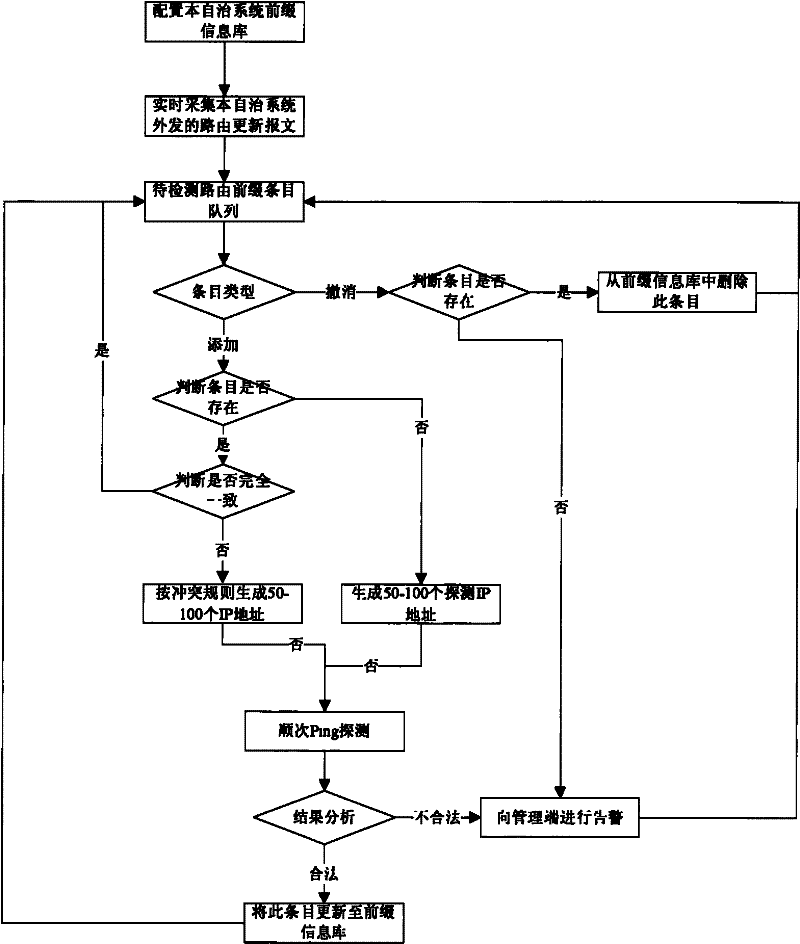
Inter-domain prefix hijacking detection method for error configuration
InactiveCN101656638BMaintain securityAvoid misconfigurationData switching networksComputer networkNetworked system
The invention provides an inter-domain prefix hijacking detection method for error configuration in a network system which at least comprises one autonomous system; the autonomous system comprises a monitoring probe which comprises a network prefix information list for storing prefix information in the autonomous system; the method comprises the following steps: the monitoring probe obtains a routing update message which is transmitted outwards by the autonomous system; all items of the routing update message is analyzed, and the item for adding types carries out the next step, and the items which exist in the network prefix information list and have completely consistent prefix information are not operated additionally, and the next item in the routing update message is directly processed; for the items which do not exist in the network prefix information list or although the items exist in the network prefix information list, the prefix information is conflicted, the validity of theitems is actively detected; the network prefix information list is updated according to the verified items for adding types. The method can avoid error configuration and maintain network safety.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com