Penetration attack detection method for intelligent Internet of Things terminal container
A technology of attack detection and intelligent IoT, which is applied in the fields of instrumentation, computing, and electrical digital data processing, etc., can solve problems such as container isolation not working, container system security issues, impacts, etc., and achieve the effect of easy discovery and repair
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In order to better understand the present invention, the content of the present invention is further illustrated below in conjunction with the examples, but the content of the present invention is not limited to the following examples.
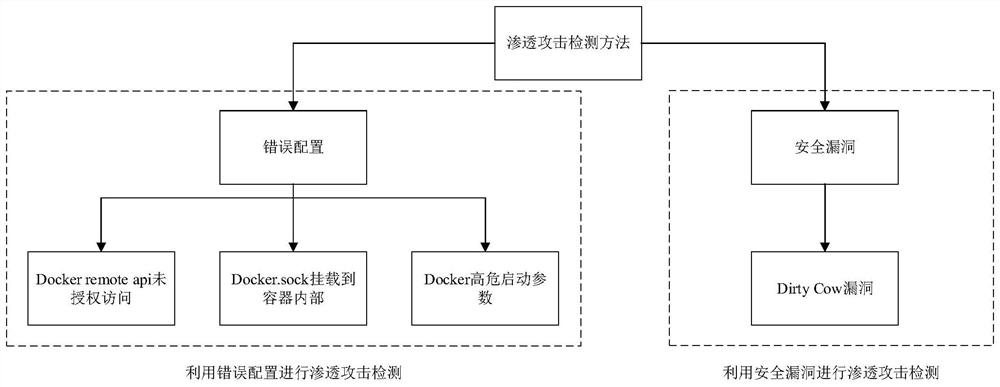
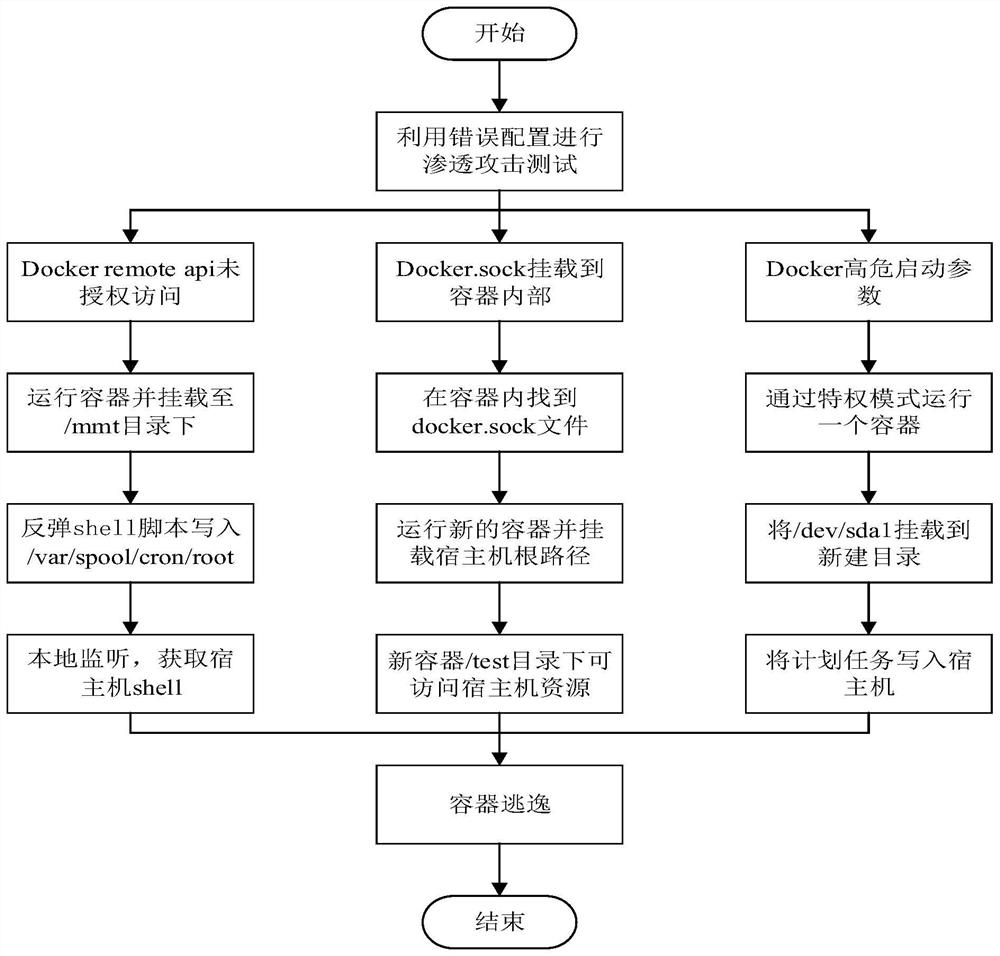
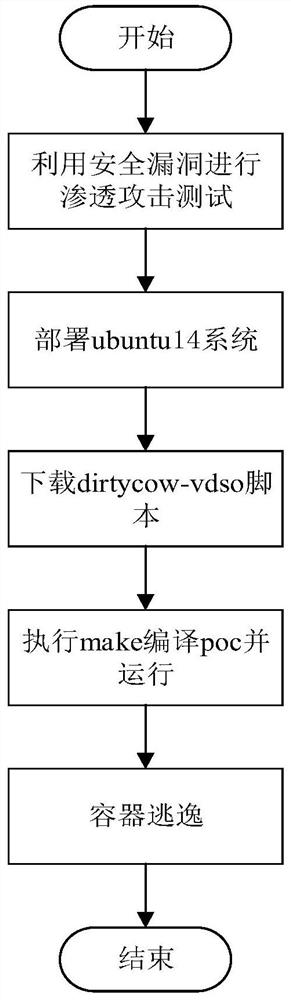
[0047] like figure 1 As shown in the figure, a penetration attack detection method for a container of an intelligent IoT terminal includes the following steps: 1) conducting penetration attacks on the container through security loopholes to detect whether the container escapes; 2) causing the container to escape through wrong configuration, and then Penetration attack detection.
[0048] The penetration attack detection method of the above-mentioned intelligent IoT terminal container needs to determine whether the current environment is in the Docker environment, and only in the Docker environment can the penetration attack test on the container be carried out. There are two commonly used judgment methods. One is to check whether / .doc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com