Network disk file tracing method, device, network disk and storage medium
A file and network disk technology, applied in the field of network disk file traceability, network disk and storage media, and devices, can solve problems affecting network disk performance, etc., and achieve the effects of being difficult to identify, good download requirements, and strong stability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
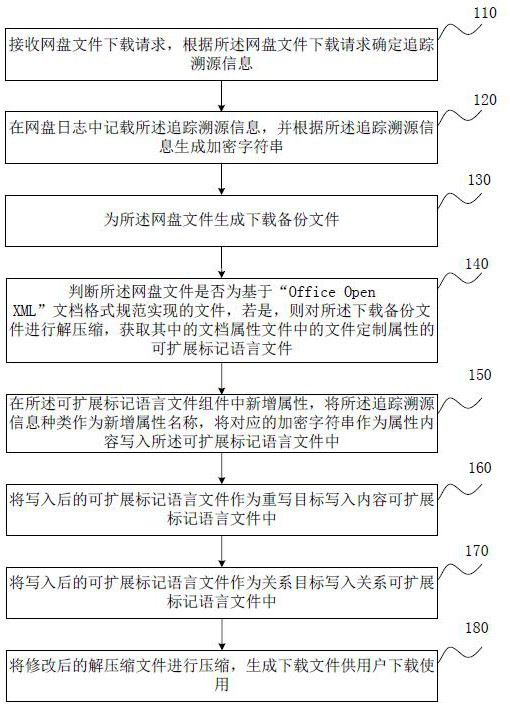
[0039] figure 1 This is a flowchart of the method for tracing files on a network disk provided in Embodiment 1 of the present invention. This embodiment is applicable to the situation of tracing off-disk files. The method can be executed by a device for tracing files on a network disk, and specifically includes the following steps:
[0040] Step 110: Receive a file download request from the network disk, and determine the traceability information according to the file download request from the network disk.
[0041] Usually, the user can download the corresponding file from the network disk to facilitate offline processing of the file. The network disk can receive user download requests for files on the network disk. When a download request for a file on the network disk is received, the traceability information of the file on the network disk can be determined according to the specific content of the request.
[0042] The traceability information is used to represent the in...
Embodiment 2
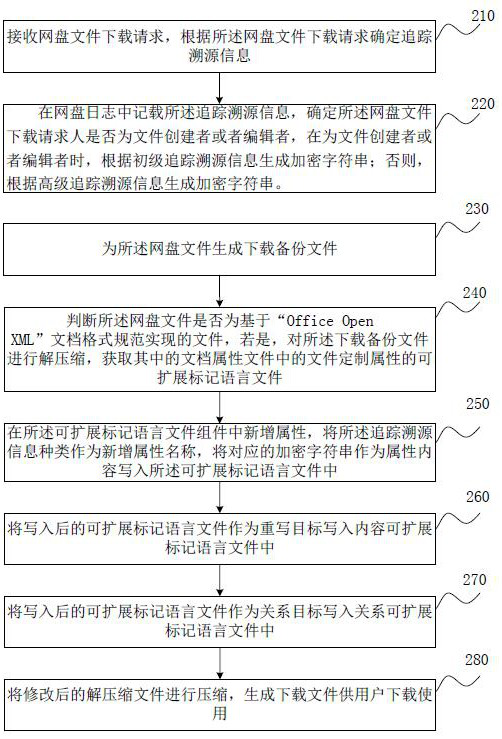
[0064] figure 2 This is a flowchart of the method for tracing network disk files provided in the second embodiment of the present invention. This embodiment is optimized on the basis of the above-mentioned embodiment. In this embodiment, the generation of an encrypted string according to the traceability information can be specifically optimized as follows: determining whether the download requester of the network disk file is a file creator. When the file creator or editor is a file creator or editor, an encrypted string is generated based on the primary traceability information; otherwise, an encrypted string is generated based on the advanced traceability information.
[0065] Correspondingly, the network disk file tracing method provided in this embodiment specifically includes:
[0066] Step 210: Receive a file download request from the network disk, and determine the traceability information according to the file download request from the network disk.
[0067] Step 2...
Embodiment 3
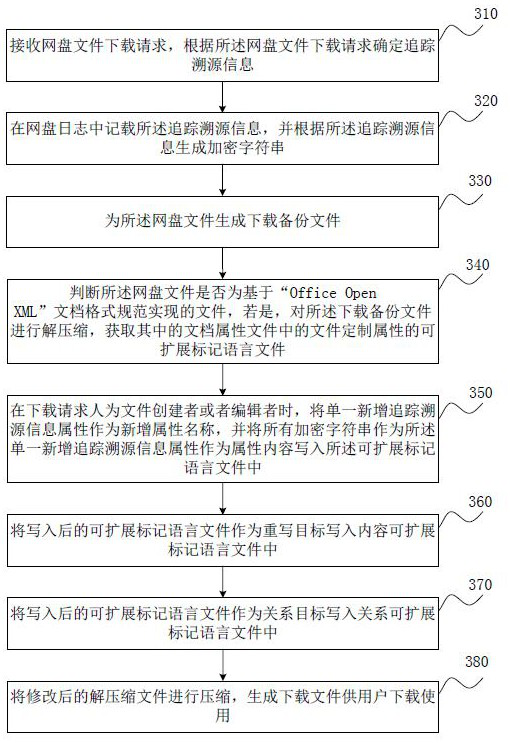
[0080] image 3 This is a flowchart of the method for tracing network disk files provided in Embodiment 3 of the present invention. This embodiment is optimized on the basis of the above-mentioned embodiment. In this embodiment, the type of traceability information is used as the name of the newly added attribute, and the corresponding encrypted character string is written as the content of the attribute into the extensible markup language file , the specific optimization is: when the download requester is the creator or editor of the file, use a single newly added traceability information attribute as the name of the newly added attribute, and use all encrypted strings as the single newly added traceability information attribute as the attribute content into the Extensible Markup Language file.
[0081] Correspondingly, the network disk file tracing method provided in this embodiment specifically includes:
[0082] Step 310: Receive a file download request from the network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com