Threat behavior analysis method based on big data analysis and server
A behavior analysis and big data technology, applied in the field of big data, can solve the problems of increasing server processing pressure, cumbersome recognition technology, and reducing recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Hereinafter, the terms "first", "second" and "third" etc. are used for descriptive purposes only, and cannot be understood as indicating or implying relative importance or implicitly specifying the quantity of indicated technical features. Thus, a feature defined as "first", "second" or "third" etc. may expressly or implicitly include one or more of such features.
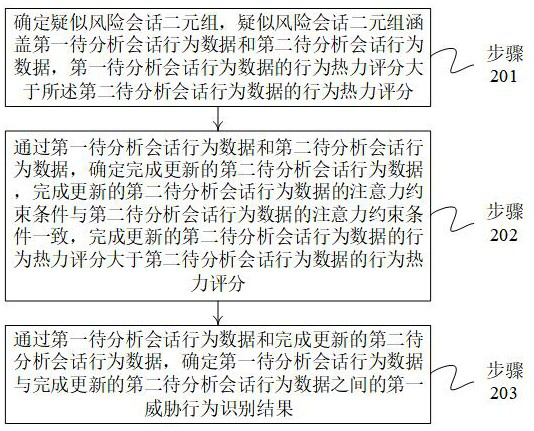
[0033] figure 1 It shows a schematic flowchart of a threat behavior analysis method based on big data analysis provided by an embodiment of the present invention. A threat behavior analysis method based on big data analysis can be implemented by a big data analysis server, and the big data analysis server can include A memory and a processor; the memory is coupled to the processor; the memory is used to store computer program codes, and the computer program codes include computer instructions; wherein, when the processor executes the computer instructions, the The big data analysis server executes the techn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com