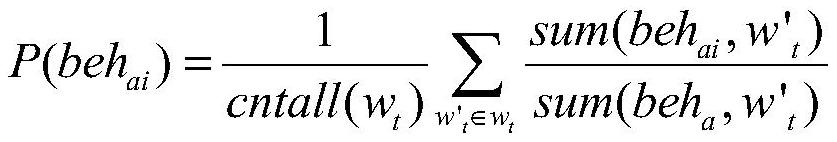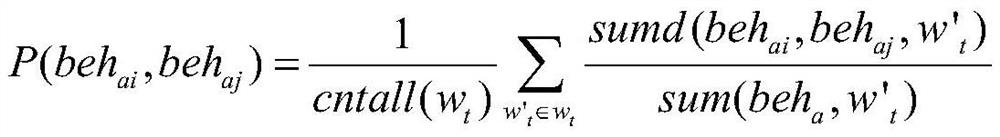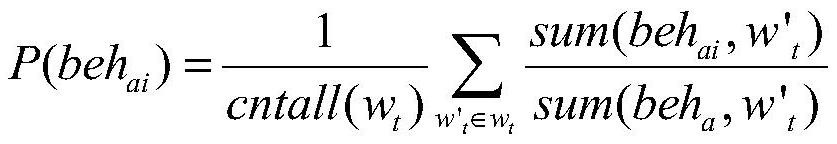Patents
Literature
32 results about "Threatening behaviour" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
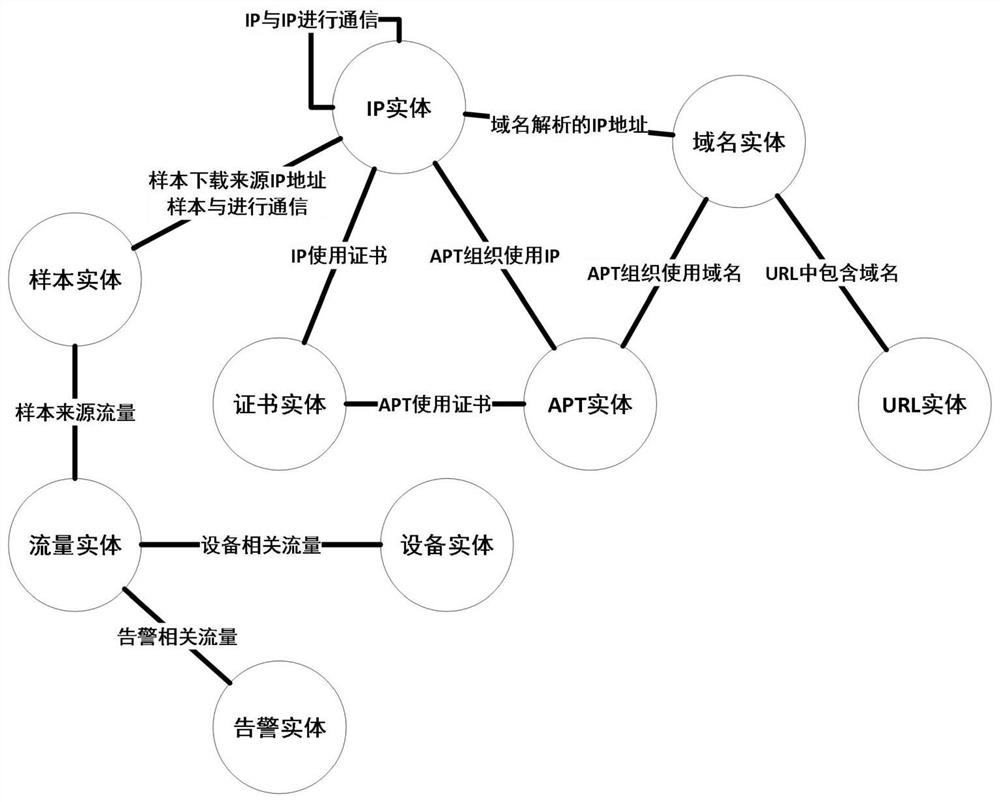
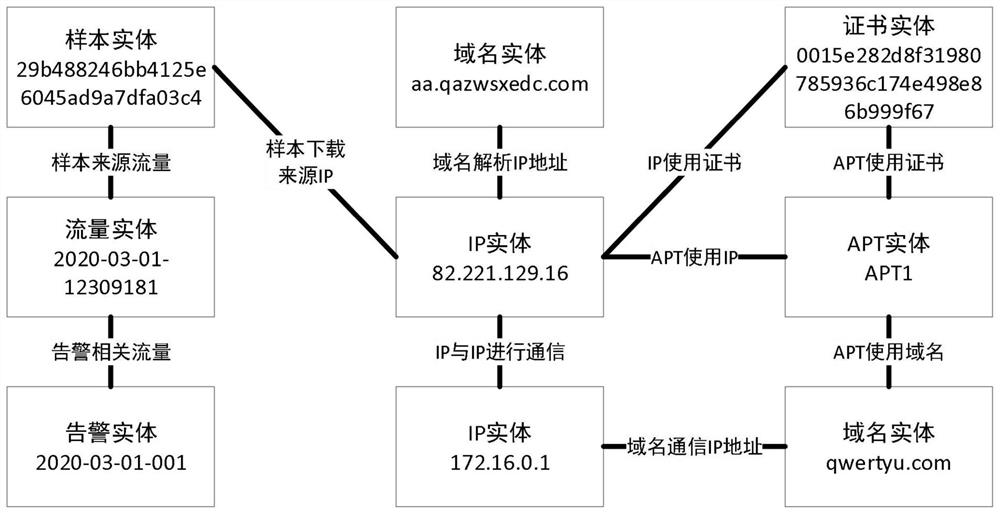
Threatening behavior is intentional behavior which would cause a person of ordinary sensibilities fear of injury or harm. It can include acts of aggression such as yelling at a colleague, pounding on desks, slamming doors,blocking or cornering, and sending threatening voice-mails, e-mails, or other written threats.
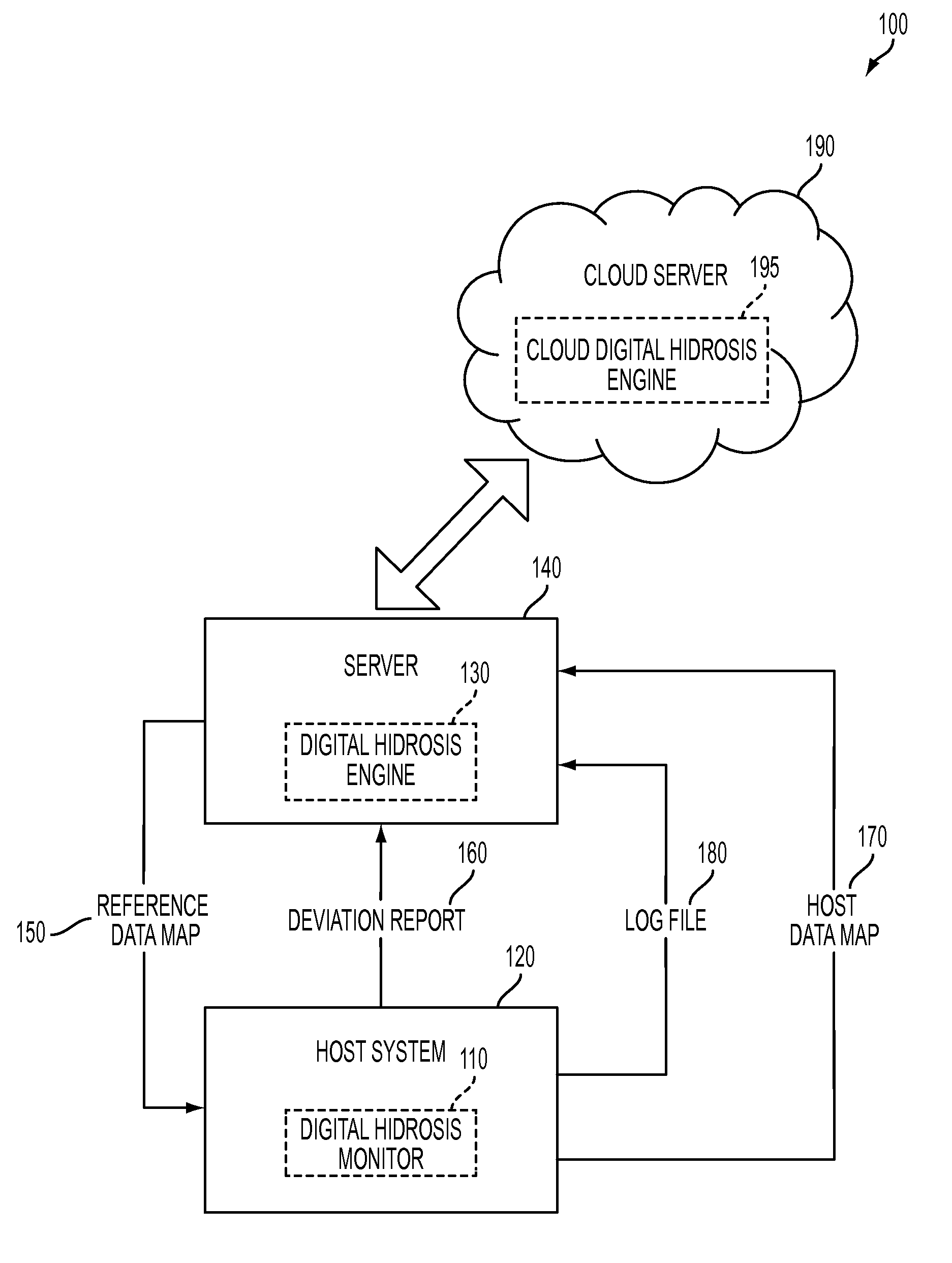
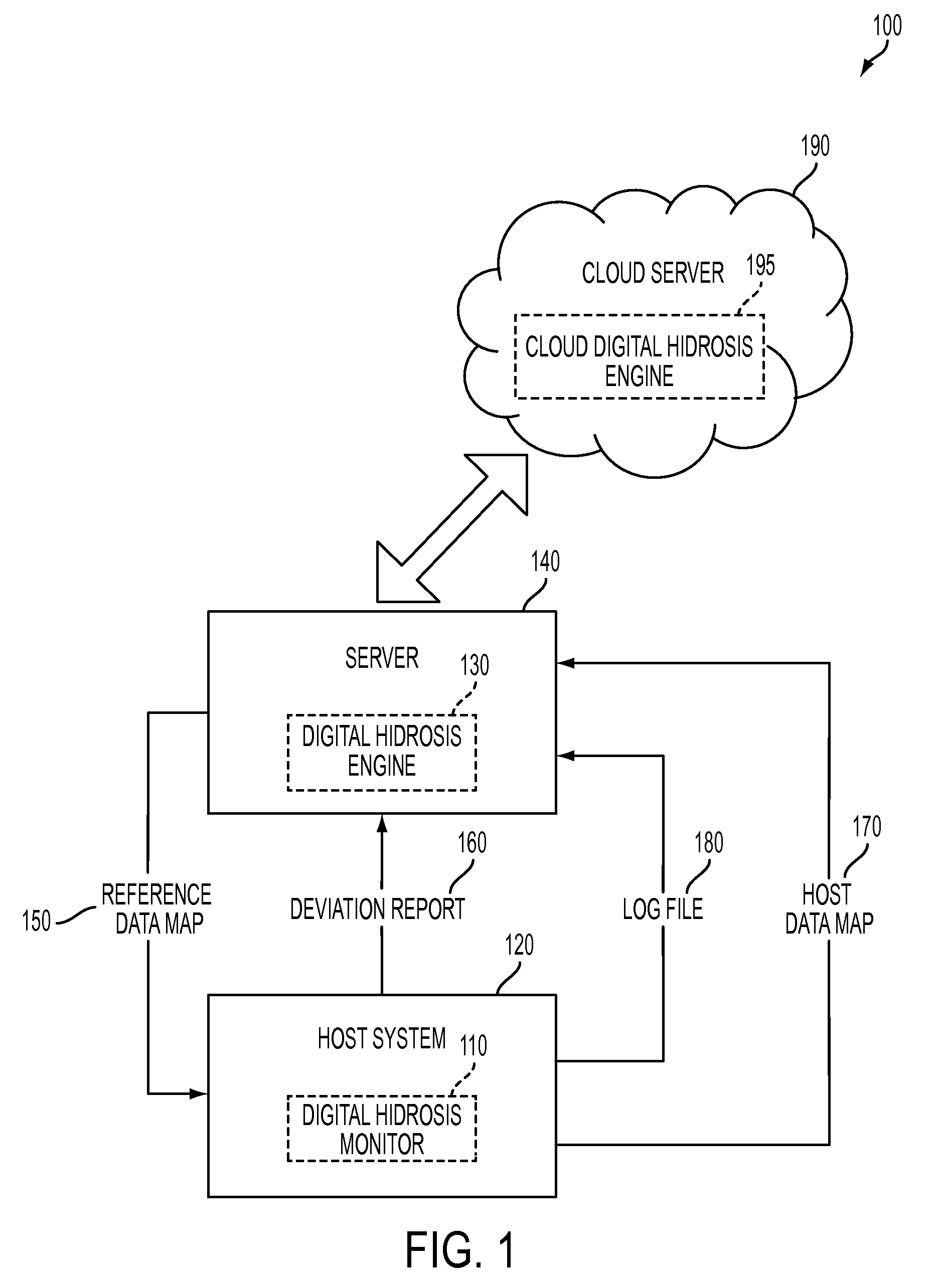
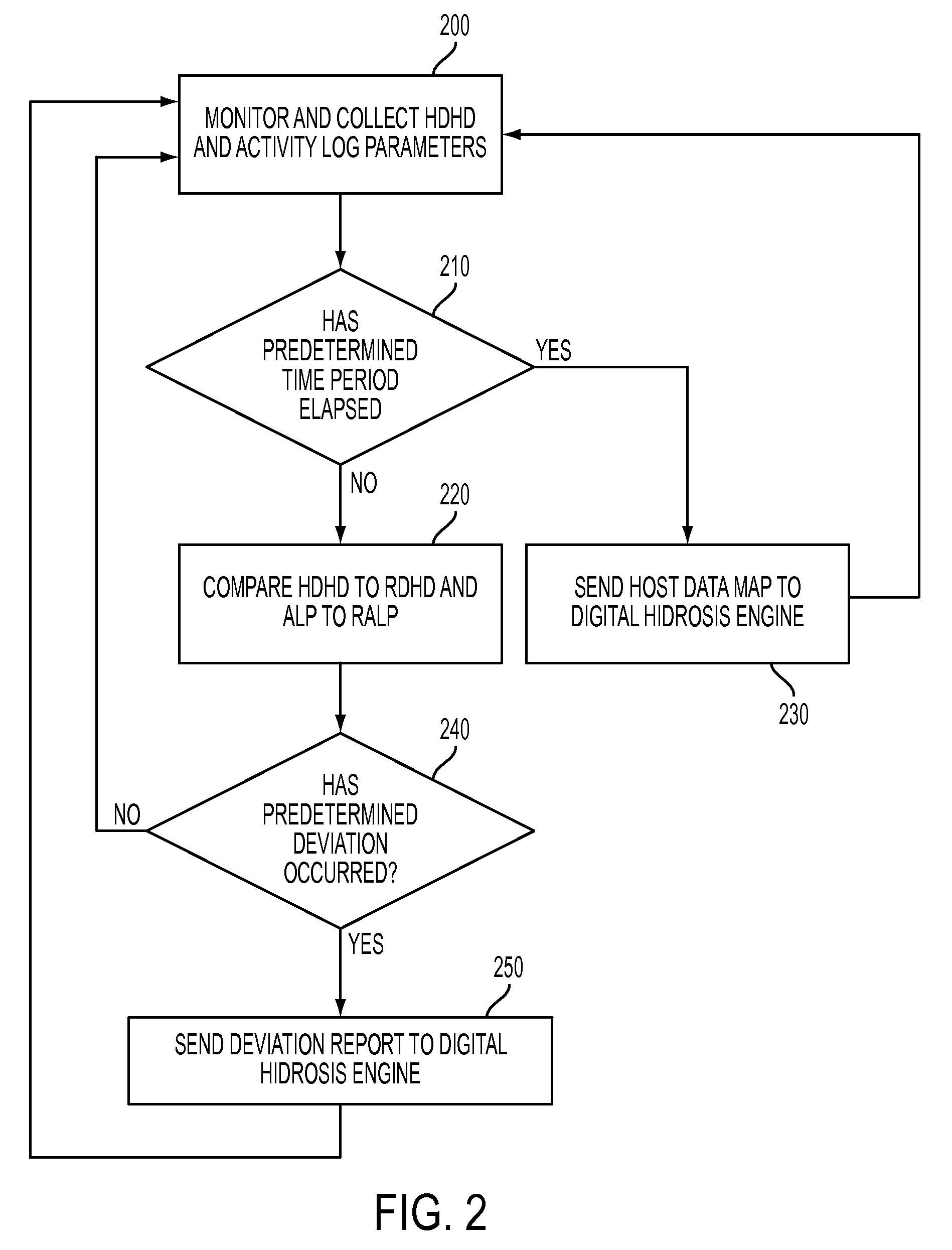
System and method for detecting potential threats by monitoring user and system behavior associated with computer and network activity
A system and method is provided to monitor user and system behavior associated with computer and network activity to determine deviations from normal behavior that represent a potential cyber threat or cyber malicious activity. The system and method uses a multi-factor behavioral and activity analysis approach to determine when a trusted insider might be exhibiting threatening behavior or when a user's computer or network credentials have been compromised and are in use by a third-party. As a result, changes in insider behavior that could be indicative of malicious intent can be detected, or an external entity masquerading as a legitimate user can be detected.
Owner:WINTERMUTE LLC
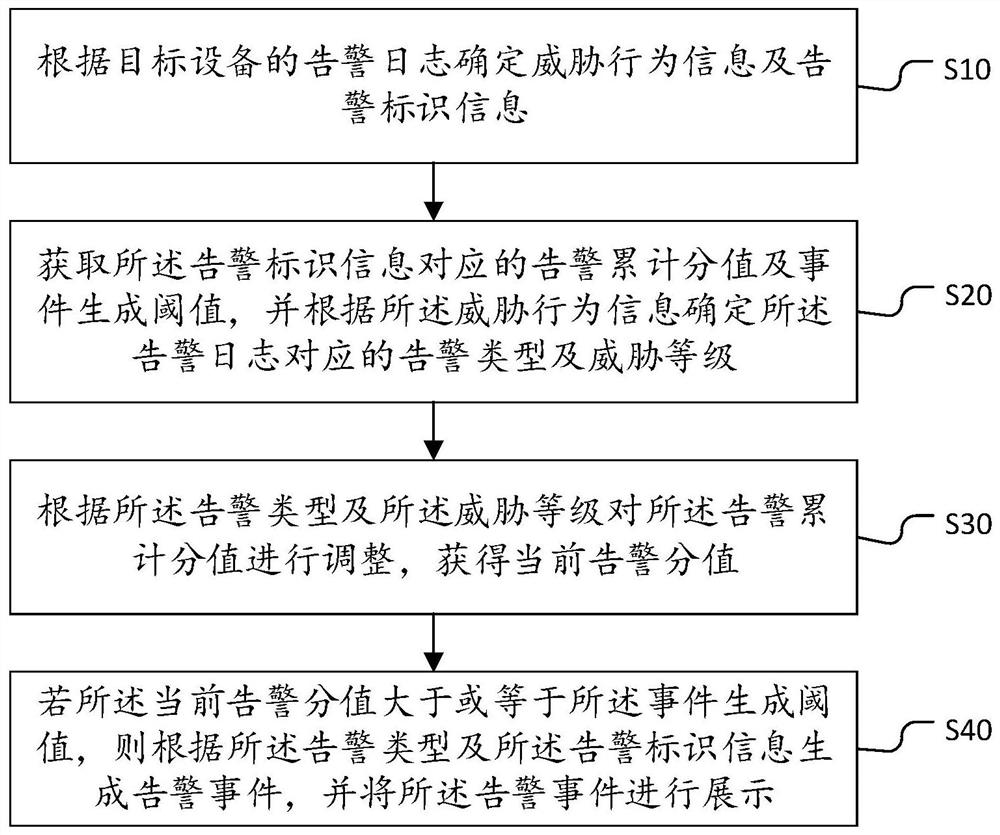
Alarm log processing method and device, equipment and storage medium
ActiveCN113515433AQuick responseHardware monitoringInformation technology support systemThreat levelThreatening behaviour
The invention belongs to the technical field of computers, and discloses an alarm log processing method and device, equipment and a storage medium. The method comprises: determining threat behavior information and the alarm identification information according to the alarm log of the target device; obtaining an alarm accumulated score and an event generation threshold corresponding to the alarm identification information, and determining an alarm type and a threat level corresponding to the alarm log according to the threat behavior information; adjusting the alarm accumulated score according to the alarm type and the threat level to obtain a current alarm score; and if the current alarm score is greater than or equal to an event generation threshold, generating an alarm event according to the alarm type and the alarm identification information, and displaying the alarm event. The alarm accumulated score is accumulated according to the alarm log, and the alarm event is generated and displayed when the alarm accumulated score is greater than or equal to the event generation threshold value, so that a manager does not need to pay attention to a complex log, and can quickly respond to a network security event according to the alarm event.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
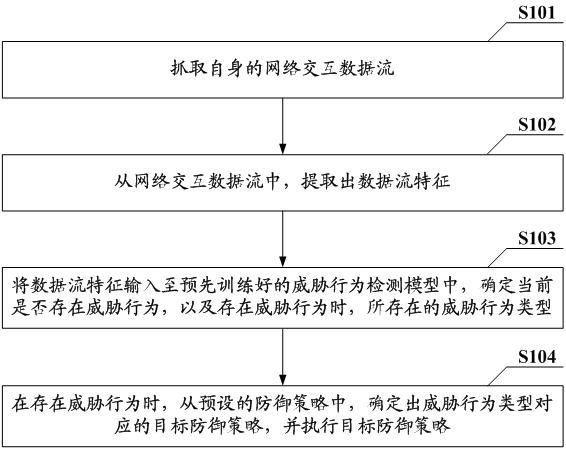
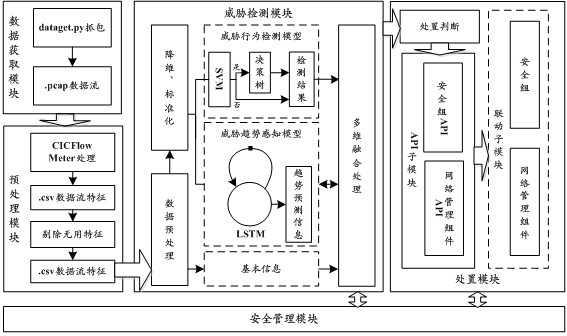
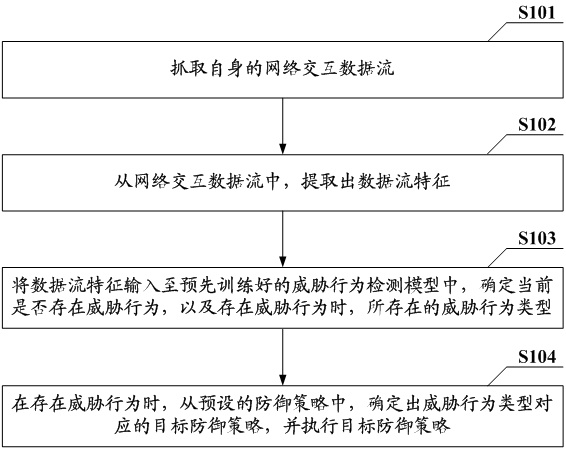
Threat processing method and device, electronic equipment and computer readable storage medium
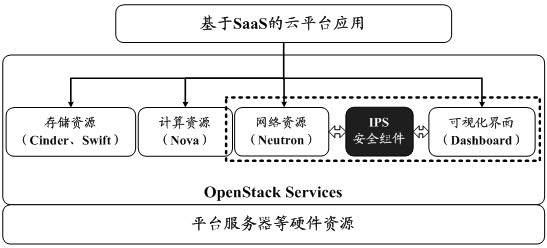
The invention provides a threat processing method and device, electronic equipment and a computer readable storage medium, and the method is applied to a target node of a cloud platform, and comprises the steps: capturing a self network interaction data flow; extracting data flow characteristics from the network interaction data flow; inputting the data flow features into a pre-trained threat behavior detection model, and determining whether a threat behavior exists at present or not and the type of the existing threat behavior when the threat behavior exists; and when the threat behavior exists, determining a target defense strategy corresponding to the threat behavior type from preset defense strategies, and executing the target defense strategy. Therefore, the monitoring and disposal of the network threat of the cloud platform are realized, and the security protection of the cloud platform is enhanced.
Owner:CHINA ELECTRONICS CORP 6TH RES INST
Data processing method and server for coping with cloud computing office threats
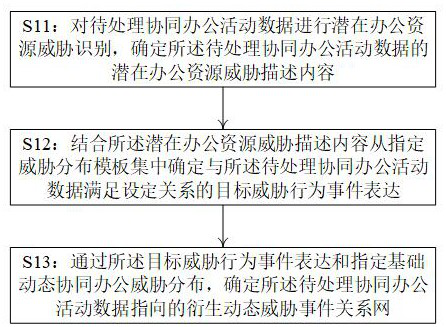
ActiveCN114676423AAccurately determineSmall scaleOffice automationPlatform integrity maintainanceEngineeringTargeted threat
According to the data processing method for coping with the cloud computing office threats and the server provided by the invention, when a derivative dynamic threat event relationship network is determined, threat behavior event expressions do not need to be frequently updated, so that the execution complexity is weakened to a certain extent; in combination with the periodic characteristics of the collaborative office staged task description content, the information scale of the specified threat distribution template set determined in advance is relatively small; the data processing server is combined with the potential office resource threat description content of the to-be-processed collaborative office activity data to timely position the target threat behavior event expression from the specified threat distribution template set; and accurately and timely determining a derivative dynamic threat event relationship network which satisfies a set relationship with the to-be-processed collaborative office activity data by means of the target threat behavior event expression and the specified basic collaborative office threat distribution.
Owner:深圳市智联云网科技有限公司
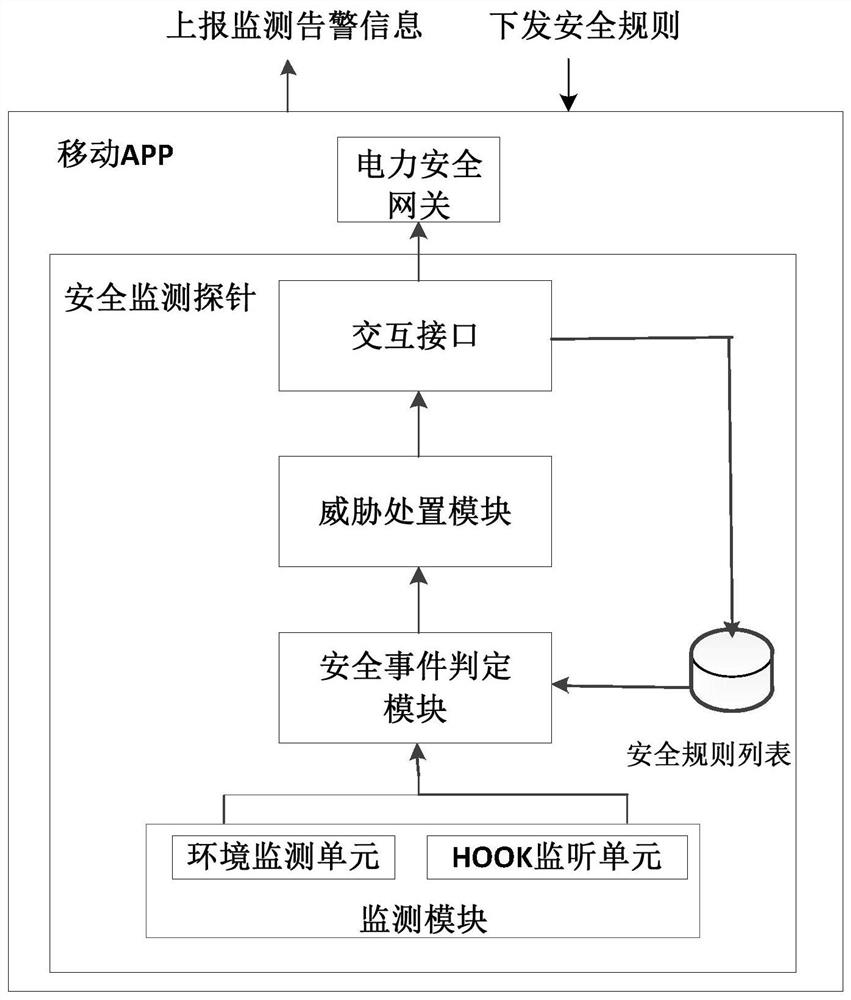
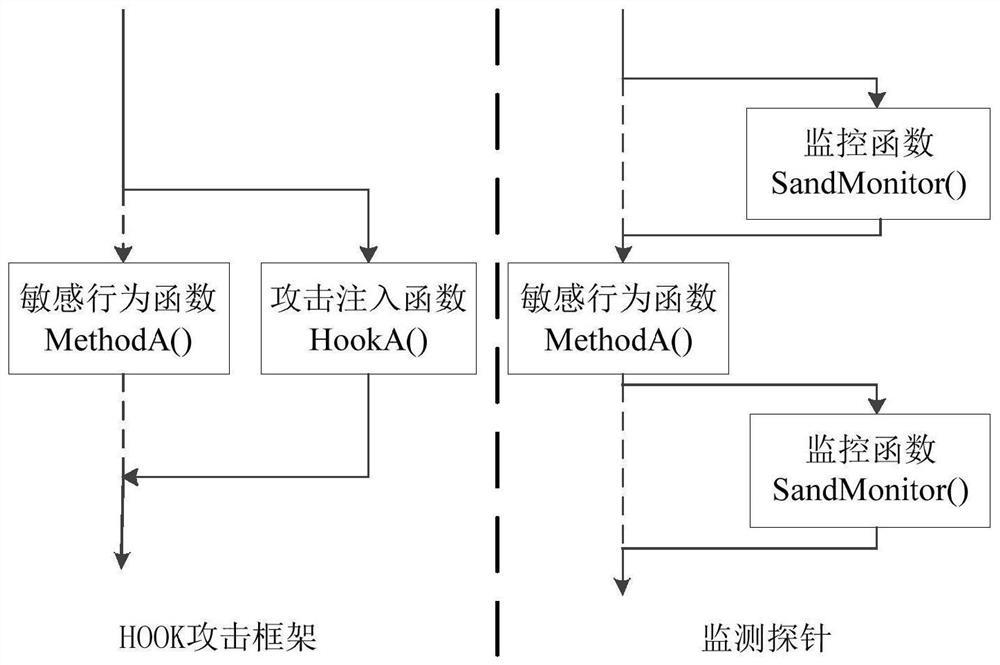
Threat disposal method and safety monitoring probe for Android application
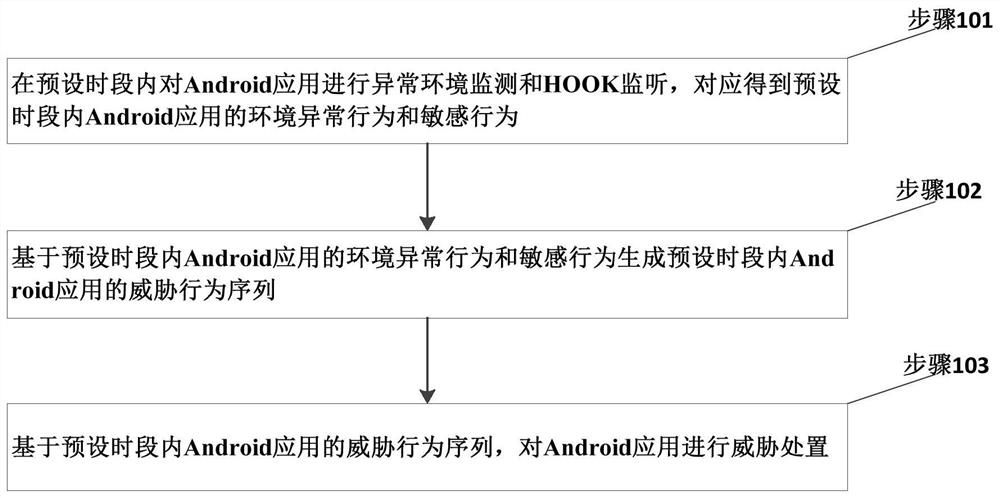
PendingCN113111347AReduce security risksAccurate Threat Disposition OperationsPlatform integrity maintainanceComputer scienceOperating system
The invention relates to an Android application threat disposal method and a safety monitoring probe. The method comprises the steps: carrying out the abnormal environment monitoring and HOOK monitoring of an Android application in a preset time period, and correspondingly obtaining the environment abnormal behavior and sensitive behavior of the Android application in the preset time period; generating a threat behavior sequence of the Android application in the preset time period based on the environment abnormal behavior and the sensitive behavior of the Android application in the preset time period; and based on the threat behavior sequence of the Android application in the preset time period, performing threat disposal on the Android application. According to the technical scheme provided by the invention, the abnormal behavior of the Android application environment and the sensitive behavior of the application are jointly monitored, so that the threat disposal operation of the Android application is accurately executed, and the safety risk of the Android application is reduced.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
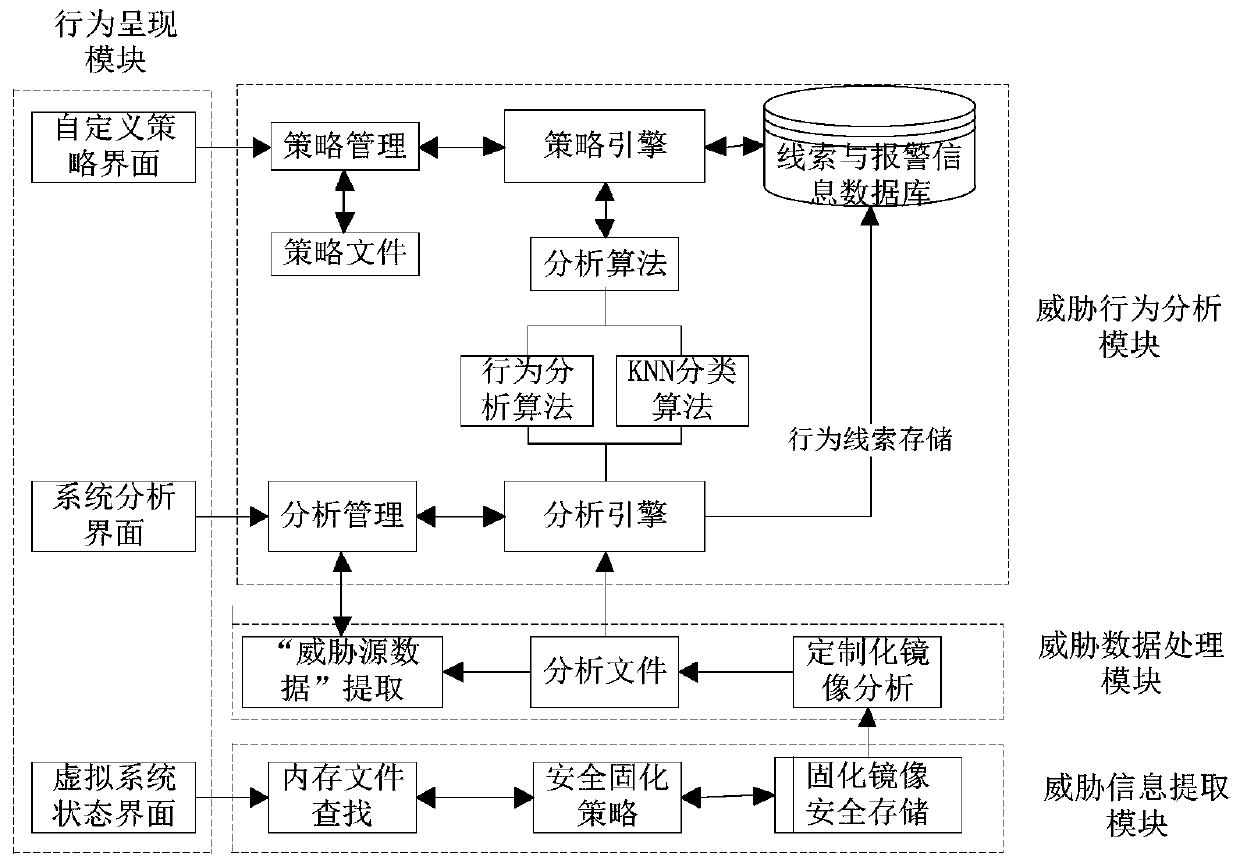
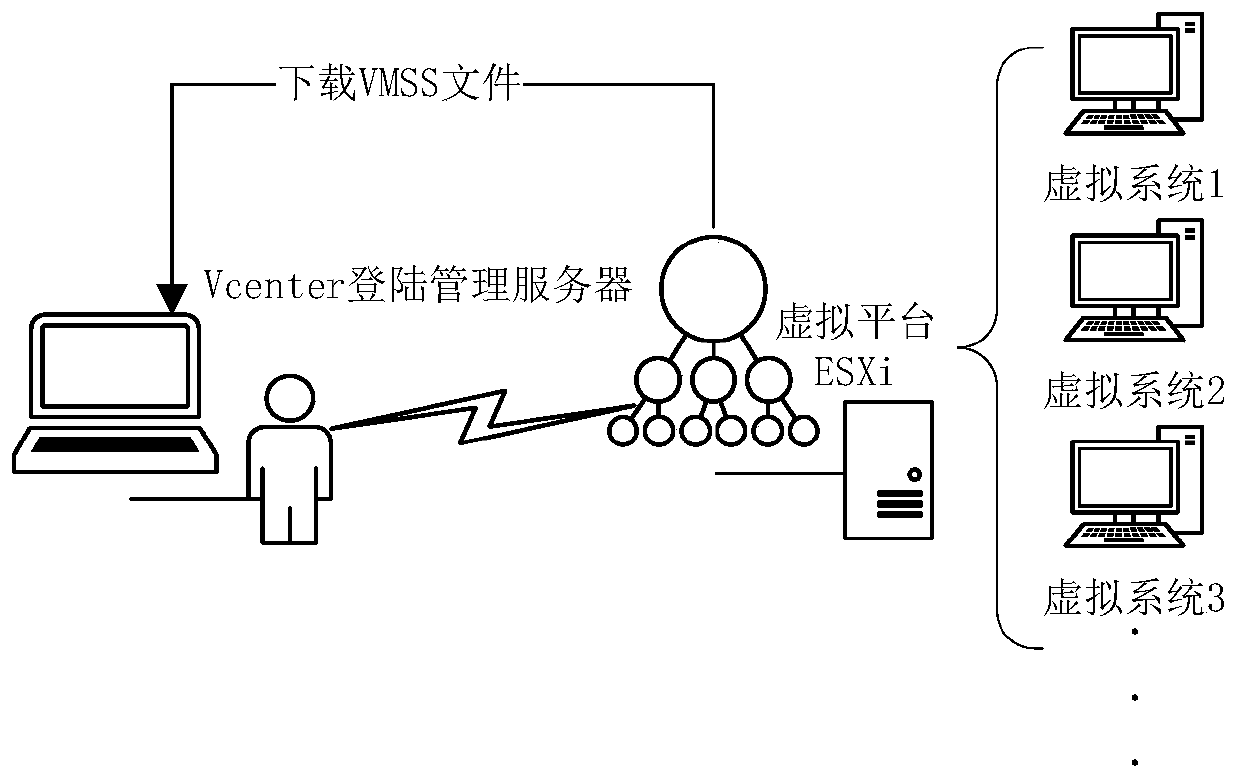
Virtual platform threat behavior analysis method and system based on KNN
InactiveCN110012013AImprove analysis efficiencyImprove accuracyCharacter and pattern recognitionTransmissionBehavioral analyticsAnalysis method
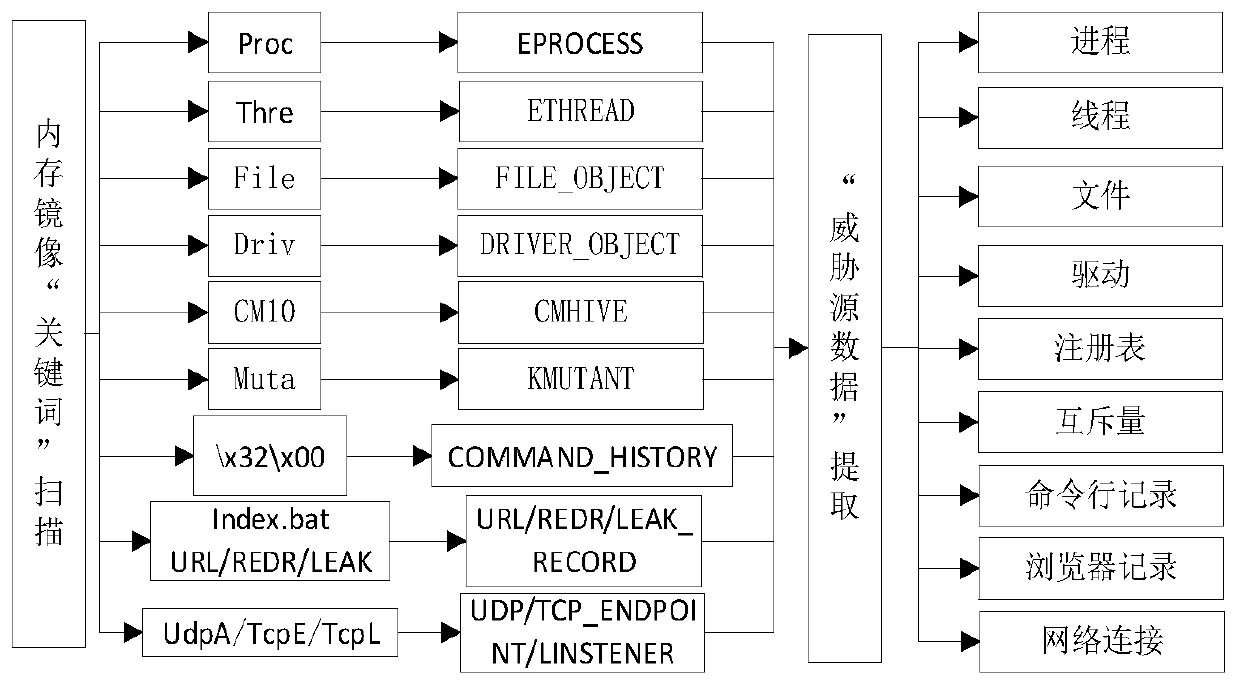
The invention discloses a virtual platform threat behavior analysis method and system based on KNN, and belongs to the field of network security, and the method comprises the steps: firstly, extracting memory data in a virtual platform; analyzing the memory data to obtain threat source data; finally, identifying threat software of the threat source data by using a K-nearest algorithm, and if the threat software does not exist, ending the algorithm; if the threatening software exists, finishing the behavior reduction of the threatening software by utilizing a clue database, and ending the algorithm; according to the method, clue data can be collected based on the outside of the VMware Vshpere virtual platform, clue coverage cannot be generated in the virtual platform, and the clue data cannot be deceived by threatening software; full-automatic analysis is peformed on the threat clues through the K-nearest algorithm, and the analysis efficiency of the threat behaviors is improved.
Owner:电子科技大学成都学院
Threat vulnerability mining method based on information security big data and information security system
InactiveCN114238992AImprove the situation where there is a vulnerability decision errorImprove the situation of vulnerability decision errorsPlatform integrity maintainanceInformation securityThreatening behaviour
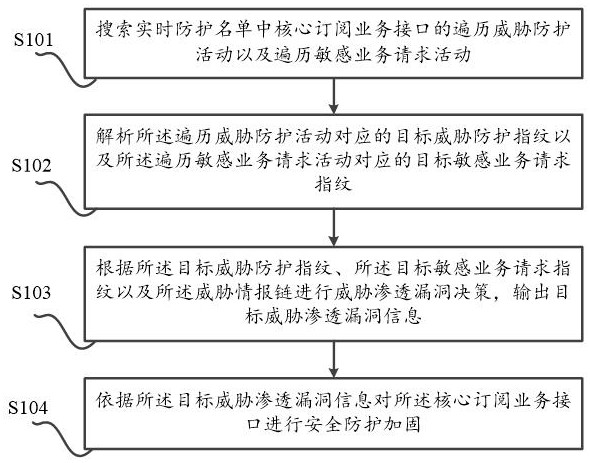
The invention discloses a threat vulnerability decision-making method based on information security big data and an information security system, and the method comprises the steps: considering a threat intelligence chain expressed by a penetration relation between behavior track nodes in a historical threat behavior model according to chain intelligence formed through the arrangement of multiple types of historical threat behavior information; the threat penetration vulnerability decision is performed according to the threat intelligence chain, so that the situation that vulnerability decision errors exist due to the fact that threat penetration vulnerability decision is performed by only considering the triggering activity of the threat behavior in the traditional scheme can be improved, and the decision accuracy of the threat penetration vulnerability between the threat protection activity and the sensitive service request activity is improved; therefore, the effectiveness of subsequent safety protection reinforcement is improved.
Owner:天津智宝通大数据服务有限公司
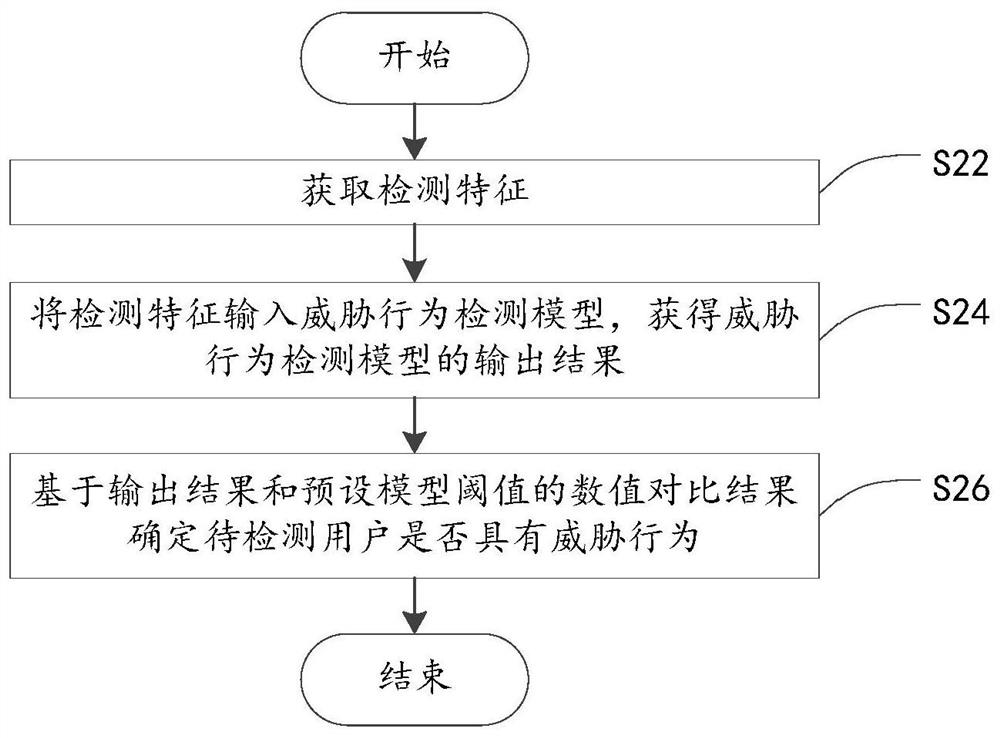
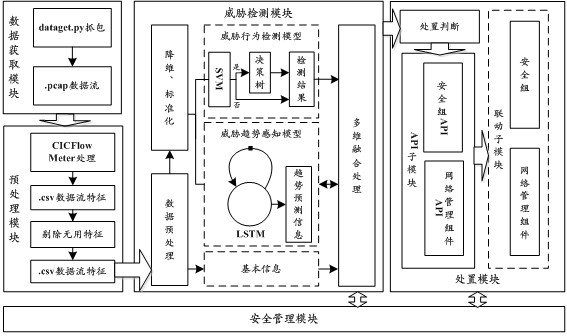
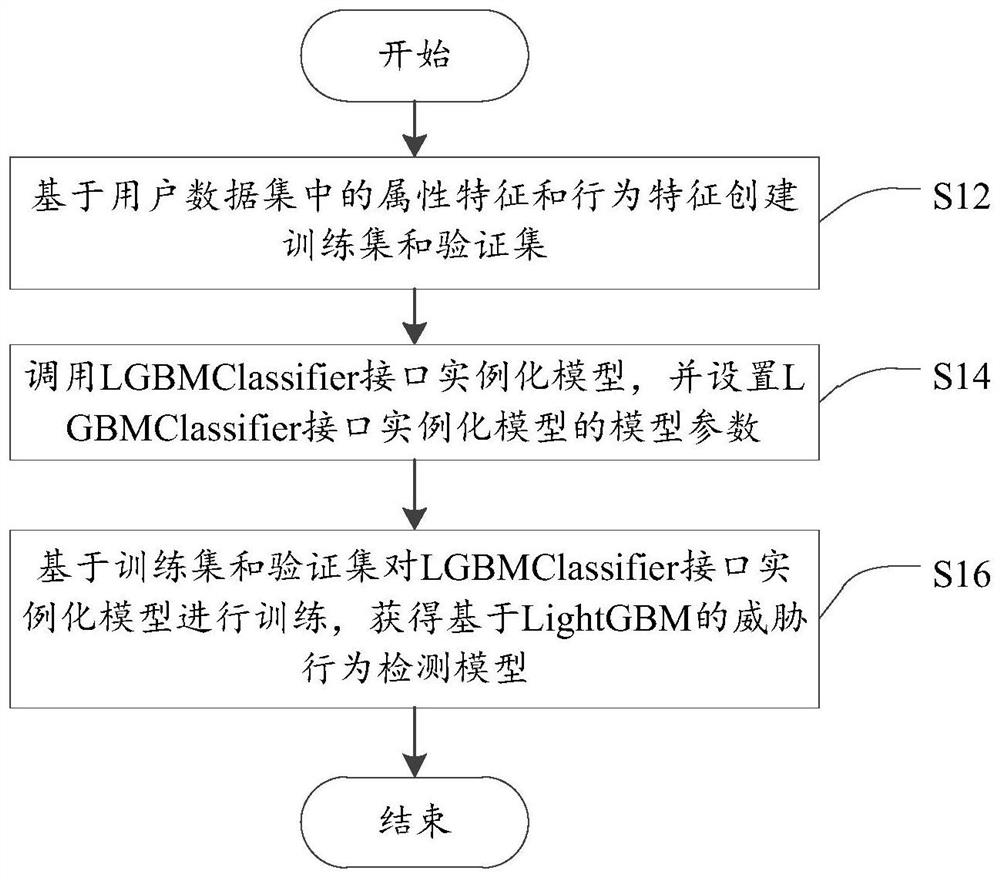
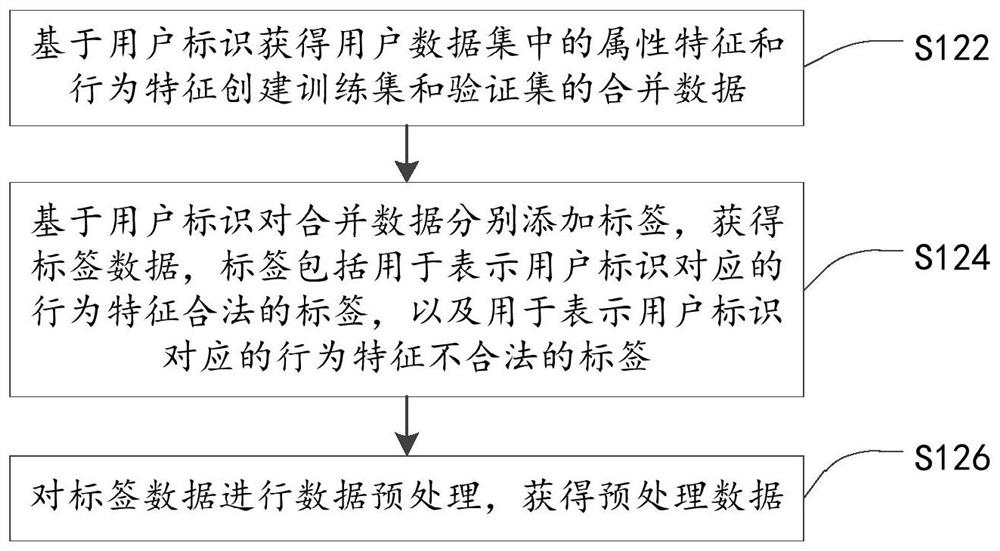
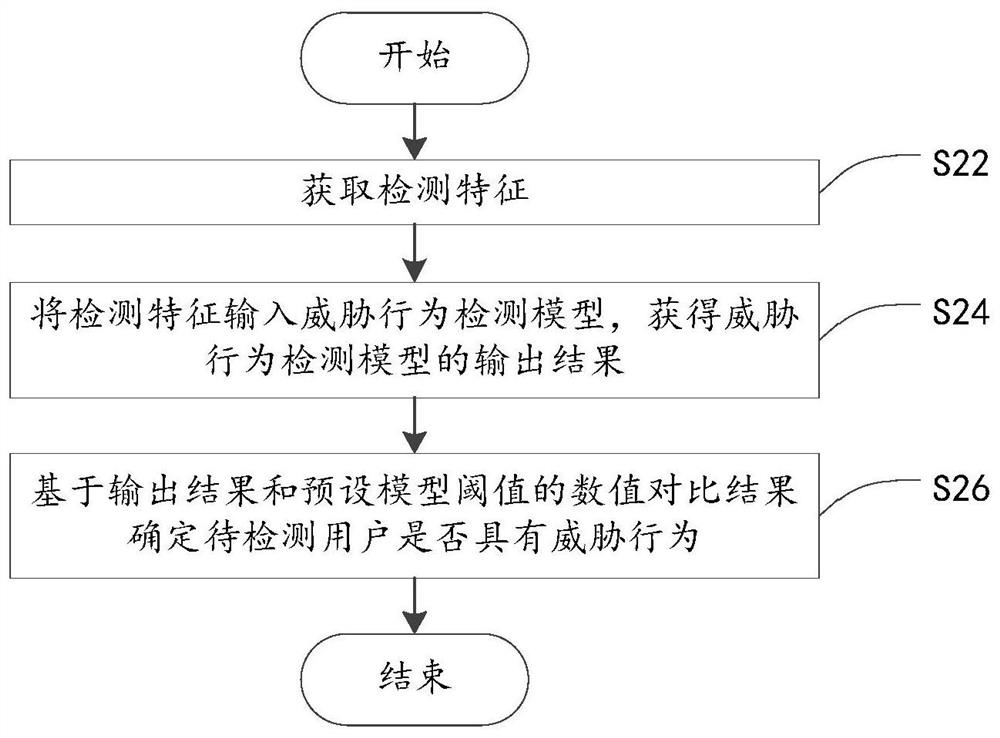
Threat behavior detection and model establishment method and device thereof, electronic equipment and storage medium
ActiveCN111988327AAvoid settingImprove modeling efficiencyData switching networksConcurrent computationData set
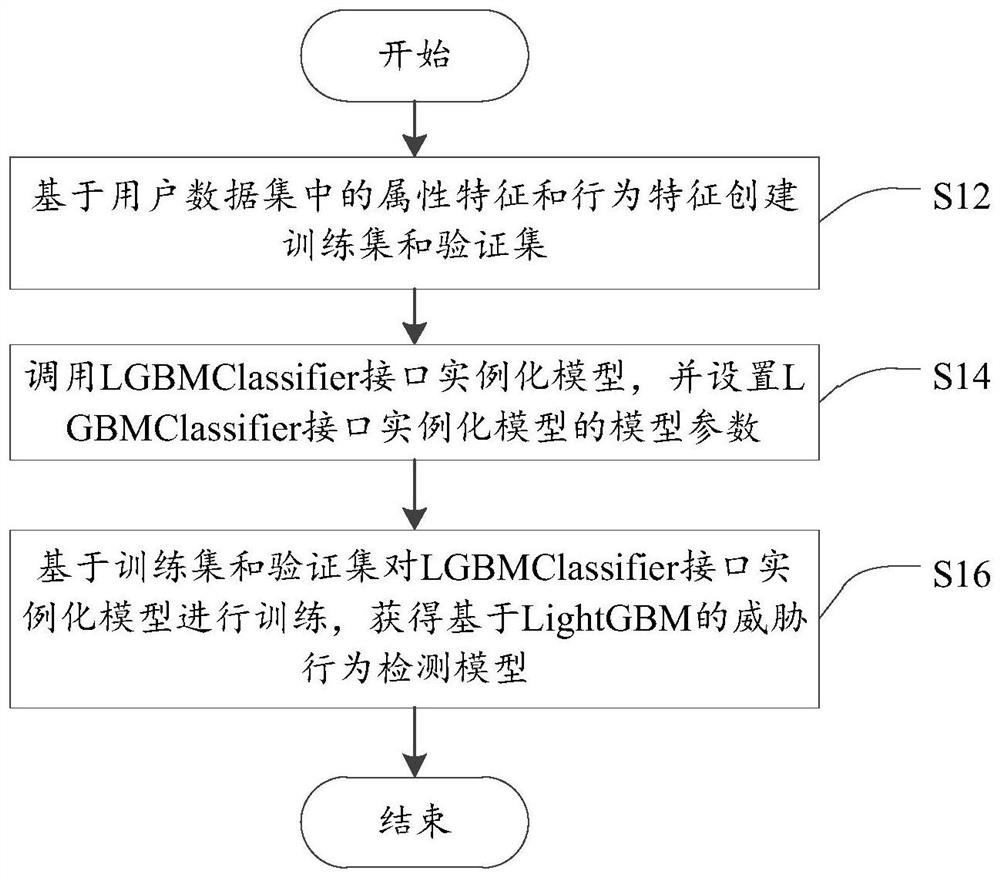
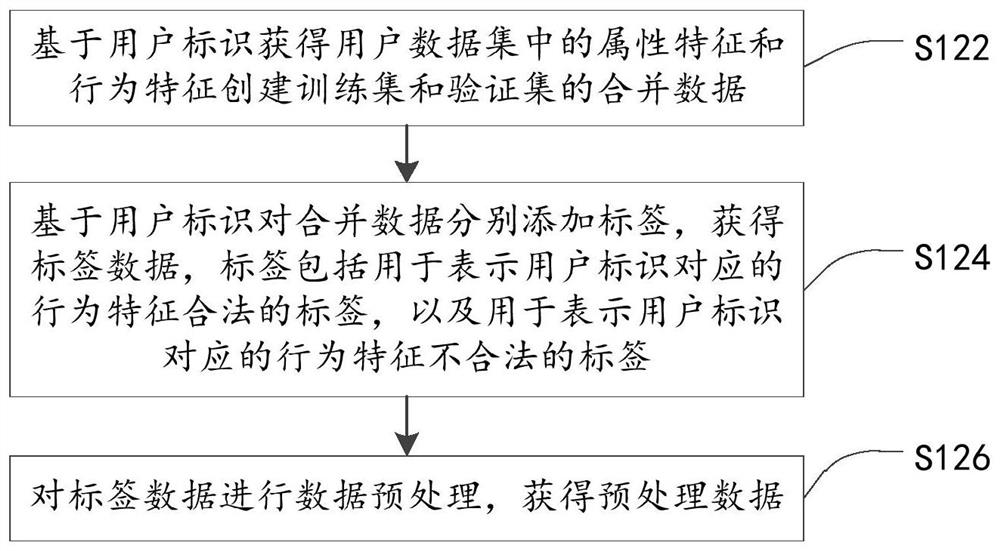
The invention provides a threat behavior detection and model establishment method and a device, electronic equipment and a storage medium, and relates to the technical field of network security. The threat behavior detection model establishment method comprises the steps of establishing a training set and a verification set based on attribute features and behavior features in a user data set; calling an LGBMClassifier interface instantiation model, and setting model parameters of the interface instantiation model; and training the interface instantiation model based on the training set and theverification set to obtain a LightGBM-based threat behavior detection model; the detection model is used for outputting an illegal probability based on an input detection feature, and the detection feature comprises an attribute feature and a behavior feature of a to-be-detected user. Threat behavior detection is performed through the threat behavior detection model without setting a separate detection model for each user, and the LightGBM algorithm has the characteristic of parallel calculation, so that the detection efficiency is improved, and the consumption of computing resources is reduced.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
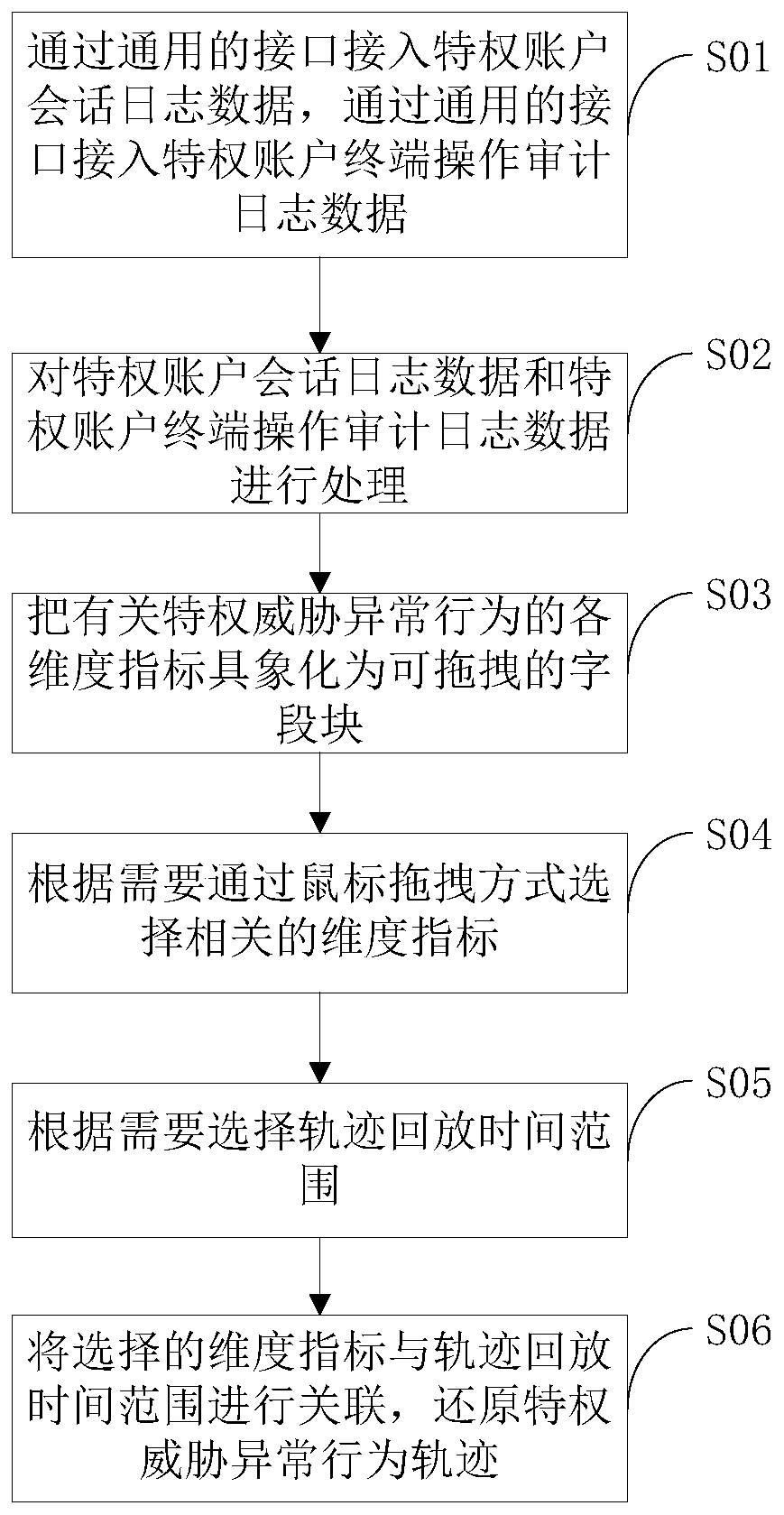
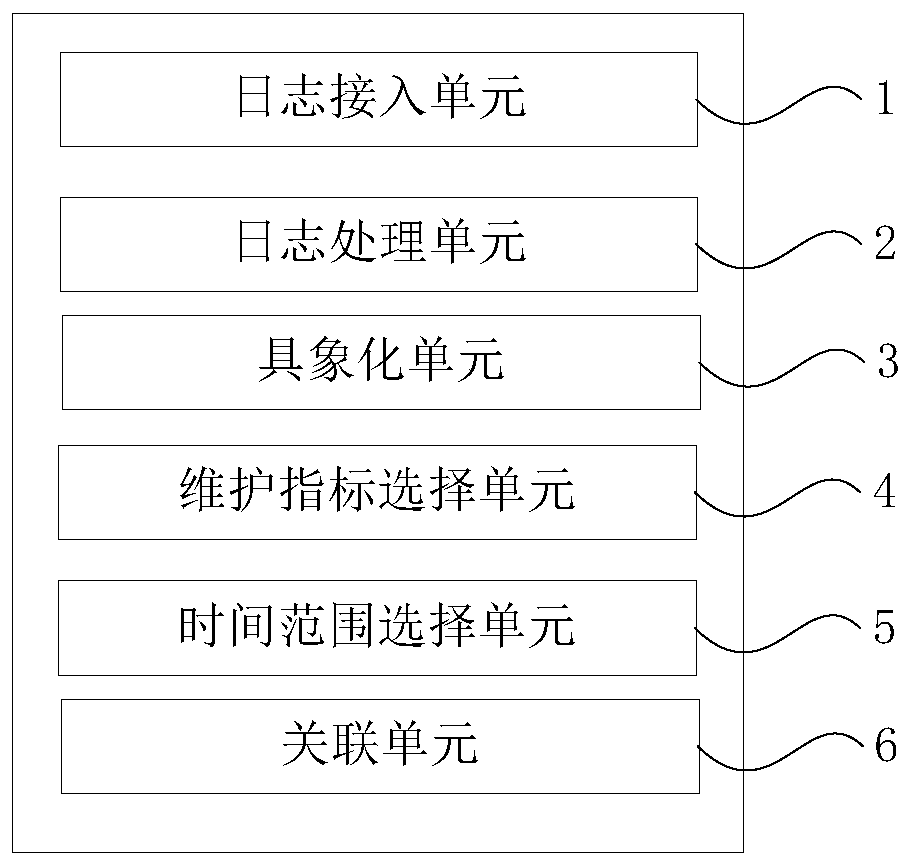
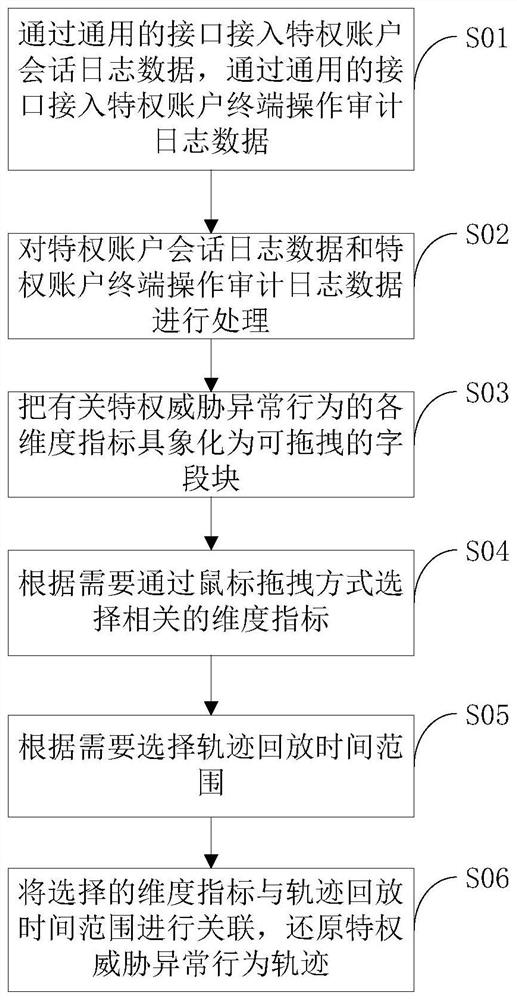
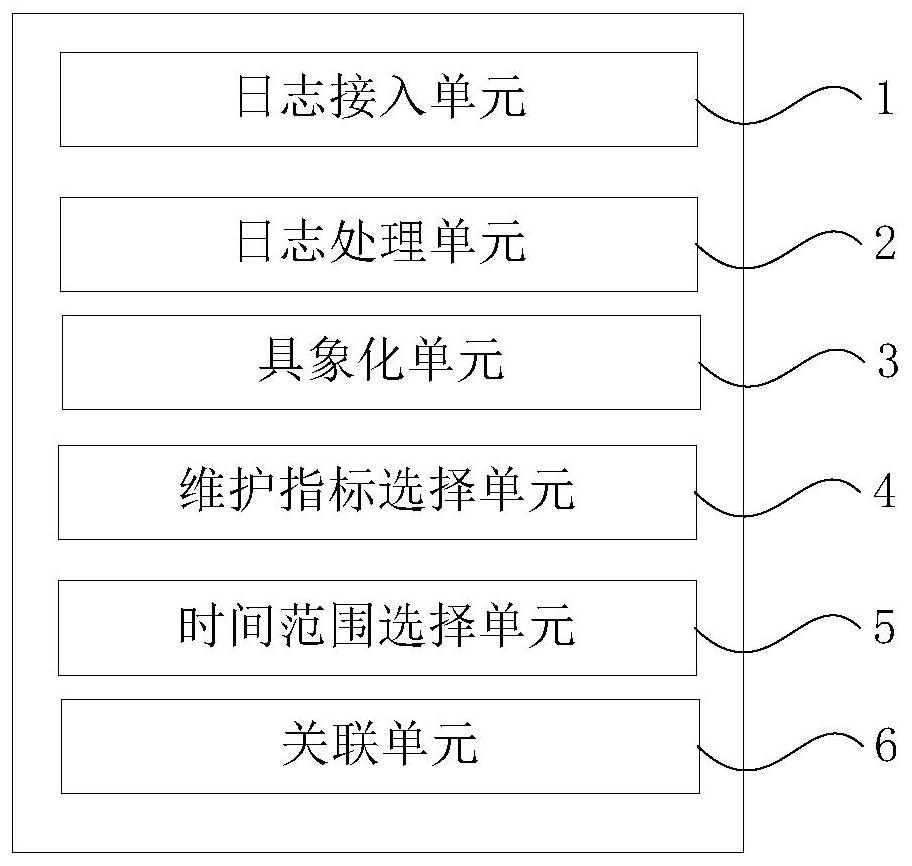
Dragging-based privileged threat behavior track associated playback method and device
ActiveCN110516440ARealize track playback analysisImprove timelinessPlatform integrity maintainanceTime rangeInternet privacy
The invention discloses a dragging-based privileged threat behavior track associated playback method and device, being applied to a privileged account threat analysis system. The dragging-based privileged threat behavior track associated playback method comprises the following steps: A) accessing privileged account session log data, and accessing privileged account terminal operation audit log data; B) processing the privileged account session log data and the privileged account terminal operation audit log data; C) visualizing each dimension index related to privilege threat abnormal behaviors into a draggable field block; D) selecting related dimension indexes through a mouse dragging mode according to needs; E) selecting a track playback time range as required; and F) associating the selected dimension index with the trajectory playback time range, and restoring the privileged threat abnormal behavior trajectory. According to the dragging-based privileged threat behavior track associated playback method, even related personnel who do not understand technologies or are not deep in technologies can rapidly achieve track playback analysis of privilege threat abnormal behaviors in asimple mouse dragging combination association mode, and timeliness and usability are improved.
Owner:广州海颐信息安全技术有限公司
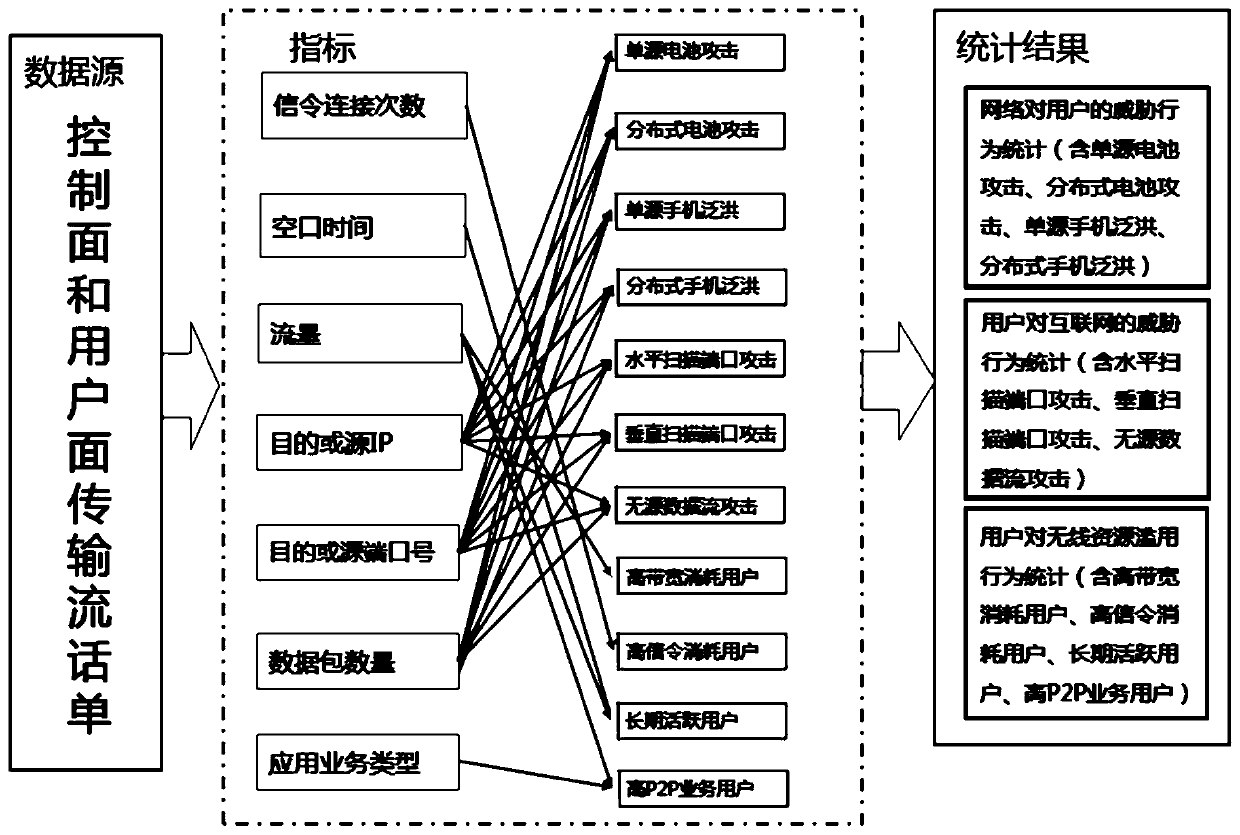
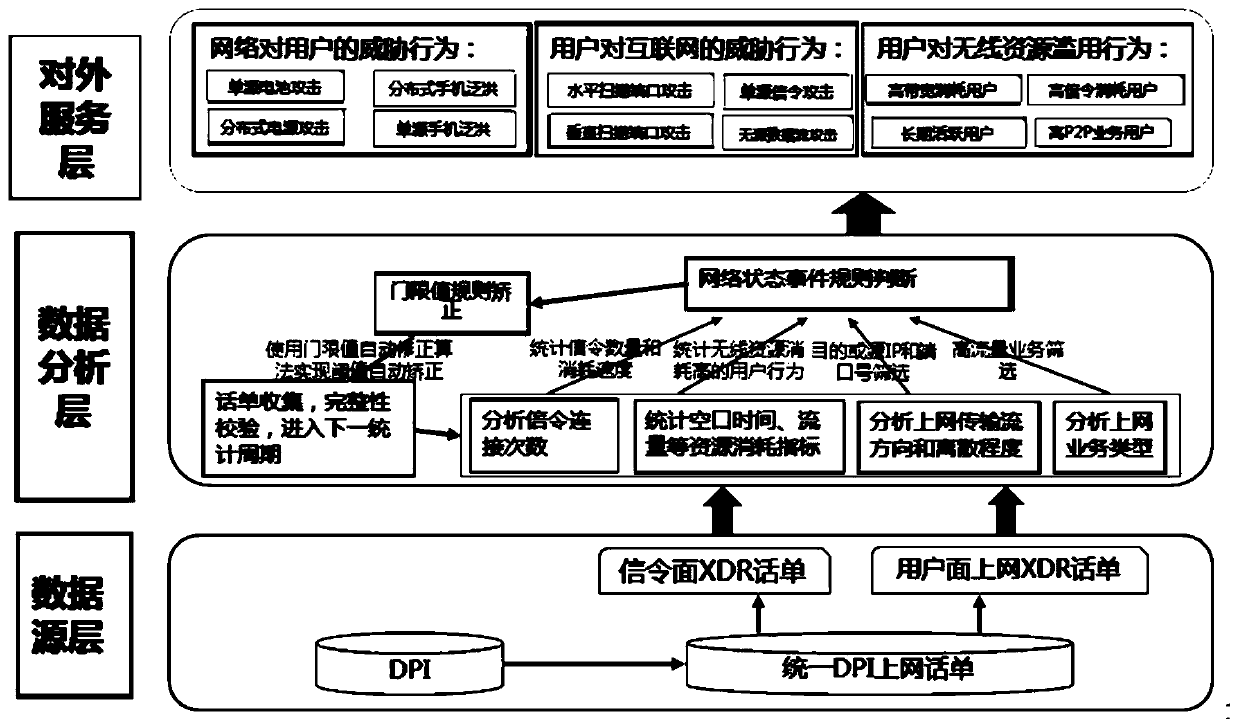
Network security protection method based on XDR telephone bill data
The invention relates to a network security protection method based on XDR telephone bill data. The method comprises that: abnormal behaviors of users are identified according to XDR telephone bill data, network security protection is performed then, and identification for the abnormal behaviors of the users Specifically comprises, according to the indexes of the XDR telephone bill data, identifying the abnormal behaviors of the users, wherein the indexes comprise signaling connection times, air interface time, flow, destination or source IP, destination or source port number, data packet number and / or application service type, and the user abnormal behaviors comprise threat behaviors of a network to a user, threat behaviors of the user to the Internet and abuse behaviors of the user to wireless resources. Compared with the prior art, the abnormal behaviors of the wireless user network are effectively monitored, then network security protection measures are taken, bad behaviors of thenetwork are purified, a green and safe network environment is achieved, and the method has the advantages of being wide in recognition range, effective and the like.
Owner:SHANGHAI TANGSHENG INFORMATION TECH
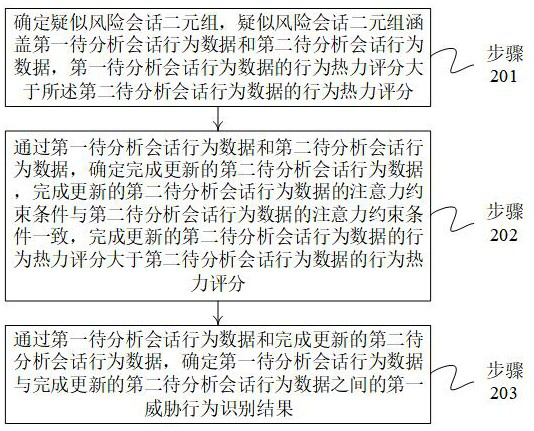
Threat behavior analysis method based on big data analysis and server
The invention provides a threat behavior analysis method based on big data analysis and a server, and the method comprises the steps: determining updated second to-be-analyzed session behavior data through first to-be-analyzed session behavior data and second to-be-analyzed session behavior data; the accuracy and reliability of the first threat behavior recognition result determined through the first to-be-analyzed session behavior data and the updated second to-be-analyzed session behavior data are better than those of the threat behavior recognition result determined through the first to-be-analyzed session behavior data and the second to-be-analyzed session behavior data; in this way, threat behavior recognition processing can be accurately and credibly realized as much as possible through limited to-be-analyzed session behavior data, so that the recognition efficiency of threat behaviors is improved, and the operation pressure of a big data analysis server is reduced.
Owner:深圳市众成信息技术有限公司
Method and device for researching and judging security alarm threats
ActiveCN113364802BThe judgment result is accurateReasonable threat factorKnowledge representationInference methodsKnowledge graphAlarm correlation
The invention discloses a security alarm threat research and judgment method and device, belonging to the technical field of network security. The method includes: constructing a network security intelligence knowledge graph based on historical intelligence database data, forming a security alarm correlation subgraph of security alarm data on this basis, performing entity threat coefficient calculation on the security alarm correlation subgraph, and obtaining the information of each threat entity element. The entity threat coefficient comprehensively calculates the security alarm threat degree of the security alarm data. The present invention applies the knowledge map technology to the field of threat intelligence, builds a network security intelligence knowledge map based on historical intelligence database data, and makes full use of the historical threat behavior of threat entity elements in the threat research and judgment of security alarms, making the judgment results more accurate.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP +2
A heuristic detection method, system and storage medium for nested class files
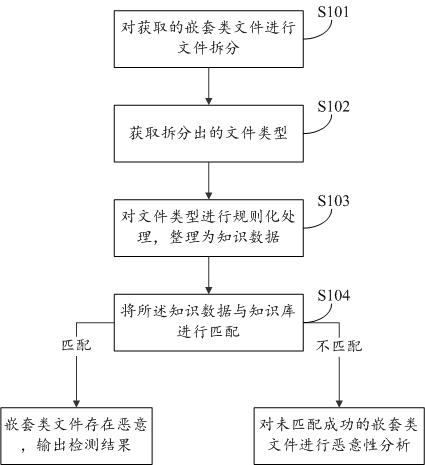
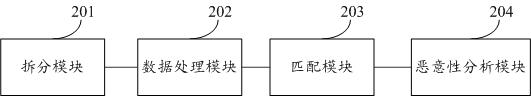
ActiveCN108229168BDetection speedImprove accuracyDigital data information retrievalPlatform integrity maintainanceAlgorithmTheoretical computer science
The present invention proposes a heuristic detection method, system, and storage medium for nested files. The method includes: splitting the obtained nested files; Regularized processing, sorting into knowledge data; matching the knowledge data with the knowledge base; if the matching is successful, the nested class file is malicious, output the detection result, and end the detection; otherwise, the nested class file that has not been matched successfully file for malicious analysis. The present invention does not need complex logical analysis, nor does it need a virtual environment to dynamically execute scripts, but performs heuristic detection based on the nature of threatening behaviors that will occur in abnormal environments based on nested class files, which can effectively improve detection speed, accuracy, etc.
Owner:HARBIN ANTIY TECH
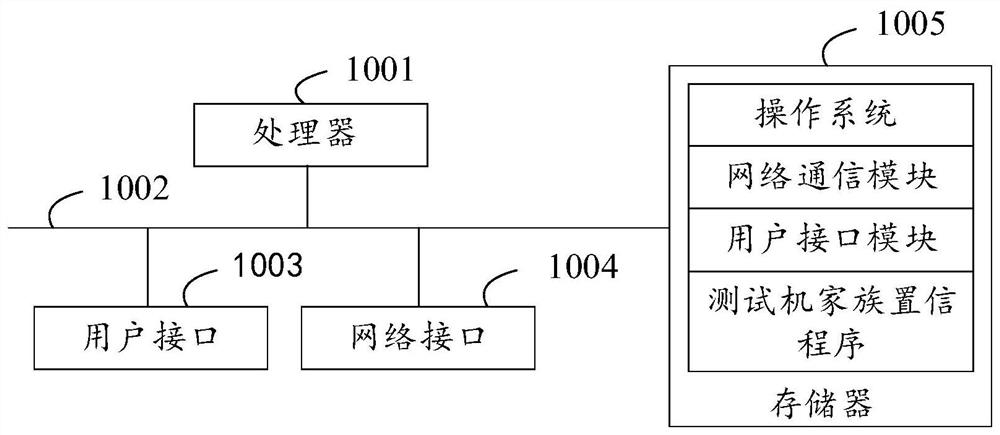
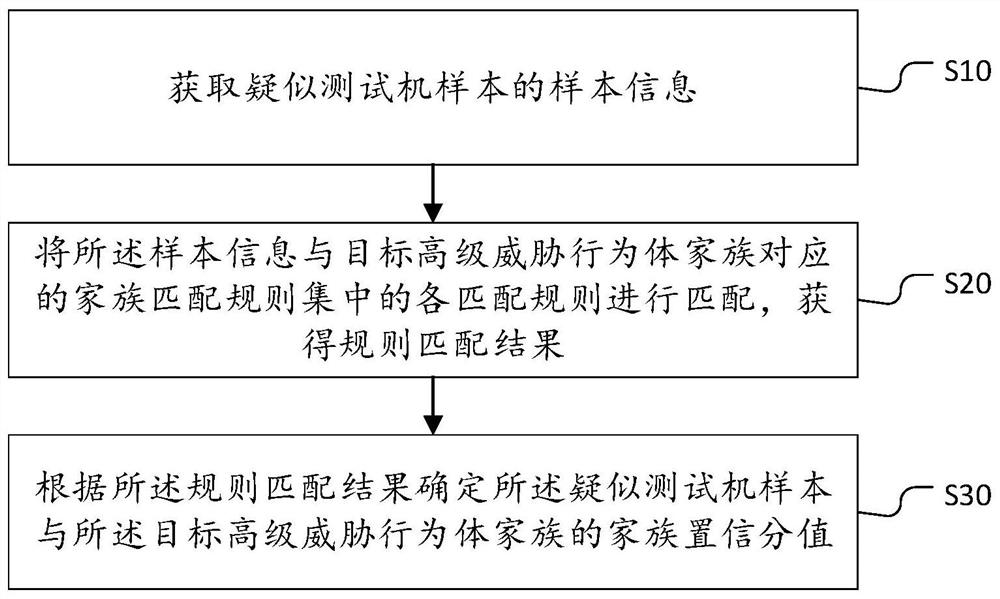
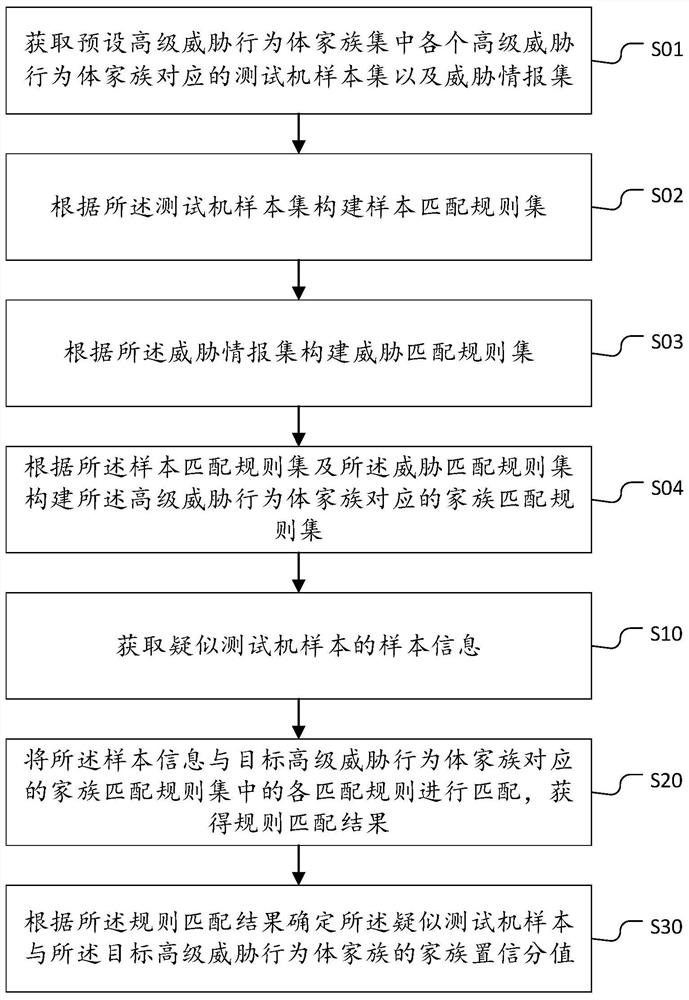
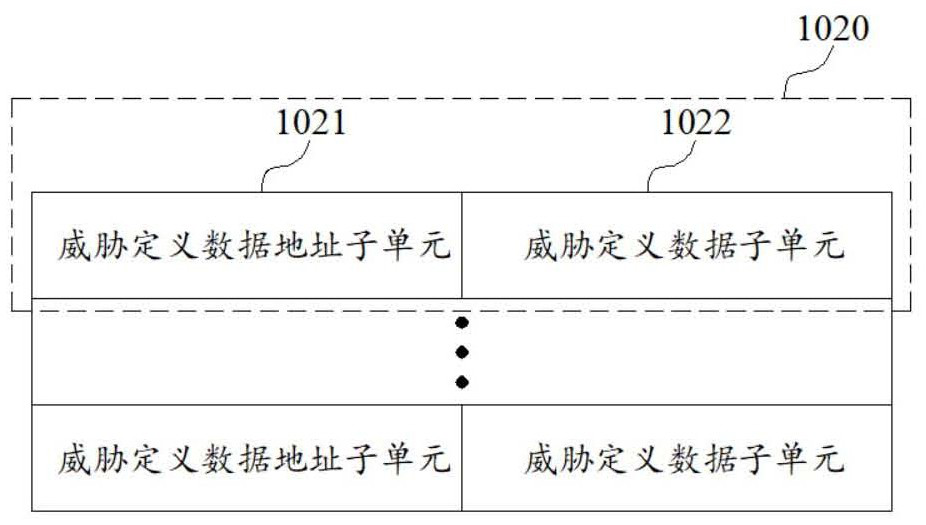
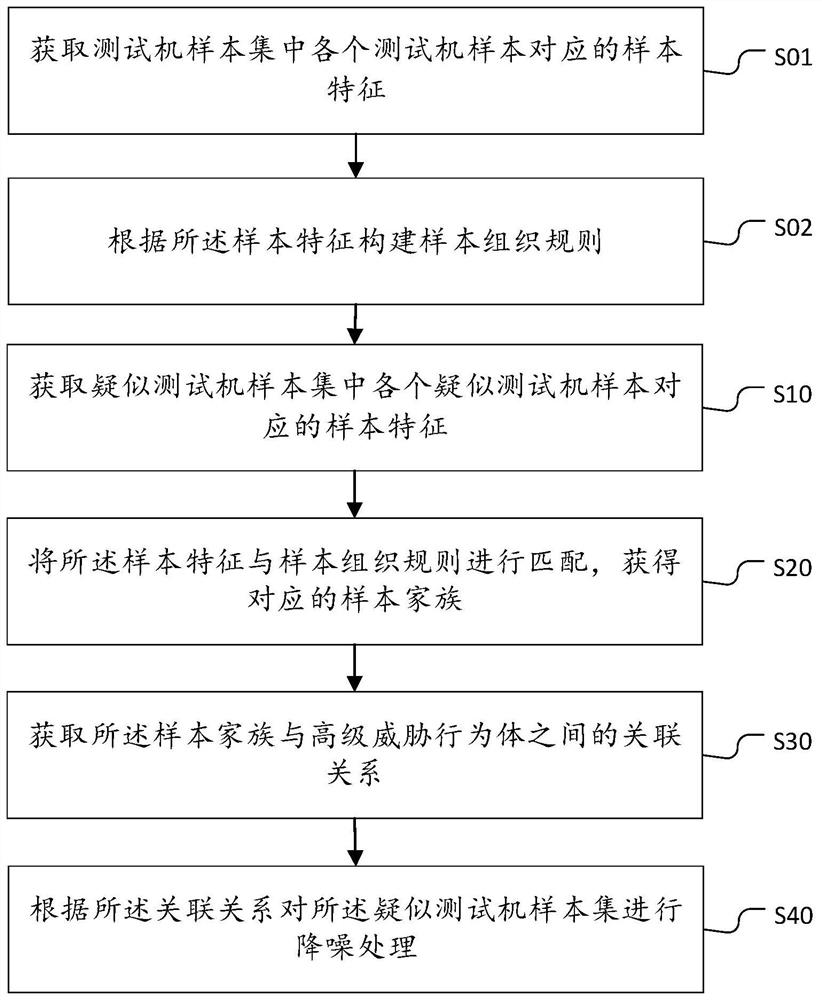
Testing machine family confidence method, device and equipment and storage medium
PendingCN114499909AQuick fixImprove matching efficiencyCharacter and pattern recognitionSpecial data processing applicationsEngineeringThreatening behaviour
The invention belongs to the technical field of network security, and discloses a method, a device and equipment for testing family confidence of a machine, and a storage medium. The method comprises the steps of obtaining sample information of a suspected test machine sample; matching the sample information with each matching rule in a family matching rule set corresponding to the target advanced threat behavior body family to obtain a rule matching result; and determining family confidence scores of the suspected test machine sample and the target advanced threat behavior body family according to a rule matching result. As the family matching rule set is preset, real-time setting is not needed, the matching efficiency is high, the family confidence score can be quickly determined, and then the possibility that the suspected test machine sample belongs to the target advanced threat behavior body family can be judged through the family confidence score; whether the suspected test machine sample is the advanced threat behavior body or not can be judged according to the possibility that the suspected test machine sample belongs to the target advanced threat behavior body family, so that whether the suspected test machine sample is the advanced threat behavior body or not can be quickly identified.
Owner:三六零数字安全科技集团有限公司
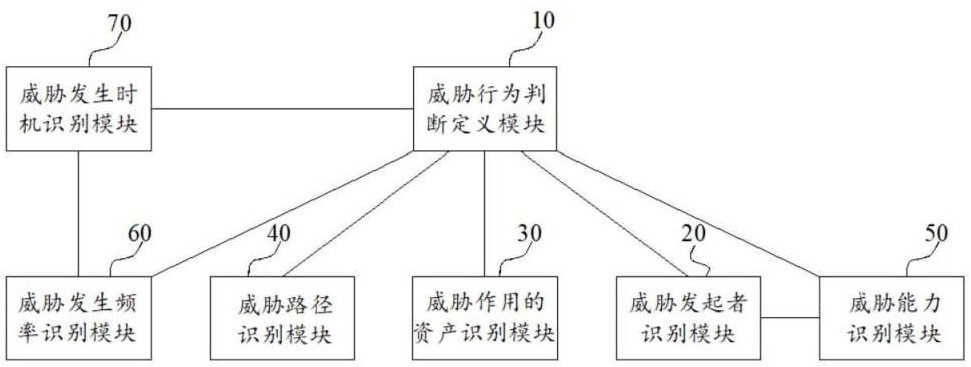
Functional impairment network security threat identification device and information system
ActiveCN112688971BImprove accuracyReduce difficultyTransmissionIdentification deviceFunctional impairment
The present invention provides a function-impaired network security threat identification device and an information system, the device comprising: a threat behavior judgment definition module, a threat initiator identification module, a threat action asset identification module, a threat path identification module, and a threat capability identification module , a threat occurrence frequency identification module and a threat occurrence timing identification module. The function-impaired network security threat identification device provided by the present invention can comprehensively and accurately identify the function-impaired network security threat, so as to accurately analyze and calculate the risks brought by the function-impaired network security threat; and the present invention provides The information system can accurately take different levels of risk protection measures for different levels of risk of function-damaging network security threats, which improves the security protection performance of the information system provided by the present invention.
Owner:国家信息中心
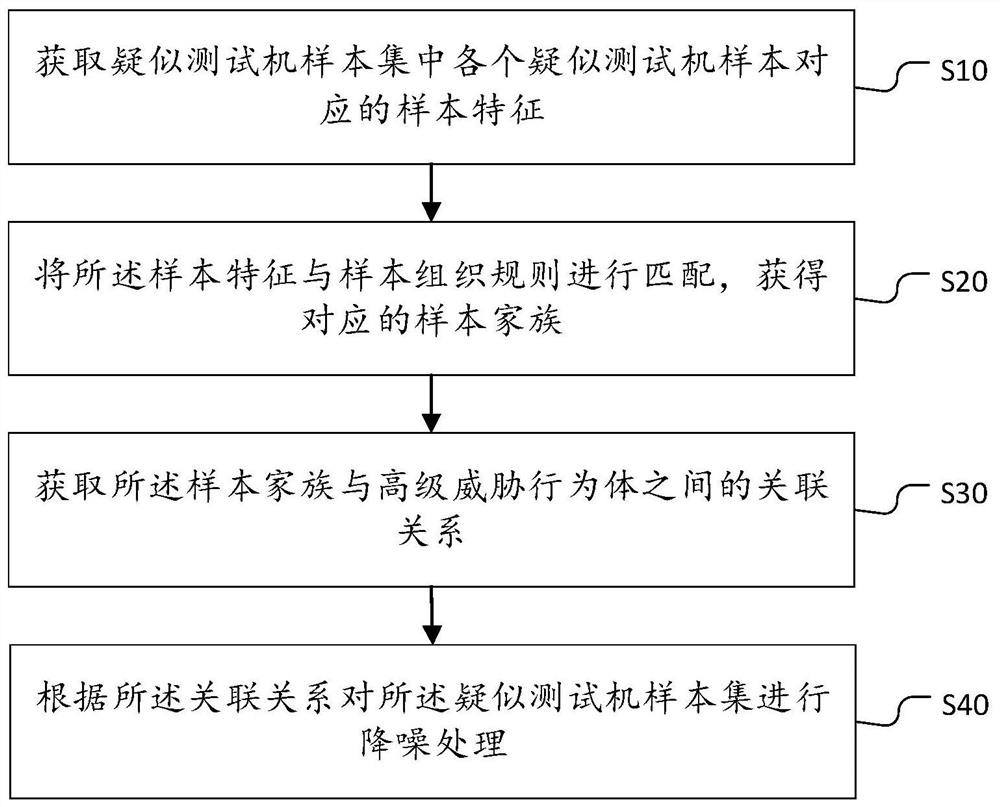
Data noise reduction method and device based on sample dimension, equipment and storage medium
PendingCN114490233AFast analysisReduce the difficulty of analysisHardware monitoringCharacter and pattern recognitionAlgorithmNoise reduction
The invention belongs to the technical field of network security, and discloses a data noise reduction method and device based on sample dimensions, equipment and a storage medium. According to the method, sample features corresponding to all suspected test machine samples in a suspected test machine sample set are obtained, the sample features are matched with a sample organization rule, a corresponding sample family is obtained, and then the incidence relation between the sample family and an advanced threat behavior body is obtained; and performing noise reduction processing on the suspected test machine sample set according to the association relationship. According to the method, the sample features of the suspected test machine samples are matched with the sample organization rules to obtain the corresponding sample family, so that the suspected test machine sample set can be quickly de-noised according to the incidence relation between the sample family and the advanced threat behavior body; and the samples with relatively low possibility that the suspected test machine samples are test machine samples are cleared, so that the loss of computing resources is reduced, the sample analysis speed is increased, and the sample analysis difficulty is reduced.
Owner:三六零数字安全科技集团有限公司
Method and device for associated playback of privileged threat behavior tracks based on drag and drop
ActiveCN110516440BRealize track playback analysisImprove timelinessPlatform integrity maintainanceDrag and dropTime range
The invention discloses a drag-and-drop-based method and device for associated playback of privileged threat behavior tracks, which are applied to a privileged account threat analysis system. The method includes: A) accessing privileged account session log data, accessing privileged account terminal operation audit log data; B) process the privileged account session log data and the privileged account terminal operation audit log data; C) visualize the indicators of various dimensions related to the abnormal behavior of the privileged threat into draggable field blocks; D) drag and drop the Select the relevant dimension index by dragging; E) Select the track playback time range according to the needs; F) Associate the selected dimension index with the track playback time range to restore the track of privileged threat abnormal behavior. The invention enables relevant personnel who do not understand technology or are not deep in technology to quickly realize the trajectory playback analysis of privilege threat abnormal behavior through a simple mouse dragging and combining method, thereby improving timeliness and ease of use.
Owner:广州海颐信息安全技术有限公司
Threat handling method, device, electronic device, and computer-readable storage medium
This application provides a threat processing method, device, electronic equipment, and computer-readable storage medium. The method is applied to the target node of the cloud platform, including: grabbing its own network interaction data stream; extracting from the network interaction data stream Data flow characteristics; input data flow characteristics into the pre-trained threat behavior detection model to determine whether there is currently a threat behavior, and when there is a threat behavior, the type of threat behavior that exists; when there is a threat behavior, from the preset In the defense strategy, determine the target defense strategy corresponding to the type of threat behavior, and execute the target defense strategy. This realizes the monitoring and handling of network threats to the cloud platform itself, and strengthens the security protection of the cloud platform.
Owner:CHINA ELECTRONICS CORP 6TH RES INST
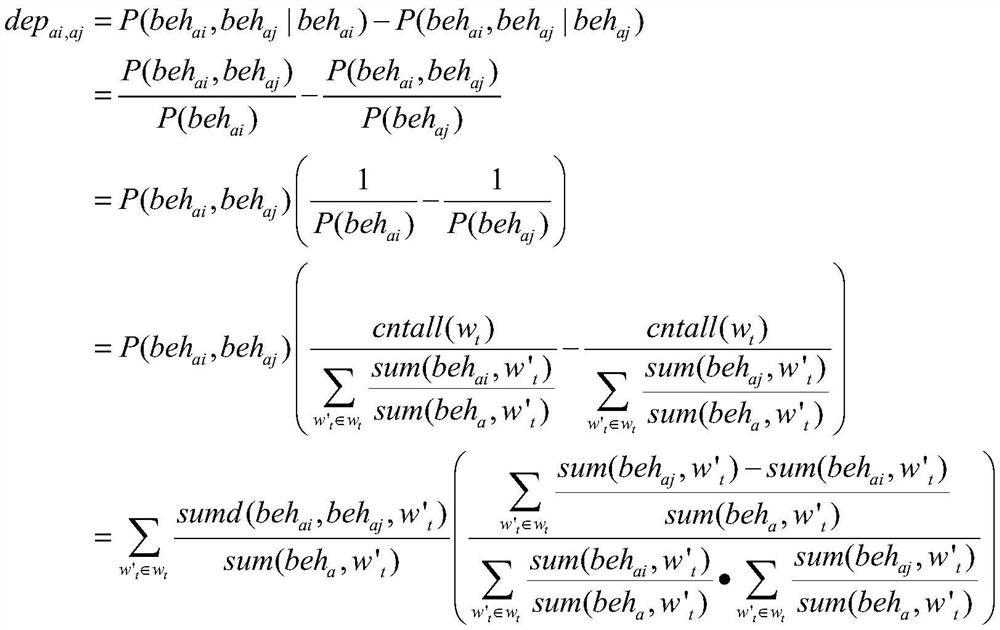
Mining method for discovering dependency relationship between threat behaviors, terminal and storage medium
ActiveCN112261006APrevent Threat AttacksImprove incident response capabilitiesTransmissionAlgorithmBusiness enterprise
The invention provides a mining method for discovering a dependency relationship between threat behaviors, a terminal and a storage medium, and the method comprises the steps: collecting log files ofall users a in a system, cleaning and arranging data in the log files, forming an employee behavior set S = {behai}, and carrying out the statistics of the time span wt in the set S; counting a behavior occurrence probability P (behai) and a behavior co-occurrence probability P (behai, behaj) based on S and wt; calculating dependency relationship values depai, aj based on the two probabilities, wherein the depai, aj reflects the dependency degree of the behavior behai on the behavior behaj; constructing an attack dependence matrix M according to all depai and aj, wherein the matrix M reflectsthe dependence relationship between every two of all behaviors of one employee; and obtaining an attack behavior path pahag -> ak through the M, wherein the pahag -> ak represents a series of completeattack actions which are most likely to occur. According to the method, the potential relationship among employee behaviors is found out, and the dependency relationship is quantified. Enterprises can quickly find out two behaviors with the closest relationship through the dependency relationship numerical value, early warning is conducted on threat behaviors according to a preset danger threshold value, and the enterprises are prevented from suffering from some threat attacks from the inside.
Owner:中孚安全技术有限公司 +3
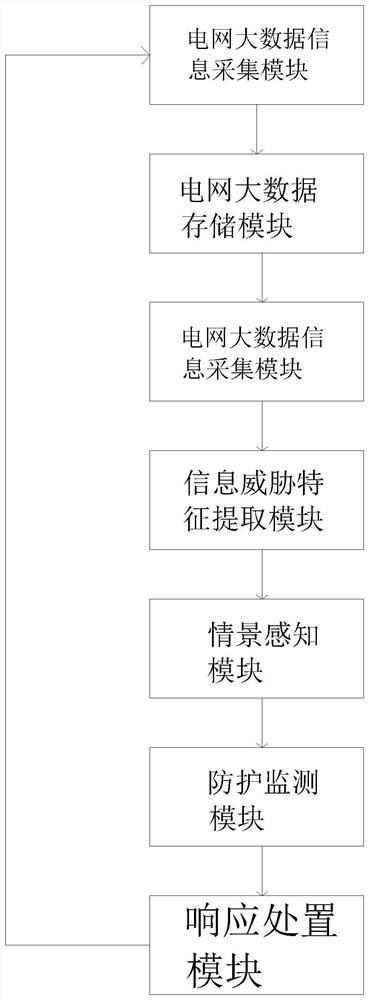
Electric power information threat context awareness and defense system based on big data
PendingCN114493338AImprove monitoring effectImprove emergency response capabilitiesResourcesInformation securityData store
The invention discloses an electric power information threat context awareness and defense system based on big data. The system comprises a power grid big data information acquisition module, a power grid big data storage module, an information threat feature extraction module, a context awareness module, a protection monitoring module and a response processing module. Wherein the power grid big data information acquisition module is used for acquiring power grid threat information; the power grid big data storage module is used for storing power grid threat intelligence; the information threat feature extraction module is used for extracting operation features of current power grid threat intelligence and realizing extraction of threat feature information; the context awareness module generates a threat behavior warning according to the threat feature information extracted by the information threat feature extraction module; the protection monitoring module is used for blocking threat behaviors; and the response processing module is used for studying and judging the threat behavior, obtaining evidence and feeding back the threat behavior to the context awareness module. The method provides powerful guarantee for information security of power systems, communication systems and the like, and has a good application effect.
Owner:STATE GRID HEBEI ELECTRIC POWER RES INST +2
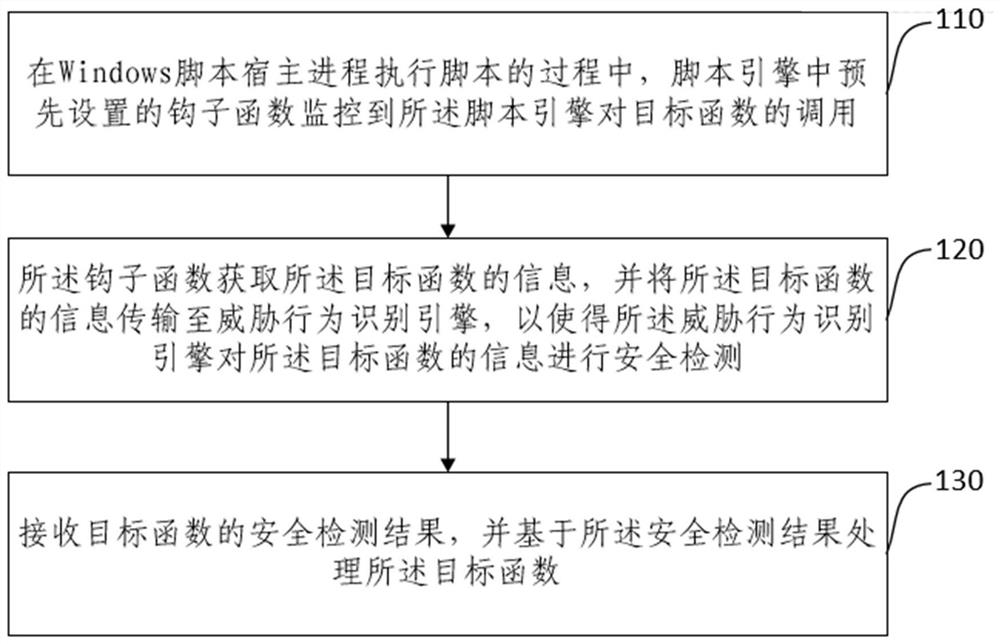
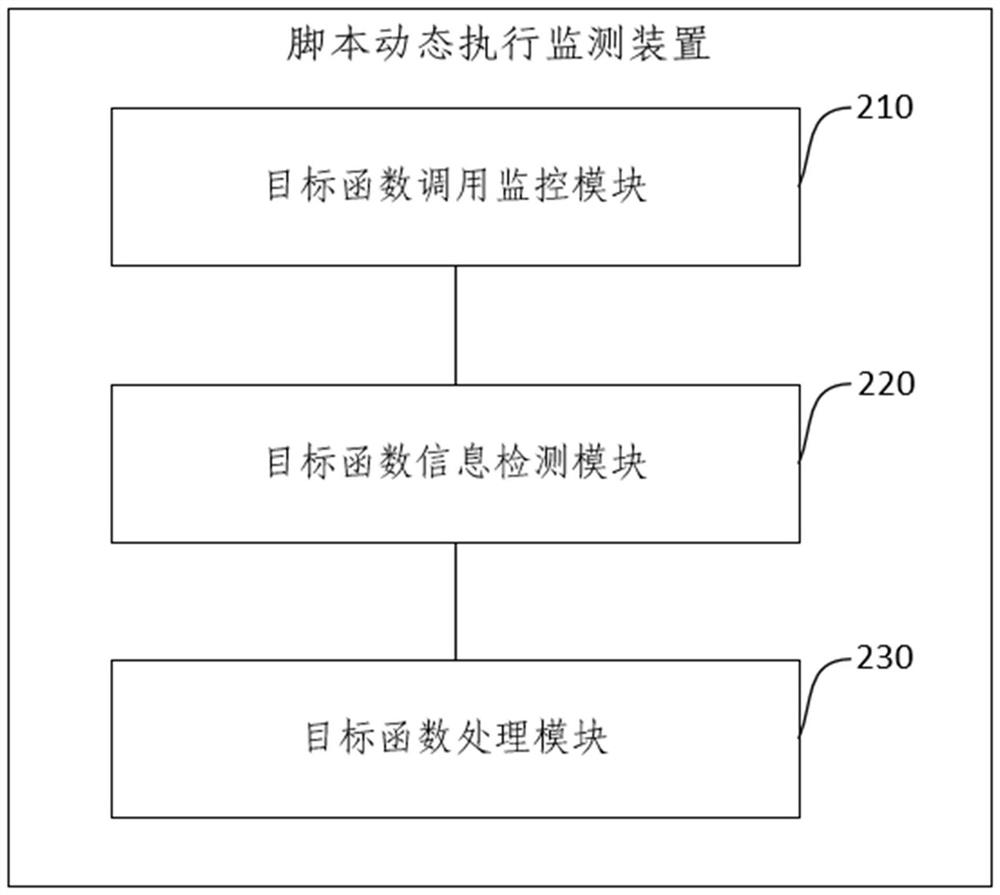
Script dynamic execution monitoring method and device, electronic equipment and storage medium
PendingCN114491527AImprove security monitoring capabilitiesPlatform integrity maintainanceEmbedded systemOperating system
The invention provides a script dynamic execution monitoring method and device, electronic equipment and a storage medium, and the method comprises the steps: in a process that a Windows script host process executes a script, a hook function preset in a script engine monitors the call of the script engine to a target function; the hook function obtains information of the target function and transmits the information of the target function to a threat behavior recognition engine, so that the threat behavior recognition engine performs security detection on the information of the target function; and receiving a security detection result of the target function, and processing the target function based on the security detection result. According to the method, the target function called by the script engine is obtained through the preset hook function, and the target function information is detected through the threat behavior recognition engine, so that the security protection monitoring capability on malicious script execution is greatly improved.
Owner:BEIJING QIANXIN TECH +1
Industrial robot system security threat evaluation method based on time-sharing frequency
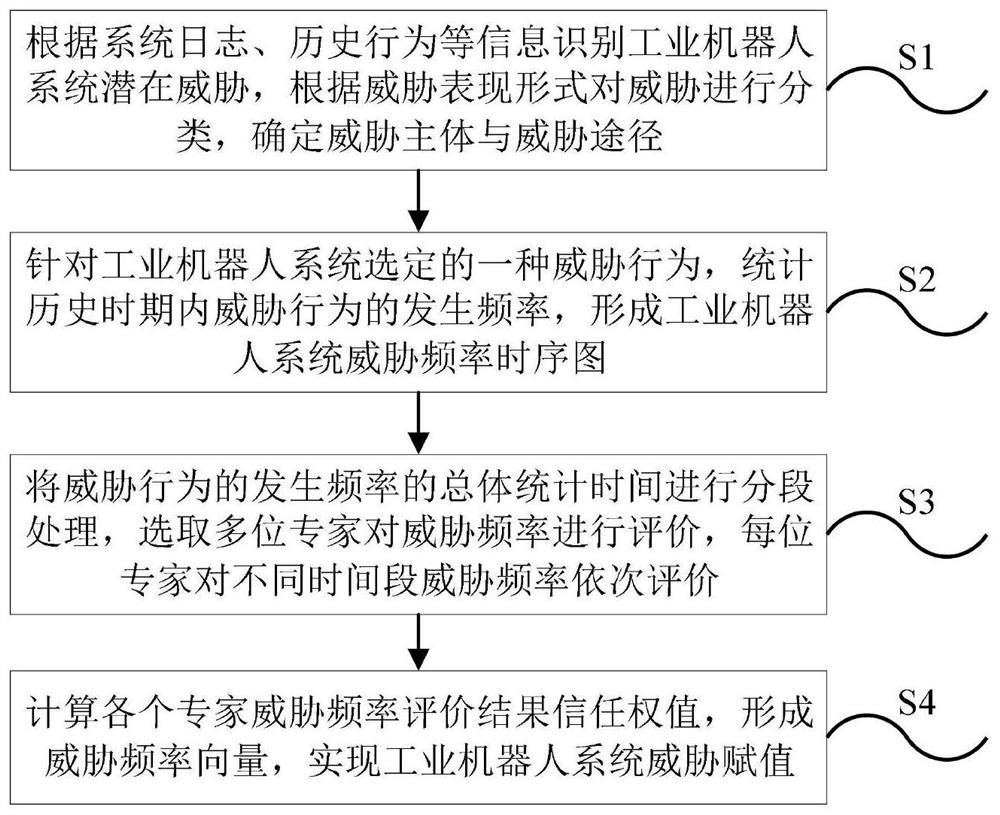
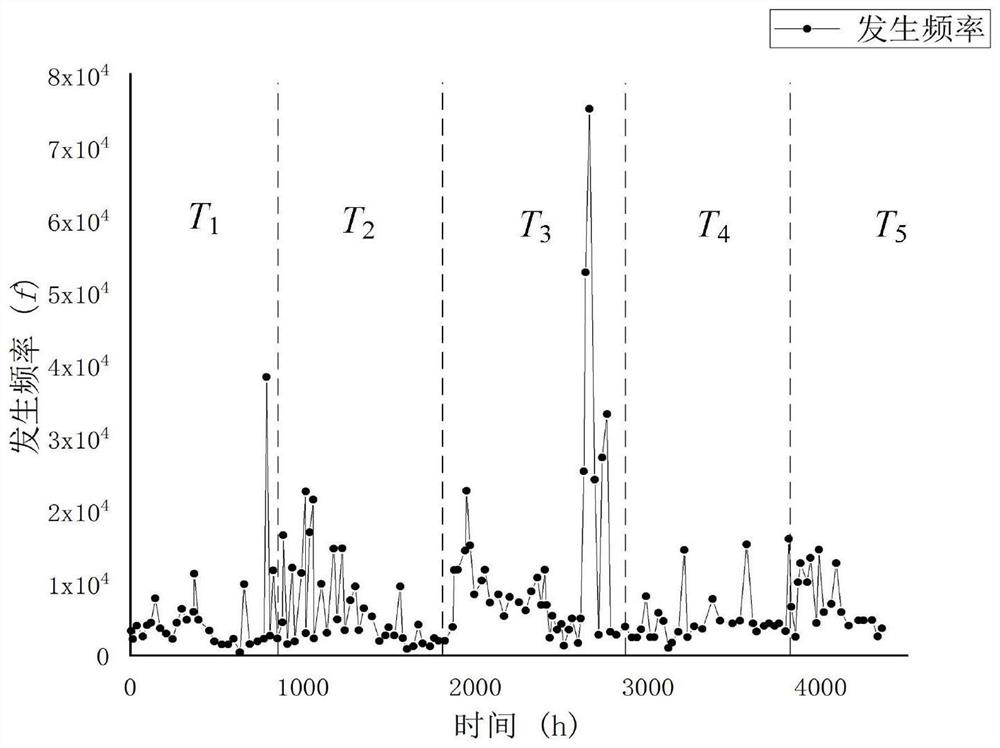
PendingCN114019942AReduce the impactThe influence of evaluation is reducedProgramme controlElectric testing/monitoringIndustrial roboticsData mining
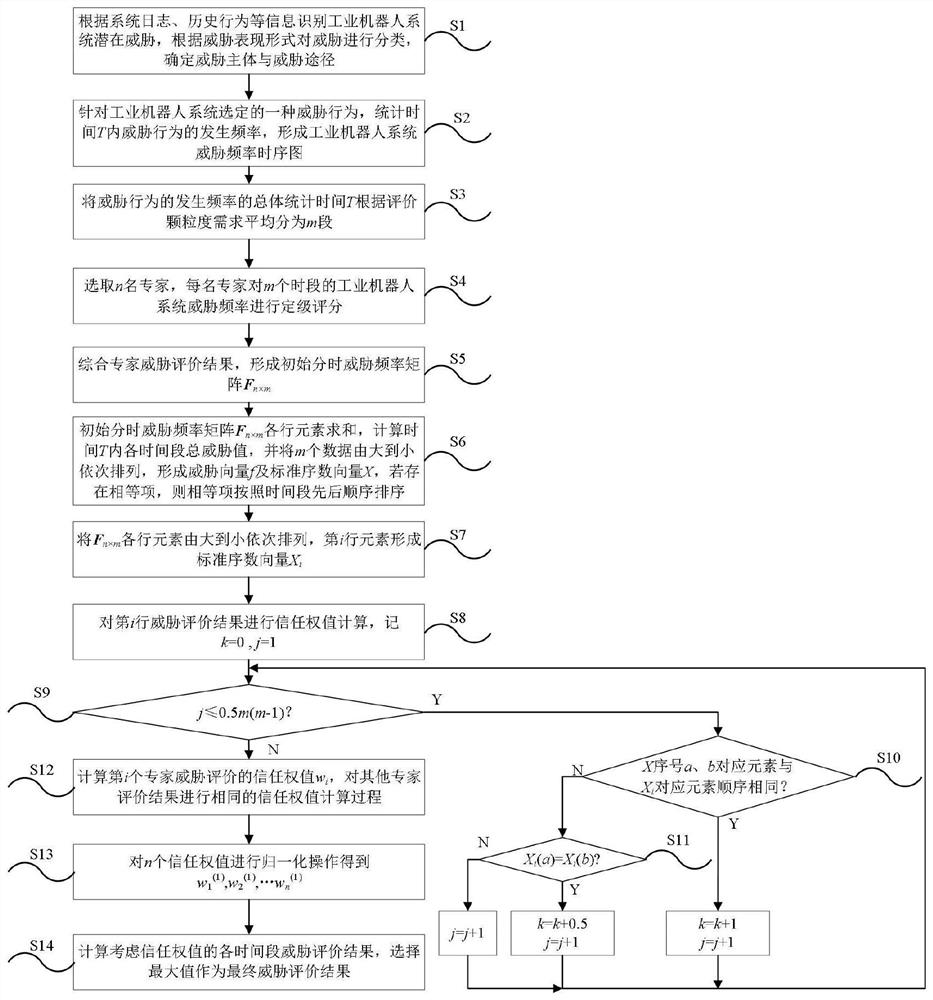
The invention discloses an industrial robot system security threat evaluation method based on time-sharing frequency. The method comprises the following steps of: S1, recognizing potential threats of an industrial robot system according to system logs, historical behaviors and other information, classifying the threats according to a threat expression form, and determining a threat subject and a threat approach; S2, aiming at a threat behavior selected by the industrial robot system, counting occurrence frequency of the threat behavior in a historical period, and forming a threat frequency sequence diagram of the industrial robot system; S3, performing segmentation processing on the total statistical time of the occurrence frequency of the threat behavior, selecting multiple experts to evaluate the threat frequency, and sequentially evaluating the threat frequency in different time periods by each expert; and S4, calculating a threat frequency evaluation result trust weight of each expert, forming a threat frequency vector, and realizing threat assignment of the industrial robot system. According to the method, security threat evaluation can be carried out on the industrial robot system with a relatively long historical security threat behavior record.
Owner:HARBIN INST OF TECH
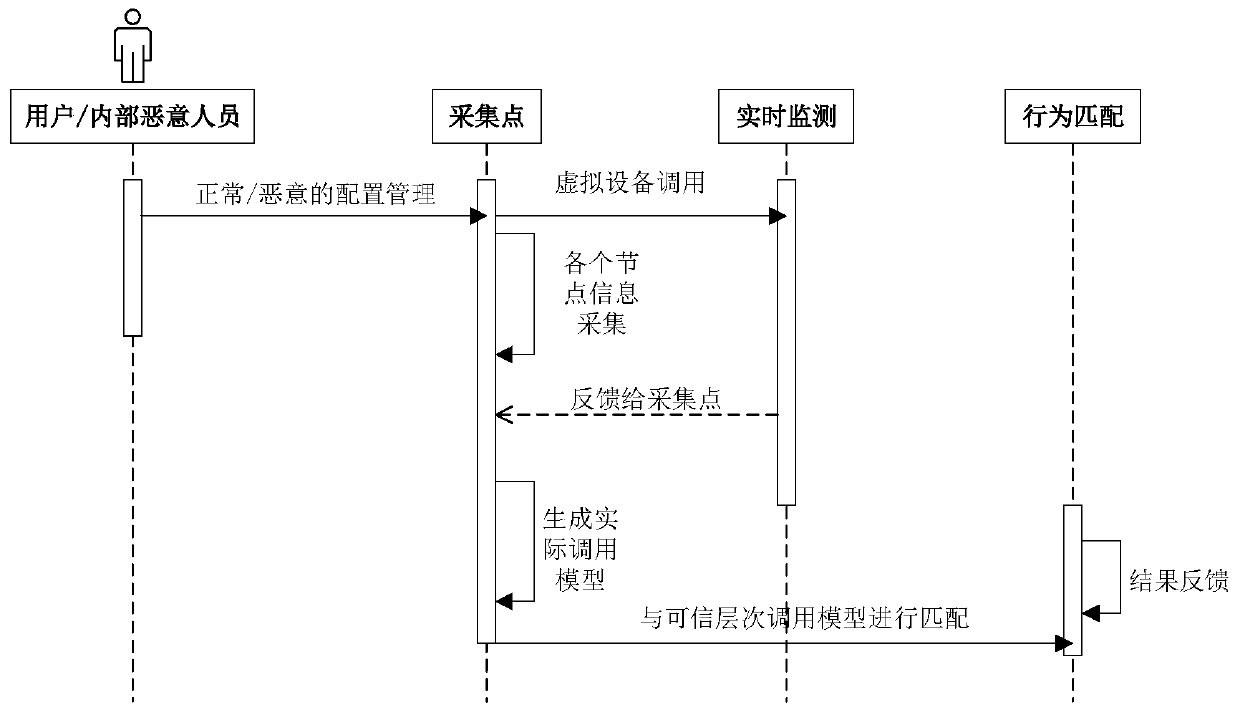
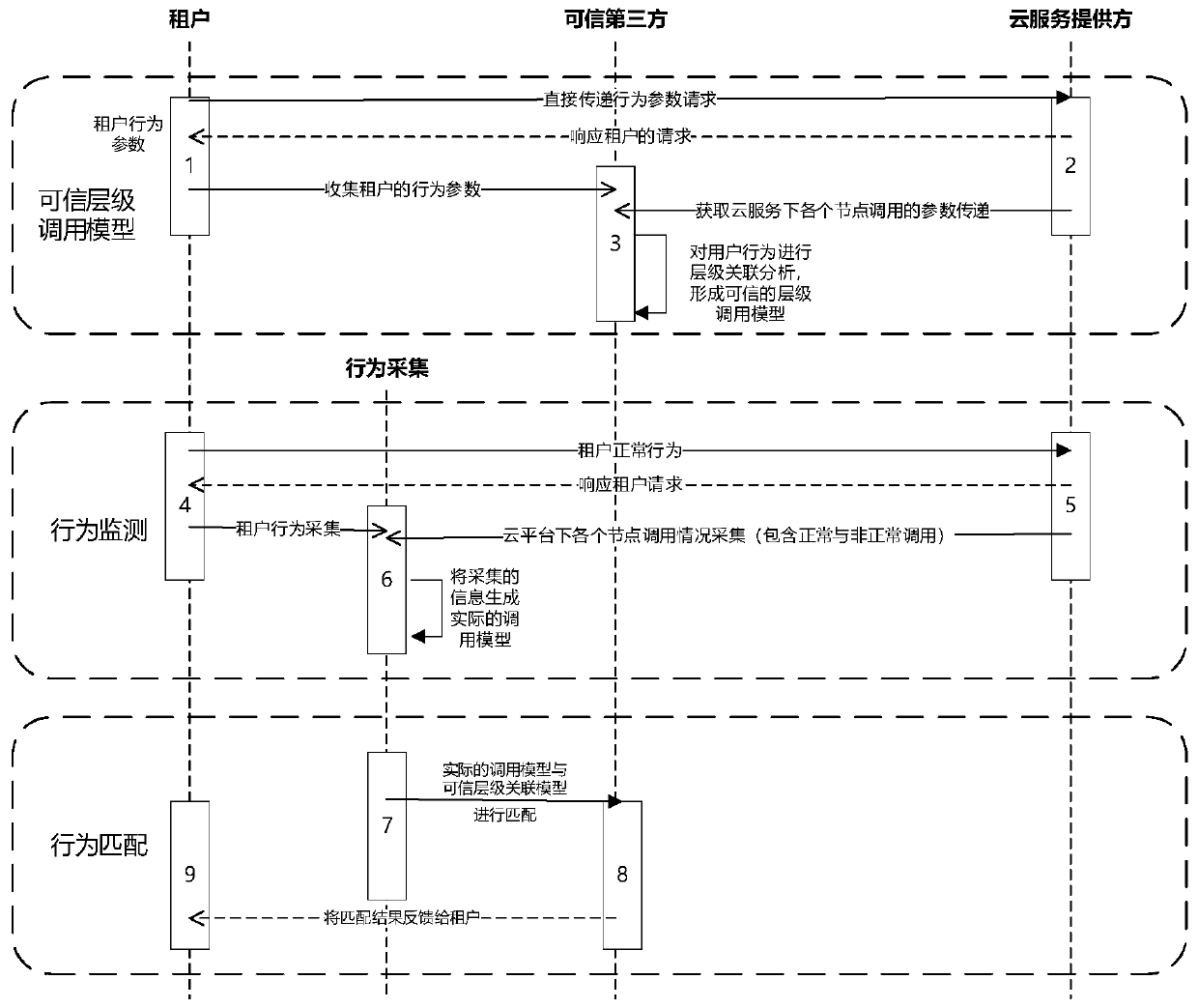
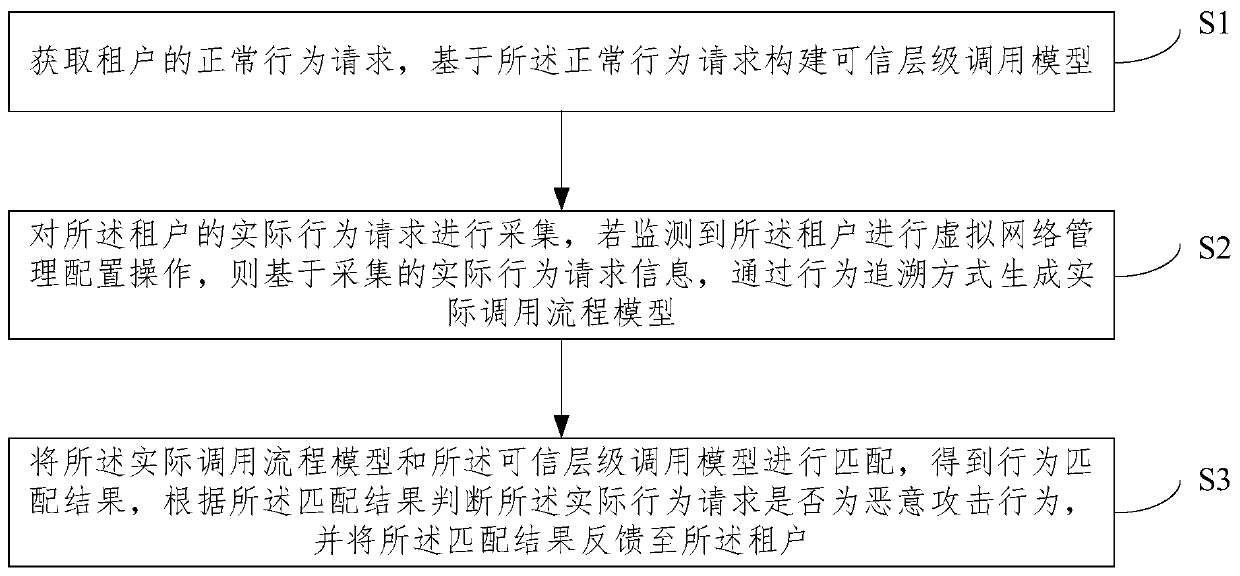
Method and system for monitoring threat behaviors in virtual network
ActiveCN110958267AEnsure safetyRealize internal security risk monitoringData switching networksAttackAssociation model
The embodiment of the invention provides a method and a system for monitoring threat behaviors in a virtual network. The method comprises: acquiring a tenant normal behavior request, and constructinga credible level calling model based on the normal behavior request; collecting actual behavior requests of the tenants, and if it is monitored that the tenants carry out virtual network management configuration operation, generating an actual call process model through a behavior tracing mode based on the collected actual behavior request information; and matching the actual call process model with the trusted level call model to obtain a behavior matching result, judging whether the actual behavior request is a malicious attack behavior or not according to the matching result, and feeding back the matching result to the tenant. According to the embodiment of the invention, by adopting a behavior tracing and monitoring method for internal security threats and combining behavior matching,on the basis of a credible hierarchical association model, an actual behavior is compared with a credible behavior model, and feedback is realized, so that internal security risk monitoring is realized, and the security of a virtual network in a cloud environment is ensured.
Owner:BEIJING UNIV OF TECH
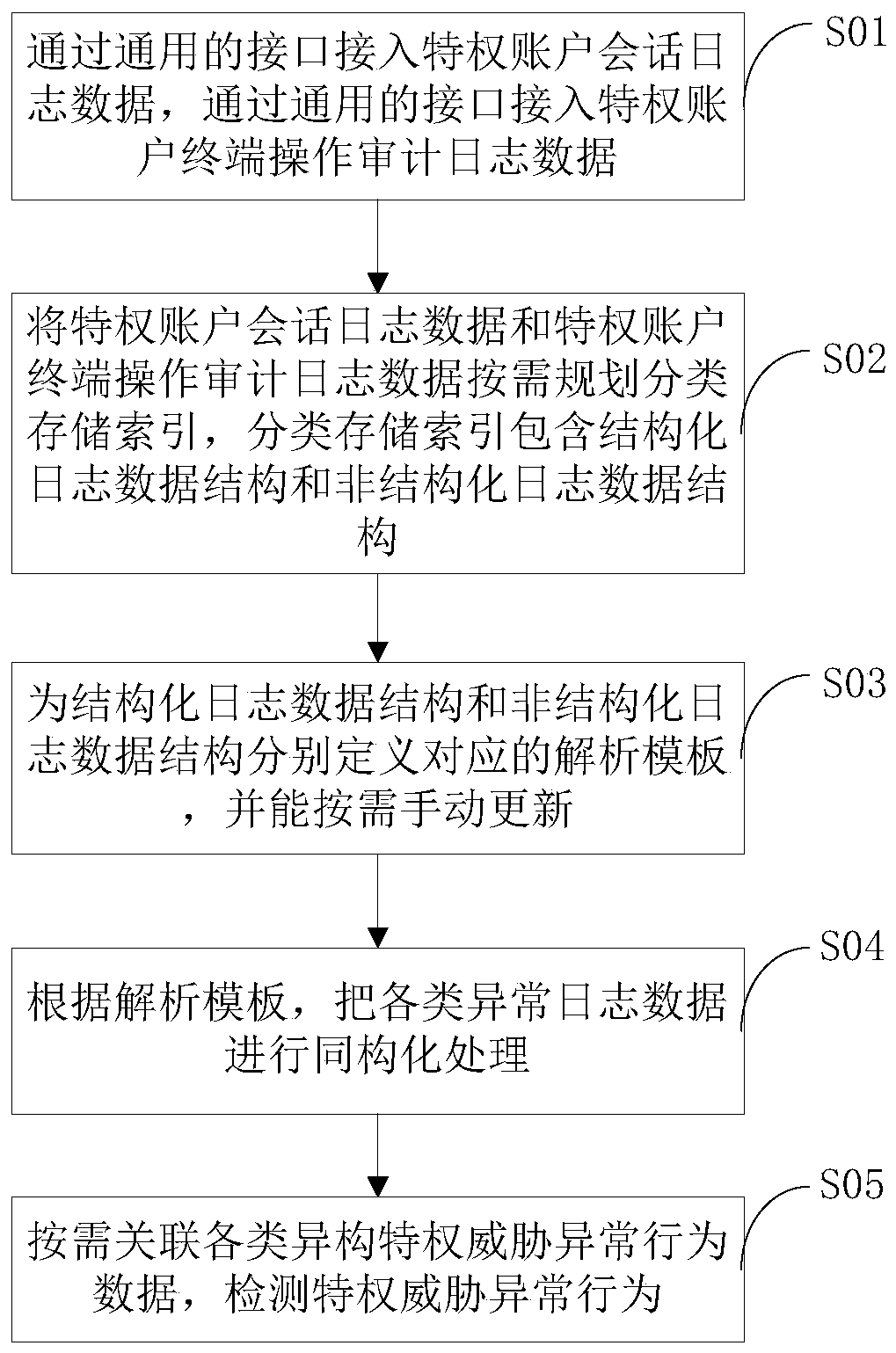
Method and device compatible with structured and unstructured privileged threat behavior data
InactiveCN110532760AReduce the risk of lossDatabase updatingDigital data authenticationBusiness enterpriseEngineering
The invention discloses a method and a device compatible with structured and unstructured privilege threat behavior data. The method comprises the following steps: accessing privilege account sessionlog data and privilege account terminal operation audit log data; planning classified storage indexes for the privileged account session log data and the privileged account terminal operation audit log data as required, wherein the classified storage indexes comprise a structured log data structure and an unstructured log data structure; respectively defining corresponding analysis templates for the structured log data structure and the unstructured log data structure, and manually updating the analysis templates as required; according to the analysis template, carrying out isomorphism processing on various abnormal log data; and associating various types of heterogeneous privilege threat abnormal behavior data as required, and detecting privilege threat abnormal behaviors. According to the method, various heterogeneous log data can be accessed and analyzed in a perfect adaptation manner, and a guarantee is provided for subsequent privilege threat abnormal behavior detection and analysis, so that the risk of loss caused by privilege threat abnormal behaviors of enterprises is reduced to the minimum.
Owner:广州海颐信息安全技术有限公司
A mining method, terminal and storage medium for discovering dependencies between threat behaviors
ActiveCN112261006BPrevent Threat AttacksImprove incident response capabilitiesSecuring communicationPathPingBusiness enterprise
The present invention provides a mining method, a terminal and a storage medium for discovering dependencies between threat behaviors, collects log files of all users a in the system, cleans and organizes the data in the log files, and forms an employee behavior set S={ beh ai }, the time span w in the statistical set S t ; based on S and w t The probability of occurrence of statistical behavior P(beh ai ) and the behavior co-occurrence probability P(beh ai ,beh aj ); calculates the dependency value dep based on the two probabilities ai,aj , dep ai,aj reflects the behavior beh ai on behavior beh aj degree of dependence; according to all dep ai,aj Construct the attack dependency matrix M, which reflects the dependency between all behaviors of an employee; the attack behavior path path is obtained from M ag→ak , path ag→ak Represents a complete, most likely series of attack actions. The present invention finds potential connections between employee behaviors and quantifies such dependencies. Enterprises can quickly find out the two most closely related behaviors through the value of the dependency relationship, and warn the threat behavior according to the pre-specified risk threshold to prevent the enterprise from being attacked by some internal threats.
Owner:中孚安全技术有限公司 +3
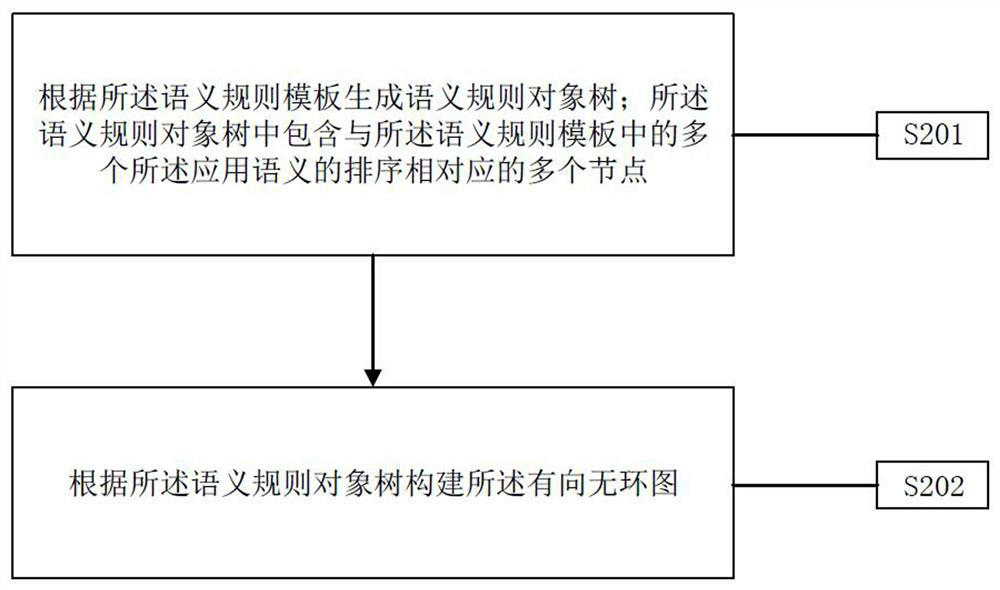
Real-time detection method and system based on threat behavior
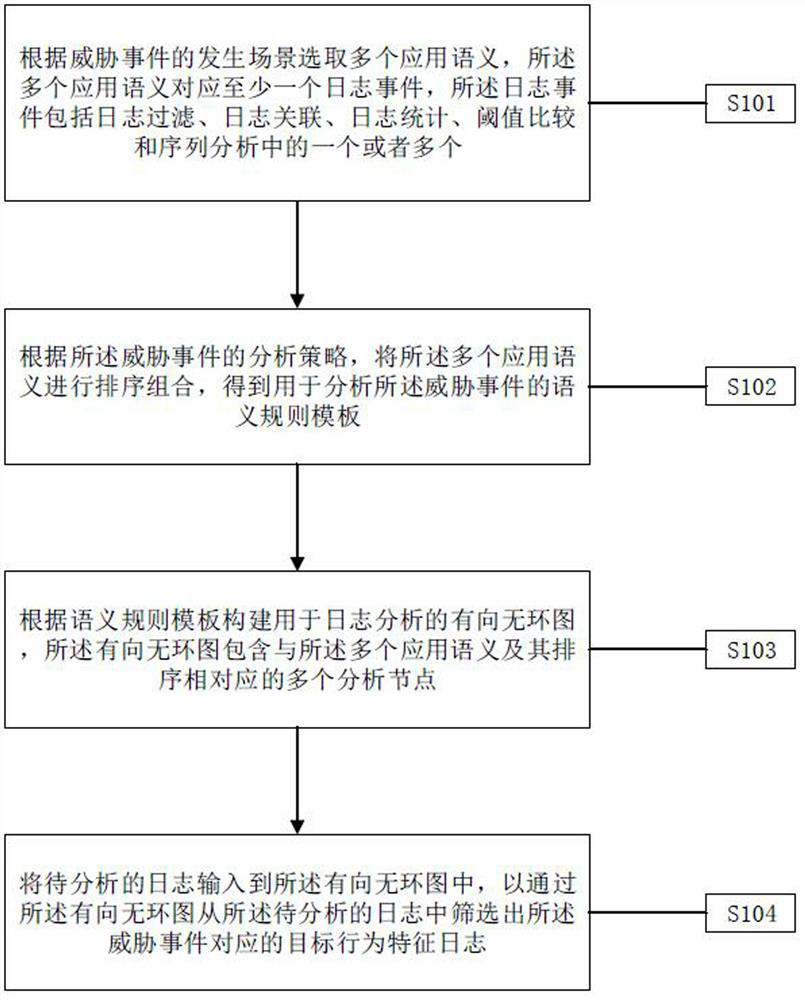
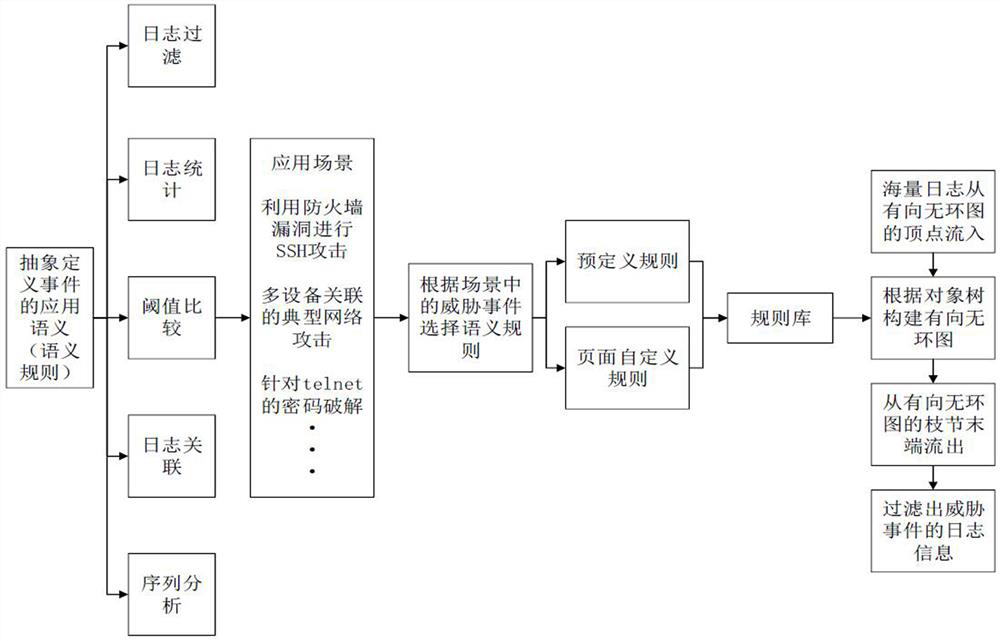
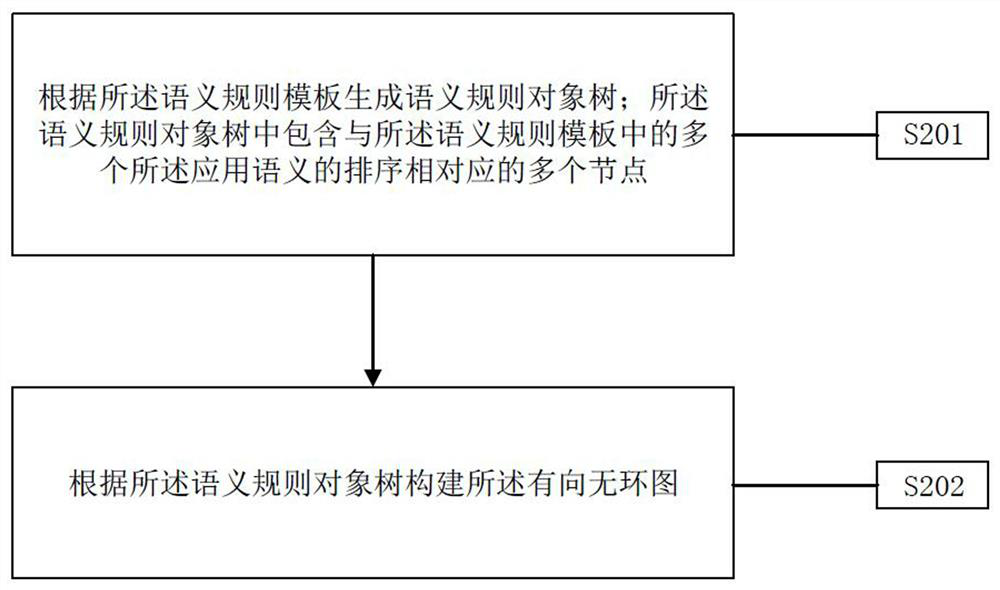
ActiveCN114531306ASolve the lack of timelinessSecuring communicationAlgorithmTheoretical computer science
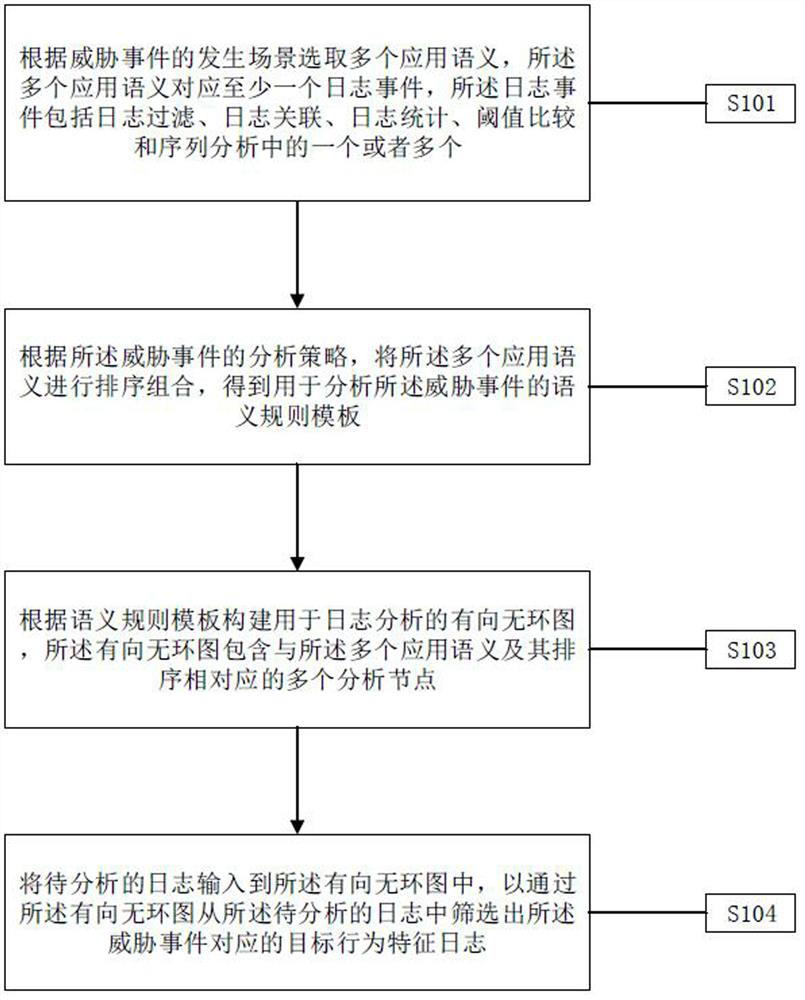
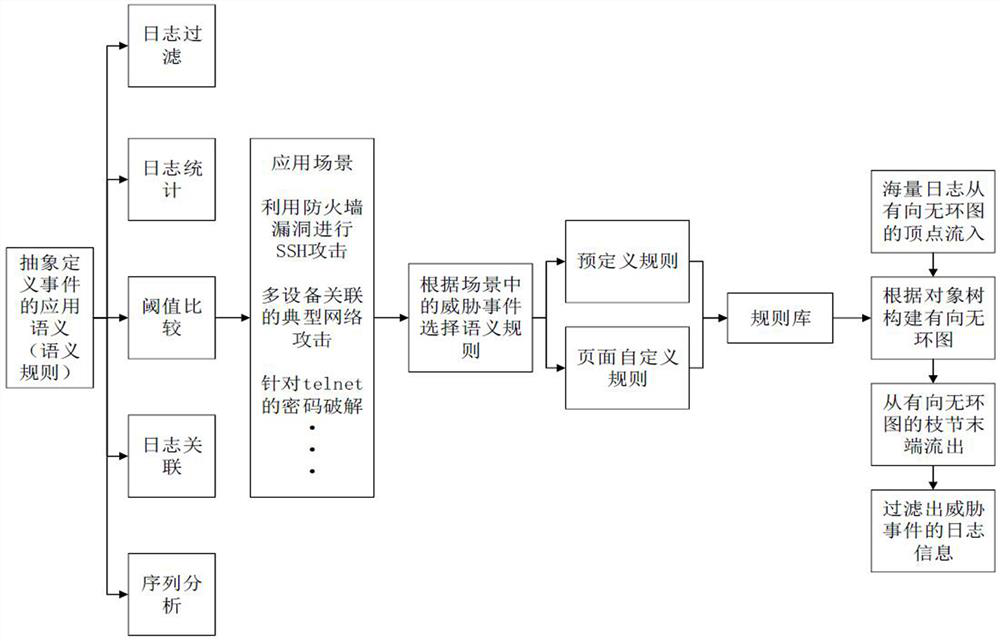
The embodiment of the invention provides a real-time detection method and system based on threat behaviors, and is applied to the technical field of computer security management. Application semantics are selected according to occurrence scenes of threat events, and a semantic rule template or a semantic rule configuration file is formed through sorting and combination according to analysis strategies of the threat events. And generating a semantic rule object tree according to the semantic rule template or the semantic rule configuration file, wherein the semantic rule object tree comprises nodes corresponding to application semantics in the semantic rule template. And finally, according to the semantic rule object tree, generating a directed acyclic graph used for checking a target behavior feature log corresponding to the threat event step by step. When the threat event is changed, the semantic rule template or the semantic rule configuration file can be redefined to generate a new semantic rule object tree, and the directed acyclic graph is updated to detect the target behavior feature log corresponding to the changed threat event in real time, so that the problem that the static network analysis of the threat event lacks timeliness is solved.
Owner:北京安博通金安科技有限公司
Threat behavior detection and model establishment method, device, electronic device and storage medium
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
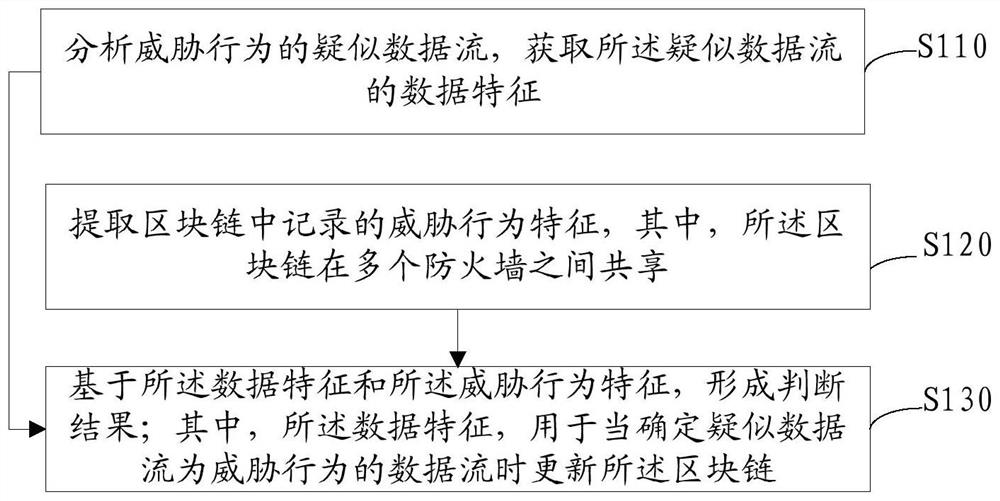
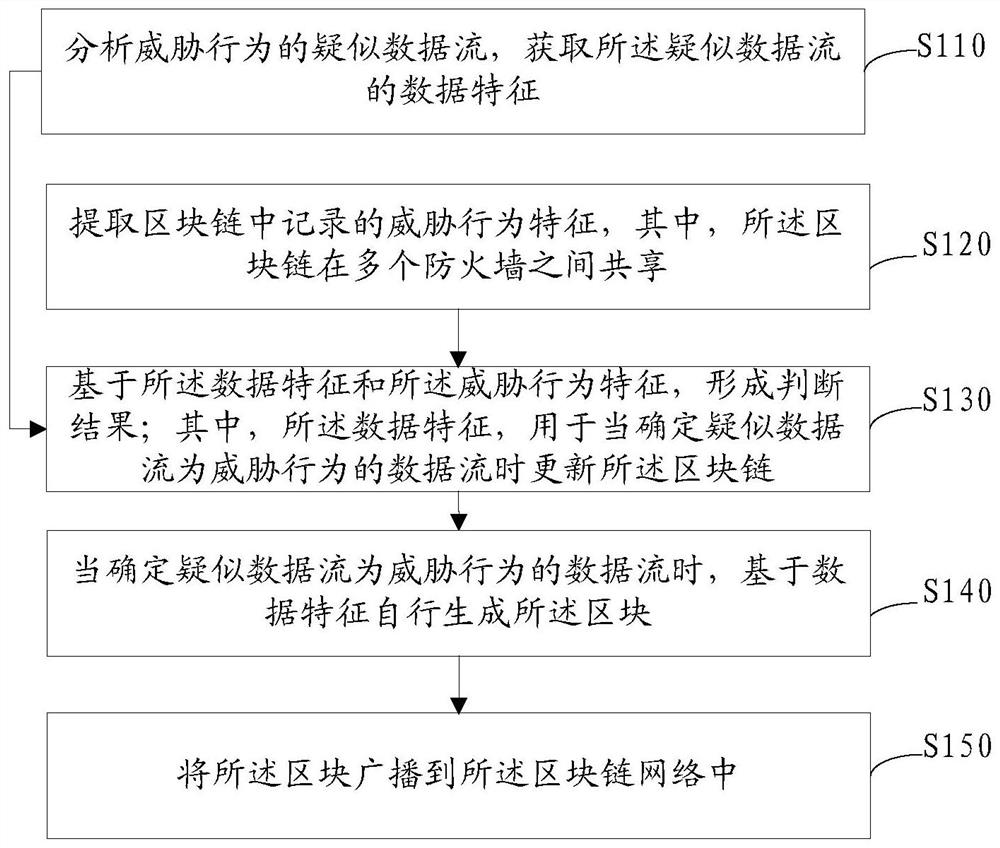
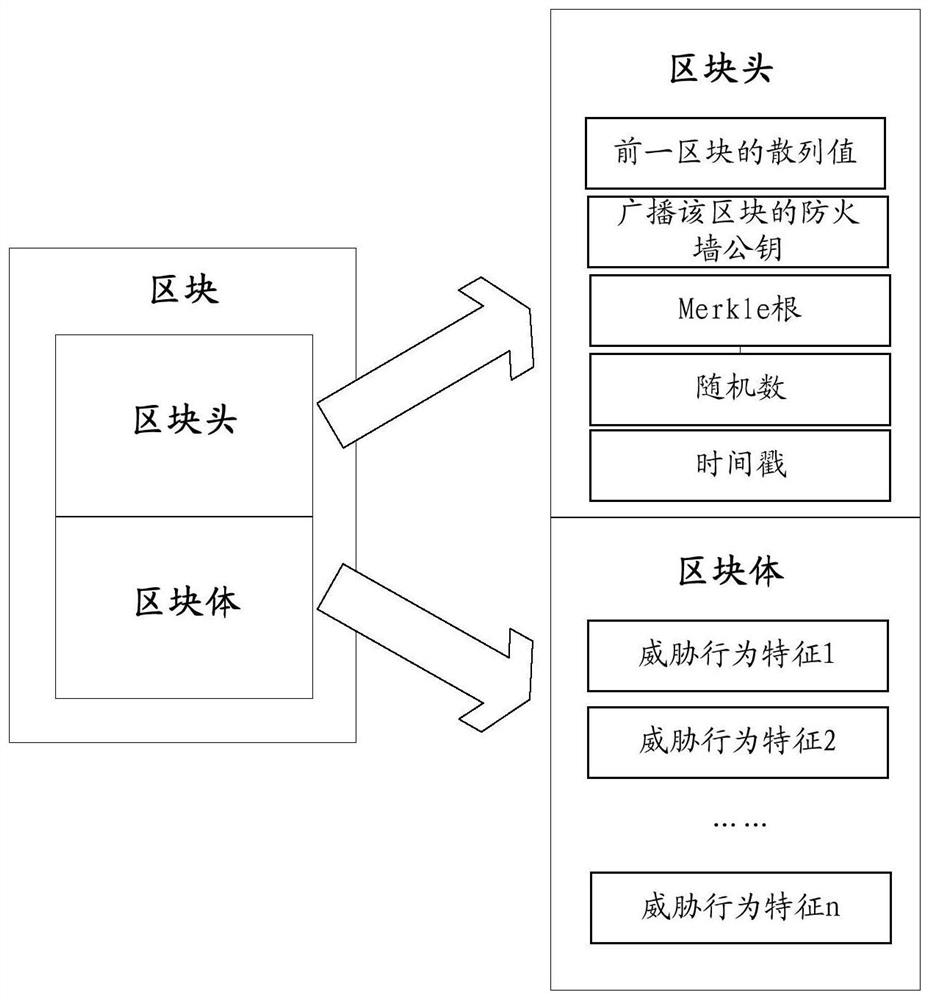
Threat behavior processing method and device, equipment and storage medium based on block chain
The embodiment of the invention discloses a threat behavior processing method, device and equipment based on a block chain as well as a storage medium, applied to electronic equipment including a firewall. The threat behavior processing based on the block chain comprises the following steps: analyzing a suspected data flow of a threat behavior, and acquiring data features of the suspected data flow; extracting recorded threat behavior features in the block chain, wherein the block chain is shared among multiple firewalls; and based on the data features and the threat behavior features, forminga judgment result, wherein the data features are used for updating the block chain when the suspected data flow is determined to be the data flow of the threat behavior. In the embodiment, based on the threat behavior features recorded in the block chain, the firewalls can be assisted to further determine whether the suspected data flow which can not be precisely identified by the firewalls basedon the current attack rules is a data flow of an attack behavior, an information barrier among the firewalls is broken, and interception capability of a single firewall and all the firewalls on the threat behavior is improved, so that security capability is improved.
Owner:CHINA MOBILE COMM LTD RES INST +1
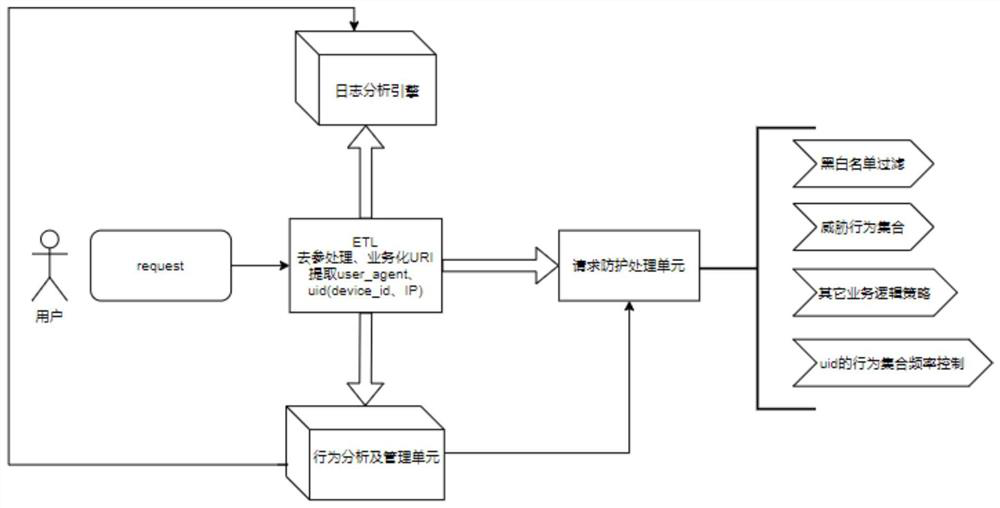
Semi-automatic anti-crawling system based on behavior characteristics
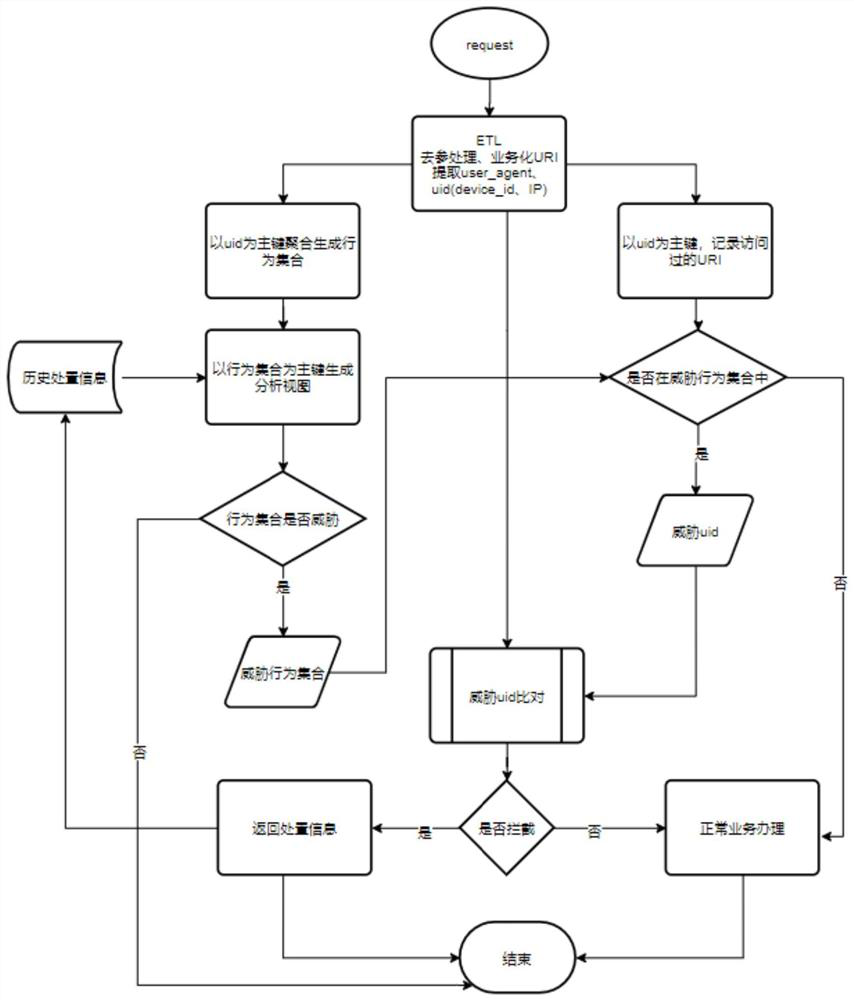
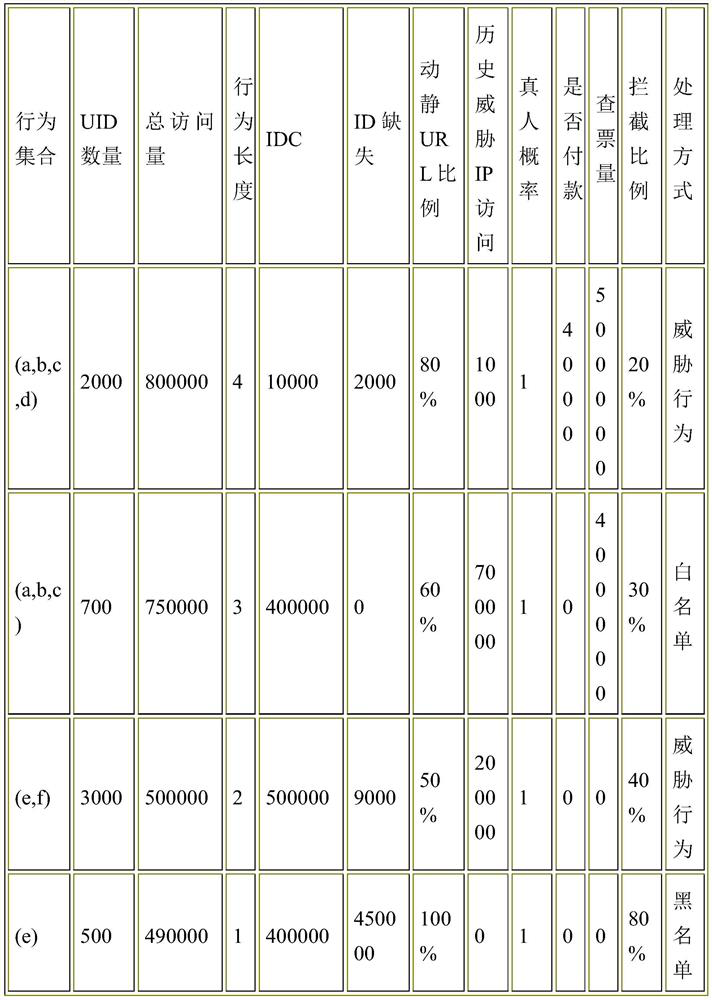
PendingCN111914255AAccurate killingRealize semi-automatic anti-climbing closed loopDatabase management systemsPlatform integrity maintainanceUniform resource identifierEngineering
The invention belongs to the field of network data security, and relates to a semi-automatic anti-crawling system based on behavior characteristics, which comprises an ETL processing unit, a behavioranalysis and management unit, a log analysis engine and a request protection processing unit, wherein the ELT processing unit is used for carrying out ETL (Extract Transform and Load) processing on request information of a request initiated by a user side to obtain UID (Uniform Identifier) and URI (Uniform Resource Identifier) data; the behavior analysis and management unit performs deduplicationprocessing on the received URI data by taking the received URI as a main key aggregation to generate a behavior set and statistical indexes related to a service scene;, takes the behavior set as a main key aggregation, and generates an analysis view to judge whether the behavior set is threatened or not; manages the threat behavior set,and if it is judged that the behavior set is the threat behavior set, records and tracks the threat behavior set, automatically generates a disposal strategy parameter according to the behavior set access frequency, the URI data type and the URI data quantity, and pushs the disposal strategy parameter to a database for crawler real-time monitoring.
Owner:北京人人云图信息技术有限公司
A real-time detection method and system based on threat behavior
ActiveCN114531306BSolve the lack of timelinessSecuring communicationTheoretical computer scienceEngineering
Owner:北京安博通金安科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com