Network security protection method based on XDR telephone bill data
A network security and bill data technology, applied in the Internet field, can solve the problems of network threats, user perception decline, complex and changeable user behavior, etc., to achieve the effect of purifying network bad behavior, identifying a wide range, and green and safe network environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
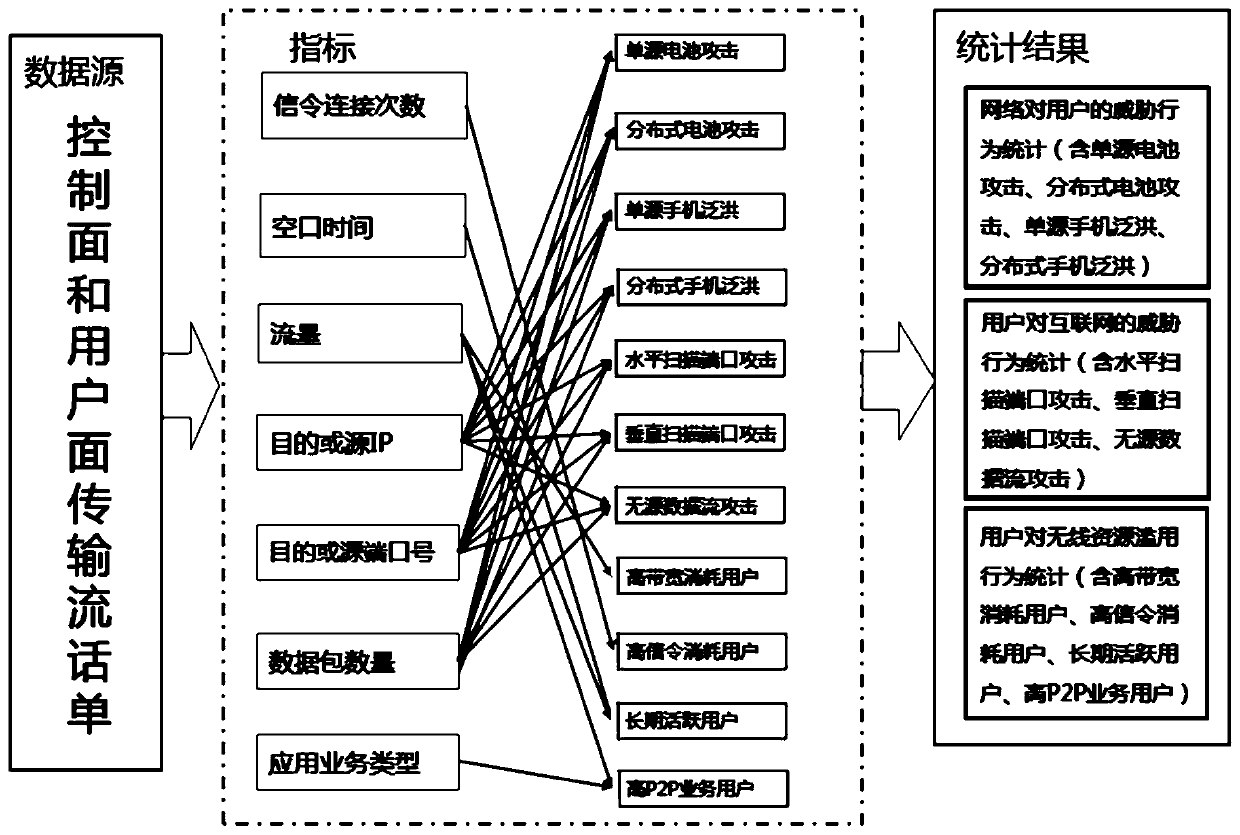
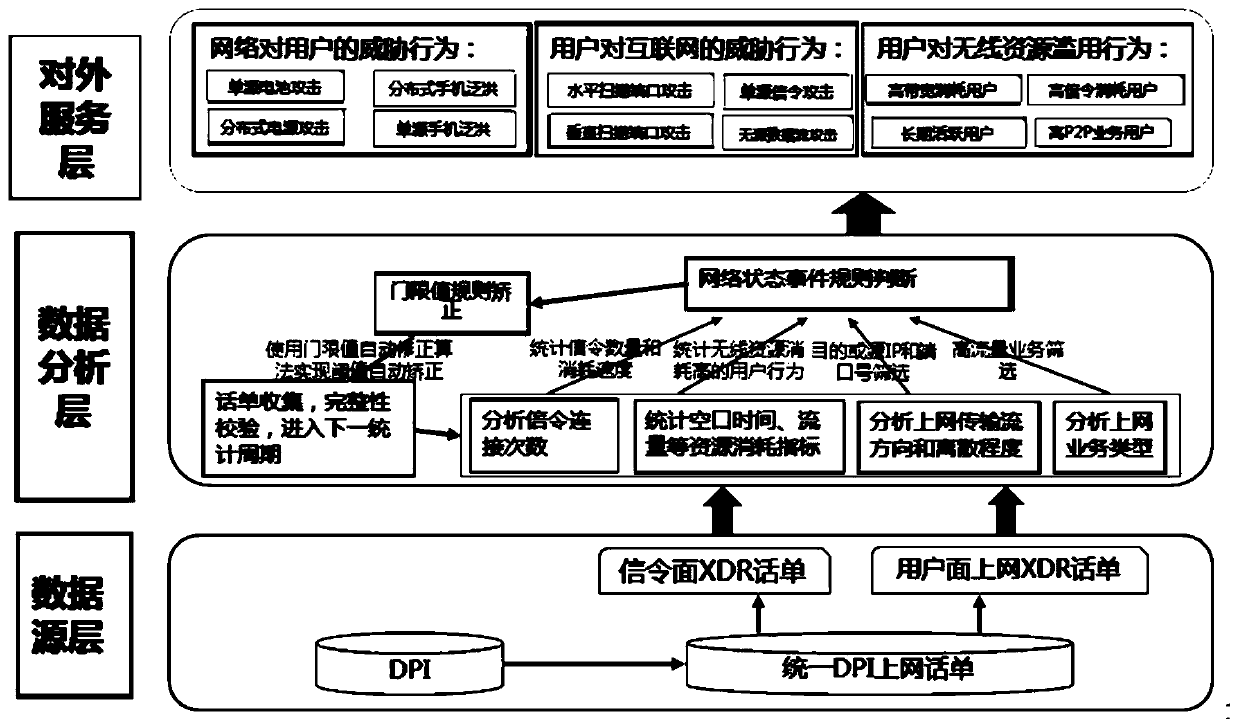
[0049] This embodiment is a network security protection method based on XDR bill data. The method identifies abnormal user behaviors according to indicators of the XDR bill data, thereby performing network security protection. Each step is described in detail below.
[0050] 1. Indicators of XDR bill data
[0051] like figure 1 As shown, the indicators of the XDR bill data include the number of signaling connections, air interface time, traffic, destination or source IP, destination or source port number, number of data packets and / or application service type.
[0052] 2. Abnormal user behavior
[0053] Abnormal user behaviors include threatening behaviors of the network to users, threatening behaviors of users to the Internet, and / or abusive behaviors of users to wireless resources.
[0054] 1) Threat behaviors of the network to users include single-source battery attack, distributed battery attack, single-source mobile phone flooding and distributed mobile phone flooding;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com