Threat behavior processing method and device, equipment and storage medium based on block chain
A processing method and blockchain technology, applied in the field of information security, can solve problems such as weak firewall protection capabilities, and achieve the effect of improving protection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
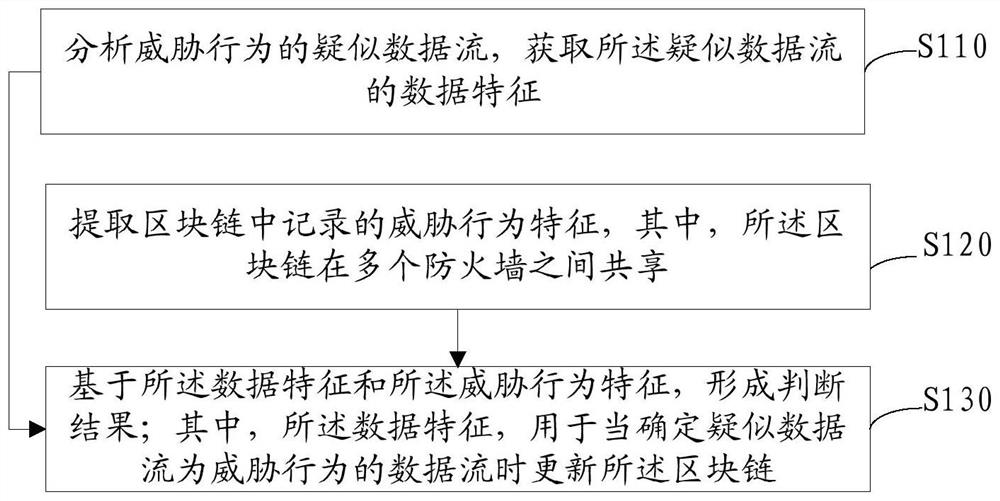
[0136] This example provides a firewall interaction method and system based on blockchain. By analyzing the threat behavior of each firewall using blockchain, and based on the generation and broadcast of blockchain to realize mutual interaction between firewalls, and then realize the overall Use firewalls to analyze threat behaviors and discover unknown and hidden attacks. Specifically, it includes a blockchain-based firewall interaction analysis method and a blockchain-based firewall interaction analysis system.
[0137] like Image 6 As shown, this example provides a block chain-based firewall interaction system including multiple firewalls, and a point-to-point communication is formed between each firewall on a logical level. The firewalls in the figure include FW1, FW2, FW3, FW n-1, and FW n; FW1 can interact with n-1 firewalls such as FW2, FW3, FW n-1, and FW n, and FW2 can interact with FW1, FW3, and FW n-1, FW n and other n-1 firewalls can interact, FW3 can interact w...
example 2
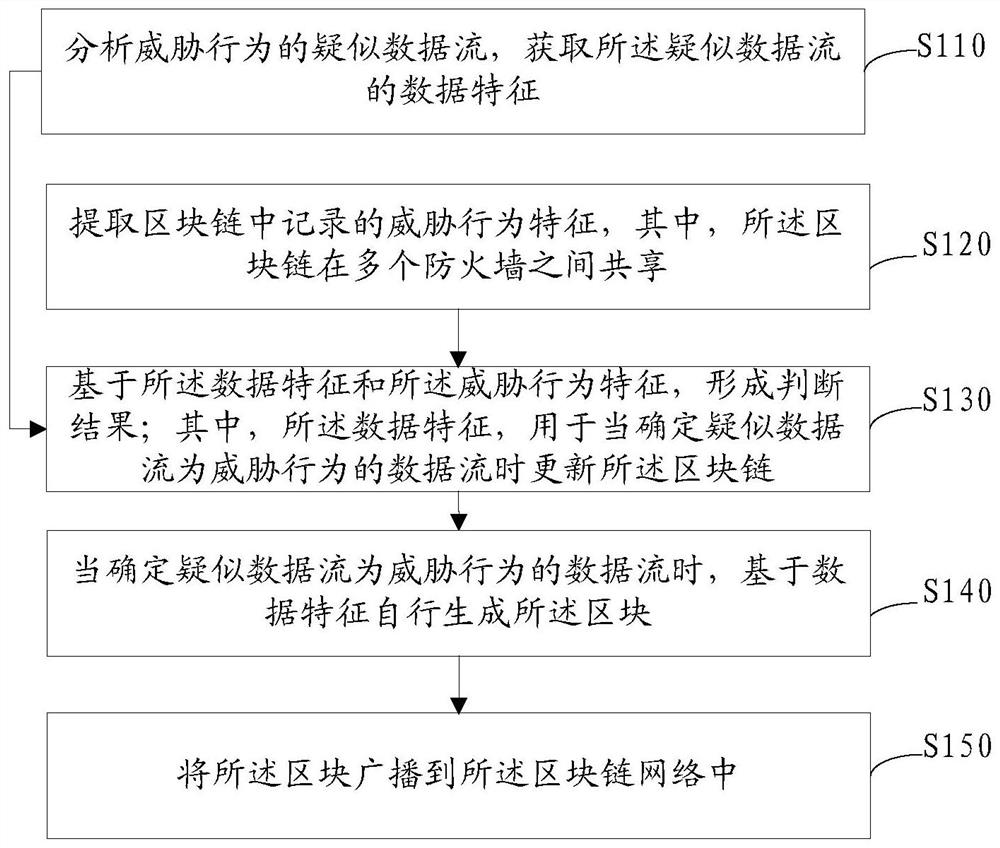
[0147] like Figure 7 As shown, the blockchain-based firewall interactive analysis method described in this technical solution includes the following steps:
[0148] Step 101: traditional firewall data processing based on attack rules. That is, the firewall receives traffic, performs data processing based on attack rules, allows normal traffic, blocks traffic matching attack rules, and proceeds to step 102 for other suspected traffic.
[0149] Step 102: For the suspected data flow, analyze the threat behavior based on the block chain. That is, the output of step 101 is received, and threat behavior analysis based on blockchain is performed.
[0150] Step 103: extract the threat behavior features stored in the blockchain, and extract the data features of the suspected data flow.
[0151] Step 104: Compare the threat behavior features and data features to obtain a judgment result, which may specifically include: performing SVM vector machine training through the threat behavi...
example 3
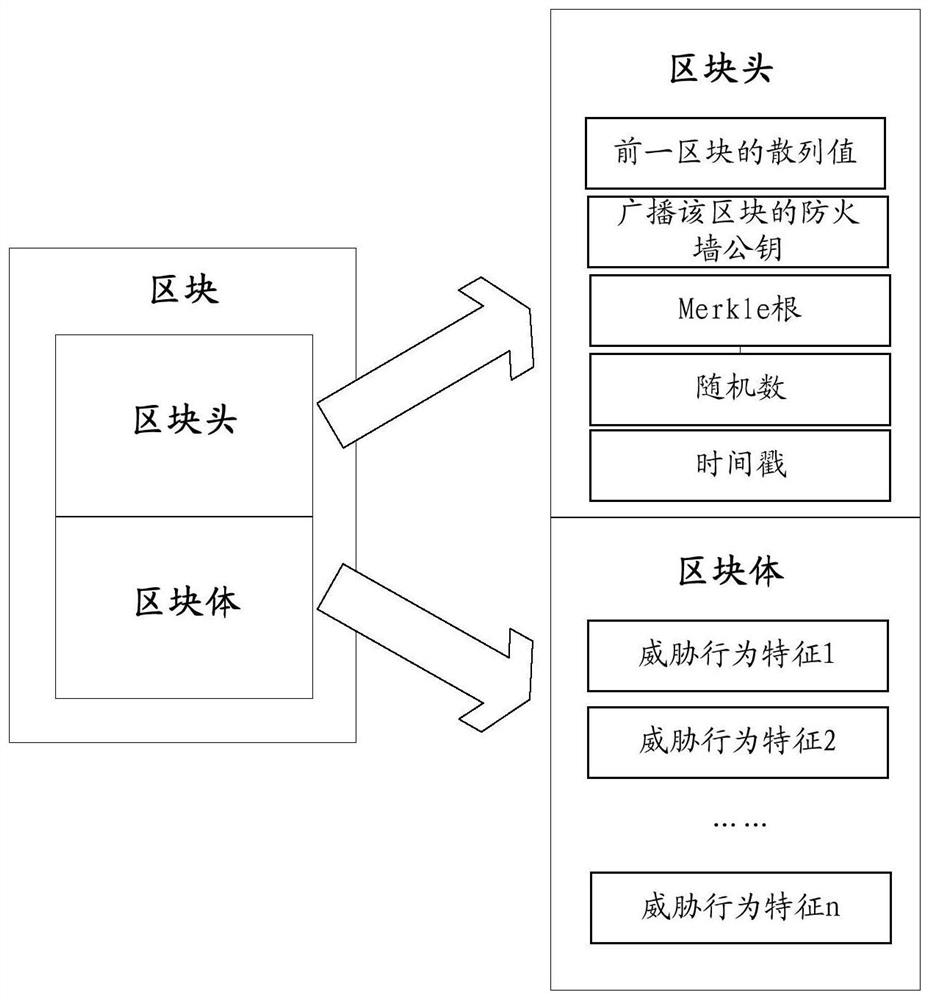
[0156] like Figure 8 As shown, the blockchain-based interactive analysis system for firewalls described in this technical solution includes 4 major parts: firewall traditional data processing module 201, blockchain-based threat behavior feature library module 202, blockchain-based Threat behavior analysis module 203 and block chain-based threat behavior feature library coordination module 204.
[0157] The block chain-based threat behavior analysis module 203 includes three sub-modules, namely: a block chain-based threat behavior extraction module 2031, a block chain-based threat behavior determination module 2032, and a block chain-based threat behavior aggregation module 2033 . details as follows.
[0158] The traditional data processing module 201 of the firewall is used to perform traditional data processing based on attack rules on the data packet flow to determine the suspected data flow, which can be used as a component of the aforementioned acquisition unit 110 .
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com