Virtual platform threat behavior analysis method and system based on KNN
A virtual platform and behavior analysis technology, applied in the field of virtual platform threat behavior analysis, can solve problems such as clue data counter-evidence technology software deception, achieve high accuracy and improve analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] This embodiment is used to specifically illustrate the method of the present invention.
[0086] A KNN-based virtual platform threat behavior analysis method, comprising the following steps:
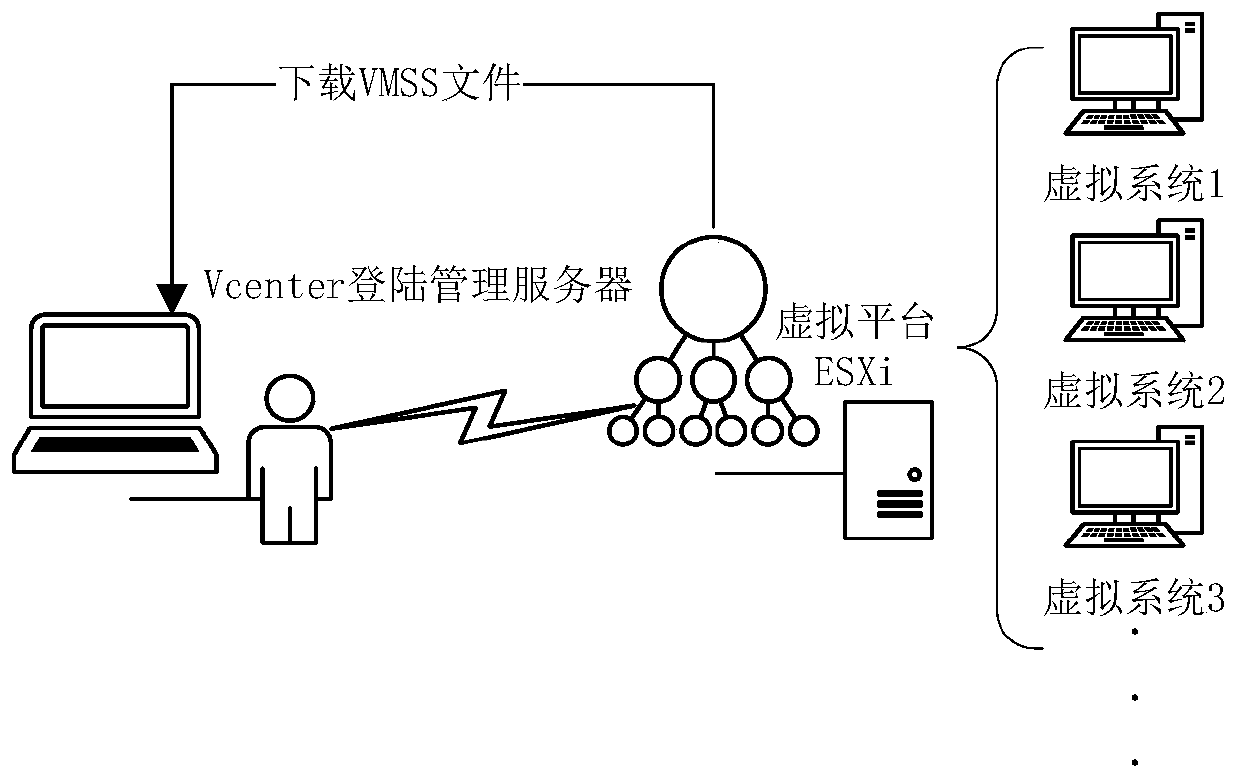
[0087] Step 1: extract the memory data in the virtual platform;
[0088] Step 101: use the Vcenter component to remotely log in to the ESXi component of the VMware Vshpere virtual platform management server;
[0089] Step 102: The Vcenter component suspends the virtual machine through the management server, and downloads a virtual machine file with an extension of VSMM, that is, memory data. The virtual machine file with an extension of VSMM is an image of memory data saved when the virtual machine is suspended.
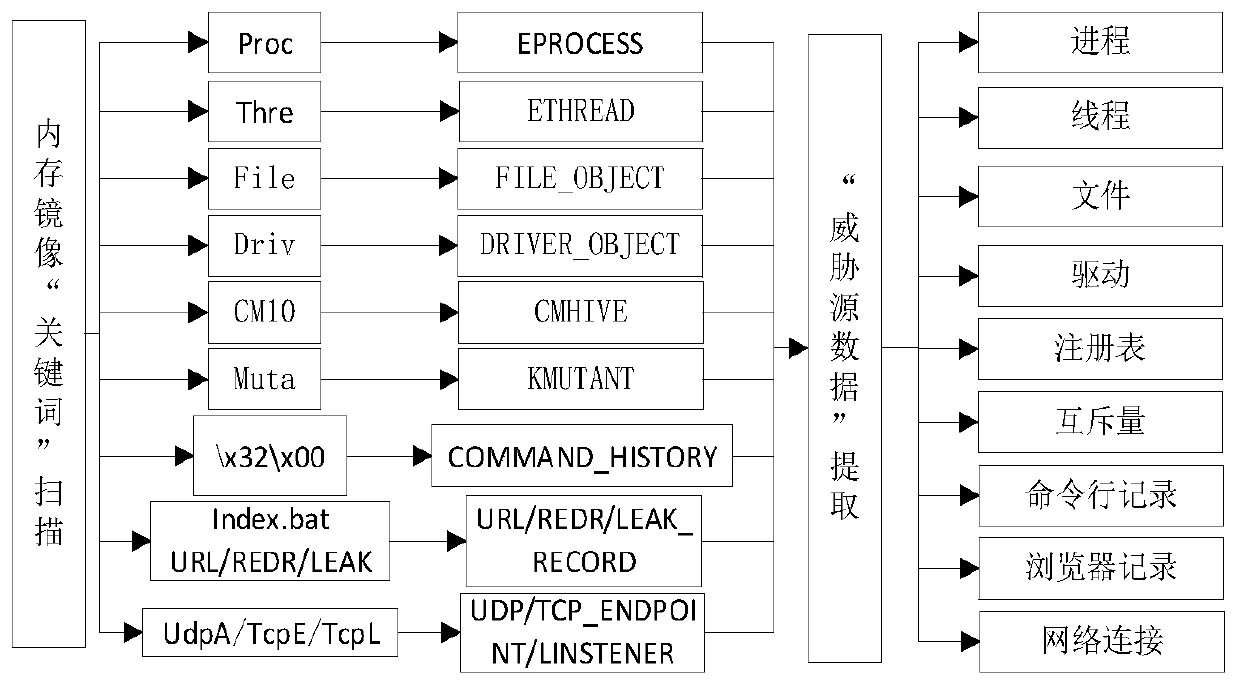
[0090] Step 2: The image file obtained in step 1 saves the registry, process, thread, file, network connection, driver, import and export table and other information of the virtual platform at that time. These information are important source data for threat behavior an...
Embodiment 2
[0113] This embodiment is used to specifically describe the system of the present invention.
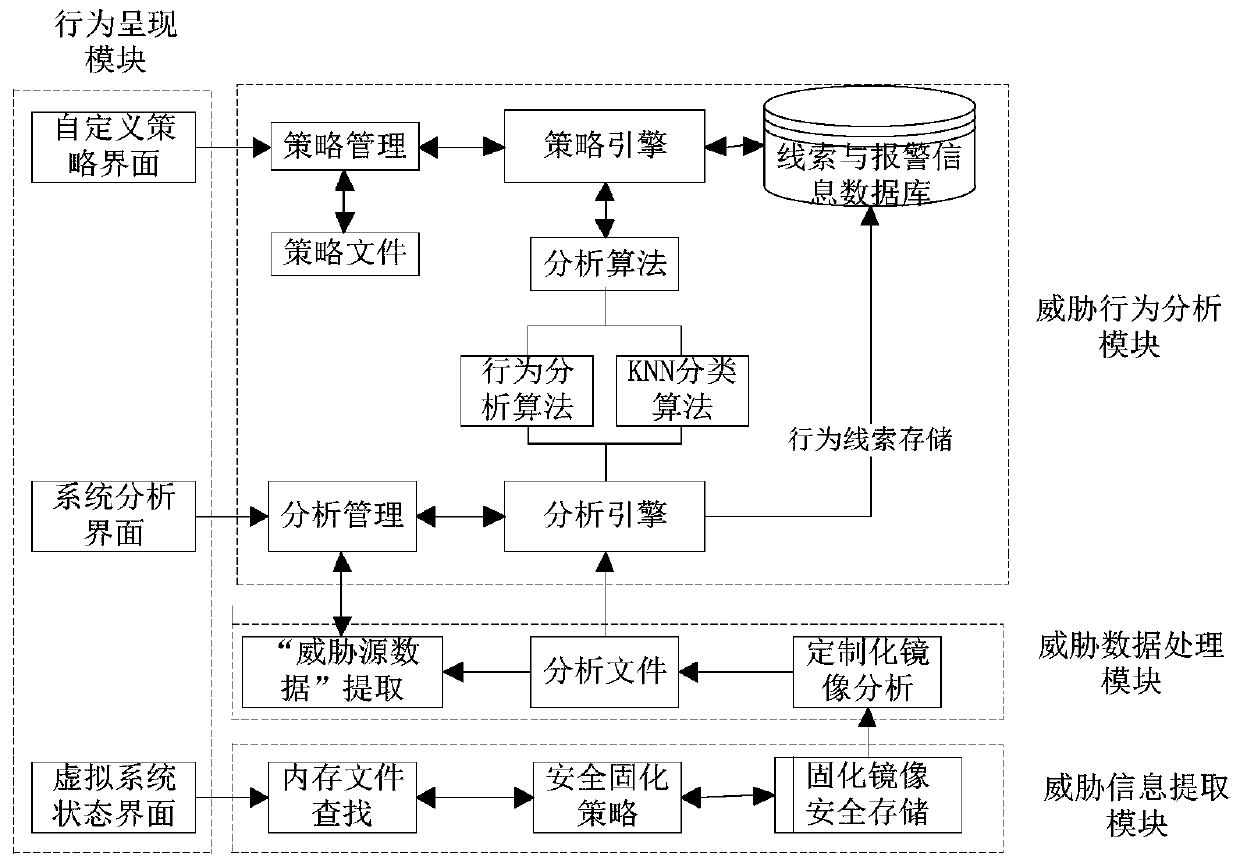
[0114] A KNN-based virtual platform threat behavior analysis system, including
[0115] Threat information extraction module: used to find and extract the memory data of the virtual platform, and solidify the memory data;
[0116] Threat data processing module: used to extract the threat source data in the memory data, and obtain the behavior characteristics of the software;
[0117] Threat behavior analysis module: used to identify and restore threat software in the threat source data;
[0118] Threat behavior presentation module: used to present the entire threat behavior analysis process.
[0119] Specifically:
[0120] The threat information extraction module searches and extracts the image file of memory data from the virtual platform, and downloads the image file without damage through the Vcenter component, stores it safely and solidifies it, and performs hash verification ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com