Threat processing method and device, electronic equipment and computer readable storage medium
A threat processing and data flow technology, applied in the field of information processing, can solve problems such as inability to monitor and deal with network threats, and achieve the effect of improving security and strengthening security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] In order to solve the technical problem in the prior art that the network threats of the cloud platform itself cannot be monitored and dealt with, an embodiment of the present application provides a threat handling method.
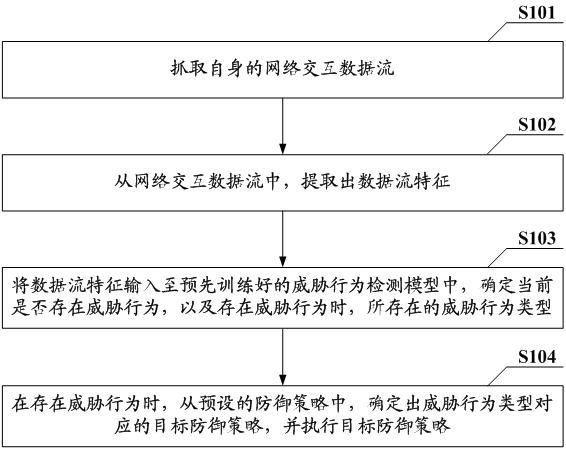
[0034] see figure 1 shown, figure 1 It is a threat processing method provided in the embodiment of this application, including:
[0035] S101: Grab its own network interaction data stream.
[0036] It should be noted that the solution in the embodiment of the present application can be applied to each target node of the cloud platform. The target node mentioned in the embodiment of the present application refers to a node in the cloud platform that faces the network and faces various network threats, such as a control node and a network node of the cloud platform.
[0037] In the embodiment of this application, a packet capture program can be configured on the target node, and by monitoring the network card of the target node, sniff all network i...
Embodiment 2
[0077] On the basis of Embodiment 1, this embodiment takes a more specific implementation manner as an example to further illustrate the solution adopted in the embodiment of the present application.
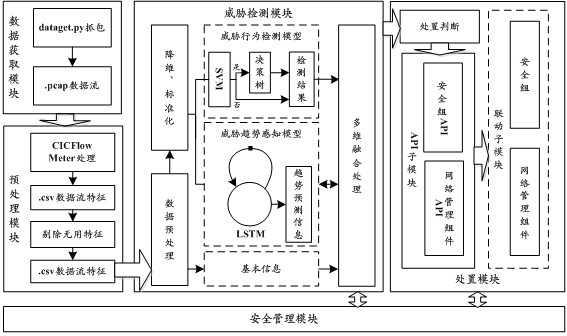
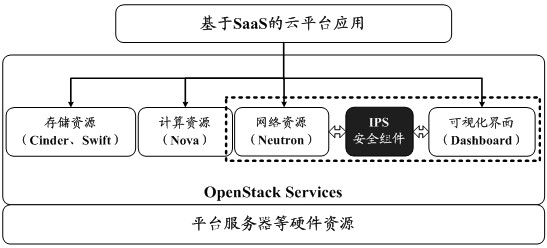
[0078] see Figures 2 to 4 as shown, figure 2 It shows an IPS (Intrusion Prevention System, intrusion prevention system) security component provided in the embodiment of the application applied to the target node of the cloud platform. Based on the IPS security component, the IPS provided in the embodiment of the application can be realized. Threat handling methods. Among them, the cloud platform is implemented based on the OpenStack architecture.
[0079] see figure 2 As shown, the IPS security component includes five parts: data acquisition module, preprocessing module, threat detection module, disposal module and security management module.
[0080] After the IPS security component is installed and enabled, first, the data acquisition module is implemented through the p...
Embodiment 3
[0105] Based on the same inventive concept, an embodiment of the present application also provides a threat processing device 100, which is applied to a target node of a cloud platform. see Figure 5 shown, Figure 5 shown with figure 1 The illustrated method corresponds to the threat processing apparatus 100 . It should be understood that for the specific functions of the threat processing apparatus 100, reference may be made to the above description, and to avoid repetition, detailed description is appropriately omitted here. The threat processing device 100 includes at least one software function module that can be stored in a memory in the form of software or firmware or solidified in the operating system of the threat processing device 100 . specifically:
[0106] see Figure 5 As shown, the threat processing apparatus 100 is applied to the target node of the cloud platform, and includes: a capture module 101 , an extraction module 102 and a processing module 103 . ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com