Database password centralized management and application method and system oriented to application software
An application-oriented, centralized management technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
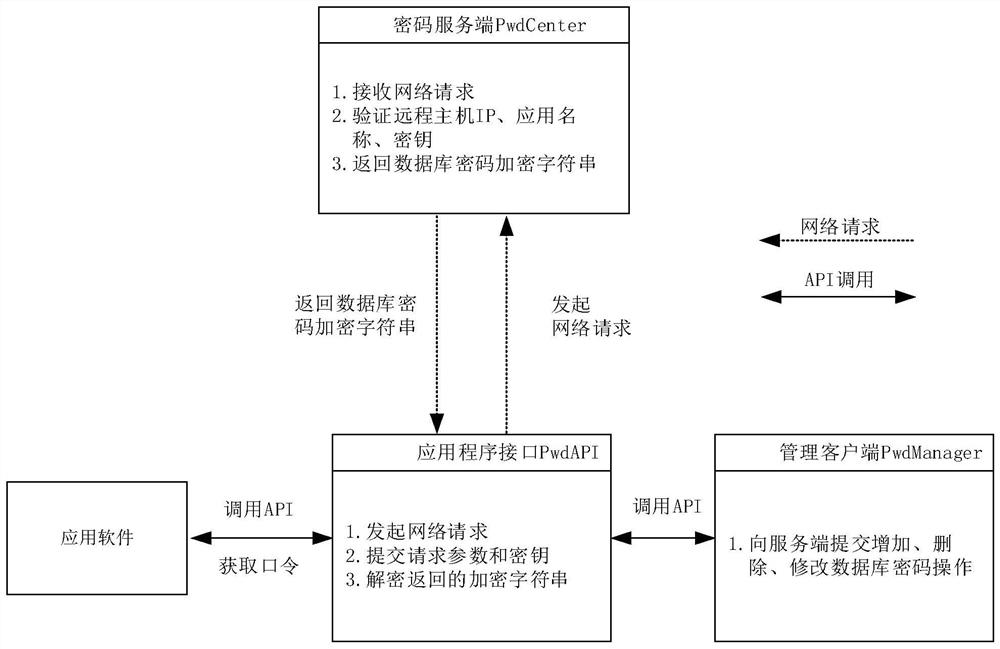
[0020] 1) The database password server PwdCenter is responsible for storing database passwords and providing network request services for application software.
[0021] 2) The database password application program interface PwdAPI can simplify the operation of the application software to request the database password from the server PwdCenter, and encapsulate the network request and encryption and decryption operations into an API interface. The application software only needs to call the API interface, perform simple function calls, and fill in Enter the call parameters and key to get the database password.
[0022] 3) The database password management client PwdManager is used to add, delete and modify the database password on the server PwdCenter.
[0023] 4) The system administrator uses the management client PwdManager to initiate a network connection to the database password server PwdCenter by calling the API interface PwdAPI.
Embodiment 2
[0025]6) When the application software of each business system needs to connect to the database, call the API interface PwdAPI, input parameters (parameter 1: database name, parameter 2: database user, parameter 3: encryption key), and the API interface PwdAPI sends a network request to Database password server PwdCenter. The API interface can provide various methods such as jar, dll, and lib library files, and supports cross-platform, cross-operating system and multi-programming language calls.
[0026] 7) After the database password server PwdCenter receives the request, follow the steps below:
[0027] (3) The database password is encrypted with a key and returned to the API interface called by the application software through the network.
[0028] 8) The API interface PwdAPI decrypts the received encrypted content again to obtain the database password and deliver it to the application software.
[0029] In this embodiment, the database administrator first completes the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com