Method of defending network transmission control protocol sync message from overflowing attack
A technology of control protocol and synchronization message, applied in transmission system, digital transmission system, data exchange through path configuration, etc., can solve the problem of wasting server system resources, and achieve the effect of avoiding system resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
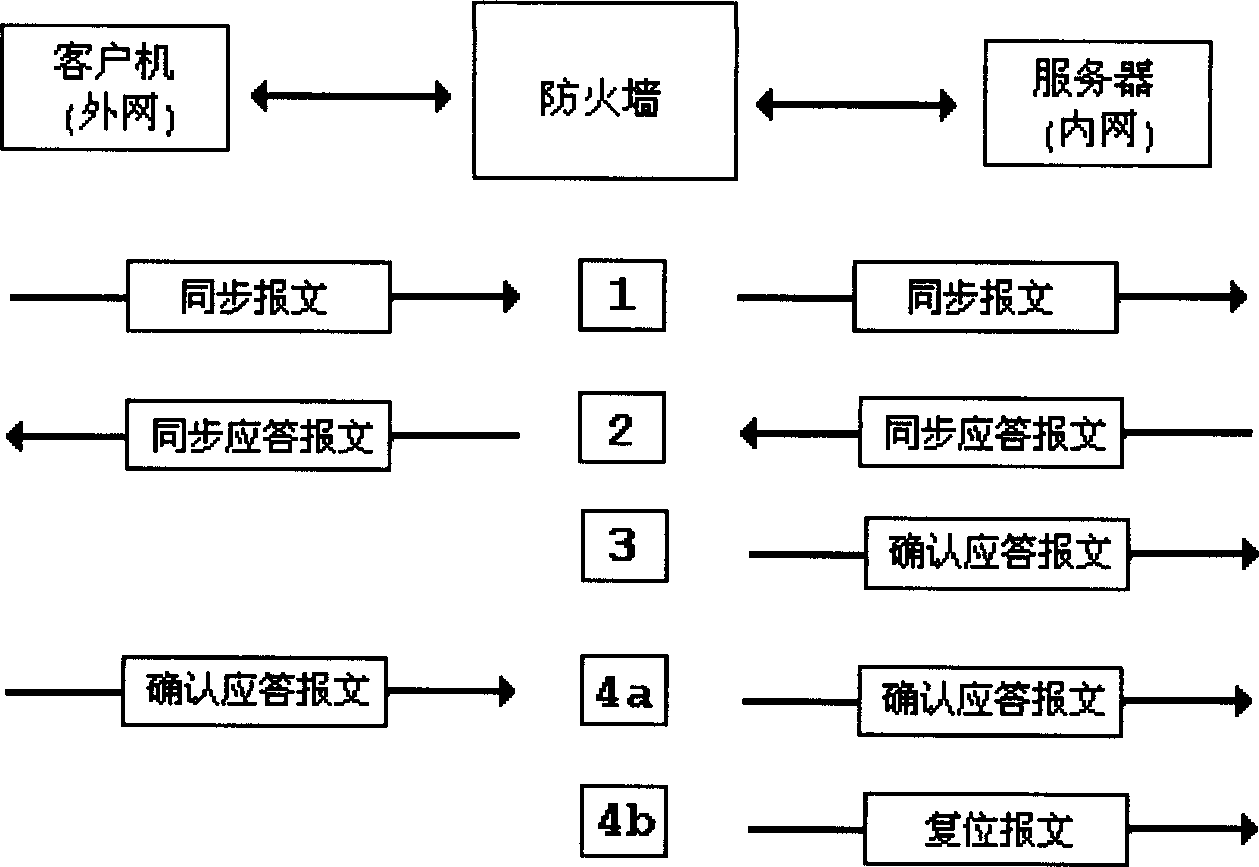
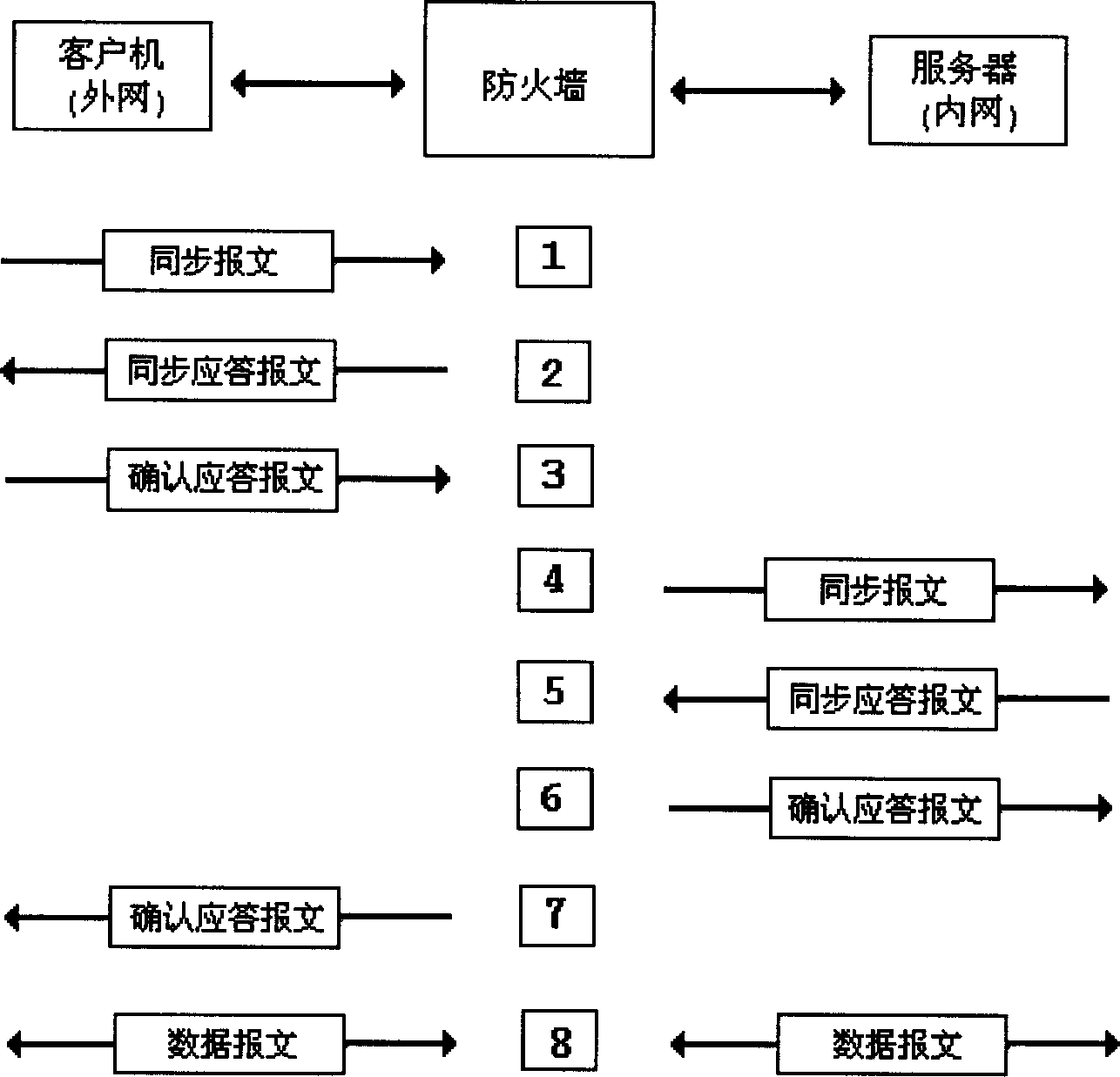
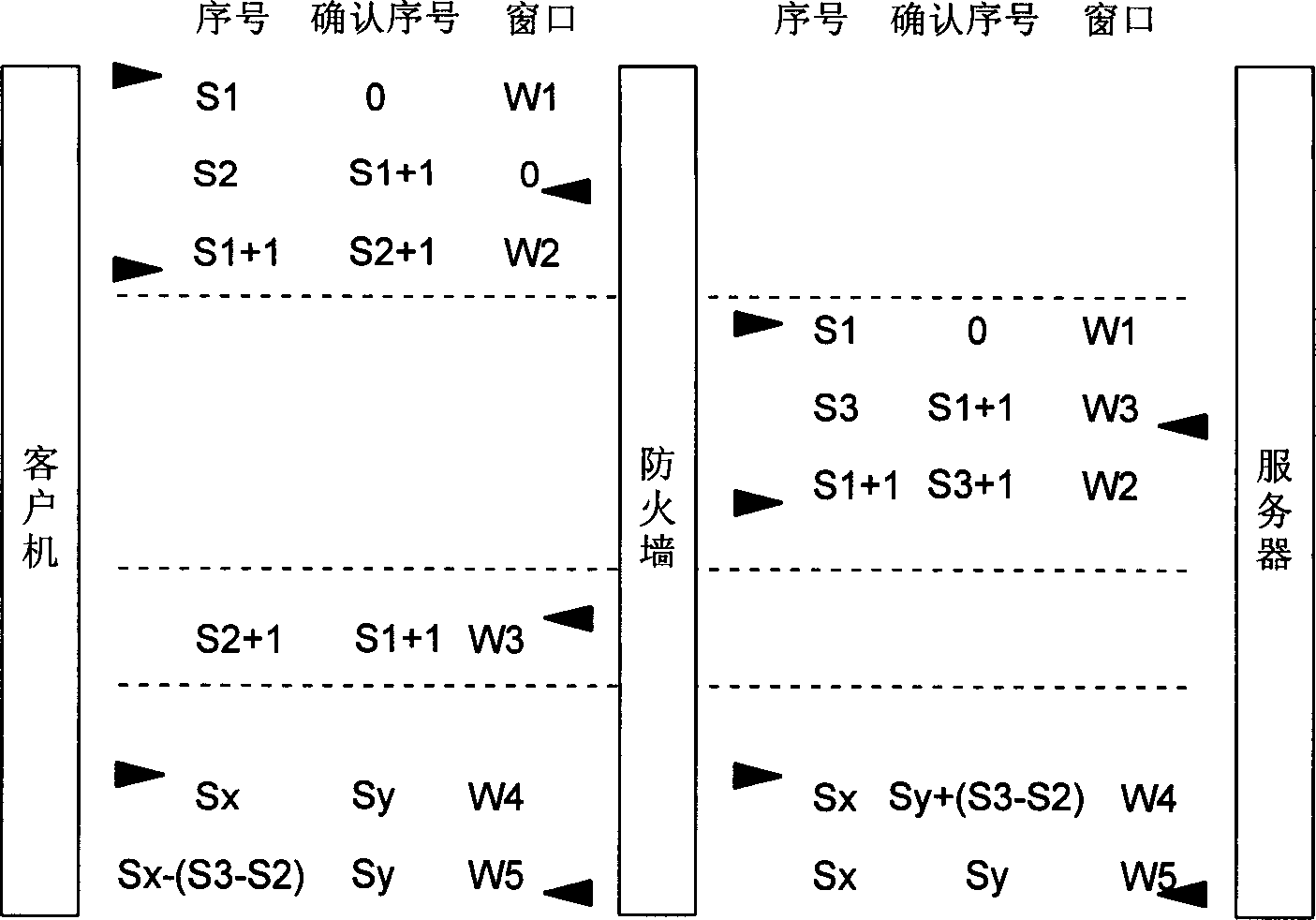
[0027] The working principle of the inventive method is as figure 2 As shown, firstly, the firewall receives a connection request (TCP synchronous message) from the client computer, and uses a window proxy server with a size of 0 to return a synchronous response message to the client computer, prompting the client computer not to transmit valid data temporarily. Then the firewall checks the legitimacy of the client computer's connection request, and at the same time, the firewall establishes a record of relevant information facing the connection request, which is used to record the sequence number, confirmation sequence number and window etc. If the firewall does not receive the confirmation response message from the client, the connection request is illegal and will not be processed. If it receives the confirmation response message from the client, the connection request is legal, and the firewall sends the connection request to the server on behalf of the client. ask. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com