Subscriber security setup maintenance method and system
A user and security technology, applied in security devices, user identity/authority verification, selection devices, etc., can solve problems such as GUSS error update, non-checking, etc., to prevent problems and reduce maintenance burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
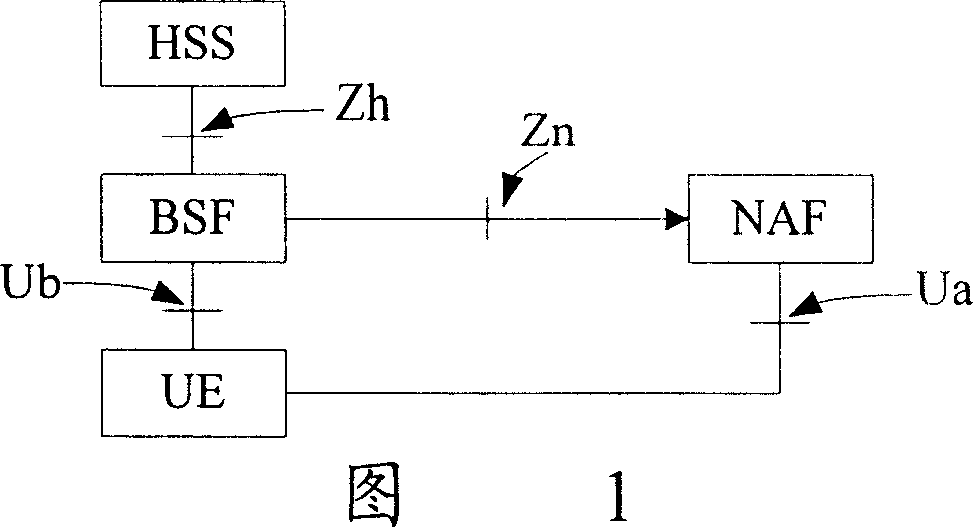
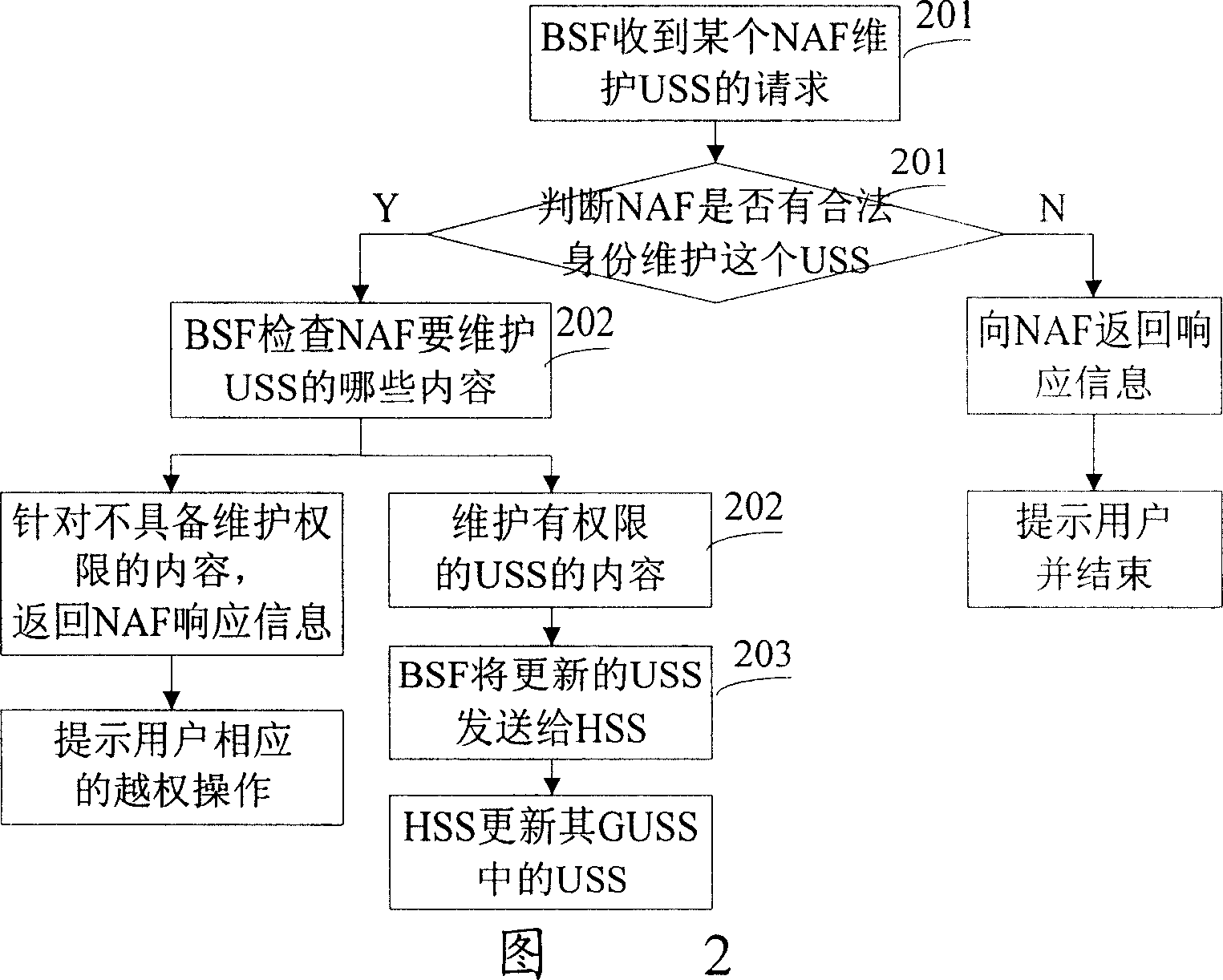
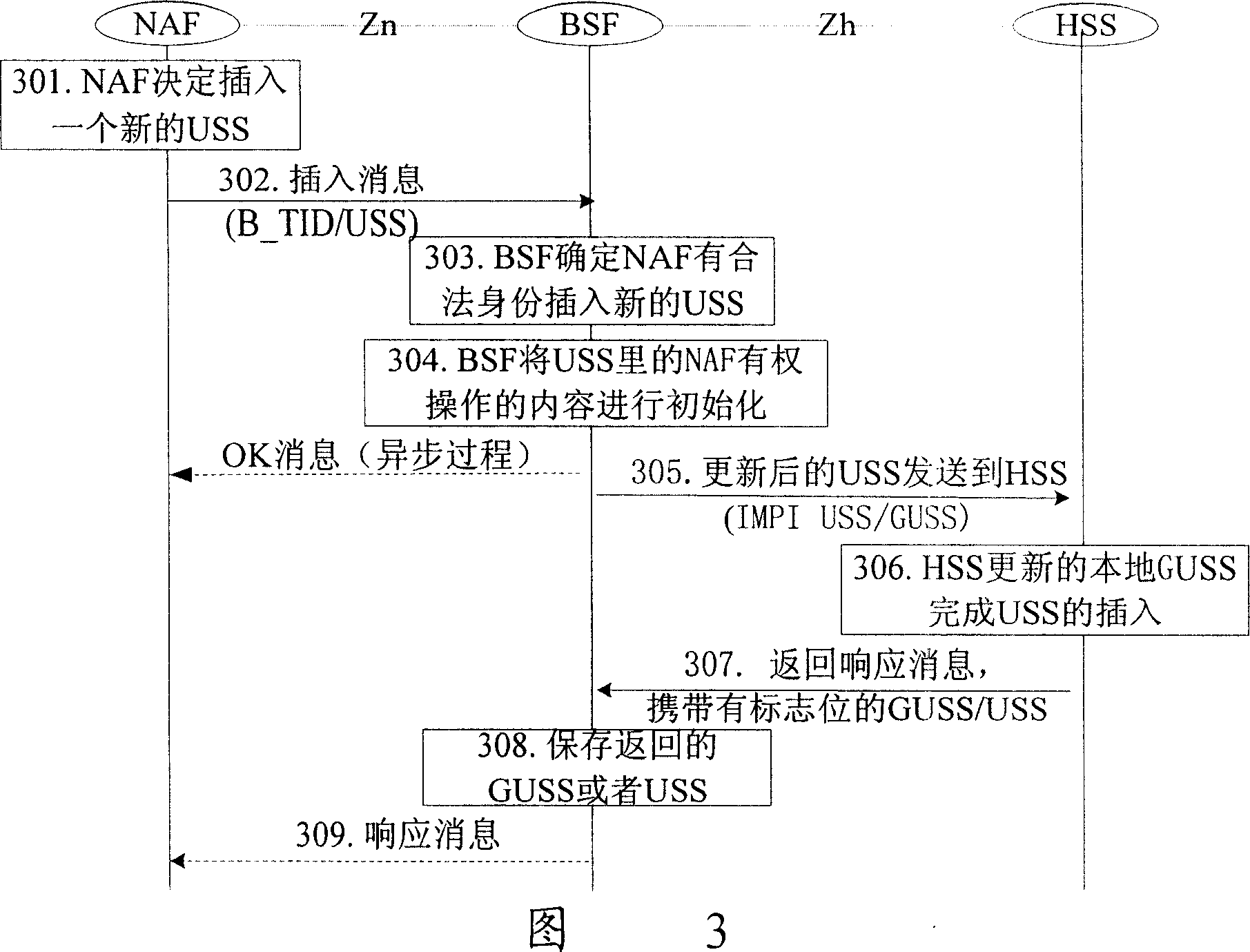
[0039]In the present invention, when the NAF maintains (including inserts, updates, and deletes) the USS, after the BSF determines that the NAF has the legal identity to maintain the USS, it further judges whether the NAF has the right to operate according to the contents of the USS, and only for The content in the USS of the operation performs the described operation. Referring to the NAF maintenance USS flowchart of the present invention shown in FIG. 2 , it includes the following steps:
[0040] Step 201: After receiving a request from a NAF to maintain (update / delete / insert) the USS, the BSF judges whether the NAF has a legal identity to maintain the USS, if so, executes the next step, otherwise returns a response message to the NAF.
[0041] Step 202: The BSF determines which USS content the NAF needs to maintain, and determines whether the NAF has the corresponding authority for each content in turn, and only maintains the content of the USS with the authority. For the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com