Patents
Literature
51results about How to "Avoid unauthorized operations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
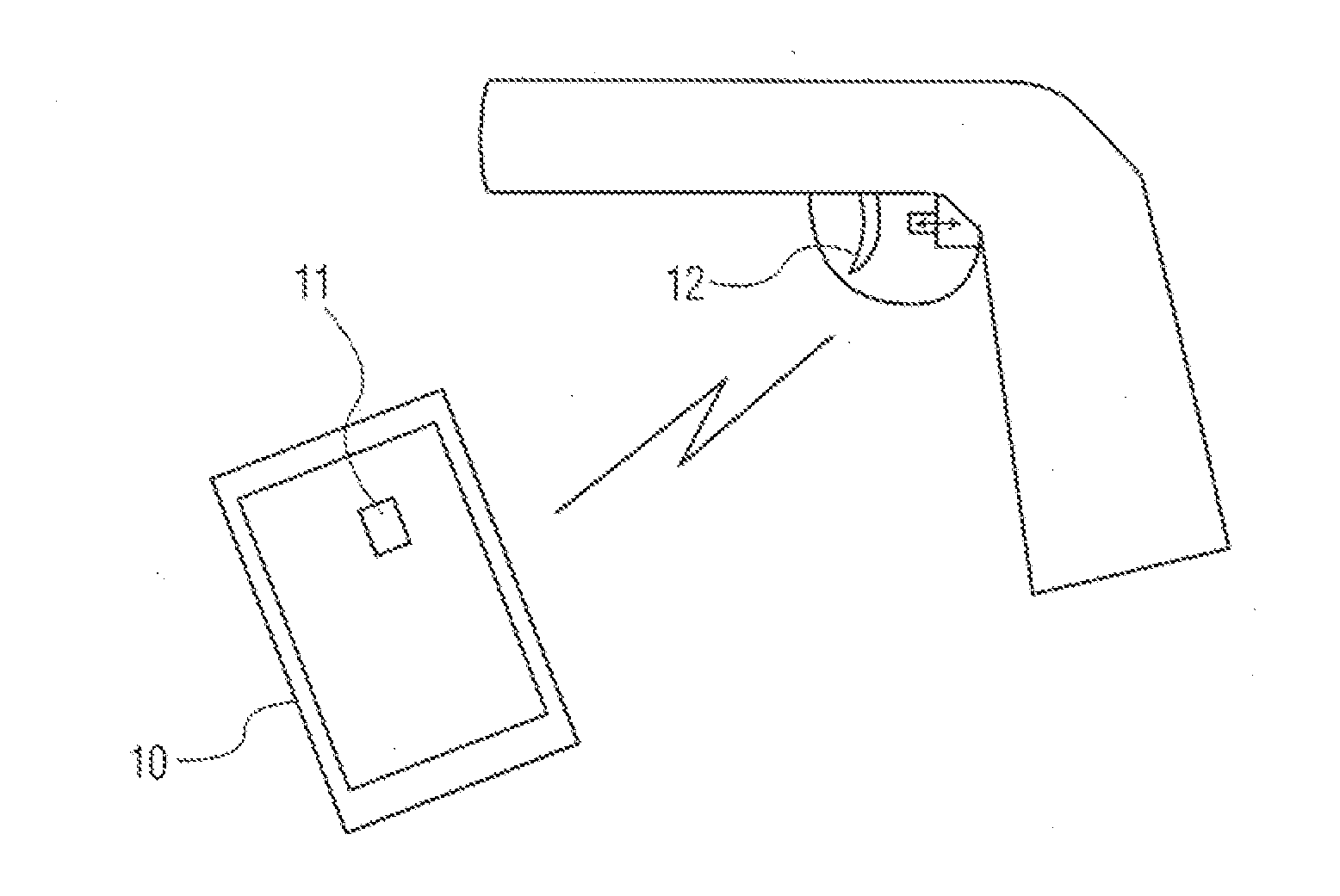
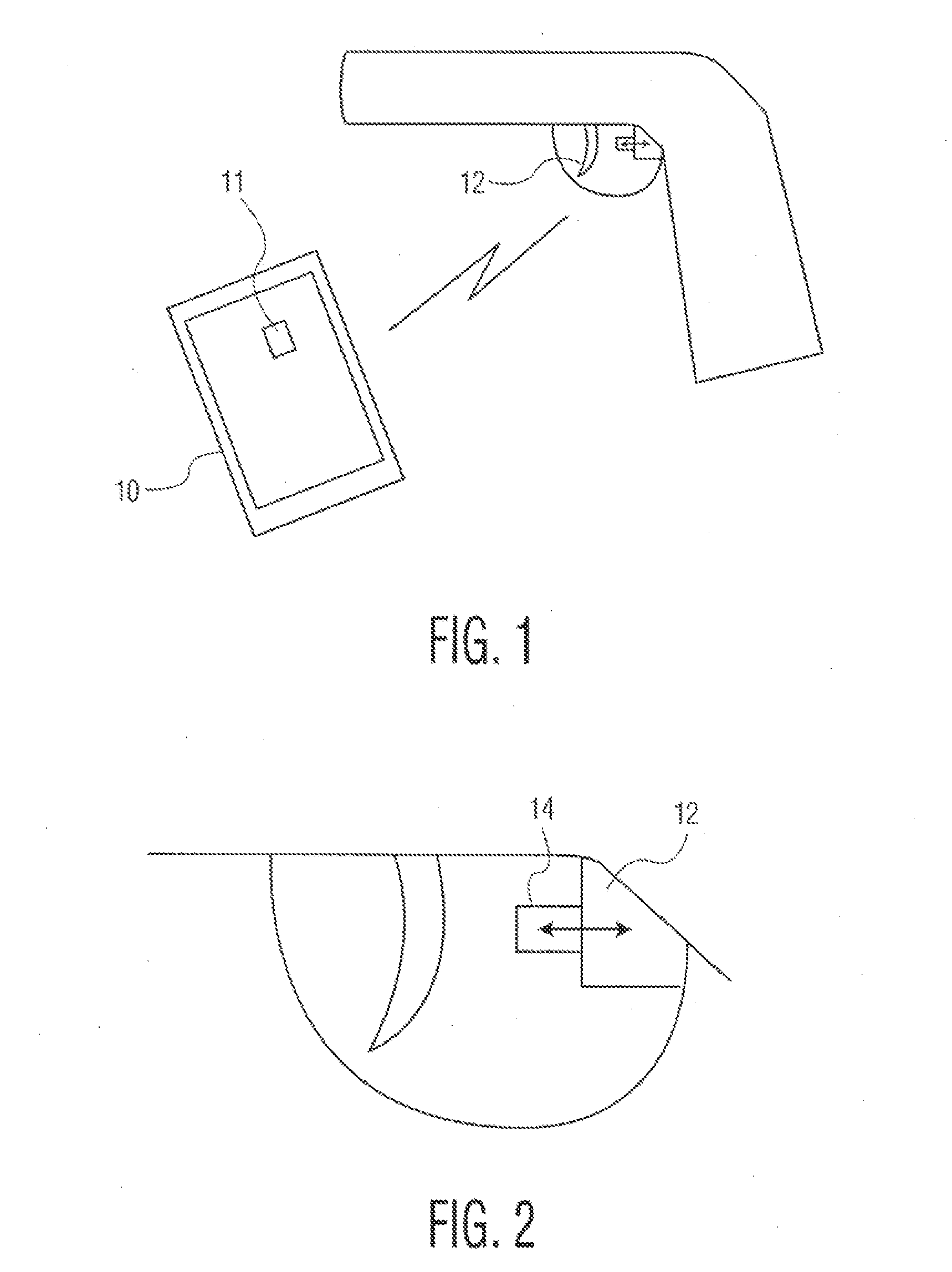
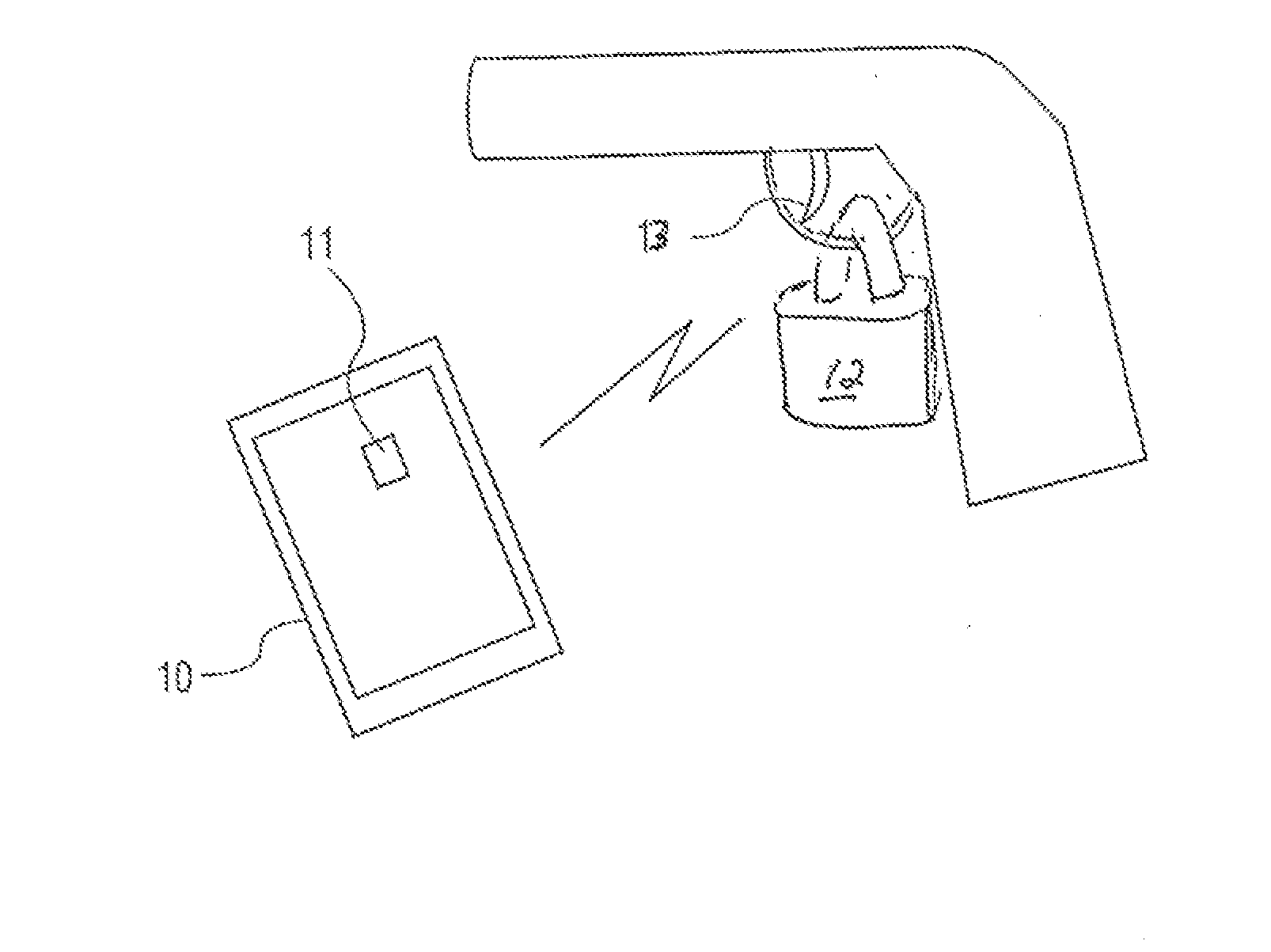
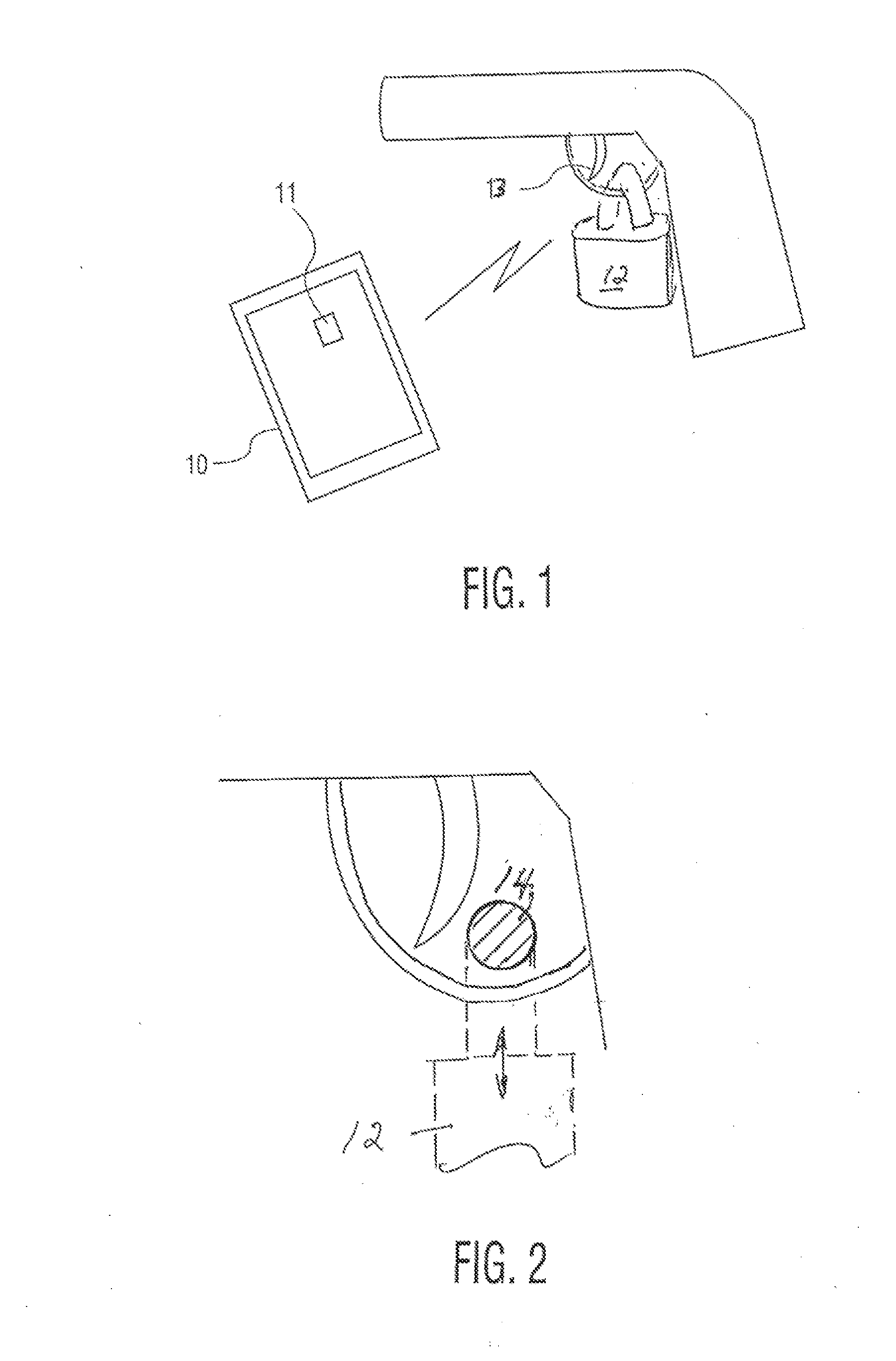
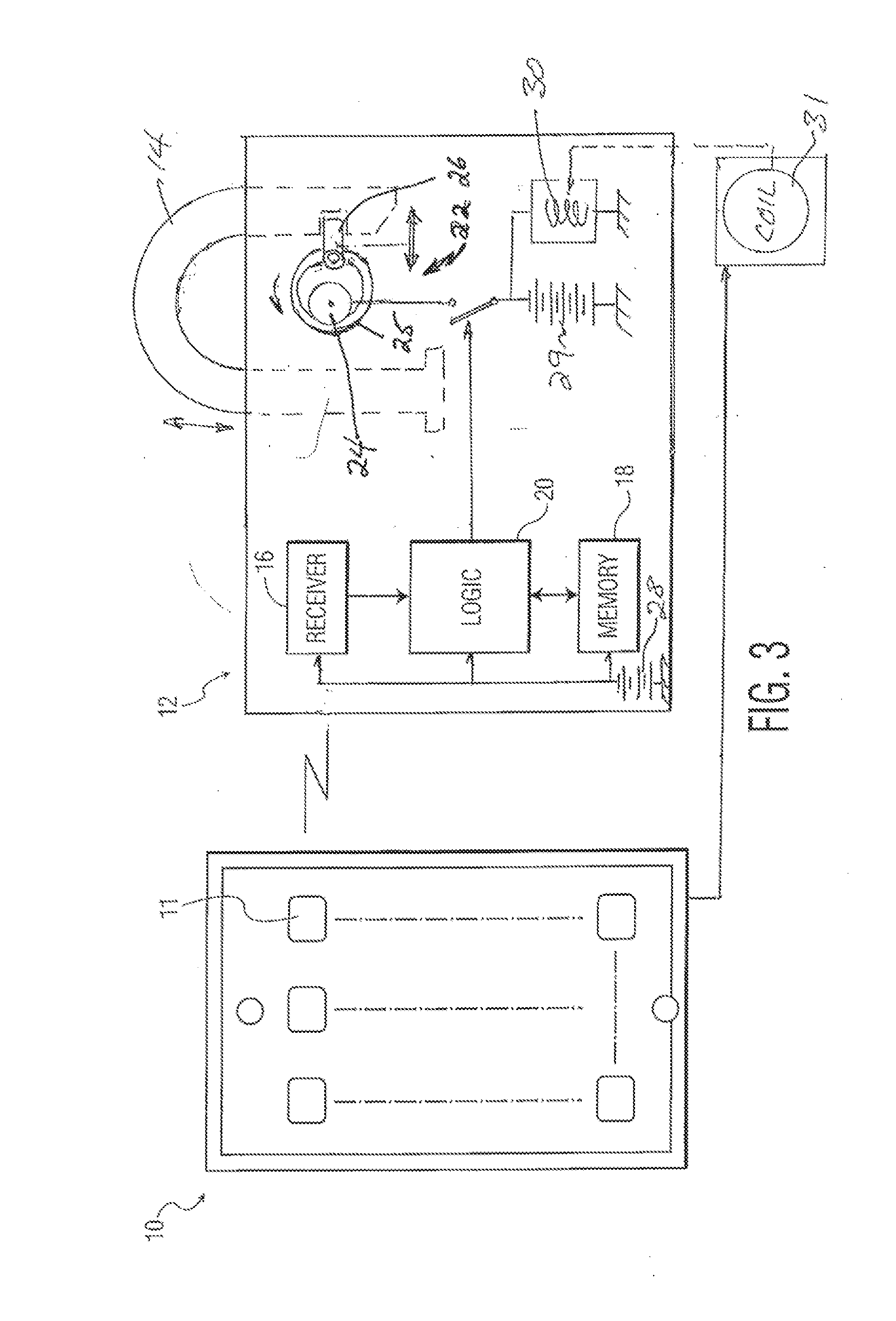
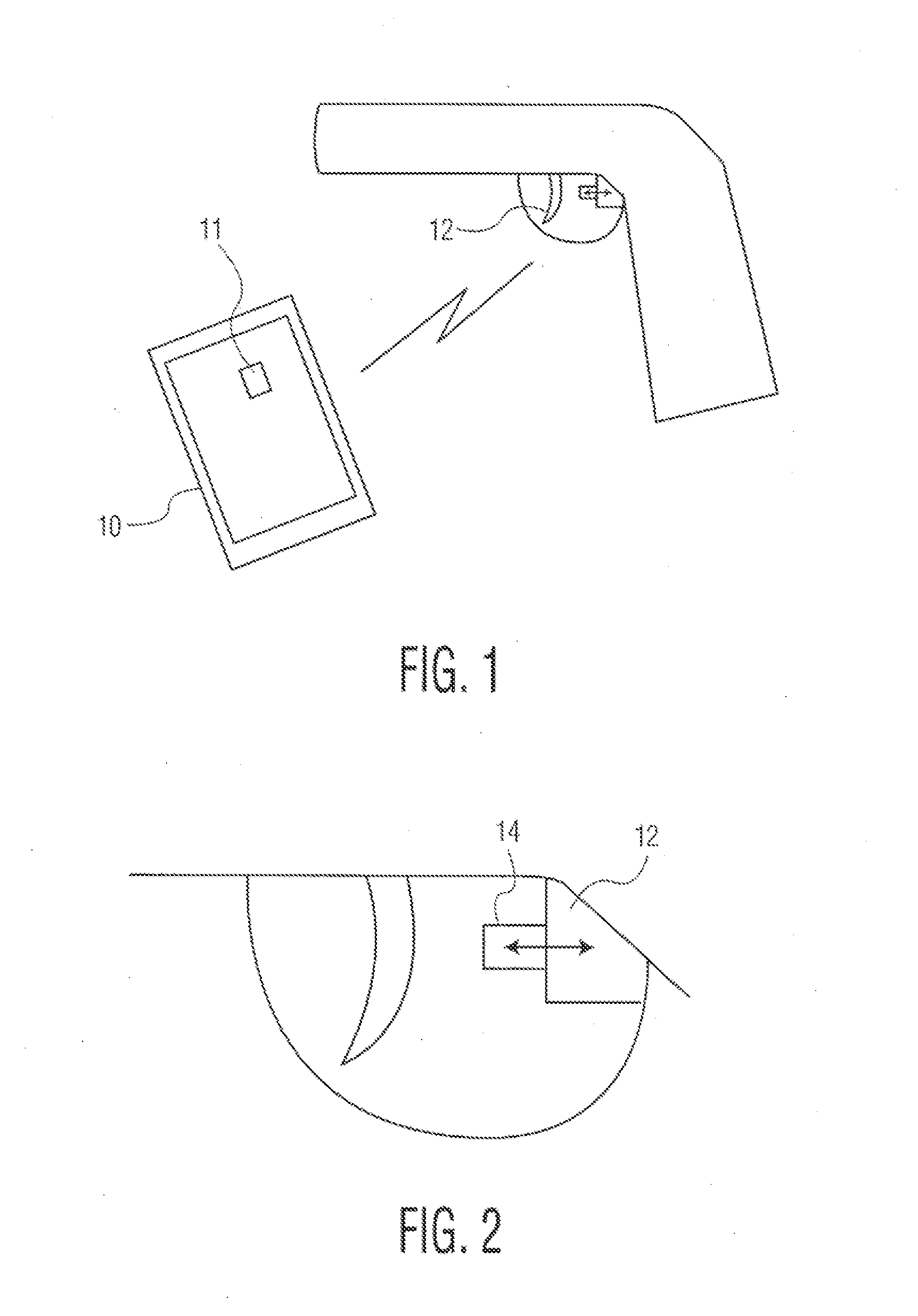
Secure smartphone-operated gun trigger lock
ActiveUS20140215881A1Prevent degradation of data storedPrevent data storedSafety arrangementIndividual entry/exit registersData transmissionData memory
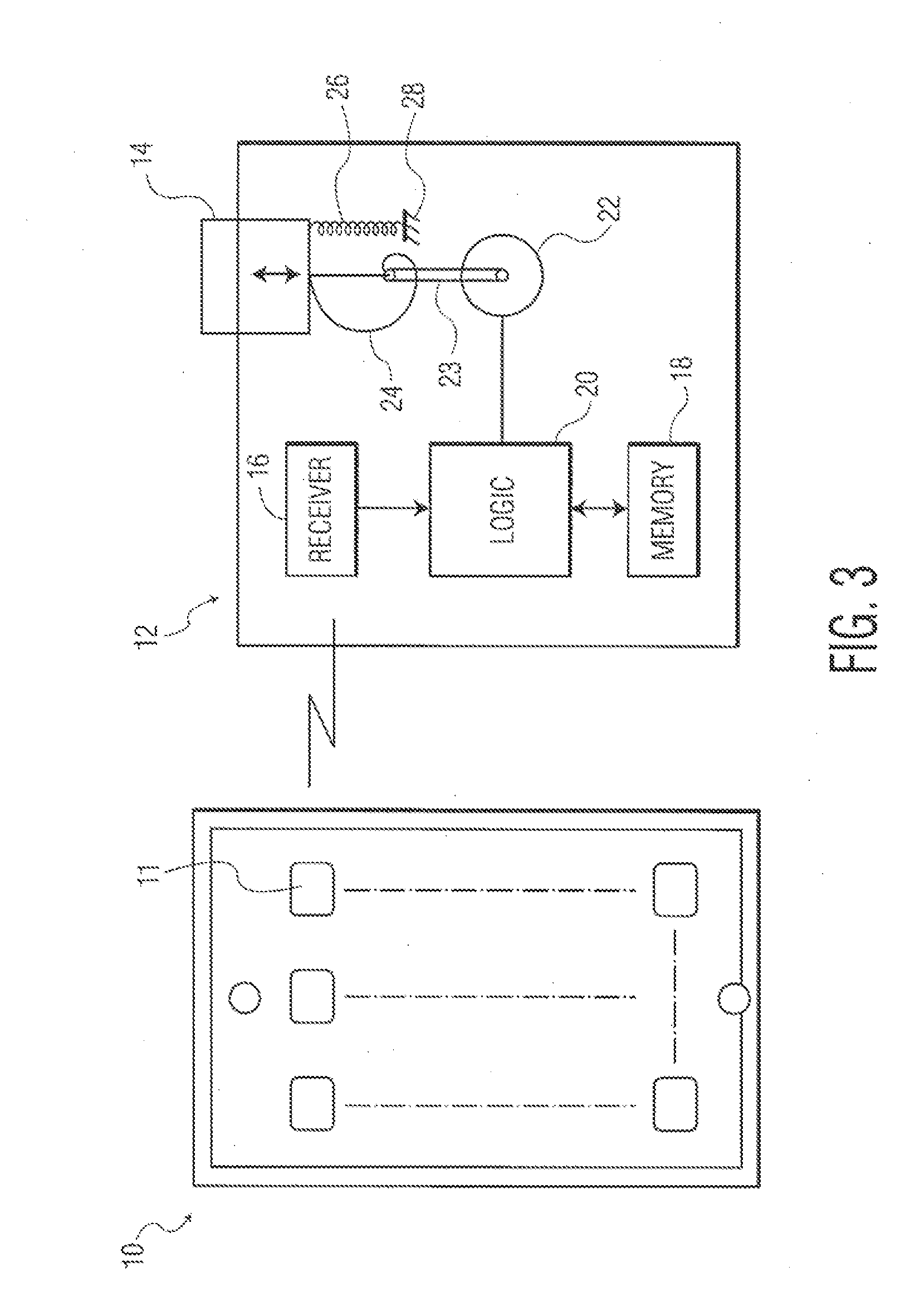
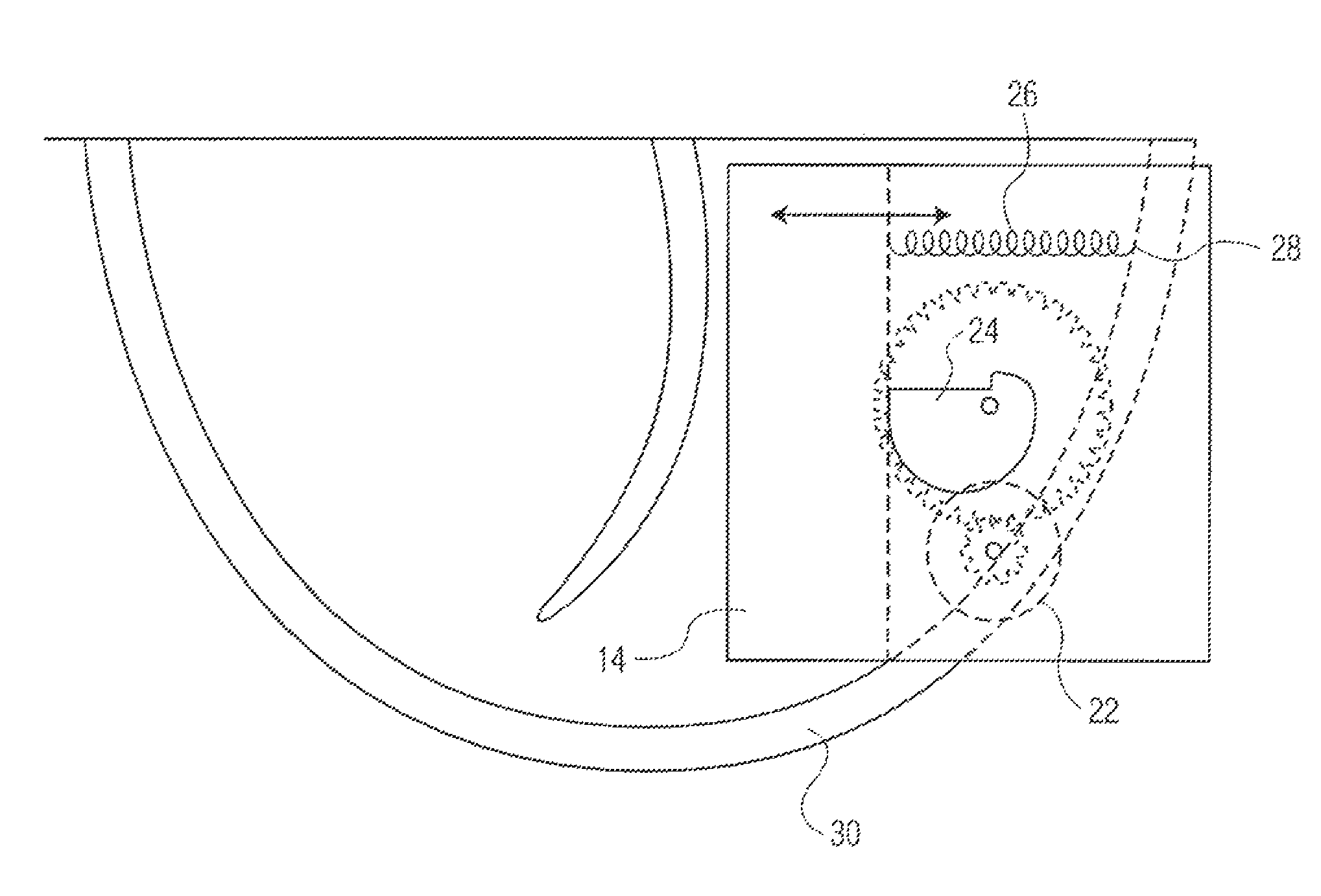
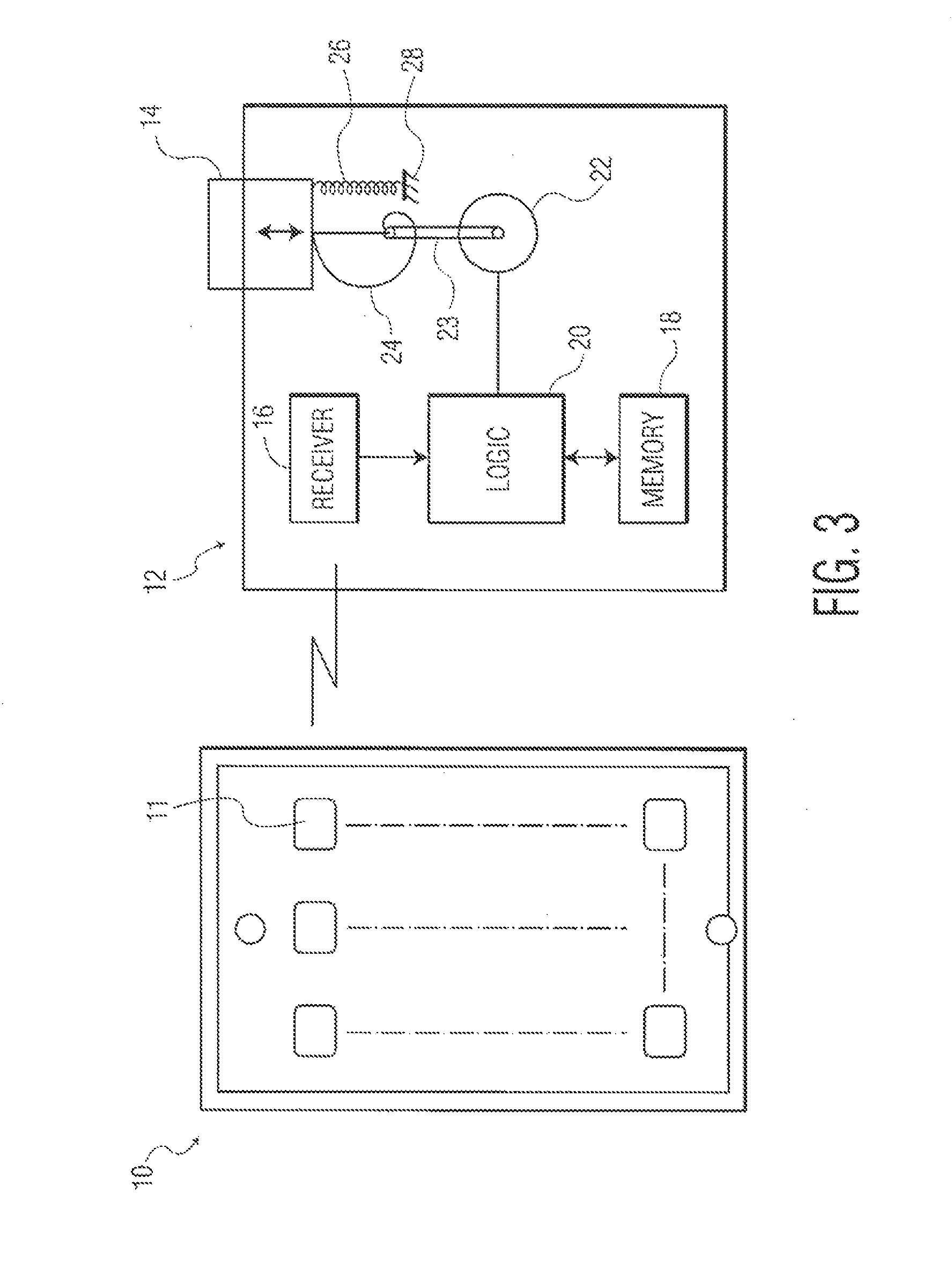
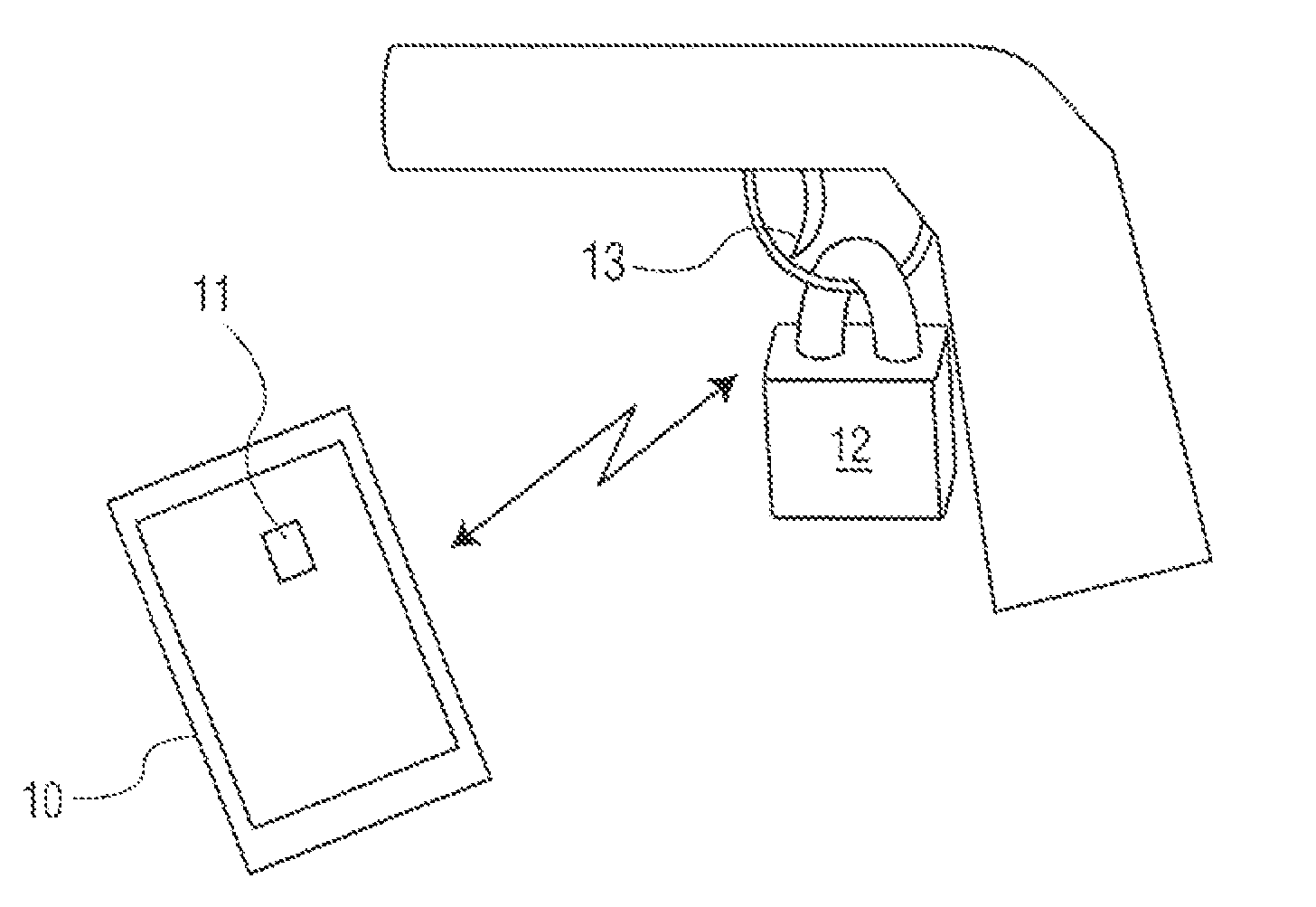
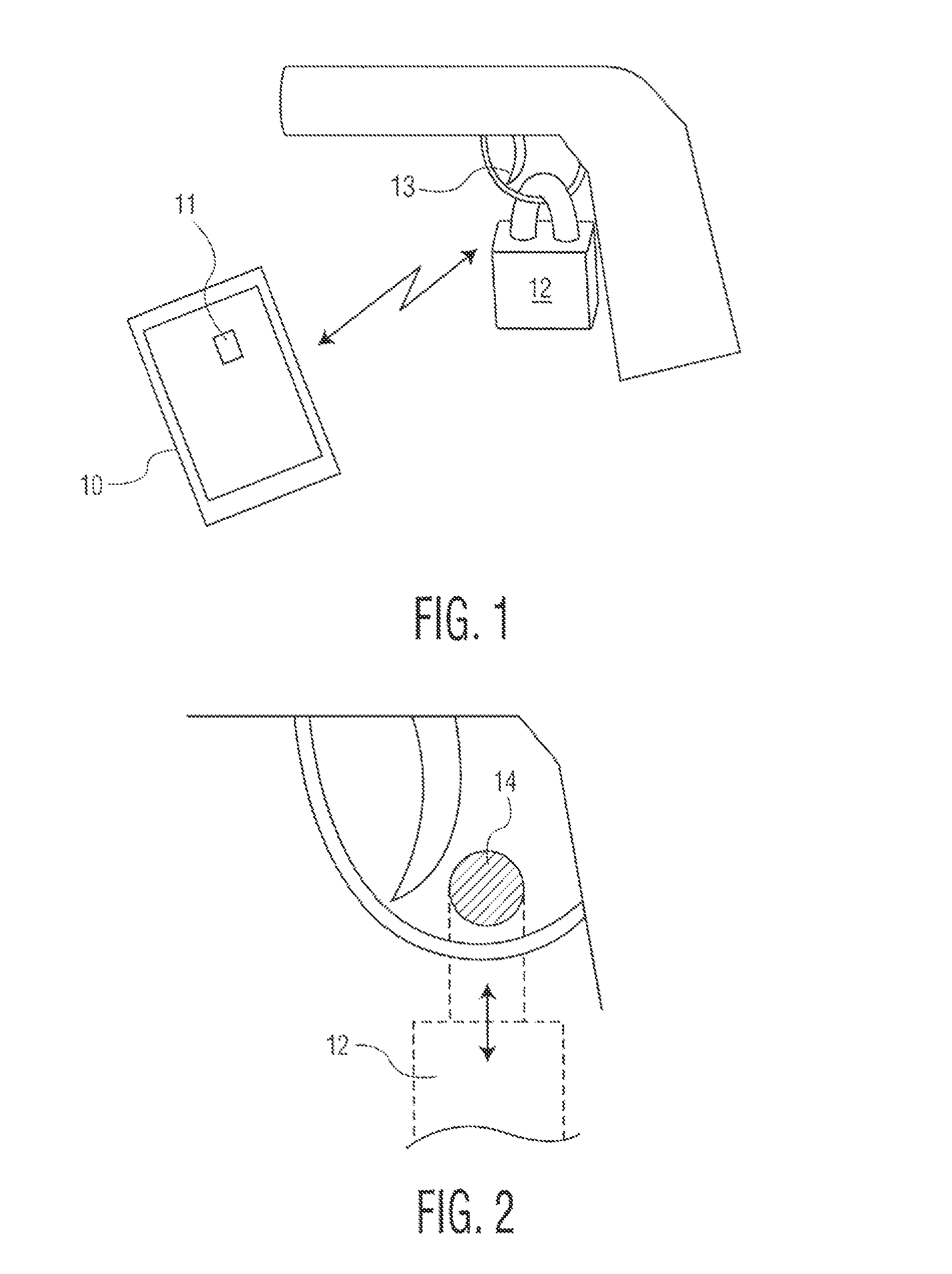
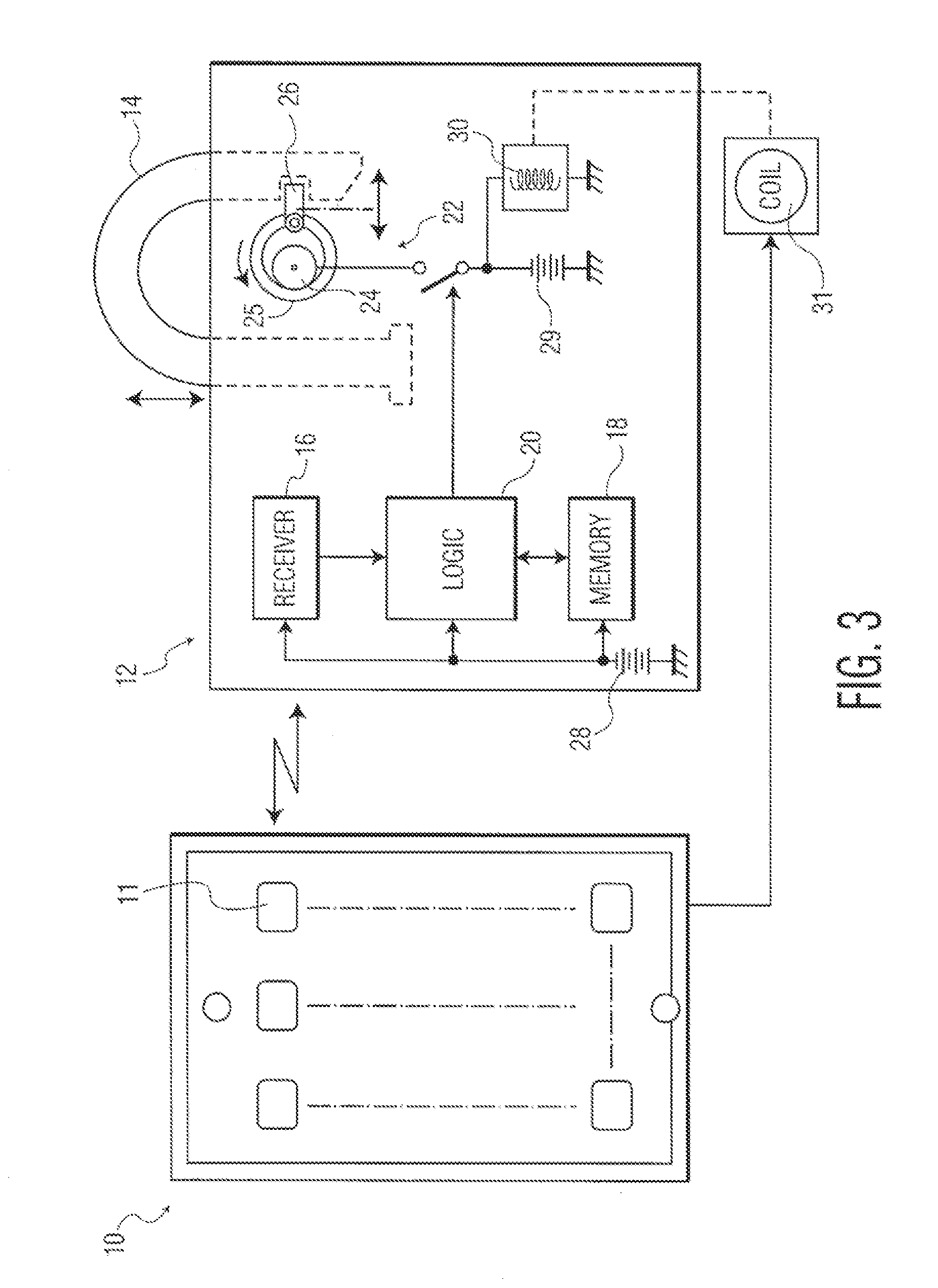
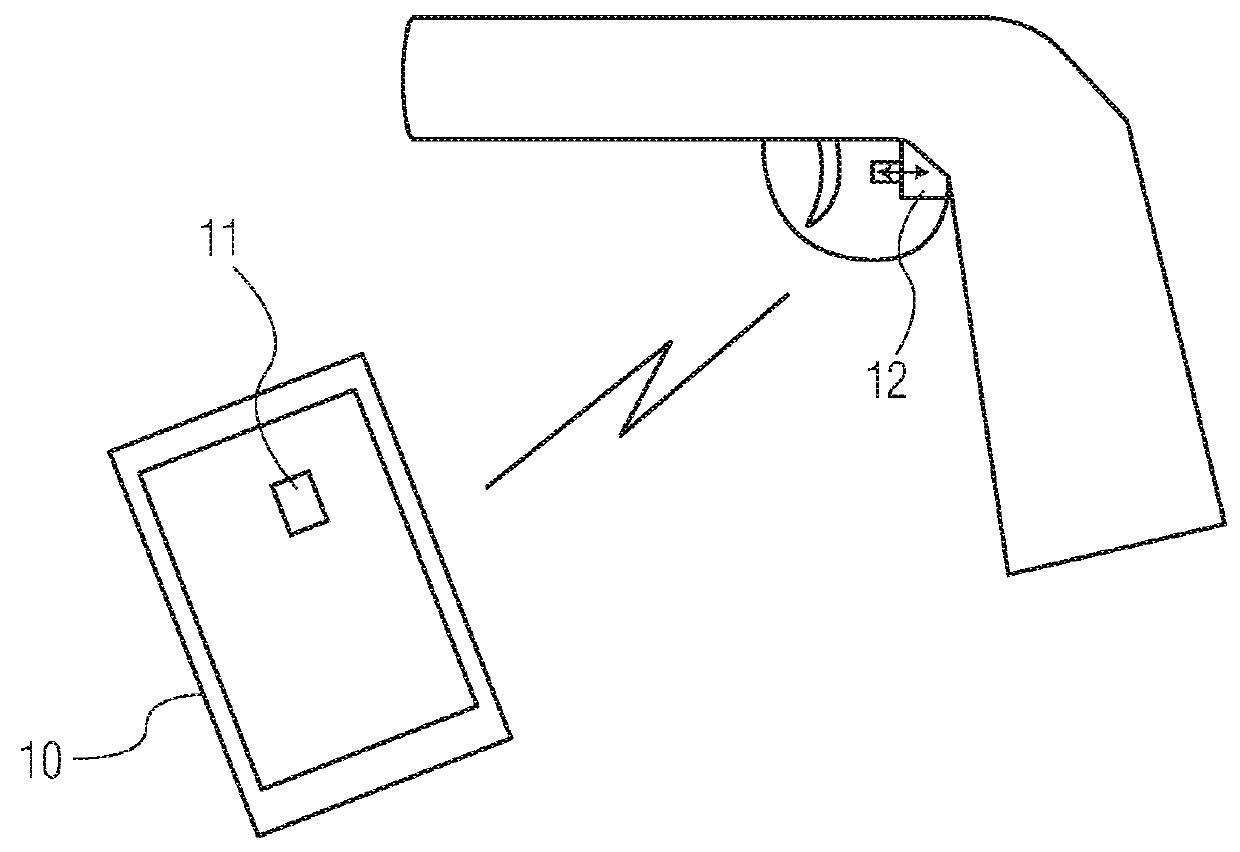
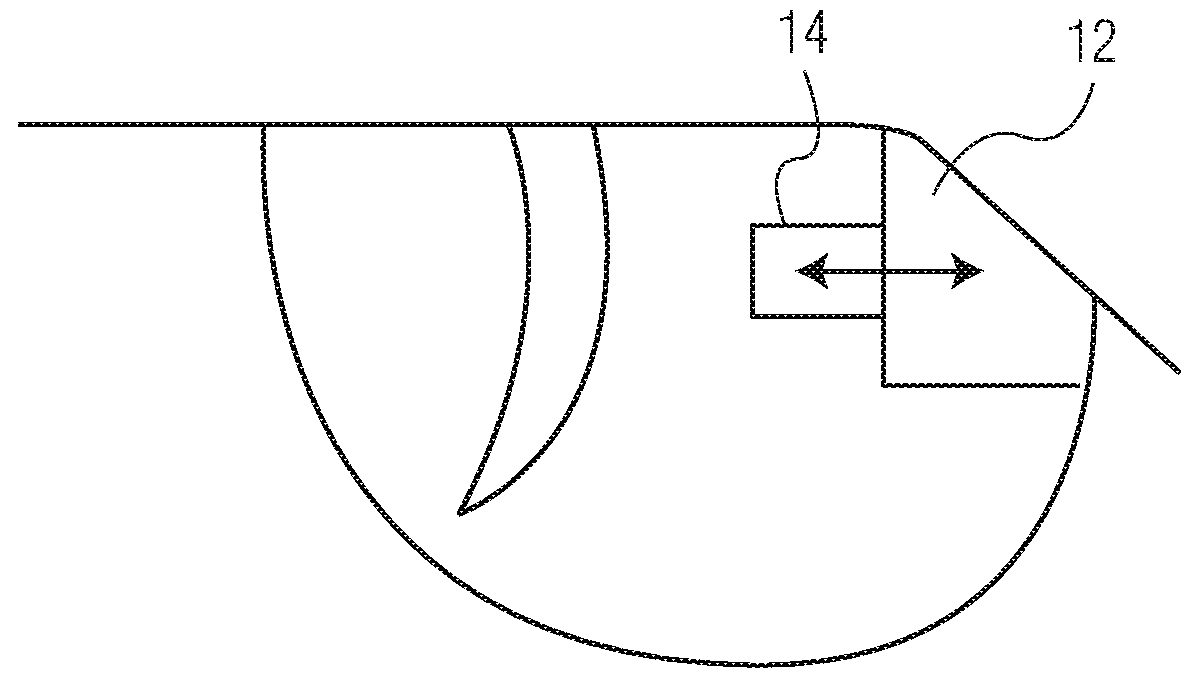
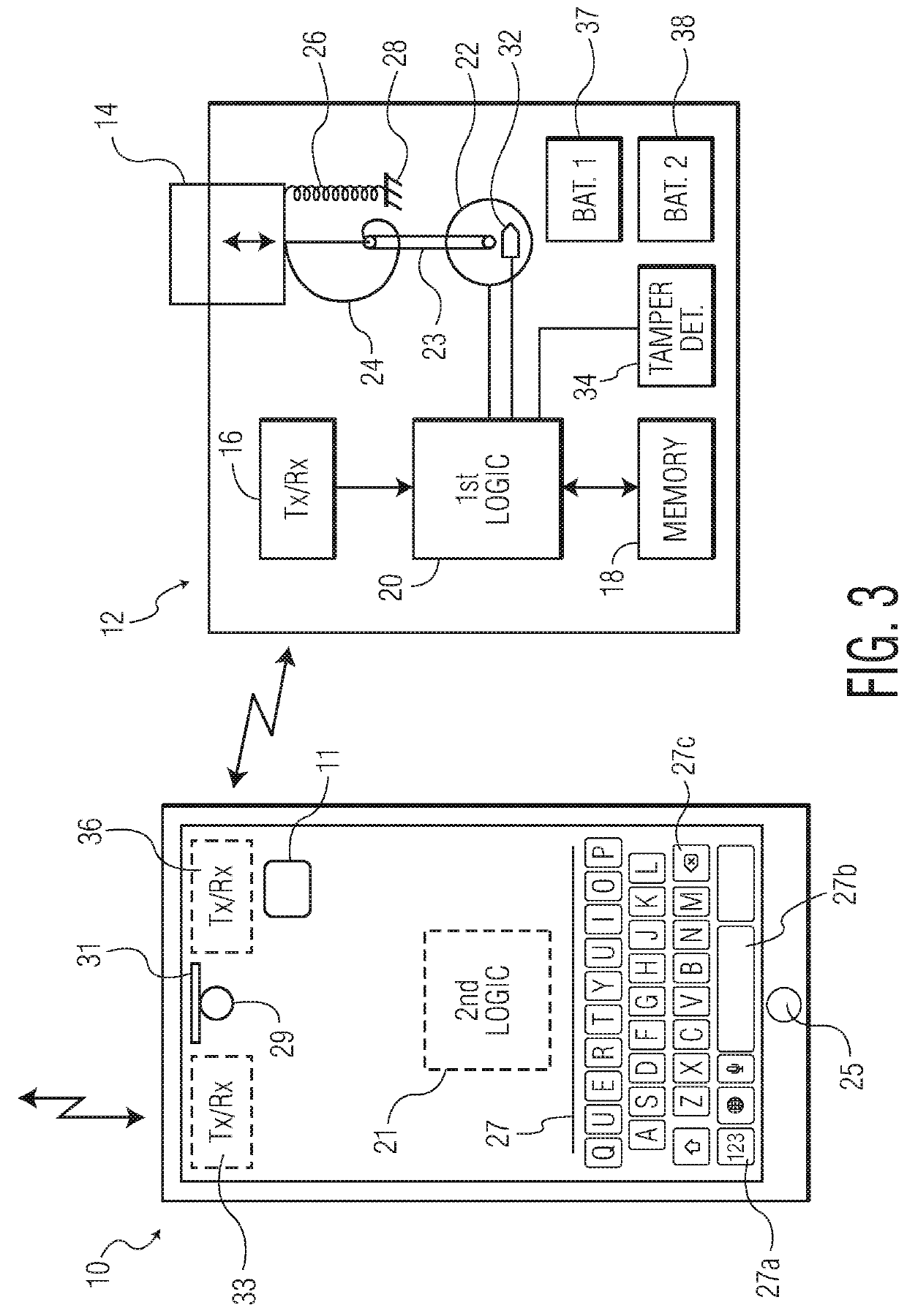
A battery-powered trigger-locking device, which is configured to be disposed on a gun with a trigger for firing, includes a data receiver, a data memory and a logic device for determining whether data received by the receiver is the same, or substantially the same, as data stored in the memory. If a data match is indicated, the logic device causes an electromagnetic device to move a trigger-locking member to an unlocked position, permitting the gun to be fired. A separate electronic gun key is provided to transmit gun unlock data to the data receiver of the trigger-locking device. This gun unlock data may be a password, a long pseudo-random number or biologic data identifying the gun owner or some other person who is licensed or otherwise authorized to fire the gun.
Owner:MILDE KARL F JR
Secure smartphone-operated gun trigger lock
InactiveUS20140215882A1Increase data storagePrevent data storedSafety arrangementNon-mechanical controlsPasswordData memory
A gun trigger-looking device which is configured to be manually installed on a gun with a trigger-blocking member disposed behind the trigger to prevent the gun from being fired. The device includes a data receiver, a data memory and a logic device for determining whether data received by the receiver is the same as data stored in the memory. If a data match is indicated, the logic device causes an electromagnetic device to move a locking member to an unlocked position, permitting the trigger-blocking member to be manually removed from the gun so the gun can be fired. A separate electronic key is provided to transmit unlock data to the data receiver of the trigger-locking device. This unlock data may be a password, a long pseudo-random number or biologic data identifying the gun owner or some other person who is licensed or otherwise authorized to fire the gun.
Owner:MILDE JR KARL F
Secure smartphone-operated gun trigger lock
ActiveUS8893420B2Difficult to compromiseAllow useSafety arrangementIndividual entry/exit registersPasswordData memory
A battery-powered trigger-locking device, which is configured to be disposed on a gun with a trigger for firing, includes a data receiver, a data memory and a logic device for determining whether data received by the receiver is the same, or substantially the same, as data stored in the memory. If a data match is indicated, the logic device causes an electromagnetic device to move a trigger-locking member to an unlocked position, permitting the gun to be fired. A separate electronic gun key is provided to transmit gun unlock data to the data receiver of the trigger-locking device. This gun unlock data may be a password, a long pseudo-random number or biologic data identifying the gun owner or some other person who is licensed or otherwise authorized to fire the gun.
Owner:MILDE KARL F JR
Secure smartphone-operated gun trigger lock
InactiveUS8919024B2Difficult to compromiseAllow useSafety arrangementNon-mechanical controlsPasswordEngineering
Owner:MILDE JR KARL F
Remote control weapon lock
Owner:MILDE KARL F JR
Login token generation and verification method and device and server
ActiveCN110493202AIncreased complexityImprove securityKey distribution for secure communicationUser identity/authority verificationInformation technologyExpiration Time
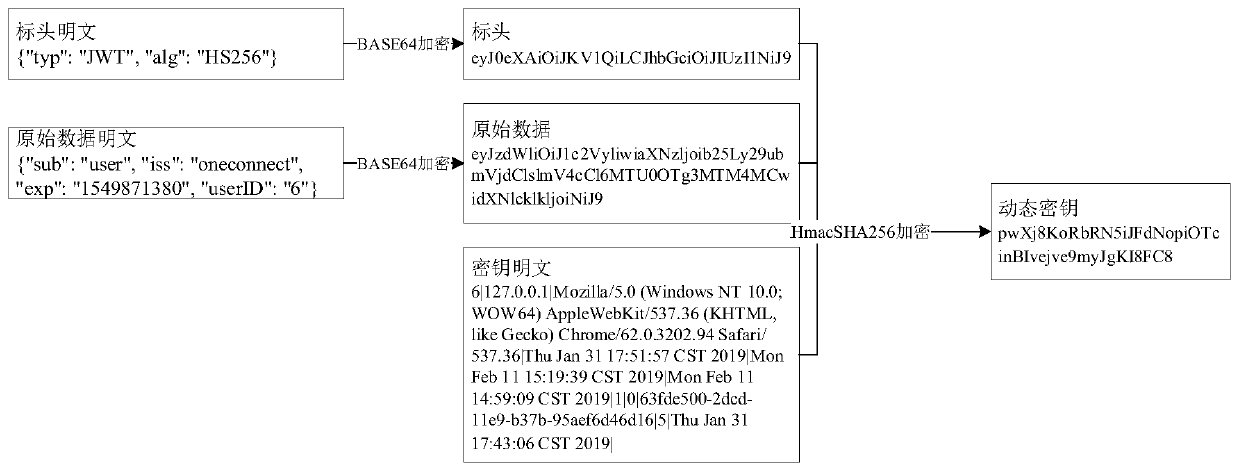
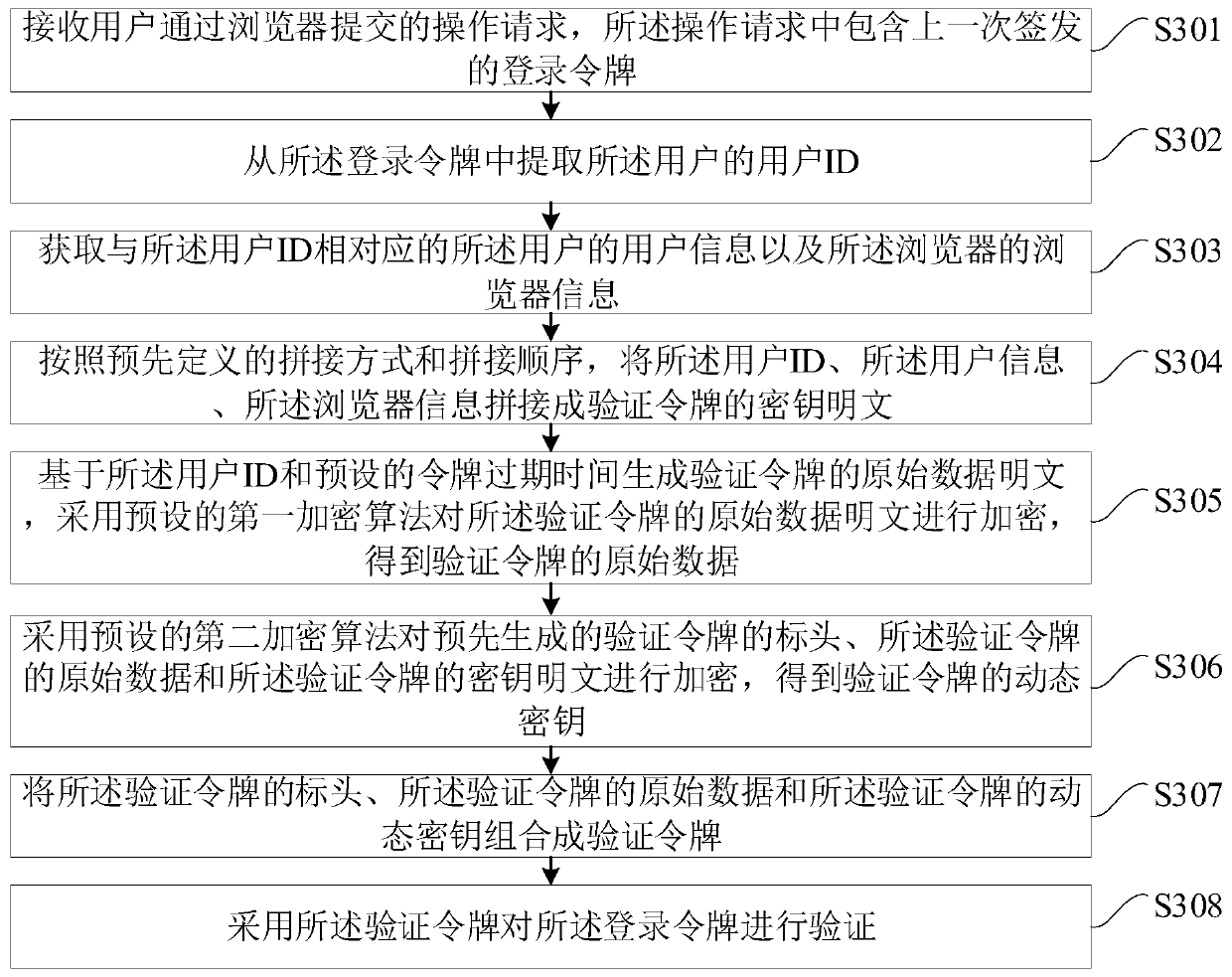
The embodiment of the invention is applicable to the technical field of information, and provides a login token generation and verification method and device and a server, and the login token generation method comprises the steps: receiving a login request submitted by a user through a browser, and verifying a user ID and a password contained in the login request; after verification succeeds, obtaining browser information and user information; splicing the user ID, the user information and the browser information into a key plaintext according to a predefined splicing mode and a predefined splicing sequence; generating an original data plaintext based on the user ID and preset token expiration time, and encrypting the original data plaintext by adopting a preset first encryption algorithmto obtain original data; encrypting the header, the original data and the key plaintext which are generated in advance by adopting a preset second encryption algorithm to obtain a dynamic key; and combining the header, the original data and the dynamic key into the login token, so that the security of the login token and the system is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Security protection method specific to unauthorized access
InactiveCN103731434AAvoid unauthorized operationsRealize background authority controlTransmissionAuthorizationAnnotation
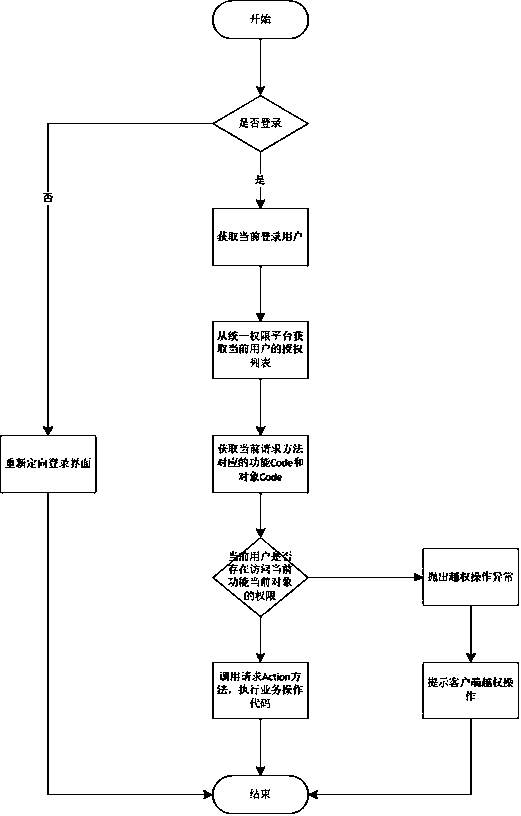
The invention discloses a security protection method specific to unauthorized access. The security protection method comprises determining whether a user logins or not according to the server session information and turning to a login interface if the user does not login; performing the authorization check further if the user logins; obtaining the login information of the current user in the server session; obtaining an authorization list from an authorization platform according to the login information of the current user, wherein the current user has access to the authorization list; obtaining a menu code and a button code which are corresponding to a request according to an annotation of an action method of the user request; checking whether the menu code and the button code of the user request are in the authorization list of the user or not and throwing out an unauthorized operation exception if the user request is not in the authorization list; prompting the user that the request is invalid due to the unauthorized operation. The security protection method specific to the unauthorized access is simple and efficient.
Owner:STATE GRID CORP OF CHINA +2
Patrol intelligent monitoring terminal and working method thereof
InactiveCN110430348AImprove targetingWide screen rangeTelevision system detailsCharacter and pattern recognitionWorking setComputer terminal
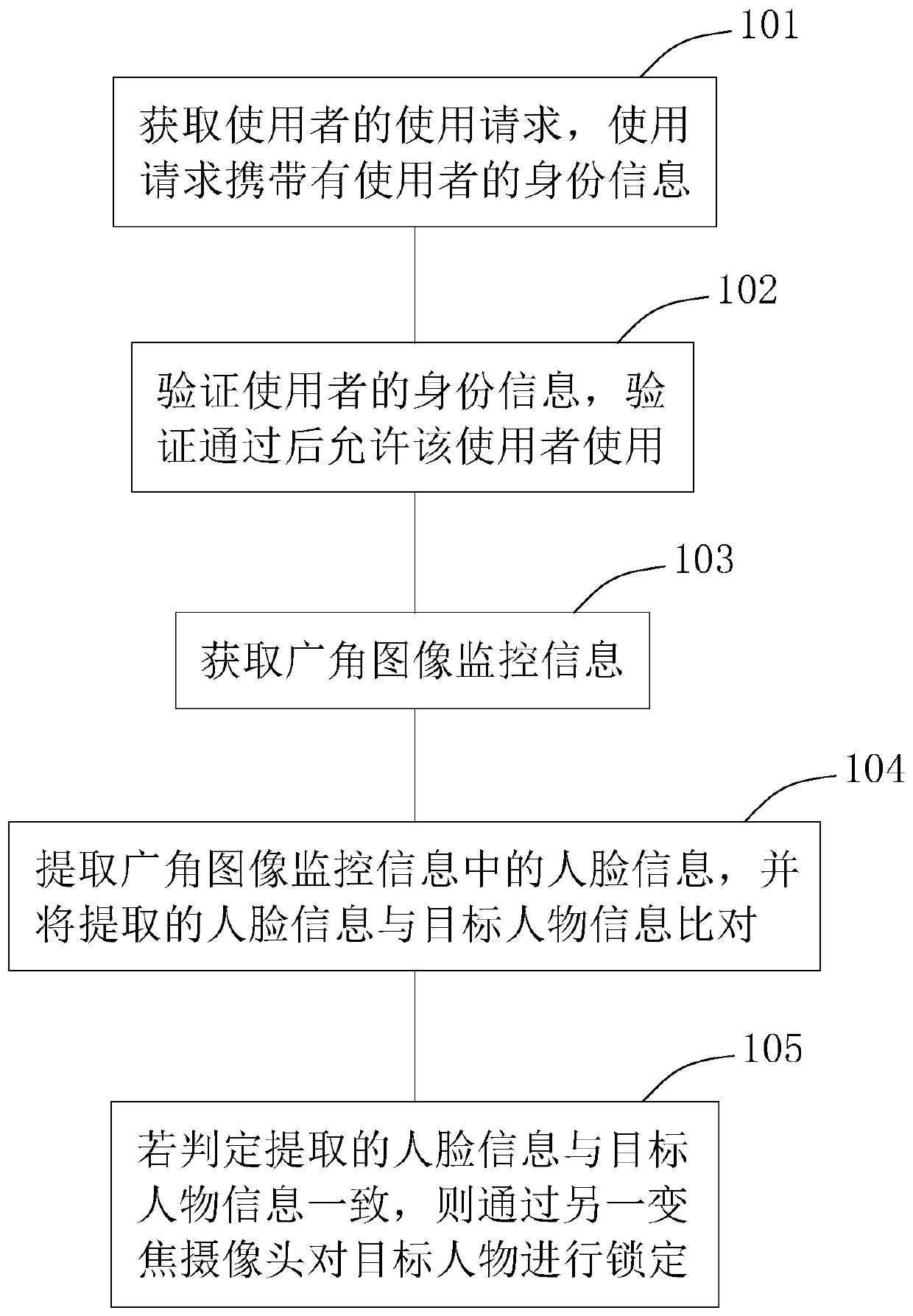
The invention discloses a patrol intelligent monitoring terminal and a working method thereof, and relates to the field of monitoring. The method comprises the following steps of verifying identity information of a user, and allowing the user to use after the verification is passed; acquiring wide-angle image monitoring information; extracting face information in the wide-angle image monitoring information, and comparing the extracted face information with target person information; and if the extracted face information is consistent with target person information, locking a target person through another zoom camera; and obtaining a use request of the user, and if the identity information passes the verification, allowing the user to use, thereby preventing a person without use permissionfrom influencing the use of the terminal. Wide-angle image monitoring information is obtained, the picture range is wide, a large range can be monitored, the extracted face information is compared with target person information, if the extracted face information is consistent with the target person information, another zoom camera is started to lock and monitor the target person, wide-area monitoring is guaranteed, and meanwhile target person monitoring is more targeted and comprehensive.
Owner:SHENZHEN WELL ELECTRIC
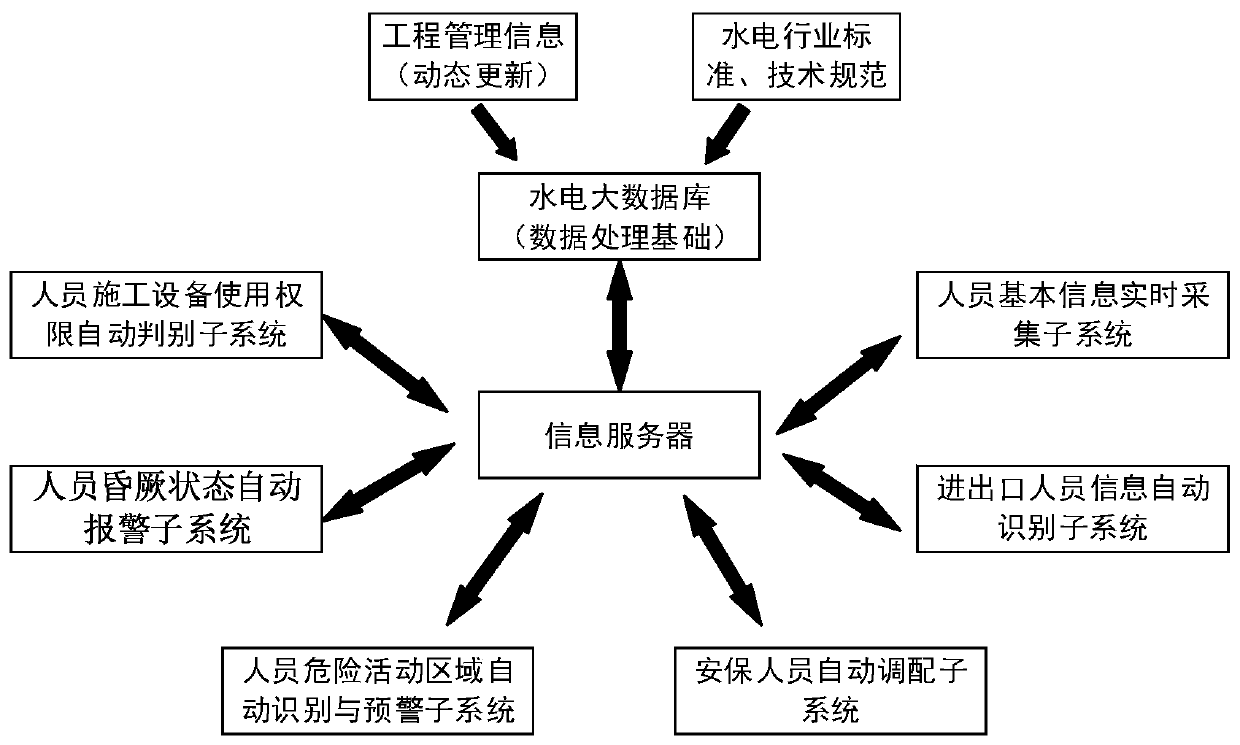
Constructor HSE integrated management system
PendingCN110490430ARealize automatic acquisitionRealize analysisRegistering/indicating time of eventsIndividual entry/exit registersTime informationReal time analysis
The invention provides a constructor HSE integrated management system. The system comprises a personnel basic information real-time acquisition subsystem used for acquiring personnel basic informationand transmitting the acquired real-time information to a hydroelectric big database; a personnel construction equipment use permission automatic judgment subsystem used for construction equipment operation management; a personnel faint state automatic alarm subsystem used for automatically judging whether the personnel is in a faint state or not and giving an alarm; a personnel dangerous activityarea automatic recognition subsystem used for monitoring whether personnel enter a dangerous area or not and giving an early warning prompt; an import and export personnel information automatic recognition subsystem used for identifying and verifying import and export personnel information; and a safety personnel automatic deployment subsystem used for monitoring the distribution condition of thesafety personnel and carrying out safety management. Real-time information acquired by the personnel basic information real-time acquisition subsystem is used as a part of data basis for real-time analysis, so that the functions of the subsystems are realized. According to the system, full-automatic HSE comprehensive management of engineering construction field personnel is realized.
Owner:CHINA THREE GORGES PROJECTS DEV CO LTD
A gesture interaction system and method applied to an intelligent classroom
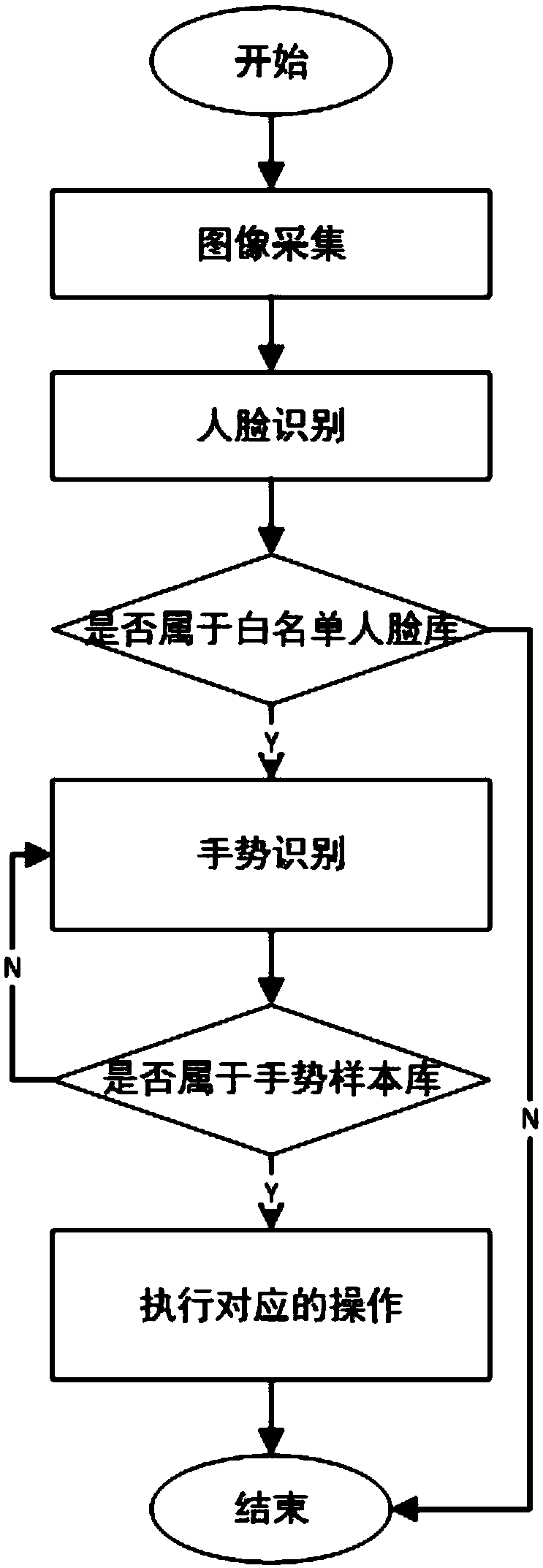
ActiveCN109542219AEasy to useAvoid interferenceInput/output for user-computer interactionCharacter and pattern recognitionInteraction systemsRecognition algorithm
The invention relates to the field of human-computer interaction, in particular to a gesture interaction system and a gesture interaction method applied to an intelligent classroom. The gesture interaction system comprise: a camera module which is used for collecting images of faces, hands and gestures of users; a storage module for storing the acquired image; a processing module which recognizesthe face in the collected image based on the face recognition algorithm, matches the recognized face with the white list face database, and judges whether the user belongs to the white list user or not; if yes, the gesture of the white list user's hand in the collected image is recognized, and the gesture is matched with the pre-stored gesture sample library. Whether the white list user gesture matches the pre-stored gesture sample is judged, and if so, an operation corresponding to the matched gesture sample is performed. The technical proposal of the invention can realize real-time authorization.
Owner:GUANGZHOU JINGBIAO INFORMATION TECH CO LTD
Authority list security control method
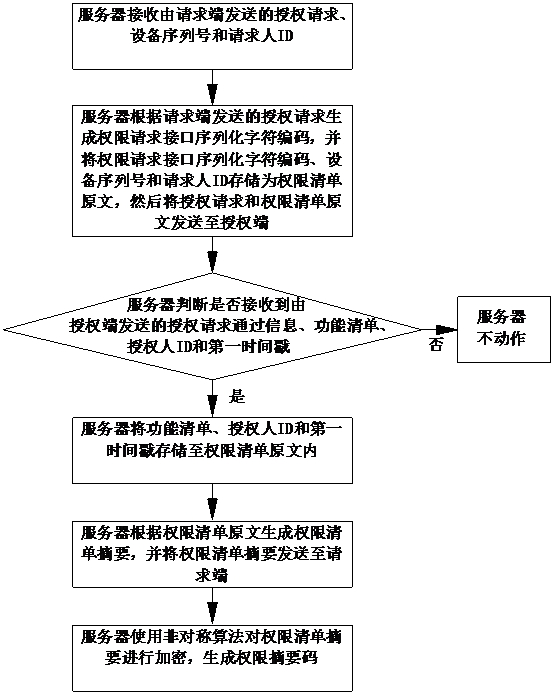
ActiveCN112016082AAvoid exposureUniqueness guaranteedDigital data authenticationInformation functionTimestamp
The invention relates to the technical field of authority control, and aims to provide an authority list security control method which comprises an authority list encryption method. The authority listencryption method comprises the following steps: receiving an authorization request, an equipment serial number and a requester ID sent by a request end; generating an authority request interface serialized character code according to the authorization request sent by the request end, storing the authority request interface serialized character code, the equipment serial number and the requesterID as authority list original texts, and then sending the authorization request and the authority list original texts to an authorization end; judging whether authorization request passing information, a function list, an authorizer ID and a first timestamp sent by the authorization end are received or not; if yes, storing the function list, the authorizer ID and the first timestamp in the authority list original texts, and if not, performing no action; and generating an authority list abstract according to the authority list original texts. The method can avoid plaintext exposure of authoritylists.
Owner:成都掌控者网络科技有限公司
Permission access control method for alliance chain cross-chain
PendingCN113992406AImprove interoperabilityClear function divisionSecuring communicationEngineeringChain network
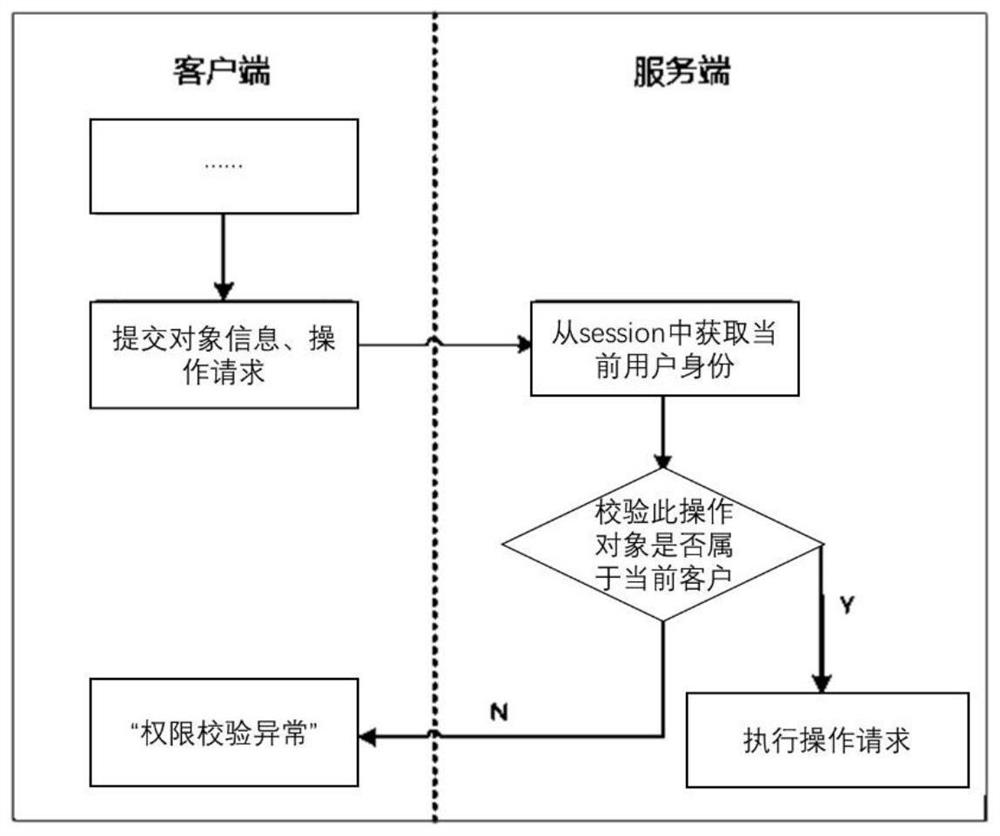
The invention discloses a permission access control method for alliance chain cross-chain. The method comprises the following steps: setting three types of user roles of an administrator, a common user and a supervision user in a cross-chain network; dividing according to user roles and setting permissions; enabling an authority management module to set authority control strategies for all operations in the cross-chain network; respectively setting corresponding permissions of the administrator, the common user and the supervision user according to the permission control strategy; setting an operation of the user management module or a mapping relation mode of an operation object and a user, and obtaining the identity of the user from the server session for judgment; setting operation of cards and order numbers, setting a server to perform unauthorized verification on object information used for business operation, verifying whether the information belongs to a current user, and if the verification is not passed, reporting an error so as to prevent the card numbers and order numbers of other people from being operated by tampering and unauthorized. According to the invention, role permission access control can be realized, so that the safety of cross-chain access is realized.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Authority assignment method for preschool education system
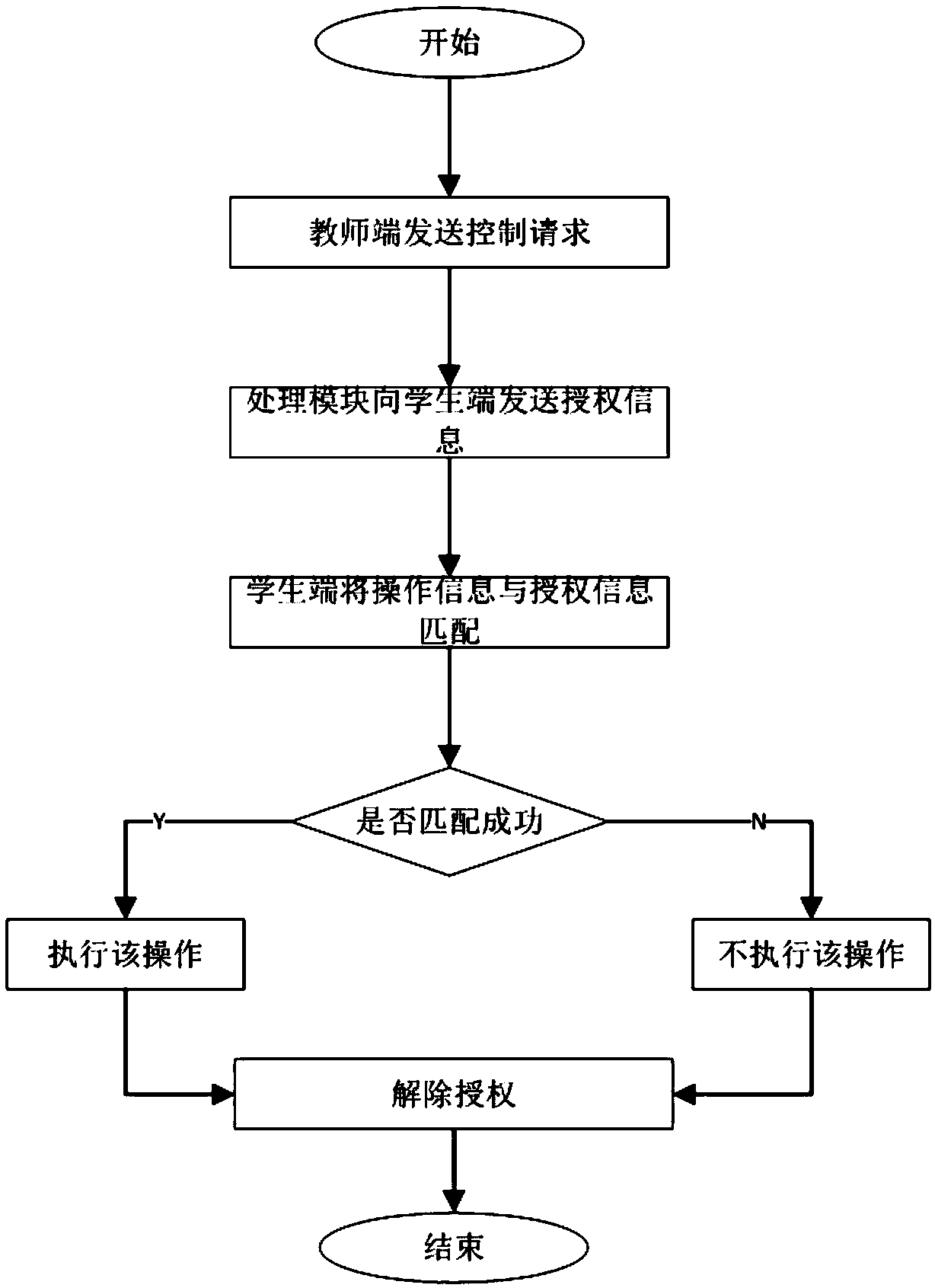
ActiveCN109686155AEasy exit or silent operationAvoid unauthorized operationsData processing applicationsElectrical appliancesAuthority controlControl models
The invention relates to the technical field of terminal user authority control and particularly discloses a authority assignment method for a preschool education system. The authority assignment method comprises the following steps: (S1) sending a control request including a control model to a processing module by a teacher terminal; (S2) receiving the control request by the processing module, and acquiring corresponding authorization information from a defaulted authority list; (S3) acquiring the authorization information from the processing module by a student terminal, after operation information of a user is received by the student terminal, matching the operation information with the authorization information, if the operation information is successfully matched with the authorization information, carrying out the operation, and if the operation information is not successfully matched with the authorization information, omitting the operation; and (S4) sending a control ending request to the processing module by the teacher terminal, and after the control ending request is received by the processing module, releasing the authorization information of the student terminal. According to the technical scheme, the authority of the student terminal can be conveniently and effectively distributed.
Owner:重庆康普达科技有限公司
Subscriber security setup maintenance method and system
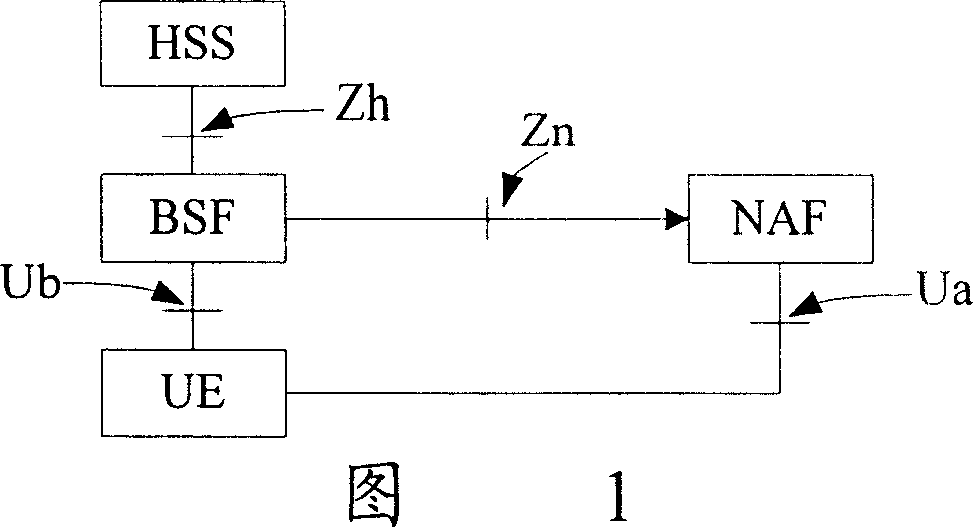
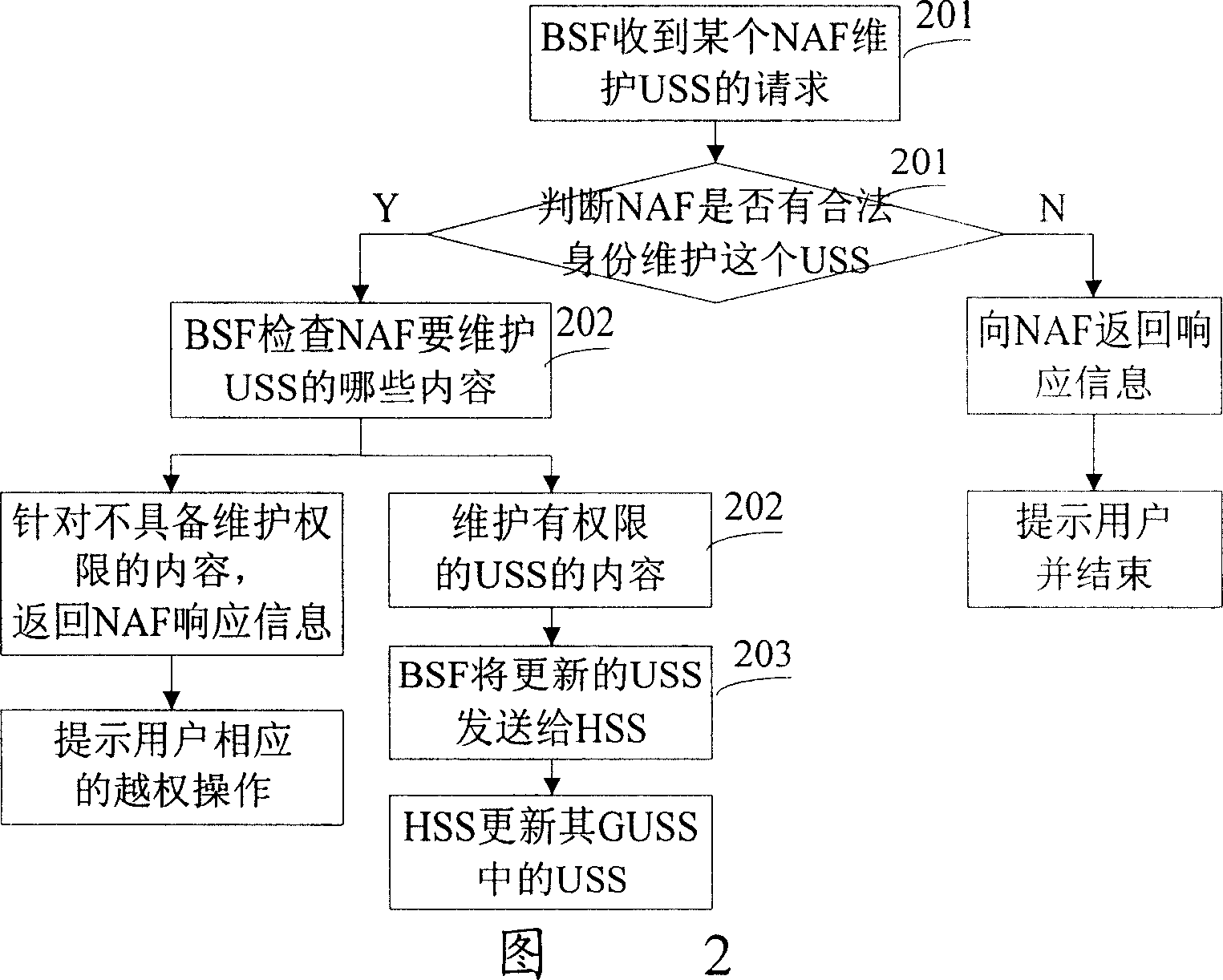
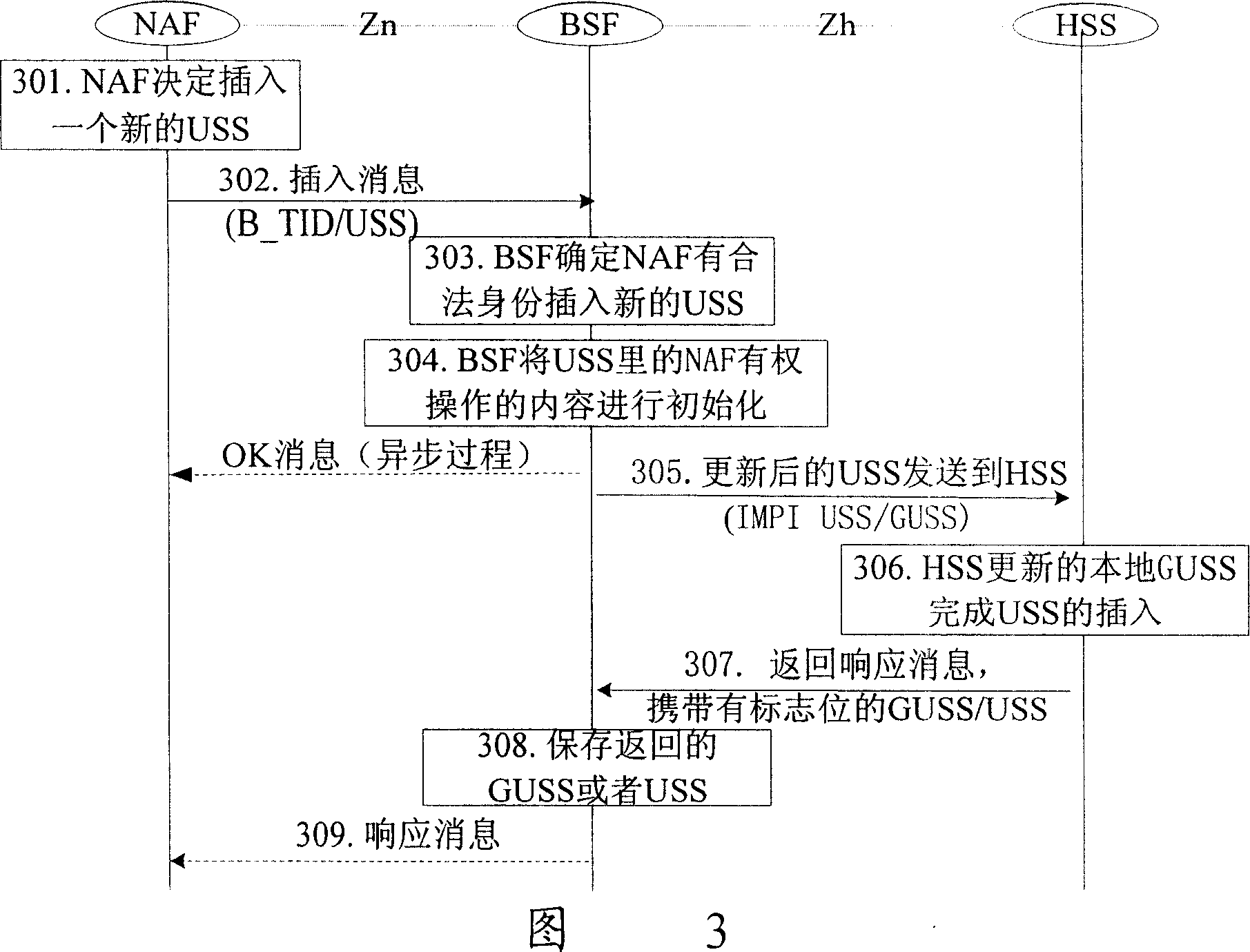
InactiveCN1968495AAvoid unauthorized operationsUnauthorized operations will not generateUser identity/authority verificationRadio/inductive link selection arrangementsComputer science
The invention relates to a method for maintaining USS, which comprises that: BSF receives the maintain request from NAF to maintain one USS; judges said legality of NAF; BSF checks the contents of maintained USS and finds out the USS content which can be operated by NAF, and operates the USS content; BSF sends operated USS to HSS, to store the USS of GUSS, and provide the system for maintaining USS. With said invention, NAF can correctly modify the USS of GUSS, to reduce HSS maintain load and support enough freedom to the NAF.
Owner:HUAWEI TECH CO LTD
Lottery ticket machine for preventing from being operated by external input equipment
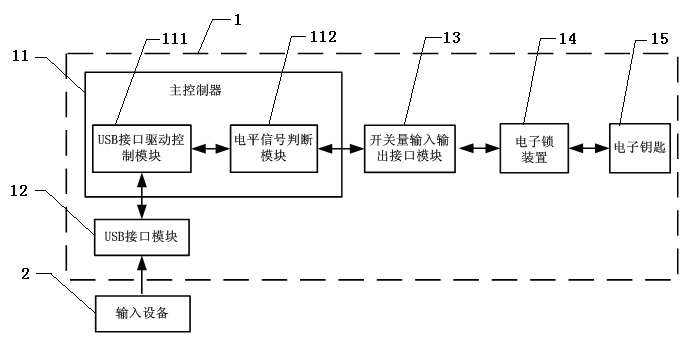
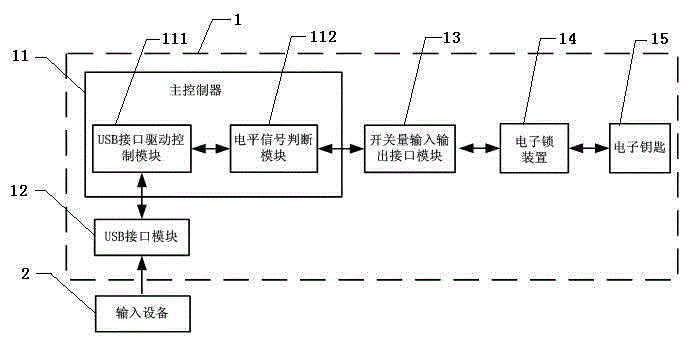
ActiveCN102013123AAvoid unauthorized operationsEnsure safetyLottery apparatusComputer moduleEngineering
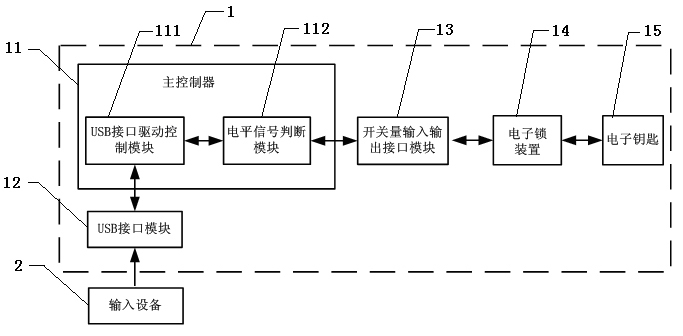
The invention discloses a lottery ticket machine for preventing from being operated by external input equipment. The lottery ticket machine comprises a main controller, a USB interface module connected with the main controller, and a USB interface driving control module arranged inside the main controller, and also comprises a switching value input and output interface module connected with the main controller, an electronic lock device connected with the switching value input and output interface module, and an electronic key matched with the electronic lock device, wherein a level signal judging module is arranged inside the main controller. The lottery ticket machine for preventing from being operated by the external input equipment can effectively prevent the lottery ticket machine from performing unauthorized operation through the external input equipment in real time, and the safety of the data of the lottery ticket machine is guaranteed.
Owner:北京亚博高腾科技有限公司
Fault detection circuit
ActiveCN102967818AReduce power consumptionGuaranteed security featuresElectronic circuit testingReal-time computingFailure detector
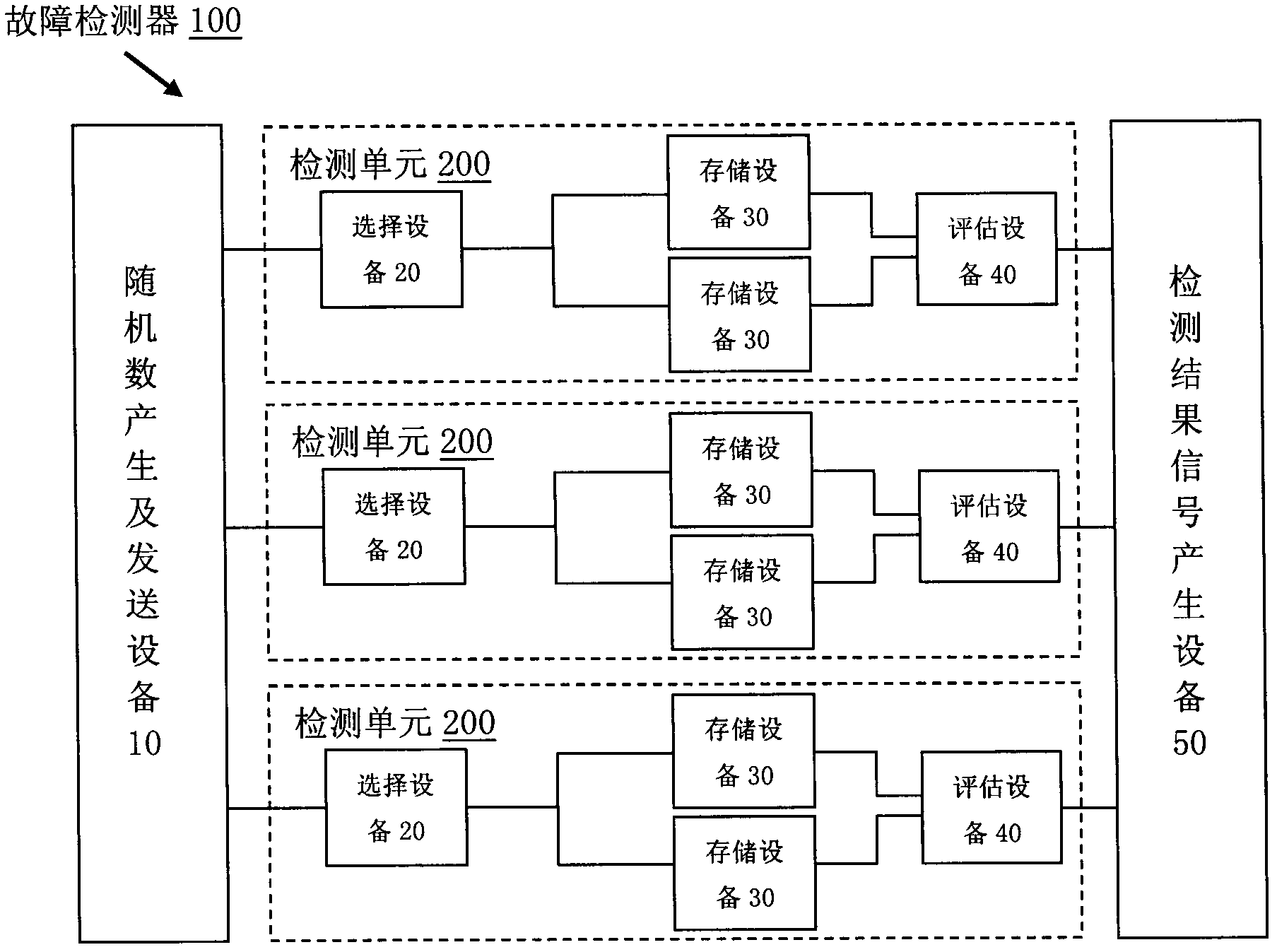
The invention provides a fault detector which is used for detecting modification of internal data of an intelligent card by various external attacks in application of high safety performance intelligent cards and stimulating corresponding protection measures to ensure that the intelligent card works in the safe and reliable state.
Owner:HUADA SEMICON CO LTD
Data supervision system based on vehicle-mounted intelligent box and automated management system thereof
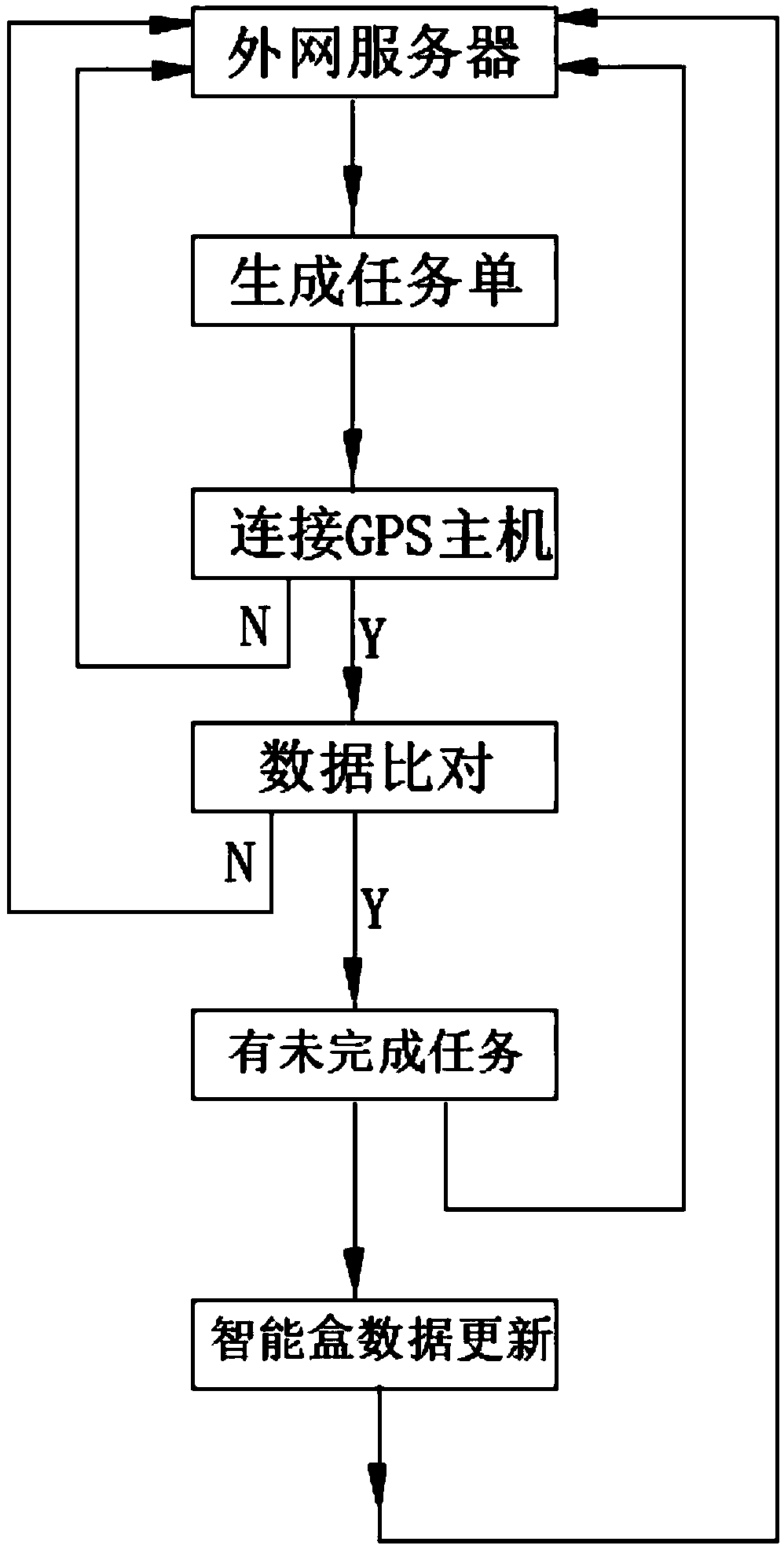
ActiveCN109347953AAvoid administrative loopholesRealize data docking and automatic managementRegistering/indicating working of vehiclesTransmissionManagement efficiencyCoal
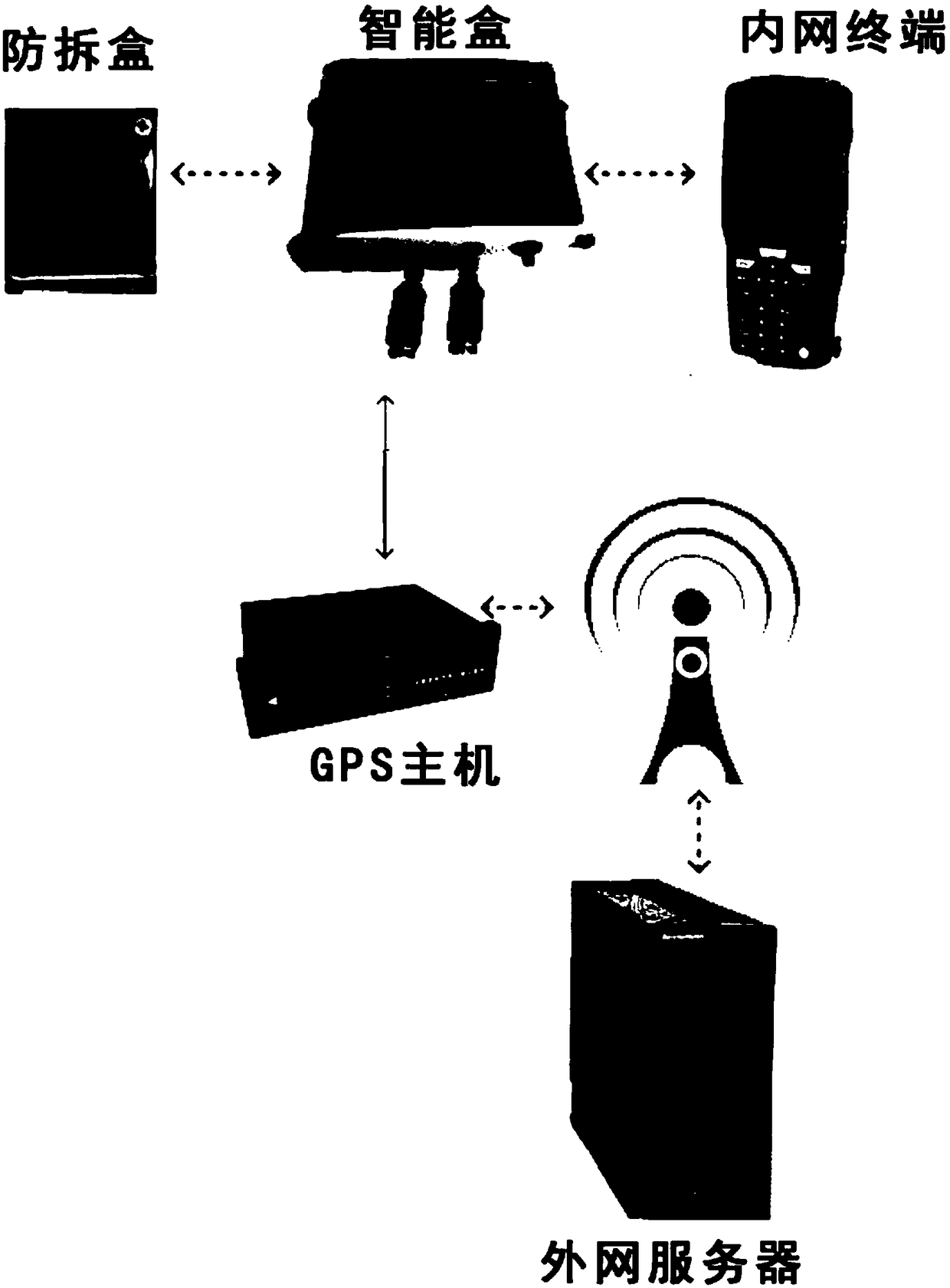
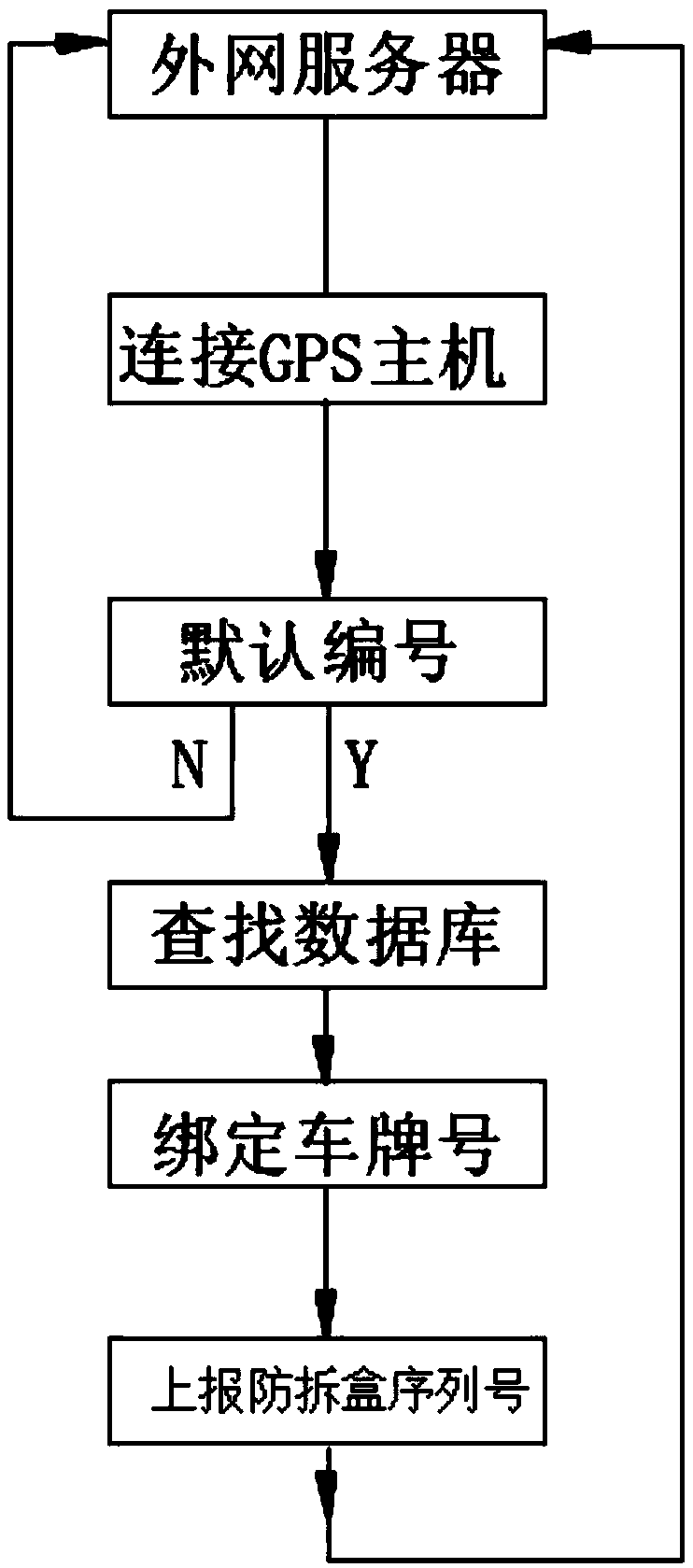
The invention discloses a data supervision system based on a vehicle-mounted intelligent box and an automated management system thereof. The data supervision system comprises intelligent boxes, anti-disassembly boxes, a GPS host, an extranet server and an intranet terminal, wherein the intelligent boxes respectively perform data interaction with the GPS host and the intranet terminal, the GPS hostperforms data interaction with the extranet server, the intelligent boxes perform data interaction with the intranet terminal, the intelligent boxes perform data interaction with the anti-disassemblyboxes, the intelligent boxes correspond to the anti-disassembly boxes one by one, the intelligent boxes are located in a cab of a vehicle, and the anti-disassembly boxes are installed on a carriage of the vehicle; and the automated management system at least comprises four process links that are initialization binding, task distribution, operation tracking and acceptance inspection. Thereby, thethree-party data of power plants, coal mine enterprises and transportation units can be docked and settled as a whole, management loopholes in the operation process of the vehicle can be prevented, the cargo conditions of the vehicle can be monitored in real time, and the management efficiency can be improved.
Owner:吴井礼
Big data platform and server thereof, and security authentication system and method
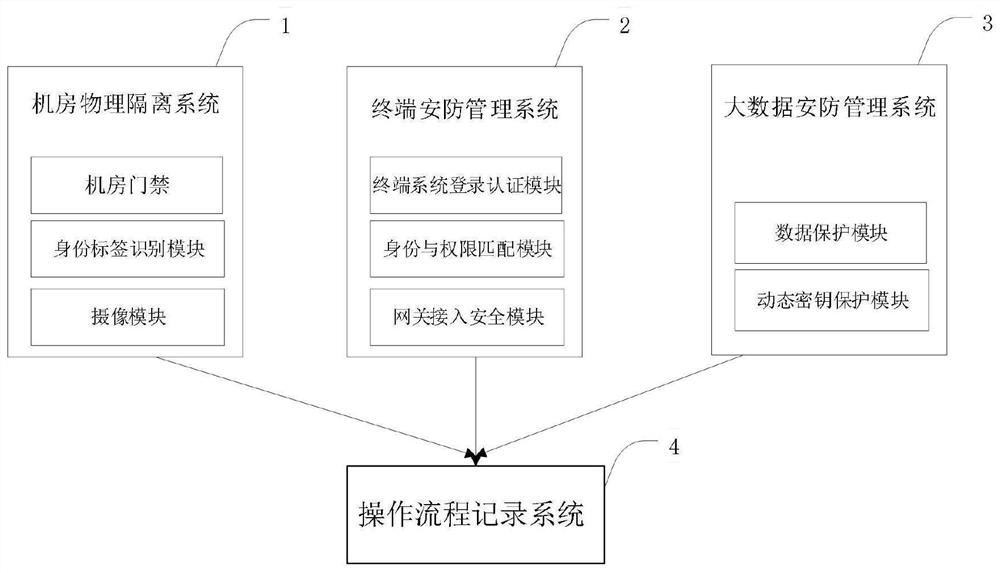
InactiveCN111935068AImprove securityEnsure safetyDigital data authenticationTransmissionData platformInformation networks
The invention discloses a security authentication system for a big data platform, and the system comprises: a machine room physical isolation system which is used for the dynamic protection of the security measures of a machine room where a terminal is located and the access security management of the machine room; a terminal security management system which is used for authenticating the identityand authority of a user logging in the computer terminal and protecting the gateway access security of the terminal and the boundary security of the internal and external information networks; a bigdata security and protection management system which is used for performing security protection on each piece of data or file on the big data platform and dynamically monitoring the operation of a user; and an operation process recording system is used for recording all operation information and processes of the user on the big data platform. According to the invention, multiple security protection measures are adopted to improve the security of the big data platform, and dynamic security protection of the Internet system is realized.
Owner:IND INTERNET INNOVATION CENT (SHANGHAI) CO LTD
Data processing method and device based on file system in satellite
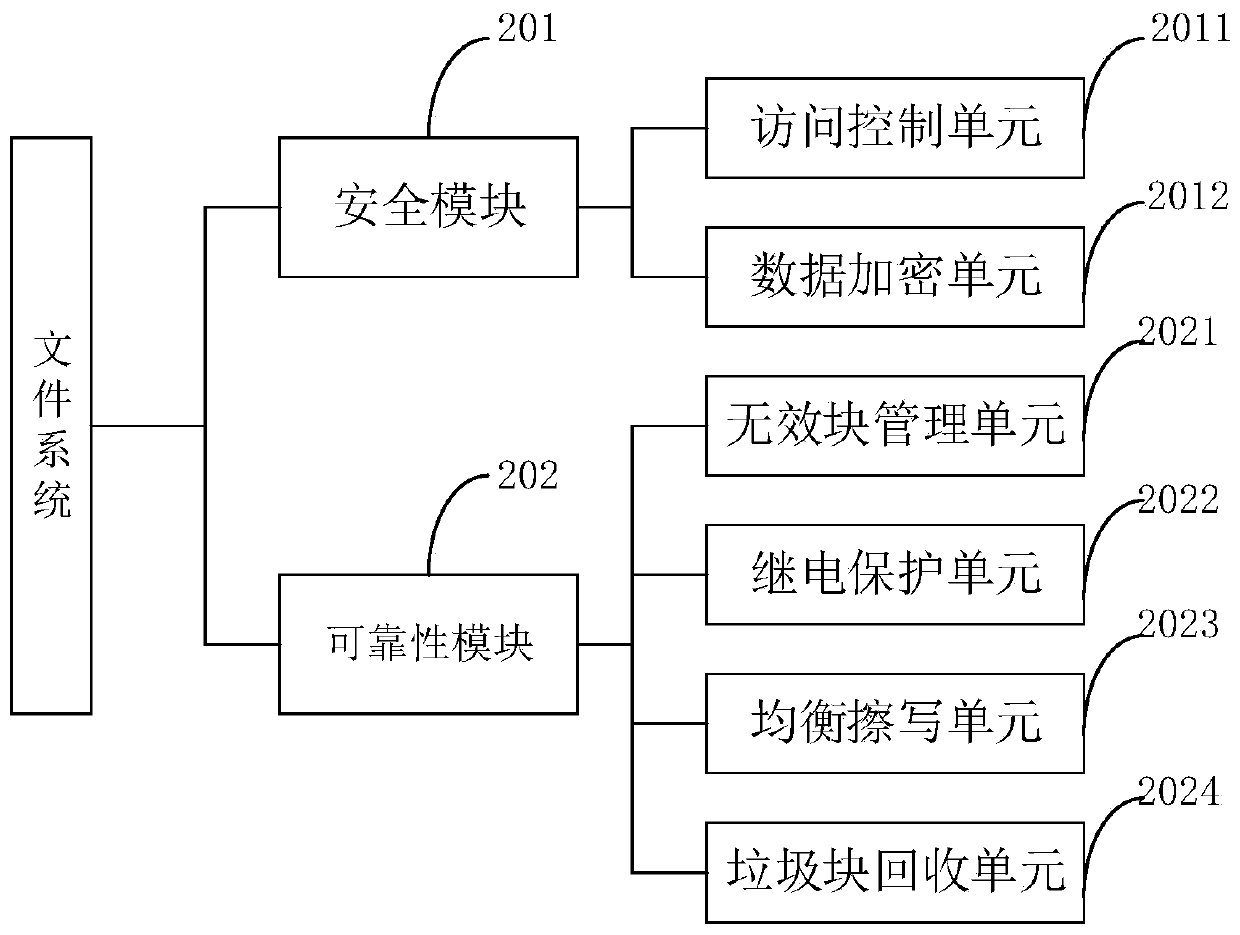
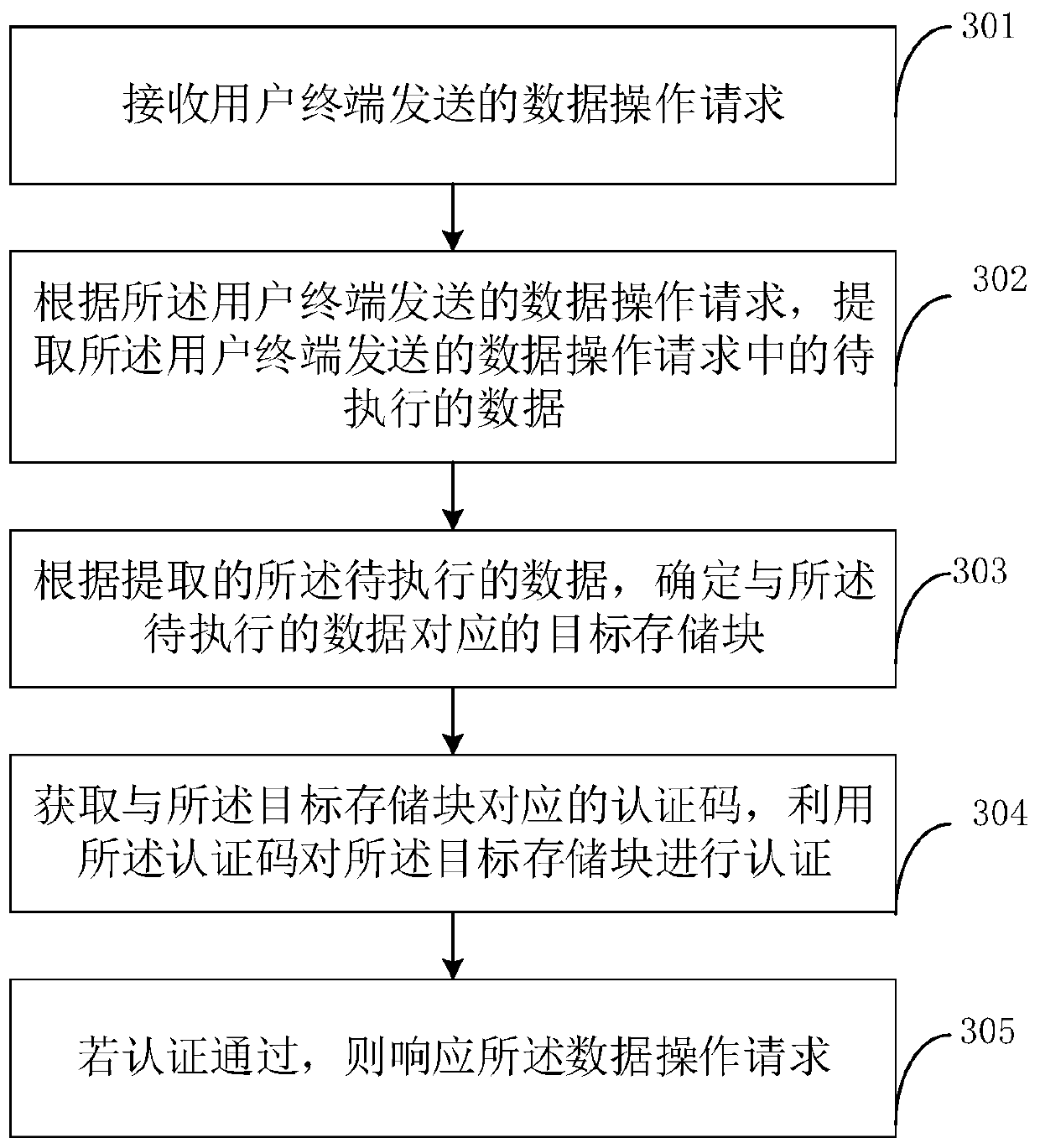
ActiveCN111008389APrevent leakagePrevent illegal tamperingDigital data protectionRedundant operation error correctionFile systemData operations
The invention provides a data processing method and device based on a file system in a satellite. The method comprises the steps of receiving a data operation request sent by a user terminal; extracting to-be-executed data in the data operation request sent by the user terminal according to the data operation request sent by the user terminal; determining a target storage block corresponding to the to-be-executed data according to the extracted to-be-executed data; obtaining an authentication code corresponding to the target storage block, and authenticating the target storage block by using the authentication code; and if the authentication is passed, responding to the data operation request. According to the embodiment of the invention, after the target storage block is determined according to the data operation request, the target storage block is authenticated, and the data operation request is responded after the authentication is passed; and data leakage or illegal tampering is effectively prevented.
Owner:CHENGDU STAR ERA AEROSPACE TECH CO LTD
Multi-tenant authority control method and system
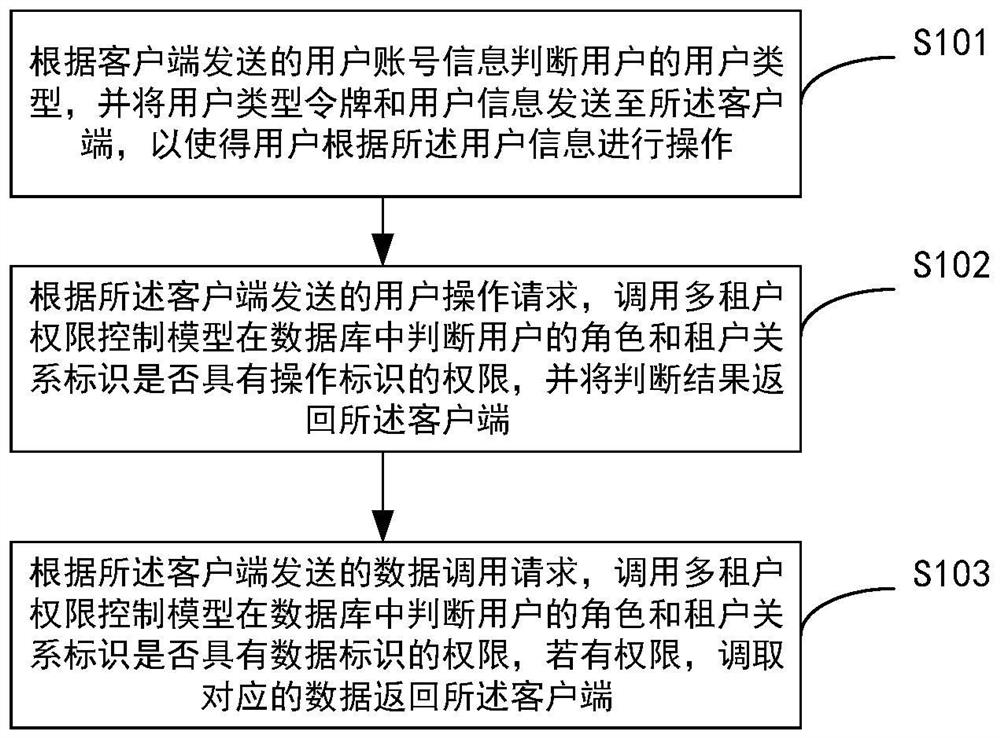
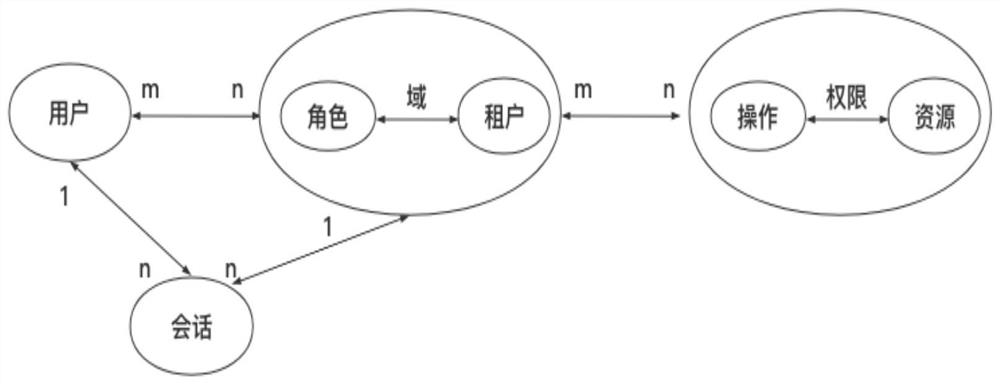
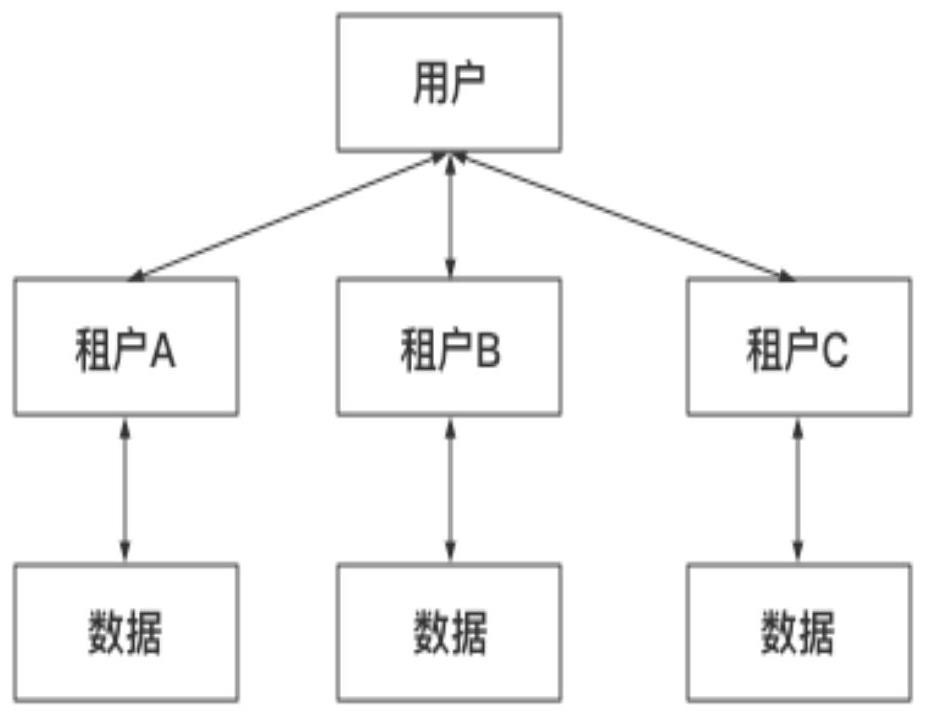
PendingCN114301714AReduce data redundancyAvoid unauthorized operationsUser identity/authority verificationRelationship IdentifierEngineering
The embodiment of the invention discloses a multi-tenant authority control method and system, and the method comprises the steps: judging a user type of a user according to user account information sent by a client, and sending a user type token and user information to the client, so that the user carries out the operation according to the user information; according to a user operation request sent by the client, calling a multi-tenant authority control model to judge whether the role of the user and the tenant relationship identifier have the authority of operating the identifier in a database, and returning a judgment result to the client; and according to a data calling request sent by the client, calling a multi-tenant authority control model to judge whether the role of the user and the tenant relationship identifier have the authority of the data identifier in a database, and if so, calling corresponding data and returning the data to the client. The client and the server can perform multi-permission inspection on user requirements, so that unauthorized operation is prevented, and data redundancy of a database is reduced while security is improved.
Owner:HANGXIAO STEEL STRUCTURE
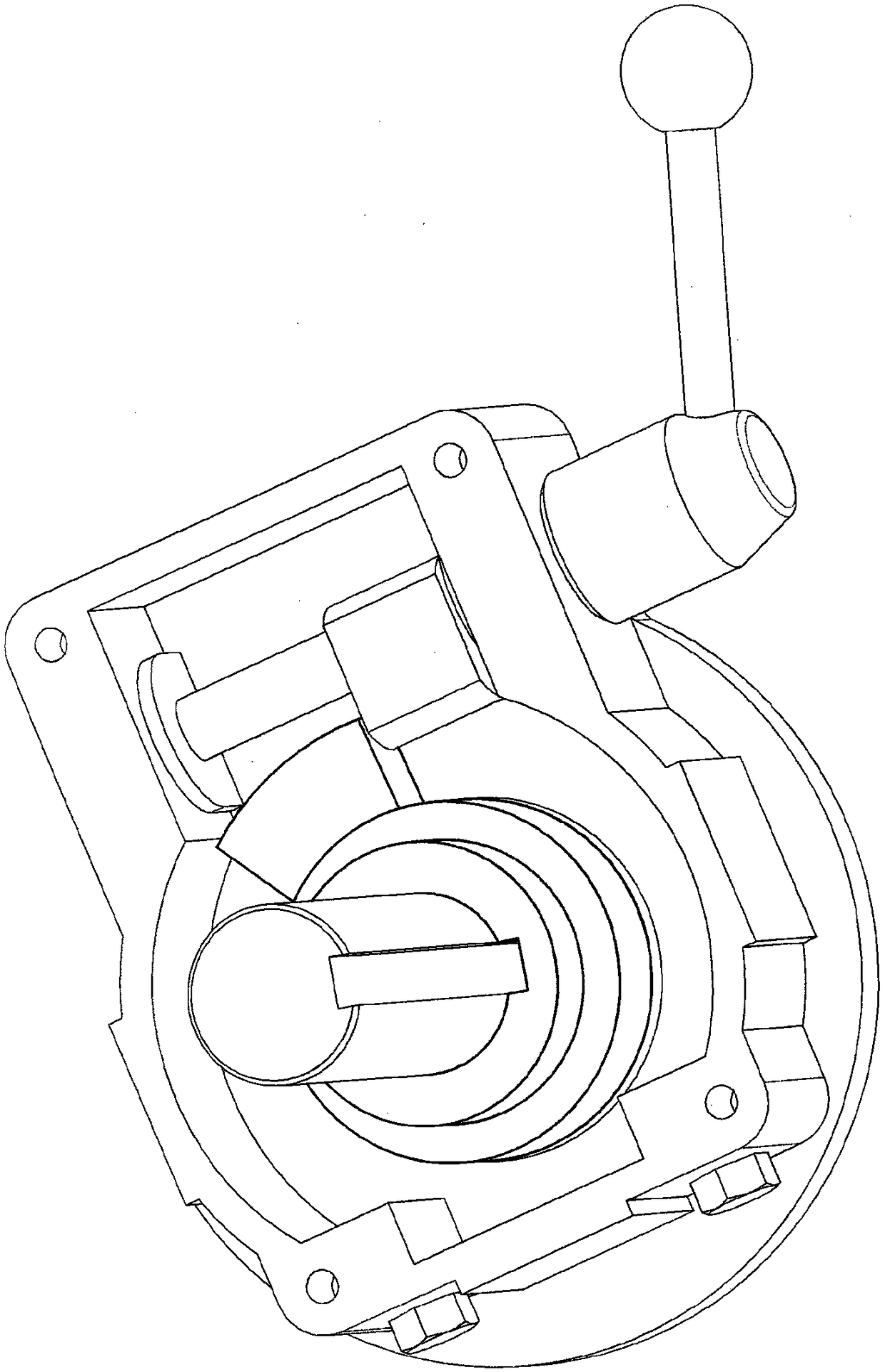
Thread connection device with locking structure
ActiveCN105545106AAvoid unauthorized operationsPuzzle locksPermutation locksEngineeringMechanical engineering
Owner:SHANGHAI SHENGXIANG SCI & TECH
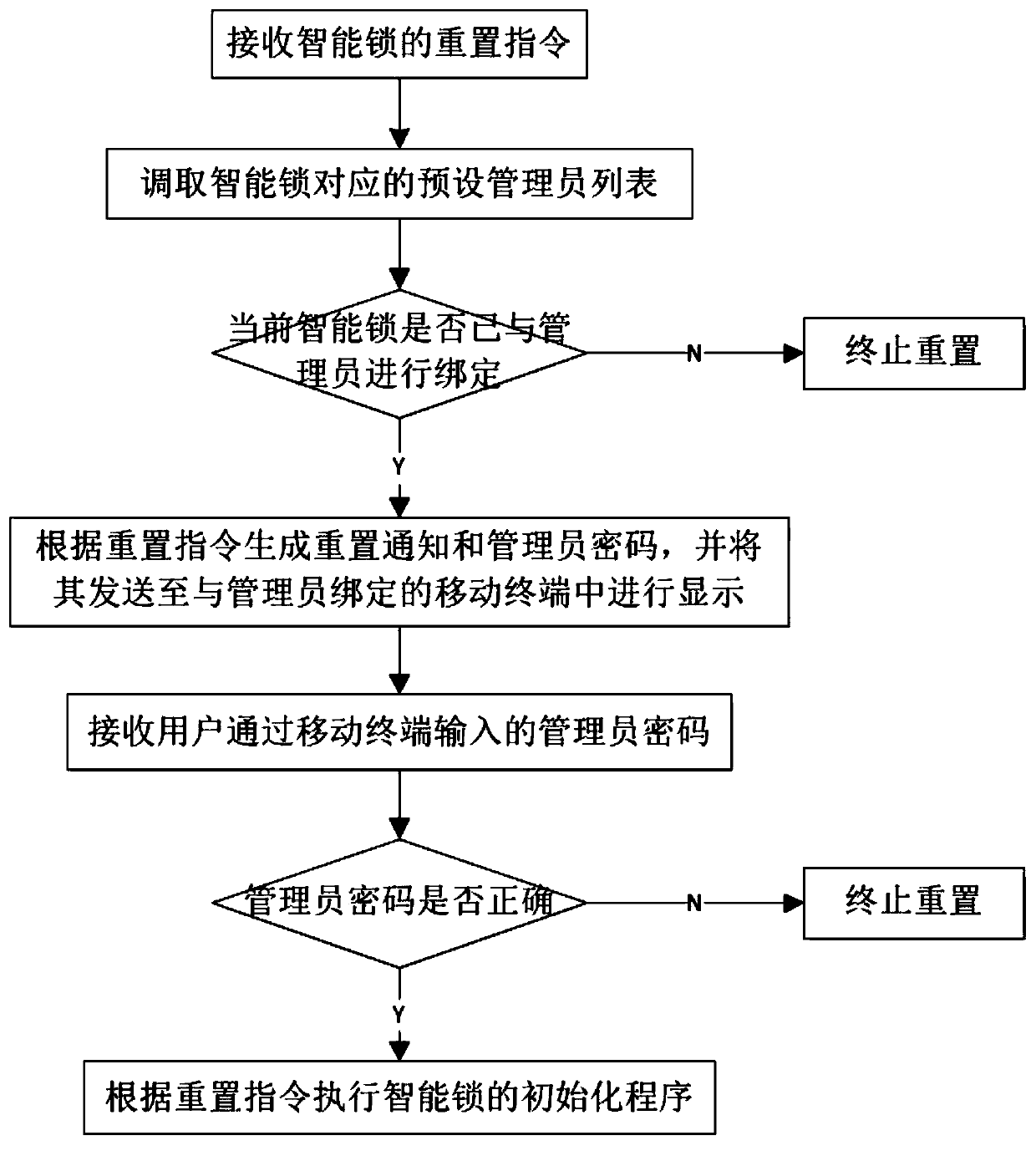
Method and device for safely restoring factory settings of intelligent lock, and storage medium
PendingCN111221580AImprove securityImplement authorized operationsBootstrappingIndividual entry/exit registersRestoration methodOperating system
The invention discloses a safe factory setting restoration method and a device for an intelligent lock, and a storage medium. The restoring method comprises the steps that S1, receiving a reset instruction of the intelligent lock; S2, calling a preset administrator list corresponding to the intelligent lock, judging whether the current intelligent lock is bound with an administrator according to the preset administrator list, and if yes, executing the step S3; if not, stopping resetting; S3, generating a reset notification and an administrator password according to the reset instruction, and sending the reset notification and the administrator password to a mobile terminal bound with an administrator for display; and S4, receiving an administrator password input by the user through the mobile terminal, judging whether the administrator password is correct, and if yes, executing an initialization program of the intelligent lock according to the reset instruction; and if not, stopping resetting. The reset verification step is added, unauthorized operation is prevented, and the safety of the intelligent lock is improved.
Owner:广东好太太智能家居有限公司
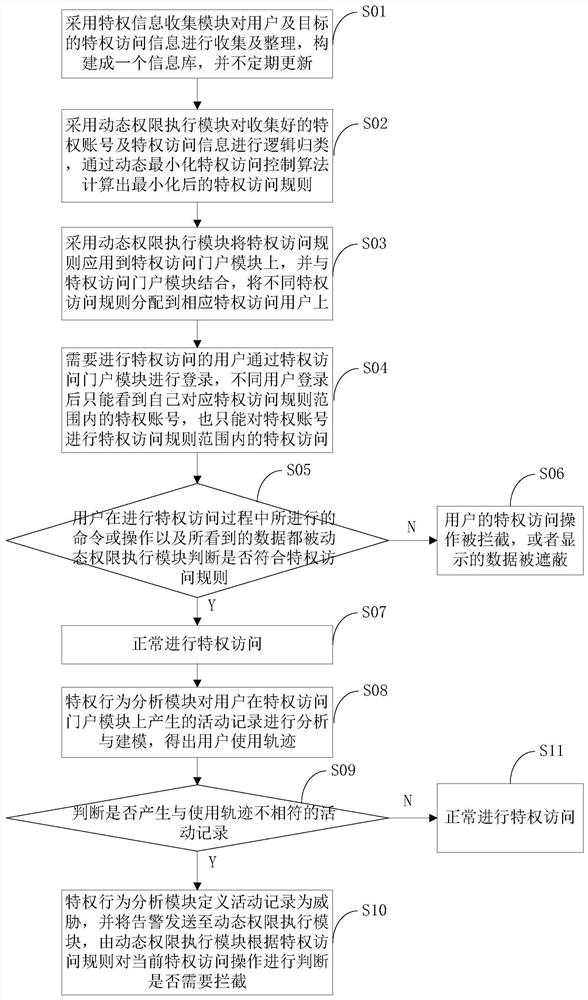
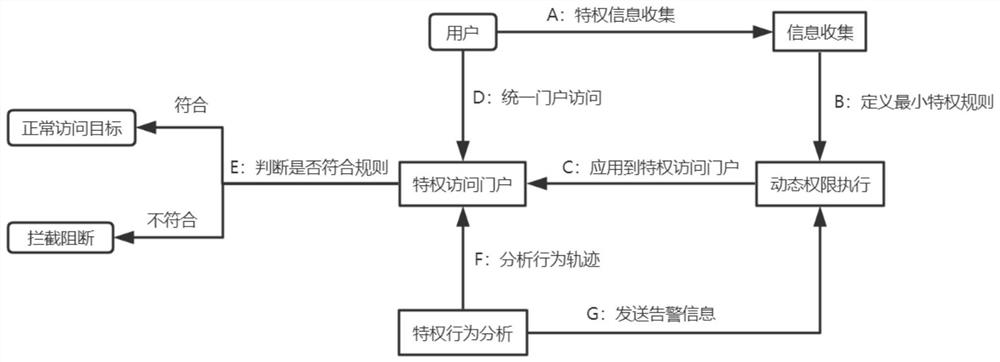
Dynamic minimized privilege access control method and device
PendingCN111800392AAvoid unauthorized operationsCharacter and pattern recognitionTransmissionEngineeringBehavioral analytics
The invention discloses a dynamic minimized privilege access control method and a dynamic minimized privilege access control device. The method comprises the following steps that different privilege access rules are distributed to corresponding privilege access users; after the user logs in, only the privileged account in the corresponding privileged access rule range can be seen, and only the privileged access in the privileged access rule range can be performed on the privileged account; commands or operations carried out in the privilege access process and seen data are judged whether to accord with privilege access rules or not by the dynamic permission execution module; if not, the privileged access operation of the user is intercepted, or the displayed data is shielded; and when an activity record inconsistent with the use track is generated, the privilege behavior analysis module defines the activity record as a threat, and the dynamic permission execution module judges whetherthe current privilege access operation needs to be intercepted or not according to the privilege access rule. According to the invention, related personnel can only carry out privileged access with the minimum permission matched with the personnel, and personnel unauthorized operation is effectively avoided.
Owner:广州海颐信息安全技术有限公司
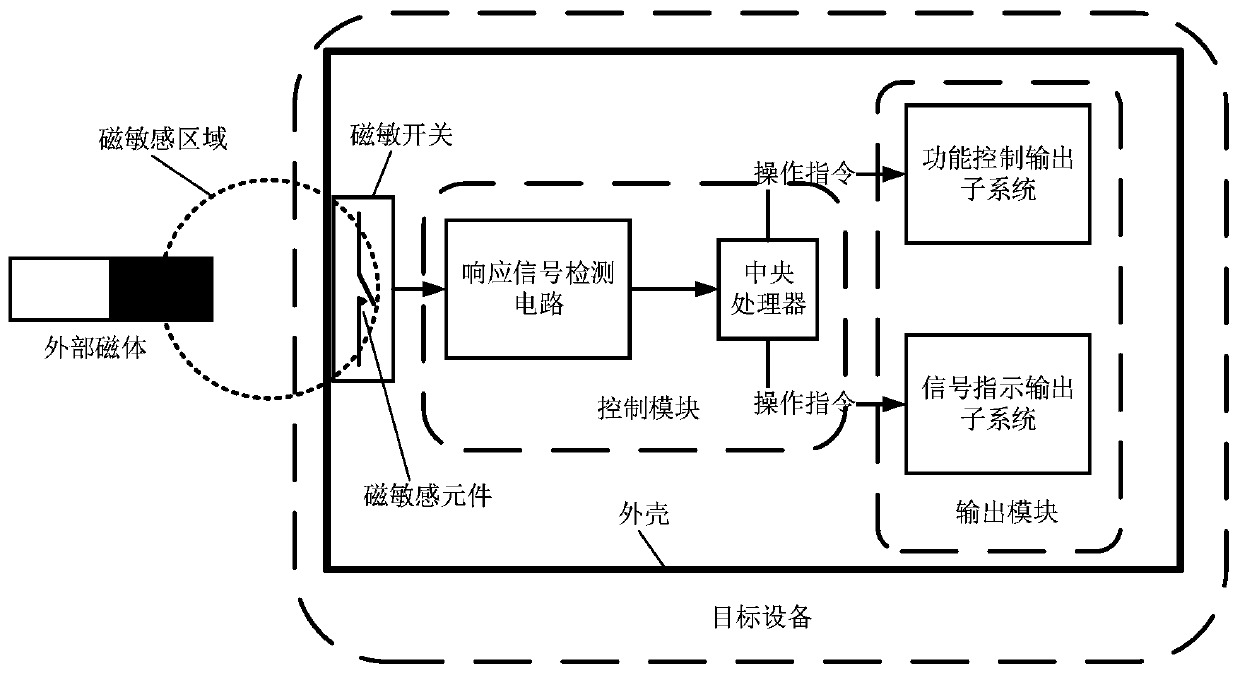
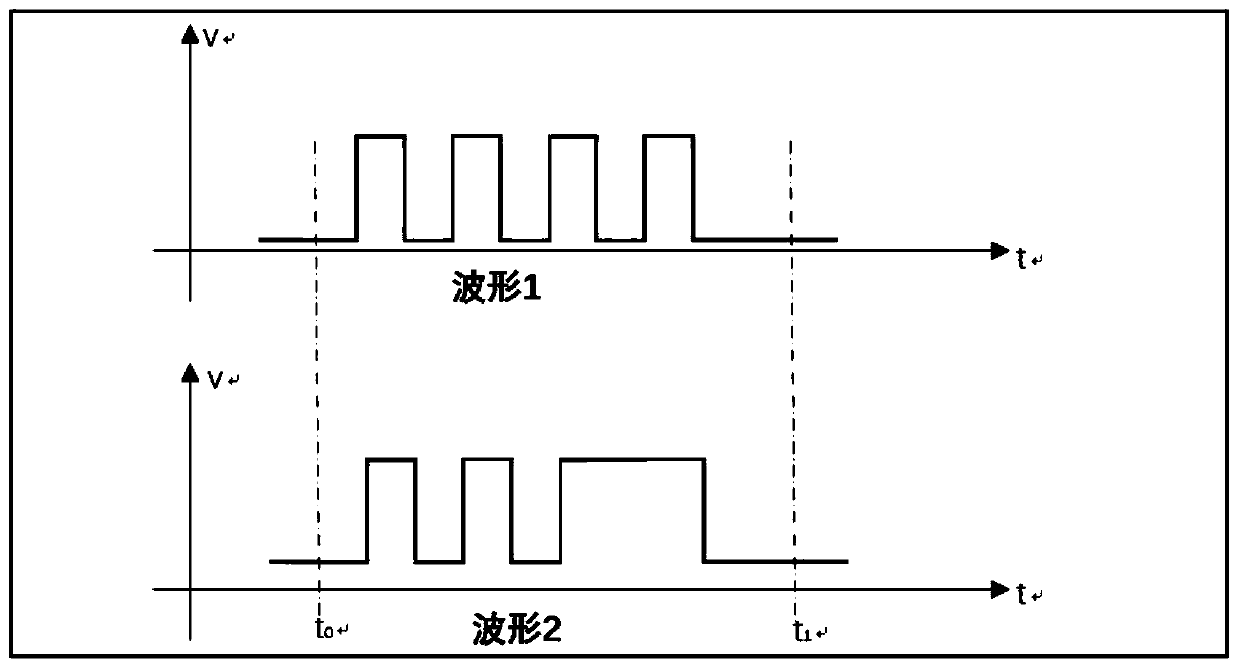
Coding control method based on magnetic sensitivity and switch system
PendingCN110535456AEnsure safe operation of equipmentAvoid misoperation and unauthorized operationElectronic switchingMultifunction keys codingEmbedded systemInstruction code
The invention relates to a coding control method based on magnetic sensitivity and a switching system. Instruction codes of response signal combinations are set through different combinations of frequencies and / or durations of an external magnet entering a magnetic sensitive area, the single magnetic sensitive switch controls the equipment to execute various different operations, holes do not needto be formed in the equipment shell, the leakproofness of the equipment shell can be guaranteed to the maximum extent, and the switching system meets the operation requirements of electronic equipment in specific environments such as sandstorm, moisture or underwater.
Owner:CHINA GEOKON INSTR
NFC passive lock with key authentication function
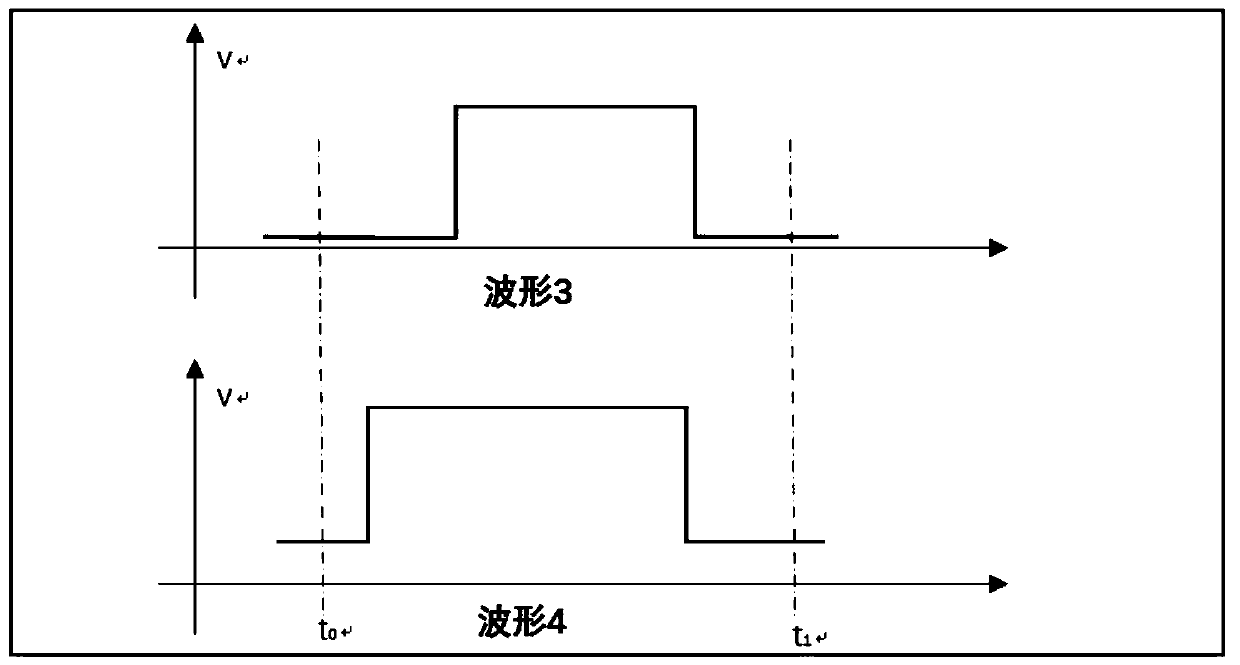
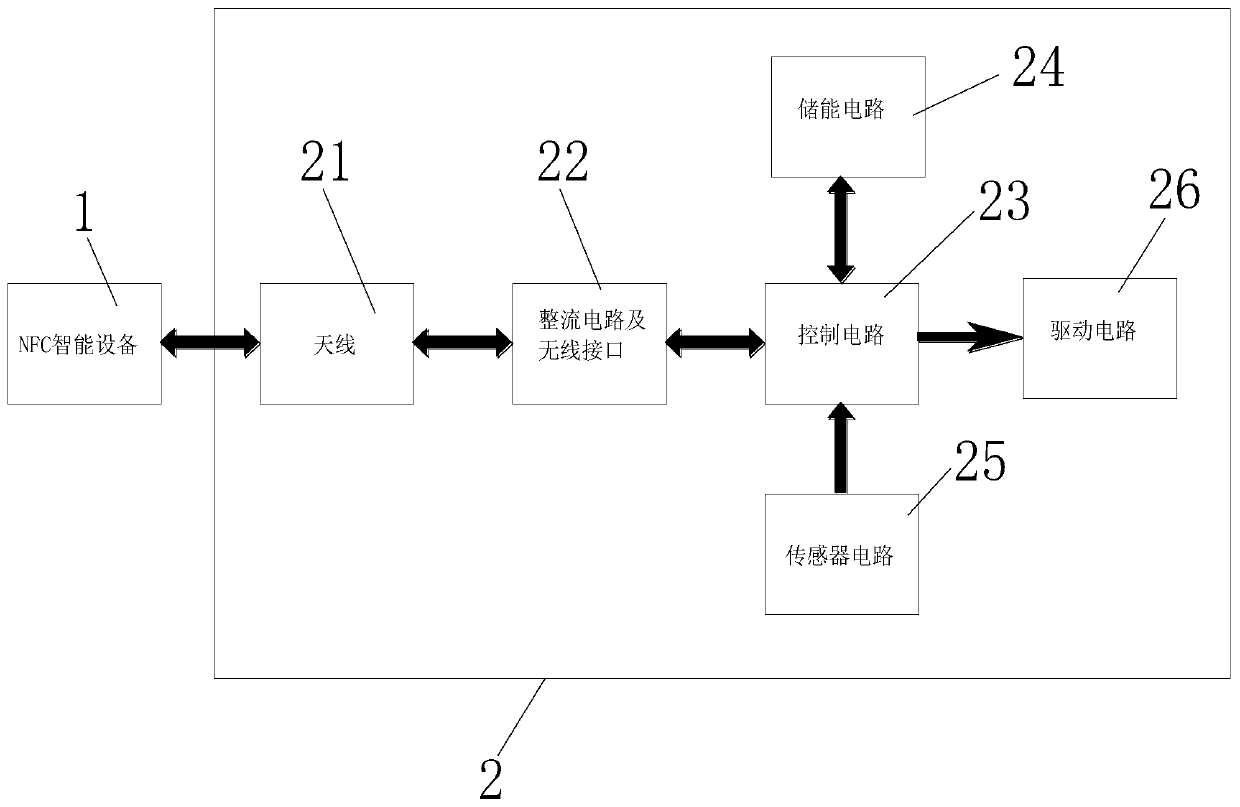
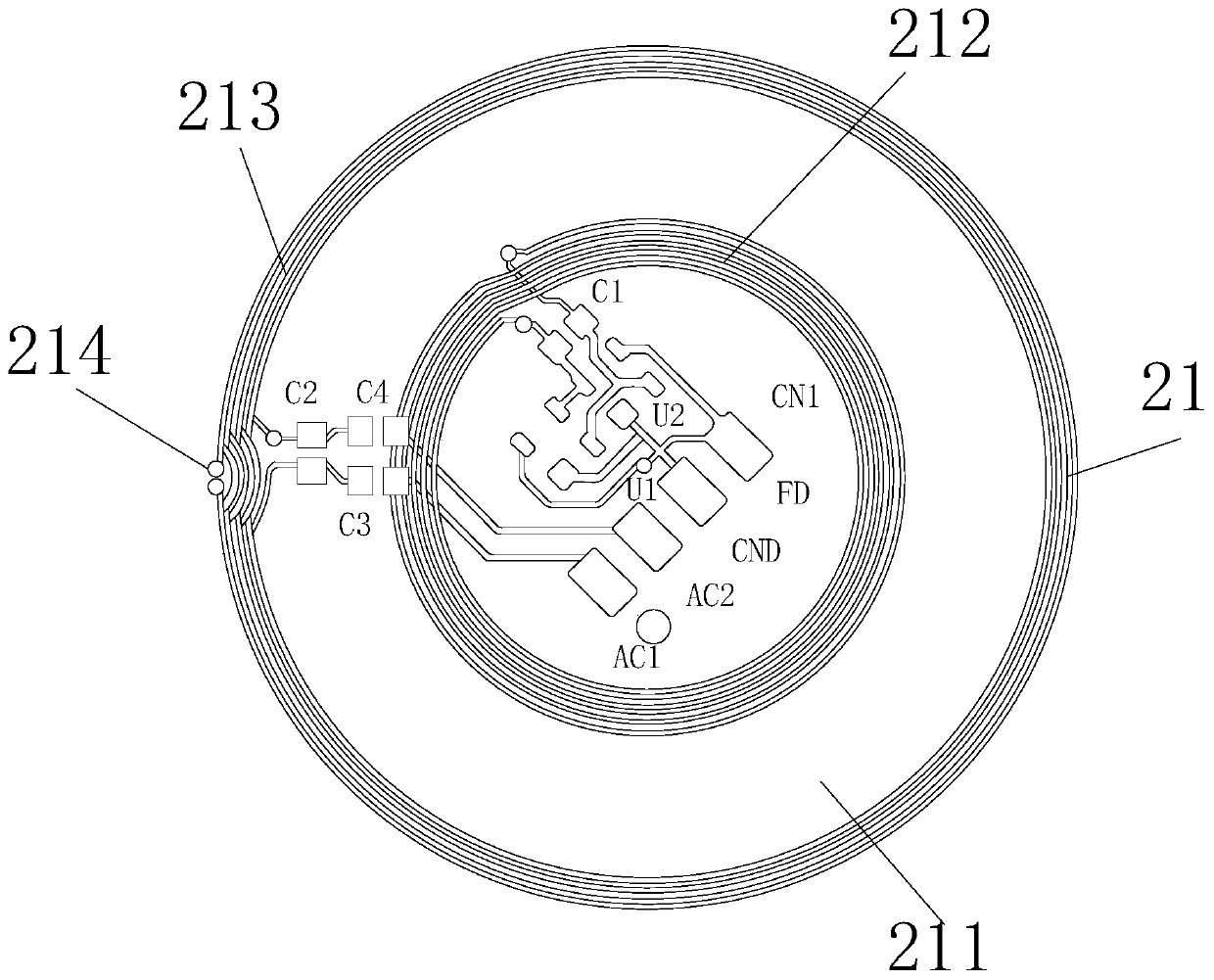
PendingCN110648446AQuick responseImprove experienceDigital data authenticationIndividual entry/exit registersInformation transmissionKey authentication
The invention discloses an NFC passive lock with a key authentication function. The NFC passive lock comprises NFC intelligent equipment and a passive lock circuit. According to the NFC passive lock,through a unique double-sided spiral structure antenna, energy transmission efficiency is greatly improved, and sufficient energy is provided for reliable unlocking by a control circuit; through mutual matching between an energy coil and a tag coil, the energy coil and the tag coil both work in an optimal state, energy transmission and information transmission are performed simultaneously, and reliable control over unlocking is realized; by adding an energy storage circuit, charging cannot be performed unless a rectifying voltage is higher than a certain voltage, tag response is accelerated, and user experience is improved; moreover, key authentication is required for unlocking, unauthorized operation is eradicated, and the NFC passive lock is safer; by adding a sensor circuit, unlocking control and lock state uploading can be accurately performed; and by adopting a special driving circuit for unlocking, reliable unlocking is guaranteed, a background perception function is achieved, whether the lock on site is closed or not is discovered in time, and therefore the NFC passive lock has the advantages of being safe and reliable in unlocking, having a state uploading function and being simple in maintenance in a later period.
Owner:深圳市红芯微科技开发有限公司
Safety protection system of charging pile
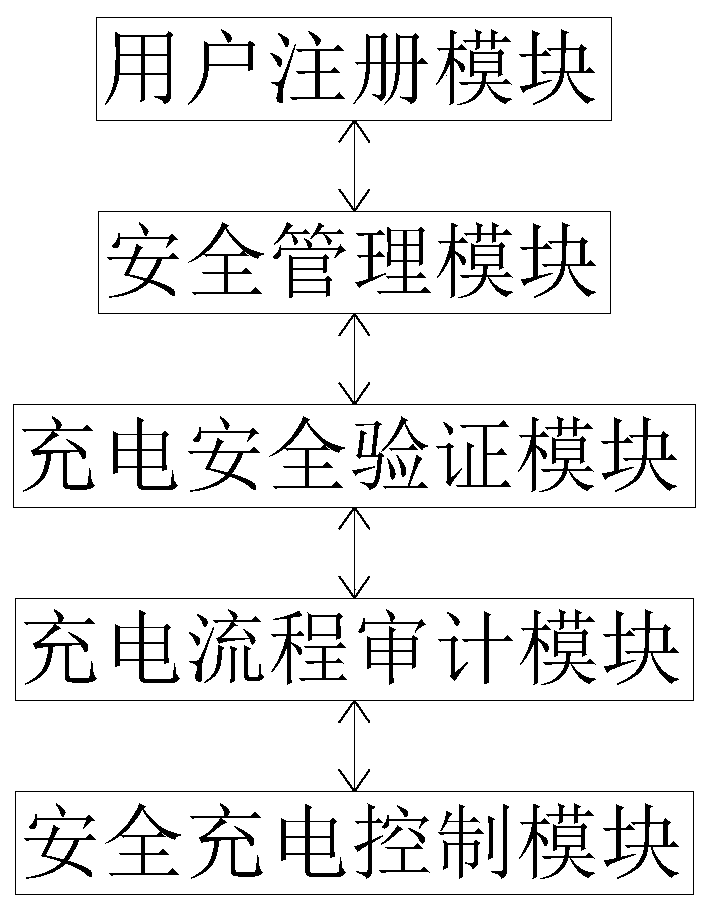
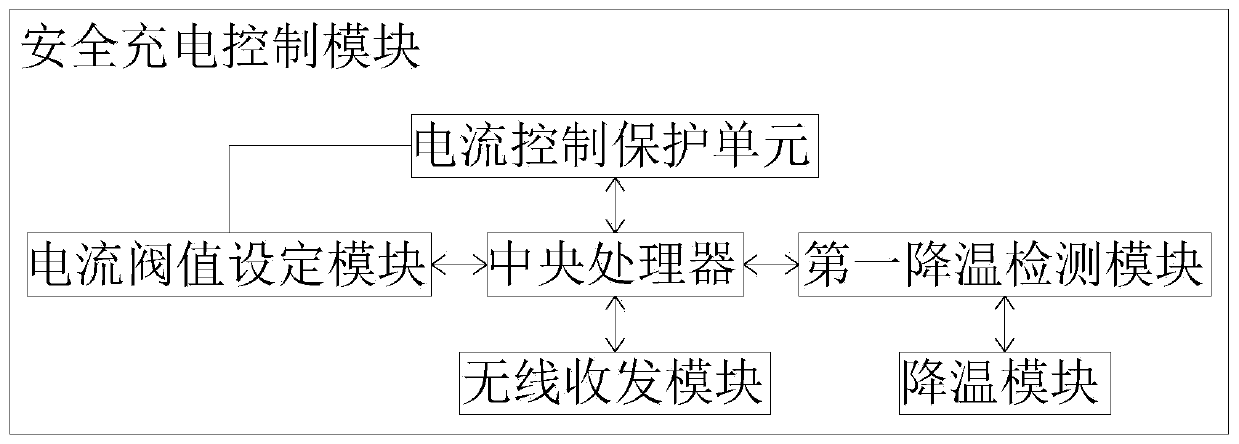
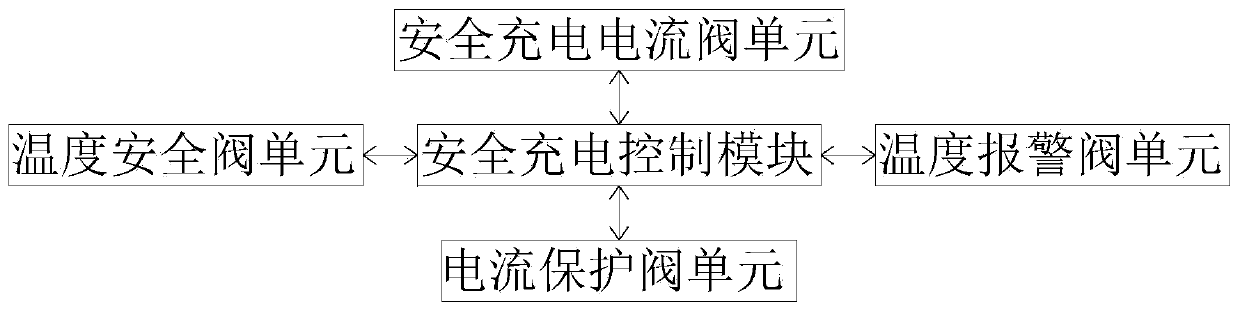
PendingCN111516540AProtect personal rightsPrevent intrusionCharging stationsDigital data protectionCharge controlMobile phone
The invention discloses a safety protection system of a charging pile. The system comprises a user registration module, a safety management module, a charging safety verification module, a charging process auditing module and a safety charging control module; the output end of the user registration module is electrically connected with the input end of the safety management module; and the outputend of the safety management module is electrically connected with the input end of the charging safety verification module. According to the safety protection system of the charging pile, the user registration module, the safety management module, the charging safety verification module and the charging process auditing module which are arranged can be matched to carry out operation protection ona mobile phone APP; and therefore, the malicious behaviors of the APP are monitored in real time, the problems of unauthorized operation and malicious stealing of sensitive information are effectively solved. The safety charging control module is used for carrying out safety protection on a situation in a charging process, so that harm caused by too high temperature generated by short circuit andoverload is effectively avoided, and the safety rights and interests of customers during charging are better protected.
Owner:浙江潮城科技发展有限公司
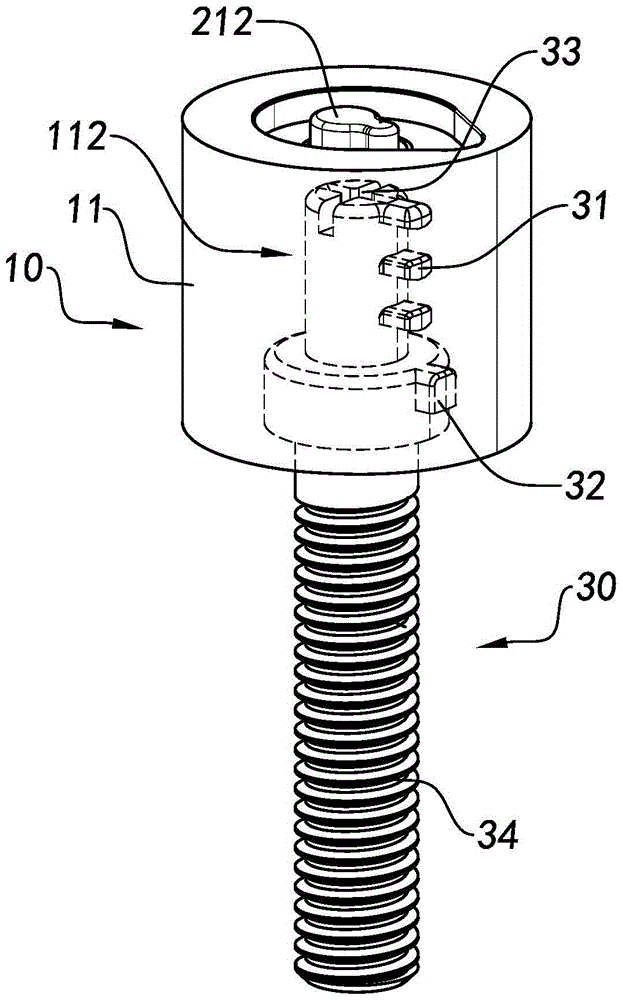
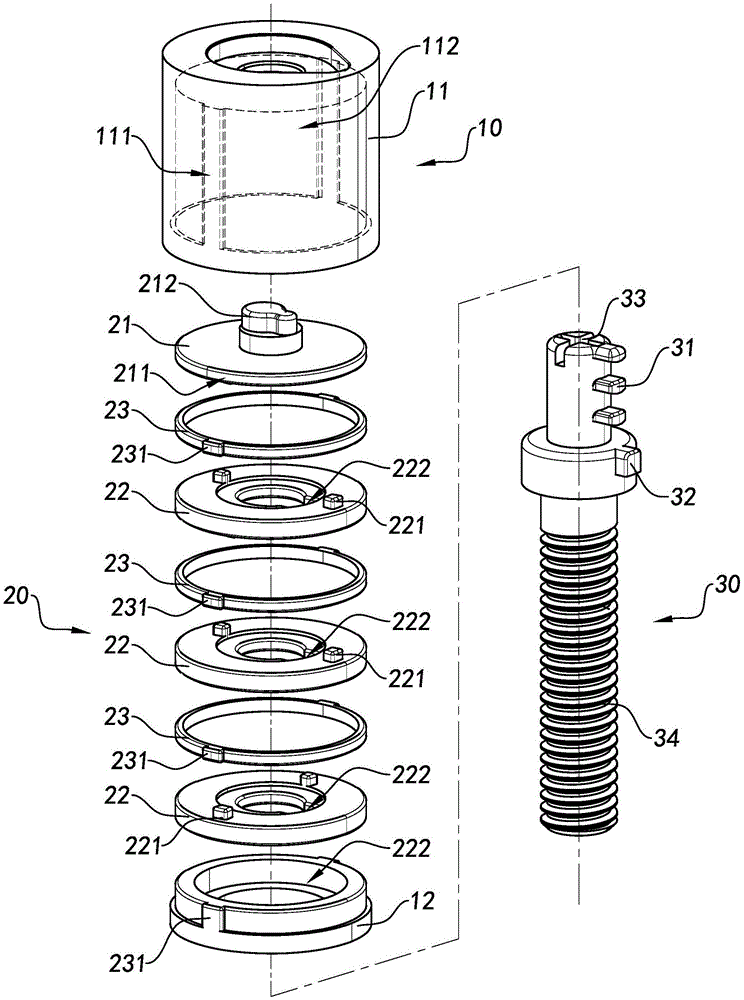
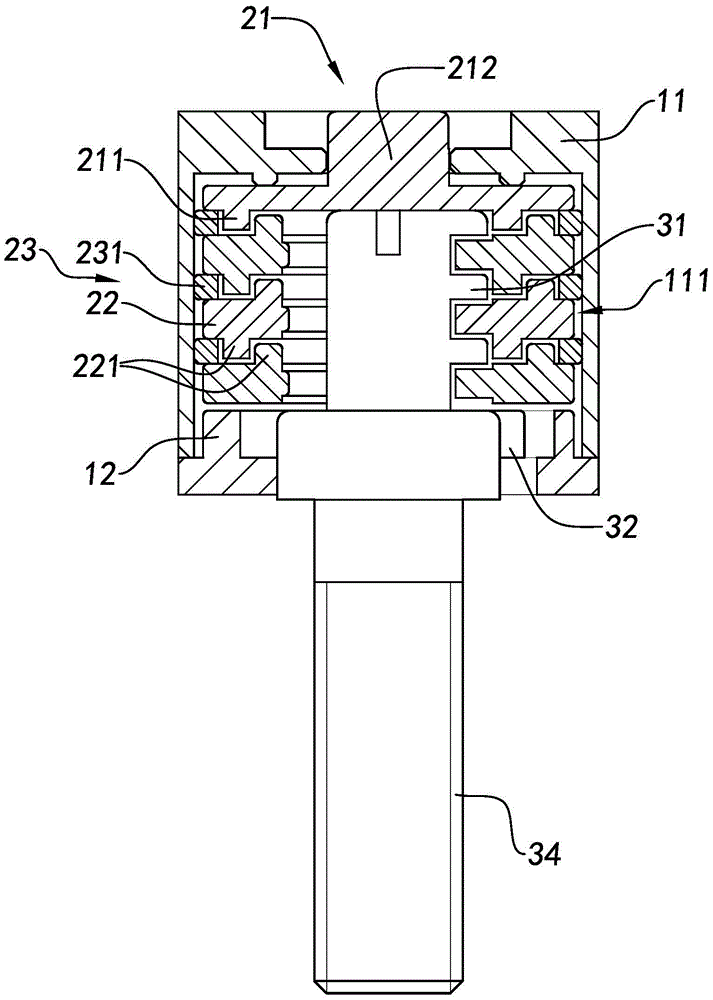
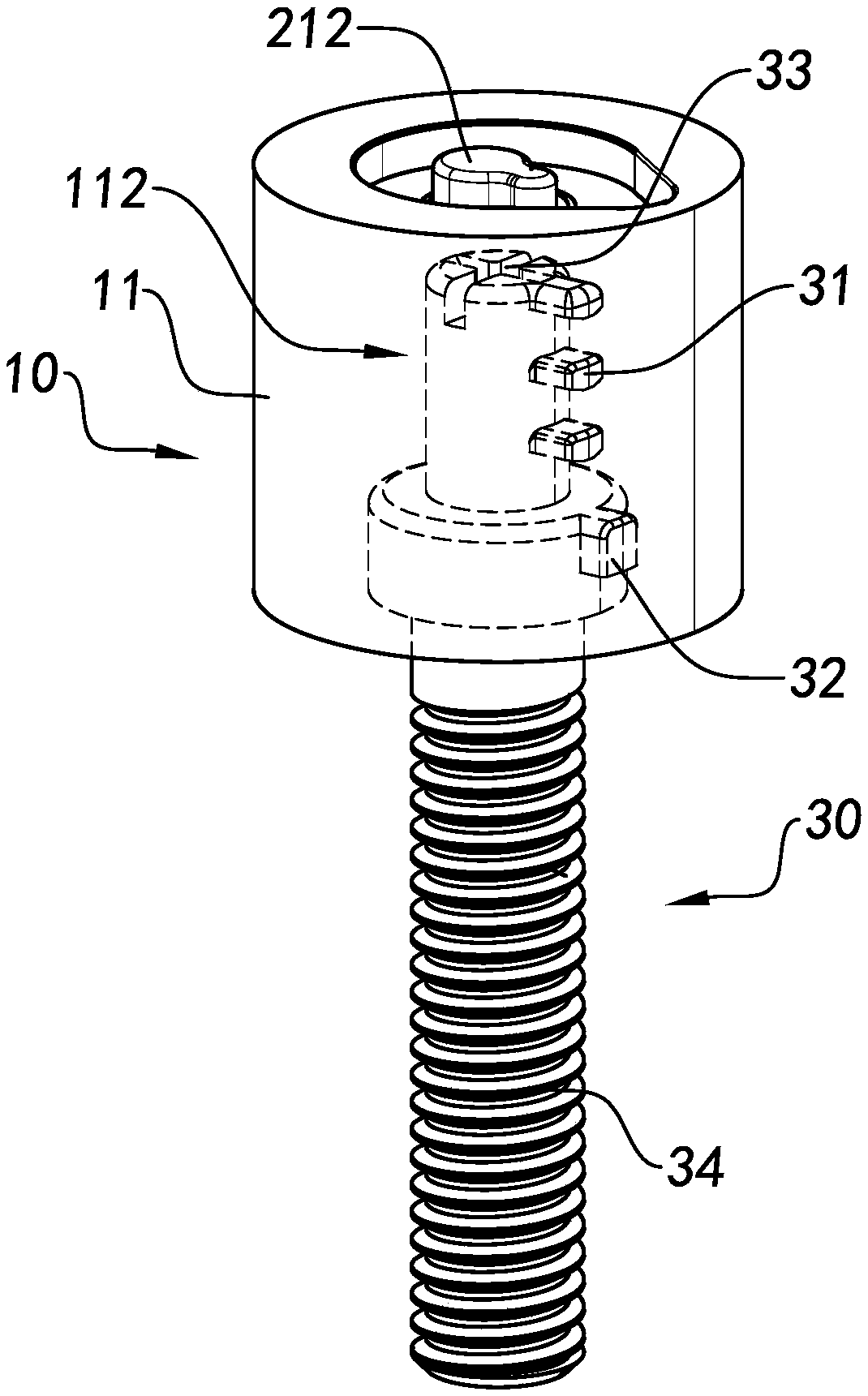
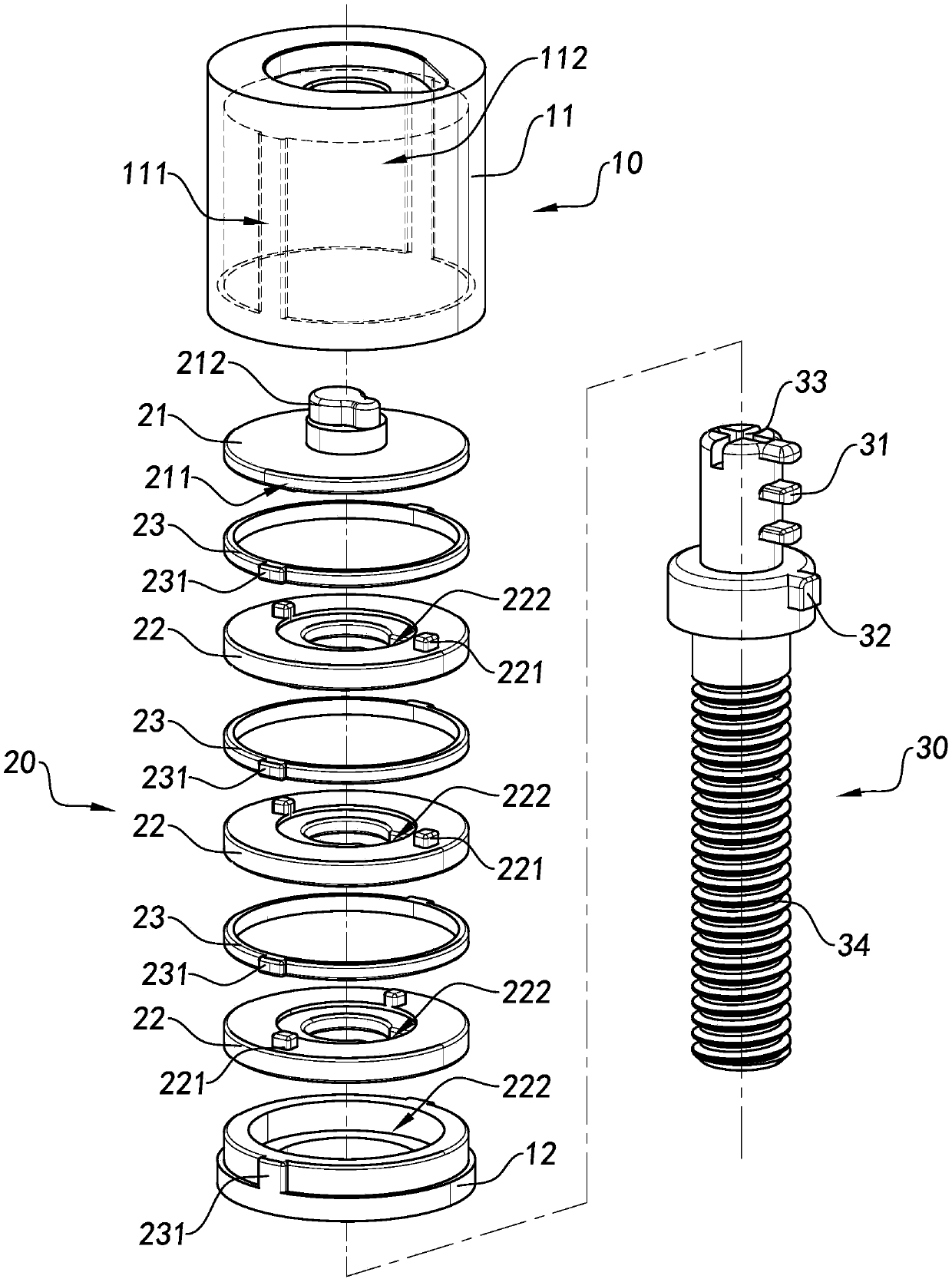
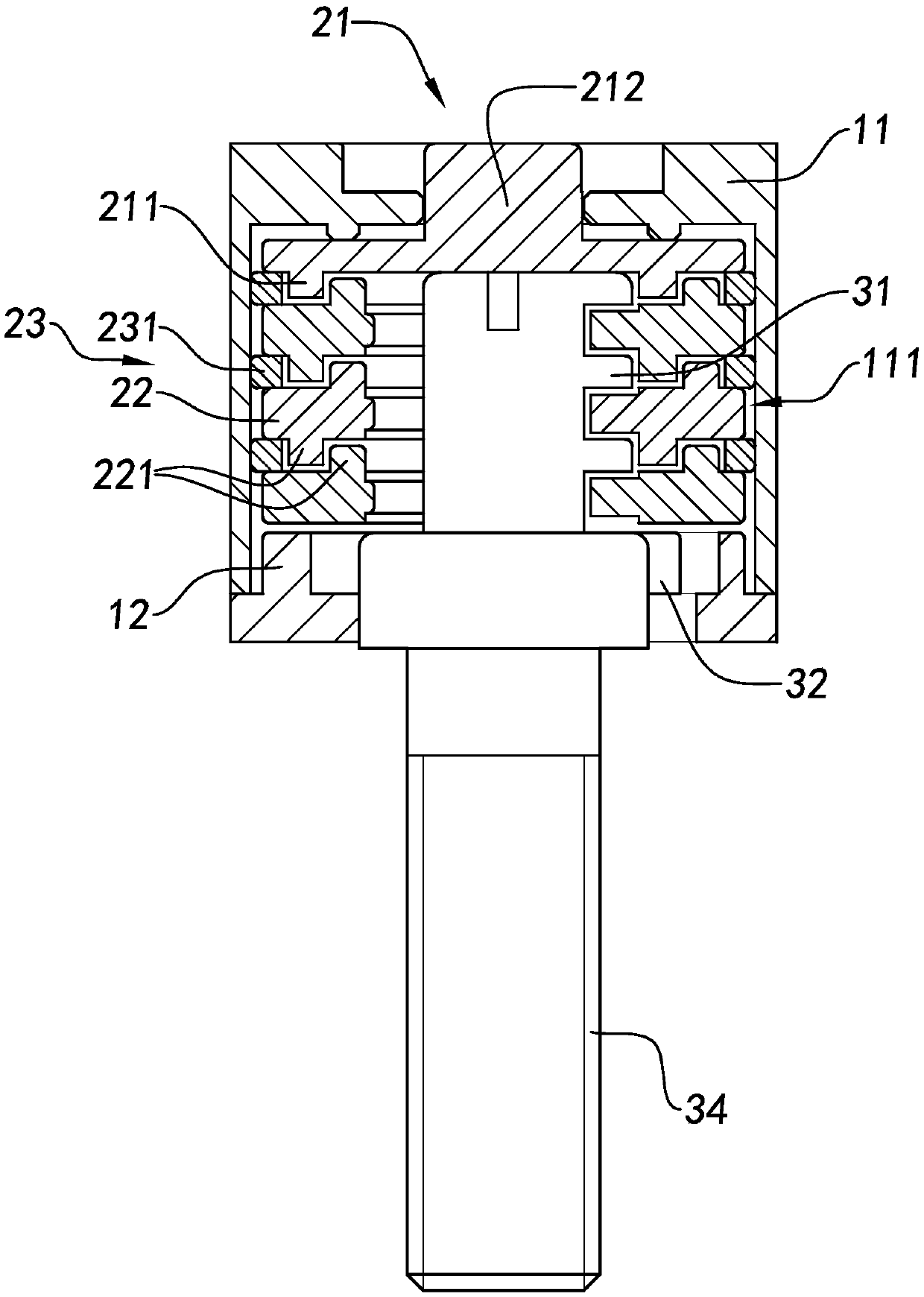
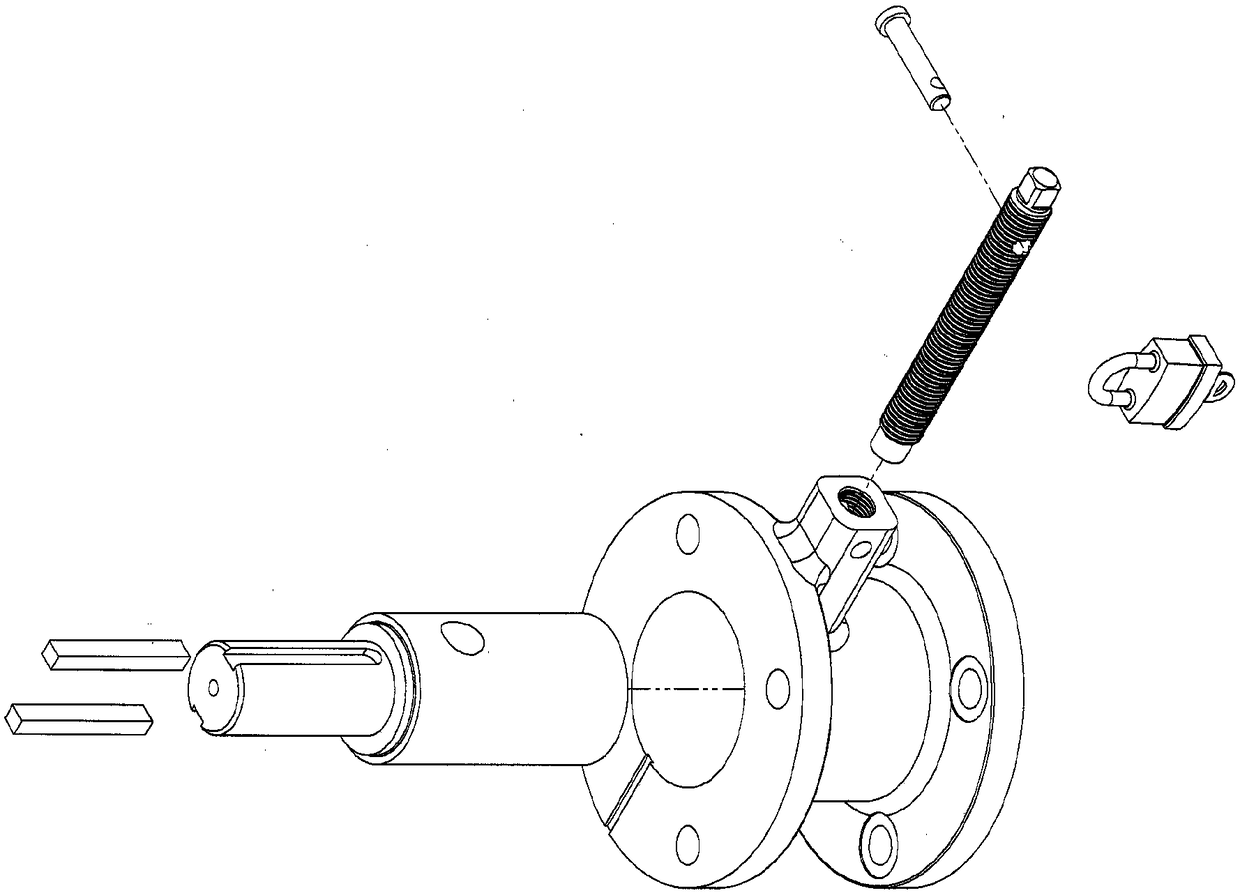
Screw connection with locking mechanism
A screw joint device with a locking structure comprises a locking structure and a screw joint portion (30). The locking structure comprises a lock cylinder (20) and at least one first locking piece (31). The first locking piece (31) is attached to the screw joint portion (30). The lock cylinder (20) has a locking state and an unlocking state. Under the locking state, the first locking piece (31) can stop separation of the lock cylinder (20) from the screw joint portion (30), so as to lock the screw joint portion (30) in an isolating and hiding manner. Under the unlocking state, the lock cylinder (20) slides out along the first locking piece (31), and is separated from the screw joint portion (30), such that the screw joint portion (30) is unlocked.
Owner:SHANGHAI SHENGXIANG SCI & TECH
Lottery ticket machine for preventing from being operated by external input equipment
The invention discloses a lottery ticket machine for preventing from being operated by external input equipment. The lottery ticket machine comprises a main controller, a USB interface module connected with the main controller, and a USB interface driving control module arranged inside the main controller, and also comprises a switching value input and output interface module connected with the main controller, an electronic lock device connected with the switching value input and output interface module, and an electronic key matched with the electronic lock device, wherein a level signal judging module is arranged inside the main controller. The lottery ticket machine for preventing from being operated by the external input equipment can effectively prevent the lottery ticket machine from performing unauthorized operation through the external input equipment in real time, and the safety of the data of the lottery ticket machine is guaranteed.
Owner:北京亚博高腾科技有限公司
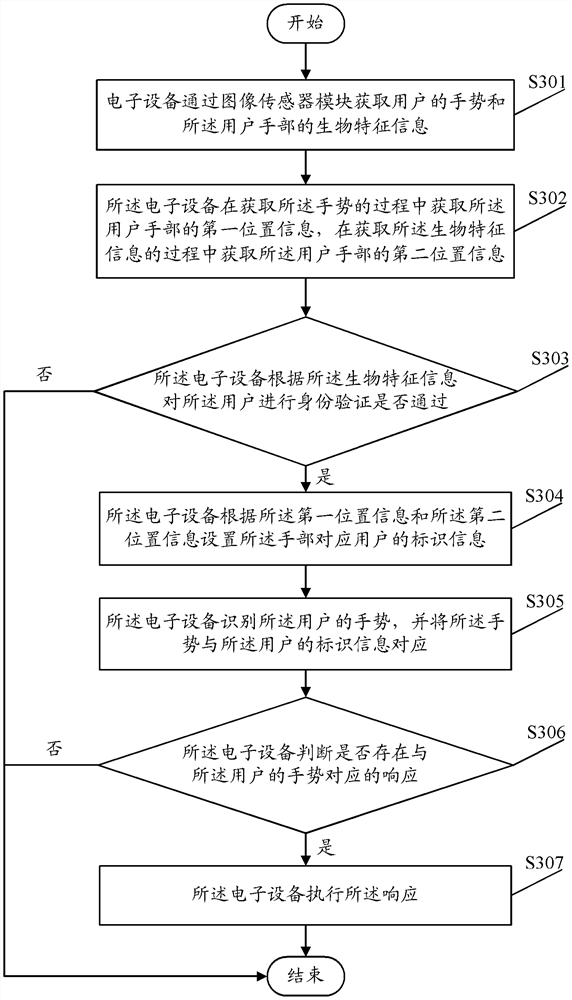
A gesture recognition method, device and electronic device
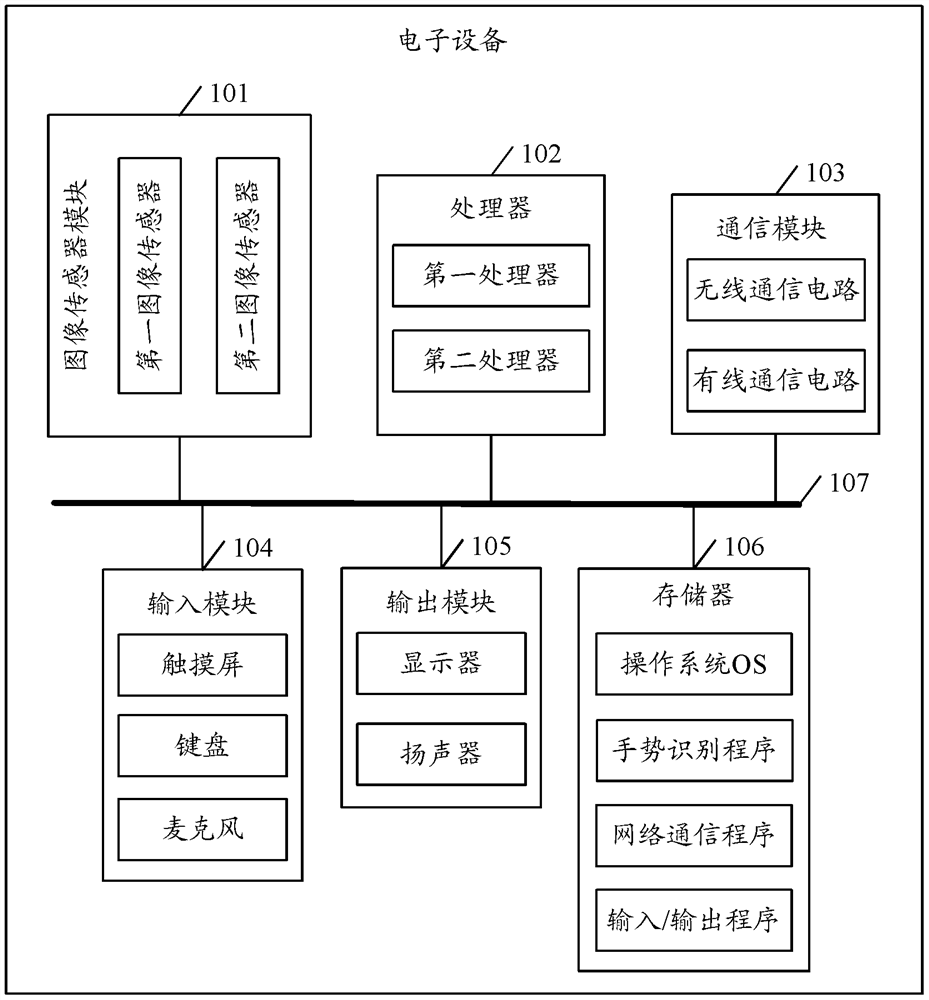
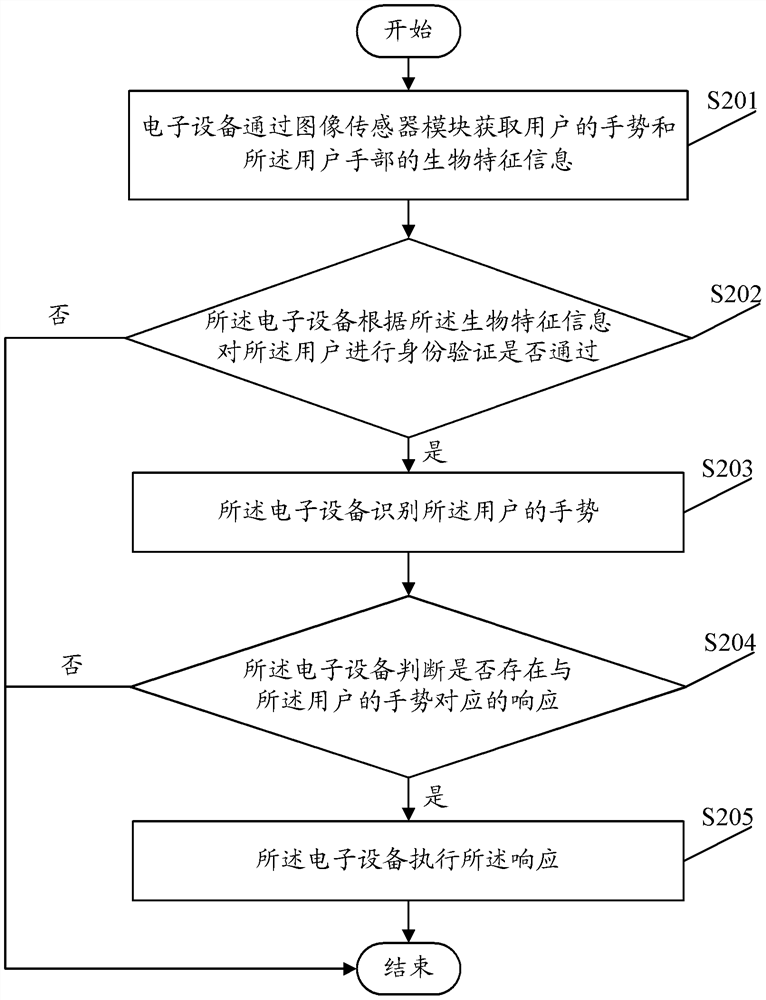
ActiveCN107533599BAvoid unauthorized operationsOrderly executionDigital data authenticationInput/output processes for data processingMedicineEngineering
Disclosed are a gesture recognition method and apparatus, and an electronic device. The method comprises: acquiring a gesture of a user and biological feature information about a hand of the user by means of an image sensor module; performing identity verification on the user according to the biological feature information; if the verification is passed, recognizing the gesture of the user; then determining whether a response corresponding to the gesture of the user exists; and if so, executing that response. By means of the present invention, a false trigger rate of a gesture operation can be reduced.
Owner:HUAWEI TECH CO LTD
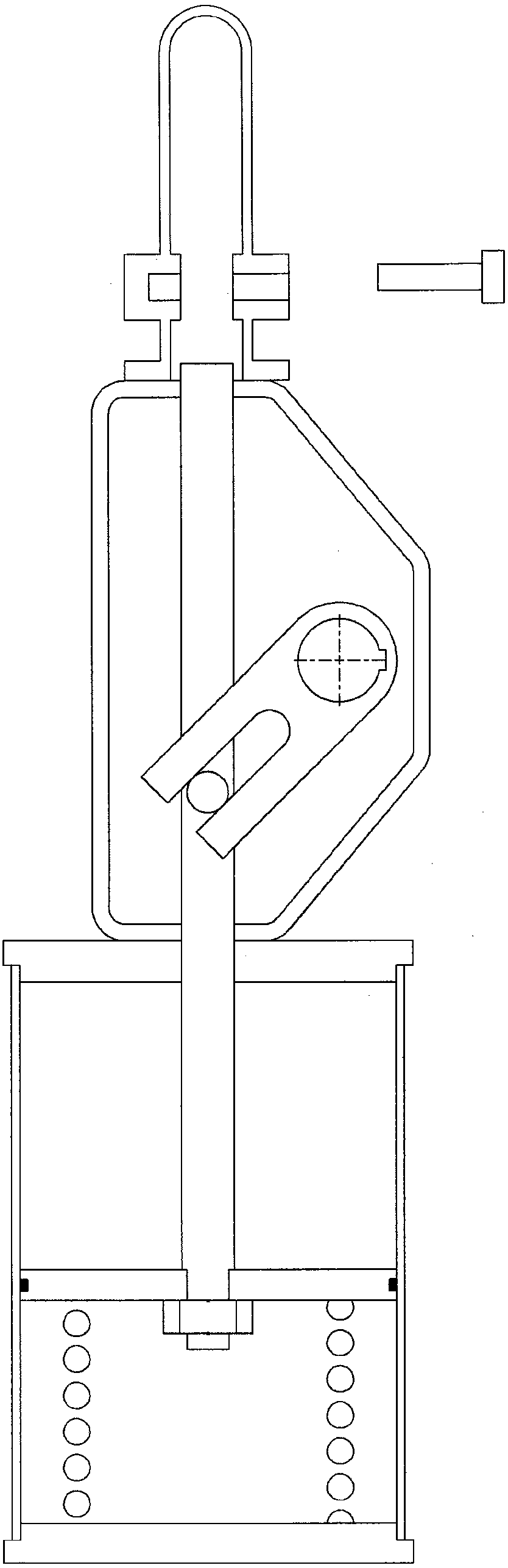
Combination device for lockout and partial stroke test of valve actuators
ActiveCN108138986AAvoid unauthorized operationsFluid-pressure actuator testingOperating means/releasing devices for valvesLinear motionValve actuator
A combination device (102) configured to effect lockout and partial stroke testing for an actuator having a piston rod (104) providing linear motion and connected to a guide block (108) in an actuator, wherein the combination device includes a device housing (102a) having a housing bore, wherein the device housing is adapted to mount on a receptacle on the actuator that aligns a device housing bore coaxially to the translatory motion axis of the piston rod; an extension rod (109) adapted to be attached to the guide block connected to the piston rod; at least two slides or a profiled bore indexsleeve (106) disposed in the device housing that when engaged provide means of restraining the movement of the extension rod in a manner that prevents said extension rod from moving and, in use, a driver element of the actuator from rotating relative to an actuator housing; a housing cover mounted over the device housing wherein the housing cover protects and retains the extension rod, and the slides or the index sleeve in the device housing and a spring biased safety pin mounted on the housing cover wherein the spring biased safety pin is configured to prevent unintended actuation of the actuator; and a tubular cover to protect the extension rod.
Owner:BRAY INT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com