Security protection method specific to unauthorized access
An unauthorized access and security prevention technology, applied in the field of enterprise security, can solve the problems of increasing code complexity and coding workload, inconsistent user permissions in the front and back ends, and users being unable to use it, so as to reduce the authorized workload and improve code readability. The effect of reducing code workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
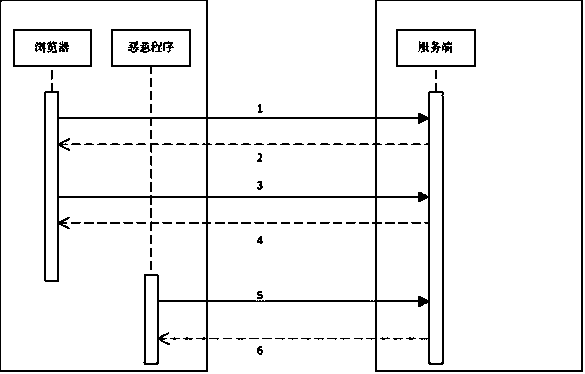
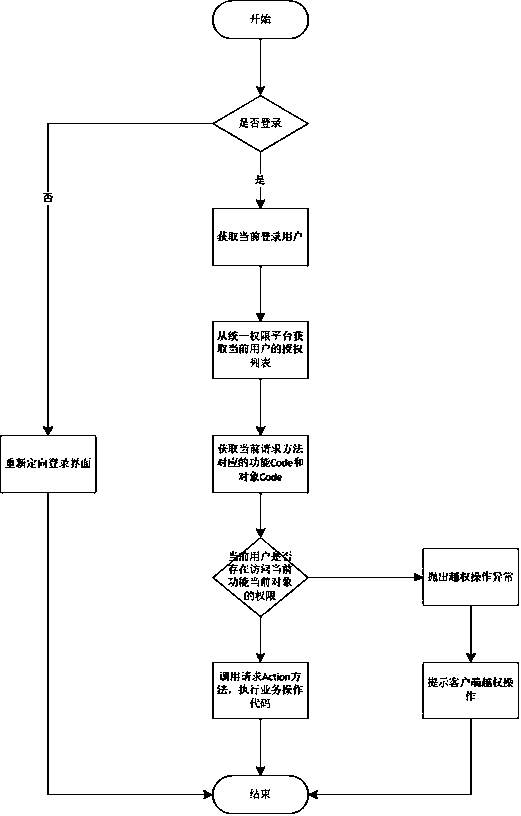
[0030] A security precaution against unauthorized access, figure 2 It is the implementation schematic diagram of the present invention. The method includes the following steps:
[0031] 1) Determine whether the user is logged in according to the session information of the server. If not logged in, turn to the login interface; if logged in, further check the authority.
[0032] 2) Obtain the login information of the current user from the server session.
[0033] 3) According to the login information of the current user, obtain the permission list that the current user can access from the permission platform, including which menus and which buttons of those menus.
[0034] 4) According to the annotation (Annotation) of the Action method requested by the user, obtain the menu Code and button Code corresponding to the request.
[0035] 5) Check whether the menu Code and button Code requested by the user are in the user's authorization list, if so, pass the authorization check,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com