Authority list security control method
A technology of security control and authority, applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of authority list loopholes, no security control means, etc., to improve encryption, ensure uniqueness, and avoid possibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
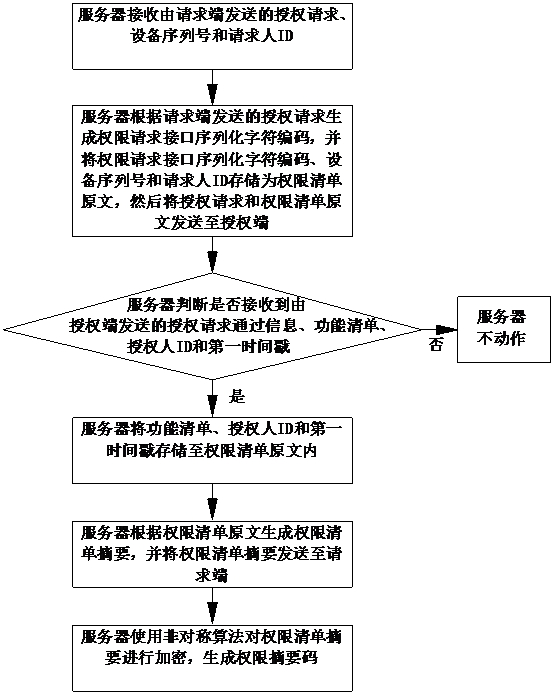
[0042] This embodiment provides a permission list security control method, such as figure 1 As shown, including the rights list encryption method, the rights list encryption method includes the following steps:
[0043] The server receives the authorization request, device serial number and requester ID sent by the requesting end;
[0044] The server generates the serialized character code of the permission request interface according to the authorization request sent by the requesting end, and stores the serialized character code of the permission request interface, device serial number and requester ID as the original text of the permission list, and then sends the authorization request and the original text of the permission list to authorized end;
[0045] The server judges whether the authorization request information, function list, authorizer ID and first time stamp sent by the authorizer are received; if so, the server stores the function list, authorizer ID and first...
Embodiment 2
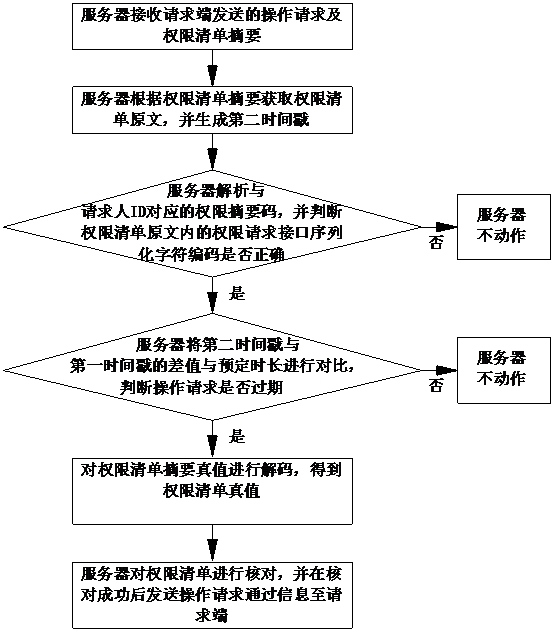
[0052] This embodiment provides a permission list security control method, such as figure 1 As shown, including the rights list encryption method, the rights list encryption method includes the following steps:
[0053] The server receives the authorization request, device serial number and requester ID sent by the requesting end;
[0054] The server generates the serialized character code of the permission request interface according to the authorization request sent by the requesting end, and stores the serialized character code of the permission request interface, device serial number and requester ID as the original text of the permission list, and then sends the authorization request and the original text of the permission list to authorized end;
[0055] The server judges whether the authorization request information, function list, authorizer ID and first time stamp sent by the authorizer are received; if so, the server stores the function list, authorizer ID and first...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com