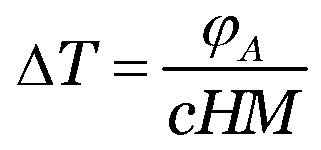Patents
Literature
151results about How to "Avoid parsing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
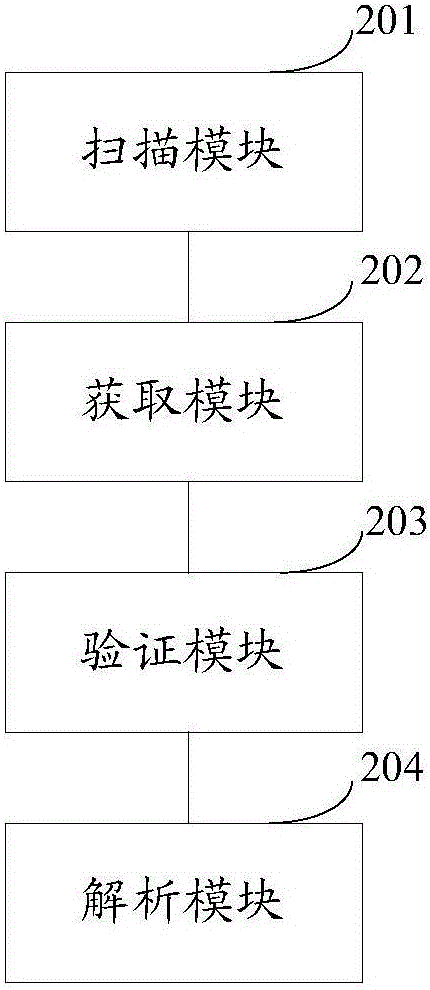
Method and device for analyzing DNS and browser
ActiveCN103561121AImprove the odds of successImprove experienceTransmissionSpecial data processing applicationsDomain nameIp address
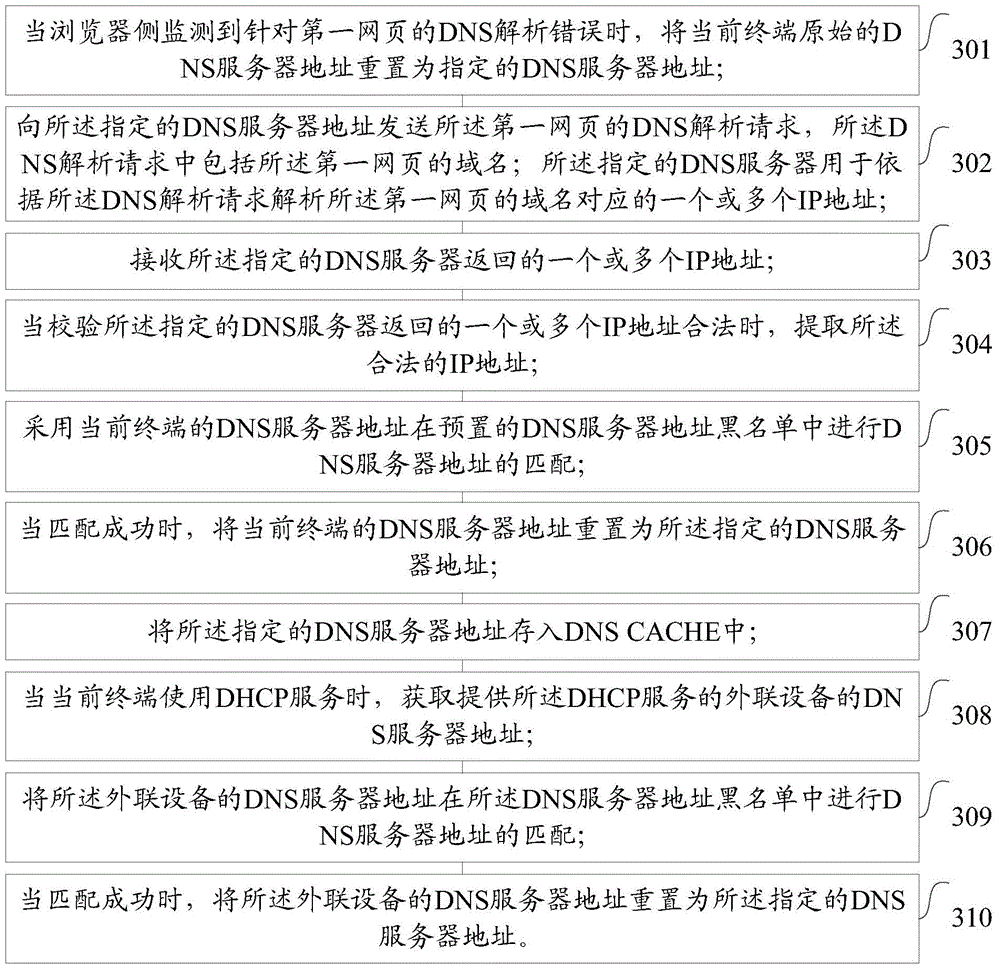
The invention discloses a method for analyzing a DNS. The method for analyzing the DNS comprises the steps that when a browser side monitors that DNS analysis of a first webpage is wrong, an original DNS address of a current terminal is reset to be an appointed DNS address; a DNS analysis request of the first webpage is sent to the appointed DNS address, wherein the domain name of the first webpage is included in the DNS analysis request; an appointed DNS is used for analyzing one or more IP addresses corresponding to the domain name of the first webpage according to the DNS analysis request; the IP addresses returned by the appointed DNS are received; when it is ensured that the IP addresses returned by the appointed DNS are legal through verification, the legal IP addresses are extracted. The probability of successful DNS analysis can be greatly increased, and user experience is improved.
Owner:三六零数字安全科技集团有限公司
Web service mapping method and system of security agent in virtual private network (VPN)
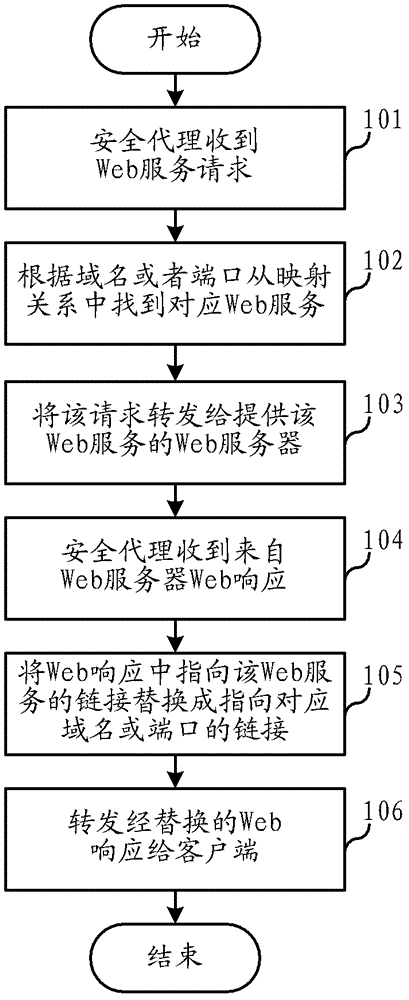
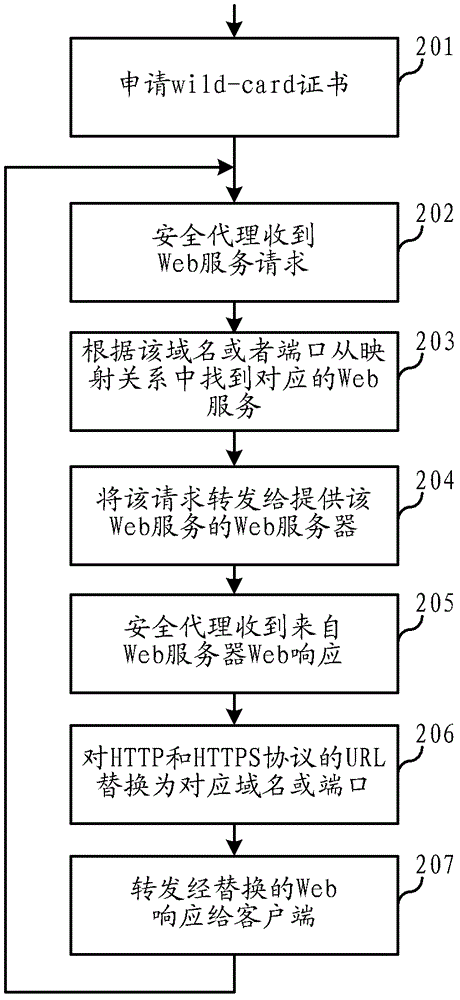
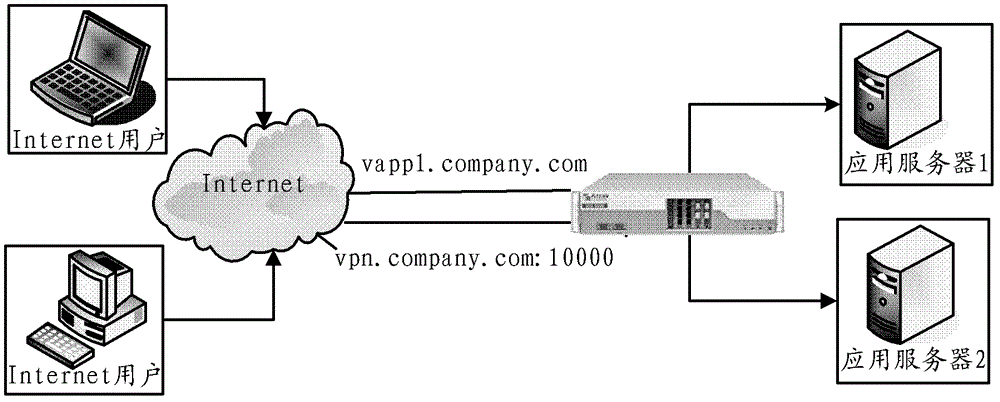
The invention relates to the field of communications, and discloses a web service mapping method and a system of a security agent in a virtual private network (VPN). Web response analysis and rewriting processes are simplified, achieving is easy, and stability and efficiency are high. In the web service mapping method and the system of the security agent in the VPN, the mapping relation of a domain name or a port which supplies web services and security agents is preset by the security agent in the VPN, wherein different web services correspond to different domain names or different ports. When the security agent receives a web service request from a client terminal, a corresponding web service is found from the mapping relation according to the domain name in the request or the port which receives the request, and the request is forwarded to a web server which supplies the web service. When the security agent receives a web response from the web server, according to the mapping relation, chaining which points to the web service in the web response is replaced by chaining which points to a corresponding domain name or a corresponding port of the security agent, and then the replaced web response is forwarded to the client terminal.
Owner:ARRAY NETWORKS BEIJING
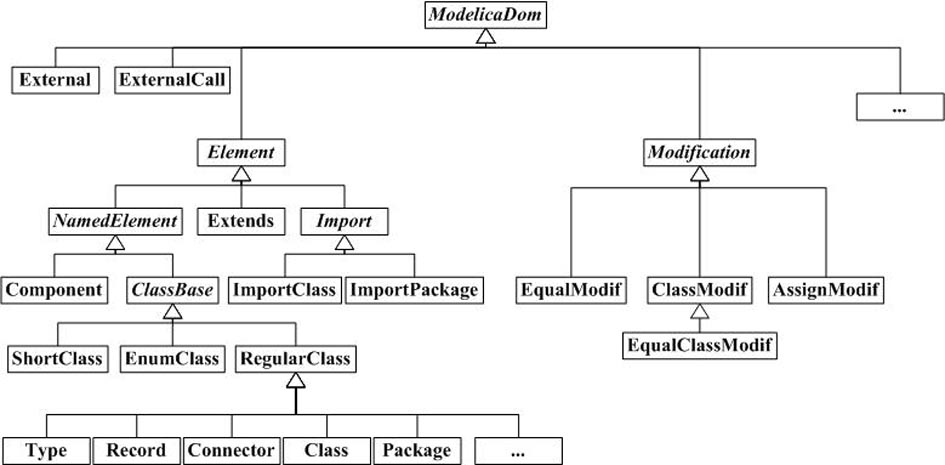
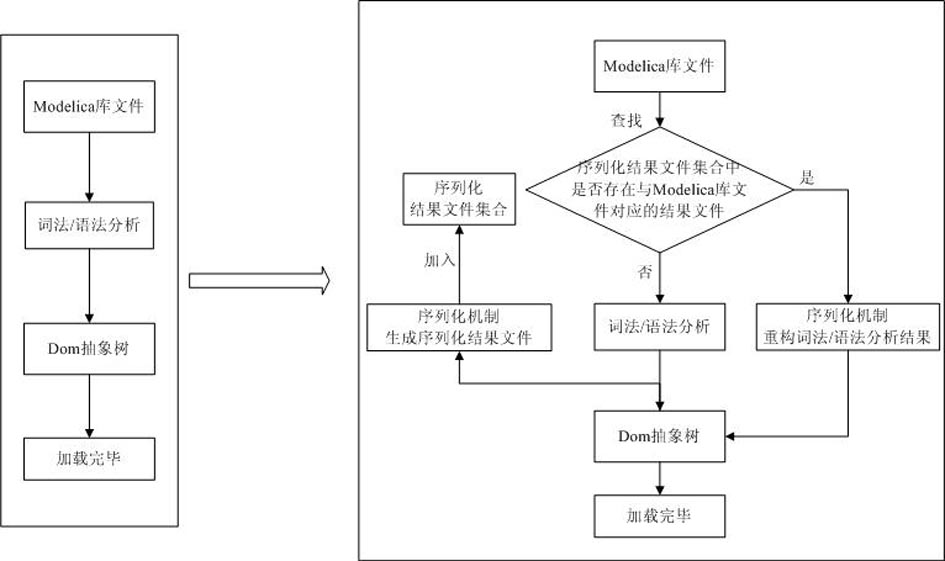
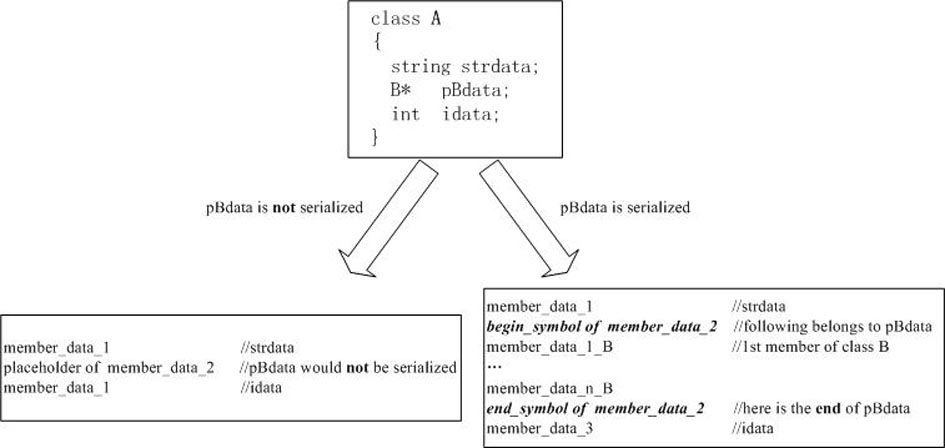
File serialization method of model library of physical modeling language Modelica
InactiveCN102043657AImprove loading speedAvoid parsingProgram loading/initiatingModelicaTheoretical computer science
The invention discloses a file serialization method of a model library of physical modeling language Modelica. The method is characterized by comprising the following steps: while loading the model library for the first time, lexical / syntactic analysis is carried out on source files of the Modelica model library; a document object model (DOM) abstract syntax tree is established; and the data of the DOM abstract syntax tree is saved in serialization destination files by a serialization technology. Meanwhile the invention further discloses a corresponding deserialization method. The method disclosed by the invention has the advantages that by means of the preprocessing course, while loading the model library for the first time, the serialization destination files are generated so as to facilitate loading the model library next time only by directly reading the destination files, thus avoiding lexical / syntactic analysis of the model library every time and greatly accelerating the loading speed of the model library. A Modelica2.1 standard library is taken as an example: while not using the method, the loading time is 300 seconds; and while using the method, the loading time is only 600 milliseconds.
Owner:苏州同元软控信息技术有限公司
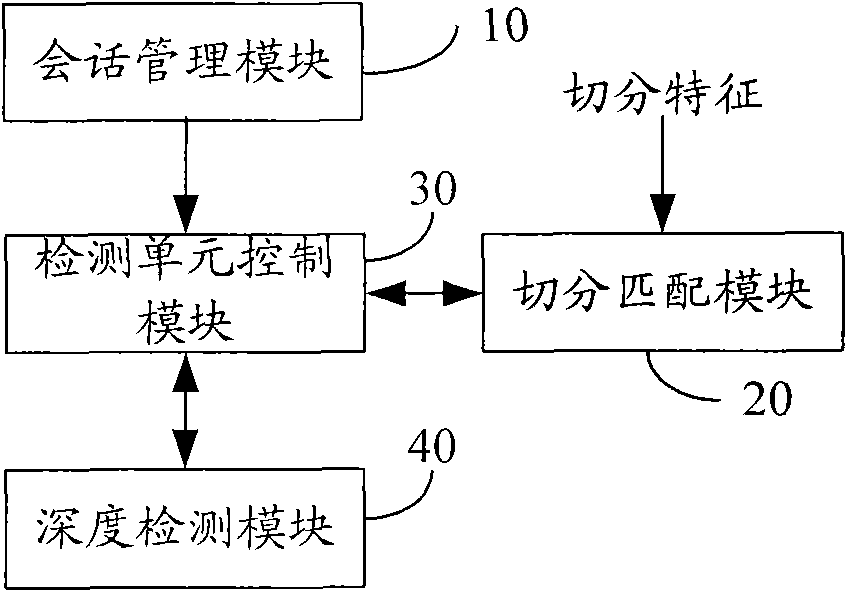
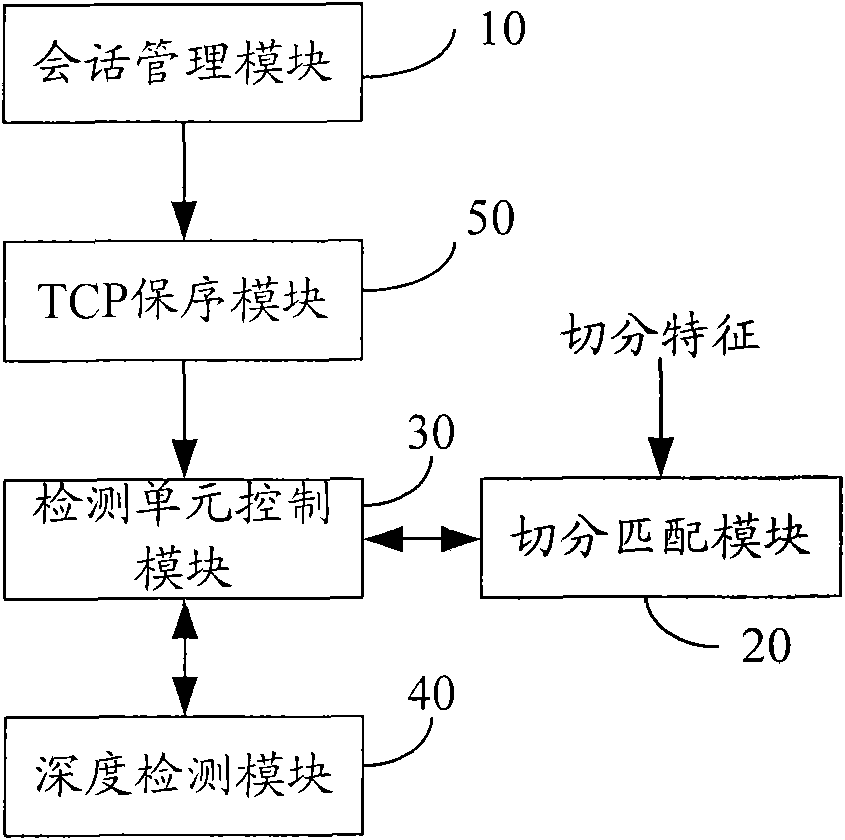
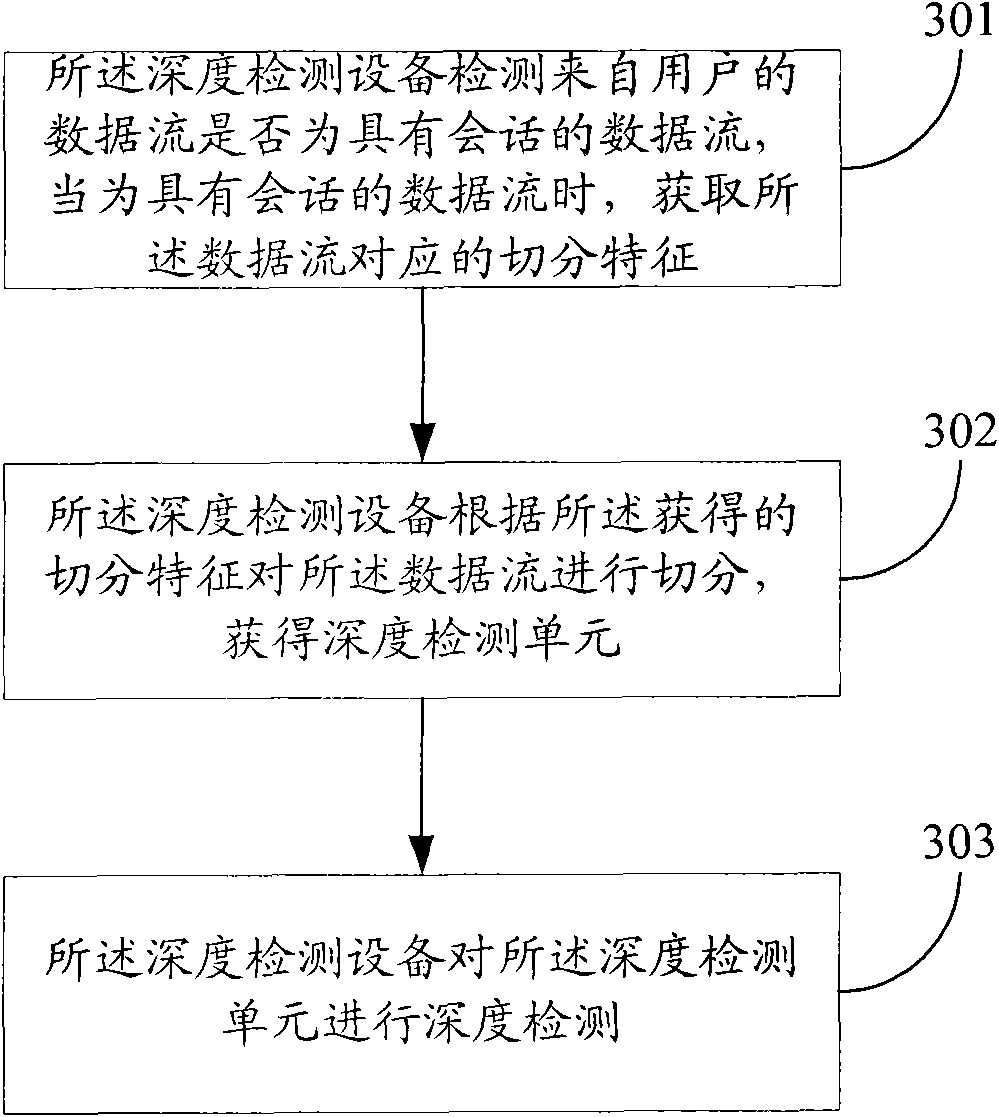
Application layer-based data segmenting method and device thereof
ActiveCN101557329AImprove accuracy and efficiencyAvoid parsingData switching networksProtocol ApplicationNetwork packet
The invention discloses an application layer-based data segmenting method which is applied to depth detection equipment. The method comprises the following steps of: detecting whether the data flow of the user is a data flow with a dialogue by the depth detection equipment and if so, acquiring the segmental characteristics corresponding to the data flow; segmenting the data flow according to the received segmental characteristics by the depth detection equipment to acquire a depth detection unit; and detecting the depth of the depth detection unit by the depth detection equipment. The method can highly effectively solve the segmental problem of the depth detection data of the application layer equipment, match the depth detection unit with the resolving process of the majority of protocols, prevent the data packet of the protocols from being analyzed and be used for depth detection-based reorganization of an engine and flow detection-based establishment and destruction of the detected flow of the engine, thus significantly improving the precision and efficiency of the detection.
Owner:HANGZHOU DPTECH TECH
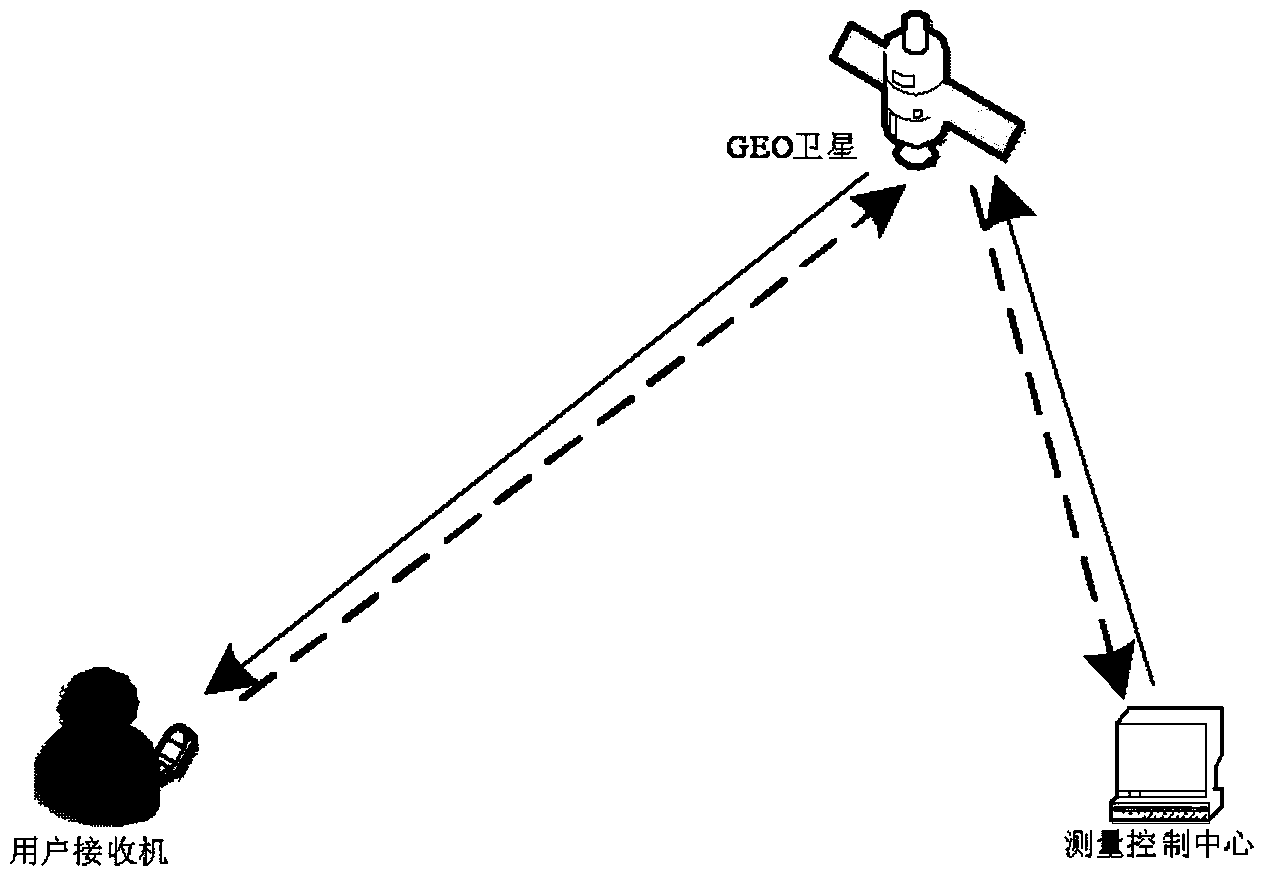
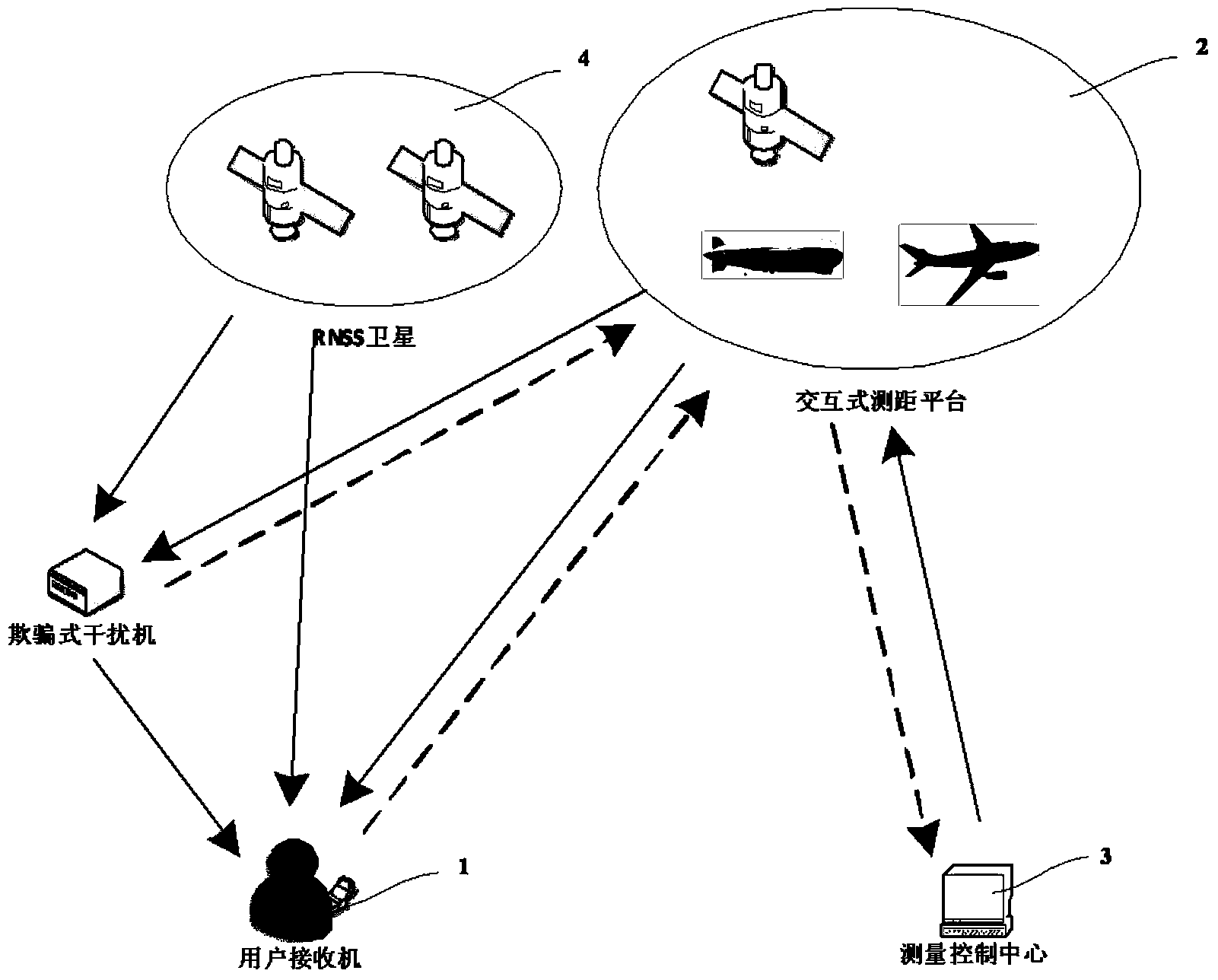
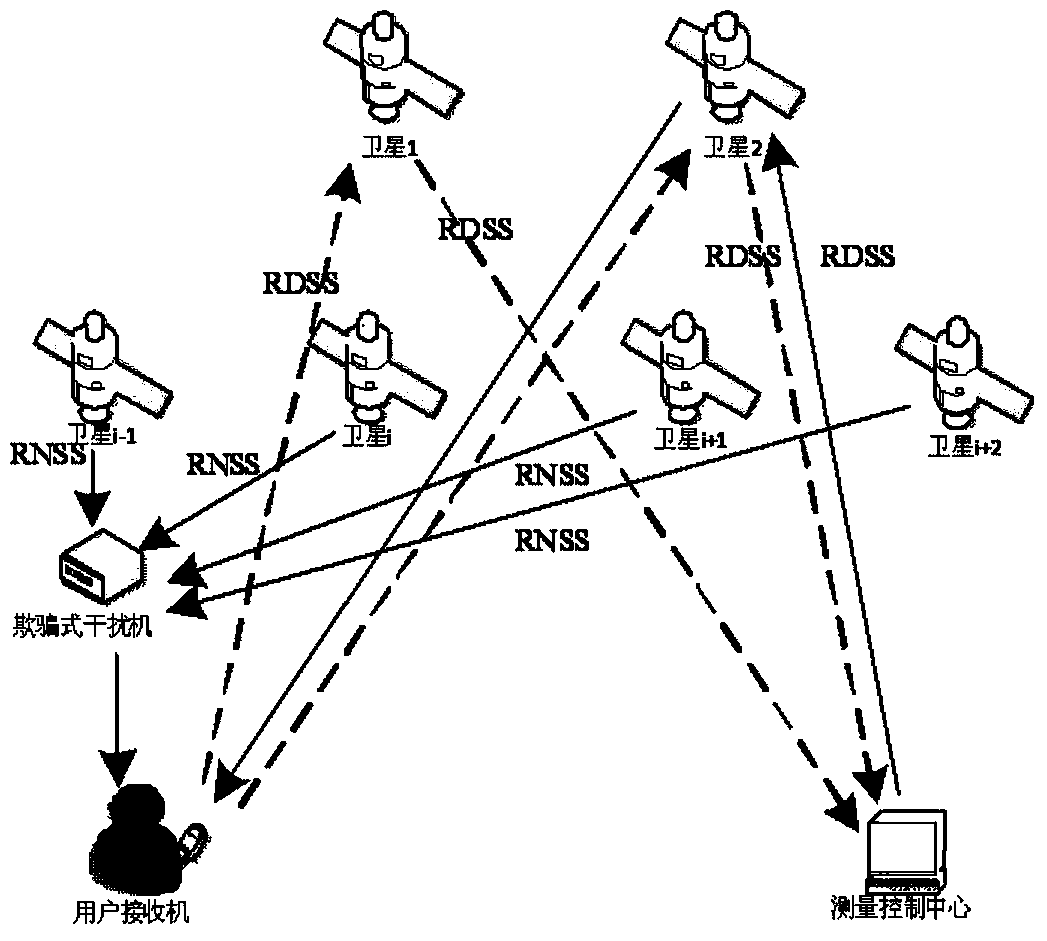
Anti-deception method based on interactive distance measurement information and RNSS
ActiveCN103713298AAvoid parsingImprove performanceSatellite radio beaconingComputer scienceDistance measurement
The invention discloses an anti-deception method based on interactive distance measurement information and an RNSS. The anti-deception method is applied to a system comprising a user receiver, an interactive distance measurement platform, a measurement control center and a navigational satellite. The user receiver exchanges interactive distance measurement signals with the measurement control center through the interactive distance measurement platform; the navigational satellite sends an RNSS signal to the user receiver; the user receiver compares positioning results or distance information obtained based on the interactive distance measurement signals and the positioning results or distance information obtained based on the RNSS, and judges whether deception interference is received; and the measurement control center judges whether the user receiver is subjected to the deception interference based on the number of interactive distance measurement answering signals received from the same user receiver and the same interactive platform nodes. The anti-deception is achieved by utilizing the interactive distance measurement platform, so that analysis on signal features can be avoided, realization difficulty is reduced, and the anti-deception can be achieved.
Owner:ACAD OF OPTO ELECTRONICS CHINESE ACAD OF SCI
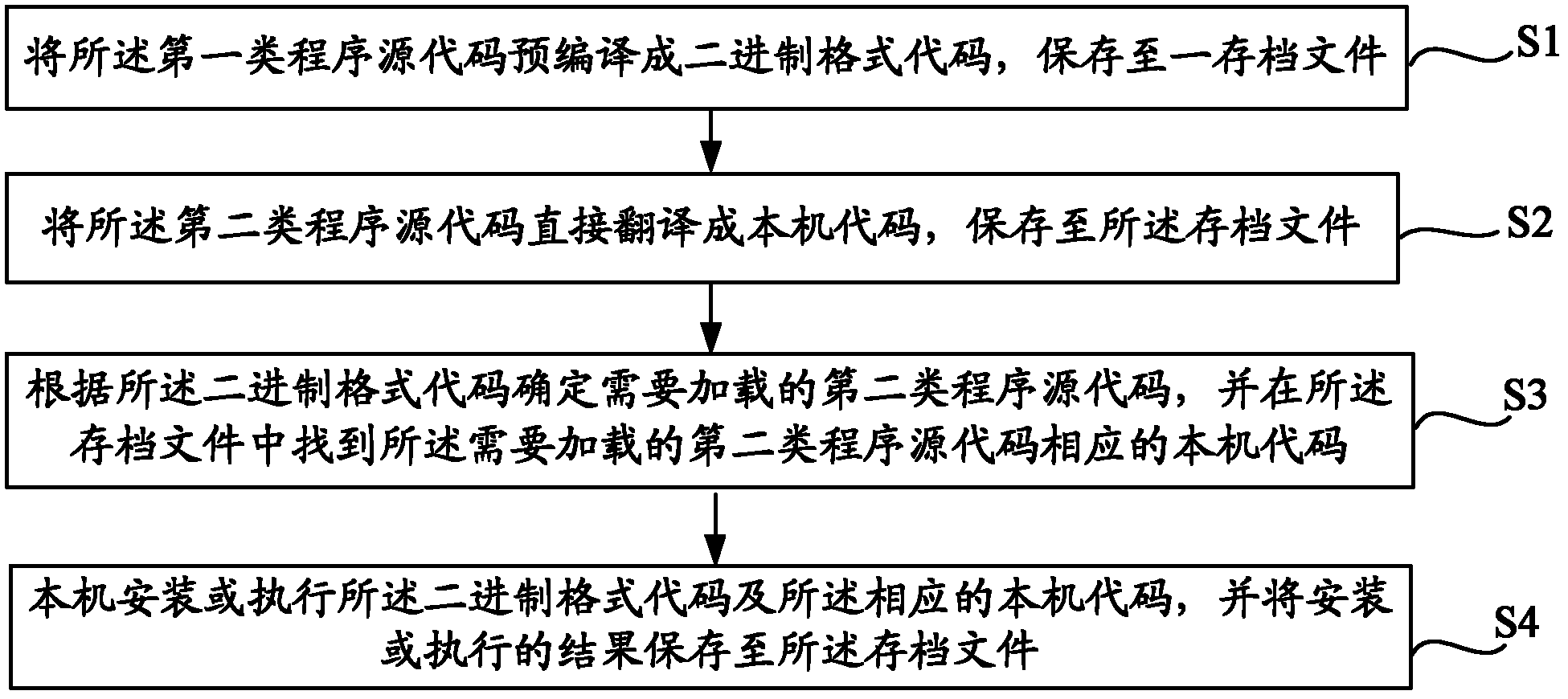
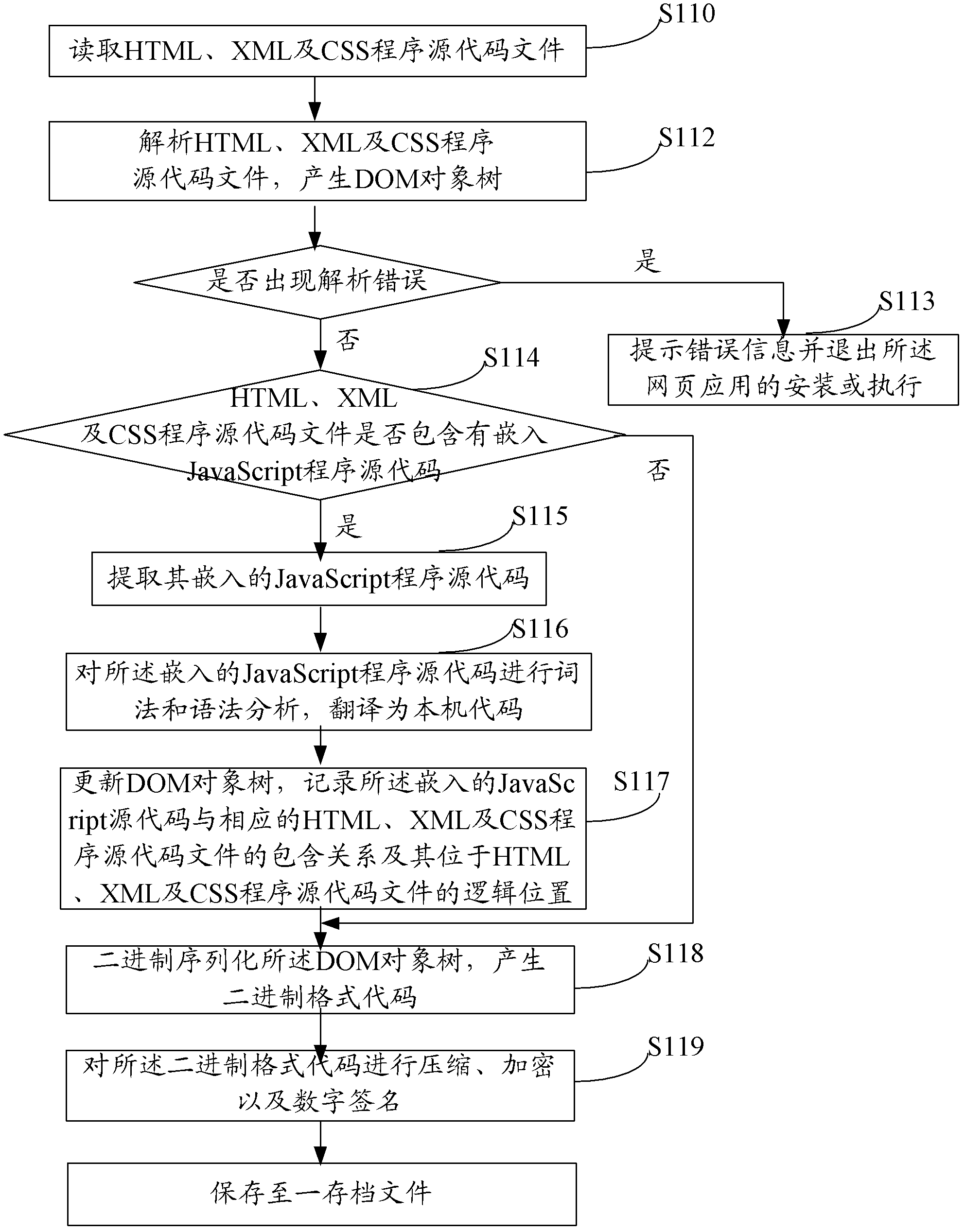
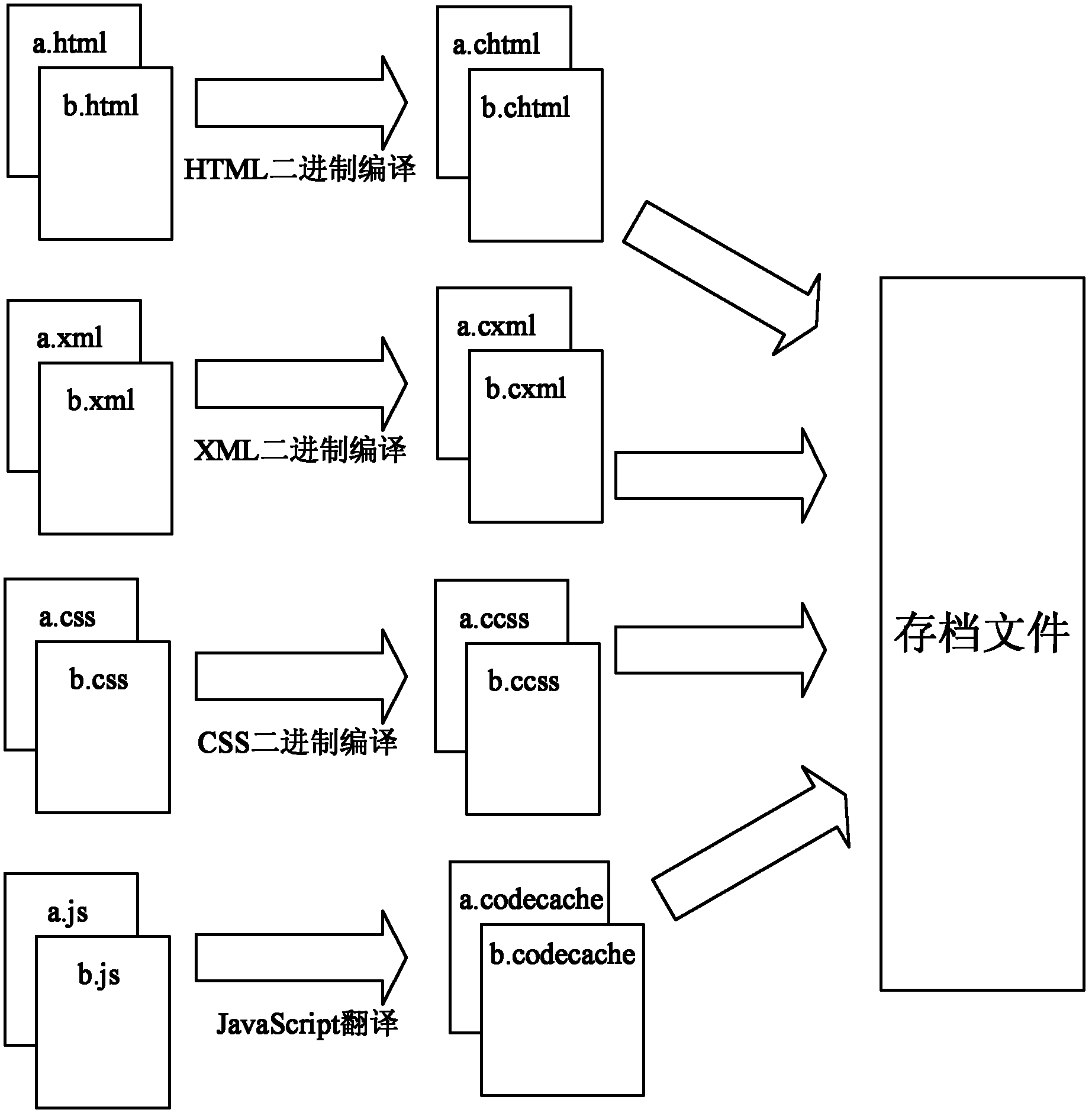
Method and system for acceleration of Webpage application execution
InactiveCN103176807AGuaranteed uptimeAvoid parsingProgram loading/initiatingMemory systemsSource code fileText mode
The invention provides a method and system for acceleration of Webpage application execution. Program source codes of hypertext markup language (HTML) or computer system simulation (CSS) or a JavaScriprt in Webpage application are compiled into binary format codes in an initial installation of Webpage application stage or a loading execution stage, source codes of the JavaScriprt are directly compiled into codes of a native machine, second type program source codes need loading can be confirmed by the native machine according to the binary format codes, codes of the native machine, corresponding to the second type program source codes need loading are found in an archived file, and then installation or execution is conducted, and a result of the installation or the execution is preserved in the archived file. According to the method and system for the acceleration of the Webpage application execution, in the process that the Webpage application is issued to be executed for multi-times, only one time of text mode code analyzing and binary translation is needed, and thus the text mode code analyzing and binary translation works conducted every time the Webpage application are executed, and thus the operating performance of the Webpage application is improved.
Owner:SHENGLE INFORMATION TECH SHANGHAI
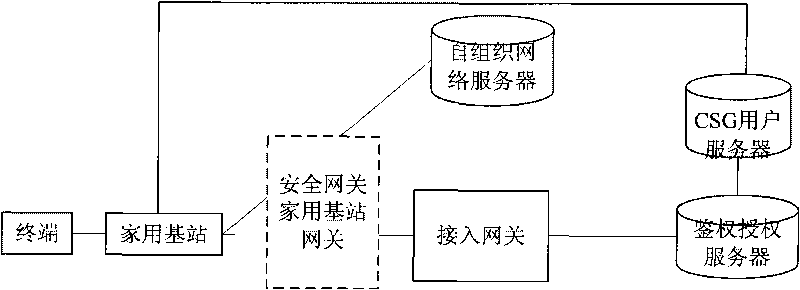
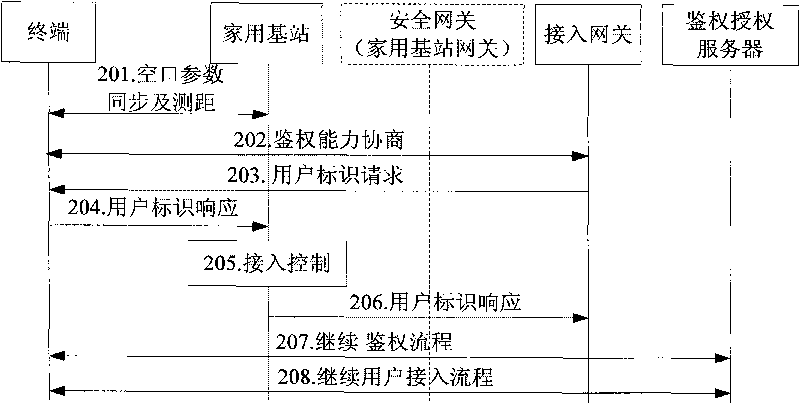
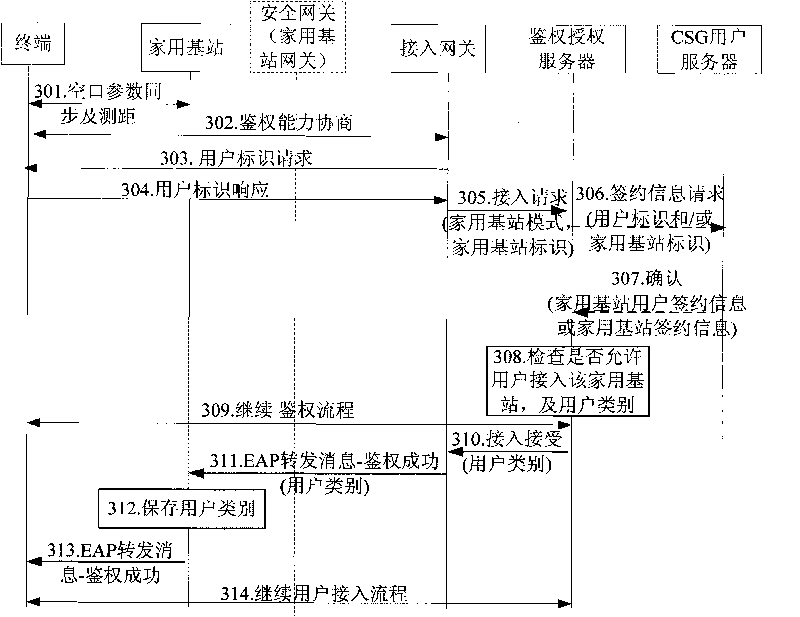
System and method for implementing authentication on user of home base station
InactiveCN101730102AAvoid parsingReduce processing burdenTransmissionSecurity arrangementUser identifierHome based
The invention provides a system and a method for implementing authentication on a user of a home base station. The method comprises the following steps that: in the process of requesting for access to the home base station in a closed access mode or a mixed access mode by a terminal, an access gateway sends user identification information, a home base station identifier and a home base station mode to an authentication and authorization server, or to a user server of a closed user group CSG through the authentication and authorization server; when the home base station is in the closed access mode, the authentication and authorization server or the CSG user server judges whether to allow the user to access the home base station or not and returns a judgment result to the home base station through the access gateway; and when the home base station is in the mixed access mode, the authentication and authorization server or the user server of the closed user group CSG determines user type information and returns the type information to the home base station through the access gateway. The system and the method can avoid transferring a real user identifier frequently at a hollow port, and reduce the burden of the home base station and the potential safety hazard of the home base station.
Owner:ZTE CORP
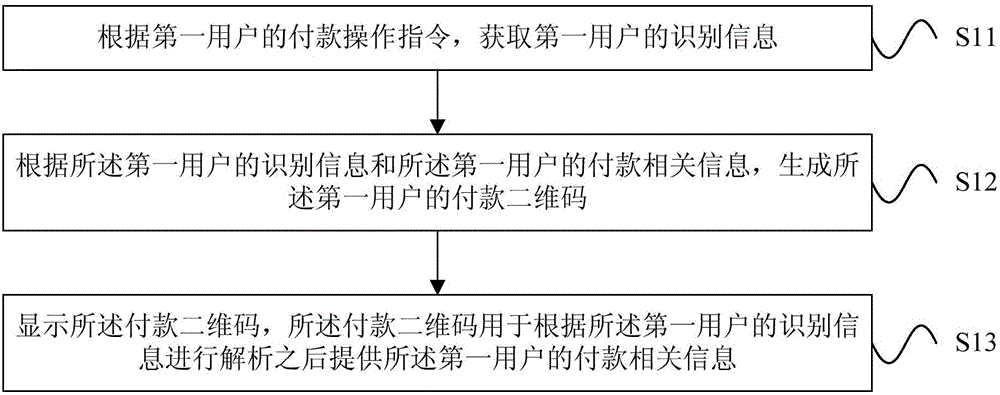
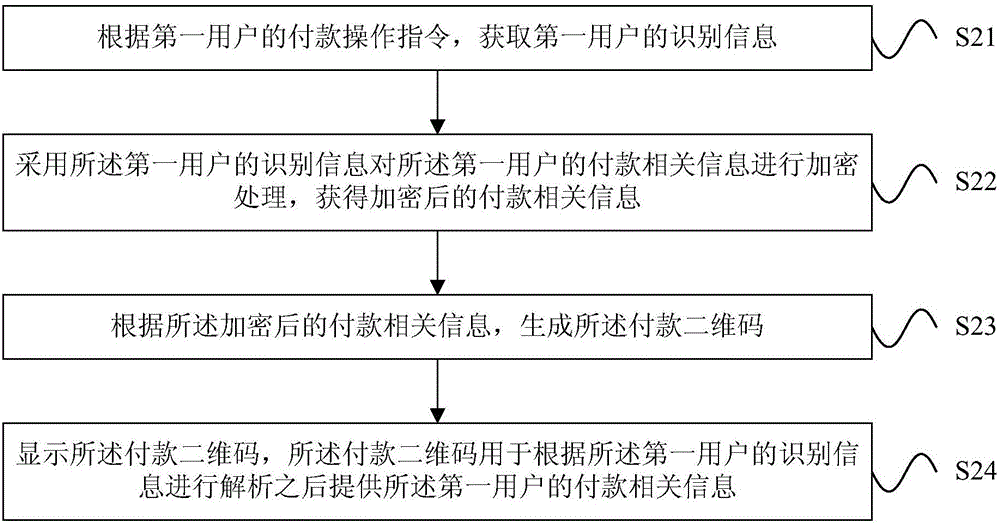
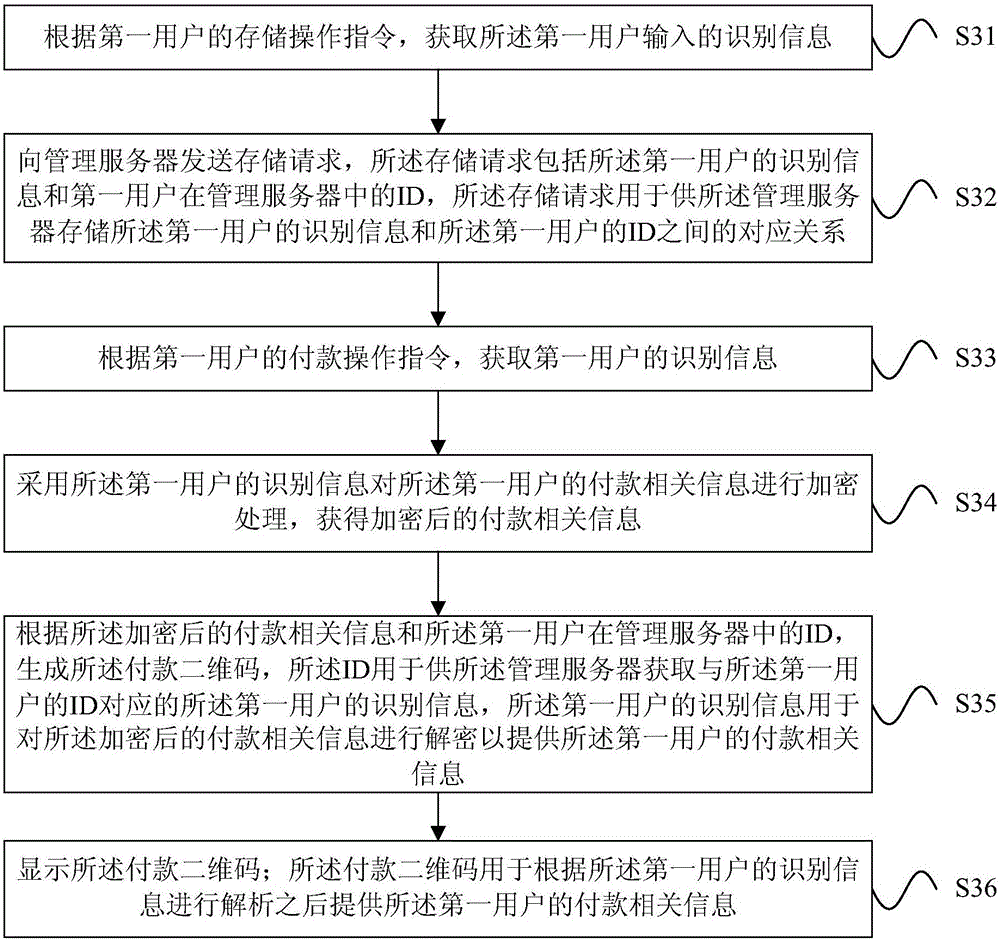
QR code-based payment method, QR code-based payment device and QR code-based payment system
The invention relates to a QR code-based payment method, a QR code-based payment device and a QR code-based payment system. The method comprises the following steps: acquiring the identification information of a first user according to a payment operation instruction of the first user; generating a payment QR code of the first user according to the identification information of the first user and the payment-related information of the first user; and displaying the payment QR code, wherein the payment QR code is used to provide the payment-related information of the first user after parsing according to the identification information of the first user. As the identification information of the first user is unique, even if the payment QR code is leaked, other users can parse out the payment-related information only according to the identification information of the first user. Therefore, acquisition of payment-related information directly according to a payment QR code is avoided, and the security of QR code-based payment is improved.
Owner:BEIJING XIAOMI PAYMENT TECH CO LTD
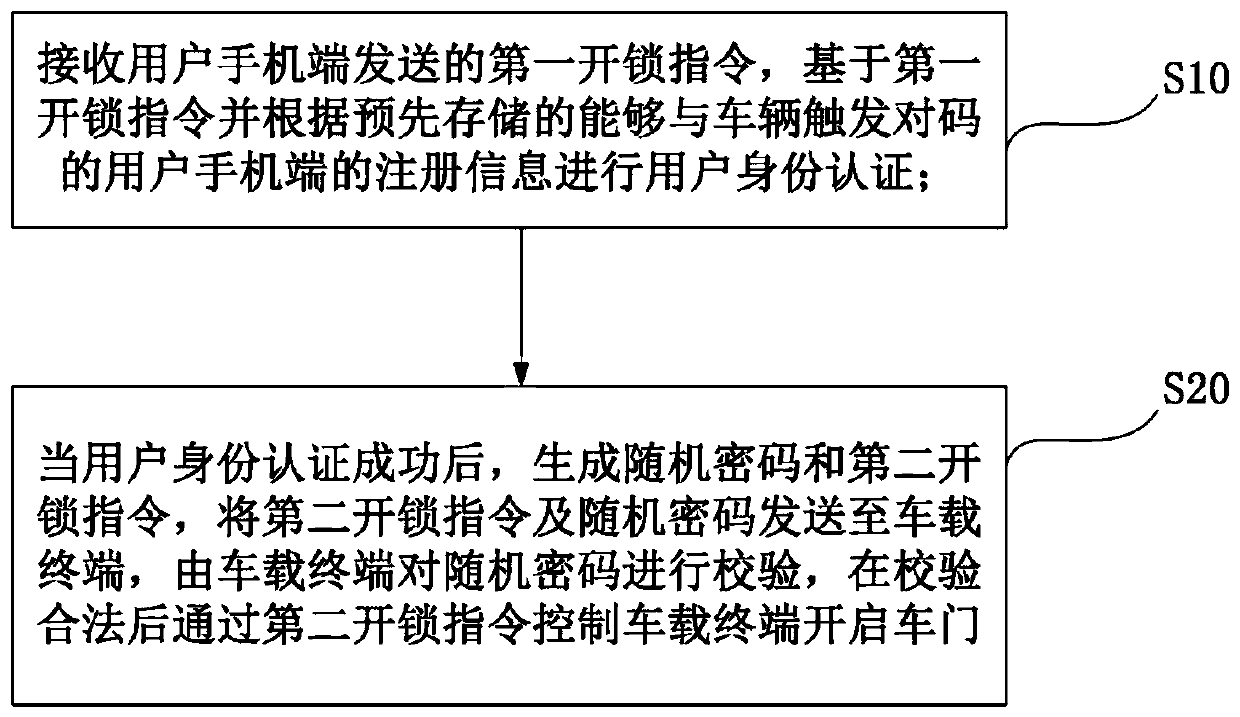
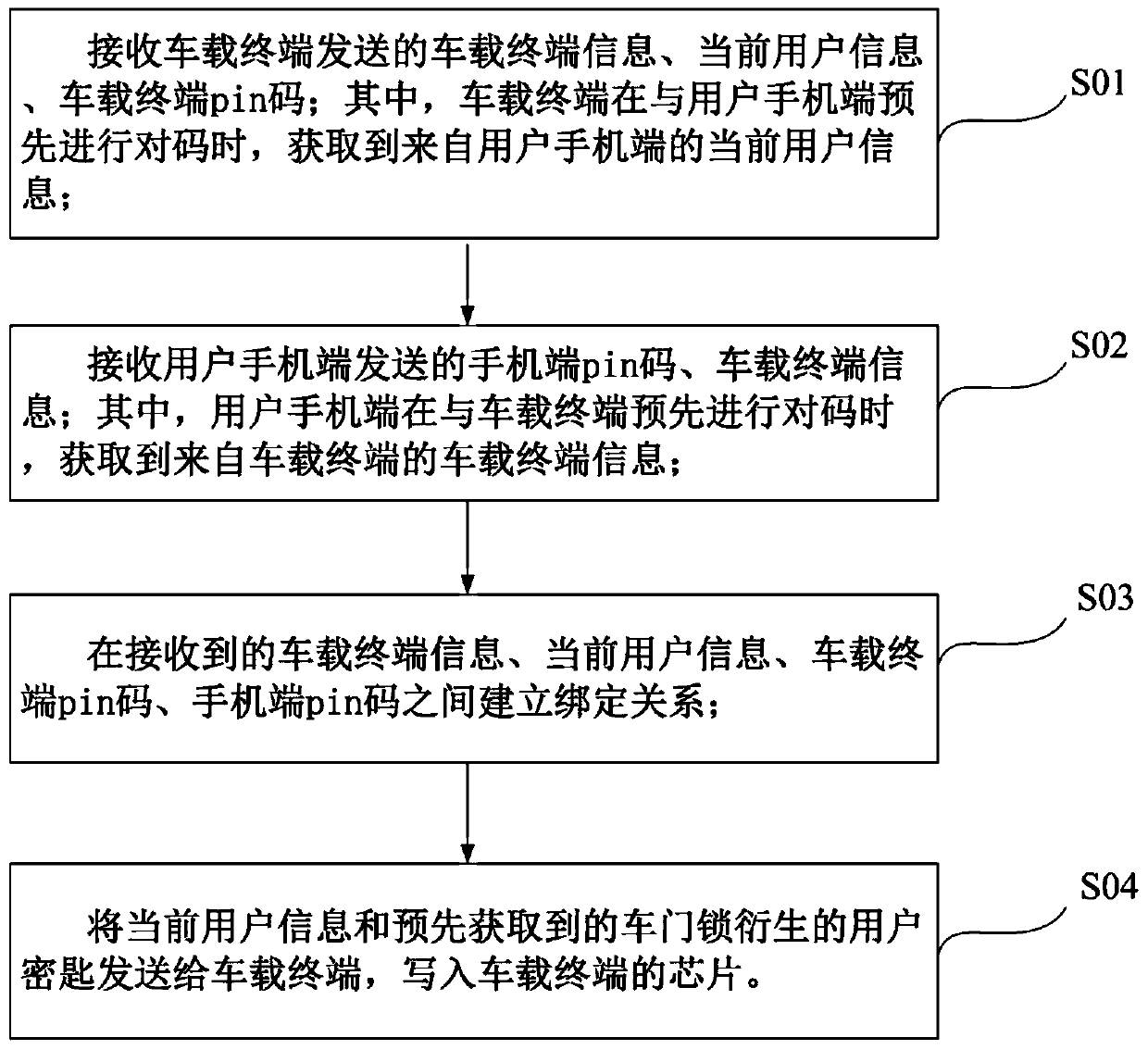
Unlocking method and unlocking system with mobile phone as automobile key
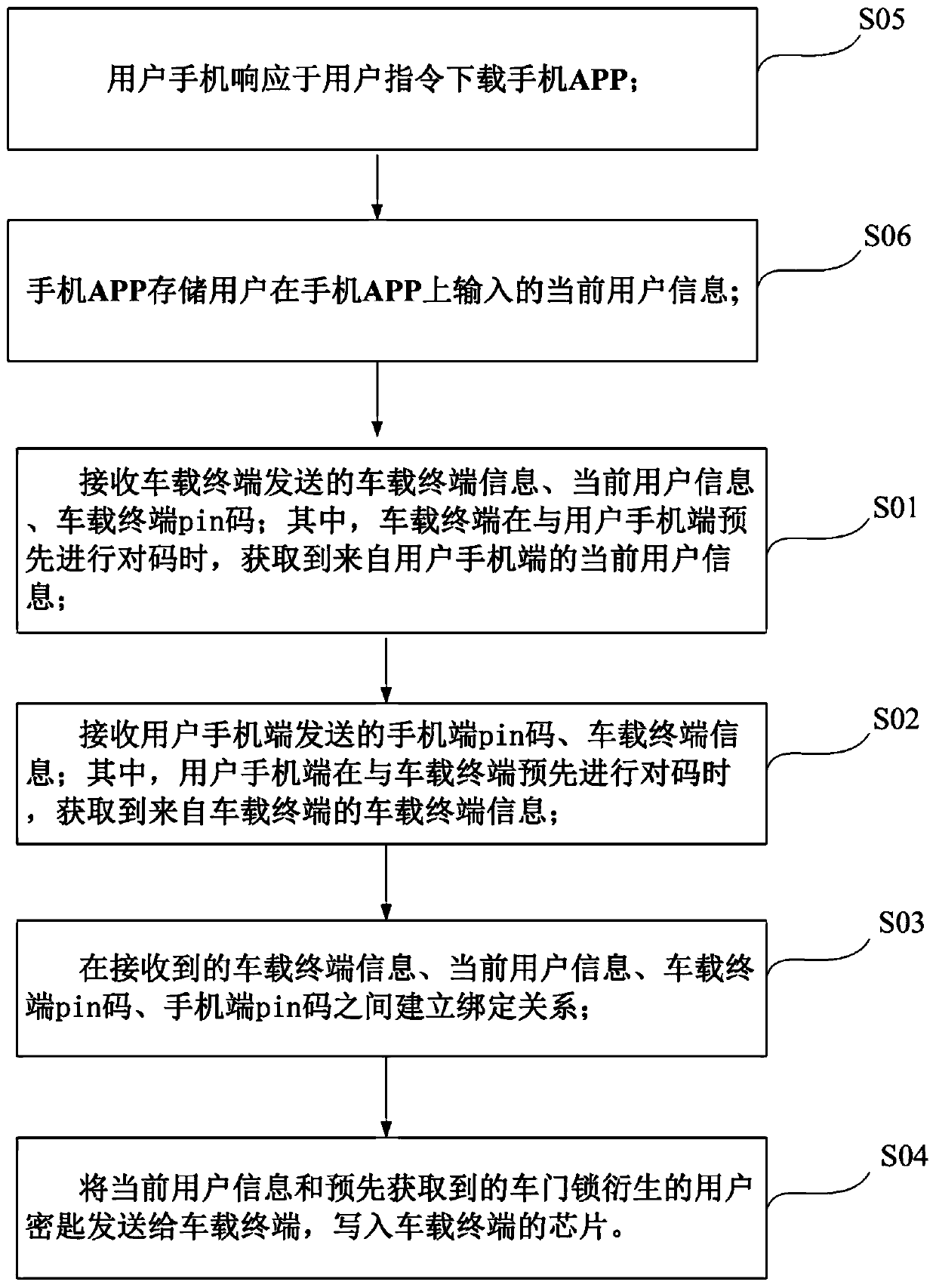
ActiveCN110381199APrevent theftImprove securityAnti-theft devicesSubstation equipmentPasswordComputer terminal
The invention provides an unlocking method and an unlocking system with a mobile phone as an automobile key, and relates to the technical field of vehicle control. The unlocking method with the mobilephone as the automobile key comprises the following steps: receiving a first unlocking instruction sent by a user mobile phone terminal, and performing user identity authentication based on the firstunlocking instruction and according to pre-stored registration information of the user mobile phone terminal capable of triggering code matching with an automobile; and after the user identity authentication succeeds, generating a random password and a second unlocking instruction, sending the second unlocking instruction and the random password to the vehicle-mounted terminal, verifying the random password by the vehicle-mounted terminal, and controlling the vehicle-mounted terminal to open the vehicle door through the second unlocking instruction after the random password is verified to belegal. When the vehicle receives the unlocking instruction, the user identity authentication needs to be conducted firstly, the vehicle can be started only after joint authentication of the mobile phone terminal and the vehicle-mounted terminal, the safety performance of the vehicle is improved, and the problem that the vehicle is stolen due to the fact that a mobile phone is lost is avoided.
Owner:GEELY AUTOMOBILE INST NINGBO CO LTD +1
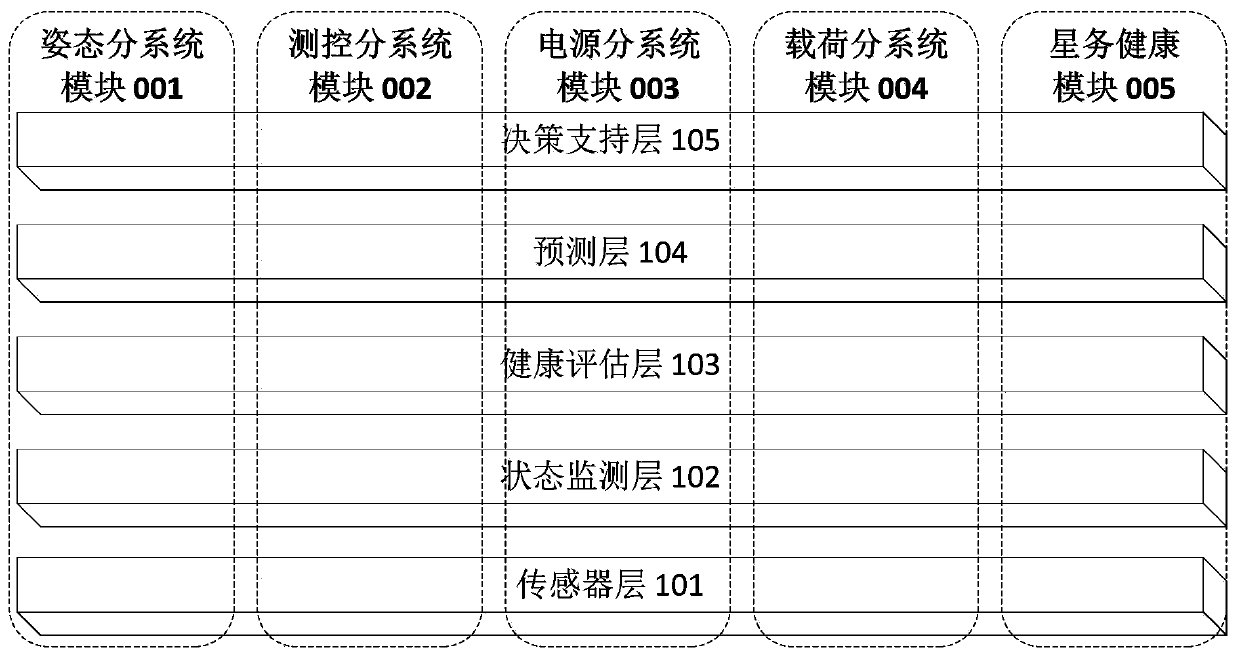
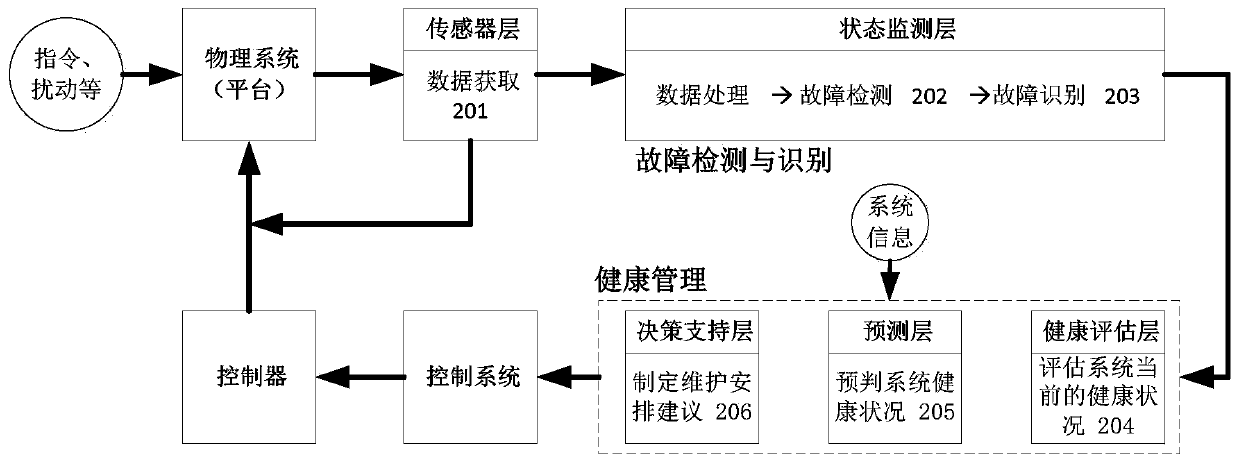
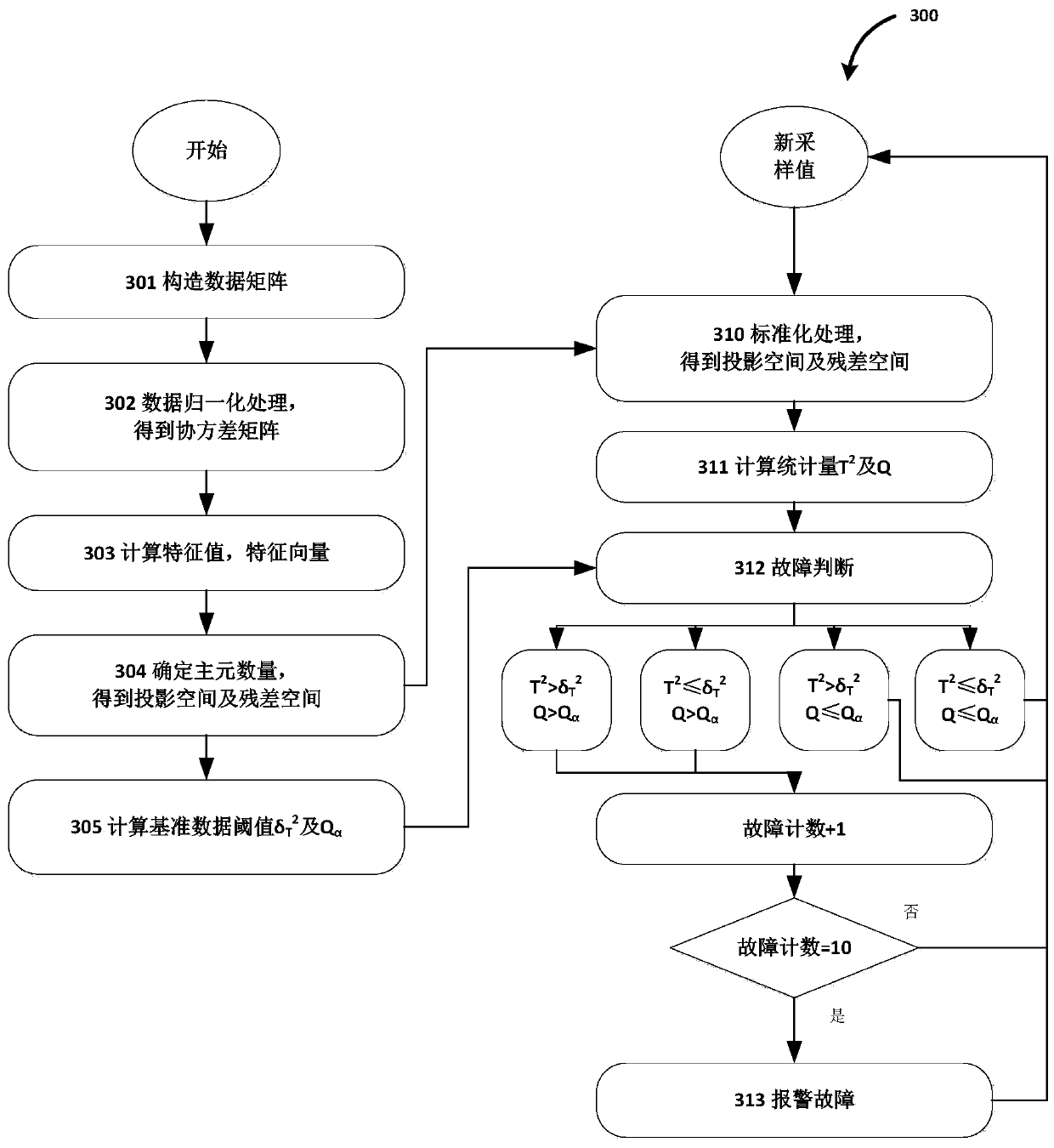
Hierarchical software health management method and system for microsatellites
ActiveCN110795309AAvoid parsingAvoid processing powerHardware monitoringHealth impactSoftware system
The invention provides a hierarchical software health management method and system for microsatellites. The hierarchical software health management system performs hierarchical health management on satellites according to different subsystems, and comprises a sensor layer, a state monitoring layer, a health evaluation layer, a prediction layer, a decision processing layer and the like. Through software sensors deployed at operation key nodes of all sub-components of satellite housekeeping, the hierarchical software health management method collects running state data of each sub-component andanalyzes the running state data to obtain fault information, hierarchically evaluates the health condition of the current satellite system in combination with satellite historical telemetry data, software system knowledge and the fault information, pre-judges the health condition of the system at the future moment, and finally makes a health hazard strategy.
Owner:INNOVATION ACAD FOR MICROSATELLITES OF CAS +1
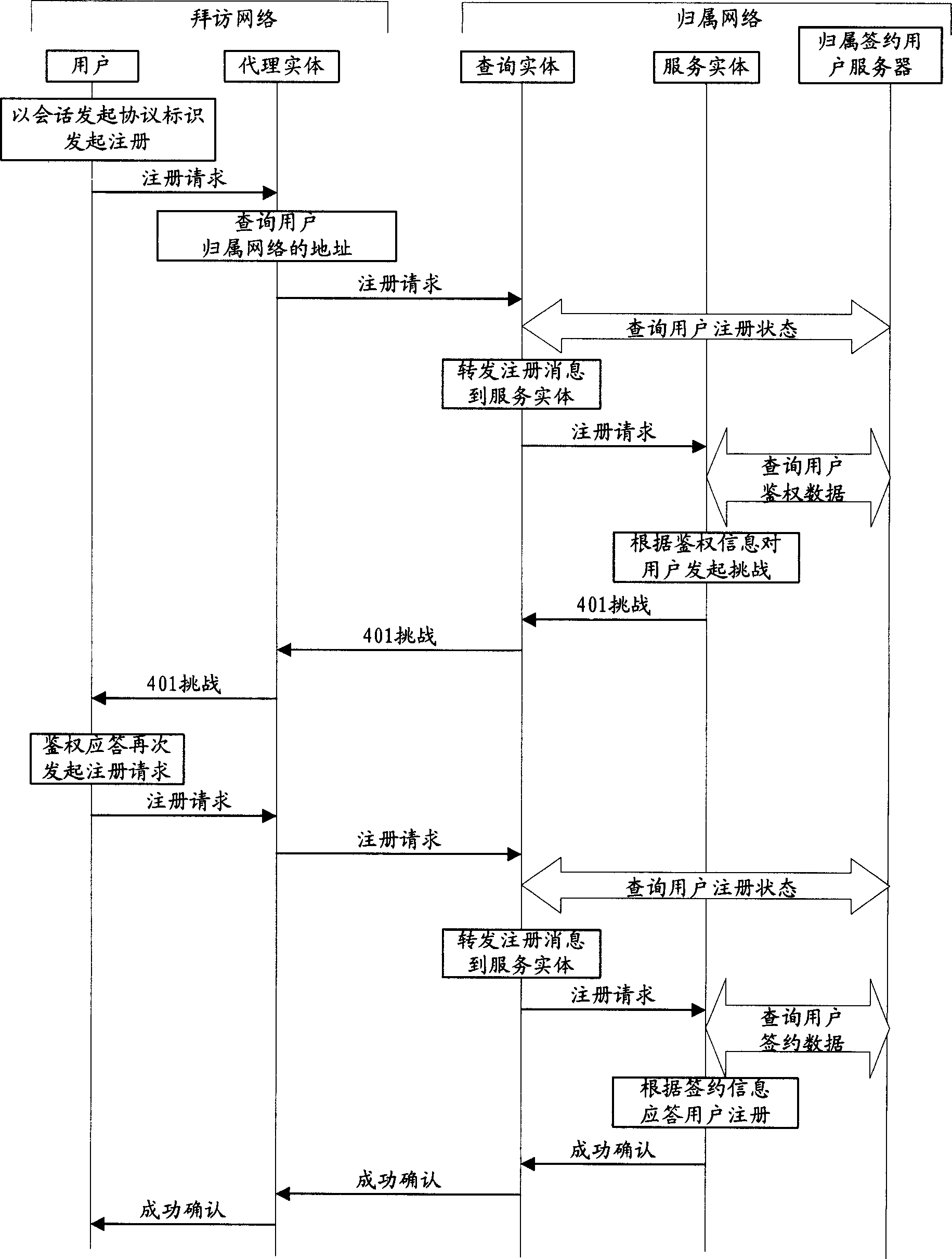
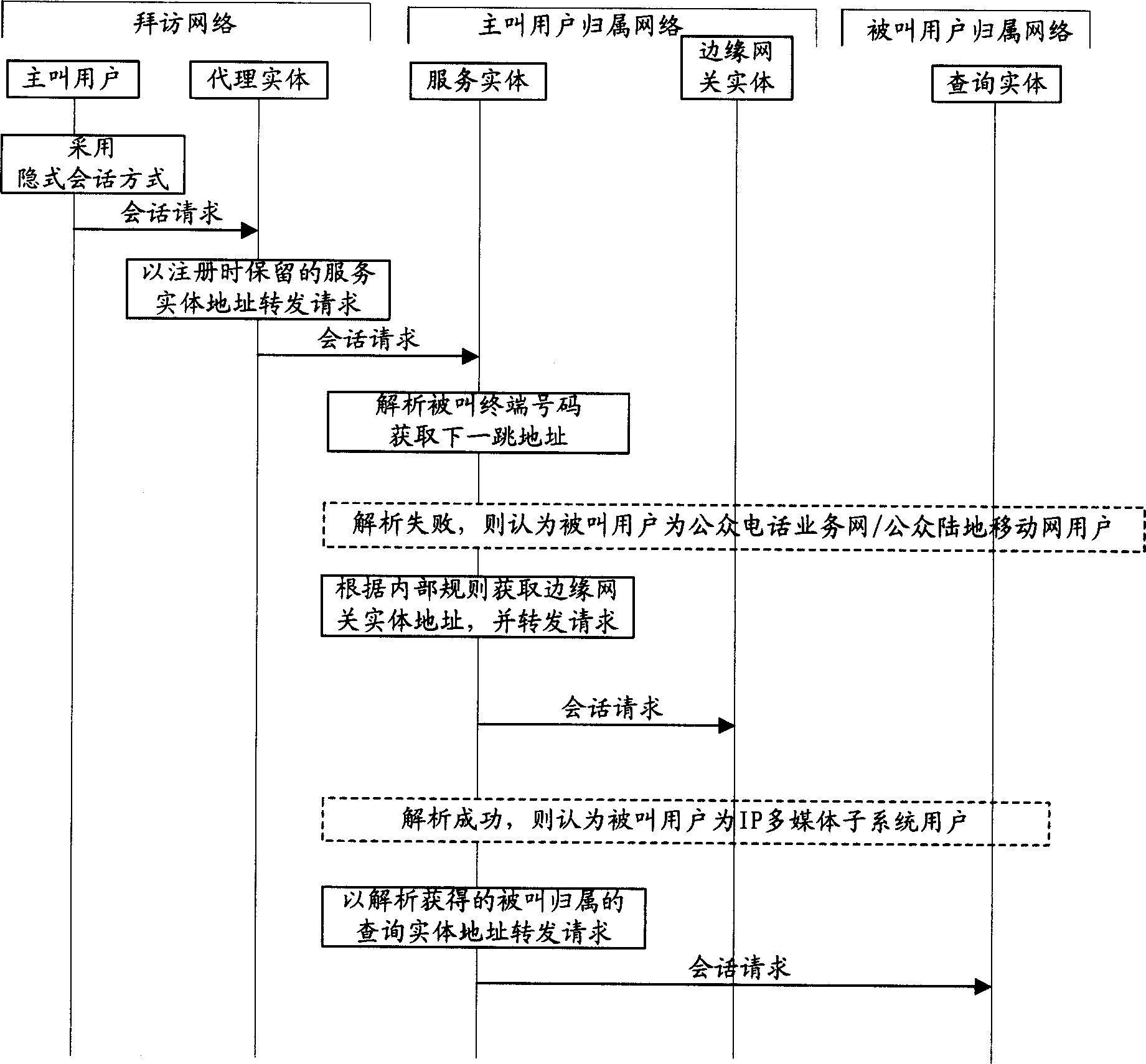
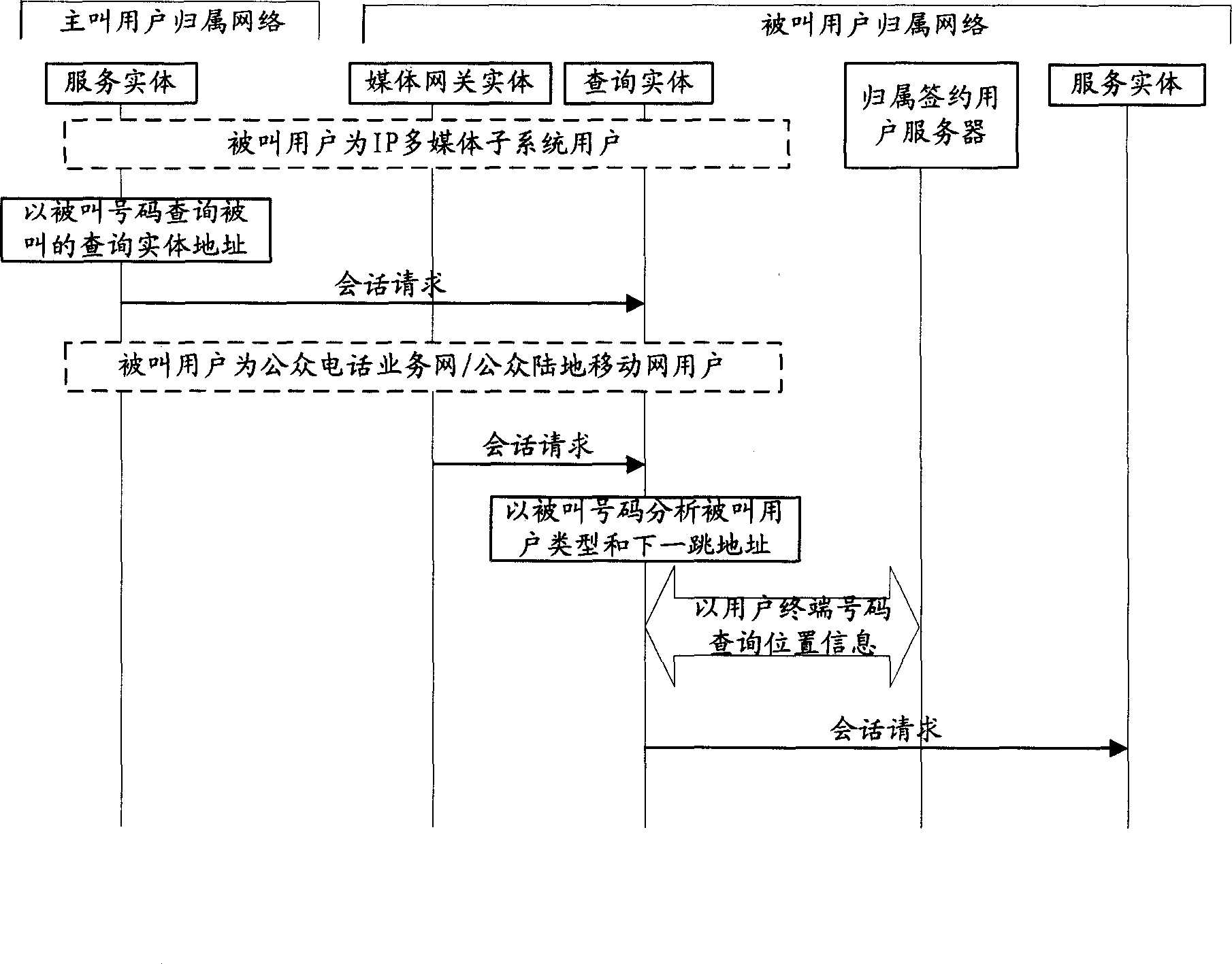
User registration and conversation switching method in IP multimedia terminal and system
InactiveCN1882172AIncrease optionalitySupport habitRadio/inductive link selection arrangementsTransmissionComplex problemsIP Multimedia Subsystem
The invention relates to a method for registering user in IP multimedia subsystem, for solving the present technique which can only register with the SIP URI mark as base mark. The inventive method comprises: user uses E.164 mark as basic mark to initialize register request; IMS terminal transforms said E.164 mark into the register mark meeting SIP protocol, and adds the register mark into the register request message; the network device of IMS network, based on said register request message, completes the priority identification and register.
Owner:HUAWEI TECH CO LTD
Method of measuring and calculating distribution of water temperatures of river channel below dam of reservoir
InactiveCN103279662AAvoid parsingReduce computational workloadSpecial data processing applicationsUsabilityWorkload
Provided is a method of measuring and calculating distribution of the water temperatures of a river channel below a dam of a reservoir. Actually-measured data of the weather and the hydrology are combined, changes of the water temperatures along the river channel below the dam of the reservoir are measured and calculated, a position below the dam of the reservoir serves as the first measuring and calculating section, and the spacing distance of sections along the river channel is calculated according to an integral multiple of the one-day and one-night flow path of a river reach with the mean velocity. Heat exchange of water in the river channel is fully considered, detailed analysis does not need to be carried out on hydrodynamic processes, the mean velocity is used for replacing hydrodynamic calculation, the analysis of hydrodynamic equations required by numerical simulation calculation can be avoided, and workloads of calculation are reduced greatly. Meanwhile, according to the method, main factors leading to the changes of the water temperatures of the river channel are fully considered, and accuracy of calculation is guaranteed. As for the method, the good accuracy is obtained, the amount of calculation is relatively small, complex boundary condition data are not needed, work efficiency can be improved greatly, application fields can be widened, the accuracy and usability can be taken into account better, and the method can effectively assist in making discharging schemes of the water temperatures and the flow quantity of the reservoir.
Owner:CHANGJIANG RIVER SCI RES INST CHANGJIANG WATER RESOURCES COMMISSION
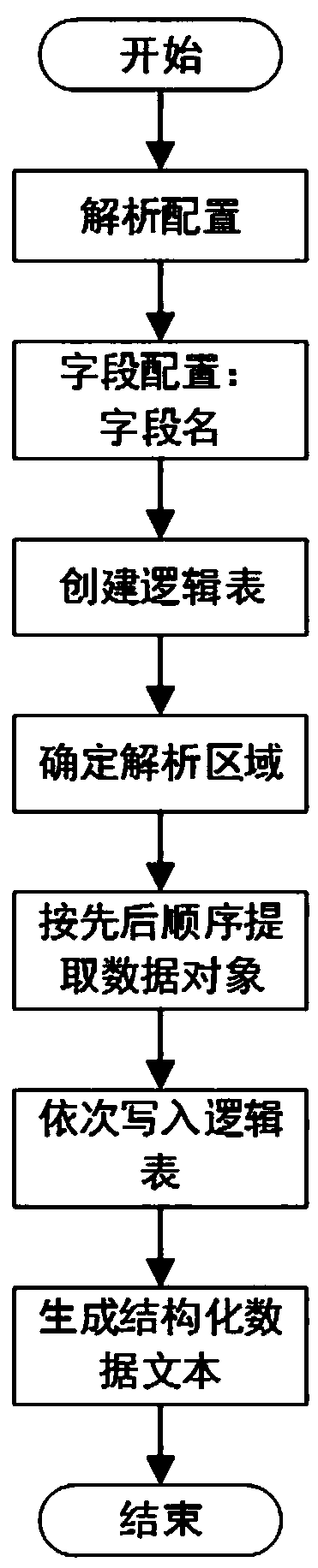
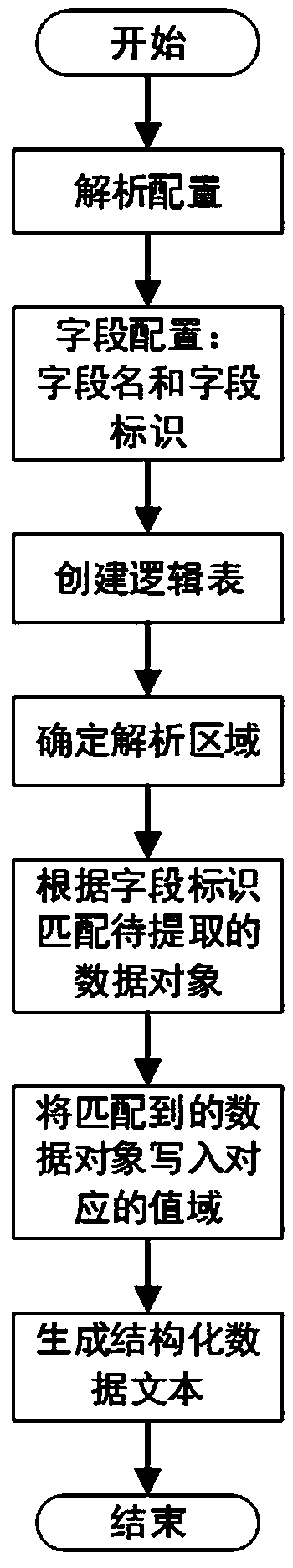
Configurable data analysis method and computer readable storage medium
InactiveCN110119423AReduce the amount of parsed dataAvoid full page parsingDatabase management systemsWeb data indexingData objectsData analysis
The invention relates to a configurable data analysis method. The method comprises the following steps: making analysis configurations; performing field configuration; creating a blank logic table, and writing each field name into the blank logic table; capturing a target webpage corresponding to the URL, extracting a data object according to the analysis type and the analysis attribute, and sequentially mapping the data object into the logic table to form a corresponding relationship with the field name, thereby converting the target webpage into a structured data text. According to the configurable data analysis method, by configuring the analysis table, webpages of different formats can be flexibly coped, webpage analysis is completed, webpage data are converted into structured data texts, and application and mining of information are facilitated.
Owner:厦门商集网络科技有限责任公司
Network storm real-time rapid detecting method used for intelligent substation
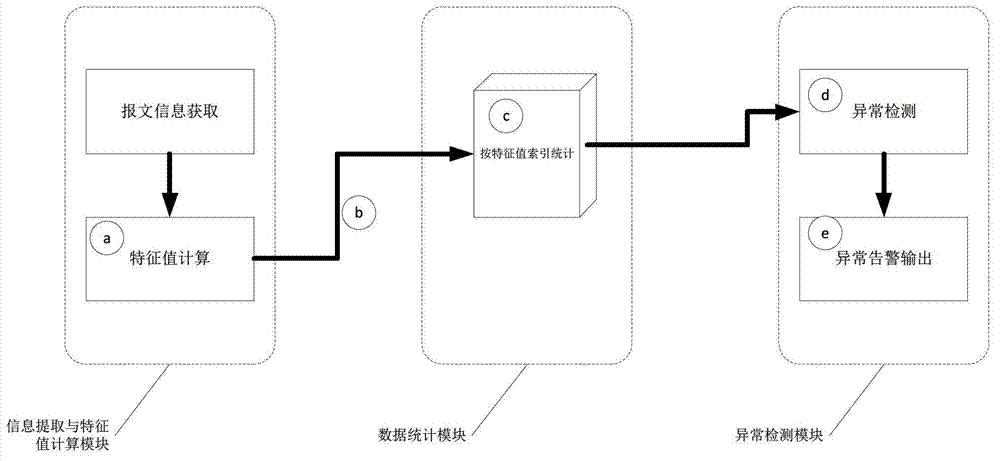
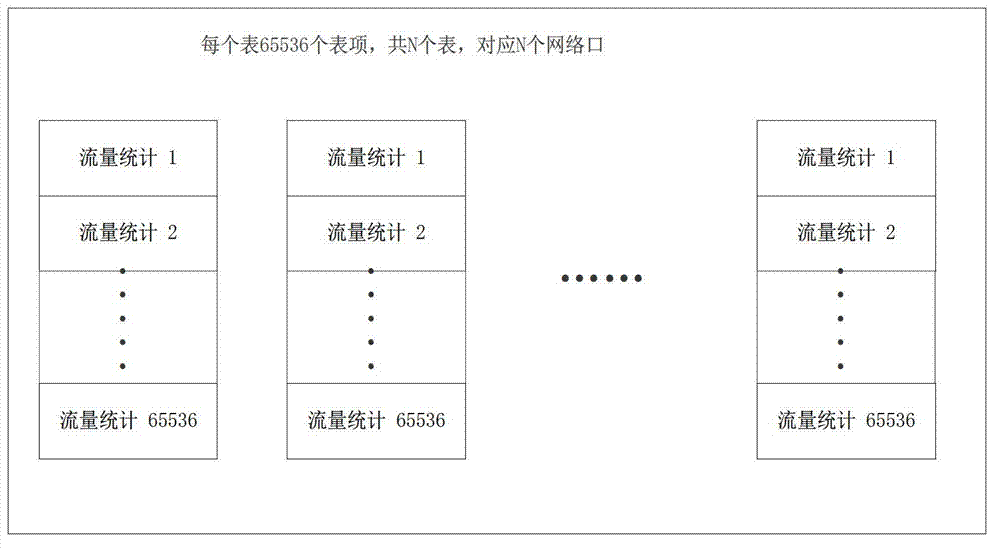
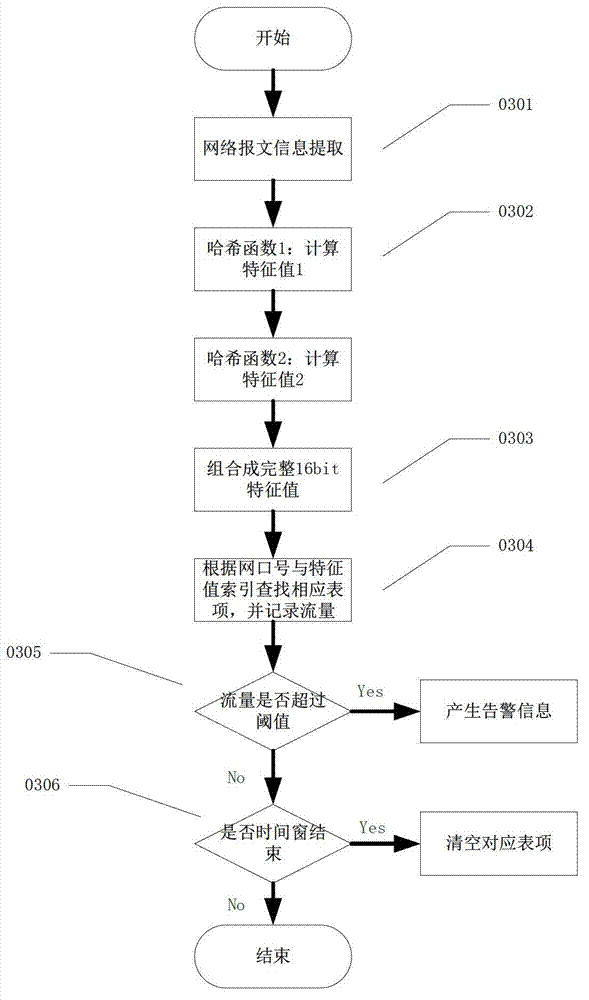
ActiveCN103297298AReduce stepsReduce disruption to normal operationsData switching networksSmart substationMessage flow
The invention discloses a network storm real-time rapid detecting method used for an intelligent substation. The network storm real-time rapid detecting method includes: utilizing existing message analytical results from a message record and analytical device to select two kinds of information which can represent message features as detecting items; performing Hash calculation to the two detecting items and combining calculated result into 16bit characteristic value; calculating message flow with the same characteristic value received from each network port within detecting time window; defining as network storm if the message flow exceeds preset warning threshold value; and calculating restoration marks when the detecting window is completed, and recording calculated data while performing zero clearing and operation. In the network storm real-time rapid detecting method, messages are utilized for analyzing abstracted message information, flow storm can be detected rapidly and accurately, and performance of devices cannot be affected.
Owner:SHANDONG SHANDONG UNIV ELECTRIC POWER TECH
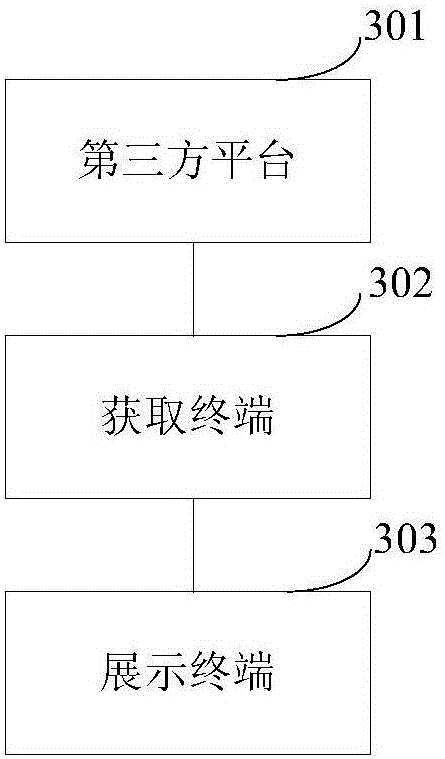
Two-dimensional code safety payment method, terminal, and system
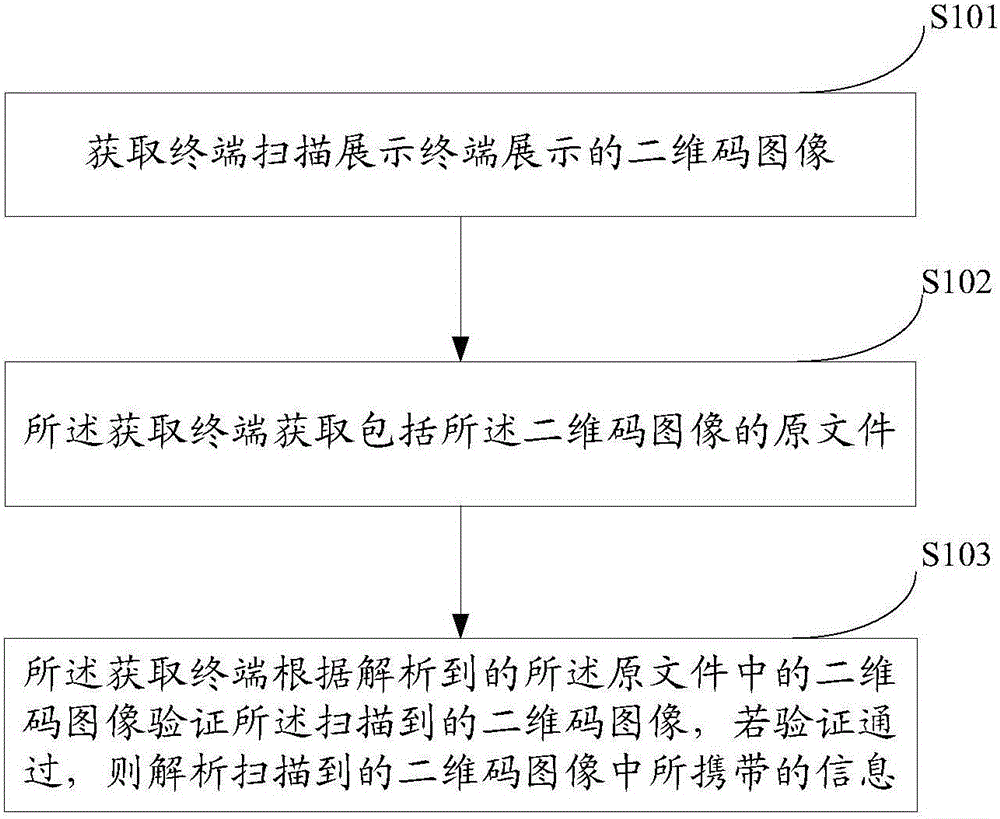
InactiveCN106022738AEnsure safetyImprove securityPayments involving neutral partyProgramming languageImage display
The invention provides a two-dimensional code safety payment method. The two-dimensional code safety payment method comprises the steps that a two-dimensional code image displayed by a display terminal is scanned by an acquisition terminal; the acquisition terminal is used to acquire an original document comprising the two-dimensional code image; the acquisition terminal is used to verify the scanned two-dimensional code image according to the parsed two-dimensional code image of the original document; when the verification is passed, information carried out by the scanned two-dimensional code image is parsed. The two-dimensional code safety payment method is advantageous in that before the content of the two-dimensional code is parsed, the safety of the two-dimensional code is verified, and by adopting the way of verifying the original document extracted from the source of the two-dimensional code, the parsing of the two-dimensional code having safety hidden troubles is fundamentally prevented, and therefore the safety of the two-dimensional code payment is improved, and the safety of the two-dimensional code used by a user is guaranteed.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
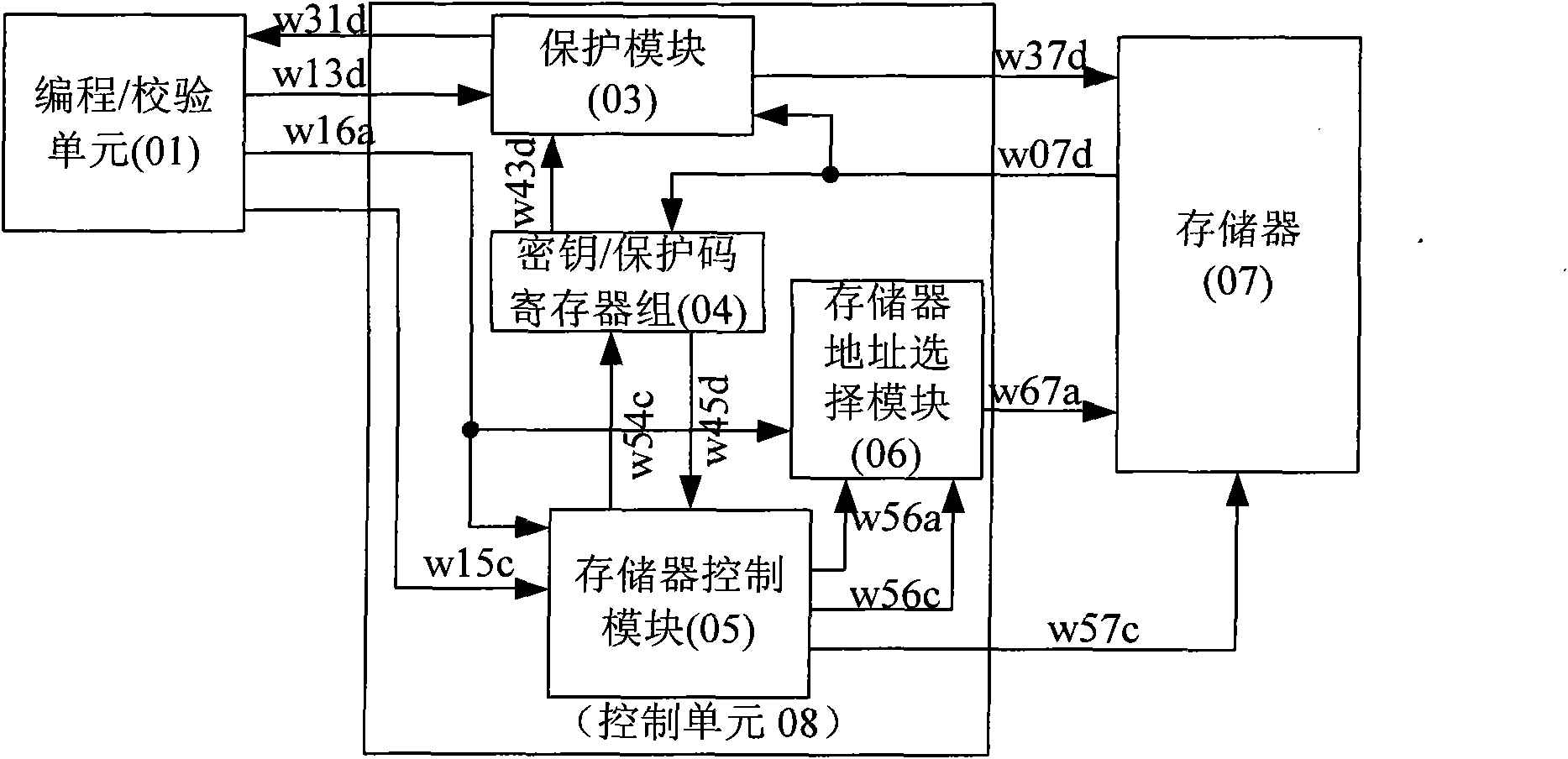
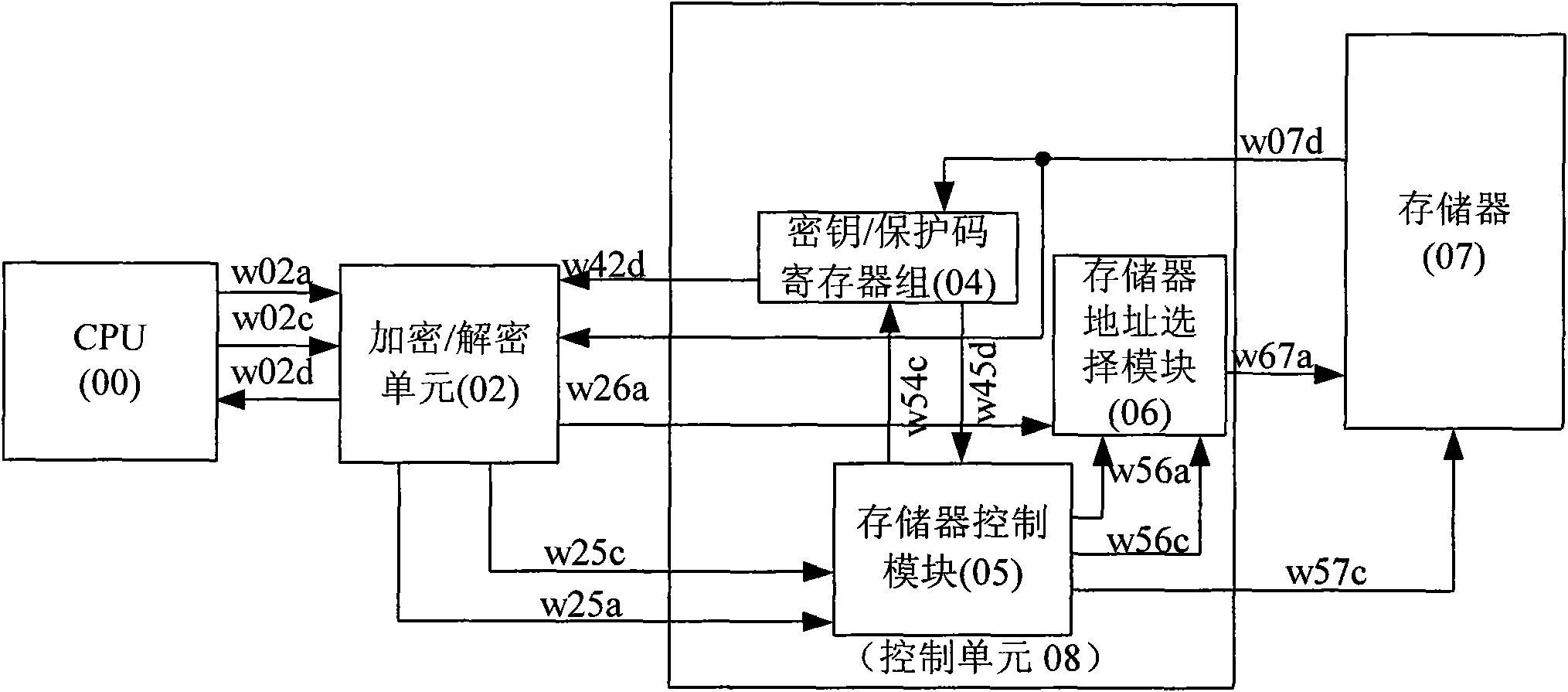
Nonvolatile memory protecting system and method
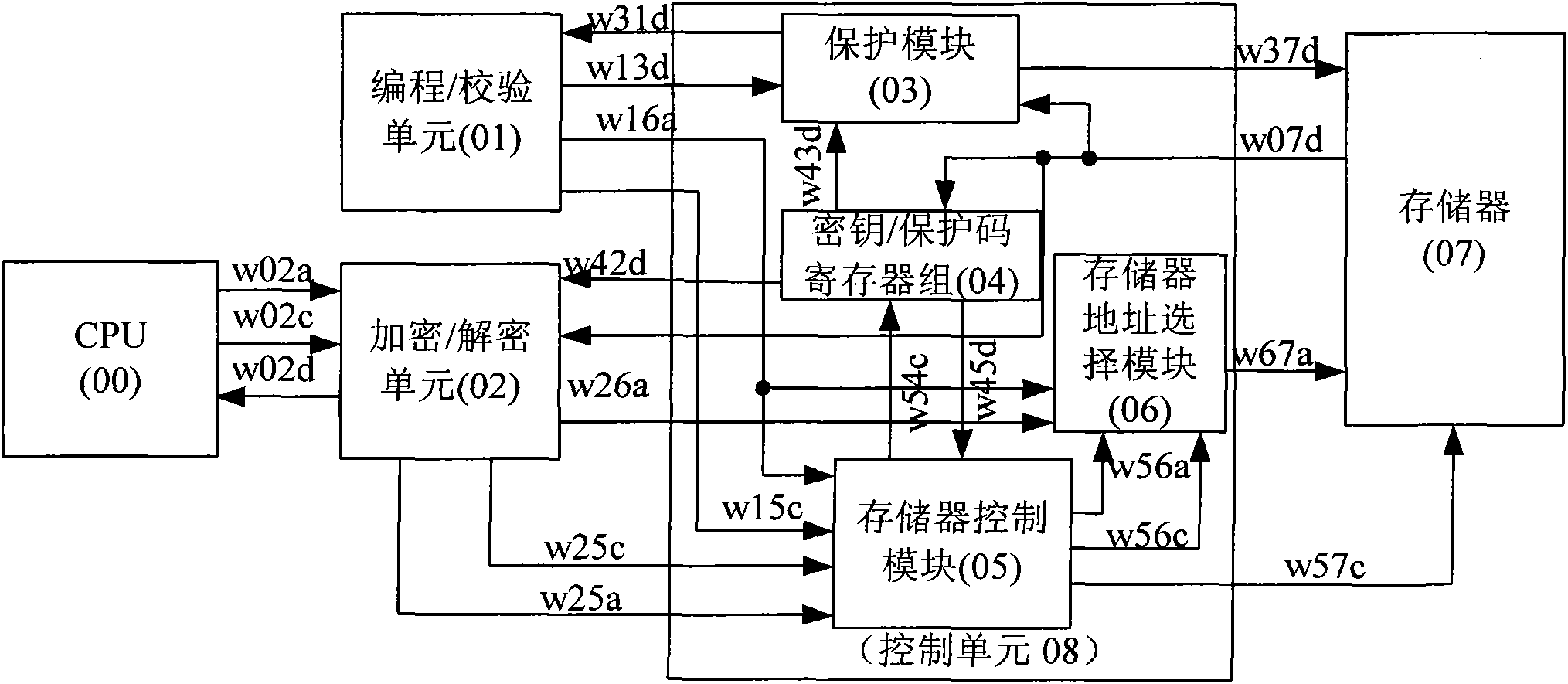
ActiveCN101901629AData/Program Check LimitsAvoid parsingUnauthorized memory use protectionDigital storageMemory addressProtected area
The invention provides nonvolatile memory protecting system and method. The method comprises the following steps of: calling a protecting code from a memory by a control unit; and limiting an unauthorized user to program or verify data / program of a protecting area. Meanwhile, the data input into the memory is encrypted data; the nonvolatile memory protecting system realizes that different memories have different keys, is not limited to one encrypting method and can provide different key protections for different addresses; if the key needs to be modified, the operation is carried out just by programming without replacing hardware; in the invention, an address encrypting key is used for encrypting the memory address, and the data of the unauthorized user for accessing the memory address is scrambling data; and a data / program decrypting key is used for decrypting the data / program of the memory, thereby preventing the unauthorized user from illegally obtaining the data and resolving.
Owner:HANGZHOU SILAN MICROELECTRONICS
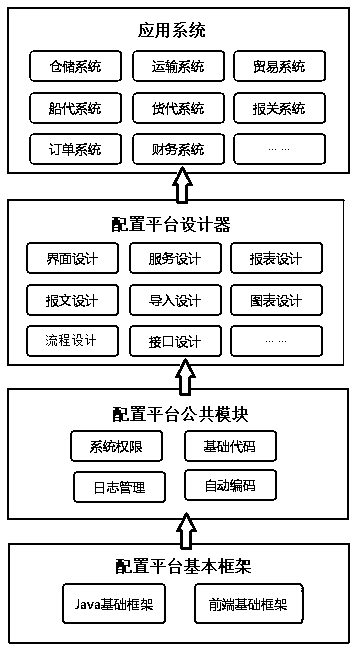
Enterprise information management system configuration platform based on JavaWeb
ActiveCN110673848AShorten development timeReduce the amount of source codeDatabase management systemsSoftware designData displaySystem configuration
The invention provides an enterprise information management system configuration platform based on JavaWeb. The platform comprises a service designer which is used for the definition, execution and monitoring of the external business logic; an interface designer used for reading a data source or an external data report designer and generating a report through an Excel template, a data display control and the data source; a chart designer used for performing chart design in combination with the data source in a visual form; a process designer used for supporting the complex business process definition; an interface designer used for butting with an external system in an interface manner through the data source; and an import designer used for designing the Excel template according to the business requirements and executing the data source to import the Excel data into the system. The enterprise information management system configuration platform based on JavaWeb is low in developmentcost, customizable in function selection and high in development efficiency.
Owner:厦门荆艺软件股份有限公司
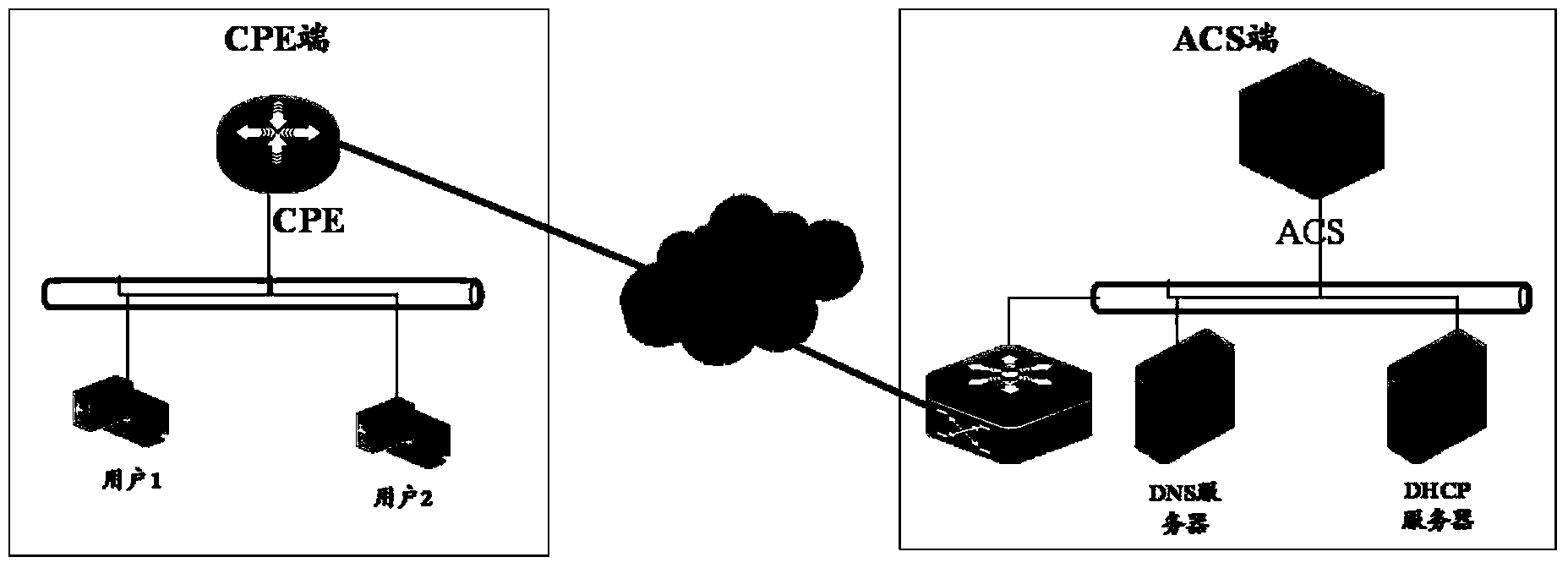
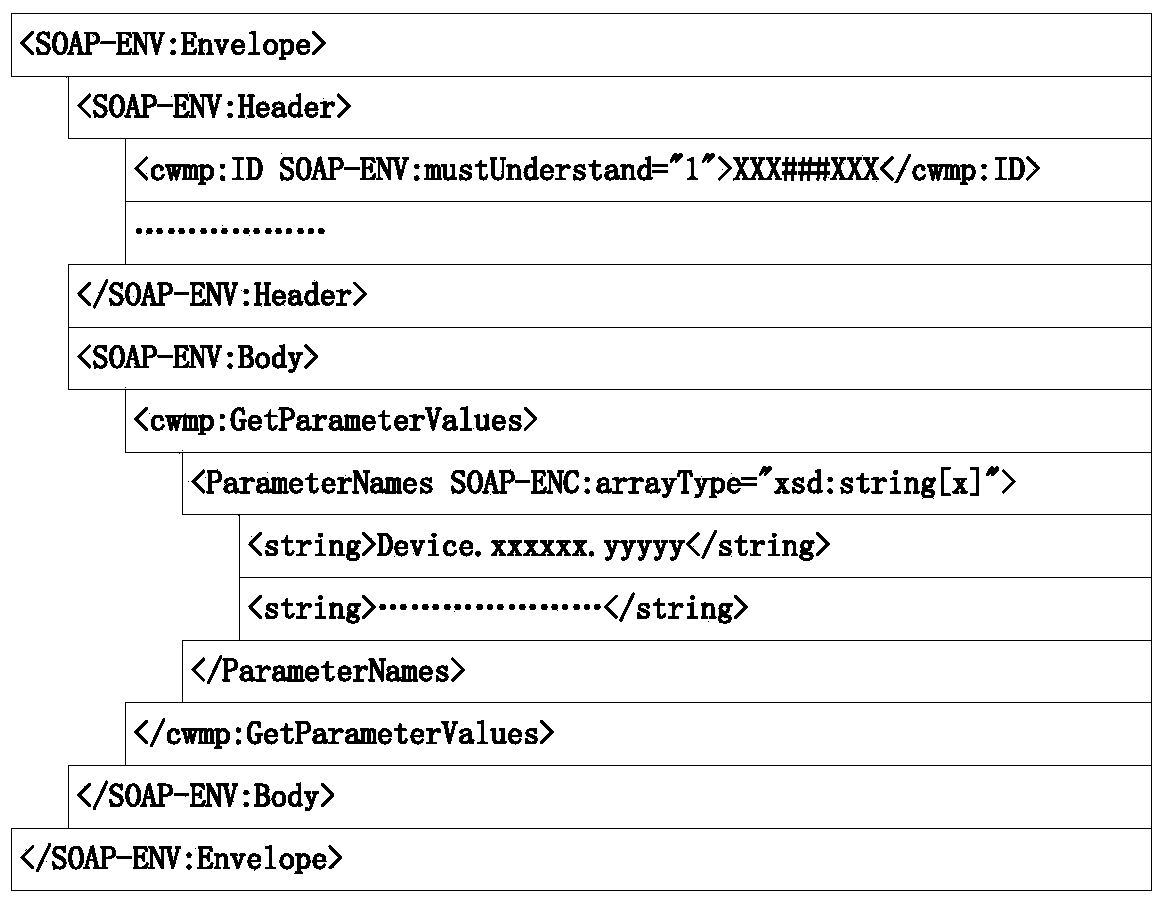
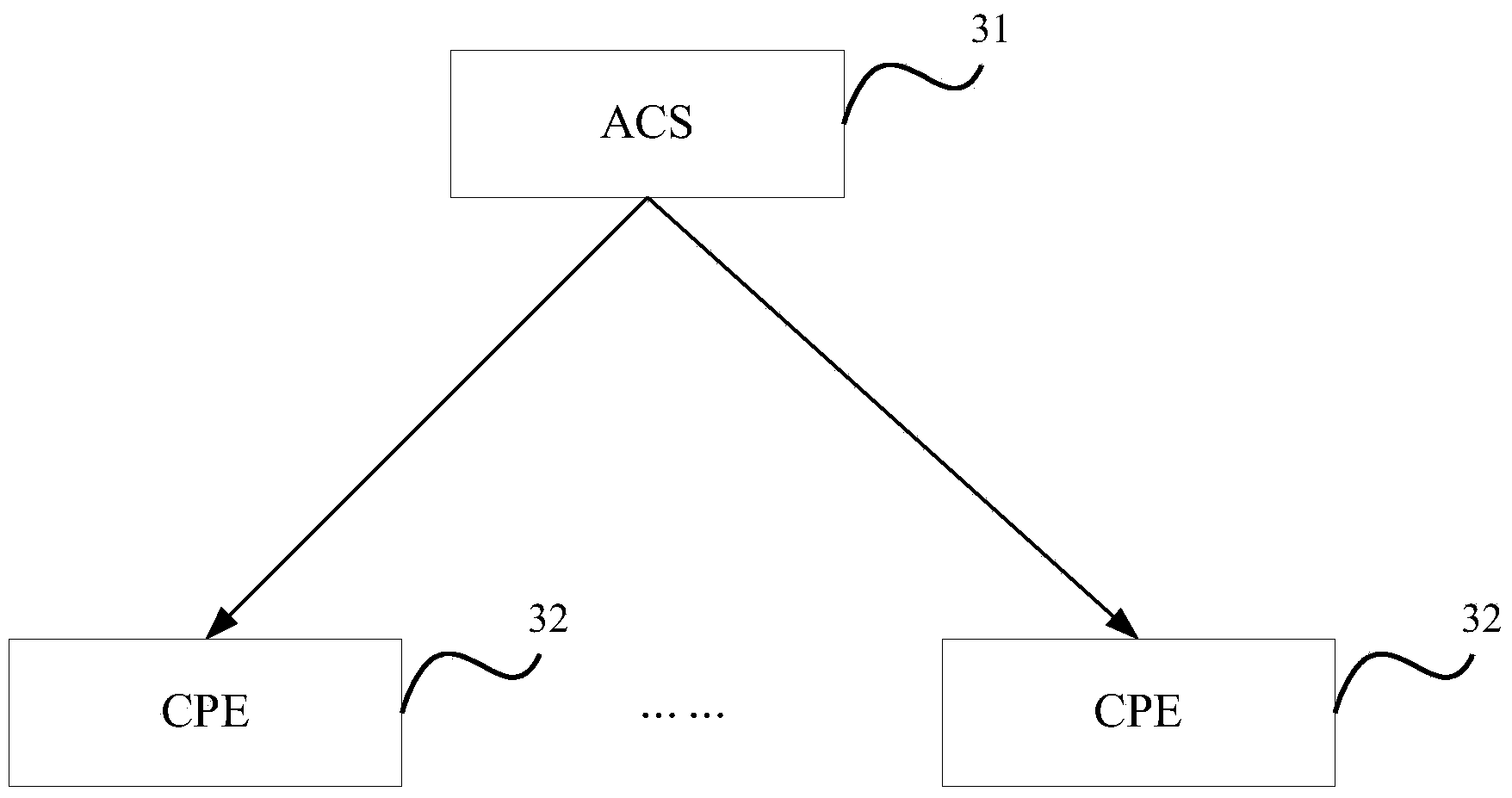
Business query method, device and system of CPE (customer premises equipment), ACS (auto-configuration server) and CPE
ActiveCN103488696AAvoid parsingAvoid screeningSpecial data processing applicationsAuto configuration serverData model
The invention discloses a business query method, a business query device and a business query system of CPE (customer premises equipment), an ACS (auto-configuration server) and the CPE, which are used for solving the problem that the processing efficiency of the ACS and the CPE is low due to the fact that the query process is complex and tedious, mass gibberish is interacted, and plenty of processing resources and network width are occupied in the existing technology for querying the business of the CPE. The business query method comprises the steps of packaging a query condition designated by a user into a request for acquiring a data model value and sending the request to the CPE designated by the user by the ACS; analyzing the received request for acquiring the data model value to obtain the query condition packaged in the request for acquiring the data model value by the CPE, and querying according to the query condition to obtain a query result conforming to the query condition; packaging the query result into a response aiming at the request for acquiring the data model value and sending the response to the ACS; analyzing the response to obtain a query result packaged in the response by the ACS.
Owner:RUIJIE NETWORKS CO LTD
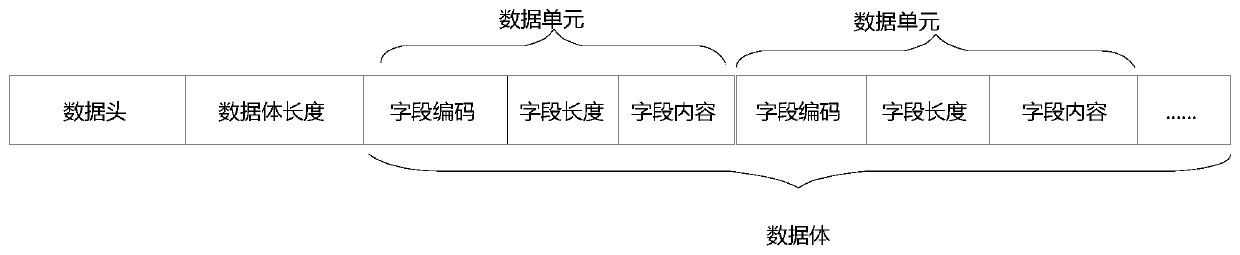
A communication text data transmission method based on a TCP protocol
ActiveCN109818930AAvoid parsingAvoid problems that take up large system resourcesTransmissionClient-sideData transmission
The invention discloses a communication text data transmission method based on a TCP protocol. text data is transmitted at the client and the server through Message format customizing; the text data is converted into a format of a data unit and then transmitting the text data; a message comprises a data header, a data body length and a data body; the Data head is taken as positioning mark, the data body length records the byte number of the space occupied by the data body; The data body is composed of a plurality of data units. each data unit comprises a field code, a field length and a fieldcontent, all data in the message is in a binary format, the field codes of the data head, the data length and the data unit are binary numbers with fixed lengths, and the analysis of the text data isrealized by establishing a field name and a field code.
Owner:广州禹龙信息科技有限公司
Two-dimensional code, and generation method and identification method thereof
InactiveCN104636784AAvoid Information LeakagePrevent leakageRecord carriers used with machinesTheoretical computer scienceSoftware
The invention provides a two-dimensional code. The two-dimensional code comprises a plaintext information part and a ciphertext information part, wherein the plaintext information part is used for downloading address information for APP (Application) identification software used for analyzing the two-dimensional code; the ciphertext information part comprises enciphered information which is enciphered and consists of a character or a plurality of identical characters. A method for generating the two-dimensional code comprises the following steps: setting the application range of the two-dimensional code; inputting information contents needing to be enciphered, and converting the information contents into character string information of corresponding positional notation; enciphering the character string information to form the enciphered information; combining the mark number of application range identifier information, the mark number of enciphered mode instruction information and the enciphered information into the ciphertext information part; generating the two-dimensional code through the plaintext information part and the ciphertext information part. The plaintext information part can remind a user to download and install special two-dimensional code APP identification software used for analyzing the ciphertext information part so as to acquire the information contents corresponding to the ciphertext information part.
Owner:LEADER TECH BEIJING DIGITAL TECH
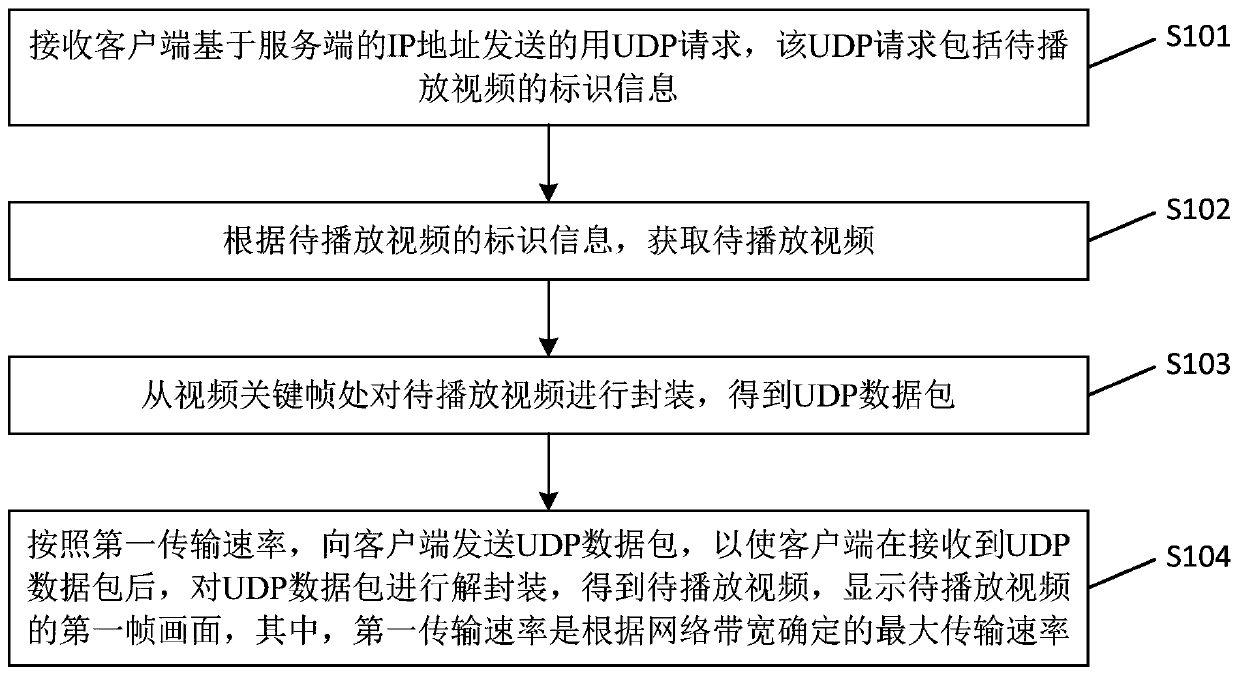
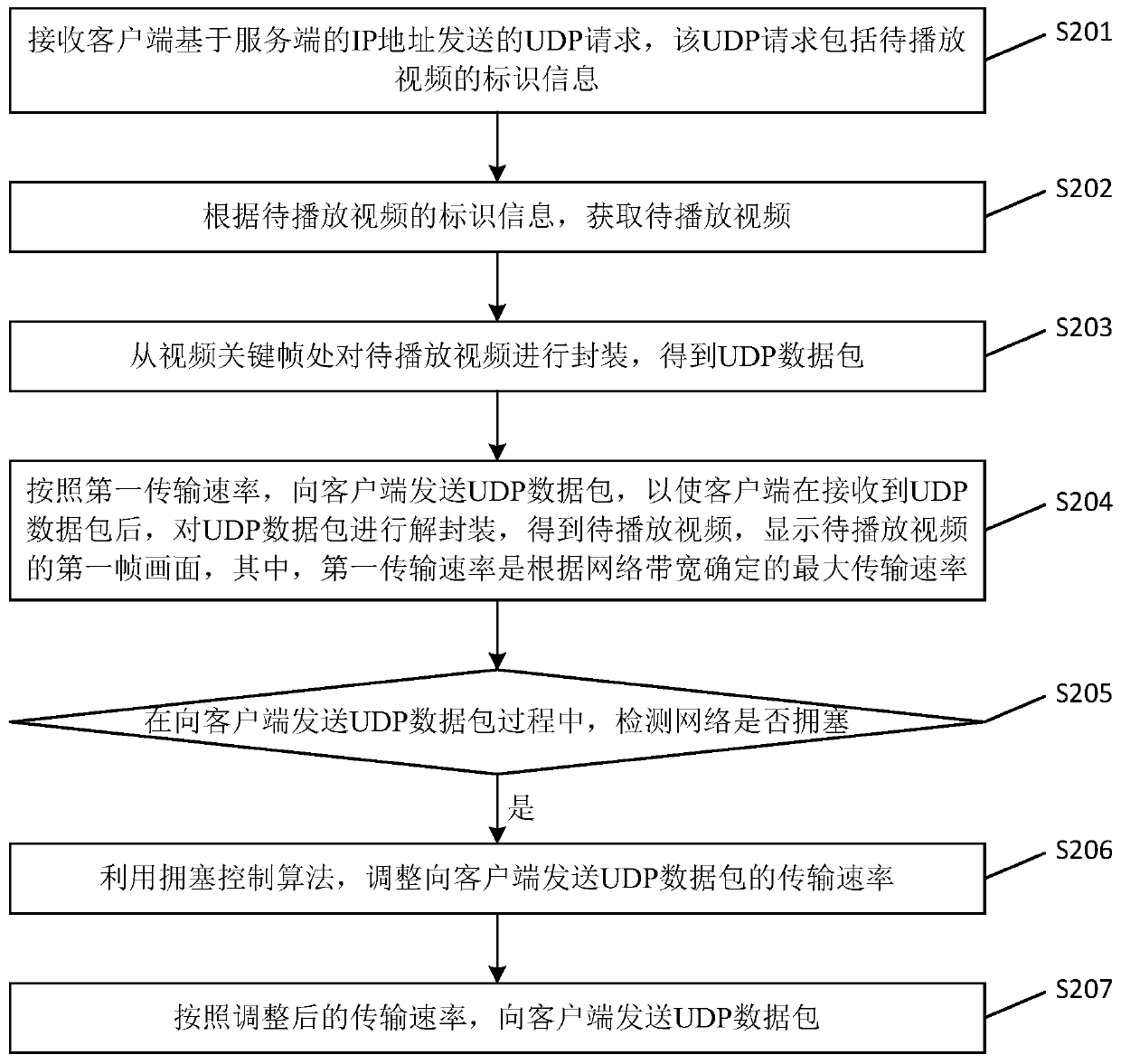
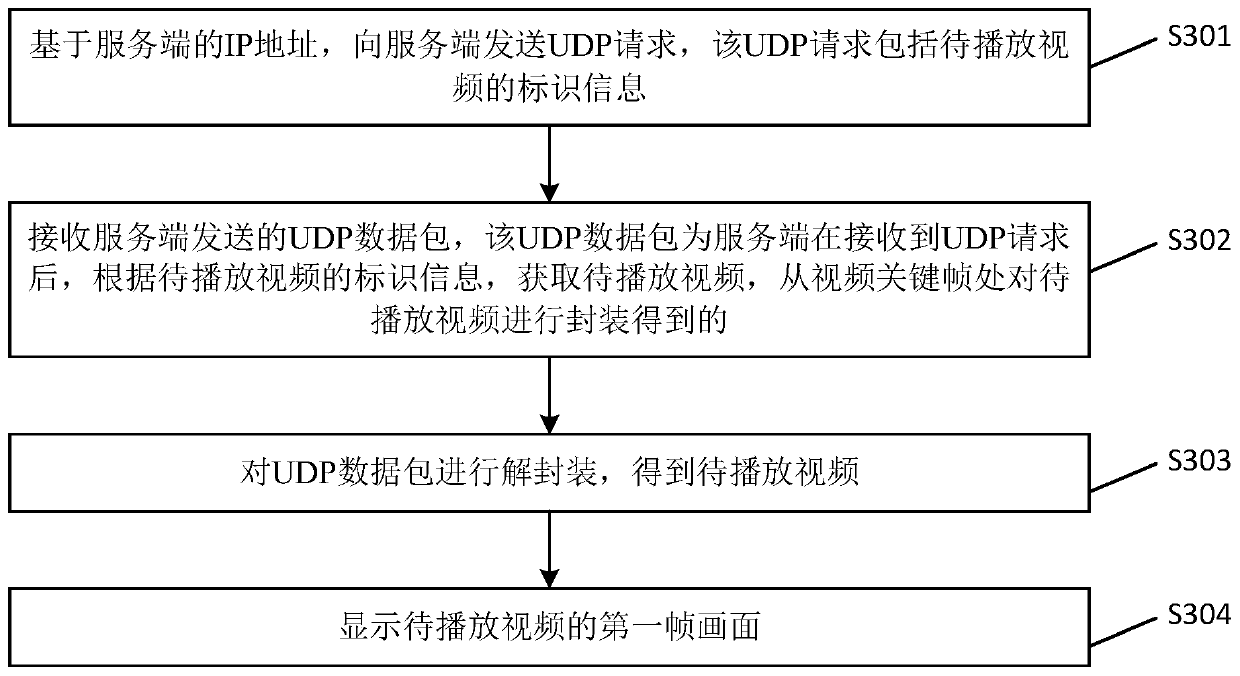
Video picture display method and device, electronic equipment and storage medium
ActiveCN110557655AAvoid parsingShort timeTransmissionSelective content distributionIp addressNetwork packet
The embodiment of the invention provides a video picture display method and device, electronic equipment and a storage medium. The method includes: enabling a server to receive a UDP request sent by aclient based on an IP address of the server, wherein the UDP request comprises identification information of a to-be-played video; obtaining a to-be-played video according to the identification information of the to-be-played video; packaging the to-be-played video from the video key frame to obtain a UDP data packet; and sending the UDP data packet to the client according to the first transmission rate, so as to enable the client to decapsulate the UDP data packet after the client receives the UDP data packet to obtain a to-be-played video, and displaying a first frame of picture of the to-be-played video, the first transmission rate being the maximum transmission rate determined according to the network bandwidth. Through the technical scheme provided by the embodiment of the invention,the display time of the first frame of image of the video is shortened, and the display speed of the first frame of image of the video is improved.
Owner:JOYME PTE LTD
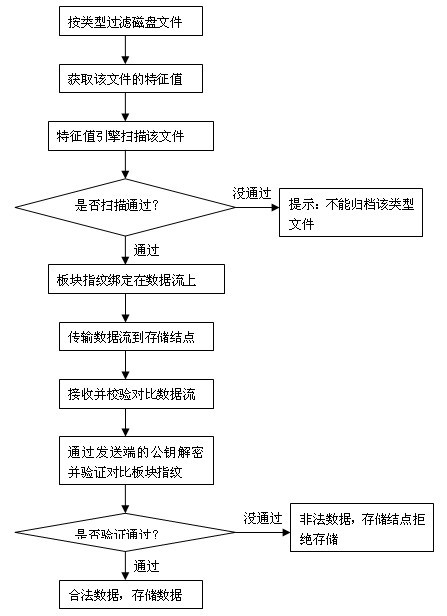
Method for deeply analyzing data based on white list mechanism
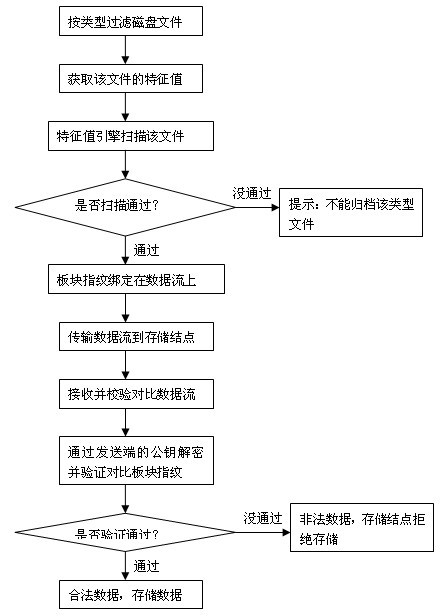
The invention discloses a method for deeply analyzing data based on a white list mechanism, comprising the following steps: building a white list, building a matching feature code list, reading a data file to be analyzed, inspecting whether a register item corresponding to the type of the file exists in the white list, reading the feature code of a file inspected by the white list, generating a block fingerprint, bonding the block fingerprint on data steam, transmitting the data steam to a storage node, receiving the data steam, checking and comparing the data steam, deciphering with a public key at a transmitting end and checking the block fingerprint, and judging that the decrypted block fingerprint is the same as the block fingerprint bonded on the data steam. The method has the beneficial effects that the defects in the prior art are overcome, the drawbacks of the existing file analyzing and filtering method are avoided, and the method for deeply analyzing the data based on the white list mechanism is provided.
Owner:成都东方盛行电子有限责任公司
Data flow identification method and device
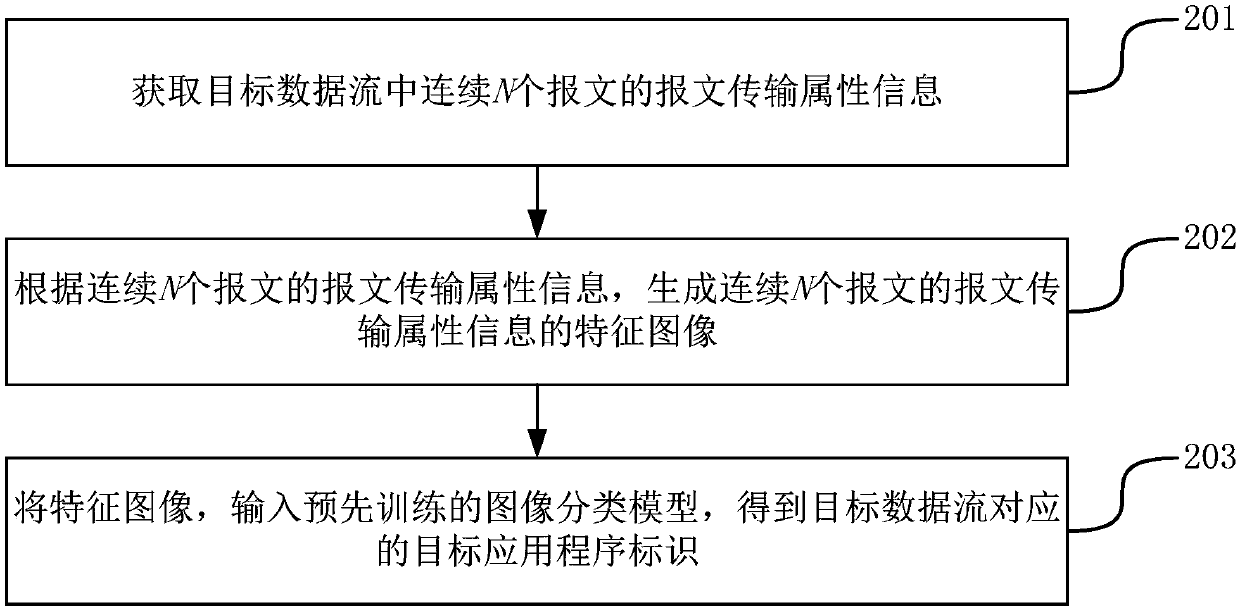
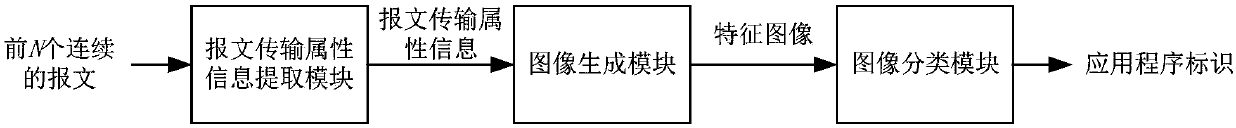
ActiveCN109905328AImprove accuracyAvoid parsingImage analysisCharacter and pattern recognitionData streamThe Internet
The invention provides a data flow identification method and device, and belongs to the technical field of the Internet. The method comprises the following steps: acquiring message transmission attribute information of N continuous messages in a target data stream; generating a feature image of the message transmission attribute information of the continuous N messages according to the message transmission attribute information of the continuous N messages; and inputting the feature image into a pre-trained image classification model to obtain a target application identifier corresponding to the target data flow. Through the application, the accuracy of identifying the application identifier corresponding to the data stream can be improved.
Owner:HUAWEI TECH CO LTD
Binlog analysis method
ActiveCN107291926AAvoid parsingAutomatically modify field typesDatabase updatingDatabase distribution/replicationCouplingAnalysis method
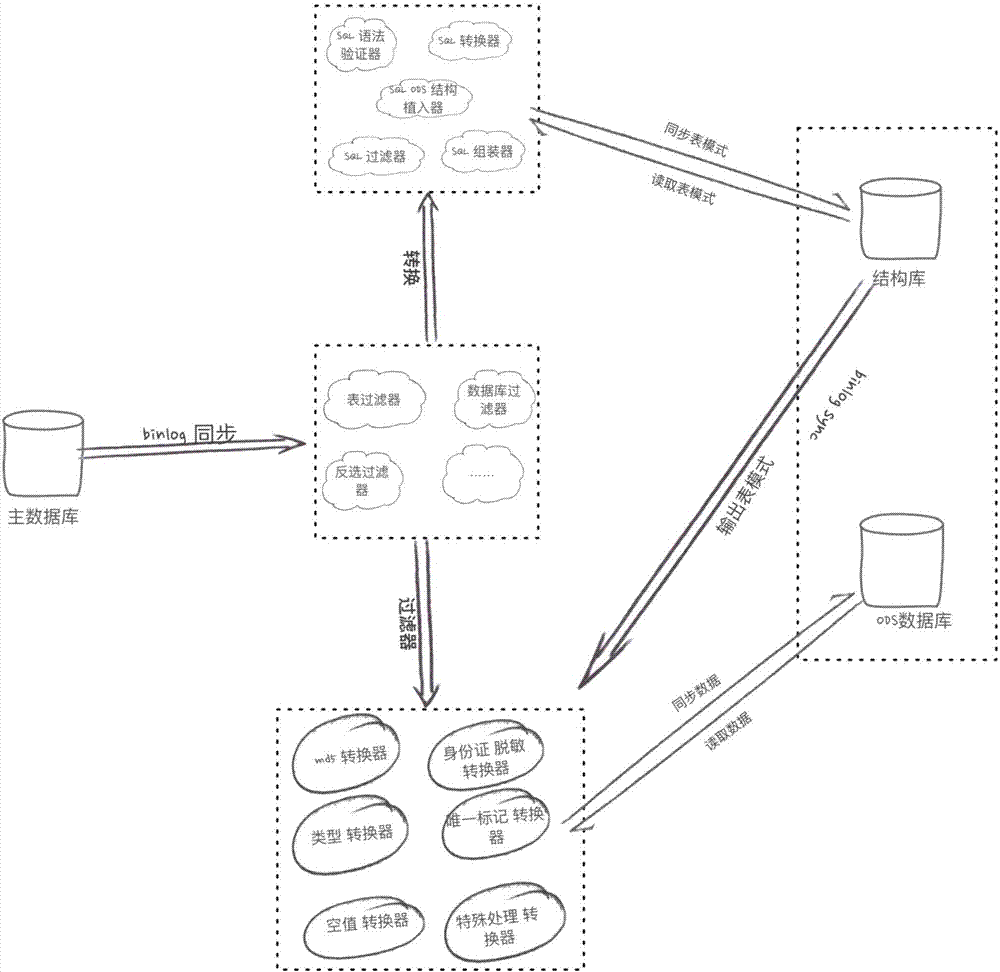
The invention provides a binlog analysis method. The method includes following steps: step 1, creating SDB and ODB to realize alternation and separation of structure and data; step 2, reading and executing configuration for a synchronous program; step 3, running the program, synchronizing data, and altering data; step 4, exiting the program, and recording a binlog file and binlog recording points. Aiming at ODS needs, automatic coupling of data structure with ODS structure, data chain stretching is realized during data synchronizing, and ODS basic data are constructed.
Owner:搜易居(北京)网络技术有限公司
Activiti-based business event and flow separation method and system
InactiveCN106971293ASolving Data ChaosAvoid processing failuresOffice automationXml dataState of art
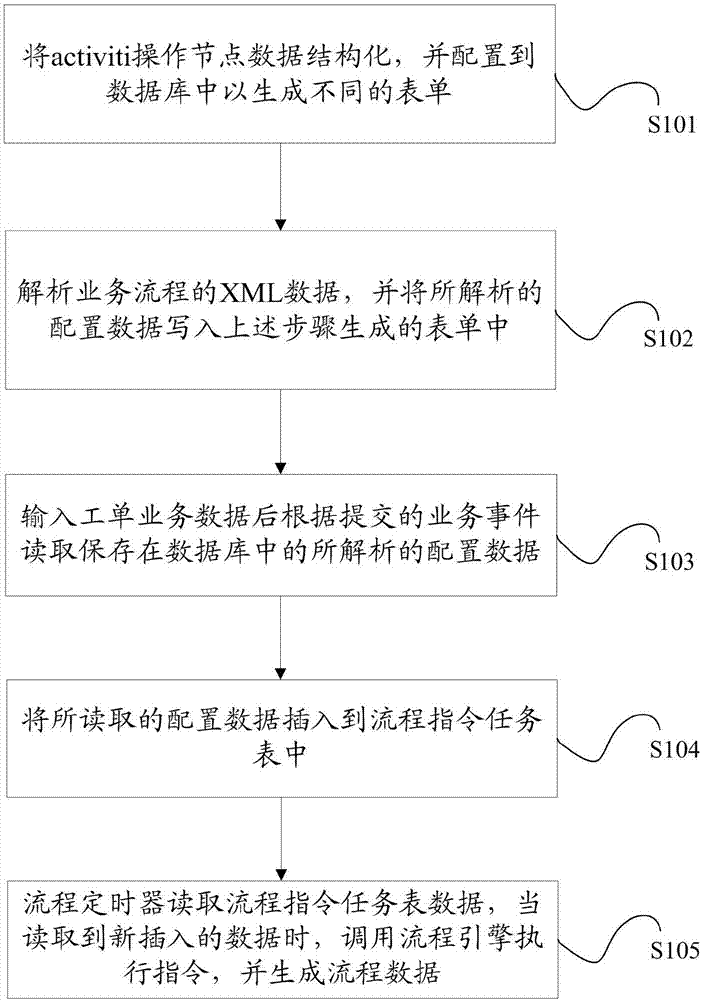
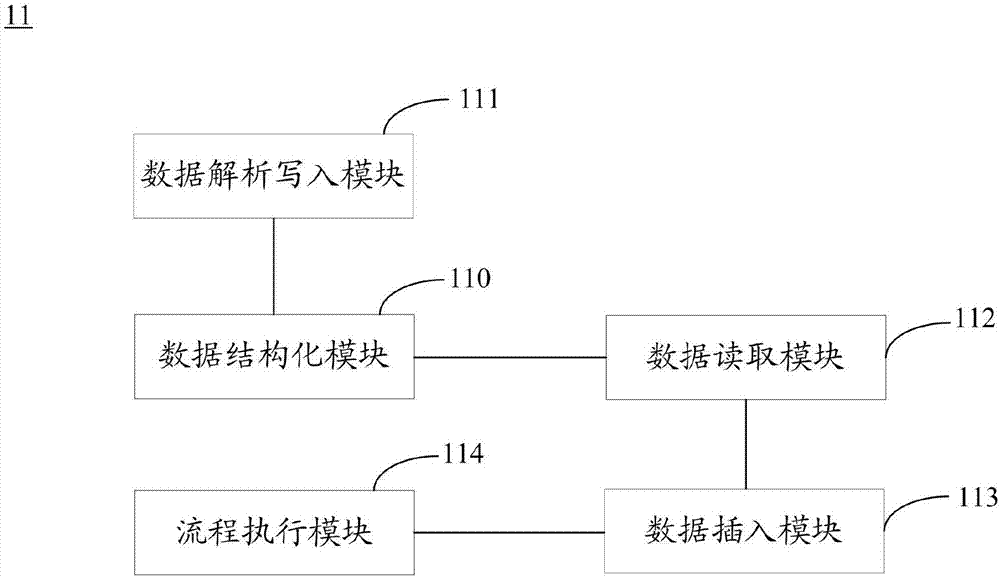
The present invention discloses an activiti-based business event and flow separation method. The method includes the following steps that: activiti operation node data are structurized, and the structurized data are configured into a database so as to generate different forms; and the XML data of a business flow are analyzed, the analyzed configuration data are written into the forms generated in the above step. According to the activiti-based business event and flow separation method of the invention, the operation node data are structurized in the database; the specific forms formed by the structurized data are read; the XML data of the business flow are analyzed, and the analyzed data are written into the above generated forms; and therefore, the separation of business processing from the business flow can be realized, business can be independent from a flow line for analyzing the customized XML of the activiti in a processing process, the analysis of the XML data which is performed each time when business is processed can be avoided, the problem of data chaos caused by XML analysis can be solved, the problem of the failure of the business processing caused by the anomalies of the flow can be solved, and the update of the flow can be updated through modifying the configuration data. The invention also provides an activiti-based business event and flow separation system.
Owner:GUANGDONG ESHORE TECH
Method, device and system for measuring video flow performance
ActiveCN101662680ARealize detectionAvoid parsingTelevision systemsDigital video signal modificationMeasurement devicePacket loss
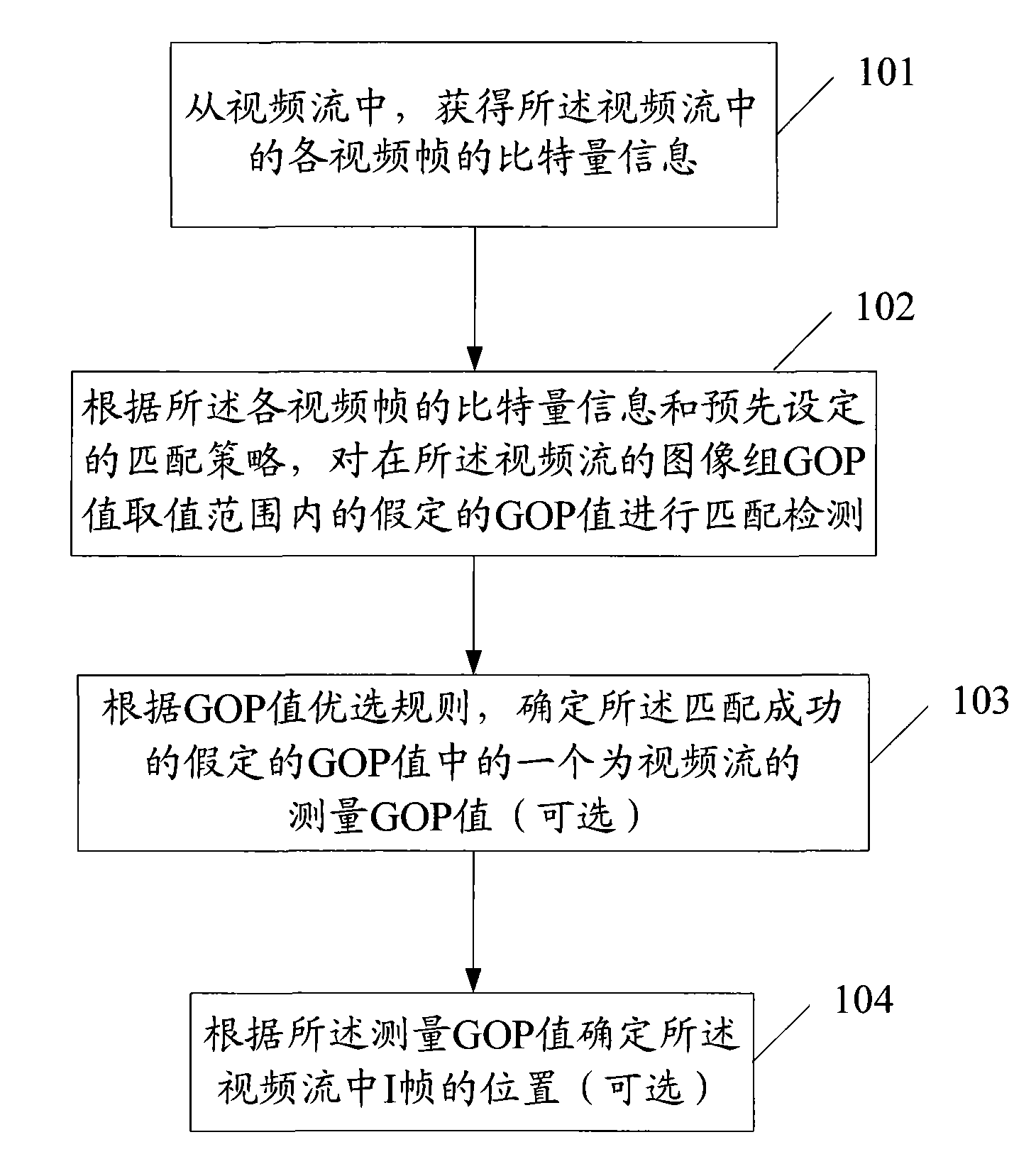
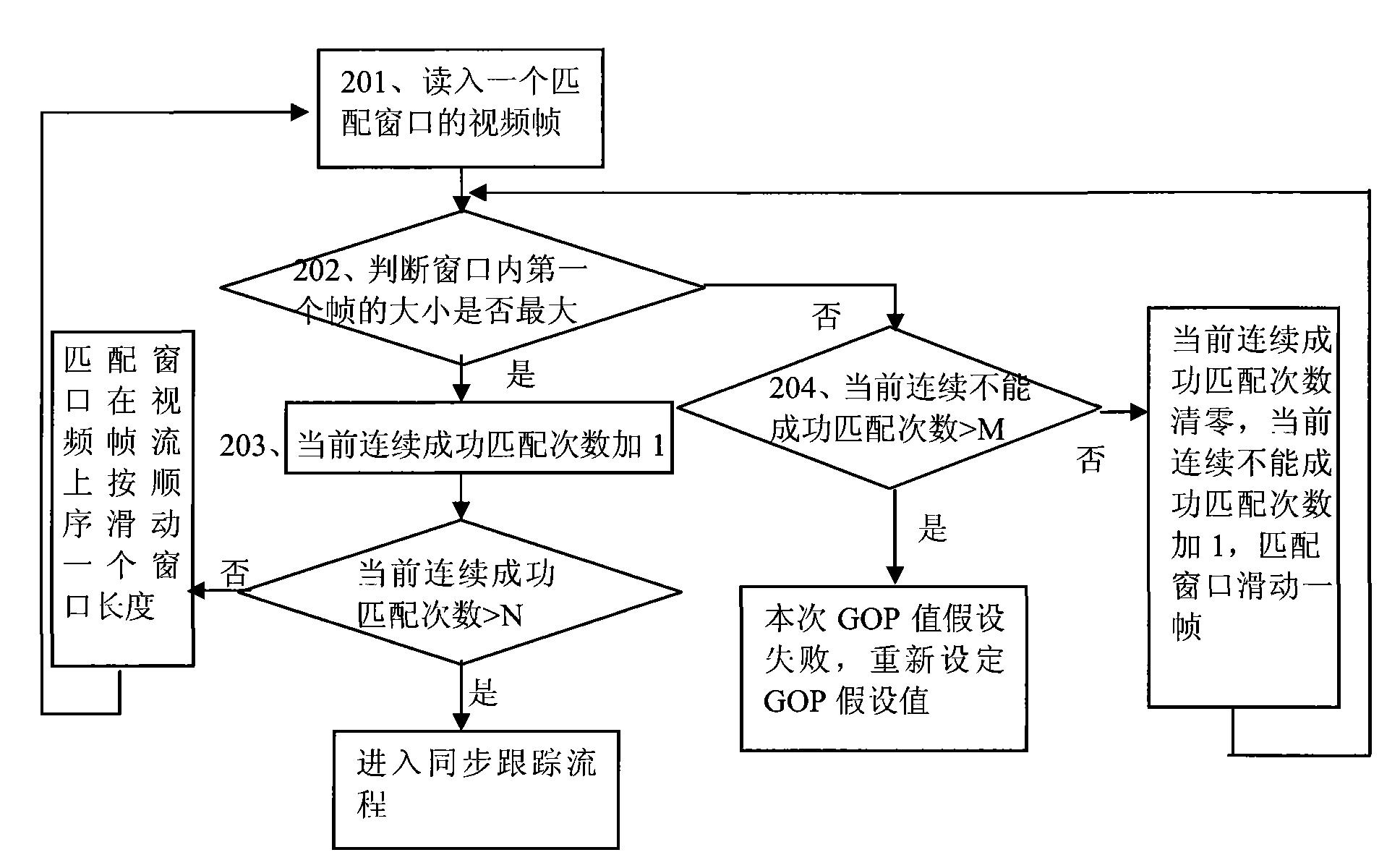
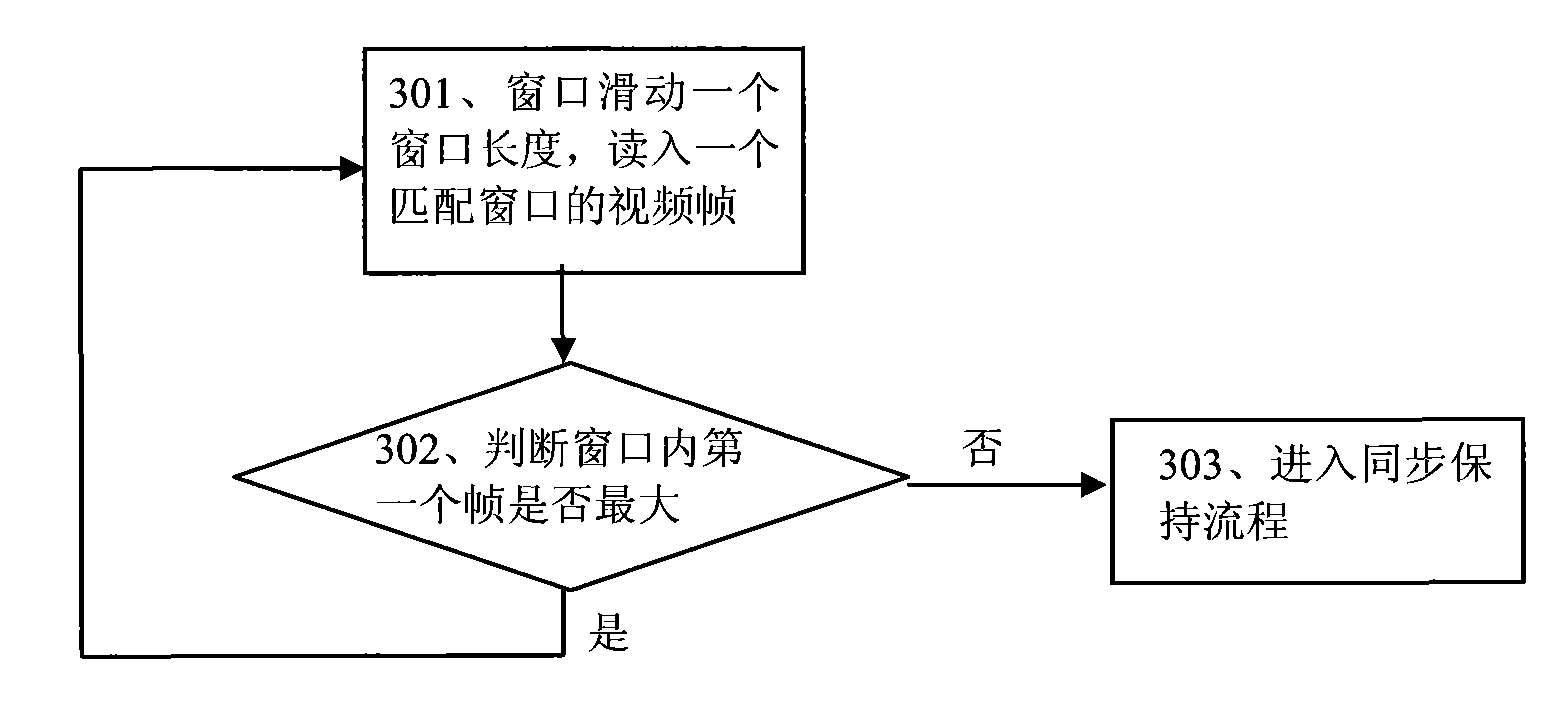
The invention discloses a device and a method for measuring video flow performance and a packet loss method. The method for measuring video flow performance comprises the following steps: acquiring bit quantity information of all video frames in the video flow; carrying out matching detection on the assumed Group of Picture (GOP) value within the GOP value span of the video flow according to the bit quantity information of the video frames and the preset matching plan; and if the matching is successful, the assumed GOP value is the GOP value corresponding to the video flow. In the scheme, theGOP value is acquired by carrying out the matching detection according to the bit quantity information of the video frames without analyzing all the frames so as to avoid decoding, excessive dependence on the transport protocol, excessive dependence on the deep protocol analysis and the problems of enciphering, copyright and the like. Thus, the measuring equipment arranged in the network can detect the GOP value of the video sequence at low cost.
Owner:泰州市海通资产管理有限公司
Exhaust recycling technology in production process of polycrystalline silicon
ActiveCN105565323ASimple recycling processReduce loadHydrogen separationHalogenated silanesHydrogenDichlorosilane
The invention discloses an exhaust recycling technology in the production process of polycrystalline silicon. The exhaust recycling technology comprises the following steps that under the catalytic action of a first catalyst, exhaust is subjected to a reaction generated by hydrogen chloride and dichlorosilane in the exhaust, and a first mixture is obtained; the first mixture is cooled to minus 5-55 DEG C, and a first liquid mixture and a first gas mixture are obtained; under the catalytic action of a second catalyst, the first gas mixture is subjected to a reaction generated by dichlorosilane and silicon tetrachloride in the exhaust, and a second mixture is obtained; the second mixture is cooled to be minus 40-minus 10 DEG C, and a second liquid mixture and a second gas-liquid mixture are obtained; the second gas-liquid mixture is subjected to gas-liquid separation, and a third gas mixture and a third liquid mixture are obtained, wherein the main component of the third gas mixture is hydrogen. The phenomena that in the recycling technology in the prior art, hydrogen chloride in the exhaust is absorbed and resolved, and dichlorosilane in the exhaust enters subsequent chlorosilane rectification purification are avoided.
Owner:XINTE ENERGY
POSS (polysilsesquioxane)-containing polymerizable surfactant and preparation method thereof
InactiveCN103071427AAvoid parsingInhibit migrationTransportation and packagingMixingGel preparationEmulsion
The invention discloses a POSS (polysilsesquioxane)-containing polymerizable surfactant and a preparation method thereof. The POSS-containing polymerizable surfactant takes POSS as a hydrophobic terminal, a polyethylene glycol molecule as a hydrophilic chain terminal and maleate as a double-bond intermediate chain, so that desorption of the POSS-containing polymerizable surfactant and migration thereof in a film can be effectively avoided, and the POSS-containing polymerizable surfactant has a very significant application value in improving the rheological property and the stability of an emulsion and the glossiness and the water resistance of a coating film, solving a water pollution problem caused by the residual surfactant in gel preparation of a solid product and the like. The preparation method of the POSS-containing polymerizable surfactant comprises one-step amidation and one-step esterification based on maleic anhydride, and is simple in process, mild in reaction condition and high in yield.
Owner:泉州鲁新新型建材有限公司
Management control communication method and equipment
InactiveCN104125097AAvoid understandingReduce couplingData switching networksManagement information baseManagement object
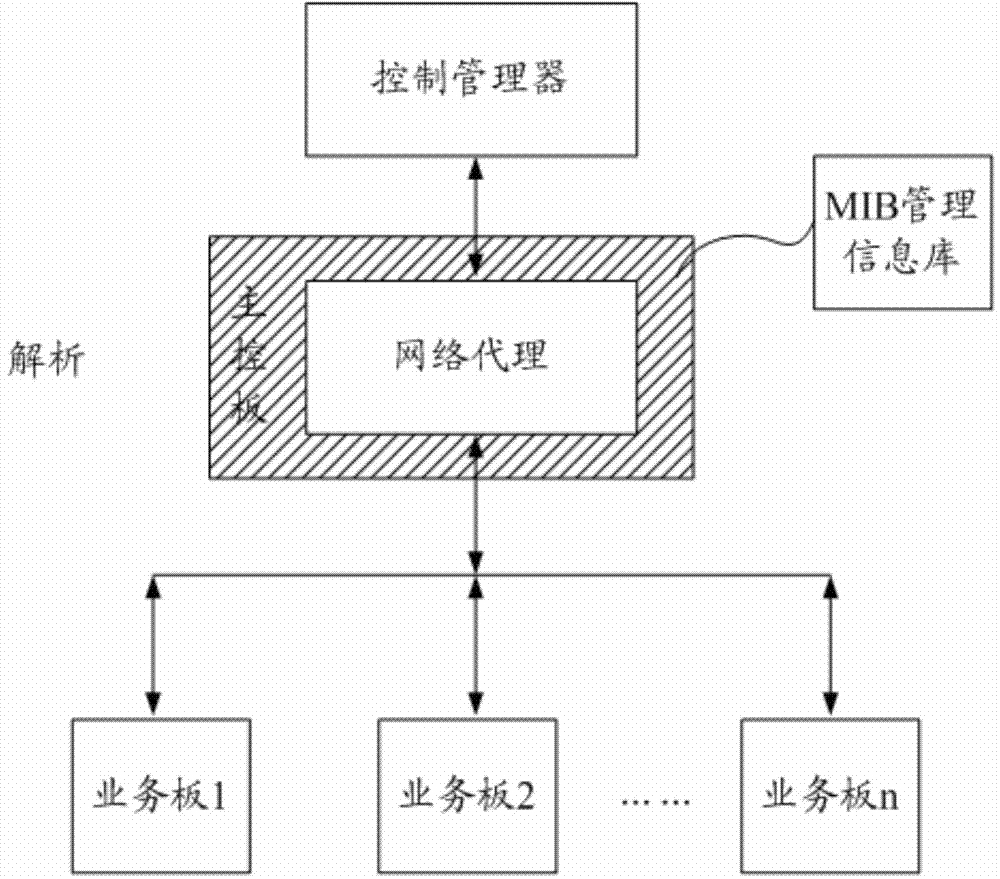
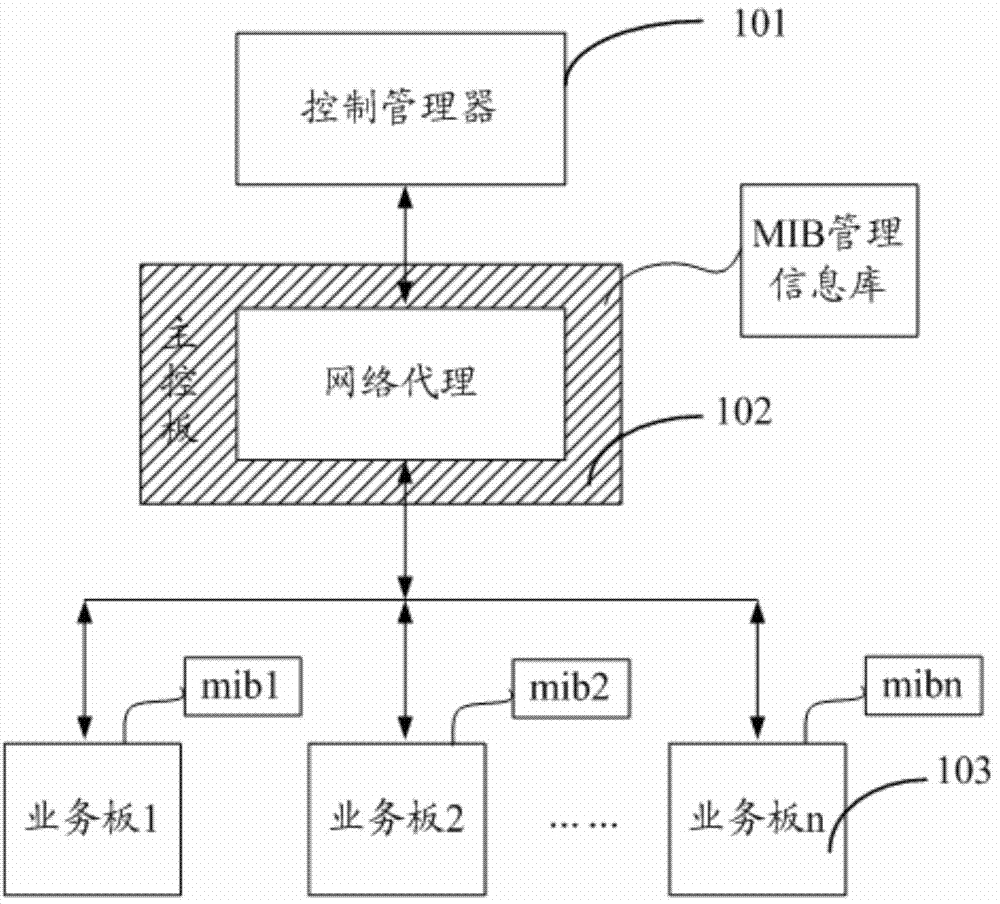
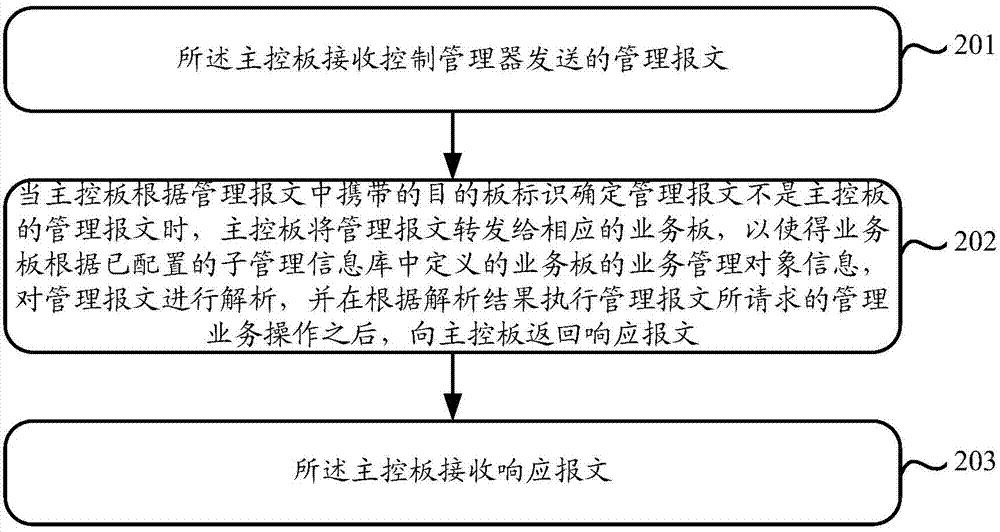
The invention discloses a management control communication method and equipment. The management control communication method mainly includes that a business board receives a management message, analyzes the management message according to business management object information of the business board defined in a configured sub-management information base, and returns a respond message to a main control board after executing the management business operation of the management message according to the analyzed result, wherein the management message is transmitted by the main control board when the main control board confirms that the management message is not the management message thereof according to an object board identification in the management message sent from a control manager. The management control communication method prevents the main control board understanding business functions of the business board; each business board is provided with the corresponding sub-management information base, so that the business management coupling relationship between the main control board and each business board is reduced.
Owner:RAISECOM TECH
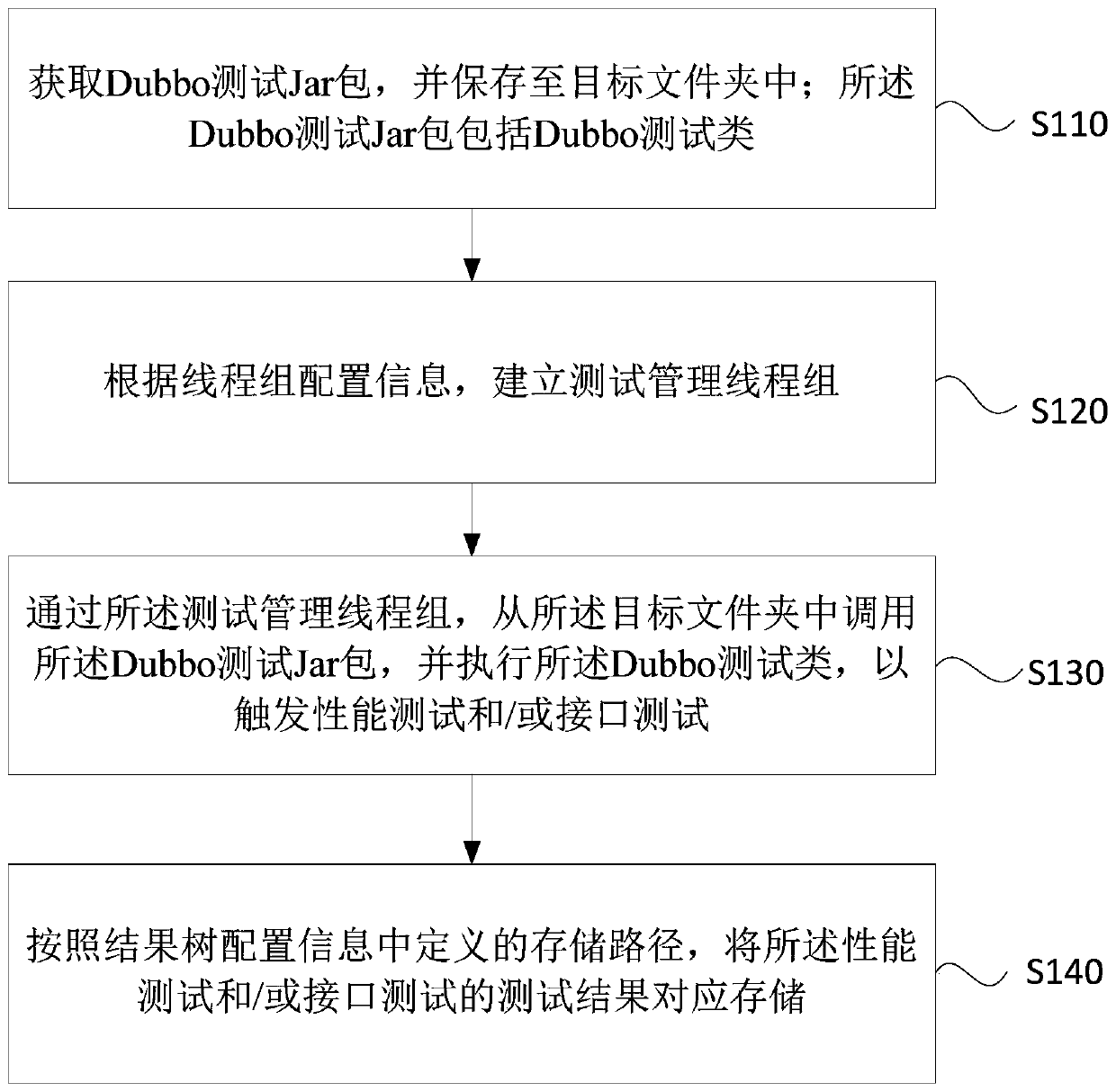
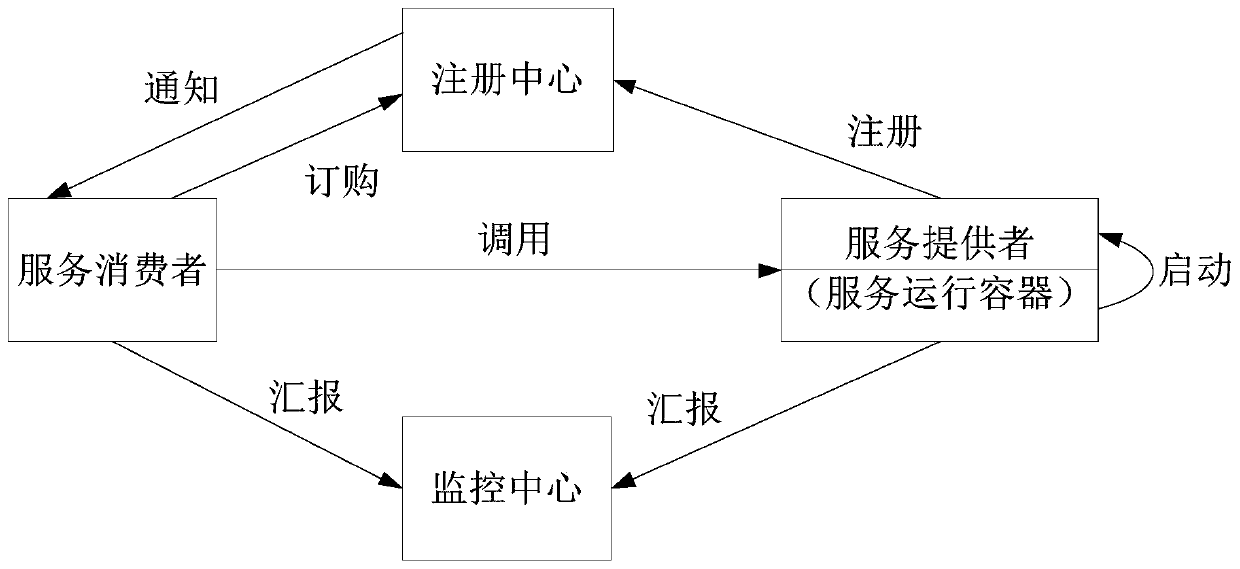
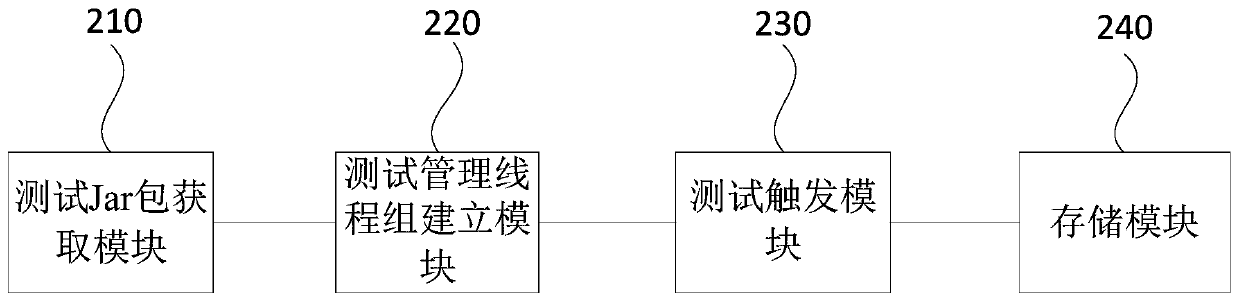
Software project testing method and device, equipment and storage medium
The embodiment of the invention discloses a software project test method and device, equipment and a storage medium. The method comprises the steps of obtaining a Dubbo test Jar packet; establishing atest management thread group according to the thread group configuration information; calling the Dubbo test Jar packet through the test management thread group so as to trigger a performance test and / or an interface test; and correspondingly storing the test results of the performance test and / or the interface test according to result tree configuration information. According to the technical scheme, the obtained Dubbo test Jar packet is called through the Jmeter, the Dubbo test class is executed, the interface test and / or the performance test of the Dubbo service are / is realized, and the test result obtained through the result tree configuration information already comprises detailed test data, so that the analysis of the output log is avoided, the test process is simplified, the consumption of test resources is reduced, and the test efficiency is improved.
Owner:ZHUHAI SUIBIAN TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com