System and method for implementing authentication on user of home base station
A home base station and user technology, applied in transmission systems, electrical components, safety devices, etc., can solve the problems of increased operating burden of base station nodes, inability to guarantee the correctness of user identification, and inability to analyze and obtain user identification information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
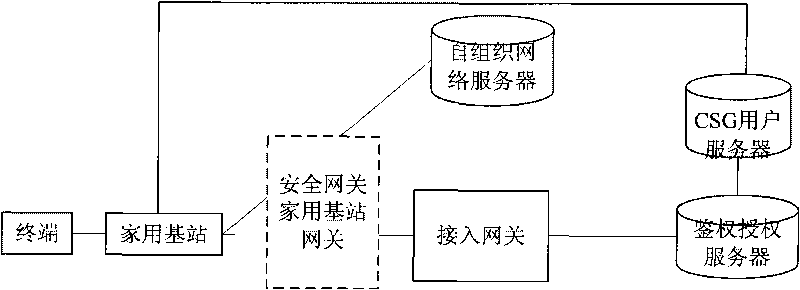
[0070] This embodiment provides a system for authenticating home base station users, such as figure 1 As shown, including: a terminal, a home base station, an access gateway, an authentication and authorization server, and a CSG user server;
[0071] The access gateway is used to send user identification information and home base station information to the authentication and authorization server when the terminal accesses the home base station in closed access mode or hybrid access mode;
[0072] The authentication and authorization server is used to judge whether the user is allowed to access the home base station when the home base station is in the closed access mode, and return the judgment result to the home base station through the access gateway; Determine the user category information when entering the mode, and return the user category information to the home base station through the access gateway.
[0073] The authentication and authorization server is used to judg...
Embodiment 2
[0129] This embodiment provides a system for authenticating home base station users, such as figure 1 As shown, including: a terminal, a home base station, an access gateway, an authentication and authorization server, and a CSG user server;
[0130] The access gateway is used to send the user identification information and the home base station information to the CSG user server through the authentication and authorization server when the terminal accesses the home base station in the closed access mode or the hybrid access mode;
[0131] The CSG user server is used to determine whether the user is allowed to access the home base station when the home base station is in the closed access mode, and returns the judgment result to the home base station through the authentication authorization server and the access gateway; In the access mode, the user category information is determined, and the user category information is returned to the home base station through the authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com