Patrol intelligent monitoring terminal and working method thereof
A technology of intelligent monitoring and working methods, which is applied in the direction of TV, color TV, cameras, etc., can solve the problems of inaccurate and efficient video acquisition, large amount of collected data, low working methods and working efficiency, etc., and achieve comprehensive monitoring effects, safe operation, wide-ranging effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
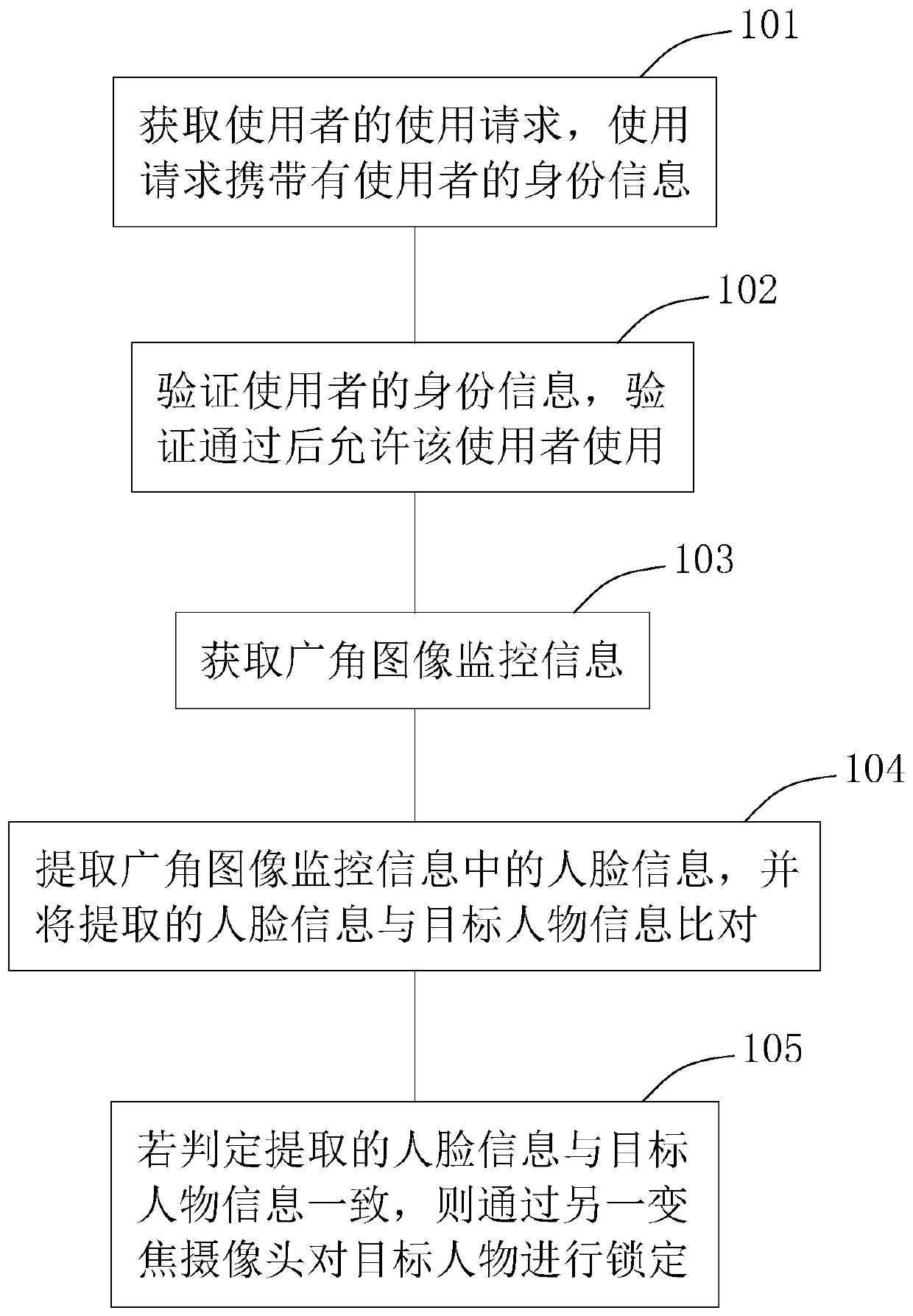
[0053] A kind of working method of patrol intelligent monitoring terminal, refer to figure 1 , including step S101 to step S105.
[0054] Step S101: Obtain a user's use request, which carries the user's identity information.
[0055] Obtaining the user's use request can be the user's fingerprint information, or information corresponding to the user's identity such as the account number and password information requested by the user. After obtaining such information, the user's use request is obtained. Request, the identity information is the unique identity corresponding to the fingerprint information or account password information.
[0056]Step S102: verify the identity information of the user, and allow the user to use after the verification is passed.
[0057] The user's identity information is compared with the information of the usable terminal preset in the database, and if it belongs to the permission information stored in the database, the user has passed the verifi...
Embodiment 2
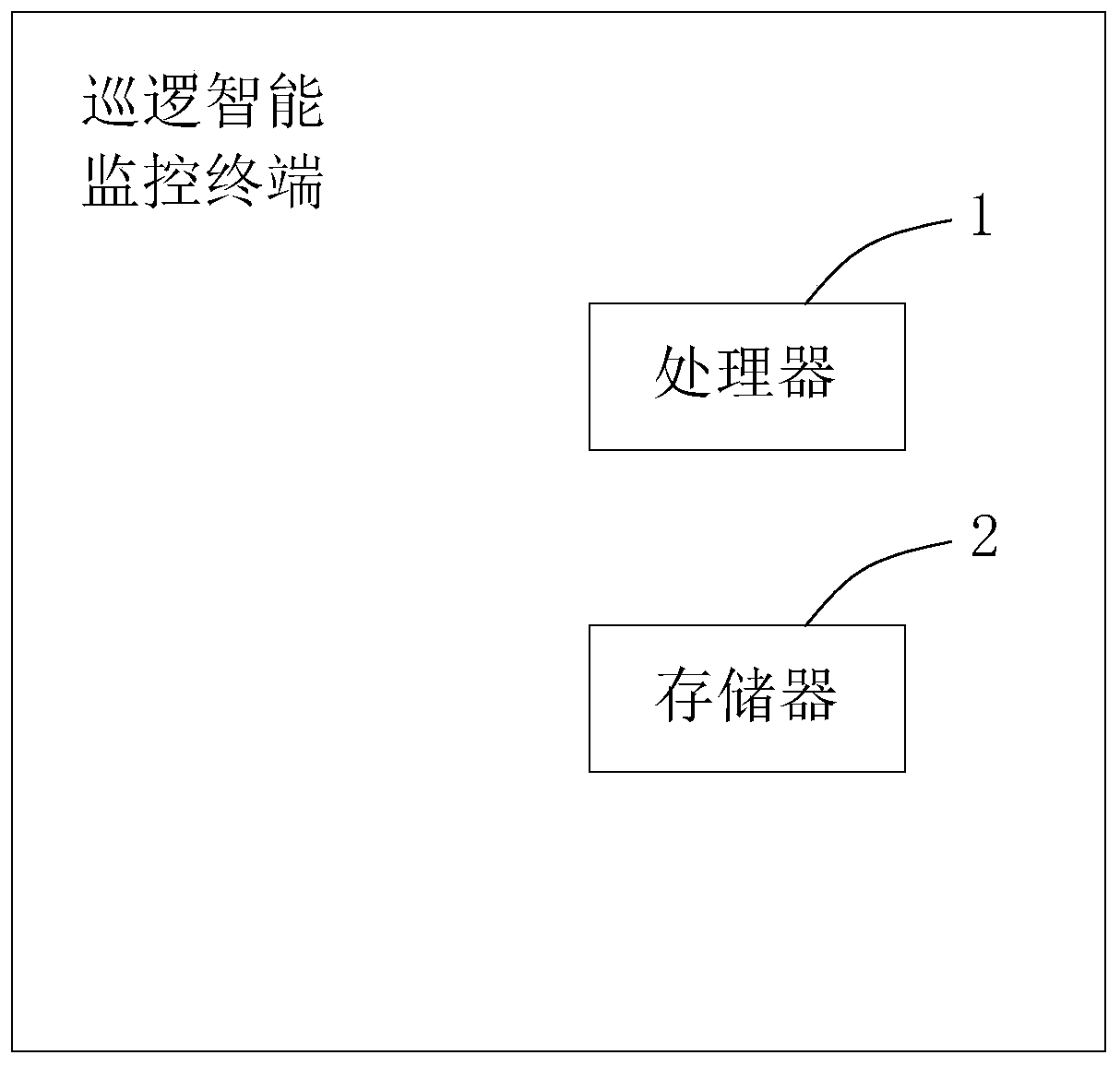
[0071] A patrol intelligent monitoring terminal, refer to figure 2 , including a processor 1 and a memory 2, the memory 2 stores an instruction set for the processor 1 to call to realize the following functions:
[0072] Obtain the user's use request, which carries the user's identity information;
[0073] Verify the identity information of the user, and allow the user to use after the verification is passed;
[0074] Obtain wide-angle image monitoring information;
[0075] Extract the face information in the wide-angle image monitoring information, and compare the extracted face information with the target person information;
[0076] If it is judged that the extracted face information is consistent with the information of the target person, then another zoom camera is used to lock the target person.
[0077] After the authentication of the identity information is passed, the use authority corresponding to the identity information of the user is released.
[0078] Lockin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com