Permission access control method for alliance chain cross-chain
A technology of access control and authority control, applied in the cross-chain field of alliance chain, it can solve the problems of difficult security interaction, uncontrollable data access, and difficulty in implementing authority access interfaces, so as to ensure security, prevent unauthorized operations, and divide functions. clear effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to clearly explain the present invention and make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the technical solutions in the embodiments of the present invention are clearly and completely described below in conjunction with the drawings in the embodiments of the present invention, in order to Those skilled in the art can implement it by referring to the text of the description. The technology of the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments.
[0048] Glossary:
[0049] CCTP: Cross Chain Transport Protocol, a cross-chain protocol that realizes data transmission between cross-chain gateways and cross-chain networks.
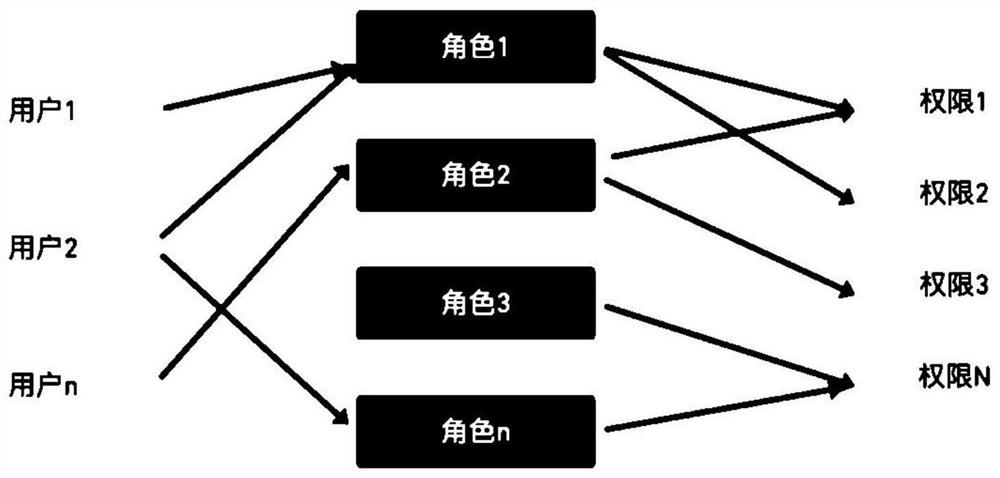
[0050] Namespace, namespace: A form of code organization is classified by namespace to distinguish different code functions.
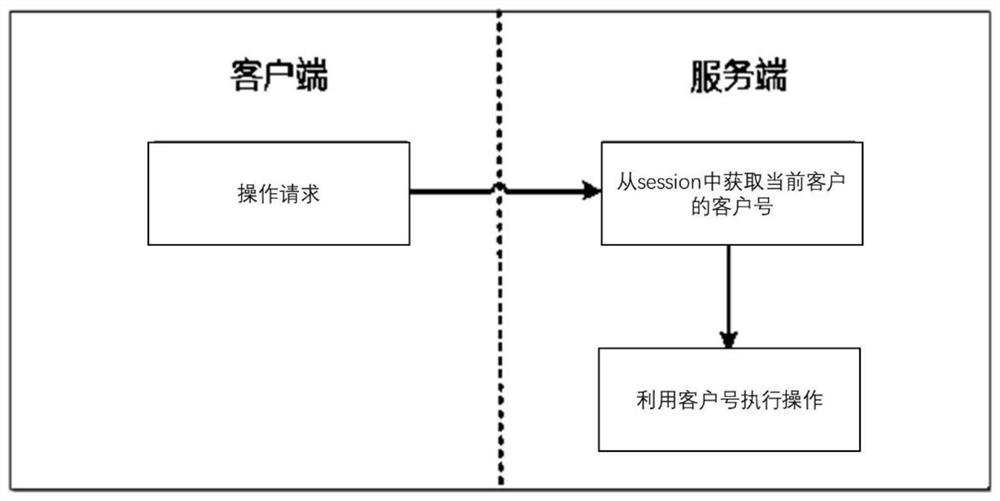
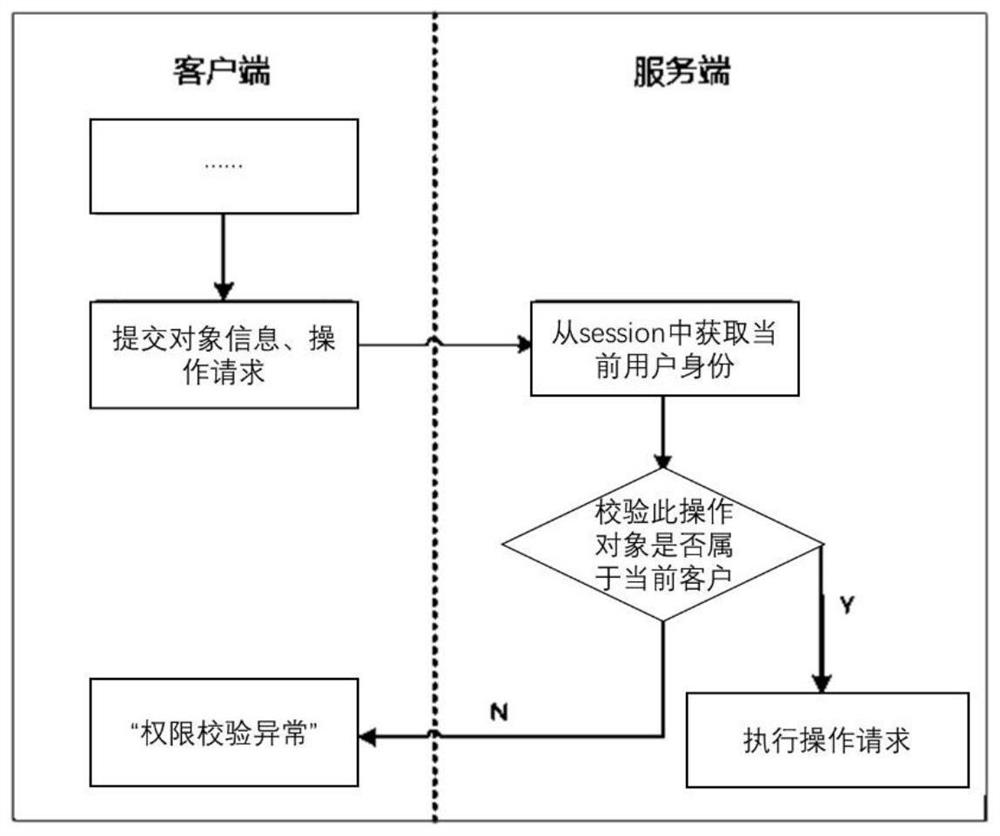
[0051] Session: session control. When the user jumps between the web pages of the ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com