System, method, and service for performing unified broadcast encryption and traitor tracing for digital content
a broadcast encryption and digital content technology, applied in the field of preventing piracy of digital content in the broadcast encryption system, can solve the problems of piracy, major concern of content providers, and threat of digital revolution, and achieve the effect of preventing future piracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027]The following definitions and explanations provide background information pertaining to the technical field of the present invention, and are intended to facilitate the understanding of the present invention without limiting its scope:
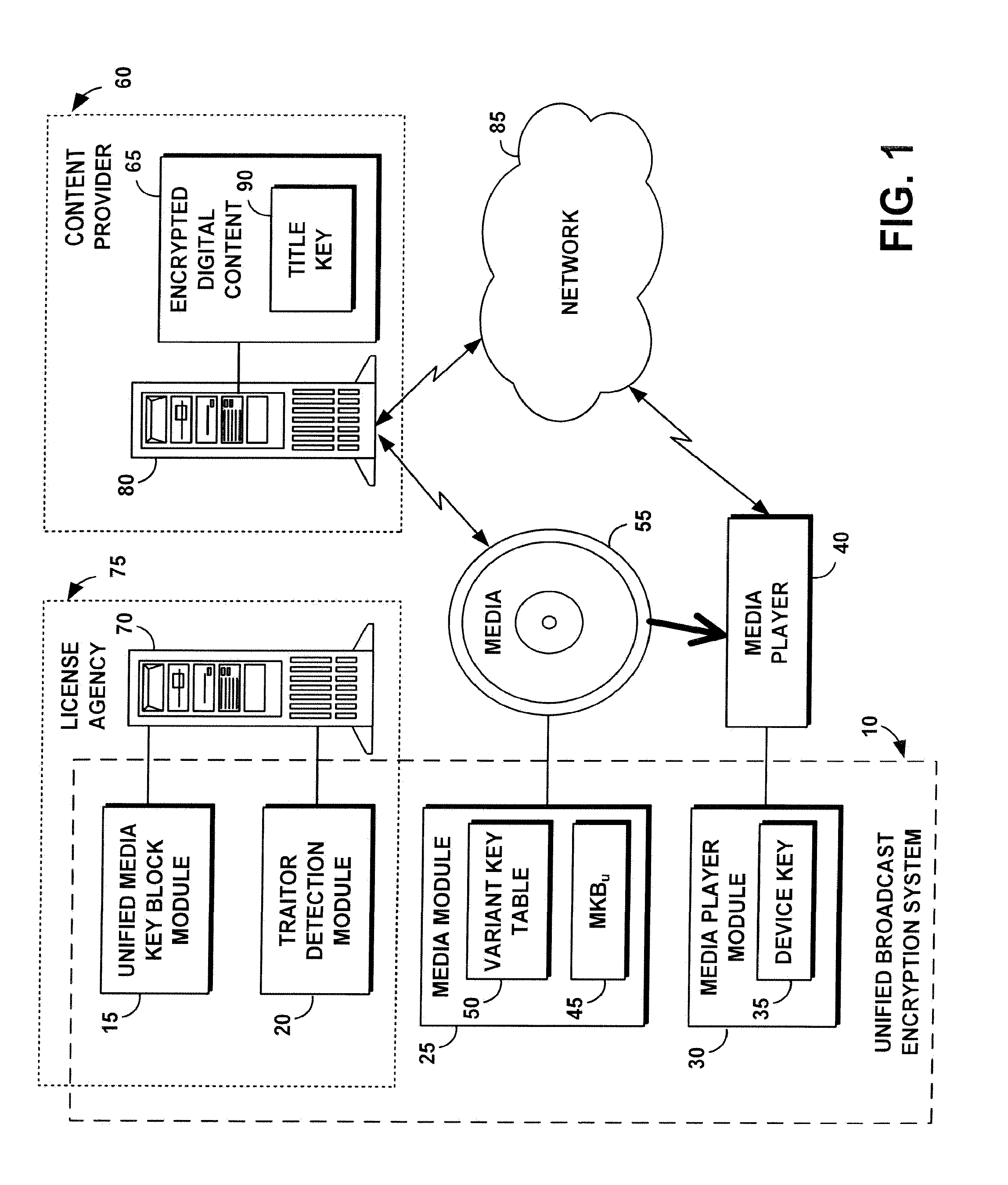
[0028]Media Key Variant (Kmv): Any of several valid media keys obtained by processing the unified media key block. In contrast, conventional processing of a conventional media key block obtains one media key.
[0029]Unified Media Key Block (MKBu): A structure comprising different media key variants encrypted by different device keys. Compliant devices obtain different valid media key variants after processing the MKBu.
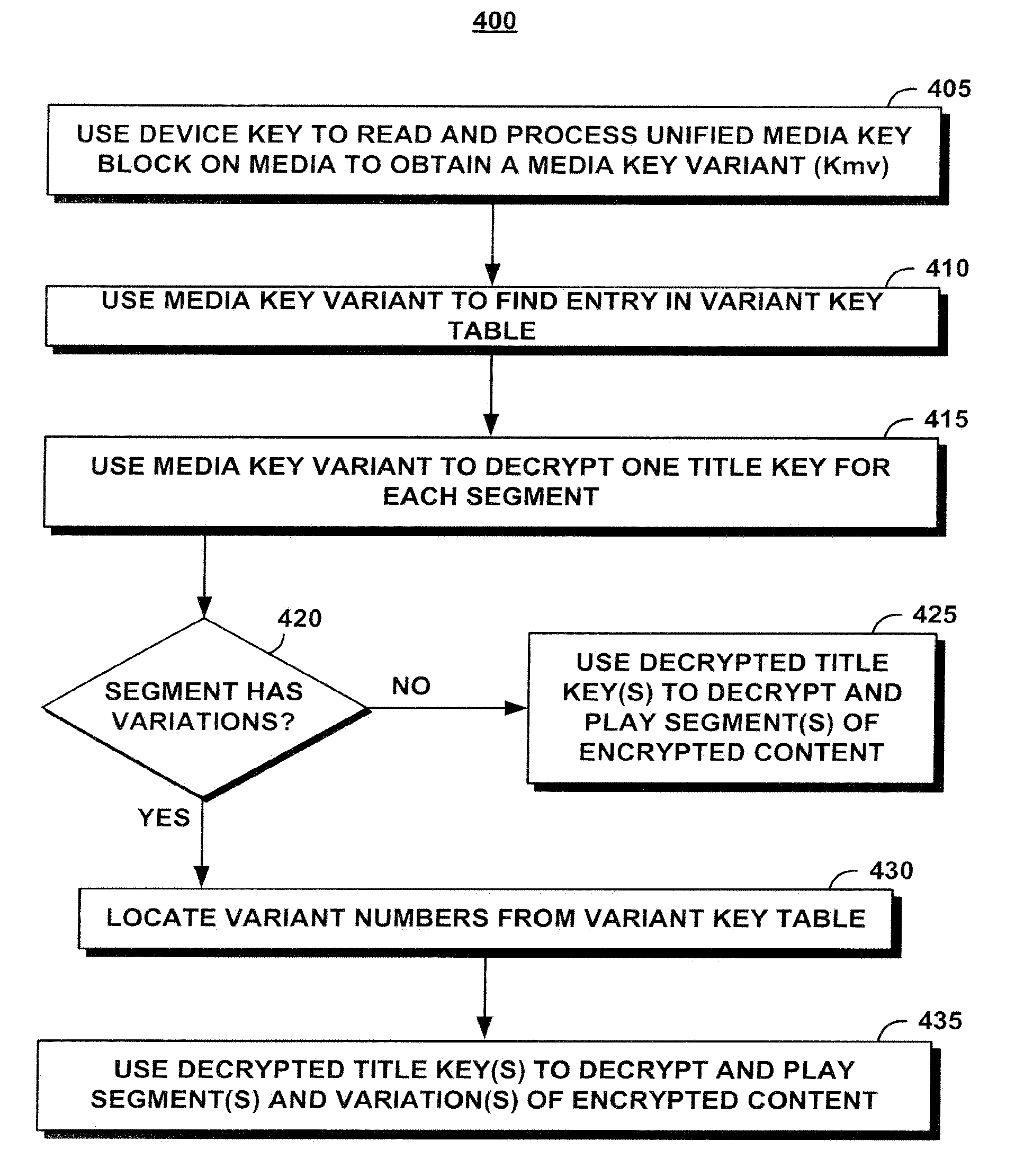
[0030]Variant Key Table: A table that allows a device with a media key variant to calculate a list of title keys. Rows of the table are indexed by Kmv. Columns of the table comprise the segments for the content. Each entry ij in the table contains the title key encrypted by Kmvi for segment j.
[0031]Title Key (Kt): The key used to encr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com