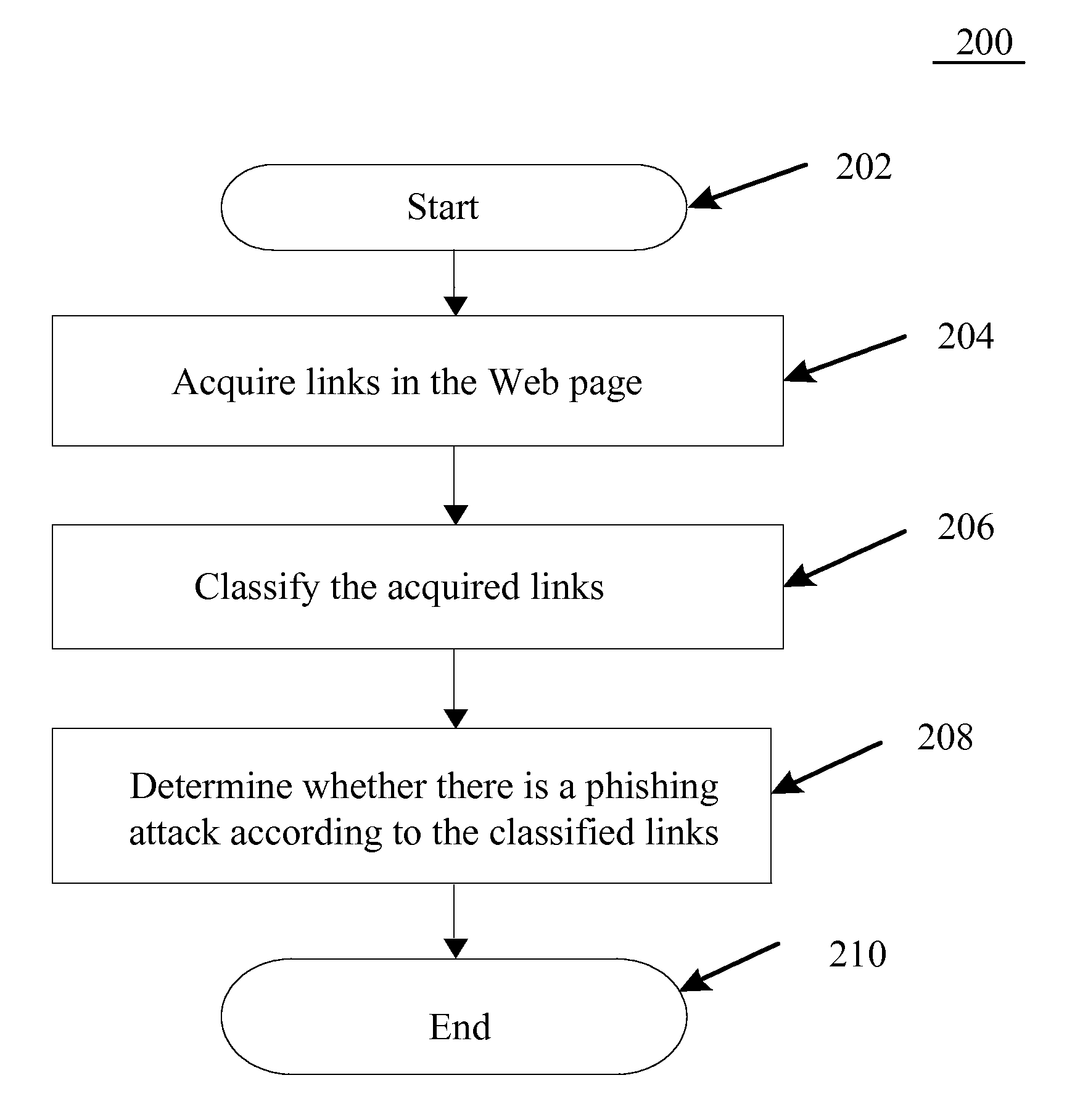
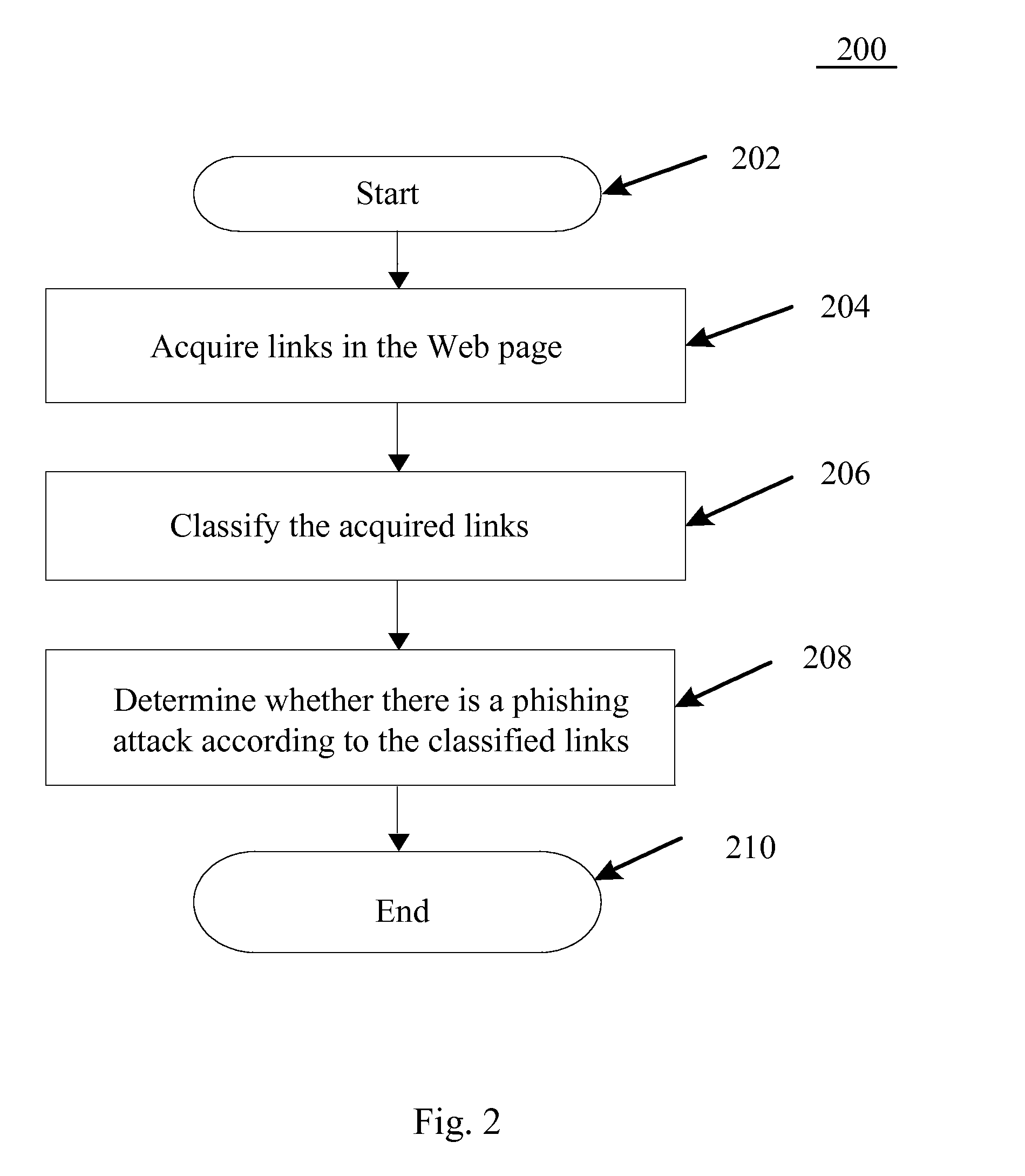
Method and System for Preventing Phishing Attacks
a technology of phishing attacks and methods, applied in the field of network security, can solve problems such as the difficulty of detecting whether a website is a fake website, and achieve the effect of preventing unnecessary losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018]In the following will be described exemplary embodiments of the present disclosure in conjunction with the accompanying drawings. For clarity and simplicity, not all the features of the actual embodiments are described herein. However, it should be understood that many decisions specific to the actual embodiments must be made during the process of developing the actual embodiments, so as to realize the specific objects of the developers, e.g., complying with those constraints related to the system and business, which constraints may change with different embodiments. In addition, it should be further understood that although the development may be complex and time-consuming, the development work is merely routine tasks for those skilled in the art with the benefits of the contents of the present disclosure.
[0019]It should also be pointed out here that, in order to prevent the present disclosure to be unnecessarily blurred by details, the drawings only illustrate the apparatus ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com