Cyber security for physical systems
a physical system and cyber security technology, applied in the field of cyber security systems and methods, can solve the problems of new vulnerabilities and susceptibilities of controlling and controlled equipment to be operated in an unwanted manner
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
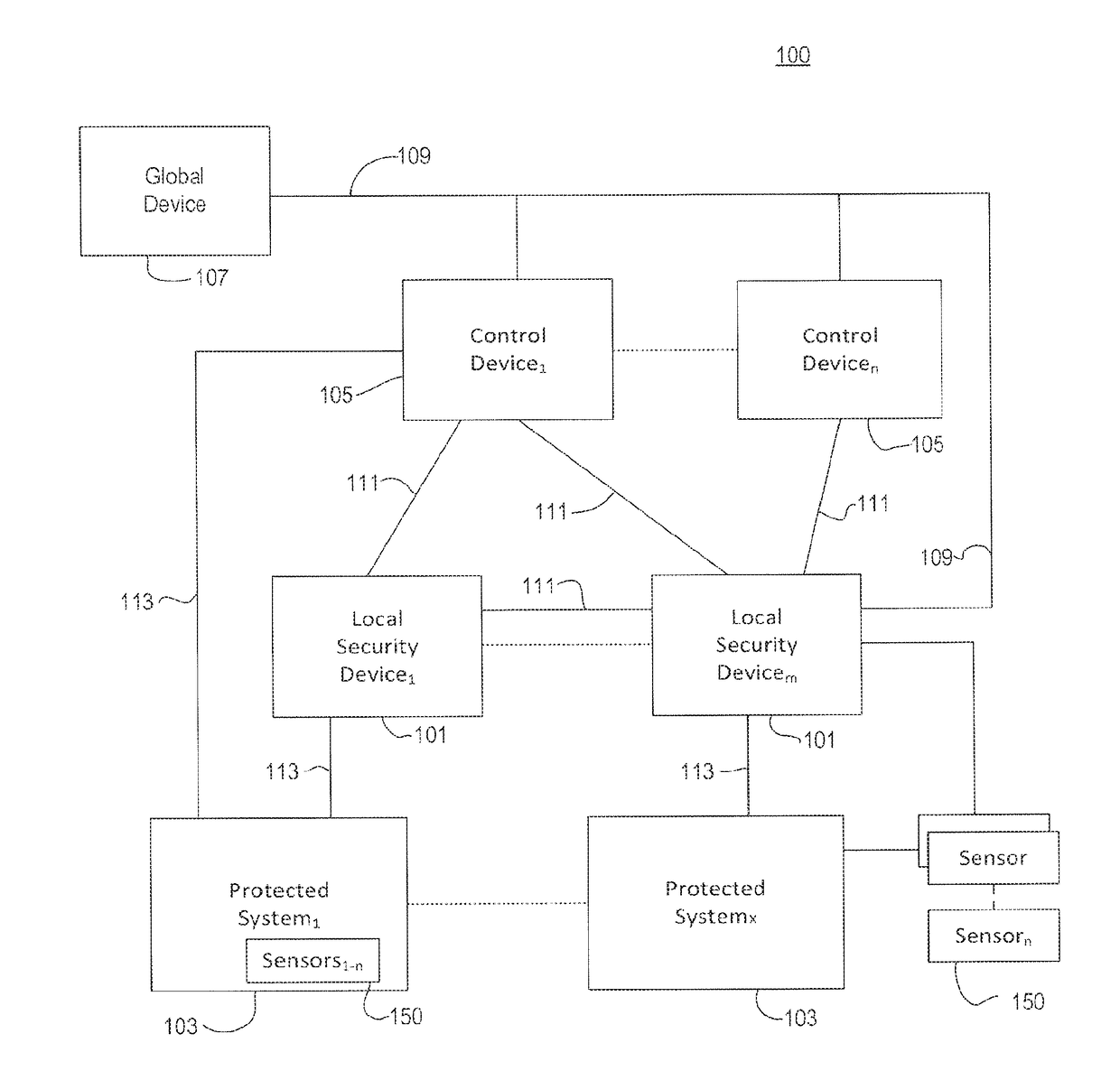
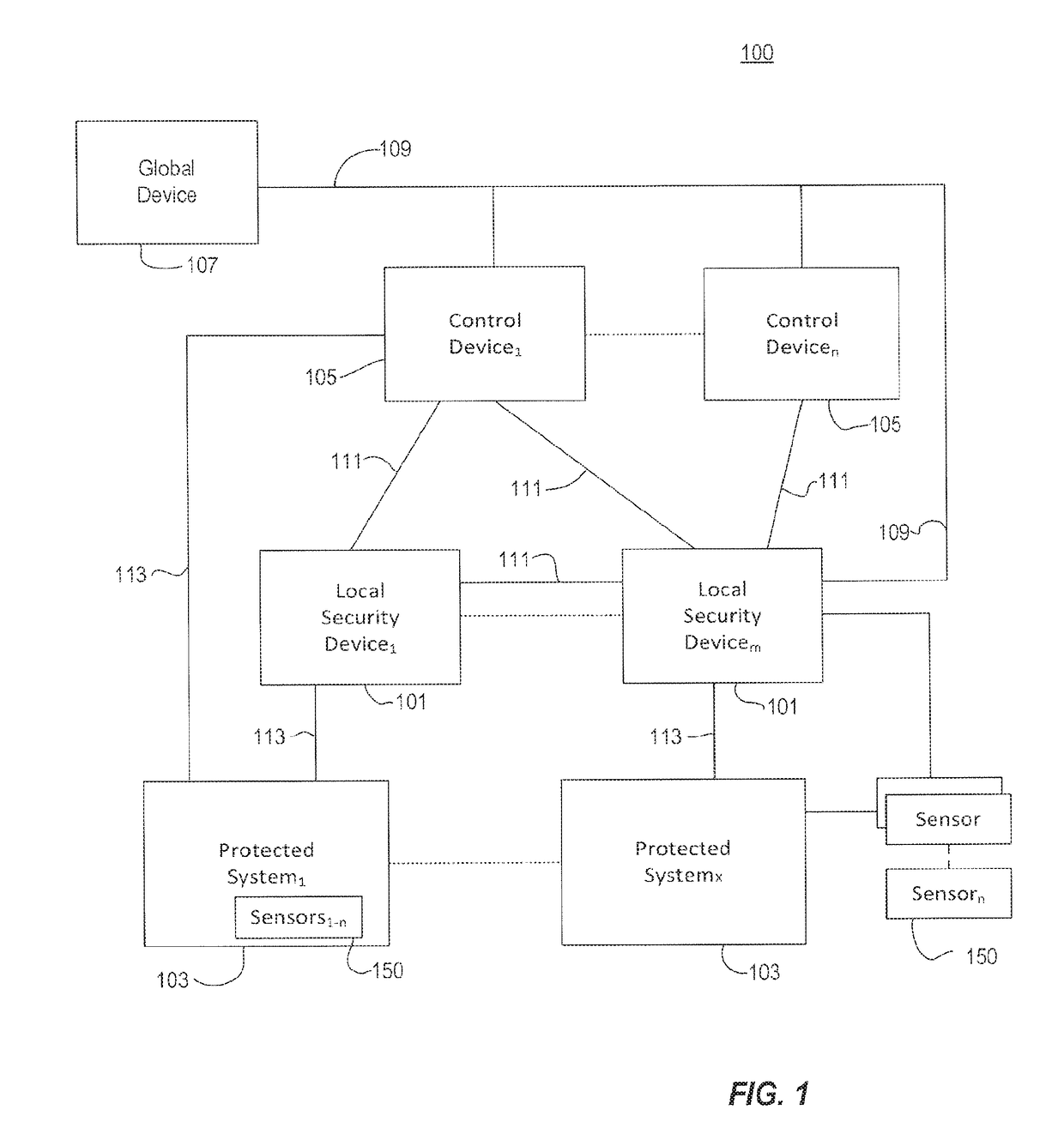
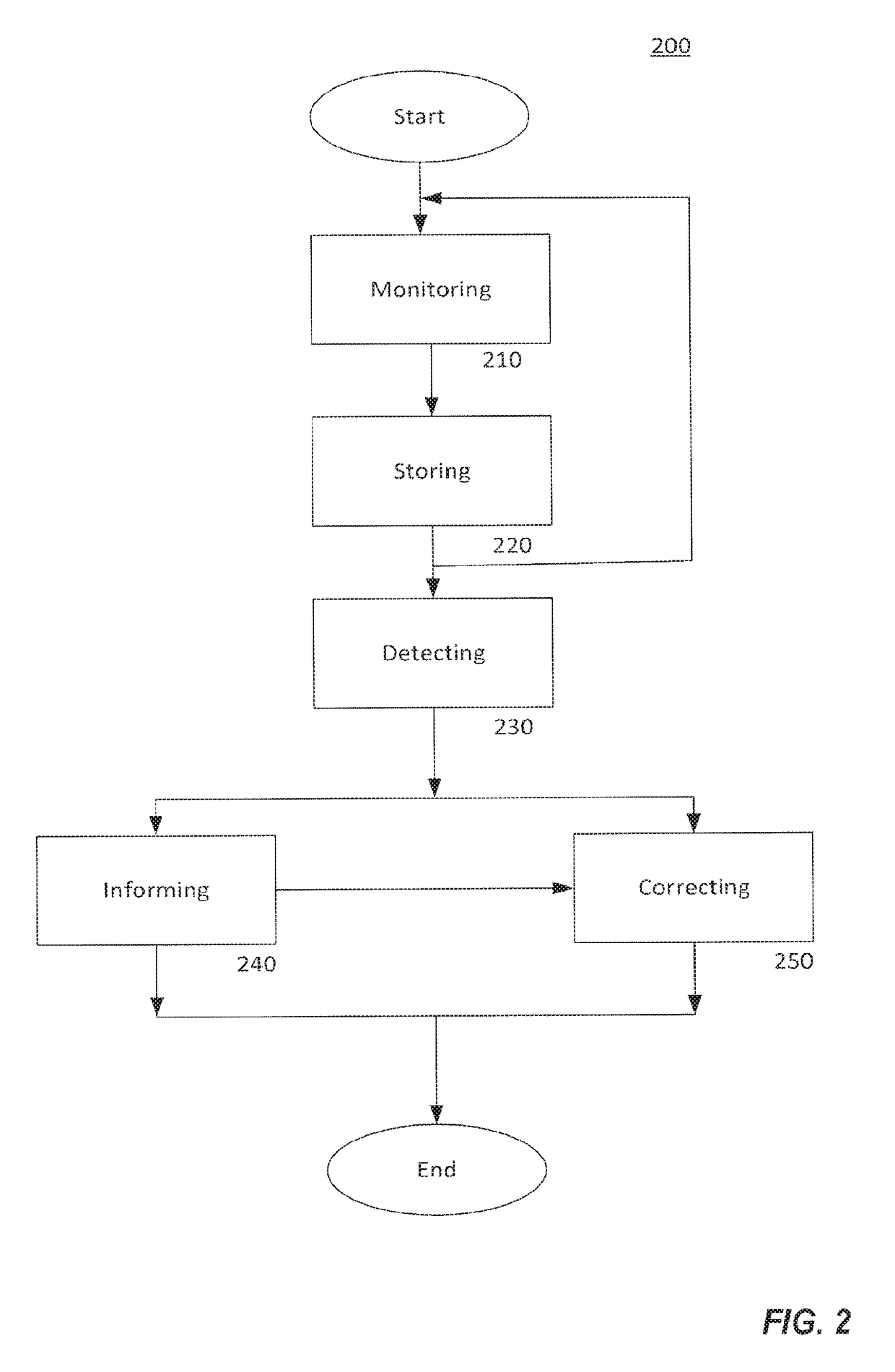
[0012]Embodiments relate generally to a cyber security system comprising at least one component, either a first or a second component, adapted to be coupled to a secured system, and may further include additional first or second components with the second component or components operatively coupled to one or more of the first components configured to monitor, control, and interact with the one or more first components based on sensed information received from the one or more first components, and a third component configured to receive information from and to monitor at least one of the second components or one or more first components as well as one or more of the third components to analyze the sensed information and the security information to determine global operational awareness. The second component is further configured to output security information to a user and to the third component. However, in some embodiments, the first component can also output security information t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com