LSP ping and traceroute for bypass tunnels
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020]The following detailed description refers to the accompanying drawings. The same reference numbers in different drawings may identify the same or similar elements. Also, the following detailed description does not limit the invention.
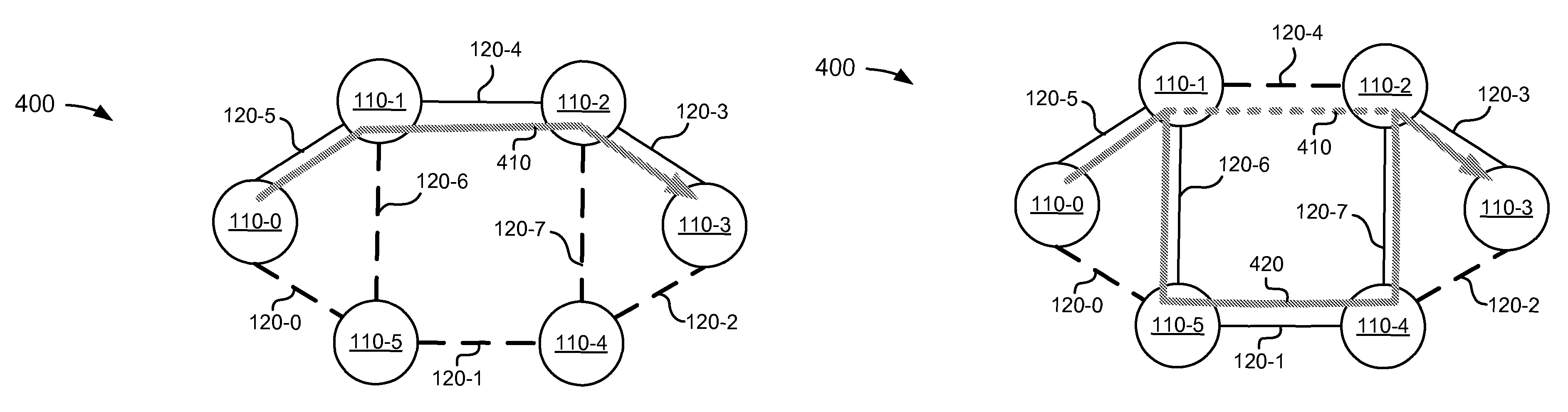
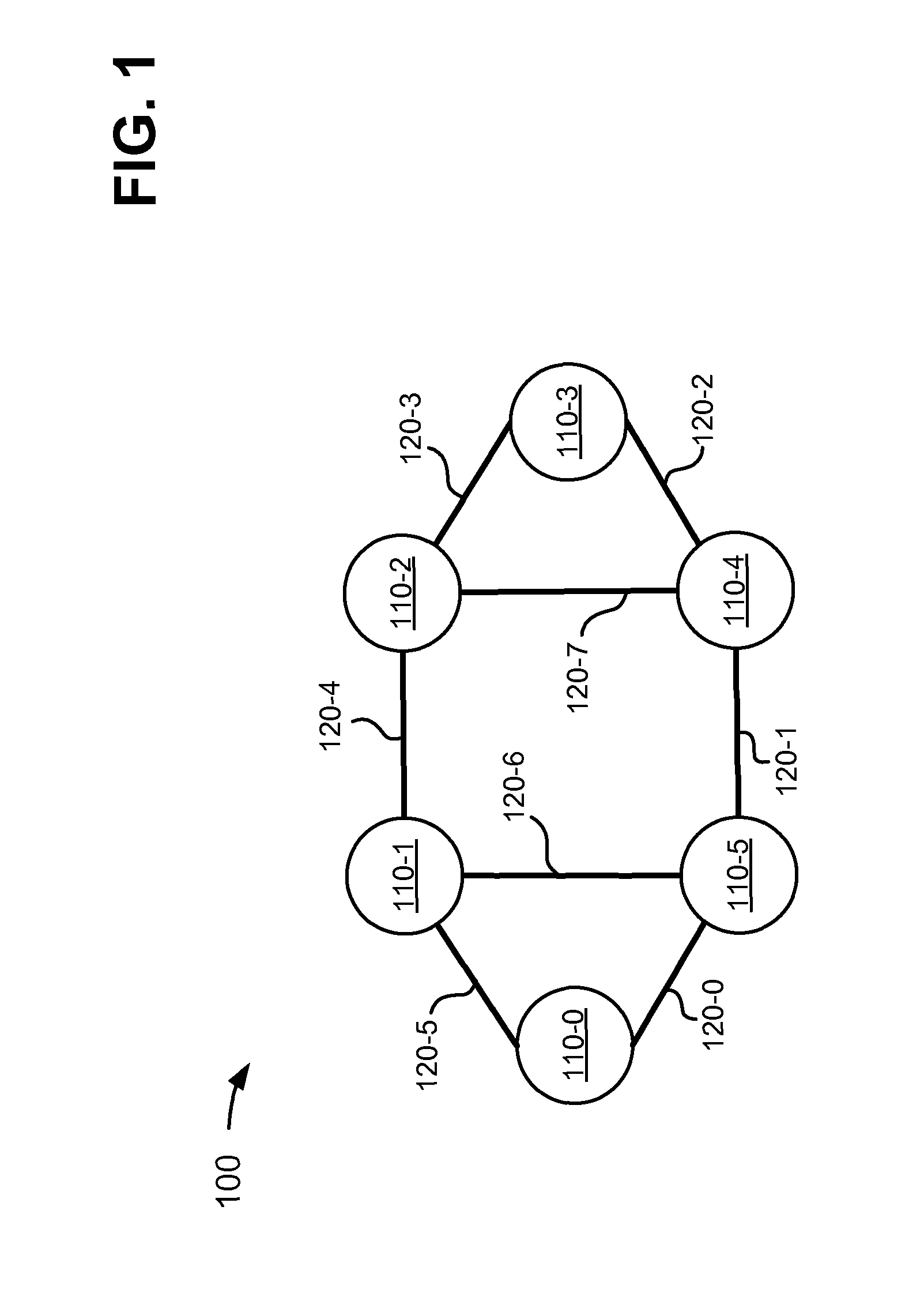
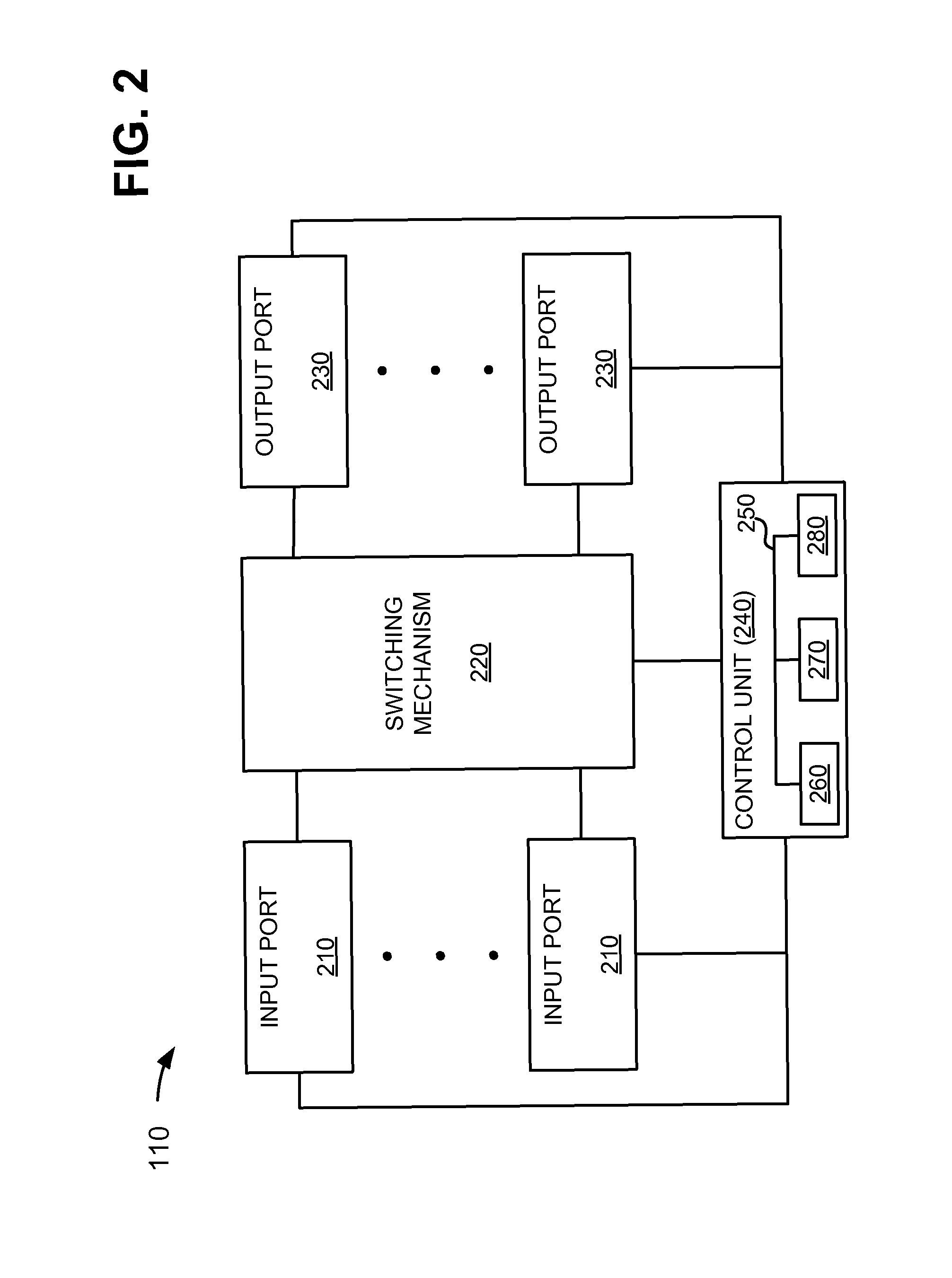
[0021]Systems and methods described herein may use label switched path (LSP) ping and LSP trace mechanisms for evaluating bypass paths, such as resource reservation protocol (RSVP) tunnels, for an LSP in a multiprotocol label switching (MPLS) network. Each bypass path may provide a failure mechanism across a protected link and / or node in the LSP. Generally, the bypass path will be used only in case of failure of the protected link and / or node. Thus, in a normal LSP scenario, there is no way for the ingress of an LSP to know if the bypass paths are working prior to a failure in the LSP. The systems and methods described herein may assemble MPLS echo request that instructs a transit node to send the echo request via a bypass path associated with the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com