Keyboard encrypting method
An encryption method and keyboard technology, which is applied to the data security of ATM operating keyboards and the field of ATM operating keyboards, can solve the problems of user account and password confidentiality data confidentiality, and achieve the effect of preventing data leakage and theft and improving data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The preferred embodiments of the present invention shown in the accompanying drawings will be described in detail below.
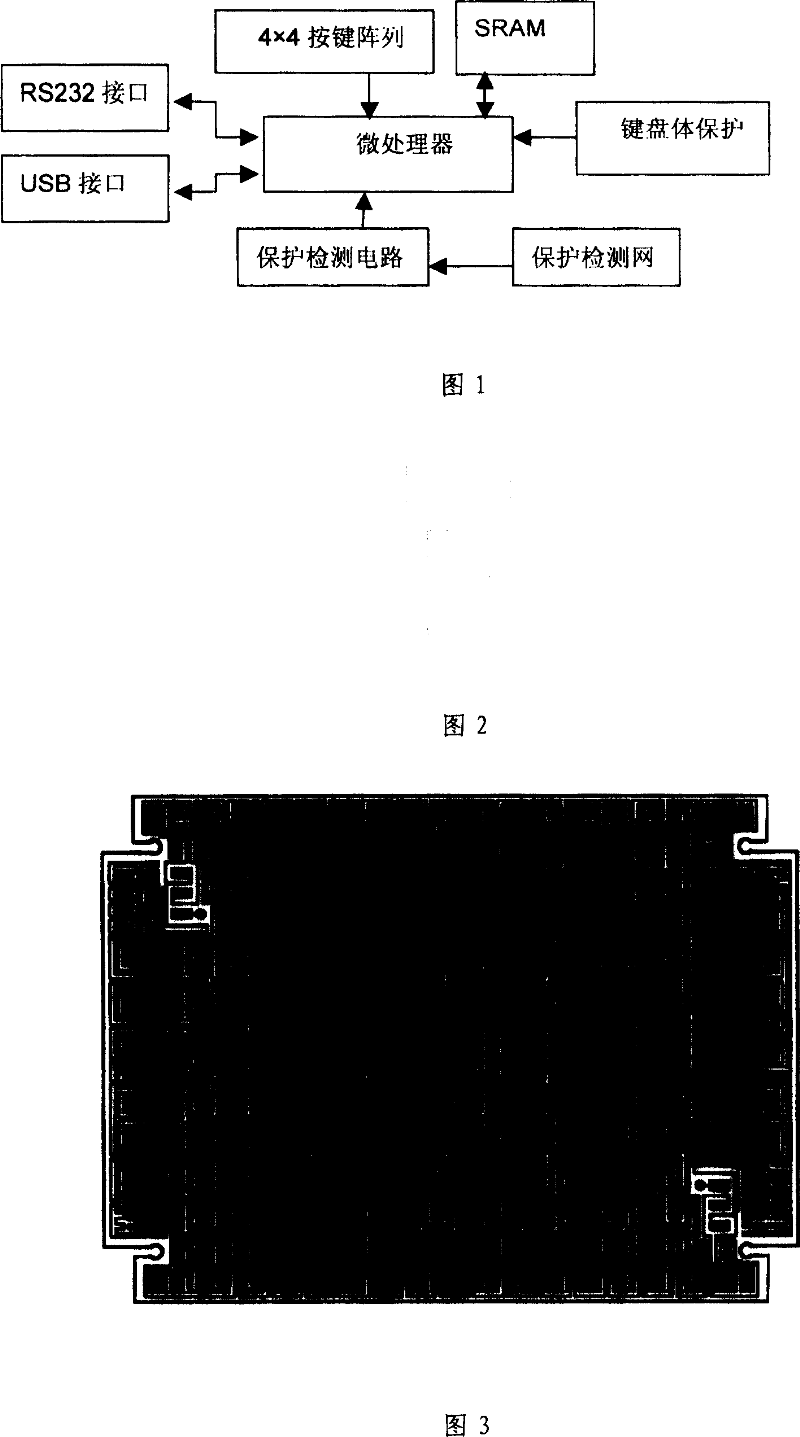
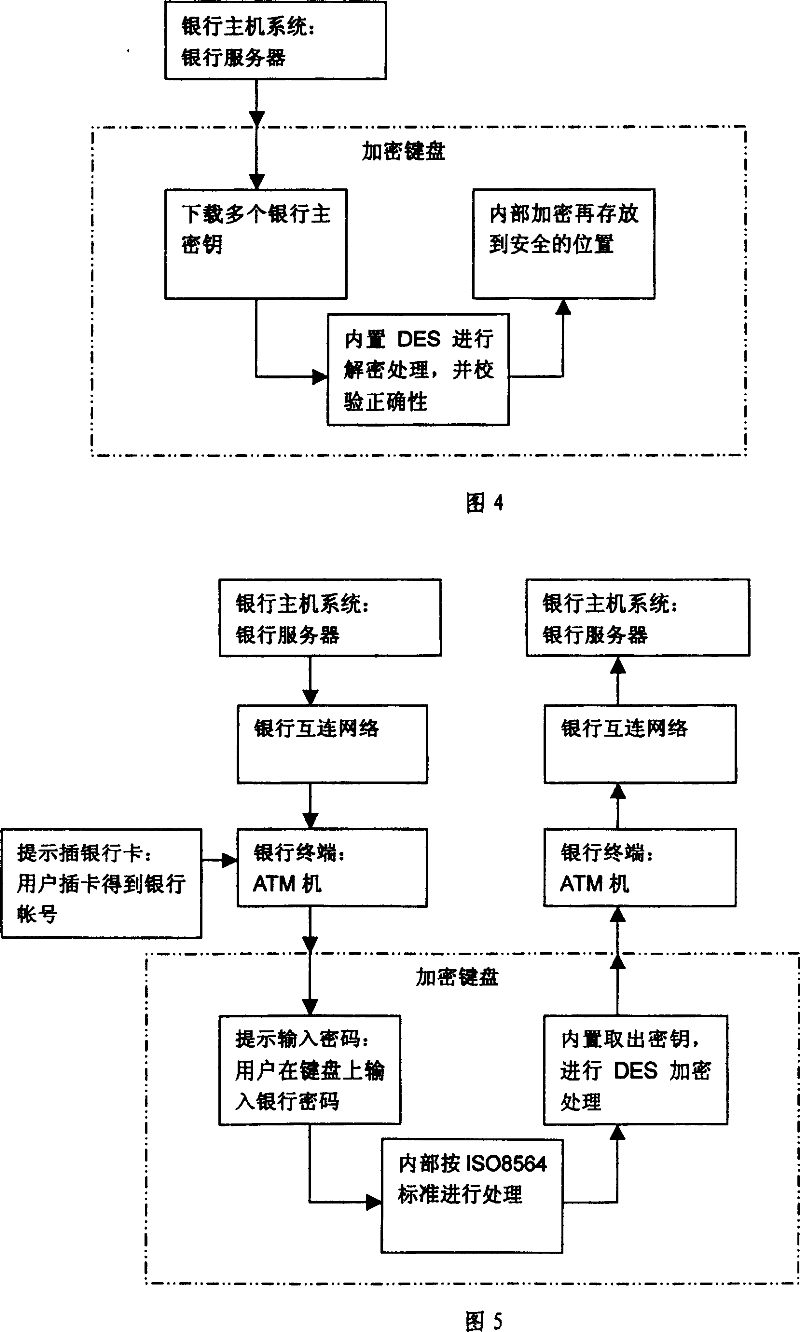
[0025] The metal encryption keyboard for an ATM terminal realized by the keyboard encryption method of the present invention includes a panel, a liner, a sealing gasket, a conductive rubber key board, and the keys are electrically connected to the printed circuit board and the base, and the panel is connected to the base. The base surrounds a keyboard cavity, the cavity is provided with a printed circuit board for keyboard processing and a power supply battery, the panel is provided with openings, and each key protrudes from the openings, and also includes a panel located between the panel and the lining. The protection small axis between the boards; the keyboard processing printed circuit board can be divided into a security function processing part and a non-secret function processing part, and the security function processing part is closed with a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com