User access authorization management method and system
A technology of access rights and management methods, which is applied in the field of management of user access rights, and can solve the problems of complex business systems that are not optimal and single users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
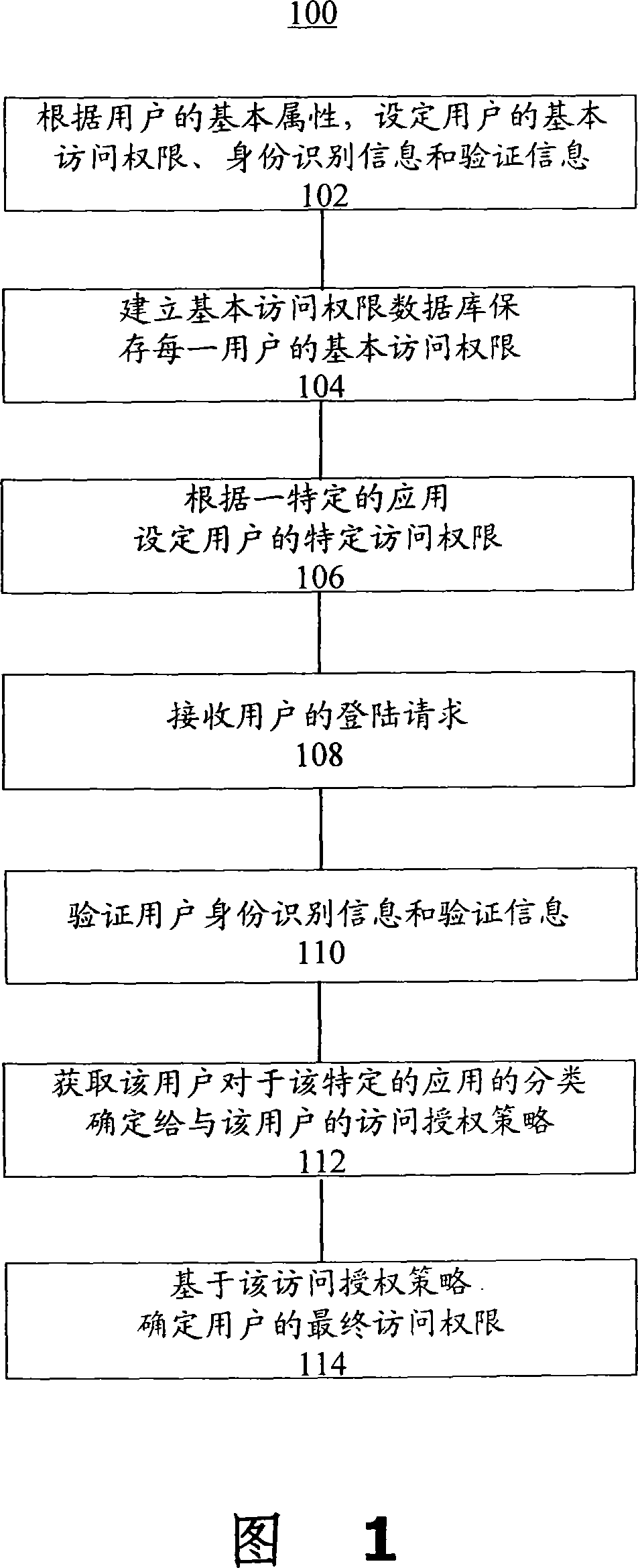
[0029] The present invention provides a method for managing user access rights. With reference to FIG. 1 , a flowchart of an example 100 of the method is shown. The method 100 includes:
[0030] 102. According to the user's basic attributes, set the user's basic access authority, identification information and verification information. According to an embodiment of the present invention, the method is applied to a public security system. At this time, the basic attributes of the user include name, position, rank, and jurisdiction. The authentication information includes user digital certificates and passwords. According to a requirement in the implementation, the user is required to submit the user digital certificate and password at the same time, and the user digital certificate should meet the requirements of the relevant state departments.
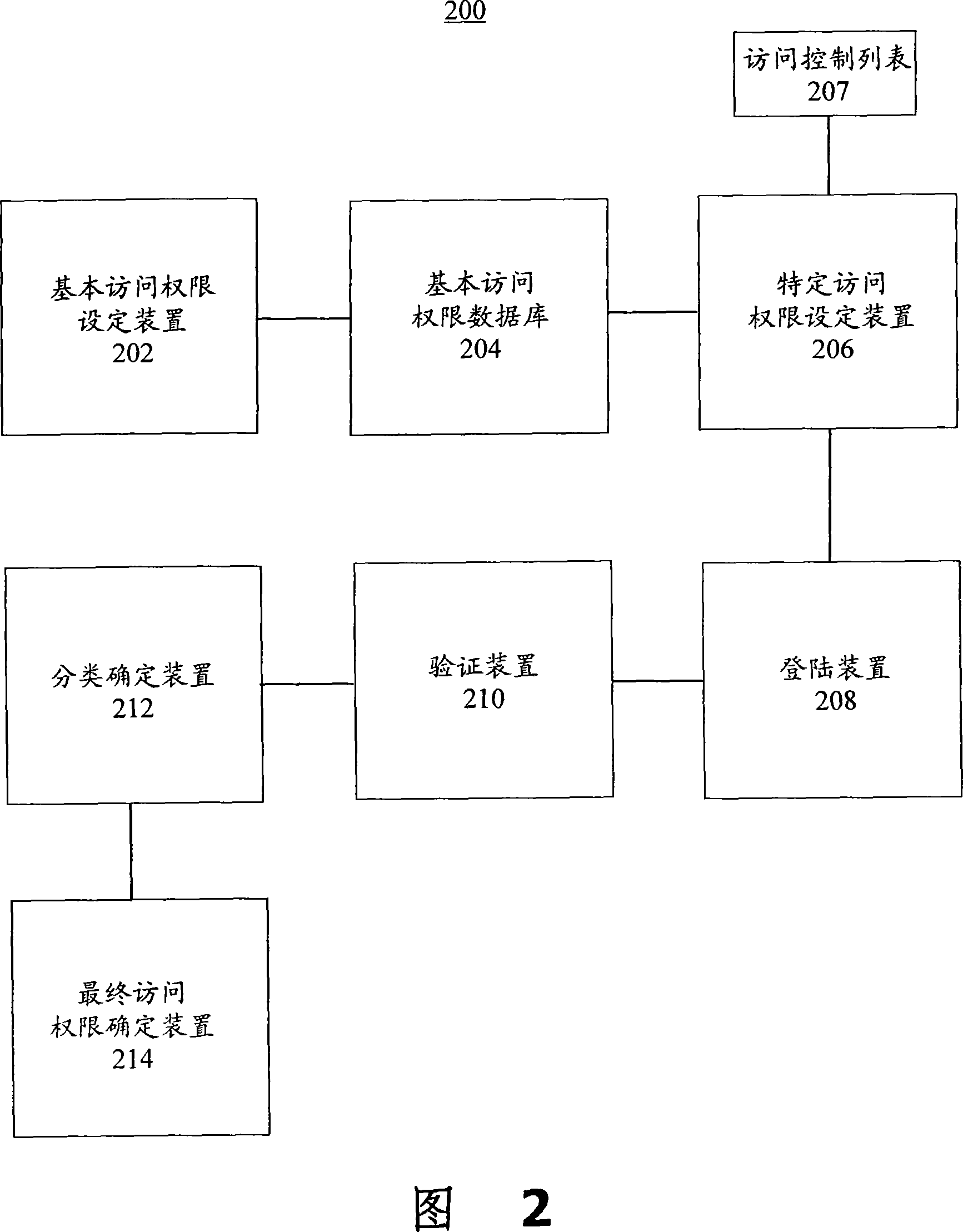
[0031] 104. Establish a database of basic access rights to store the basic access rights of each user. The basic access authority d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com