Network equipment identification method
A technology of network equipment and authentication method, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the threat to MS communication security and other issues, achieve the effect of simple authentication process and solve the threat of user communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
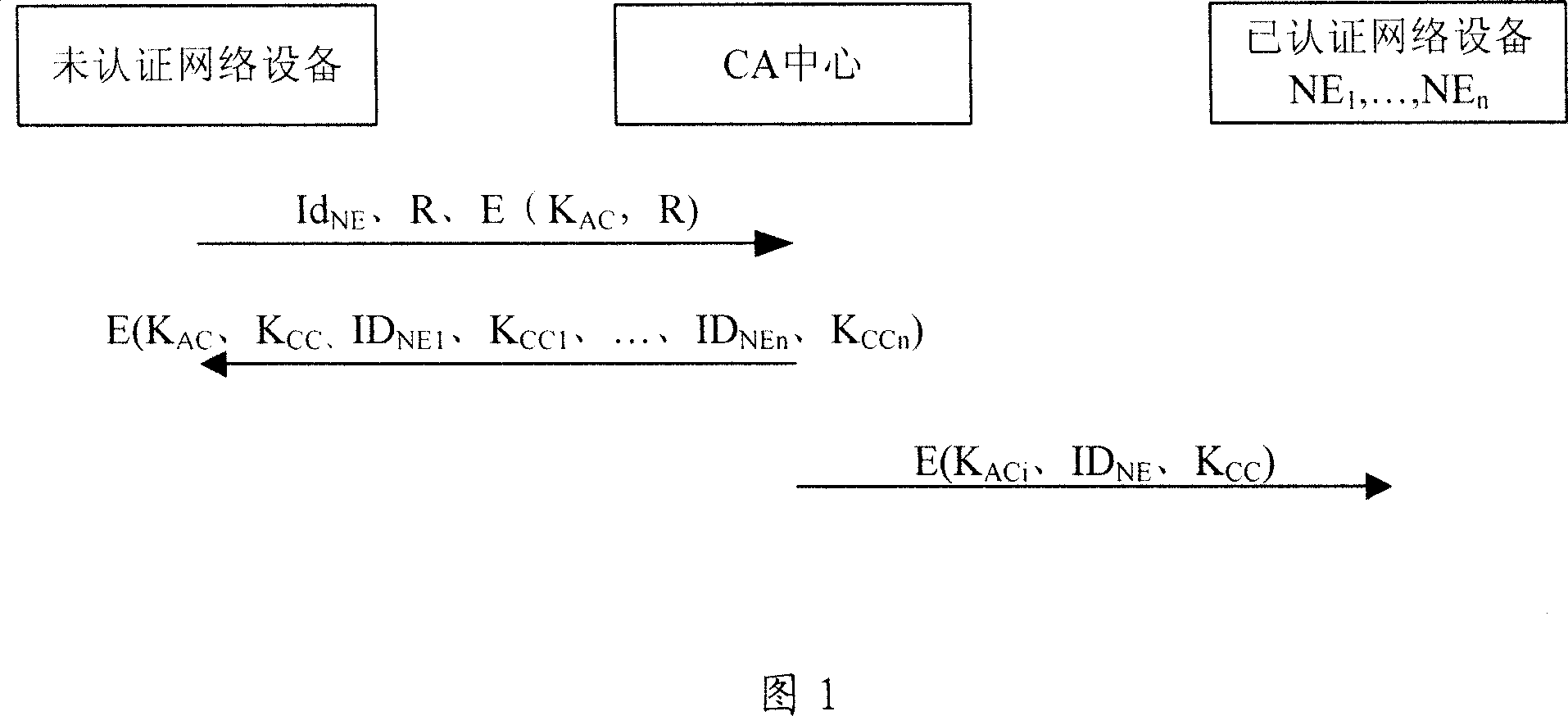
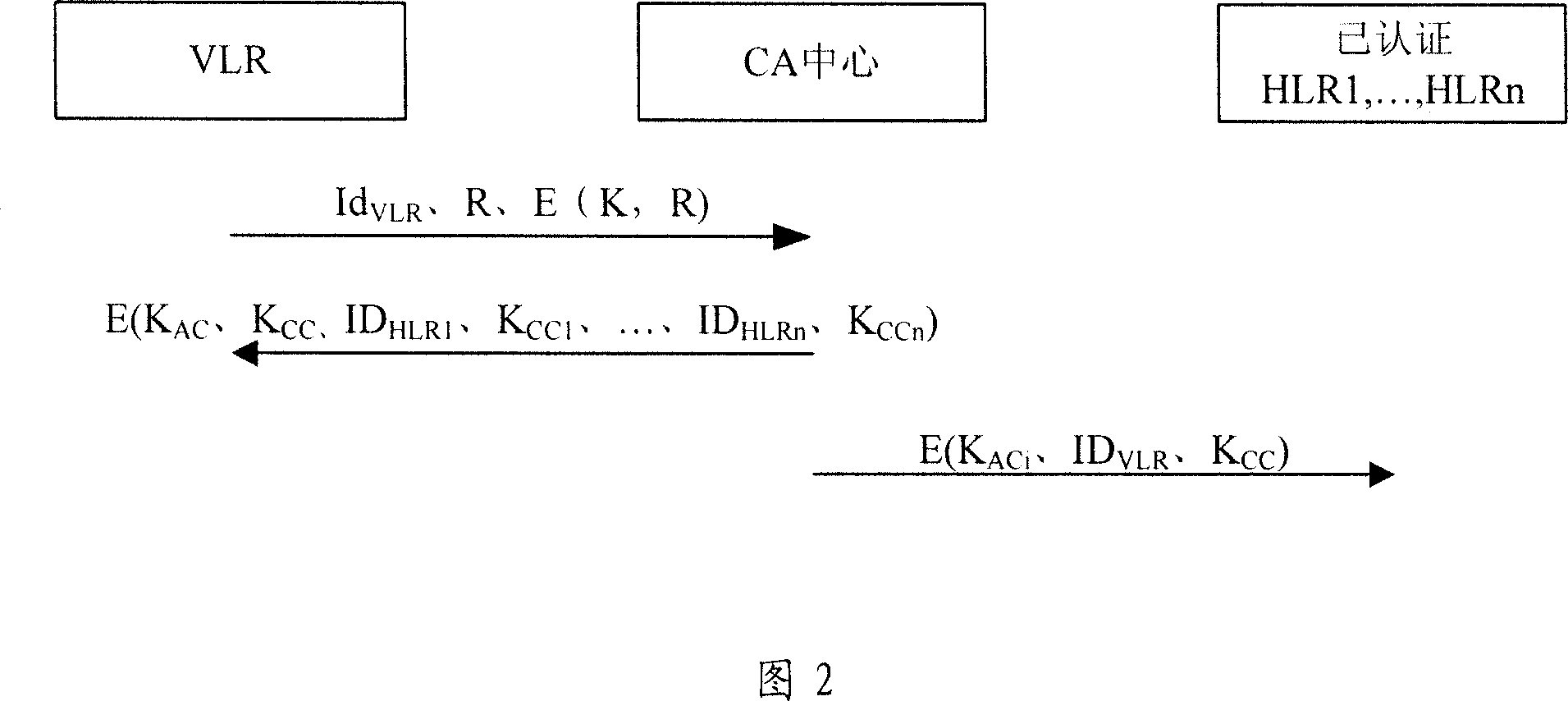
[0020] In order to facilitate a deep understanding of the technical content of the present invention, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0021] A network device authentication method provided by the present invention, the method includes:
[0022] Provide a smart card to a network device that needs to be authenticated, and the smart card includes at least a network device identity ID NE , the encryption key K shared with the CA center AC One or more of the information in ;
[0023] The network device generates a random number R and uses the encryption key K AC Encrypt the random number R to obtain the encrypted result E(K, R);
[0024] The network device sends the above encryption result E(K, R), the random number R, and the network device identity ID NE Send to CA center;
[0025] The CA center uses the encryption key K shared with the network equipment AC Decrypt the encrypte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com