Authentication method and authentication equipment for implementing network access, and user equipment
A technology of user equipment and authentication equipment, which is applied in the field of communication, can solve problems such as complicated authentication process, poor network usability, and complex process, and achieve the effects of improving network security, resisting exhaustive attacks, and simplifying the authentication process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
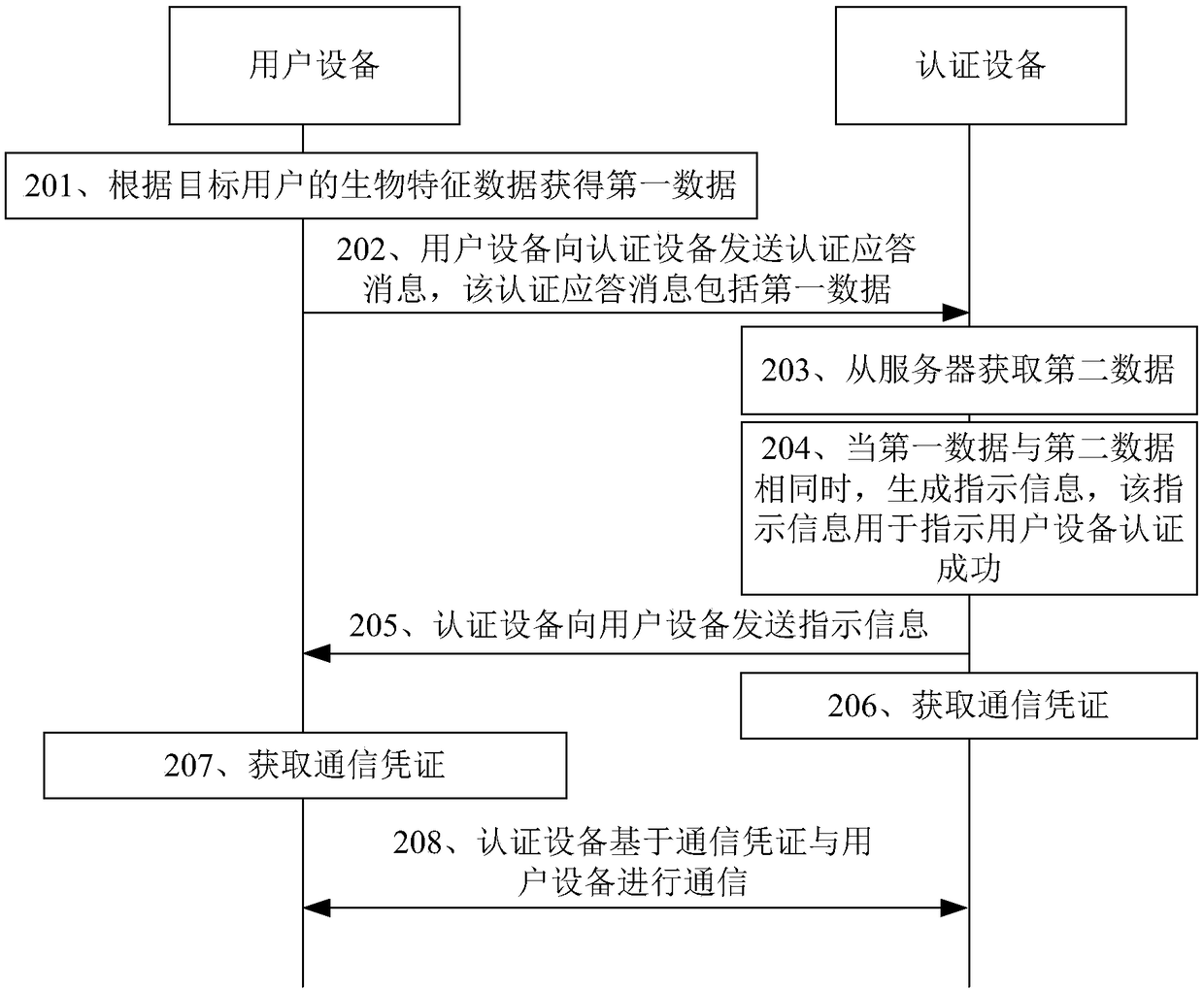
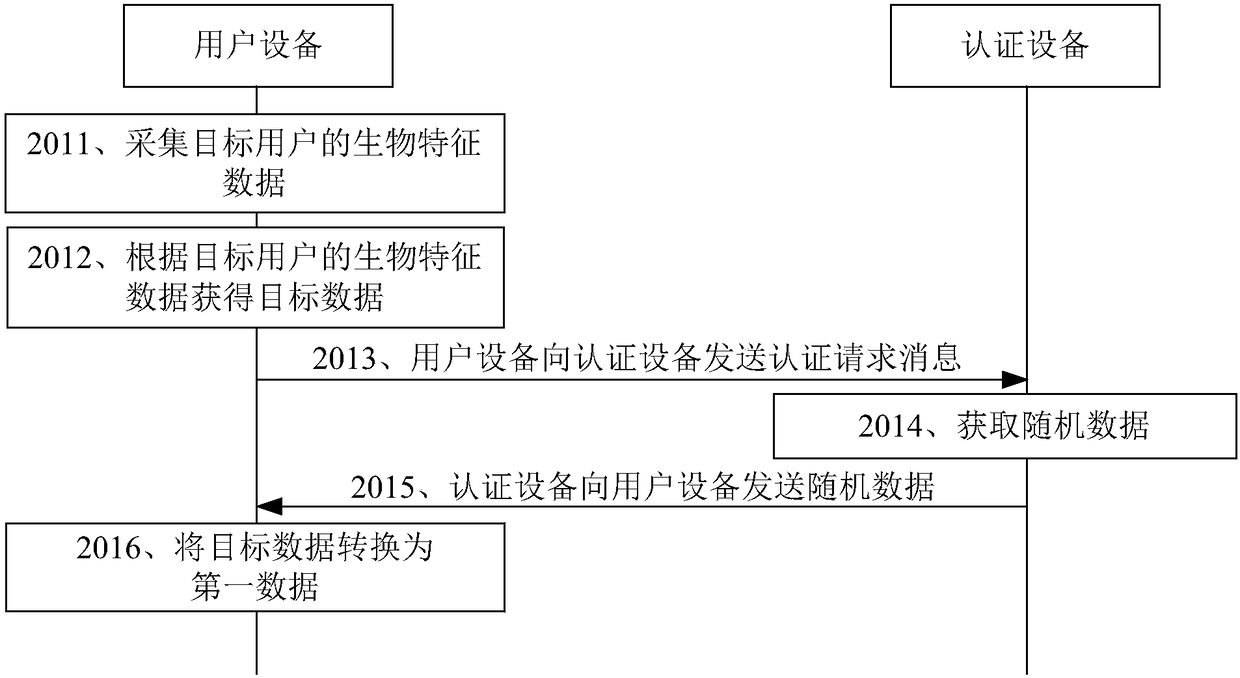
[0064] In order to make the purpose, technical solution and advantages of the present application clearer, the implementation manners of the present application will be further described in detail below in conjunction with the accompanying drawings.
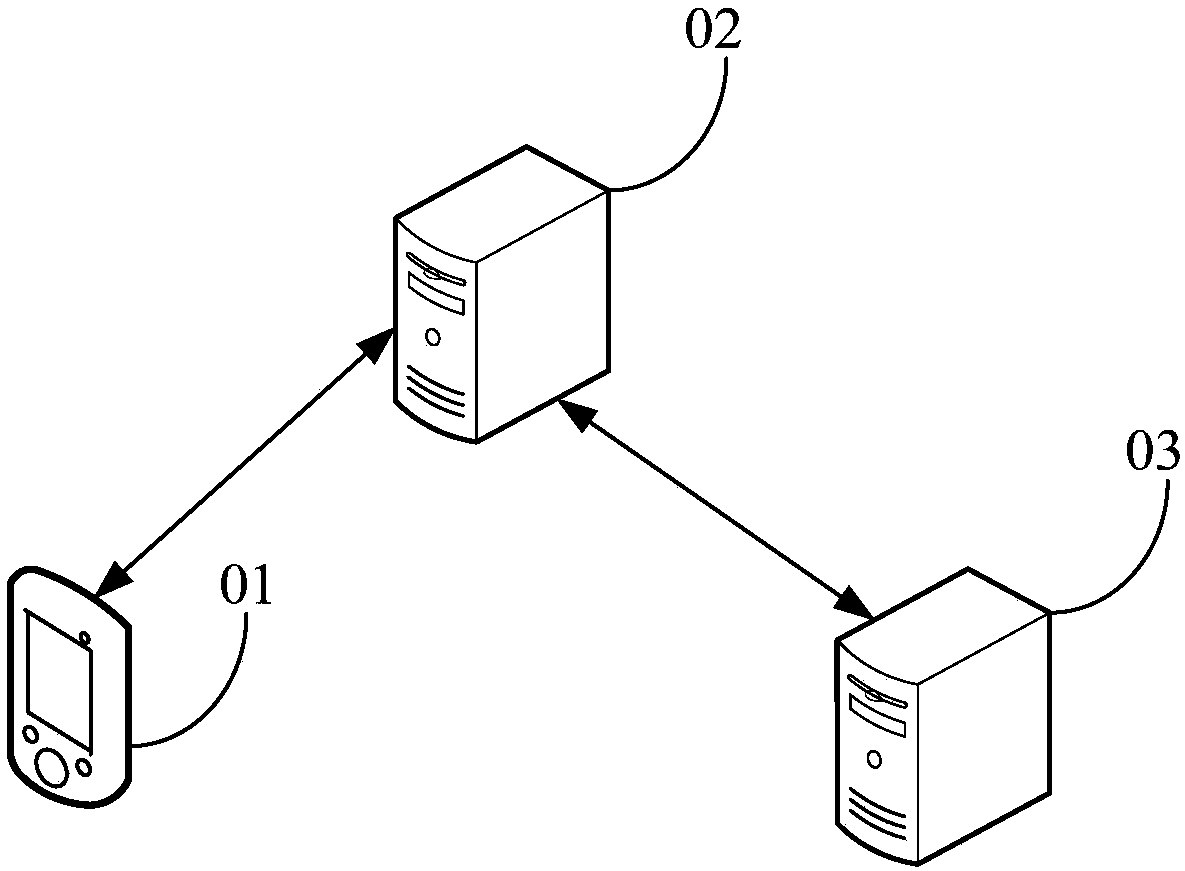
[0065] Generally, a home network often adopts technologies such as WIFI (such as 802.11), visible light communication (Visible Light Communications, VLC) (such as 802.15.7) and other technologies for wireless Internet access. During this process, the user equipment uses a password to perform an authentication operation. When user equipment adopts password to perform authentication operation, there are often the following problems: 1. Wireless equipment, such as WIFI access point (Access Point, AP), or customer premise equipment (Customer Premises Equipment, CPE) are less stable, often error occured. After a fault occurs, the wireless equipment or customer premises equipment needs to be reset and restarted. Taking a wireless dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com